CHAPTER
10
Attack Attribution

One of the key elements in the practical application of profiling to a problem is the issue of objectives. Defining the optimal outcome(s) of a profiling operation is one of the first tasks that should be undertaken before the project is even launched. While it might seem like the most obvious and single-minded outcome is the identification, pursuit, and prosecution of a specific malicious online actor or group of actors, in reality, a number of outcomes should be examined before the profiling mission is deployed. For example, the identification and detention of an individual could be the end of a series of maneuvers whose sole purpose is the prosecution of a single perpetrator, or it could signal the opening act of a maneuver to acquire an important asset from which additional valuable intelligence could be acquired.
Under different circumstances, the objective of profiling techniques may be to gather and accumulate valuable intelligence that, when examined in aggregate and placed within analytical frameworks as simple as a taxonomy or as complex as a large, multivariate statistical model, could be used in subsequent operations to assist in identification, pursuit, and prosecution activities. The development of sophisticated databases that contain relational links between specific bits of information—people, places, codes, and other pieces of evidence—can provide important clues as to the identities, motives, and locations of perpetrators known or as yet unknown.
A longer-term objective involves deploying profiling techniques and strategies as one of a number of information-gathering tools used in building data sets to facilitate the analysis of more abstract, macro-level complex organizational and social structures that are emerging and evolving within the hacking and cyber criminal subcultures. These objectives belong somewhat more naturally in the realm of the intelligence analyst than the criminal investigator, but there are applicable lessons to be learned for both categories of professionals. For example, collecting and analyzing data on the elements of the social structure of the hacking community and its evolution over the past ten years can assist both the intelligence analyst and the criminal investigator in determining the nature, shape, and probability of near-term or future perils that may emerge within the cyber threat matrix.
As another example, changes in the distribution of motives of malicious online actors may also be useful in assisting members of the intelligence community, law enforcement agencies, and information security professionals in resource planning, tool or sensor innovations and deployment, and proactive defensive/offensive measures development.
In this chapter, we will discuss profiling techniques and strategies that are centered more on the objectives of identification, pursuit, and prosecution. In the course of these discussions, we will examine in more detail some of the profiling vectors briefly outlined in Chapter 4.
We will also discuss the application of profiling data and analytical techniques that represent more strategic than tactical objectives. This approach is focused on developing a more comprehensive understanding of how social forces and technology shape behavior within the hacking and cyber criminal communities. There are distinct social norms, values, and social-control mechanisms embedded in these communities. Gathering information about these characteristics and social processes can give the analyst a better understanding of how these forces help guide behavior. Understanding how these processes evolve over time can help the analyst gain some insight on how the threat environment may change over the longer term due to shifts in these social forces. This understanding then also helps with the development of cyber threat scenarios likely to emerge in the near term. This type of strategic analysis is a key element in developing longer-term strategic thinking about how the cyber threat matrix may evolve. On this basis, analysts may create threat scenarios that have predictive and logistical value, and that also facilitate discussions on how current policies and actions may have an impact on future threats, probabilities, and consequences.
In the final section of the chapter, we will turn our attention to an emerging archetype that appears to have the potential to become a very serious threat within the cyber threat matrix: the civilian cyber warrior.
A Brief Note About Levels of Information Present in Objects
Before we engage in an examination of some of the profiling vectors, let’s take a look at some inherent characteristics of information or evidence that can have a nontrivial effect on the strategies and outcomes of using some of those vectors.
In a very crude analogy to the theoretical notions of information theory first formulated by Claude Shannon, profiling to a certain extent deals with an analogous process of examining and extracting information (signal) from evidential objects that may also contain other useless bits of information (noise) (Shannon, 1948).
Evidential objects or observations obtained during an investigation involving profiling techniques may contain different levels of information, and there are limits to the amount of useful information inherent in each object. For example, a packet may contain information in terms of its size and content that is useful in identifying a specific type of attack, while the contents of a single line in an IRC conversation may speak volumes about the motives or identity of a malicious actor. In a way, this is analogous to Shannon’s notion of channel capacity, where there is a tight upper bound on the amount of information that can be reliably transmitted over a communications channel. Some channels will have very high upper bounds in terms of carrying information, and other channels will have much lower upper bounds.
Such evidentiary clues, which taken together form a pattern, allow the profiler to produce a signature that can be used, for example, to link together other incidents or attacks that can be attributed to that actor.
At the other end of the spectrum are IRC chat messages, text from e-mail messages or websites, photographic images or graphic illustrations, or even full-motion video. Their content may take the form of concrete pieces of information, such as nicknames, geographical locations, language used, specific technical skills, and claims of responsibility for specific attacks. These types of rich evidence also often include important socially meaningful clues that the profiler can use to provide a much broader and deeper profile of the individual or individuals in question. For example, different types of statements made by the participants in an IRC chat room may indirectly reveal who is likely to be the leader of a hacking gang through the analysis of the different types and frequency of statements made by the participants.
In another example, the profiler can assemble a list of potential cyber gang members, associates, and friends though a simple analysis of the pages of a social networking website. An examination of an online video may assist the profiler in identifying an offender by his use of dialect or culturally specific idioms in text-based postings, audio clips, or video clips. Accents within the video or audio clip may also be useful in identifying the ethnic origins of potential suspects. References to specific music, products, or culturally relevant items may also be useful clues.
The use of specific phrases is also a potential identification marker. The identification of FBI mole Robert Hanssen was greatly assisted when counterintelligence agents came across a specific and peculiar phrase—“the purple-pissing Japanese”—that had been used by the mole and recognized by one of the agents as something that he had heard Robert Hanssen say in the past (Wise, 2002).
Each element along this information spectrum also has its own unique characteristics when it comes to analysis of the data. At the low end of the spectrum, analysts can develop automated analytical tools that assist the profiler in sifting through the data for signatures that can identify malicious actors, which may then help link them to hitherto unattributed cyber crimes.
At the high end of the information spectrum, it is much more difficult to develop automated tools that can efficiently and accurately analyze or taxonomize socially meaningful symbols. While there are a number of ongoing efforts to develop tools such as sentiment-identification engines (Saplo, Alchemy, and others) and WarmTouch to assess the level of threat posed by a specific insider (Shaw and Stroz, 2004), the automation of the analysis of socially meaningful objects is still in its very early stages. Automation is important in that analysts are often forced to sift through very large bodies of data to extract meaningful interpretations. This is especially true in the intelligence community, where these tools must be deployed against vast warehouses of rich data elements.
Extracting feature-rich information out of data types that are typically lower on the data-richness spectrum is a primary goal. The ability to extract socially meaningful data from low-level data that is easier to collect and analyze in an automated fashion would be of significant value to profilers and investigators. However, keeping in mind some of the concepts about the limits of information transmission originally hypothesized by Shannon and extensively explored by experts in information theory today, the challenges of successfully mining social meaning-rich data from these low-level data sources have slowed the development of this type of approach.
In summary, as you explore some of the specific profiling vectors discussed in the following sections, keep in mind the preceding discussion about levels of information, both technical and socially meaningful, present in the data you collect and analyze.
Profiling Vectors
Now we will examine four profiling vectors: time, motivations, social networks, and skill level. These are just a few of the many vectors that may be helpful in profiling cyber attackers. Also, this material should not be taken as a definitive enumeration of all the potential ways in which a specific vector may be exploited, but rather as a jumping-off point for further exploring them.
Time
The value of time as a profiling vector may appear to the beginning profiler as deceptively simple and low level in nature, but it is difficult to overestimate its importance. The value of time, especially when linked to other socially meaningful information, can often be invaluable. Part of this is due to the fact that time has significant social meaning in most cultures. Time as a socially important force has been the object of examination for social scientists since at least as far back as 1913 (Bergson, 1913). Cultural anthropologists and social psychologists have made efforts to study the effects of time on cultures and people.1
From a social perspective, time organizes many everyday activities: work, school, sleeping, eating, and so on. The nature of the relationship between humans and time is often circadian in nature, with activities bound within 24-hour rhythms. The temporal nature for these kinds of activities often is normatively prescribed both in terms of time of day and duration. Work and school activities for many cultures usually occur at regular times during the day or sometimes evening. Time for sleep often is reserved for hours after darkness has set in for many cultures. These daily activities also typically take up a significant amount of contiguous time within a 24-hour period.
A similar observation applies to the temporal aspects of hacking behavior. Individuals often spend significant amounts of contiguous time engaged in hacking, coding, testing, communication, attacks, and other computer-related activities. Because computer-related hacking activities and obligatory activities (such as work) are typically difficult to engage in simultaneously, individuals must organize and manage their time within a 24-hour day. This increases the likelihood that malicious actors are going on their computers for extensive periods of time and often during similar time periods of the day.
The first consequence of this is that you are more likely to see temporal patterns for nonautomated APTs that are guided by a human actor. If an examination of your security logs shows a reconnaissance or attack preparation during a specific time of the day, then there is a higher probability that further activity, including the actual attack, may occur during a similar time period. It may also be the case that the attackers are aware of the time zone in which the intended server or computer network is located and has chosen a time when they believe there is the least chance of being detected. This time may coincide with heavy network traffic that they can hide in, or it may correlate with the attackers’ belief that there will be fewer actual information security personnel on duty at the time of the intended intrusion.
There are several advantages that this temporal pattern may hold for the profiler and information security personnel. First, if these technical personnel are present during the actual time of the intrusion, there may be actions that they can take that will allow them access to greater information about the activities of the intruder. Second, if the profiler or information security personnel have planned some sort of active engagement with the intruder, such as attempting to involve him in a live online conversation, then knowing when the malicious actor is likely to appear is a distinct advantage.
Another benefit to somewhat regular temporal patterns of activity by malicious actors is that you can make an attempt to narrow down the geographical area from which they are launching their attack. Each location on earth lies within a particular time zone. Coupled with the previous discussion of culturally and socially driven activities in time, you can sometimes use that information to concentrate investigative efforts on certain time zones, and set aside specific time zones that are more likely to hold malicious actors. It often is useful for the profiler to build a “time of day” timeline of observed malicious activity.
This logic gets a bit of additional traction in that often human activities revolve around specific days of the week. This means that the international dateline can be useful in discriminating between weekdays and weekends—while it is daylight on a Friday in the United States, it may be Saturday morning in China.
The profiler can also construct a database of important national holidays, anniversaries, birthdates, and similar dates from countries around the world. Many of these dates are idiosyncratic to a specific country as a national holiday, so changes in activities and activity level are likely to take place. The nature of some of these dates may increase the chances that the malicious actor will surface (for example, on a nationally mandated holiday). In other cases, a holiday season may do just the opposite. In the case of the Islamic holidays of Ramadan, individuals are proscribed from eating during the day and must wait until sunset to break the fast. By the end of the day, most Ramadan observants are hungry, and the first thing they are going to do is break the fast. This means that an intrusion during the first hour or so during the evening may be less likely if the malicious actor is an observant Muslim.
Establishing a time zone for the offender may also be useful in more proactive strategies where the profiling team wishes to manipulate the behavior of the target. For example, knowing the time zone within which an individual lives can suggest how physically alert the target may be at any given time that person is observed online. Catching the target when he is more likely to be tired and less likely to make careful, informed decisions may be useful in increasing the odds that a particular person may be manipulated into performing the actions desired by the profiling team.
In summary, time can be a valuable data point for the profiler. When taken together with other pieces of the picture, the temporal vector of a profile may provide some valuable insight into the identity and location of the malicious actor or actors.
Motivations
Motivations can be an important component of the profile of a malicious online actor or group of actors. Motivational profiles can assist defenders in highlighting their most attractive targets within their organization. Max Kilger lays out six main motivations for malicious behavior on the Internet: money, ego, entrance to social group, cause, entertainment, and status, or MEECES for short (Kilger, 2010).2
Money
Money is now by far the most frequent motivation for malicious acts online. However, money is not necessarily the most common motivating factor for APTs. There are still a large number of “soft targets” on the Internet that have significant monetary payoffs that do not require the skill level or level of effort typically required for an APT, and these targets are often amenable to large-scale automated attacks.
These large-scale criminal attacks use a multitude of tactics, such as phishing e-mail messages, infection of documents, flash animations, malware for “drive-by” infection of website visitors, presentation of scareware messages that dupe users into downloading fake antivirus software, and a host of other strategies. These are effective techniques whose main characteristics are the ability to scale the threat to encompass a very large potential pool of victims and the automated installation and collection of valuable financial data, such as bank account and credit card numbers, personal passwords to financial sites, and other personally identifiable information.
The ratio of financial return to effort to deploy the malware is quite high, so to some extent, this reduces the attractiveness of the often less automated APT attacks. However, this does not mean that money is still not an important motivation for some advanced threat attacks. When the financial value of a potential target for an advanced threat is high, there will be malicious actors who are willing to put in the additional effort, expertise, and time necessary to make a “low and slow” attack successful.
An additional item worth noting are the changes that significant amounts of money can bring to the normal social relationships within the hacking or cyber criminal gang. The hacking community has been described as a strong meritocracy (Kilger et al, 2004). Traditionally, an individual’s position within the status hierarchy of the hacking group has almost exclusively been determined by the level of technical skill and expertise that member brought to the group. This status position has validity within the person’s home hacking group, as well as within the hacking community as a whole.
In the early days of the hacking community, hacking for money was often looked down on as a violation of the community’s norms and values—that is, the rules that community members are expected to follow, as well as the beliefs and objectives that are shared among members. Individuals who used their computer skills to illicitly obtain funds were labeled as deviant within the community and often shunned.
As the hacking community matured, more opportunities arose to use technical skills to illegally obtain money or other financial goods. This began to attract individuals who, in addition to reasonable technical skills, also had a dominant interest in financial gain by illegitimate means. It also tempted members of the hacking community who had previously resisted or had not even thought of using their skills and expertise to illegally acquire financial and material resources. As individuals who collectively were violating the norms of the hacking community, they naturally began to band together into criminal hacking crews whose main objective was to use their technical skills for financial gain through illicit or illegal methods. As the incidence of these individuals continued to grow, individuals motivated by money began to diffuse through the community, often by having membership in multiple hacking groups, some mainly driven by motivations other than money.
As the motivation of money continued to propagate through the hacking community, it brought with it associations with individuals who were also highly motivated by money, but did not have the technical skills to carry out attacks for monetary gain. These individuals sometimes belonged to traditional organized crime gangs, especially those found in former republics of the Soviet Union. These outsiders held status in their own organizations through more traditional means, such as violence and money. As these outsiders connected with similarly motivated individuals in the hacking community, tenuous alliances between these groups of individuals formed.
Ego
Ego is the second of the six motivations for malicious online behavior outlined by Kilger. This particular motivation is not just restricted to the behaviors of individuals with malicious intent, but can also apply across the entire spectrum of individuals, including typical white-hat network defenders.
Ego refers to the positive psychological feelings that one accrues when successfully overcoming some significant technical hardware or software challenge. This might be something as simple as getting a device to perform some function it normally would not do to something as difficult as defeating a sophisticated security software suite without leaving a trace of the attack. This motivation has been around since the early beginnings of the hacking community and continues to motivate individuals to produce elegant code. Tom Holt refers to this motivation as “mastery,” and suggests that it is one of three traits that researchers have consistently observed over time within the hacking subculture (Holt, 2007).
Sometimes this motivation can result in a reversal of the old saying that “the ends justify the means,” becoming “the means justify the ends.” In a number of cases where ego is the main motivating factor, the fact that the code does something beneficial or does something malicious is moot. The intensity of the technical aesthetic embodied in the code (for example, the primacy of the quality of the hack and the level of difficulty in getting the code to work) reigns over all other rational evaluation criteria.
The technical skill sets of groups that regularly produce and deploy APTs are usually higher than those of other kinds of hacking groups. For them, the most difficult challenges are often the most attractive ones. Attacks on computer systems and networks that are protected by sophisticated security technology, such as ones associated with military or governmental entities, have great appeal for these individuals and groups. Sometimes the true reward for individuals who are highly motivated by ego is merely the successful compromise of the network or computer system and egress without ever being detected. This is similar to the practice of counting coup performed by Native Americans of the Great Plains of North America. In this practice, a warrior risks serious physical injury or death by touching his enemy in battle with a coup stick (often a beaded stick specifically used for this purpose) without causing harm to the other combatant. This was considered the highest honor in battle in this culture (Linderman, 1957).
Ego can be a very powerful motivation, especially for individuals who are very highly skilled. Nation-states can sometimes exploit this motivation, often in combination with appeals to nationalistic or patriotic sympathies, to enlist these very highly skilled individuals into special cyber warfare units. The combination of extreme technical challenges, coupled with the skills to meet them, makes this motivation an important factor when profiling or evaluating sophisticated and persistent threats.
Ego as a motivation for hacking can also be used to manipulate highly skilled individuals into performing specific acts. For example, if you believe that a specific exploit is being tightly held by a targeted individual or group, and the objective is to get the attackers to deploy that exploit, you might set up a specific server or network and widely spread claims over the Internet that this server or network is totally immune to the specific class of attack that the exploit employs. If the targeted group or individual is motivated by ego, then you have produced a scenario where it is much more likely that the attacker will deploy the exploit in question against the target, thereby allowing the profiling team to collect valuable data on the exploit itself.
Entrance to Social Group
Entrance to social groups is the third motivation for performing malicious online acts cited by Kilger. He asserts that hacking groups are more or less status homogenous in terms of technical expertise. That implies that in order for individuals to join a hacking gang, they must possess some level of expertise in hardware or software that is commensurate with the level of expertise present in that group. One way that an individual may demonstrate that level of expertise is to write an elegant piece of code that is then shown to the members of the group. If the group consensus is that the code demonstrates expertise or potential talent that approaches the minimum acceptable level for the group, then the candidate is accepted into the group, sometimes donating the code to the group as a type of initiation fee for joining.
There often are one or two individuals within a hacking group (sometimes more within larger hacking groups) who are considered to possess a level of technical skill that puts them at the bottom of the skill pool for the group. These individuals may be new to the group but have potential (newbies), or they may be longer-term members who have failed to live up to the full technical standards of the group but are tolerated largely because of social bonds they have formed with other members. These lower skilled individuals may also serve a function as boundary markers for minimum entrance into the group when new candidates are considered for membership.
Profilers may also use entrance to a social group as a method to gather information from an individual. For example, the team might establish an elite hacking group through the development of a comprehensive legend. The idea is to lure targeted individuals into disclosing valuable information in order to facilitate their membership into the group. While this deception probably will not be sustainable for very long, the information gained during the duration of the deception may be valuable enough to deploy this strategy.
Cause
Cause is the fourth motivation for malicious online acts, and it can play a key role in motivating individuals under the right circumstances. Kilger notes the following:
Cause as a motivational factor for malicious actors is often a complex result of one or more of the consequences of more macro-level geo-political, cultural, ideological, nationalistic or religious forces. There are a number of potential objectives and courses of action available to a cause-oriented malicious online actor. One of these objectives may involve the attempt to pressure an entity—particular government, political party, military, commercial or non-governmental organization, etc.—to do something that supports the actor’s favored cause.
The significant increase in recent years in the incidence of cause as a motivational factor in malicious online acts has encouraged the search for better understanding of this aspect of cyber crime and cyber espionage.
Some of the malicious acts motivated by cause may have benign consequences. Website defacement demonstrates one popular malicious act driven by this motivation. Individual actors or groups of actors who oppose the ideals or actions of a specific organization or nation-state may take it upon themselves to deface one or more official websites for that entity with slogans or rhetoric that attacks the organization. But often, no effort is made to interfere with the functions of the site. Examples of this include the 2008 attacks on CNN websites in protests related to coverage of the Olympics in China and the attacks on Australian government websites during 2009 and 2010 to protest the Australian government’s plan to filter websites that it concluded contained objectionable material.
A more serious threat motivated by cause comes in the form of the theft of confidential or secret documents from an institution or government. The purpose of the theft is often to coerce the institution or government to change a policy or action that the malicious actor or group considers unethical or morally wrong. Perhaps the best and most recent example is the WikiLeaks case involving theft of more than 400,000 government documents, many of them classified, that detailed the inner workings of various diplomatic and policy positions of the US government. Here, the ostensible purpose was to embarrass the US government by revealing the inner machinations of various government entities to influence the policies and actions of foreign governments and actors. However, when we more closely examine the actions and behaviors of the main protagonist, Julian Assange, it becomes apparent that cause is perhaps at best a secondary motivation for his actions. We’ll examine this issue in more detail when we discuss status as a motivation for malicious online activities.
The most serious instances of cause-motivated malicious online activities involve cyber attacks on nation-states’ critical industrial, military, and governmental infrastructures, with the intent to obtain intelligence and develop plans to interrupt, damage, or destroy them. One class of malicious actors involved in these cause-based activities consists of individuals who are formal members of nation-state teams for whom these are official, sanctioned objectives. These teams are experts at deploying APTs through a number of different channels, including direct attacks on networked technologies, placement of individuals within targeted organizations, and social engineering designed to extract key documents and data.
A second class of individuals are those who are semiofficially or unofficially encouraged to engage in activities to devise exploits, conduct intrusions, and gather information on a foreign nation-state’s critical industrial infrastructure, secret government documents, and military capabilities. Perhaps the most obvious example of this is the significant number of hacking groups working in the PRC. Many of these groups consist of individuals with strong nationalistic ties to their homeland, and they consider their technical expertise in hardware and software as a personal manifestation of the power that their country projects.3 One potential example of this is a 2009 Google incident that involved probable collaboration with Chinese officials. Chinese hackers compromised databases within Google, as well as 34 other major US corporations, including defense contractor Northrup Grumman. John Markoff and David Barboz reported that two Chinese technical universities were linked to the intrusions and attacks. The reporters cited James Mulvenon from the Center for Intelligence Research and Analysis, who stated, “the Chinese government often involves volunteer ‘patriotic hackers’ to support its policies” (Markoff and Barboza, 2010).
Finally, some individuals do not have any ties or support from governments and act either alone or in concert with others supporting their cause through attacking institutions and infrastructure elements of other foreign nations to further their political, religious, or ethnic cause. While these individuals usually do not figure in most APT scenarios, they do present a clear danger to foreign national infrastructures. Even individuals who do not possess significant technical skills can produce significant harm to online assets through the use of malicious software tools adapted by others who do have those skills. Note that this type of cause-motivated threat could be directed in a cyber attack on domestic critical infrastructure. This issue of the “civilian cyber warrior” is one worthy of further discussion and will be revisited later in this chapter.
Entertainment
Entertainment is probably the least known and least prominent motivation for malicious online acts. It reflects the individual’s sense of humor, as well as a mild form of social control. Individual hackers torment and play with less sophisticated system administrators, breaking into their weakly secured networks and leaving them messages admonishing them to better secure their systems.
In the past several years, this motivation has seen somewhat of a resurgence due to the spread of networked consumer devices. Devices such as mobile phones, MP3 players, and other networked digital consumer items owned by individuals with little or no technical expertise provide a large and rich target environment for members of the hacking community. These hackers may take delight in forcing the devices to transmit humorous messages or behave in an unexpected manner.
Status
Status is the last motivator in the MEECES acronym. Kilger describes the nature of the hacking community as a strong meritocracy. The position of an individual in the status hierarchy—both the hierarchy within his hacking group and externally within the larger status hierarchy of the hacking community as a whole—depends on the level of expertise in hardware, software, and networking that the individual possesses. The higher the level of technical skills, the higher the status position that person occupies.
Acquiring status can come about in a number of different ways. For example, writing an elegant piece of code or malware can elevate the status of an individual (or a team of individuals if it was a team effort). Being able to bypass a sophisticated security system is another example of how an individual might accrue status and move up the status hierarchy.
One issue that arises within this strong meritocracy is a paucity of status markers that can signal an individual’s position in the status hierarchy. Interestingly, many of the forms of digital communications that members of the hacking community use are narrow bandwidth channels, such as e-mail, IRC chat rooms, SMS texting, and the like—the metier of the hoi polloi. These narrow bandwidth communication channels do not carry many status clues that give each of the participants an idea of the other person’s position in the status hierarchy. This lack of available status cues is one reason you see the large amount of derogatory communications within the community.
Even those members who communicate via VoIP schemes like Skype or video calls using webcams are subject to limitations on the transmission of status cues, such as looking while speaking and looking while listening. This is also why hacker conventions play such an important role in the hacking community. It gives individuals the opportunity to meet face-to-face. Interpersonal communication bandwidths are much bigger, and verbal and nonverbal status cues can be exchanged more effectively. This reduces the frequency of status conflicts between individuals and helps satisfy the egos of the higher status individuals, who are expecting to be treated with respect and deference. Thus, hacker conventions play a very functional role in attenuating conflict within the community.
Status can also be acquired through the acquisition of objects with status value. The status value of these objects can be transferred to other individuals. A good example of a status object is a confidential or classified document. The personal possession of expressly forbidden information can elevate one’s status within the group. Thus, hackers or cyber criminals can improve their status by coming into possession of status objects. This brings the WikiLeaks discussion back to the table.
Private Bradley Manning, one of the principals at the center of the WikiLeaks controversy, was not considered a hacker. As an Army intelligence analyst, he had access to a vast number of classified documents. Through simple deception, he was able to copy large numbers of these documents and transfer these copies out of their classified environment. He had only some minor assistance from several technical individuals, who gave him encryption software and showed him how to use it so that he could more safely transport the copies. Even though he used only nominal technical skills in his actions, the documents he obtained had significant status value.
When these stolen documents were transferred to Julian Assange, the status value of those documents transferred as well. During the early days following the discovery of the theft of the documents, the case sounded very much like one that was motivated by cause. Many of Assange’s public statements had themes that revolved around disclosing the secret machinations of governmental and military entities as a means to coerce these organizations into behaviors that he and his followers felt were more ethically correct.
However, there were a number of signs that what was motivating Assange was not cause but status. One of the most important clues was the hesitancy to divulge all of the documents at once, but rather to dribble them out in small chunks. When an individual or hacker holds information that has status value, if he publicly discloses that information, it loses its status value because it is no longer secret or closely held. If Assange had been motivated by cause, then he would have been much more likely to release all of the documents at once in order to cause maximum embarrassment and thus enhance the chances that the disclosure would have a real effect on the governmental entities involved. Instead, he released them in smaller chunks so that he would only partially “spend” the status value of the documents with each release.
Status as a motivation can also be put to effective use in an offensive capacity. As noted earlier, the formation, maintenance, and communication of status hierarchies within hacking groups are often problematic. One consequence of this is that from a status perspective, these groups are not very stable. It does not take much discordant information to cause significant rifts within the group. For example, if inconsistent status information about a targeted group member (such as the group leader) is introduced into the communication channels, the result can be the initiation of considerable conflict that can lead to the serious disruption of the group’s activities and plans. This inconsistent status information might be introduced by manipulating another group member to denigrate the skills of the target in an e-mail or IRC communication, which in turn is leaked to other group members, as well as the hacking community at large.
Motivational Analysis
Now that we have discussed the six motivations associated with malicious online behavior, let’s see where an understanding of these motivations can be useful to profilers.
A very useful application of motivational analysis is the evaluation of the assets of an enterprise to see what servers have what kind of value to which kind of individual. This allows information security personnel to prioritize how resources are spent in the defense of the network and its servers. Using the six motivations as a simple taxonomy, each device within the enterprise can be coded in terms of the likelihood of attack motivated by each motivation. This kind of analysis may be useful in gauging the current threat environment in terms of the motivation of known actors and attacks in play, so that resources can be shifted to protect those assets that appear at greatest risk at the moment.
Another example involves the status value of stolen data or documents, which was discussed in the previous section. Imagine that you are a secret government agency, and over the weekend, a server was compromised and sensitive documents were copied and spirited outside the network to an unknown location by an unknown actor or actors. While the technical personnel patch the security hole that allowed the intrusion to take place, the reaction from senior managers at the agency may be one of resignation to the fact that the documents are now no longer secret.
The dilemma faced by senior management may not be as straightforward as it seems. It depends on the motivation of the actor or actors who committed the crime. If the motivation of the actors was one of cause, then it is likely that the documents will not remain secret very long. The documents probably will be exposed in the press at the first opportunity, or they may be on their way to a foreign power’s intelligence apparatus. However, if the motivation of the intruders was one of status value, there is a chance that all is not lost. Remember that these secret documents lose their status value when they are disclosed or copied and distributed to others. They retain their status value only as long as they remain secret and in the custody of the original perpetrators. This means that the government agency has a window of opportunity—albeit usually a small one—to assemble a technical team, put as many clues together as quickly as possible, and attempt to identify and apprehend the perpetrators while they are still sitting on the documents.
If the organization fails to apprehend the individuals in time, there is still value to the motivational assignment process. The idea here is to think of ways that you can alter the status value of the stolen assets. One possibility is to disclose the essence of the documents before the perpetrators can, in a manner that minimizes the collateral damage to the original owners of the data. Another strategy may be to generate a story around the documents that suggests that the information in them is false or misleading, and that this was done intentionally for purposes that are not going to be disclosed.
A third application of motivational analysis is the idea of tuned honeypots. A tuned honeypot system is a series of computers, each of which houses a different kind of information. If you want to understand the motivations of individuals who are attempting to compromise your network, placing a set of tuned honeypots within your enterprise can assist in providing more information about the potential motives of the attackers.
Imagine a military installation that installs a tuned honeypot system to help determine the motivations of a specific APT that has been observed attempting to compromise a particular network. One server in the tuned honeypot system might house a real-looking but fictitious e-commerce server for the base PX that would be attractive to individuals whose motivation is money. Another server might contain some real but stale troop movement and logistics information that would be attractive to individuals working for a foreign nation-state intelligence service. A third server might hold documents that contain false information about something that might otherwise embarrass the government but can be disproven as disinformation if it is ever compromised. By watching how the individuals behind the APT move around the tuned honeypot system and observing which files they examine and take, you can construct an educated hypothesis about their motivations.
A proactive example application of motivational profiles takes advantage of the nature of strong meritocracy within the hacking community, and more specifically, within a targeted hacking group itself. Given the strong presence and maintenance of the status order within the targeted group, efforts that disturb this status hierarchy can serve to disrupt the structure of the group and social relationships within that group, thus reducing its stability. This often involves the introduction of inconsistent status information concerning one or more members of the group. This technique targets the higher status, more skilled individuals in the hacking group. It may involve the public disclosure of a vulnerability in the code that the target individual has developed or the p0wning of a system that the high status target individual owns. Efforts that introduce inconsistent (for example, lower) status information about high-status individuals within the hacking group increase the likelihood of status conflicts within the group, which will strain social relationships among its members. This strategy has been effectively deployed by at least one entity within the global intelligence community.
A somewhat different approach based on similar principles could be applied to a cyber criminal gang. Recall that one of the tensions that develops within these groups results from the introduction of money as a competitive status characteristic. Aside from technical skills, status position within a cyber criminal group can depend on the amount of money the member possesses or extracts from the criminal enterprise. If the conflict revolving around which status characteristics—technical skills or money—can be amplified through a defender’s communications is directed to specific members of the cyber criminal group, then it may be possible to destabilize the cyber gang along technical and monetary issues.
Social Networks
Social networks are an incredibly data-rich and important profiling vector, especially when it comes to objectives such as identification, pursuit, and prosecution. Social networks often give profilers direct clues about many different dimensions of an individual’s life. These clues allow them to produce a very detailed profile of an individual, as well as make inferences about those individuals beyond the information present on their social networking pages.
What information sources might provide data that could be found in a typical social networking analysis? Data of this type is usually found in the form of exchanges or relationships between actors. For example, a series of IRC chats may be harvested to map the flow of message exchanges between a set of actors of interest. In another example, a profiler may extract information from the pages of online social networking websites themselves to populate a social networking analysis data matrix. Figure 10-1 is an illustration of a LiveJournal social networking page for a member of a Russian hacking crew from a recent study (Holt et al, 2009).
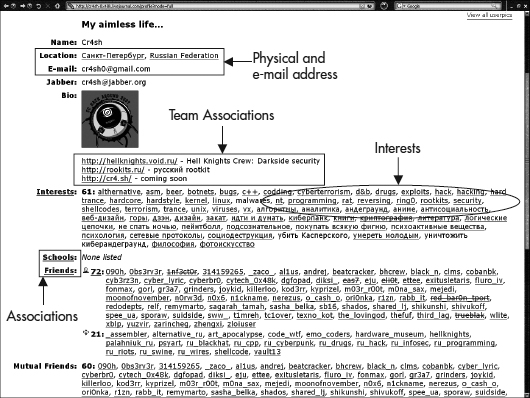
Figure 10-1 Example of a hacker’s LiveJournal web page
Notice that the webpage lists the following information about this crew member:
Using a standard link analysis, profilers can build a fairly elaborate and extensive database structure that can be used to connect individuals to each other. Additionally, this information can be used to do more formal social network analysis, where profilers can identify different nodes or individuals within the network and ascribe specific social network metrics to them. Using the social network analysis option of a commercial platform such as Analyst’s Notebook or free network analysis packages such as Pajek,4 profilers can estimate a number of social networking metrics. They can ascertain the neighborhood for a particular actor/node, determine the degree and degree centrality of actors/nodes, and measure distances between actors/nodes of interest.
Figure 10-2 illustrates a simple social network structure that might represent two very small hacking groups. One group contains foo, Amy, dng3r, and k4. The other hacking group consists of pwnr, b0b, d00d l33t, and k4. Notice that k4 belongs to two different hacking groups. This is not at all unusual; you will often find actors that belong to two or more groups. These dual membership individuals often play an important role in intergroup communications and relationships.
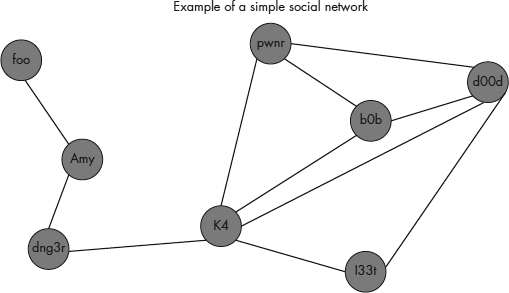
Figure 10-2 Example of a simple social network
The lines between the nodes in Figure 10-2 represent friendship ties. When any two nodes have a direct line between them, they are said to be adjacent, and the entire set of individuals that are adjacent to a specific node or actor is said to constitute that node’s neighborhood (Scott, 2000). For example, the neighborhood for b0b consists of members d00d, pwnr, and k4. Neighborhoods are a useful concept when attempting to learn more about a specific target such as b0b. While information about b0b may be scarce, you might be able to collect either direct or inferred information about b0b through one or more of the individuals in his neighborhood.
The centrality of a node can also play an important part in analyzing the structures of hacking or cyber crime groups. The most common metric of centrality in social network analysis is degree centrality. Degree is the number of lines that connect a node directly to other nodes. Thus, a high degree for a specific node also denotes a high level of degree centrality (Nooy et al, 2005). In Figure 10-2, k4 has a high degree of centrality in comparison with some of the other actors in the social network. Degree centrality can be useful to identify various characteristics of actors or nodes within the social network diagram, such as evaluating the popularity of an individual. In the case where lines indicate communication paths, a node with a high level of degree centrality can suggest a communications hub or an actor critical to communications within the network.
There are other measures of centrality at the individual node level as well as aggregated across an entire network,5 but the idea here is that measures of local network centrality help profilers and investigators identify key individuals or entities that play an important role in the network. Once these individuals are identified, the investigators can determine what further measures they might deploy against these central targets.
Centrality can also play a part in the analysis of diffusion processes as well. The rate at which the diffusion of some object, such as a piece of information or an exploit, occurs depends to some extent on the centrality of the node that originated that object (Nooy et al, 2005). For example, an exploit that originates from a node/actor that has high centrality will diffuse faster on average than an exploit that originates from a node/actor that has lower centrality. If analysts can obtain a timeline of the diffusion of an exploit, they may be able to work backward in time to estimate the centrality of the originating node or actor, which may give them an additional profile characteristic that could be helpful in identifying the original source of the exploit. This relationship could also be used in the situation where analysts have identified an actor who has developed an exploit that he has kept to himself. In this situation, the analyst may be able to estimate the temporal window of the diffusion process if and when the exploit is released by examining the degree centrality of that actor within his larger social network.
The profiler or analyst does not necessarily need to have an extensive background in social network analysis to extract useful information from social network diagrams of malicious online actors. Sometimes just a visual inspection of a social networking diagram can unveil some interesting and useful information. Let’s take the original social network diagram shown in Chapter 4 (Holt et al, 2010) and annotate it a bit in our example, as shown in Figure 10-3.

Figure 10-3 Mutual friends networks
Notice that there appear to be two sets of nodes or actors that are considered serious threats here. The first set includes three actors (identified by a red circle in the color version of the diagram) who reside in the center of the friendship network and appear, from visual inspection, to have a high level of degree centrality. The second set, on the left side of the diagram, consists of four serious threat actors who are more typically social isolates. We know from the previous discussion that the high centrality, high threat group likely has a faster exploit diffusion rate than the socially isolated high threat group. Thus, any malware that escapes from these individuals is likely to spread to more malicious actors faster, and thus has a higher probability of being modified, adapted, and deployed.
Another perspective on the social network diagram shown in Figure 10-3 involves the socially isolated serious threat group of four actors. Why is the degree for these actors significantly lower than for the other high risk group? Is it because these are individuals who have purposely declined to form friendship bonds with other hackers in order to lower the probability of detection and identification? Or perhaps the motivation for these individuals is different from that of the others in the social network diagram. If these actors were motivated by money, for example, and the other actors in the network were driven primarily by other motivations such as ego or status, then this could also explain the social isolation of this second set of serious threat actors. It is also possible that these individuals are members of an unidentified group.
Another social networking diagram taken from the same study (Holt et al, 2010) can also yield some useful information from visual inspection. Figure 10-4 shows a social networking diagram that uses the different Russian hacking groups as nodes in the network.
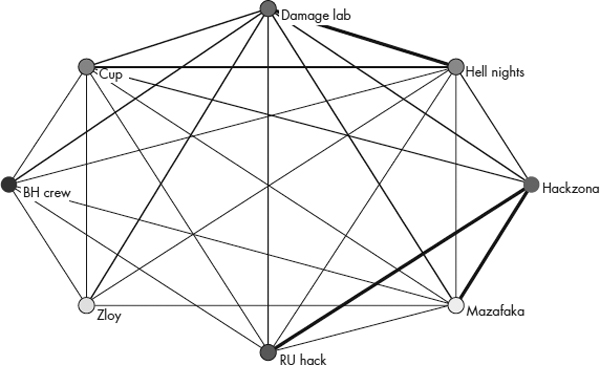
Figure 10-4 Strength of group ties
The thickness of the lines connecting adjacent nodes represents the strength of friendship ties between the groups. A thick line means that there are a large number of total friendship relationships between members in each group. A thin line means that there are a small number of friendship ties between the two adjacent groups.
A simple inspection of the diagram in Figure 10-4 reveals that Hackzona and RUhack seem to be strongly cemented to each other in terms of friendship ties. On the other hand, there appears to be only a few friendship ties between BHCrew and Mazafaka. This information could be useful in a number of ways. One way is that it suggests the likely paths that exploits might take when they are finally diffused out of the originating hacking group. There is a good chance that the exploit will follow stronger friendship ties when traversing one hacking group to another. Another interpretation could be that the lack of friendship ties for a specific hacking group indicates that the group members are deliberately isolating themselves from other hacking groups and individuals in order to minimize their signature and the amount of information that is known about them. A third possibility is that the linkages between the groups have been obscured by their use of a cutout or intermediary whose knowledge of the actors in the social network is generally very limited.
Another use for this network diagram is to assess the potential for collaboration or even a merger among these Russian hacking gangs. The larger the number of friendship ties between two groups, the more likely that there may be cross-gang collaboration or even mergers. If there is a potential breakup of one of the groups, this diagram also might be useful in predicting which of the groups would be the most likely recipients of “refugees” from the disintegrated group.
Finally, this diagram may also prove to be useful for proactive counterintelligence purposes. If it turns out to be difficult to insert someone into a specific hacking group represented here—Damage Lab, for example—then it might be possible to insert an agent into one of the other groups that has a large number of friendship ties with Damage Lab, such as Hell Nights. Once inserted, the agent can then work on establishing reputation and rapport within Hell Nights, especially with individuals who, according to the social networking diagram, have a number of friendship ties with members in Damage Lab. Eventually, this may allow the agent to assimilate himself into the targeted Damage Lab hacking group over time and carry out the objectives assigned to that individual.
Skill Level
A lot of attention has been paid to the level of skill a malicious online actor possesses. As discussed in Chapter 4, skill level plays an important part in attempting to build a taxonomy of different types of malicious online actors (see Rogers, 2005, for example). This makes sense, given that in APTs, skill level is an important profile signature of an attack and the people behind it. The attacker’s skill level also serves as a key indicator of the level of threat posed to other assets owned by the potential victim, as well as suggesting the magnitude of threat posed to the computing community at large.
A significant improvement on these efforts was put forth in a study by Donn Parker and fellow researchers, where they examine two theoretical characterization metrics: the skill set and level of skills possessed by the attacker, and the application of those skills to a specific attack event (Parker et al, 2004). Parker and his associates utilize information from the postattack analysis to fill in the details for these two attacker characteristics. They suggest evaluating the ease with which the tools used for the attack are deployed. Someone who is an expert on the theory and mechanics of a particular tool is likely to use it in a more efficient and elegant manner than an attacker who is not so familiar with the tool. There are likely to be fewer mistakes and misapplications of the tool by individuals who are well acquainted with its methods and mechanics.
The availability of the tools used in the attack is also important, as Parker notes. The suspected distribution frequency of the tools gives the analyst an idea of the size of the potential pool of suspects. If it is a tightly held or rarely seen tool, then its distribution may also be highly restricted. In the case of rare tools being used, the enhancement of the skill analysis with a social network analysis may help illuminate the pathway that the tools have taken and highlight individuals who may have come into possession of those tools. Parker and his associates also suggest that skill levels required for the attack may be mitigated by other contextual or situational factors. For example, if the attack comes from inside the targeted network or organization, then the skills necessary to pierce the organization’s external firewalls and security systems may not be necessary for the attack’s successful outcome.
Finally, Parker and his associates suggest that more advanced adversaries may deploy feints or diversions that indicate a less competent or skilled adversary. The intent of these activities may be to obfuscate the true skill level of the attacker or to bury the APT within a cloud of more numerous, less skilled, attack traffic.
Consistent with this multidimensional approach is the idea of separating the skill level of the individuals responsible for the attack into a number of interrelated factors. These factors include, but are not limited to, the following:
Making the effort to produce this complex attack signature provides several benefits to the defenders. First, it provides a signature that can be used and compared against other attacks to assess the likelihood that the attacks are either directly or indirectly linked. Second, the attack signature can be compared to multidimensional skill level characteristics of malicious online actors (with known or unknown identities) present in a database. This assumes that a previous concerted effort has been made to gather intelligence and data on the skill levels of malicious online actors in the areas addressed by the attack signature. Proactively building and updating a comprehensive database of these individuals and their skill characteristics is a forward-looking strategy that may have significant benefits and payoffs in linking specific actors to specific attacks. Such a database may also provide a foundational basis for gathering intelligence in other relevant areas.
One source of data for this skill and tool utilization database is the information extracted from postattack analyses. In this case, skill levels, tools utilized, presence or absence of feints, level of skill deployed in covering up the attack, and other factors can be attached to tables within the database that use specific attacks as the basic unit of analysis.
A second and perhaps even more important source of data for this profiling database is the rich and detailed data that can be accumulated from text-based intelligence. Data sources that can be useful in building this dimension of the profiling database include conversations gleaned from IRC chat forums, text-based materials from websites that belong to individual hackers or hacking groups, and legally obtained e-mail communications. Intelligence can also be gleaned from visual materials by closely examining photos or video posted on individual or group websites. Books, manuals, empty software boxes, CD labels, and other items shown in these photos and videos can be useful in determining possession of specific skills on specific platforms.
One issue that often comes up when dealing with the use of self-reported claims of skill and expertise is the bias in self-reported skills. Fortunately, when the researcher understands the nature and consequences of the strong meritocracy that exists within the hacking community, it becomes clear that the self-report skill-based information acquired online, especially in places like IRC chat rooms, is probably a reasonably accurate assessment of the individual’s actual skills. An attempt by an individual to claim skills that he does not have will almost always be challenged by other individuals within the hacking group or social network.
Overstating or misleading others in the community about one’s skill level is a serious norm violation in a strong meritocracy. Such claims will almost always result in attempts by other individuals within the violator’s social network to engage in social-control statements and actions to let the individual know he has violated a core community norm. These social-control actions might come in the form of text-based attacks on the violator in an IRC chat room, directly challenging the skill and expertise claims that the violator has made. Members of the community may also post derogatory comments about the violator on other lists or websites. Continued violation of this norm may lead to more aggressive social-control behaviors, such as efforts to compromise the violator’s personal computer or network as a shaming mechanism. Continued attempts to claim unearned expertise may lead to the expulsion of the violator from the hacking gang. Thus, claims of expertise within hacking groups are not taken lightly.
In the case of criminal gangs, where some of the individuals are members of more traditional organized crime elements, overstated claims of skill and expertise in technical areas may temporarily escape retribution due to the fact that these criminal outsiders often do not possess the technical expertise to quickly uncover the misleading information. However, if the overstated skill claims result in the repeated failure of the claimant to produce successful outcomes in the criminal venture, the reaction of the traditional criminal element of the gang may be much more unpleasant than the hazing performed by typical hackers. Also, over time, a small but important group of criminal outsiders may have gained the necessary technical expertise. This event may short-circuit some of the issues surrounding the skill gap between members of the hacking community and more traditional criminal outsiders.
In any case, understanding the strong meritocracy of the community assists the profiler or analyst in determining which pieces of skill-related information have a high, medium, or low level of validity. Those skill claims that are exposed to the scrutiny of the group member’s peers and skill superiors are likely to be fairly accurate. Those claims of expertise that have not been similarly exposed to others who know the claimant are more apt to be suspect in terms of validity.
Vector Summary
The previous discussions have only touched on some of the many vectors that may be of use in profiling malicious online actors. Each of these areas should be pursued in depth to provide a better picture of the attackers and their motivations, in order to find clues to their identities.
An example of another potentially useful profiling vector is the application of linguistics and semiotics to communications made by hacking gang members. This may provide some probabilistic predictions for basic demographics of the individual, such as gender, age, educational attainment, ethnicity, and geolocation. Additionally, cataloging word frequencies, phrases, and other unique speech or text fragments in a database can assist in the identification of individuals of interest and help an investigation narrow its focus to a smaller set of targeted individuals. The application of concepts and principles from linguistics and semiotics may also be useful in determining the level of threat that someone represents, such as the WarmTouch system developed by Shaw and Stroz.6
Whatever profiling vectors are selected, when the profiler or analyst constructs a description of a targeted individual or individuals using multiple vectors or dimensions, the resultant profile, when combined with other forensic evidence provided by investigators, can often provide a much more complete picture of individuals pursuing advanced and persistent threats.
Strategic Application of Profiling Techniques
Now we turn from the analysis and construction of profiles for groups or individuals to profiles of the hacking community as a whole. Understanding how the social structure of the hacking community is changing can provide strategic analysts with a better understanding of how the cyber threat matrix may change in the future, and how members may migrate to and from other groups, such as cyber criminal gangs. Analysts can also gain enough understanding of the social forces involved to be able to build realistic future potential threat scenarios. These types of objectives support longer-term objectives that include areas such as proactive defenses, resource planning, and developing legislative and governmental policies that address the contingencies of emerging cyber threats.
Example Study: The Changing Social Structure of the Hacking Community
One of the early attempts to analyze the social structure of the hacking community was conducted by Kilger and his colleagues (Kilger et al, 2004). This analysis was driven by the application of a hybrid qualitative/quantitative research methodology to uncover the hidden social dimensions within the hacking community. The investigation used a contextual analysis of the Jargon File as it existed online in 1994.
The Jargon File was an accumulation of a large number of words and phrases that had special meaning within the hacking community.7 It was maintained and updated by a series of caretakers, with its gradual demise sometime after 2003. There were never proven accusations of malfeasance in the manner in which the file was being maintained. The analysis of the Jargon File identified 18 social dimensions within the hacking community, which included, but were not limited to, technology, derogatory, history, status, and magic/religion. The incidence of thematic terms suggests to some extent the importance of the social dimension within the community itself.
This study was repeated again a number of years later using one of the last versions of the Jargon File in 2003, around the time that conflicts among its various caretakers and proponents effectively ended its community-wide acceptance (Kilger, 2010). The objective of the replication was to be able to compare the social structure of the hacking community between two periods of time. Given the swift rate at which technology and the community itself is evolving, the nine-year time window between the two studies should be sufficient to detect changes in the social structure.
Figure 10-5 shows the distributions of the social dimensions embedded within the hacking community for 1994 and the reanalysis of data from 2003. Examining the data over this period shows some significant changes within the hacking community’s social structure. In the following sections, we’ll look at the technology, derogatory, and magic/religious dimensions in more detail.

Figure 10-5 Dimensions of the social structure of the hacking community
Technology
Technology obviously plays a key role in the community, and this can be seen by its ranking as the social dimension with the most terms and phrases associated with it in the Jargon File. While this statement is true for both time periods under investigation, it can be seen that there has been a substantial drop in the incidence of this dimension.
It’s very likely not the case that the rate of introduction of new technical terms has significantly decreased given the evolving nature of the field. What does seem to be the case is that there is less focus on technology and technical terms than in the past. While the interpretation of this shift is not entirely clear, part of it may be due to several factors, including an influx of individuals into the hacking community who lacked some of the professional engineering training and background that was more prevalent in the field in 1994.
Derogatory
The second important dimension found in the analysis is the derogatory dimension. Derogatory terms have historically been used by members of the hacking community as elements of social-control processes within the community. For example, when status conflicts arose from issues such as challenges to claimed skill levels, derogatory terms were utilized as social-control mechanisms to attempt to resolve those conflicts. Terms such as “luser” and “lamer” were dispatched in an effort to disparage the individual making allegedly false or overinflated skill or expertise claims.
Notice in the time that has elapsed since the first study there has also been a decrease in the number of derogatory terms within the hacking subculture. Perhaps this is due to a moderate deemphasis on technical skills within the community, which would correlate with the decrease in technology terms. Or perhaps it is the cumulative effects of the rise in popularity and attendance at hacker conferences. Remember that these status conflicts arise more often online than offline because of the limited bandwidth that is normally used for communications among members of the hacking community (such as e-mail and IRC chat rooms). As more and more members of the community meet face-to-face where these communication constraints are absent, it may be the case that more status conflicts within the hacking community are being resolved, and thus the need for additional derogatory terms and phrases within the community shrinks accordingly. This hypothesis may receive a bit of further support when one looks at the social dimension of status within the hacking community. There is a fairly significant decline in the incidence of status-related terms and phrases in the Jargon File between 1994 and 2003.
Magic/Religion
One of the most telling shifts in the social structure of the hacking community is reflected in the more than 50 percent decline in the number of terms that are associated with magic/religion. The concepts of magic and religion have been present and important core social elements in the hacking community since its early beginnings.8
Magic/religion might at first glance seem like an unlikely key element in the social structure given its technical nature. However, it is in fact due to the complex nature of the technology at the heart of the industry that this concept is present and plays such a key role in the original core spirit of the hacking community.
One way to explain this dimension is to imagine some object A—for this example, some operating system shell command with various parameters. Suppose that the hacker issues the command to the operating system, and the result of that command is event B. If the hacker cannot logically explain why command A resulted in event B—that is, the complex operating system functions as a black box—then one way to look at the phenomenon is as the result of magic. This emergence of a belief in magic is not unlike similar studies in the anthropology literature, where members of an indigenous tribe use magic to explain the reason for certain phenomena occurring in the natural world around them.
Especially during the early days of the hacking community, operating systems and their internals were rather cryptic, and the reasons for following specific procedures were mystical at times.9 There arose a need to develop a Zen-like attitude toward operating and maintaining complex and often cantankerous operating systems. This nurtured a sense of magic about the relationship between system administrators and the servers in their care. Unix wizards, as they came to be known, were people who knew incredible amounts about the operating systems and hardware, and were revered for being able to help their fellow, less-experienced system administrator friends out of serious jams. Many times, the wizard would guide the panicked system administrator through a series of procedures to resolve the issue, but would refuse to explain the logic behind the rescue, preferring instead to label it magic. Everyone had a wizard they could call on in those days. The need to rely on those wizards generated strong social bonds between many individuals in the hacking community.
The system administration environment has changed dramatically since those early days. While operating systems are more complex than ever, the prevalence of graphical user interfaces and gigabytes of online technical resources diminish the original social dimension of magic. Instead of calling wizards with whom they have personal relationships, corporate system administrators call outsourced technical support professionals, often halfway around the world. The shifts in these technologies and practices have greatly diminished the role of magic/religion within the technical community, and the disparity between the incidence of magical/religious terms between the years 1994 and 2003 provides further evidence of this decline.
Micro- and Macro-Level Analyses
We’ve taken a brief look at one example of how profilers and analysts might analyze more macro-level phenomena such as shifts in the social structure of the hacking community. But why would this effort be useful?
Part of the answer lies in the fact that these more macro-level forces do have more micro-level consequences. Understanding how certain dimensions of the social structure of the hacking community are changing can provide profilers and analysts with an important contextual foundation on which to place their more micro-level profiling efforts. It gives the profiler the advantage of understanding the bigger context within which individual actors and groups are operating. This can contribute significant additional insight and give meaning to attitudes and behaviors that the profiler or analyst is observing in a specific situation, which in turn can color the interpretations and conclusions that come as a result of some specific investigation.
There are also advantages to taking into account both macro- and micro-level social forces in the area of proactive investigations/actions where an analyst/investigator may need to assume the role of a malicious online actor. Understanding the social norms and values of the larger community as a whole can help investigators and analysts better frame their attitudes and behaviors so as to lessen the chance of violating social norms or holding values that lie outside the normative definitions of the community they are supposed to be joining. In turn, this significantly reduces the probability that they will be exposed.
Secondly, studies like the one in the hacking community social structure example provide the analyst with clues to the direction of longer-term trends within the community that might not otherwise be observable from a more micro-level analysis. Changes in these more macro-level structures can suggest that there are as yet unidentified events or actors whose occurrence or actions are affecting the hacking community or the cyber criminal underground in ways that might be obscured or difficult to observe from the analysis of individual-level data alone.
The value these kinds of studies and information bring to the analysis environment can be substantial. However, the number of macro-level studies of the hacking community or the cyber criminal underground is at present fairly limited. One exception to this observation is in the area of the carding10 communities. Researchers have expended some larger than normal efforts to better understand the macro-level forces in that particular subculture.11
We hope that one of the benefits of the discussions in this chapter is that more analysts and social scientists will become interested in conducting research with the objective of producing a better understanding of the hacking and cyber criminal communities and their subcommunities at all levels of analysis.
The Rise of the Civilian Cyber Warrior
Finally, let’s take a brief look at the emergence of the civilian cyber warrior. In order to understand the significance of this phenomenon, it is necessary to briefly examine the nature of the power relationship between the nation-state and the individual. This topic is most certainly not new; it has been discussed at length by a number of philosophers and social scientists.12 However, in the past few years, the psychological balance of power between these two entities has begun to shift.
An example may help illustrate this point. Imagine in the era before the Internet, a person we’ll call John is living in his home country, which we’ll call Country A. John feels that the government of Country B committed some act that he considers immoral. What is John to do? Well, he could write a letter to the president of Country B and tell the president that the country had done a bad thing and should stop doing it. What’s the likely outcome of this effort? Probably nothing would change.
So now John decides to go to Country B’s embassy in a nearby city and protest along with some other people. What’s the outcome of this action for John? Likely, it would be arrest and/or a quick whack with a police baton.
Finally, John withdraws his life savings from the bank and travels to Country B. There, he purchases some explosives and plans to blow up some building or other facility. What’s the likely outcome here? John will be arrested before he has the opportunity to carry out his plot, and he will spend a long time in prison. Or, John may die in an explosion when attempting to attack the target at hand. The likely result is that John will end up with a very negative outcome and fail at his objective at very great personal cost.
Now fast-forward to current times with the easy availability of the Internet. A person from Country A, who we’ll call Mary, is angry at the policies of Country B. She walks into her bedroom, turns on her computer, and begins to search for critical national infrastructure facilities in Country B that might be vulnerable to cyber attack. She selects a target, and then begins the slow reconnaissance, preparation, and deployment of an APT. At the appropriate time, she unleashes this threat and disables or seriously damages the critical national infrastructure element.
The Balance of Power
For the first time in history, individuals have a pathway to effectively attack a nation-state.13 This opportunity represents a dramatic shift in the power relationship between the nation-state and the individual. To some extent, the awareness of this opportunity has been available within some elements of the hacking community for a number of years. The famous 1998 incident where Mudge from the hacker group L0pht told congressional leaders that he could take down the Internet in 30 minutes is one example of the existence of that awareness early on.
This issue of the change in the balance of power between the nation-state and the individual is becoming a more encompassing concern as the salience of this shift diffuses and spreads through the hacking community and beyond. One interesting evolving scenario involves the rise of hacking gangs in China and their shadowy, informal, semiofficial, or even formal relationships with various entities within the Chinese government The focus here is on the power relationship between these private hacking groups and the Chinese nation-state.
As Chinese hacking groups proliferate and become more proficient, they are beginning to amass instruments of power and prestige. These instruments may take a number of different forms. They may take the financial form of stolen credit cards, bank accounts, and actual funds withdrawn from companies and organizations in other countries. These assets may also take the form of sensitive documents containing valuable intellectual property and trade secrets, as well as sensitive documents extracted from government or military websites. These assets allow Chinese hacking gangs to enhance their power through the purchase of additional hardware, network access, and the skills of other individuals. The gangs also receive protection from local, regional, and even national-level authorities through the deployment of these assets in the form of the handover of secret documents or dispersal of bribes or other illicit payments.
Perhaps an even more serious facet of this phenomenon is the development by these Chinese hacking gangs of very sophisticated and powerful software tools and malware that allow them to continue to collect ever-increasing amounts of these assets. These tools are in and of themselves assets that have the potential to shift power relations between nation-states, as well as between the nation-state and the individual. In the case of nation-state to nation-state, shifts in the balance of political and military power can, in part, be facilitated by the extraction and exfiltration of secret government and military data and documents from foreign countries to the Chinese government. This may take place through various methods. The hackers may be employed or conscripted into government service so cyber attacks on sensitive organizations in other countries may be directly carried out by these individuals. In other cases, the Chinese hacking gangs may be obtaining information of this nature through their own initiative, and thus contributing to shifts in political, economic, and military power between China and other nation-states.
Even more interesting are the potential shifts in the power relationships between the nation-state and the individual. This is of particular interest in places like China, where a strict authoritarian form of government attempts to tightly control certain aspects of civil society, including rights to free speech, constrained economic determinism, access to the political process, and access to news and information. One potential outcome of the accumulation of financial assets is the use of these assets by Chinese hacking gangs to gain political and economic power within local regions of China. Expending these assets intelligently, such as by bribing or suborning local authorities, could conceivably expand the power base from which the private hacking gangs operate.
At the extreme, the strategic use of these malicious software tools and malware against Chinese industrial, governmental, and military infrastructures is conceivable. This potential ability could significantly shift the power relationships between individual and nation-state in the case of China. So, how real might this potential scenario be? The answer to that question is certainly not obvious. Several significant factors could effectively limit or possibly completely negate any potential shifts in power between the individuals that make up these hacking gangs in China and the Chinese government apparatus.
The first factor is the authoritarian nature of the Chinese government itself. The Chinese government has broad, sweeping powers over its populace. For example, the Ministry of State Security is involved with both foreign and domestic intelligence matters. The Ministry of State Security has wide latitude in pursuing activities and individuals who are deemed subversive or a threat to the state. In addition, China’s legal system is still tightly linked to committees within the Communist Party’s Central Committee (Cohen, 2011) and thus so-called subversive crimes committed against the state are likely to be harshly punished.
A second factor that probably has a strong inhibiting effect on the exercise of economic, political, and technical power by Chinese hacking gangs against the Chinese government is the high level of nationalism and nationalistic pride that many Chinese citizens, including members of Chinese hacking groups, exhibit. These nationalistic feelings among members of Chinese hacking groups often visibly surface during heightened tensions between China and other nations resulting from a specific incident or event. One example is the 2001 Hainan incident, where a US reconnaissance aircraft collided with a Chinese fighter aircraft, and the US aircraft was forced to land in Chinese territory. Chinese hackers attacked a number of US government websites, including that of the White House. Another incident was the accidental bombing of the Chinese embassy by NATO forces in 1999, which led to US government website defacements.14
Finally, we must assess the potential enlistment of larger segments of the population into attacks against the nation-state’s critical infrastructures. Historically, the focal actor for attacks on the nation’s infrastructure has been limited to highly skilled members of the hacking community, terrorists, and, to some extent, cyber criminals. The ongoing shift in the nation-state versus individual power balance, however suggests that this set of focal actors is likely to expand to include other segments of the population. For example, in early February 2010, the Chinese government raided and shut down a “hacking academy” whose objectives were to educate its members in cyber attack methods and facilitate the distribution of malware. There were more than 12,000 members of this hacking academy when it was raided.
Potential Civilian Cyber Warrior Threats
The preceding discussion brings focus to the research question: Given the ready availability of the skills or tools necessary to launch a cyber attack against a nation-state, under what circumstances would people outside the usual focal actor set feel impelled to act? Would individuals from the general population be willing to attempt cyber attacks, and if so, what level of damage might they inflict? This discussion also includes the potential for domestic terrorism cyber attacks against domestic critical infrastructures. To date, there appears to be a paucity of research that addresses these particular issues.
One research study investigating this potential new threat involves assessing the likelihood that individuals would use either physical or cyber attacks to punish a foreign nation-state or their own homeland for acts of aggression against their country or their own citizens. A study currently under way by Holt and Kilger examines the magnitude or severity of a physical or cyber attack that individuals would carry out against a foreign country or the country they consider their homeland (Holt and Kilger, 2011). Multivariate statistical models from the study examine the potential effects of a number of variables on the severity of attack. Respondents in the study include both US and foreign students at a Midwestern US university. Some of the independent variables in this study are gender, age, advanced computer skills, software or media piracy, homeland,15 out-group antagonism, and emotional ties to their homeland (such as feelings of nationalism).
While this study is still underway, very early results from the study models suggest that relationships exist among some of these variables and the severity of attack against another country or their own country. For example, early models suggest that there is a positive relationship between pirating media and software and the level of severity of a cyber attack or a physical attack against one’s own homeland. Individuals who considered some country other than the United States as their homeland also indicated they would initiate more severe cyber attacks against their own homeland. The study also hints at a possible relationship between the severity of contemplated cyber attacks and the severity of potential physical attacks against their own homeland.
When completed, the study may provide additional insight into the willingness of a more general population of individuals to launch a cyber attack against a nation-state—either foreign or their own. For example, results from this study suggest that the factors involved depend both on the type of attack—physical or cyber—and the intended victim—a foreign country or one’s own homeland. As one might expect, those with less strong feelings of patriotism were more likely to initiate a cyber attack against critical infrastructures in their own homeland. Respondents whose homeland was somewhere other than the United States were more likely to conduct a cyber attack against critical infrastructure elements in their own homeland. Those respondents who had engaged in software or media piracy acts were more likely to engage in a cyber attack against a foreign country.16
Conclusion
This chapter described a small number of the many profiling vectors that play a part in profiling APTs, providing some examples of profiling characteristics and strategies. We addressed some of the strategies that might be used in profiling specific cyber attacks or attackers, with the goal of enhancing the digital forensic investigation process.
This chapter also introduced the idea of using profiling data on a strategic level to gain a better understanding of macro-level forces at work. We discussed the potential for individuals to conduct cyber attacks against their own or other nation-states.
We hope that some of the ideas presented here will spark additional professional interest in the area of cyber profiling, as well as remind more traditional technical forensic teams of the importance of knowing your enemy.
References
Bergson, H. (1913). “Time and free will: an essay on the immediate data of consciousness.” New York: Macmillian.
Cohen, J. (2011). “Law unto itself.” South China Morning Post, March 30, 2011.
de Nooy, W., Mrvar, A. and V. Bagtagelj (2005). “Exploratory social network analysis.” New York: Cambridge University Press.
Foucault, M. (1977). “Discipline and punish.” Canada: Random House Holt, T. (2007). “Subcultural evolution—Examining the influence of on and offline subcultural experiences on deviant subcultures.” Deviant Behavior (volume 28, pp. 171-198).
Holt, T. and M. Kilger (2011). “Civilian participation in cyber conflict.” Presented at the 10th Annual Honeynet Project Workshop, Paris, France.
Holt, T., Kilger, M., Strumsky, D. and O. Smirnova (2009). “Identifying, exploring and predicting threats in the russian hacker community.” Presented at DefCon17, Las Vegas, Nevada.
Holt, T. and E. Lampke (2010). “Exploring stolen data markets online: Products and market forces.” Criminal Justice Studies 23 (pp. 33-50).
Kilger, M. (2010). “Social dynamics and the future of technology-driven crime.” In T. Holt and B. Schell (Eds.), Corporate Hacking and Technology Driven Crime: Social Dynamics and Implications (pp. 205-227). Hershey, PA: IGI-Global.
Kilger, M., Stutzman, J., and O. Arkin (2004). “Profiling.” In The Honeynet Project. Know Your Enemy (pp. 505-556). Addison Wesley Professional.
Linderman, F. (1957). Plenty-coups, Chief of the Crows. Lincoln, NE: University of Nebraska Press.
Markoff, J. and D. Barboza (2010). “2 Chinese schools said to be tied to online attacks.” New York Times published February 18, 2010, retrieved on May 1, 2012 from www.nytimes.com/2010/02/19/technology/19china.html.
McGrath, J. and F. Tschan (2004). “Temporal matters in social psychology: Examining the role of time in the lives of groups and individuals.” American Psychological Association.
Parker, T., Shaw, E., Stroz, E., Devost, M., and Sachs, M. (2004). “Cyber adversary characterization: Auditing the hacker mind.” Rockland, MA: Syngress.
Rabinow, P. (2008). “Marking time: on the anthropology of the contemporary.” Princeton, NJ: Princeton University Press.
Rogers, M. (2005). “The development of a meaningful hacker taxonomy: a two dimensional approach.” CERIAS, Purdue University.
Scott, J. (2000). “Social network analysis: a handbook.” London: Sage.
Shannon, C. (1948). “A mathematical theory of communication.” The Bell System Technical Journal (volume 27, pp. 379-423).
Shaw, E., and Stroz, E. (2004). “WarmTouch software: assessing friend, foe and relationship.” In Parker, T. (Ed.), Cyber Adversary Characterization: Auditing the Hacker Mind. Syngress Publications, Rockland, Mass.
Wise, D. (2002). “The inside story of how the FBI’s Robert Hanssen betrayed America.” New York; Random House.
Wu, X. (2007). “Chinese cyber nationalism: evolution, characteristics and implications. Langham.” MD: Lexington Books
1 For an anthropological take on time, see Rabinow, 2008. For a social psychological perspective, see McGrath and Tschan, 2004.
2 The MEECES acronym is based on the original acronym MICE used by the FBI for the reasons individuals would betray their country: money, ideology, compromise, and ego.
3 For a much more complete picture of this phenomenon, see Wu, 2007.
4 For a good practical guide on using Pajek to analyze social networks, see Nooy et al, 2005.
5 For examples of other measures of centrality, see Nooy et al, 2005:pp. 123-137.
6 WarmTouch is a psycholinguistic system developed by Shaw and Stroz that utilizes psychological profiling algorithms to analyze the psychological states and characteristics, such as anger, emotional vulnerability, and anxiety, as well as evaluating potential behaviors of a suspected malicious actor.
7 For an example of the Jargon File, see www.catb.org/jargon/.
8 Indeed, since the early beginnings of many Unix and Linux operating systems, magic numbers have played an important role in disk and file structures. The magic command can be found in the manuals for these operating systems.
9 Once Kilger shut down a Unix system for the weekend, and on return that Monday, found to his horror that when he turned on the power switch, nothing happened. He quickly called his Unix wizard, who told him to disconnect all the cables from the CPU. The next direction was to lift the CPU over his head and do the hokeypokey. When asked why, the wizard said “just do it.” After performing the magic hokeypokey, the wizard instructed the author to reconnect the cables and turn on the power switch. The server came to life immediately. When asked why, the wizard at first said “magic,” and then relented and explained that the lubricant in that particular hard drive the server used had solidified over the weekend, and the shaking the CPU endured during the hokeypokey session broke the lubricant’s grip on the hard drive spindle, allowing the drive to spin up and the server to boot.
10 Carding refers to the activities involved in the acquisition, buying, and selling of stolen credit card numbers.
11 For an example of a carding community study, see Holt and Lampke, 2010.
12 See Foucault, 1977 for examples of such discussions.
13 By “effectively,” we mean that there is a reasonably high probability of success, the level of damage that is inflicted is orders of magnitude larger than might otherwise be the case for a physical attack, and the attacker has a reasonably small probability of being apprehended.
14 For a more comprehensive look at the issues of nationalism among Chinese hackers, see Wu, 2007.
15 “Homeland” refers to the country that the respondents indicate they feel is their homeland, regardless of whether or not they are US citizens.
16 The geographical scope of this original research is being expanded to other countries, including Taiwan, Australia, Italy, South Africa, and Russia, with the intent of being able to make cross-national comparisons of the motivators for physical and online attacks by individuals against nation-states.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
