Introducing Business Continuity and Disaster Recovery
Chapter 10, “Disaster Recovery and Business Continuity and the Cloud,” examines business continuity and disaster recovery in detail. Within Chapter 10, you will learn that companies will always face a variety of risks. Every company’s goal is to evaluate its risks and to determine ways to mitigate (reduce) them. When you work with security issues, the same technique applies. To start, you must determine where your system is vulnerable and then you must take steps to reduce the vulnerability. The following sections examine common security threats.
Understanding Data-Storage Wiping
In Chapter 6, “Data Storage in the Cloud,” you learned that many facilities offer cloud-based storage. Often, a cloud-based data-storage provider may share a storage device across multiple customers. Assume, for example, that you store a confidential company document within the cloud. Later, you delete that document. Normally, when the file system deletes a file on disk, the file system simply marks the locations within which the file resided as available for use to store other files. Assume that another customer comes along and allocates space on the disk for storage but does not write any information to the space. Should the customer examine the allocated space, the customer may have access to your previously deleted confidential document!
To prevent such inadvertent data access, many cloud-based data-storage facilities will “wipe” a file’s contents upon deletion (overwriting the previous file space with a series of values). In this way, as shown in FIGURE 9-2, should a customer allocate space within a cloud-based disk, that customer cannot read the disk’s previous content.

FIGURE 9-2 Within a cloud-based disk-storage facility, file wiping overwrites a file’s previous contents when the file is deleted.
Understanding Distributed Denial of Service (DDoS) Attacks
A denial-of-service attack is a hacker attack on a site, the goal of which is to consume system resources so that the resources cannot be used by the site’s users. The motivation for and the implementation of denial-of-service attacks differ. The following batch file, for example, repeatedly sends ping requests to a specified website. Because the site must respond to the requests, it may need to deny or delay service to other users:

A distributed-denial-of-service (DDoS) attack uses multiple computers, distributed across the Internet to attack as target site, as shown in FIGURE 9-3.
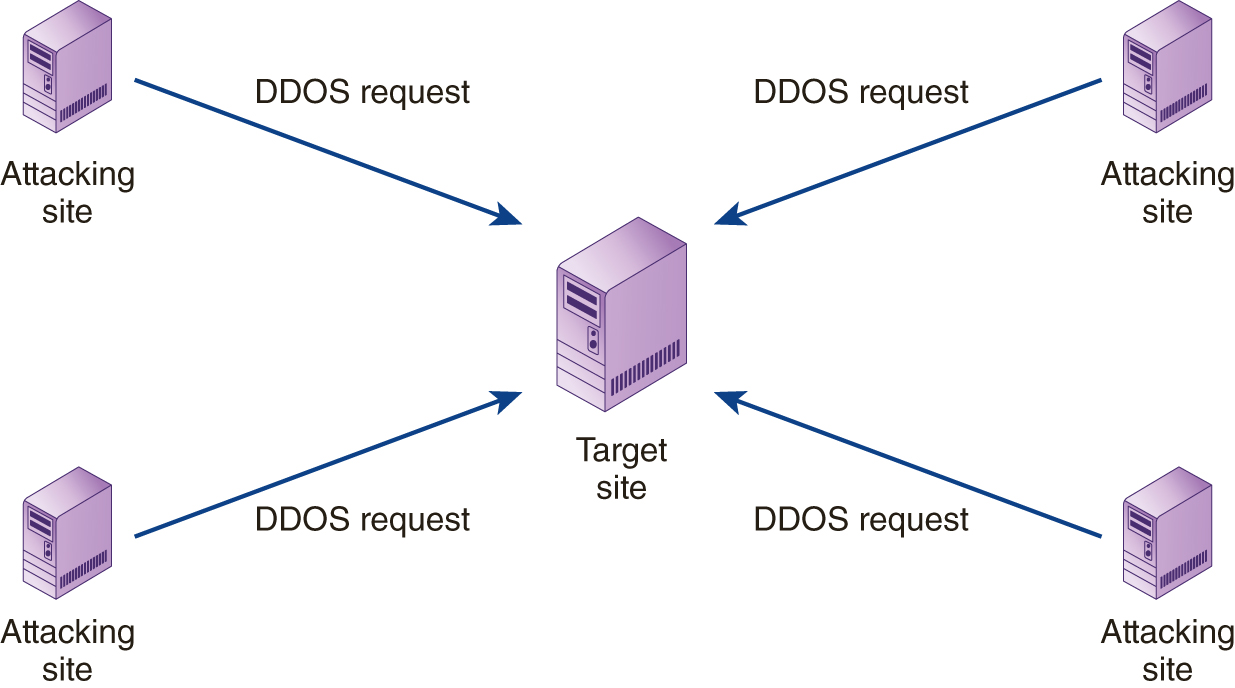
FIGURE 9-3 A DDoS attack employs multiple computers to attack a target site.
It can be challenging for a server to defend itself against denial-of-service attack. Often, a server slows down considerably before the attack can be detected and defended. The advantage of a cloud-based host with respect to a denial-of-service attack is that the cloud server may scale its resources quickly to respond to the attack messages in such a way that the site’s users are not impacted. The increased scaling will notify the administrators that the site is under attack so they can initiate defensive actions.
Packet Sniffing
Across the Internet and cloud, applications communicate by exchanging packets of data. As shown in FIGURE 9-4, within a wired network, each computer examines packages to determine which ones are addressed to it.
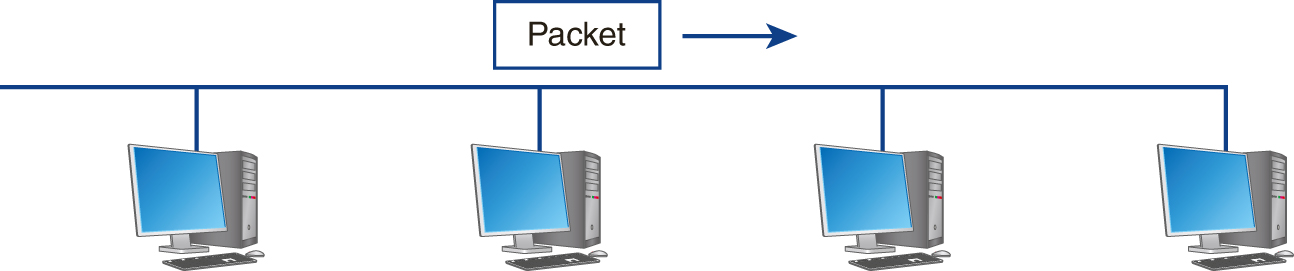
FIGURE 9-4 Network applications communicate by exchanging network packets. Each computer within a wired network examines the message address to determine if the message is for an application it is running.
A hacker can write code which lets his or her system examine the content of each packet that travels past it. Such programs, called packet sniffers, allow the hacker to view, and in some cases, change, a packet’s contents. Within a wireless network, hackers can simply monitor the air ways to intercept packets.
The best defense against a packet sniffing attack is to use secure (encrypted) connections. The cloud, because it allows users to connect to applications from anywhere, increase potential risks, because users may connect from an insecure network or one from within which the wireless traffic is being monitored. To reduce the threat of such attacks, you will see more cloud-based applications requiring secure connections in the future.
Man-in-the-Middle Attack
A man-in-the-middle attack is much as it sounds. In general, the attack occurs when a hacker, as shown in FIGURE 9-5, is able to interrupt network messages and essentially place him or herself between the user and remote system. Once the hacker is positioned this way, messages can be sent that appear to come from either the user or system, as needed.
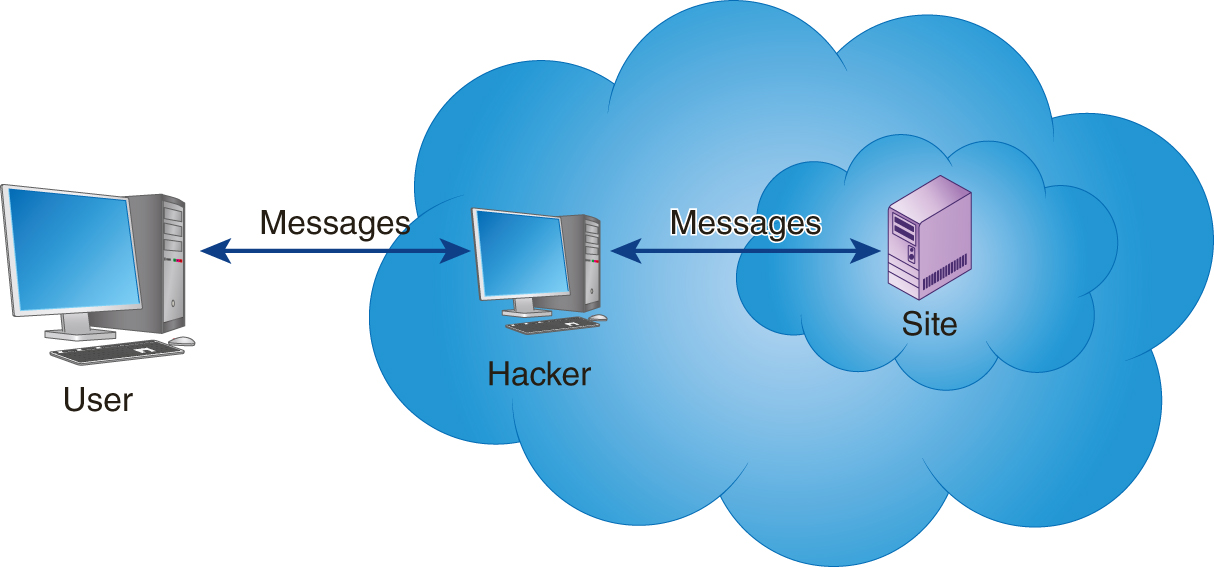
FIGURE 9-5 Within a man-in-the-middle attack, a hacker intercepts messages a user and system are exchanging. The hacker can view and/or change the message contents.
Because cloud-based solutions rely on user communications across the Internet, the solutions are at risk for man-in-the-middle attacks. A good defense against such attacks is to establish a secure (encrypted) connection with the remote server.
Monitoring Device Screens
Years ago, when employees accessed sensitive or confidential data from within their office only, the data was better physically protected from prying eyes. The cloud, however, extends the delivery of such data to users, any place, at any time, and often, from any device. The net result is that within a busy Starbucks or an airport, strangers can see data ranging from human-relations information, customer-sales data, student grades, and more.
Unfortunately, the problems caused by remote data access will only get worse. The best defense against screen monitoring is user training. Users who access sensitive data must be aware of their surroundings.
Malicious Employees
Companies spend considerable amounts of money trying to protect their data and communications from hackers. IT staffs deploy firewalls, use encryption, monitor network traffic for intrusion, and much more. With all of these security features in place, the most difficult challenge for a company to defend itself against is the malicious employee. Developers, for example, have access to databases and IT staff members have access to various system passwords, which means, each may have access to human-relations data, payroll data, email content, and more.
By shifting data to the cloud, you move sensitive data away from your own employees. However, the data is now accessible to a staff of IT personnel that you do not know. For many data items, such as payroll data, the cloud-based staff is likely less interested and curious about the data. That said, companies must feel confident that the data they store within the cloud is secure. To meet these concerns, cloud-based solution providers are intensifying their recruitment and hiring processes.
Hypervisor Attack
Chapter 8, “Virtualization,” introduced you to the concept of server virtualization. As you learned, when you virtualize a server, each server operating system runs on top of special virtualization software called the hypervisor, as shown in FIGURE 9-6.
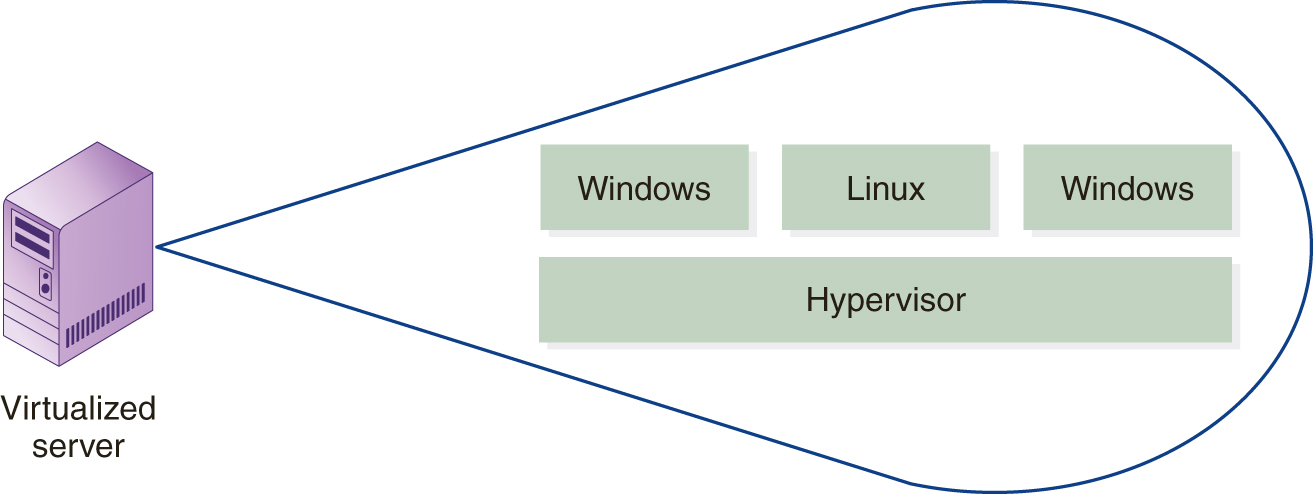
FIGURE 9-6 The hypervisor is special software that allows virtualization of system resources.
As you might imagine, hypervisor developers such as VMware and Microsoft constantly focus on ways to lock down and secure the hypervisor to reduce risks. That said, the hypervisor will remain an attractive hacker target as companies continue to virtualize solutions. Hackers refer to the process of taking over the hypervisor as hyperjacking. In the future, to reduce the chance of a hypervisor being taken over by malicious code, the underlying hardware may assign a CRC-like (cyclic-redundancy check) state value to the hypervisor. Should this value change, the hardware can detect that the hypervisor has been attacked or replaced.
Guest-Hopping Attacks
Within a virtualized server, the operating systems that execute are called guest operating systems. Assume, as shown in FIGURE 9-7, a virtual server is running three operating systems and that a hacker is trying to attack operating system A.
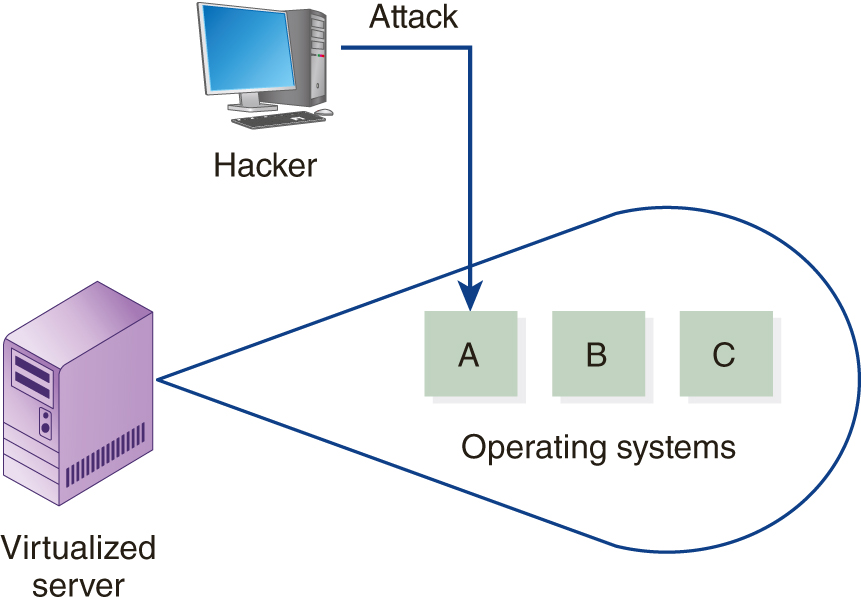
FIGURE 9-7 A virtualized server running three guest operating systems with a hacker trying to attack operating system A.
If the hacker is unable to directly attack operating system A, the hacker may then try to attack operating system B. If the hacker is successful, the hacker may then initiate a peer-level attack on operating system A, as shown in FIGURE 9-8. Hackers refer to an attack from one guest operating system to another as a guest-hopping attack.

FIGURE 9-8 A guest-hopping attack occurs when a hacker tries to attack one guest operating system from another.
SQL-Injection Attacks
Many web applications present forms that users must complete by filling in fields and then submitting the form contents for processing. The application that receives the form data often stores the data within an SQL database. An SQL-injection attack occurs when a malicious user inserts one or more SQL queries within one or more of the fields. For example, rather than simply typing in his or her last name, the hacker might type:
![]()
Depending on how the database uses the user input, the processing may result in the execution of the injected SQL, which in this case would delete the database of the company’s employees. When developers prompt users to enter data within forms, the developers must be aware of and test for such injections.
Many cloud-based SaaS solutions are multitenant applications, which means different customers may share underlying resources, such as a database. If the SaaS application falls victim to SQL injection, it might be possible for a user in one company to view, change, or destroy the data of another.
Physical Security
In Chapter 10, “Disaster Recovery and Business Continuity and the Cloud,” you will examine a variety of system threats. A cloud-based solution provider, like all data-center facilities, is subject to multiple threats, including fire, flood, theft, earthquakes, tornadoes, hurricanes, and power outages. Most, however, will reduce the risk of such threats by replicating (collocating) identical systems at geographically dispersed locations, as shown in FIGURE 9-11.

FIGURE 9-11 Using collocated replicated hardware and software, cloud-solution providers reduce many threats to IT resources.
Should one system fail, the service provider can immediately failover to the other system. Further, because most cloud-service providers have state-of-the-art data centers, they normally have fire suppression systems, backup power generators, and strong physical security measures in place.
