3. Take Down Your Competitor’s Web Site
It’s 4:30 p.m. and Phoenix has had about all he can take from his boss today. As he gathers his belongings and gets ready to leave work, he fights the urge to go tell his boss to go jump in a lake, along with some various profanities. As Phoenix heads for the train station, his cell phone chirps to let him know he’s just received a text message. He opens it and a text message from a number that reads 0000000000 says: “The normal place at 6.” Phoenix is overcome with confusion, anger, and fear all at the same time. He knows who this message must be from. However, he threw away the phone he used to communicate with the shady Mr. Dobbs months ago, shortly after the last job he did for him. For a moment Phoenix ponders how the hell this guy got his personal cell phone number, and then realizes it’s a dumb thing to ponder. Dobbs had told him that he’s always watching him and always will be.
After boarding the train, Phoenix debates with himself on whether he should go to the normal coffee shop and wait for Mr. Dobbs, or just ignore the message and continue with his life as normal. The debate is relatively short. As Phoenix recalls some of the threats Mr. Dobbs made in the past, he quickly decides that ignoring him is probably not the best idea. “Next stop Madison and Wabash,” the announcer says over the intercom of the train. Phoenix gets up and waits at the door for the train to stop. He gets off, heads down the platform to the street below, and quickly makes his way to the coffee shop about halfway down the block. He looks at his watch and it is 5:50 p.m. “Good timing,” Phoenix thinks.
As he walks into the coffee shop, he quickly scans the room and realizes that Mr. Dobbs is nowhere in sight. Just as Phoenix is about take the opportunity to bolt, a gentleman sitting in the corner calls out, “Hey kid, come here for a minute.” Phoenix walks over to the man and asks whether he can help him. “Yeah, Dobbs referred you.” At that, Phoenix replies, “I don’t know who or what you’re talking about, sir.” The man glares at Phoenix and then sternly says, “Dobbs said you might be a little nervous, but he told me to tell you that the grass at 5638 Cherry Street really needs to be cut, whatever that means,” the man shrugs. Phoenix now feels the familiar chill come over his body and his mouth goes completely dry. Phoenix knows very well what it means, and realizes that Mr. Dobbs really did send this man. With this affirmation, Phoenix takes a seat across the table from the gentleman and hesitantly asks, “So, what do you need?”
The man wastes no time getting to the point. “My client is an e-commerce–based company that sells computer parts and peripherals online. It nets about $9 billion per year. A public interest nonprofit entity is planning to release some damaging information about my client a week from tomorrow. We have someone working on the inside of the entity to eventually get the person responsible for digging up this information fired. And at that point, it’ll be a non-issue. But we need the nonprofit’s Web site to be down or inaccessible on that day. We need it down long enough for the market to close and trading to end. The information being released might scare away some investors and could have devastating effects on our stock price. We require the site to be down only that day because we will be releasing our earnings numbers for the quarter the following day. So, my client really doesn’t want its stock to tank the day before it releases its quarterly numbers.” With that, the man stops talking and looks at Phoenix in anticipation of a response.
“So, you want me to take down the Web site for a day?” Phoenix asks.
“Yes,” replies the man.
“What about defacing it?” Phoenix asks.
“No, we need it to just appear that it is having technical difficulties. We know the nonprofit is underfunded. So, we infer it is hosting its own Web site and doing so with minimal bandwidth.”
Phoenix thinks for a second, and then replies, “Okay, so what’s the nonprofit’s name?”
Quickly the man lays a big brown envelope on the table and shoots back, “All you need to know is in there. I’m not concerned about you failing. Dobbs said you were good, and he said to let you know he’d deal with it personally if you were unsuccessful. There’s $5,000 cash in the envelope along with other documentation you might need. Meet me here at the same time on the day of the attack to receive final payment, which will be an additional $50,000.”
Before Phoenix can even get the word “okay” out of his mouth, the man is up and heading for the door.
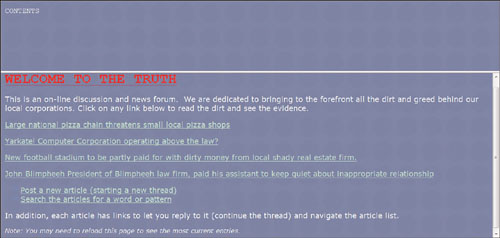
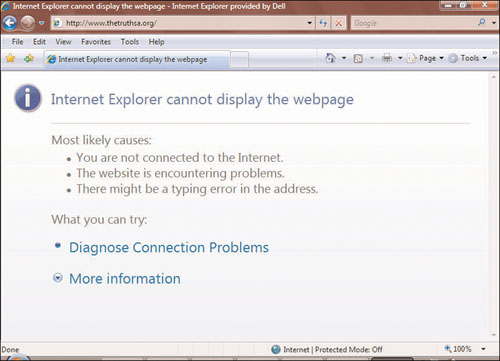
On his way home, Phoenix runs scenarios through his mind, remembering various techniques he’s read about taking down Web sites. He doesn’t even bother to open the brown envelope until he makes it home. Phoenix walks into his living room and collapses onto the sofa. He rips away the tape holding down the flap on the brown envelope and opens it. The first page is a printout with details of the target. Phoenix chuckles at the name of the target company: The Truth. “How original,” Phoenix says to himself out loud. Phoenix gets up, grabs the envelope, goes over to his desk, and visits the company’s Web site. He types www.thetruthsa.org into his browser, as displayed in Figure 3.1.
The first thing Phoenix notices is how poorly put together the site seems. He decides to do a little recon on the nonprofit. It doesn’t take long for Phoenix to find, via Google, an article that explains how the nonprofit allowed high school students to build its Web page to gain learning experience. “Hmm,” Phoenix says to himself, “I bet security was not at the forefront of this design, and I bet the organization has limited bandwidth as well.” Phoenix bookmarks the page, stands up, and heads for bed.
Phoenix will use a plethora of techniques to eventually bring down his target Web site. The following is a summary of the techniques Phoenix will use to bring down the Web site:
1. Locate an unprotected wireless network to use as the connection to do the hack.
2. Use an anonymizer service to cover his tracks.
3. Construct a DDoS (distributed denial of service) attack using the Freak88 DDoS tool.
4. Test the tool in his lab.
5. Infect many unprotected computers with the Freak88 Server.exe Trojan.
6. Take control of the infected machines and instruct them to continuously ping the target Web site.
Phoenix is now ready to begin creating his attack. As with every hack Phoenix does, he always begins by doing somewhat of a proof of concept before actually carrying out the attack. Phoenix, paranoid by nature, hates surprises and likes to lab things out before unleashing them to the wild. As Phoenix thinks of the tools he might use, he remembers a DDoS tool named Freak88. “It’s worth a shot,” Phoenix thinks. With that, he googles “Freak88.” He gets about 14,000 results and begins the process of going through them. After going through about four links, Phoenix finds what appears to be a real download of the tool. He clicks Download and waits for it to finish. “Let’s see what we got here,” Phoenix says out load. He unzips the file he just downloaded and views the contents, displayed in Figure 3.2.
According to data published by Microsoft on April 22, 2008, attackers have begun to drop e-mail-based phishing attacks in favor of Web-based attacks. As systems administrators have gotten a better handle on blocking malicious content that found its way in through e-mail and e-mail attachments, attackers are finding more success with Web-based attacks such as cross site scripting, SQL injection, and other forms of attack. One type of attack not covered broadly is the additional vulnerability introduced by mechanisms such as inline frames, CSS (Cascading Style Sheets), and other features allowed to be indiscriminately introduced into our environments. One big problem with Web security is the fact that we’re now allowing everything to be dumped into what I call “business rich” Web sites and still call it all HTML. In 2007 and so far in 2009, there have been several inline frame vulnerabilities discovered. Default inline frame behavior has several fundamental problems, but more important is the way the most popular Web browsers handle inline frame content by default. As more businesses advance to making their Web site their primary interface to the outside world, we can expect to see attacks on corporate, government, and private Web sites increase and become more complex.
Phoenix will attempt to use various DDoS tools that utilize mechanisms such as ICMP (Internet Control Message Protocol) to bring down a competitor’s Web site. The concept is simple: Ping a Web site with as many pings as possible from different sources or hosts, and bring down the site by overwhelming it with the ping echo requests (which, according to the protocol, the site must reply to with echo replies). Because a lot of network administrators and engineers have put a halt to many ICMP-based attacks by prohibiting the transport of that protocol, ICMP attacks are becoming less effective. Phoenix will undoubtedly face this problem, but utilize other built-in features of the HTML language to render the same net effect.
This section includes the details of each step in Phoenix’s chained exploit, including
• Attack #1: The Test
• Attack #2: The One That Worked
• Getting Access to the Pawn Web site
• Lab-Testing the Hack
• Other Possibilities
The section ends with a summary of this chained exploit.
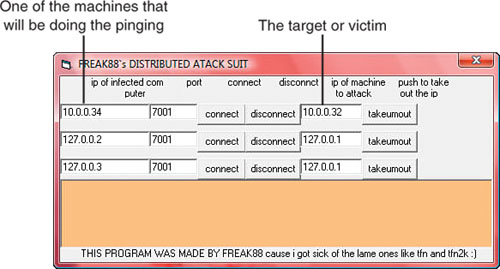
Phoenix wastes no time reading up on the Freak88 tool and learning how it’s used. “So, server.exe needs to be on the boxes I’ll control and use to actually do the pinging. No pings will actually come from my box. Sweet! I’ll use clienttrino.exe to actually control the boxes that I successfully put the server.exe Trojan on. Okay, that all makes sense.” Now that Phoenix understands how the tools are supposed to work. he immediately goes to work labbing it. First Phoenix creates a diagram showing how the setup and attack are supposed to work, as shown in Figure 3.3.
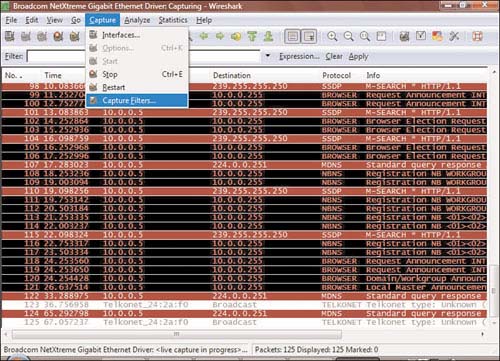
Phoenix fires up a few of his test computers and goes to work installing the pieces of the Trojan on his test machines. Phoenix copies the server.exe file to his test machine with the IP address of 10.0.0.34. This will be the zombie, or pawn, which will actually do the pinging. Phoenix then installs and starts Wireshark on the machine that will act as the victim. From the Wireshark menu items, Phoenix selects the Capture drop-down list and then chooses Capture Filters, as shown in Figure 3.4.
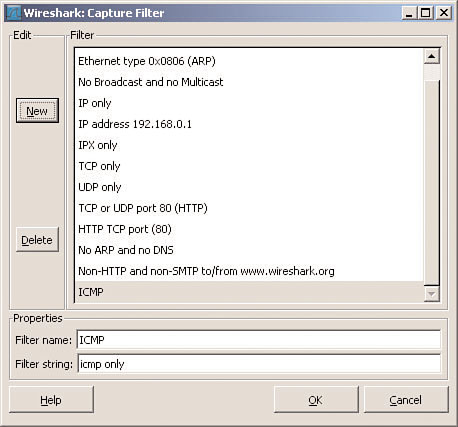
In the resulting dialog, Phoenix enters ICMP in the Filter name box. In the Filter string box, he enters icmp only. He then clicks the New button. The new ICMP filter now appears in the Filter selection list, as shown in Figure 3.5.
Next Phoenix goes to the computer that will act as the zombie. He finds the server.exe file he copied to the C: drive and double-clicks it. Phoenix then goes back to his attacker machine and double-clicks the clienttrino.exe file. He is immediately prompted with the dialog in Figure 3.6.
Phoenix now inputs the corresponding IP addresses where appropriate in the dialog, as shown in Figure 3.7. In the ip of infected computer box, he enters the address of 10.0.0.34. In the ip of machine to attack box, he enters the address of 10.0.0.32. After this small configuration task, Phoenix clicks the connect button. The message dialog lets him know he’s connected with the message of “Hello, who do you want to phuk today?”
Phoenix now goes to his victim machine and opens to the Wireshark dialog. He clicks the Capture drop-down list and selects Interfaces, as shown in Figure 3.8.
Phoenix then clicks the Start button immediately to the right of the correct interface, which has the IP address of 10.0.0.32. Quickly the capture window jumps to life and begins to display all traffic passing in and out of the network card, as shown in Figure 3.9. Phoenix then enters in the Filter box the letters icmp (which is the name of the filter he just created a few minutes ago).
Next Phoenix clicks the Apply button to the right of the Filter box area. Immediately all the capture traffic disappears, as shown in Figure 3.10.
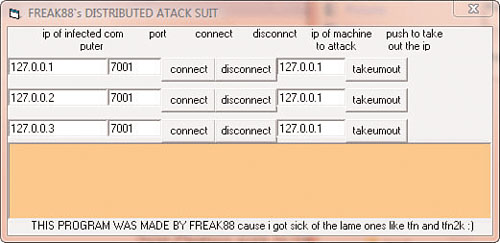
With all the filtering and packet capturing set up, Phoenix is ready to launch his mock attack. So, he goes back to his attacker machine. In the Freak88 dialog on the attacker machine, Phoenix clicks the takeumout button as shown in Figure 3.11.
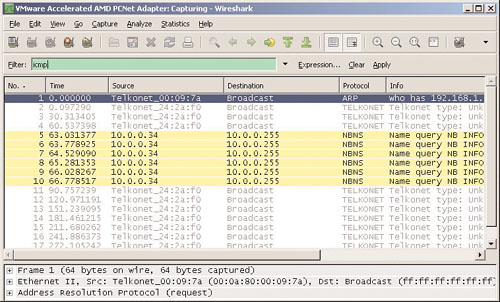
“This will be just what the doctor ordered,” Phoenix thinks as he heads across the room to his victim to see whether Wireshark is capturing any ICMP traffic now. Phoenix looks at the screen and snaps his fingers in approval. “It works,” he says. Just as expected, the traffic is indeed coming from the zombie at 10.0.0.34, and not his machine, as shown in Figure 3.12.
“Excellent,” Phoenix exclaims. “I’m attacking the machine with pings by instructing another machine to actually do the pinging.” On a hunch, Phoenix decides to see whether he can ping the Web site he’s planning to attack. He pops up a command line and types the following:
ping www.thetruthsa.org
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Phoenix is dumbfounded by the results of his ping. He then browses to the Web site in his Web browser and sees that it’s up and running. “What the hell?” he shouts. Phoenix’s good spirits start to sink. He never finished reading the article on the creation and setup of the Web site. He goes back and pulls up the article. Toward the end of the article, Phoenix is crushed when he reads that the kids put in a PIX (Private Internet Exchange) firewall and, on advice from Cisco, disabled ICMP to the Web server. “Dammit!” Phoenix yells. He now realizes that this attack will not work.
Phoenix sits down and thinks. “This is not the time to get upset. I need to come up with another way,” he thinks to himself. Just at that moment Phoenix remembers reading an article about hackers using inline frames to launch DDoS attacks by instructing the inline frames to perform normal HTTP (HyperText Transfer Protocol) GET requests to Web sites. The attackers get control of popular sites, and then put the inline frames in those sites. After doing this, every visitor to the site will be an unknowing and unwilling participant in the DDoS attack. The concept is simple. If a site gets 100 visitors per minute, and the site’s inline frames instruct visitors’ browsers to load a target site ten times, the net effect will be the target site getting ten visits per one visit to the hosting Web site. Multiply that by 100 visitors per minute and that’s 1,000 hits per minute. “That just might do it,” Phoenix says. “If there was a way I could instruct the inline frames to not only load the target Web site, but also constantly refresh it, I would increase the traffic to the target exponentially. It’s worth a shot,” says Phoenix.
Without wasting any more time, Phoenix writes out his revised plan in steps:
1. Pick a company with a Web site that has lots of traffic and lots of bandwidth.
2. Socially engineer the Web design company that has write access to the company’s home page.
3. After gaining access to this high traffic site, modify the home page by inserting into the HTML code inline frames that will call multiple instances of the target Web site (www.thetruthsa.org).
4. Sit back and watch thetruthsa.org get slammed by a huge amount of traffic from users all over the world.
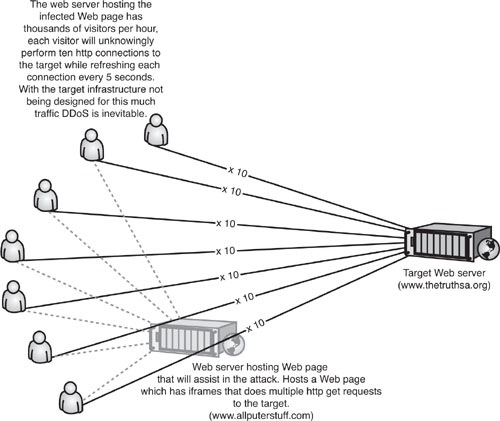
Phoenix decides to make himself a graphic illustration to get the concepts clear in his head. After 10 minutes in Visio, Phoenix produces the graphic in Figure 3.13.
Basically, every time a visitor visits the pawn Web site (www.allputerstuff.com), the inline frames embedded in that Web site’s home page will instruct that visitor to load ten instances of the target Web site, then refresh it every 5 seconds. With thousands of visitors visiting this Web page, it will no doubt bring down the cheaply developed www.thetruthsa.org Web site.
Phoenix chose allputerstuff.com because it boasts huge amounts of traffic for advertisers and does many millions per year in sales from its Web site. Also its Web site has a logo at the bottom that says it is designed and maintained by bebop web. Phoenix knows that this Web design company is actually small although it has some high profile clients. He also knows that it is local. Phoenix decides his best first approach is to somehow social engineer someone at Bebop Web Design into giving him login information to modify the Web site of allputerstuff.com. Phoenix starts research on Bebop Web Design and very soon finds its office location. Phoenix prints the MapQuest directions Bebop has on its Web site and heads out the door to give the company a visit.
Arriving at the address of Bebop, Phoenix is amazed at the glamour of the building and how big it is. “A small Web design firm can afford this?” he thinks to himself. Phoenix enters the building and looks for the building directory. He finds it in the middle of the lobby. “Bebop Web Design suite 208,” Phoenix says out loud. Phoenix jumps on the first available elevator. Inside the elevator, an older gentleman with a name badge and a blue and brown uniform greets him. “Hi,” the man says.
“Hello,” shoots back Phoenix.
The gentleman starts a conversation. “I’m Greg, I’m a janitor here. Let me give you one of my cards because I also do landscape work, wash cars, and other things.” The man hands Phoenix a cheap-looking homemade business card. Phoenix puts the card in his pocket.
“You’re a man of many trades,” Phoenix jokes.
With a slight grin, the man replies, “Well, with the economy being the way it is, we can’t get no overtime any more and a man has to eat.”
“I understand that,” says Phoenix. With that comment, the elevator dings and stops on the second floor. Phoenix gets off and tells the janitor to have a good day. As the doors are closing, the janitor calls to Phoenix, “Don’t forget to call me if you need any landscape or handyman work done.” Phoenix nods in agreement and heads left to suite 208.
As Phoenix enters the suite, an attractive 20-something-year-old woman greets him and asks if she can help. “Yes,” says Phoenix. “I own a multimillion dollar company and we’re in the process of looking for a new Web design firm to spearhead our e-commerce rollout from a design perspective.” With Phoenix having a fresh new haircut and wearing a new suit, he certainly looks the part of a young professional tech dude who started a company and is very successful.
“Sure, we can help you with that. If you’ll just have a seat, I’ll let you talk to our head designer,” says the receptionist, now with a bigger grin and a seemingly elevated urge to help. “Amazing how money makes people act,” Phoenix says under his breath. Within a few minutes an overweight, underdressed 35ish-looking man comes out and asks Phoenix to step into his office. After offering Phoenix coffee or soda and then sitting down, the man speaks. “Melinda told me what you were looking for, but we don’t actually do the e-commerce part. We just create a nice front end, and we partner with another company for the e-commerce function.”
“I see,” says Phoenix as he pretends to write in a notepad. In a professional tone, Phoenix says, “Tell me about your process.”
The man smiles and starts talking. “Well, as I said, we do only the front end part. And we’re one of the best at it. If you’d like, I can show you some of our work,” the man offers.
“Sure,” said Phoenix, “but what I’m most concerned about is response time. In other words, if we call and need a change, what is your process?” Phoenix asks.
“Okay,” replies the man who has now identified himself as Bret. “Fortunately, I just got a request for a change right before you came in. So, I’ll let you see the process firsthand.”
With a thoughtful smile, Phoenix replies, “That would be great.”
With that the man pulls out a three-ring binder and starts flipping through pages. Bret glances up at Phoenix and tells him that he keeps all the login information to his clients’ Web sites in this book. He doesn’t store anything digitally, so hackers can never get to it.
“Right,” Phoenix agrees. After Bret reaches a page that obviously has the credentials for the client Web site he’s about to modify, he stops and pulls up an FTP client. Within minutes he’s logged in, grabbed the home page HTML file, made the changes requested, and saved the file.
He looks at Phoenix and comments, “There you go, that’s all there is to it. A total of what, maybe 2 minutes?”
Phoenix nods and artificially exclaims, “That’s pretty impressive.” Bret puts the folder back inside the open door on the cabinet behind his desk and closes it.
“Well, I think I’m pretty much sold,” says Phoenix. “I’ll be in contact with you or one of your other designers within the next couple of days so that we can get started.”
As Phoenix gets up, Bret tells him that he’s the only designer there. “Okay, that’s fine,” says Phoenix. “I’ll contact you directly then. Do you have a card?” Bret hands Phoenix a couple of business cards and walks with him to the front door.
“Thanks again,” says Phoenix as he steps into the elevator. Before Phoenix even reached the elevator his brain was already in hyper drive trying to come up with ways to get the folder Bret has in the cabinet behind his desk. That folder has all of Bebop’s clients’ Web site FTP login credentials. When he reaches the lobby, he sees Greg the janitor again. Without even giving it a second thought, Phoenix gets Greg’s attention and asks him to walk with him outside. When they reach the street Phoenix gets right to business. “Greg, how would you like to make $3,000 in 10 minutes?”
Greg smiles and says, “Aw, how in the world can somebody make that much money in 10 minutes?”
Phoenix smiles back and asks, “Do you work the second floor?” Greg nods and replies, “Yeah, I work the entire building.”
Phoenix thinks for a second. “Okay, good. Do you know the company Bebop Web Design on the second floor?”
Greg smiles and replies, “Sure do, this smug guy named Bret runs that place.”
Phoenix pauses and then fires another question at Greg: “Do you ever clean at night or after everyone is gone?”
Greg wastes no time responding: “I do once a week. Like tonight, for example, I have to clean the carpet on all the floors that have it, so I have to do that at night.”
Phoenix looks Greg in the eyes and gives him the task. “Tonight when you’re cleaning, all you have to do is go inside the cabinet behind Bret’s desk, get the red three-ring binder from it, and make a copy of all the pages—there shouldn’t be more than 20 pages in there. Simply put it back, and call me when you leave the building. Meet me with those copies, and I’ll put $3,000 cash in your hand.”
Greg immediately agrees. They exchange cell phone numbers and part ways. With Greg being as hard up as he is for cash, and the economy being a little shaky, he didn’t hesitate to take on this small task. Six hours later, at around 9:30 p.m., Phoenix’s cell phone rings. When he answers, Phoenix is pumped to hear Greg on the other end. “I got your package,” Greg says.
“Cool,” shouts Phoenix, “Meet me at Jack’s Ribs at Adams and State in 20 minutes.” Greg agrees and ends the phone call. Phoenix jumps up, heads out the door, and goes to the restaurant. There he and Greg exchange the package for money. Phoenix decides to head straight home, but Greg has decided to stay and enjoy a rack of BBQ ribs. Phoenix thanks Greg once more, and heads out the door.
As most successful hackers and penetration testers will attest, it’s important to lab out any hack or attack that you’ve never carried out before. It’s downright foolish to be learning the hack after you’re inside your target. Usually if a hacker finds himself doing that, he probably didn’t do enough recon.
After Phoenix makes it home, he heads right to his desk and starts working on the technical aspects of actually making his attack work. “First thing I’ll need to do is lab the hack out.” With that thought Phoenix goes to one of his test boxes running Windows 2003 Server. He opens Notepad and constructs a simple HTML page that displays the message “hacked.” Phoenix then saves the page to C:inetpubwwwroot. Next he begins the configuration of IIS (Microsoft’s Internet Information Services) to host this page. Then he goes to Start, Administrative Tools, Internet Information Services (IIS) Manager, as shown in Figure 3.14.
Next, Phoenix clicks the + symbol to the left of his server name. He then does the same to the Default Web Site icon below it, as shown in Figure 3.15.
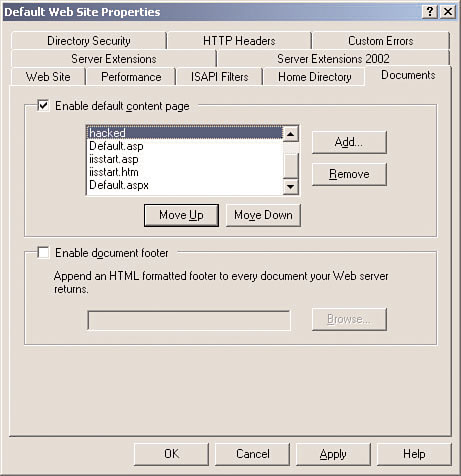
Phoenix then right-clicks the default Web site icon and then selects Properties. In the resulting dialog box, Phoenix selects the Documents tab. He then clicks the Add button and types the name of the HTML file he saved earlier. Next he repeatedly clicks the Move Up button until his file is at the top of the list, as illustrated in Figure 3.16.
Phoenix then clicks the Directory Security tab and clicks Edit. In the resulting dialog, Phoenix clicks the Enable anonymous access check box and leaves all other settings set to their default value, as shown in Figure 3.17.
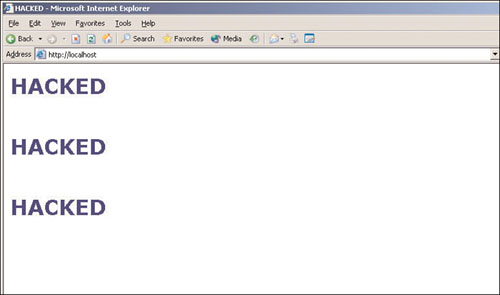
Phoenix then makes sure the default Web site is running, and turns to another computer to see whether he can successfully browse to the Web site by entering the 2003 server’s IP address. On being greeted by his “hacked”-themed Web page as shown in Figure 3.18, Phoenix is satisfied.
“Now for the fun part,” Phoenix says to himself. “I need to know a little bit more about inline frames if this is going to work.” He opens up Firefox and goes to www.google.com. He starts searching for information pertaining to how inline frames work. After several hours of reading tutorials, forums, and message boards, Phoenix is comfortable that he has a firm enough understanding of inline frames. So, he goes to work on his test page. Phoenix opens his hacked.html page in Notepad and starts to construct his first inline frame. He starts by injecting the following code into the HTML document:
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
Phoenix studies the code he just entered. He thinks, “Based on this code, when I view my hacked.html Web page, it should open inline frames, which are mini Web pages inside the hacked.html file. Each mini Web page will be a unique instance of www.google.com. By opening hacked.html, I’m also opening ten instances of Google, each with a height and width of 200.” He then browses to his test hacked.html Web site at http://10.10.10.32 (his test server’s IP address), as shown in Figure 3.19.
Phoenix examines the code after he’s pasted the inline frame code into the document nine more times:
<html>
<head>
<meta http-equiv="Content-Language" content="en-us">
<meta http-equiv="Content-Type" content="text/html; charset=windows-1252">
<title>HACKED</title>
<!—mstheme—><link rel="stylesheet" href="jour1000.css">
<meta name="Microsoft Theme" content="journal 1000, default">
<meta name="Microsoft Border" content="tlb, default">
</head>
<body>
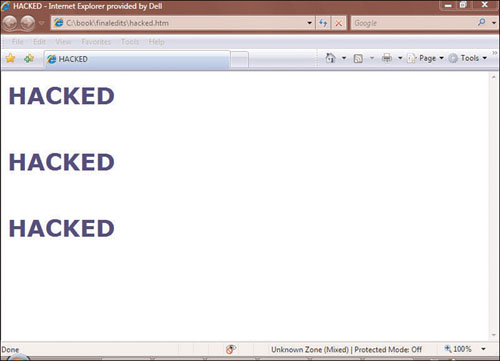
<p><b><font size="6" color="#000080">HACKED</font></b></p>
<p> </p>
<p><b><font size="6" color="#000080">HACKED</font></b></p>
<p> </p>
<p><b><font size="6" color="#000080">HACKED</font></b></p>
<p> </p>
<html>
<head>
<meta http-equiv="refresh" content="20">
</head>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
<iframe
src=http://www.google.com
width=200 height=200>
</iframe>
</html>
</body></html>
“Alrighty, let’s see if it opens ten instances now.” Phoenix selects the File drop-down list and clicks Save on the HTML document hacked.html. He then goes back to his Web browser and clicks the Refresh button. He is delighted to see the results shown in Figure 3.20.
“This is cool!” Phoenix yells. “Now let’s start fine-tuning it a bit. I need to figure out how to make the inline frames reload the pages every 5 seconds.” At this point, Phoenix realizes he hasn’t read enough. So, he goes back to Google and launches a few searches for inline frame refreshes. It’s not long before he finds exactly what he’s looking for. Based on an article he found in an online Web developer publication, he modifies his inline frames accordingly by going back to Notepad and opening his hacked.html document. Phoenix then adds the following meta tags to refresh the inline frames every 5 seconds:
<html>
<head>
<meta http-equiv="refresh" content="5">
</head>
Phoenix saves his HTML document, goes back to his Web browser, and refreshes the still loaded hacked.html. At first nothing happens except all the inline frames refresh. But just like clockwork, in exactly 5 seconds, they all reload. And 5 seconds later, they all reload again. “This should work nicely!” Phoenix blurts as he gives himself a thumbs up of approval. Then it hits him: Even the most nontechnical end user will know something is up if a Web page that’s supposed to show computers and computer parts has a massive number of instances of Google loading in the middle of the page. “I need to find a way to hide these,” thinks Phoenix, and he tries the obvious first. He again opens hacked.html in Notepad and modifies the width and height settings of each inline frame. He changes the settings to a height of 0 and a width of 0 and leaves everything else unchanged:
<iframe
src=http://www.google.com
width=0 height=0>
</iframe>
After saving these changes, Phoenix goes to his browser and refreshes the Web page. After the refresh he smells success as the page loads without any visible signs of the inline frames, as shown in Figure 3.21.
Now Phoenix can’t tell whether the inline frames are even loading because they’re hidden. “Let me take a look at traffic in Wireshark.” Phoenix opens Wireshark, starts a capture on his NIC (network interface card), and immediately sees the HTTP GET requests to Google’s IP address, as displayed in Figure 3.22.
Now Phoenix stops and thinks for a while. “How’s this gonna play out in the real world?” he asks himself. “Five instances might not do the job...hmm. Heck, I could make it 100 instances of the inline frame if I wanted! But that might actually DoS the end user, though. Actually, I think ten instances should do it. Besides, 100 instances will certainly set off an alarm or something either on the Web server side, or something inside a potential random person’s network when they pull 100 simultaneous connections to www.google.com. Now that I think about it more, ten might actually be flirting with that same outcome. But I’ve had nearly ten instances of Google open searching for different things, so I should be okay using ten.” Phoenix goes through this process of conversing with himself for another 10 minutes before deciding to leave the inline frame instance number at ten.
At this point, Phoenix has done all the testing he can probably do. Now it’s time to connect to the Web server that hosts www.allputerstuff.com and actually modify the home page. Let’s look at the steps Phoenix will go through to perform this:
• Connect to www.allputerstuff.com and copy down the home page.
• Using only Notepad, insert inline frames into the HTML of the downloaded allputerstuff home page. These inline frames will call www.thetruthsa.org as the page to load instead of www.google.com that Phoenix used in his test lab.
• Replace the original home page on the Web server with the modified version, which includes the inline frames.
• Sit back and watch as www.thetruthsa.org is rendered unable to serve any more HTTP requests.
Phoenix is now ready to begin pulling down a copy of the pawn Web site. He opens Internet Explorer, connects to the array of anonymizer services he uses, and then browses to www.allputerstuff.com. As soon as the page loads, Phoenix simply clicks on View in Internet Explorer, and then selects Source. Windows opens a Notepad window and shows the source code of the Web site. Phoenix begins to make adjustments.
Next Phoenix opens the hacked.html file he created for testing earlier. He modifies the source pointers from www.google.com to www.thetruthsa.org and then copies the inline frame text. He pastes it into the local version of the www.allputerstuff.com HTML that he has open in Notepad as well. Phoenix wants to test the modified page locally first to see what the display will look like and to be reassured that the inline frames won’t show up. He saves his version of www.allputerstuff.com to his desktop. After it saves, he double-clicks the file. Internet Explorer opens a new window and shows him the page, as shown in Figure 3.23.
For a moment, Phoenix freaks out at all the red Xs on the screen where graphics should be. Then he slaps himself in the head and reminds himself in his own cheerful way, “Relax, Phoenix. You don’t have those images stored locally.” He sees the inline frames are not showing up anywhere. He fires off another capture session in Wireshark, and sure enough, there are HTTP requests going out to www.thetruthsa.org.
“Okay, this looks good,” Phoenix says as he tries to calm himself. By now the adrenaline is starting to kick in, and his palms and forehead are already starting to get moist with sweat. Now to log in to allputerstuff.com’s Web server and replace the default home page with his modified version. Phoenix glances over at the clock on his desk. It’s 5:45 a.m. “This is a good a time as any,” Phoenix says to himself. It’ll be only a couple of hours before traffic starts to ramp up on the site, and he needs thetruthsa.org to be inaccessible by 8:00 a.m.
Phoenix then fires up his FTP client. He flips through the documents he had the janitor copy for him. On the third page he sees the name allputerstuff.com. Right beside the Web site name is a username of bbking and password of ngbTyz45opw$. “Well, at least he used a relatively strong password,” Phoenix thinks to himself. He then turns his attention back to his FTP client. He enters the hostname of ftp.allputerstuff.com and fills in the username with bbking and carefully enters the password ngbTyz45opw$ in the password field. Phoenix takes a deep breath and clicks the Connect button on his FTP client. The FTP client software quickly scrolls a few messages about binary data and other typical messages, and with a quick ding, Phoenix is connected and looking at the contents of the Web server.
“Not much here at all,” Phoenix says. “I guess all the good stuff is actually stored somewhere on a more secure server. I guess that’s what all those weird .NET and C# LIKE calls I saw inside the HTML are pointing to: a more secure place.” Those thoughts interrupt Phoenix’s thought process for only a few seconds. He immediately grabs his modified index.html file from his desktop, and drags and drops it onto the window in his FTP client showing the contents of the Web server. He gets the typical “this file already exists, do you want to replace” message. Phoenix answers yes and just like that the home page at www.allputerstuff.com is replaced by Phoenix’s version of it.
“Now it’s just a waiting game.” Phoenix drops back in his chair, lets out a deep yawn, and stretches. He browses to www.thetruthsa.org to see whether anything has happened yet. The page loaded normally. Phoenix looks at the clock again and it’s now 6:19 a.m. “Still probably not many people browsing www.allputerstuff.com yet.” Phoenix decides to grab breakfast and come back and see what’s happening in an hour or so.
After eating a healthy McDonald’s breakfast and reading the newspaper, Phoenix comes back into his apartment, and a quick glance at the clock tells him it’s 7:45 AM. “Okay, something should be going on now.” Phoenix clears the cache from his Web browser and browses to the www.thetruthsa.org Web site again. The page loads, but much slower than before. It almost takes it a full 30 seconds to display anything. Phoenix tries to think of reasons the site isn’t down yet. “There probably just isn’t enough traffic to allputerstuff.com yet,” he tells himself. Phoenix, realizing it’s been more than 24 hours since he showered, heads to the bathroom and takes a long hot shower. After some time he comes out, dries himself off, and heads to his computers once more. Again, he opens his Web browser and types in www.thetruthsa.org. And he sees the results in Figure 3.24, indicating his success.
“Game over!” Phoenix says. Just to make sure, he clicks the Refresh button a few times, then goes to another computer and browses to the Web site. He’s greeted with the same results. Reflecting, Phoenix now goes into another one of his conversation-with-self trances. “I wonder how long it’ll take before they figure out what’s going on and how to fix it. They certainly won’t have the skills internally to diagnose what’s going on or how to stop it. Now that I think about it, it could be weeks before they even have a clue what to do. Even switching to another server and changing DNS records with their registrar won’t help because my inline frames call by URL, not IP address, so the inline frames will continue to pull from wherever the URL resolves to. There will hardly be a way for them to trace where the attacks are coming from because the HTTP requests will be coming from random people who browse to allputerstuff.com. Most likely it’ll be someone who connects to allputerstuff.com from behind a secure network with a sharp security team who actually figures it out. And that they’ll actually report it to the guys at www.thetruthsa.org is highly unlikely. They’ll probably just block the site from inside, or if they actually do a little bit of forensics on their internal boxes, they might even block allputerstuff.com and call it a day. If somebody contacts allputerstuff.com and informs it that its Web site is being used to launch DDoS attacks against a nonprofit, then the problem could very well be solved. But even then it’ll take someone actually looking at the HTML code to figure out what’s actually going on. The guys at allputerstuff.com might also simply replace my file with the original, but there’s still the issue of my version being cached all over the Web and inside browsers. At the very least, I think it’ll easily meet my client’s demand of www.thetruthsa.org being down for 48 hours. I guess I can make the call and collect the rest of my money now.”
Even though Phoenix’s main goal was to simply bring down www.thetruthsa.org, he could have done many more things to wreak havoc, not on the target only, but also on the Web site he compromised and loaded with the inline frames. Imagine if instead of simply putting in inline frames that called multiple instances of a Web site, Phoenix instead inserted a source pointer in the inline frame that pointed to a customized Trojan. What if the inline frame source is a keylogger engine that Phoenix stores on an FTP server on the Web? Wouldn’t it appear that the innocent company, allputerstuff.com, runs a Web site that attempts to infect all visitors with Trojans? In actuality, it would be the truth. Because regardless of whether the owners knew about the changes Phoenix made, they’d still be held partly responsible. Some people would say you can disable this in Internet Explorer and other Web browsers. However, the truth of the matter is that many (if not most) users and even system administrators enable the loading of ActiveX and Java applets without prompting just because users see it as an annoyance. From an identity theft and credit card fraud perspective, the possibilities are truly limitless.
The following are the steps Phoenix has taken for this chained exploit:
1. He was able to find information through passive recon, which ended up being just simple Google searching in this case. This included high school kids doing the Web site and some technical details about the implementation.
2. He constructed a solid DDoS attack plan using the Freak88 DDoS tool.
3. He discovered through more recon that ICMP is blocked on the target Web server.
4. He adjusted his attack plan to bring down the site using legitimate HTTP traffic.
5. He found a company that boasts huge bandwidth and lots of traffic to act as the pawn.
6. He easily determined which Web design firm updates the Web site chosen to be the pawn by the “designed by” advertisement on the page.
7. He visited the Web design firm looking for a social engineering angle to obtain the credentials to the pawn Web site.
8. He took advantage of a poorly paid custodian to get access to privileged documents inside the Web design firm.
9. He constructed a lab to practice the attack. Phoenix then built inline frames inside HTML code to call multiple instances of a target Web site and refreshes them every 5 seconds, invisibly.
10. He gained access to the pawn Web site by using credentials stolen by the poorly paid custodian.
11. He replaced the original version of the pawn Web site’s home page with his inline frame–embedded version.
12. He browsed to the target page until he validated that the site is actually inaccessible because of excessive traffic from the pawn Web site’s visitors.
This section discusses the various countermeasures you can deploy to protect against these chained exploits.
The one simple countermeasure here is to be careful what you post or advertise about your company on the Web. After something is on the Internet, it will probably never be taken off completely. These are just the nature and mechanics of the Internet. There are other ways to passively gain information about a company’s Web presence. Netcraft, for example, enables you to find information such as Web server IP addresses, what operating system the Web server is running, and what version of that OS, all the way down to the last time the server was rebooted! Fortunately you can opt to have this information suppressed by doing a couple of things. Make sure you configure all your DNS (domain name system) and contact information to be private and not public with whichever domain registrar service you’re using. Most Web server platforms allow you to suppress or, better yet, customize this information to broadcast to the world whatever you tell it to broadcast. The number one question any company or employee should ask before making any information publicly available is simply, “Why does this information need to be made publicly available?”
The target company, at the urging of the firewall hardware vendor, exercised the best countermeasure for DDoS attacks via ICMP. Disabling ICMP on all Web or outside-facing interfaces on all devices has been a standard Security 101 practice for a while now, but it’s quite startling how many companies do not follow this practice. In recent years ISPs have started to develop ways to minimize the impact of DDoS attacks, but still have not managed to prevent them. If your Web site has to allow pings from the outside for one reason or another, script solutions and firewall solutions can cause IP addresses to be blocked instantly if they exceed a certain number of pings in a given time frame. However, if the attacker is truly performing a DDoS attack, this countermeasure loses a considerable amount of its effectiveness.
This is a much harder task, mainly because you can’t just deny or block some protocols entirely. How can a Web server function as a Web server if it’s not allowing any HTTP requests? How can a device designed to communicate across the Internet or a network build up communications channels if TCP (Transmission Control Protocol) is not allowed?
Well, there are several answers to those questions. One answer is by using/creating highly modified and customized stacks. This is extremely expensive from a development and maintenance standpoint and is usually reserved for the most highly secure environments. For most others, there are technologies such as rate limiting, which allows only a certain amount of bandwidth or a certain number of connections to be served to any one host in a given time frame. There are also rate limit options on most modern network equipment that allow for the limiting of certain kinds of traffic.
Black hole filtering is a solution that sends all suspicious or malicious traffic to a null or nonexistent interface. Although this won’t stop a DDoS attack, it can provide significant relief from a massive flood of any one kind of traffic.
You should implement ingress and egress filtering at all entry points to your corporate network. This type of filtering minimizes the chances of spoofed packets entering your network.
There is one problem with all these solutions: They all go against the reason companies put Web sites up in the first place. The original vision for the Web was for it to be open, free, and easily accessible. We’ve accomplished that, and now those in the security world are being asked to secure it. It’s the same as building a mansion with 700 wide open doors, and then telling two security guards to secure them all. Phoenix had to do some guessing as to the limitations or allowances of his target Web site, but he just assumed there really weren’t any other than default connection limits in various border hardware and server side software. Again, ISPs are making decent strides in the area of DDoS mitigation and impact minimization. If your company is serious about preventing these kinds of attacks, the authors suggest conversing with your ISP or carrier about such concerns.
In the scenario in this chapter, a lot of responsibility falls on the pawn company (allputerstuff.com) because that company’s site hosted the malicious inline frames. For corporations that use third parties to modify, create, and update content on their Web sites, it should be policy to ask for information security statements and explanations as to how access to your Web sites will be protected. It is a common misconception that not putting information in any digital format protects that information from hackers and malicious parties.
Additionally, there should be other methods of checking in place for Web site modifications. A generally accepted practice is that if you’re using a third party for Web site maintenance or design, your organization should authorize all modifications. This is usually stipulated in contractual agreements. The problem is in actually enforcing this practice. One solution would be to use one-time passwords—in other words, a pregenerated list of passwords that can only be used once. This list stays with the Web site owner (your company). To make modifications, the third party would have to contact the owner of the Web site to obtain the next password in the list. This forces the third party to communicate with the Web site owner before any modifications are possible. This would have made Phoenix’s compromise of the janitor at the Web site design firm fruitless.
We often forget there were criminals, thieves, and hackers well before there were computers as we know them today. And as demonstrated in this chapter, the compromise of the allputerstuff.com Web site was carried out without many technical tools or techniques whatsoever. To make the site even more secure, there could be mandatory two-factor authentication required to modify any portion of a corporate Web site. If your site is hosted by a third party that can’t provide this, it might be advisable to look for a new host. If PayPal can offer millions of customers the ability to use two-factor authentication to make purchases via PayPal, any hosting provider should be able to offer this to clients that have chosen to use them as their hosting entity.
When Phoenix approached Greg about stealing copies of Bret’s login information, he’d already scoped the office out, knew there were no security cameras around, and knew that the cabinet Bret stored the documents in did not have a lock. It’s generally a bad idea to store passwords in paper form anyway. These passwords should be stored electronically and well protected via encryption and strong access control. This would mean Bret should have those passwords only on his workstation, and have it locked down. Moreover, his company should probably implement a mandatory encrypted hard drive policy.
A janitor usually has unlimited access to everything at all times, so there are steps you should take on that front, too. The janitor would have been a lot less useful if he’d been required to use a swipe card to enter Bret’s office. It would be a good deterrent if the janitor has to use a swipe card and has been told that all access is being logged. This is mainly because the janitor would know that if the stuff ever hit the fan, access to the office at a particular time on a particular day could be easily traced back to him. Separation of duty and the principle of least privilege are critical to internal security. For example, the janitorial staff that works the building during the day could be relieved at close of business and replaced by someone paid just to do night jobs; that way the people working at night have no knowledge of what goes on during the work day.
The author intentionally did not include any fancy tools to pull off the successful DDoS against the target company. You should understand that some of the most successful hacks of all time involved nothing but a thorough understanding of the protocols and technologies used in predictable ways on a day-to-day basis. Essentially, Phoenix found success by forcing thousands of people to do HTTP GET requests to his target Web server. In other words, he just forced a bunch of people to repeatedly browse to the target Web site. Distinguishing this from just a huge influx of traffic would be difficult for most to decipher and, more importantly, even more difficult to stop once the attack is underway.
DoS and DDoS attacks are old news, but most Web sites are still vulnerable to them. In speaking with clients over the last few years about this, most just have never done anything about it because they feel it won’t happen to them. A classic kind of DDoS attack involves making thousands of computers on the Internet zombies by infecting them with a Trojan that makes a call to either a Web server controlled by the attacker or the attacker’s computer itself, or makes connections to IRC channels and inevitably becomes part of an IRC botnet. Today you can visit literally hundreds of channels and sites that will lease a few thousand or a couple hundred thousand of these bots to you for you to do your dirty deeds. They’re already infected, already under control of the bot master, and waiting for command to launch an attack. All the hard work has been done; all an attacker has to do is connect to specific IRC channels and begin his attack.
This problem certainly will not go away because just as with most of our defenses in cyber warfare, defenses against DDoS attacks act in predictable ways and are easily fooled. The best defenses against DDoS attacks are staying up-to-date with current trends and methods, and making strong efforts at the border or ISP level of your infrastructure to throttle bandwidth and connections. Also it’s a good idea to have alternative domains in place and be ready to move your site to one of them at a moment’s notice. There are several coordinated joint efforts currently in operation to try and develop defenses against these kinds of attacks. Some of them are Prolexic at www.prolexic.com, Radware at www.radware.com, and Top Layer at www.toplayer.com. Although this certainly isn’t an exhaustive list, the author of this chapter has worked directly with these three companies.