Practice Exam 1
This exam consists of 72 questions that reflect the material covered in this book. These questions represent the types of questions you should expect to see on the Network+ exam; however, they are not intended to match exactly what is on the exam.
Some of the questions require that you deduce the best possible answer. Often, you are asked to identify the best course of action to take in a given situation. You must read the questions carefully and thoroughly before you attempt to answer them. It is strongly recommended that you treat this exam as if it were the actual exam. When you take it, time yourself, read carefully, and answer all the questions to the best of your ability.
The answers appear in “Answers to Practice Exam 1.” Check your answers against those in the “Answers at a Glance,” and then read the explanations in “Answers and Explanations.” You might also want to return to the chapters to review the material associated with any incorrect answers.
1. Which of the following devices operates at the network layer of the OSI model?
![]() A. AP
A. AP
![]() B. Switch
B. Switch
![]() C. Hub
C. Hub
![]() D. Router
D. Router
2. A client on your network has had no problems accessing the wireless network in the past, but recently she moved to a new office. Since the move, she has had only intermittent network access. Which of the following is most likely the cause of the problem?
![]() A. The SSID on the client is misconfigured.
A. The SSID on the client is misconfigured.
![]() B. The client system has moved too far from the AP.
B. The client system has moved too far from the AP.
![]() C. The WEP settings are incorrect.
C. The WEP settings are incorrect.
![]() D. The AP is using an omnidirectional antenna.
D. The AP is using an omnidirectional antenna.
3. You are a network administrator managing a midsized network that uses a NetWare print server, a Windows application server, and a Linux firewall server. One of your servers loses network connectivity. You type ifconfig at the command line to determine whether the server has a valid IP address. Which server has lost connectivity?
![]() A. The firewall server.
A. The firewall server.
![]() B. The print server.
B. The print server.
![]() C. The application server.
C. The application server.
![]() D.
D. ifconfig is not a valid command on any of these platforms.
4. You are managing a network that uses both a UNIX server and a Windows 2000 server. Which of the following protocols can you use to transfer files between the two servers?
![]() A. Telnet
A. Telnet
![]() B. PPP
B. PPP
![]() C. FTP
C. FTP
![]() D. PPTP
D. PPTP
5. A user complains that access to a web page is very slow. What utility can you use to find the bottleneck?
![]() A. ping
A. ping
![]() B. Telnet
B. Telnet
![]() C. tracert
C. tracert
![]() D. nbtstat
D. nbtstat
6. During a busy administrative week, you install a new virus suite in your network of 55 computers, a new RAID array in one of the servers, and a new office suite on 25 of the computer systems. After all the updates, you are experiencing system errors throughout the entire network. What should you do to help isolate the problem?
![]() A. Disable the RAID array.
A. Disable the RAID array.
![]() B. Uninstall the office suite.
B. Uninstall the office suite.
![]() C. Check the virus suite vendor’s website for system patches or service packs.
C. Check the virus suite vendor’s website for system patches or service packs.
![]() D. Reinstall the virus software.
D. Reinstall the virus software.
7. What utility would you use to check the IP configuration on a Windows Vista system?
![]() A. netstat
A. netstat
![]() B. winipcfg
B. winipcfg
![]() C. ping
C. ping
![]() D. ipconfig
D. ipconfig
8. Which of the following services or protocols use SSH technology to provide additional security to communications? (Choose two.)
![]() A. SCP
A. SCP
![]() B. SFTP
B. SFTP
![]() C. SNMP
C. SNMP
![]() D. SMTP
D. SMTP
9. Which of the following backup methods clear the archive bit? (Choose the two best answers.)
![]() A. Differential
A. Differential
![]() B. Sequential
B. Sequential
![]() C. Full
C. Full
![]() D. Incremental
D. Incremental
10. You are troubleshooting a server connectivity problem on your network. A Windows Vista system is having trouble connecting to a Windows Server. Which of the following commands would you use to display per-protocol statistics on the workstation system?
![]() A.
A. arp -a
![]() B.
B. arp -A
![]() C.
C. nbtstat -s
![]() D.
D. nbtstat -S
![]() E.
E. netstat -s
11. You are working as a network administrator on a UNIX system. The system uses dynamic name resolution. What is used to dynamically resolve a hostname on a UNIX server?
![]() A. TCP
A. TCP
![]() B. ARP
B. ARP
![]() C. DNS
C. DNS
![]() D. UDP
D. UDP
12. During the night, one of your servers powers down. Upon reboot, print services do not load. Which of the following would be the first step in the troubleshooting process?
![]() A. Examine the server log files.
A. Examine the server log files.
![]() B. Reboot the server.
B. Reboot the server.
![]() C. Reinstall the printer.
C. Reinstall the printer.
![]() D. Reinstall the printer software.
D. Reinstall the printer software.
13. Which of the following standards uses UTP cable?
![]() A. 100Base-TX
A. 100Base-TX
![]() B. 10Base-FL
B. 10Base-FL
![]() C. 100Base-UX
C. 100Base-UX
![]() D. 10Base2
D. 10Base2
14. Which of the following utilities can be used to view the current protocol connections on a Windows system?
![]() A. ping
A. ping
![]() B. netstat
B. netstat
![]() C. Telnet
C. Telnet
![]() D. tracert
D. tracert
15. Which of the following statements about the 10Mbps IEEE 802.3 network standards is incorrect?
![]() A. There are 10Mbps networking standards for both UTP and fiber-optic cable.
A. There are 10Mbps networking standards for both UTP and fiber-optic cable.
![]() B. The 802.3 10Mbps network standards use a logical bus topology.
B. The 802.3 10Mbps network standards use a logical bus topology.
![]() C. Irrespective of the type of cable, the maximum length of a 10Mbps network segment is 185 meters.
C. Irrespective of the type of cable, the maximum length of a 10Mbps network segment is 185 meters.
![]() D. 10Mbps networking standards use a CSMA/CD media access method.
D. 10Mbps networking standards use a CSMA/CD media access method.
16. Which of the following is a connectionless protocol?
![]() A. TCP
A. TCP
![]() B. THC
B. THC
![]() C. IP
C. IP
![]() D. UDP
D. UDP
17. Which of the following networking standards specifies a maximum segment length of 100 meters?
![]() A. 10Base2
A. 10Base2
![]() B. 10Base-FL
B. 10Base-FL
![]() C. 10Base-YX
C. 10Base-YX
![]() D. 10Base-T
D. 10Base-T
18. Which copper-based medium offers speeds of up to 10Gbps and has a minimum of 250MHz of bandwidth?
![]() A. Category 6b
A. Category 6b
![]() B. Single-mode fiber
B. Single-mode fiber
![]() C. Multimode fiber
C. Multimode fiber
![]() D. Category 6
D. Category 6
19. You are experiencing a problem with a workstation, and you want to ping the local loopback. Which of the following are valid ways to check your local TCP/IP configuration? (Choose the two best answers.)
![]() A.
A. ping host
![]() B.
B. ping localhost
![]() C.
C. ping 127.0.0.1
![]() D.
D. ping 127.0.0.0
20. Which of the following network devices operates at the physical layer of the OSI model?
![]() A. Router
A. Router
![]() B. Hub
B. Hub
![]() C. Bridge
C. Bridge
![]() D. NIC
D. NIC
21. You have been asked to implement a RAID solution on one of your company’s servers. You have two hard disks and two hard disk controllers. Which of the following RAID levels could you implement? (Choose the three best answers.)
![]() A. RAID 0
A. RAID 0
![]() B. RAID 1
B. RAID 1
![]() C. Disk duplexing
C. Disk duplexing
![]() D. RAID 10
D. RAID 10
![]() E. RAID 5
E. RAID 5
22. Which of the following is a Class B IP address?
![]() A. 191.23.21.54
A. 191.23.21.54
![]() B. 125.123.123.2
B. 125.123.123.2
![]() C. 24.67.118.67
C. 24.67.118.67
![]() D. 255.255.255.0
D. 255.255.255.0
23. What utility produces the following output?

![]() A. netstat
A. netstat
![]() B. nbtstat
B. nbtstat
![]() C. ping
C. ping
![]() D.
D. tracert -R
24. You have been called in to troubleshoot a problem with a newly installed email application. Internal users can communicate with each other via email, but neither incoming nor outgoing Internet email is working. You suspect a problem with the port-blocking configuration of the firewall system that protects the Internet connection. Which of the following ports would you allow to cure the problems with the email? (Choose the two best answers.)
![]() A. 20
A. 20
![]() B. 25
B. 25
![]() C. 80
C. 80
![]() D. 110
D. 110
![]() E. 443
E. 443
25. What is the default subnet mask for a Class B network?
![]() A. 255.255.255.224
A. 255.255.255.224
![]() B. 255.255.255.0
B. 255.255.255.0
![]() C. 127.0.0.1
C. 127.0.0.1
![]() D. 255.255.0.0
D. 255.255.0.0
26. At which OSI layer does TCP operate?
![]() A. Network
A. Network
![]() B. Transport
B. Transport
![]() C. Session
C. Session
![]() D. Presentation
D. Presentation
27. What is the basic purpose of a firewall system?
![]() A. It provides a single point of access to the Internet.
A. It provides a single point of access to the Internet.
![]() B. It caches commonly used web pages, thereby reducing the bandwidth demands on an Internet connection.
B. It caches commonly used web pages, thereby reducing the bandwidth demands on an Internet connection.
![]() C. It allows hostnames to be resolved to IP addresses.
C. It allows hostnames to be resolved to IP addresses.
![]() D. It protects one network from another by acting as an intermediary system.
D. It protects one network from another by acting as an intermediary system.
28. Email and FTP work at which layer of the OSI model?
![]() A. Application
A. Application
![]() B. Session
B. Session
![]() C. Presentation
C. Presentation
![]() D. User
D. User
29. What is the IPv6 equivalent of 127.0.0.1? (Choose two.)
![]() A. 0:0:0:0:0:0:0:1
A. 0:0:0:0:0:0:0:1
![]() B. 0:0:0:0:0:0:0:24
B. 0:0:0:0:0:0:0:24
![]() C. ::1
C. ::1
![]() D. ::24
D. ::24
30. While reviewing the security logs for your server, you notice that a user on the Internet has attempted to access your internal mail server. Although it appears that the user’s attempts were unsuccessful, you are very concerned about the possibility that your systems might be compromised. Which of the following solutions are you most likely to implement?
![]() A. A more secure password policy
A. A more secure password policy
![]() B. A firewall system at the connection point to the Internet
B. A firewall system at the connection point to the Internet
![]() C. File-level encryption
C. File-level encryption
![]() D. Kerberos authentication
D. Kerberos authentication
31. Which of the following pieces of information is not likely to be supplied via DHCP?
![]() A. IP address
A. IP address
![]() B. NetBIOS computer name
B. NetBIOS computer name
![]() C. Subnet mask
C. Subnet mask
![]() D. Default gateway
D. Default gateway
32. While troubleshooting a network connectivity problem, you notice that the network card in your system is operating at 10Mbps in half-duplex mode. At what speed is the network link operating?
![]() A. 2.5Mbps
A. 2.5Mbps
![]() B. 5Mbps
B. 5Mbps
![]() C. 10Mbps
C. 10Mbps
![]() D. 11Mbps
D. 11Mbps
33. Which of the following is a valid IPv6 address?
![]() A. 42DE:7E55:63F2:21AA:CBD4:D773
A. 42DE:7E55:63F2:21AA:CBD4:D773
![]() B. 42CD:7E55:63F2:21GA:CBD4:D773:CC21:554F
B. 42CD:7E55:63F2:21GA:CBD4:D773:CC21:554F
![]() C. 42DE:7E55:63F2:21AA
C. 42DE:7E55:63F2:21AA
![]() D. 42DE:7E55:63F2:21AA:CBD4:D773:CC21:554F
D. 42DE:7E55:63F2:21AA:CBD4:D773:CC21:554F
34. While troubleshooting a network connectivity problem on a Windows Server system, you need to view a list of the IP addresses that have been resolved to MAC addresses. What command would you use to do this?
![]() A.
A. arp -a
![]() B.
B. nbtstat -a
![]() C.
C. arp -d
![]() D.
D. arp -s
35. Which of the following statements best describes RAID 5?
![]() A. A RAID 5 array consists of at least two drives. Parity information is written across both drives to provide fault tolerance.
A. A RAID 5 array consists of at least two drives. Parity information is written across both drives to provide fault tolerance.
![]() B. A RAID 5 array consists of at least three drives and distributes parity information across all the drives in the array.
B. A RAID 5 array consists of at least three drives and distributes parity information across all the drives in the array.
![]() C. A RAID 5 array consists of at least three drives and stores the parity information on a single drive.
C. A RAID 5 array consists of at least three drives and stores the parity information on a single drive.
![]() D. A RAID 5 array consists of at least four drives. The first and last drives in the array are used to store parity information.
D. A RAID 5 array consists of at least four drives. The first and last drives in the array are used to store parity information.
36. Which of the following IEEE specifications does CSMA/CD relate to?
![]() A. 802.11b
A. 802.11b
![]() B. 802.2
B. 802.2
![]() C. 802.5
C. 802.5
![]() D. 802.3
D. 802.3
37. While you are troubleshooting a sporadic network connectivity problem on a Windows Vista system, a fellow technician suggests that you run the ping -t command. What is the purpose of this command?
![]() A. It shows the route taken by a packet to reach the destination host.
A. It shows the route taken by a packet to reach the destination host.
![]() B. It shows how long, in seconds, the packet takes to reach the destination.
B. It shows how long, in seconds, the packet takes to reach the destination.
![]() C. It allows the number of ping messages to be specified.
C. It allows the number of ping messages to be specified.
![]() D. It pings the remote host continually until it is stopped.
D. It pings the remote host continually until it is stopped.
38. Which of the following IEEE wireless standards uses the 5GHz RF range?
![]() A. 802.11g
A. 802.11g
![]() B. Infrared
B. Infrared
![]() C. 802.11a
C. 802.11a
![]() D. 802.11b
D. 802.11b
39. What type of physical topology is shown in the following figure?
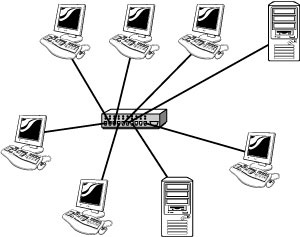
![]() A. Star
A. Star
![]() B. Ring
B. Ring
![]() C. Bus
C. Bus
![]() D. Mesh
D. Mesh
40. A remote user reports that she is having a problem connecting to the corporate network over her DSL connection. She can connect to the Internet and browse web pages, but she can’t connect to the corporate remote-access gateway. Which troubleshooting step would you perform first?
![]() A. Check the corporate remote-access gateway to see if it is running and operating correctly.
A. Check the corporate remote-access gateway to see if it is running and operating correctly.
![]() B. Have the user reboot her system.
B. Have the user reboot her system.
![]() C. Have the user reconfigure the IP address on her system to one of the address ranges used on the internal corporate network, and then try again.
C. Have the user reconfigure the IP address on her system to one of the address ranges used on the internal corporate network, and then try again.
![]() D. Have the user power-cycle the DSL modem and try again.
D. Have the user power-cycle the DSL modem and try again.
41. You have installed a web-based database system on your PC so that you can enter troubleshooting information and retrieve it from any location on the network. Your system’s IP address is 192.168.1.164. You are not overly concerned about security, but as a basic measure, you allocate the web server application a port number of 9191 rather than the default port of 80. Assuming that you are working from another system on the network, what would you type into the address bar of a web browser to access the database?
![]() A. http://192.168.1.164.9191
A. http://192.168.1.164.9191
![]() B. http://192.168.1.164/9191
B. http://192.168.1.164/9191
![]() C. http://192.168.1.164//9191
C. http://192.168.1.164//9191
![]() D. http://192.168.1.164:9191
D. http://192.168.1.164:9191
42. Which of the following IEEE standards has the highest maximum transmission speeds?
![]() A. 802.3ae
A. 802.3ae
![]() B. 802.3xr
B. 802.3xr
![]() C. 802.3z
C. 802.3z
![]() D. 802.3u
D. 802.3u
43. Which of the following best describes the function of PoE??
![]() A. Routes data to PPP ports
A. Routes data to PPP ports
![]() B. Provides power over twisted pair cable
B. Provides power over twisted pair cable
![]() C. Increases speeds of twisted pair cable
C. Increases speeds of twisted pair cable
![]() D. Trunks switch ports
D. Trunks switch ports
44. Which of the following is the IPv6 equivalent to IPv4 automatic 169.254.0.0 APIPA addressing?
![]() A. Link local
A. Link local
![]() B. Site local
B. Site local
![]() C. Global address
C. Global address
![]() D. Unicast
D. Unicast
45. You are tasked with specifying a way to connect two buildings across a parking lot. The distance between the two buildings is 78 meters. An underground wiring duct exists between the two buildings, although there are concerns about using it, because it also houses high-voltage electrical cables. The budget for the project is very tight, but your manager still wants you to specify the most suitable solution. Which of the following cable types would you recommend?
![]() A. Fiber-optic
A. Fiber-optic
![]() B. UTP
B. UTP
![]() C. Thin coax
C. Thin coax
![]() D. STP
D. STP
46. Which of the address types sends data to all systems on a subnet or network instead of single hosts?
![]() A. Multicast
A. Multicast
![]() B. Unicast
B. Unicast
![]() C. Broadcast
C. Broadcast
![]() D. Anycast
D. Anycast
47. A user informs you that she can’t access the Internet from her system. When you visit her, you run the ipconfig /all utility and see the following information. What is the most likely reason the user is having problems accessing the Internet?
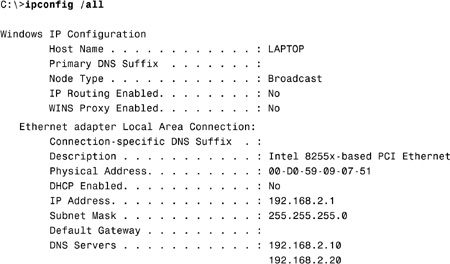
![]() A. The system is on a different subnet than the DNS servers.
A. The system is on a different subnet than the DNS servers.
![]() B. DHCP is not enabled.
B. DHCP is not enabled.
![]() C. The subnet mask is incorrect.
C. The subnet mask is incorrect.
![]() D. The default gateway setting is not configured.
D. The default gateway setting is not configured.
48. Your ISP account manager suggests that it might be appropriate for you to install a DNS server internally. Which of the following functions does the DNS server perform?
![]() A. It performs network address translation services.
A. It performs network address translation services.
![]() B. It streamlines the resolution of NetBIOS names to IP addresses.
B. It streamlines the resolution of NetBIOS names to IP addresses.
![]() C. It allows some hostname-to-IP address resolutions to occur internally.
C. It allows some hostname-to-IP address resolutions to occur internally.
![]() D. It allows users to retrieve Internet web pages more quickly.
D. It allows users to retrieve Internet web pages more quickly.
49. Which of the following is not one of the private address ranges?
![]() A. 192.168.x.x
A. 192.168.x.x
![]() B. 10.x.x.x
B. 10.x.x.x
![]() C. 172.16.x.x
C. 172.16.x.x
![]() D. 224.181.x.x
D. 224.181.x.x
50. Which of the following is a distance-vector routing protocol used on TCP/IP networks?
![]() A. ARP
A. ARP
![]() B. NLSP
B. NLSP
![]() C. OSPF
C. OSPF
![]() D. RIP
D. RIP
51. If you contacted IANA, what would you most likely be trying to do?
![]() A. Get a new telephone number
A. Get a new telephone number
![]() B. Get an IP address to connect a system to a public network
B. Get an IP address to connect a system to a public network
![]() C. Get an Internet domain name reassigned
C. Get an Internet domain name reassigned
![]() D. Get an IP address to connect a system to a private network
D. Get an IP address to connect a system to a private network
52. Which of the following technologies can be implemented on a switch to create multiple separate logical networks?
![]() A. Proxy
A. Proxy
![]() B. Subnet masking
B. Subnet masking
![]() C. NAS
C. NAS
![]() D. VLAN
D. VLAN
53. Which of the following protocols is responsible for network addressing?
![]() A. IP
A. IP
![]() B. HTTP
B. HTTP
![]() C. SSH
C. SSH
![]() D. TCP
D. TCP
54. You are upgrading the antenna on your wireless network. You need to purchase an antenna that provides a 360-degree dispersed wave pattern. Which of the following antenna types would you select?
![]() A. Omni-dispersed antenna
A. Omni-dispersed antenna
![]() B. Directional-dispersed antenna
B. Directional-dispersed antenna
![]() C. Directional antenna
C. Directional antenna
![]() D. Omnidirectional antenna
D. Omnidirectional antenna
55. What protocol is used by systems within a multicast group to communicate registration information with each other?
![]() A. ICMP
A. ICMP
![]() B. IGMP
B. IGMP
![]() C. NNTP
C. NNTP
![]() D. NTP
D. NTP
56. Which of the following connectors would you use when working with fiber-optic cable? (Choose the two best answers.)
![]() A. RJ-11
A. RJ-11
![]() B. SC
B. SC
![]() C. RJ-45
C. RJ-45
![]() D. ST
D. ST
![]() E. BNC
E. BNC
57. Your manager asks you to procure a cable with a Type A connector on one end and a Type B connector on the other. What kind of interface are you most likely to be dealing with?
![]() A. FireWire
A. FireWire
![]() B. USB
B. USB
![]() C. RJ-11
C. RJ-11
![]() D. Fiber-optic
D. Fiber-optic
58. Which of the following wireless security protocols uses TKIP?
![]() A. WEP-open
A. WEP-open
![]() B. WEP-shared
B. WEP-shared
![]() C. WPA
C. WPA
![]() D. WAP-shared
D. WAP-shared
59. You have enabled HTTPS because of concerns about the security of your web server application, which runs on a web server system in the DMZ of your corporate network. However, remote users are now unable to connect to the application. Which of the following is the most likely reason for the problem?
![]() A. Port 80 is being blocked on the corporate firewall.
A. Port 80 is being blocked on the corporate firewall.
![]() B. Port 443 is being blocked on the corporate firewall.
B. Port 443 is being blocked on the corporate firewall.
![]() C. Remote users need to enable HTTPS support in their web browsers.
C. Remote users need to enable HTTPS support in their web browsers.
![]() D. Port 110 is being blocked on the corporate firewall.
D. Port 110 is being blocked on the corporate firewall.
60. Which of the following is a valid Class A IP address?
![]() A. 124.254.254.254
A. 124.254.254.254
![]() B. 127.0.0.1
B. 127.0.0.1
![]() C. 128.16.200.12
C. 128.16.200.12
![]() D. 131.17.25.200
D. 131.17.25.200
61. Which of the following wireless technologies provide limited transmission distance and are used primarily for personal area networking and cable replacement? (Choose two.)
![]() A. IrDA
A. IrDA
![]() B. 802.11a
B. 802.11a
![]() C. Bluetooth
C. Bluetooth
![]() D. Ethernet wireless
D. Ethernet wireless
62. You are the administrator for a network with two Windows 2000 Server systems and 40 Windows XP Professional systems. One morning, three users call to report that they are having problems accessing the Windows servers. Upon investigation, you determine that the DHCP server application running on one of the servers has crashed and that the three systems are using addresses assigned via APIPA. All other systems, which were started before the DHCP server application crashed, are functioning correctly. Which of the following statements about the situation are correct? (Choose two.)
![]() A. Systems with an APIPA assigned address will be able to communicate with each other.
A. Systems with an APIPA assigned address will be able to communicate with each other.
![]() B. Systems with an APIPA assigned address will be able to talk to other systems that have an IP address from the DHCP server.
B. Systems with an APIPA assigned address will be able to talk to other systems that have an IP address from the DHCP server.
![]() C. Systems with an APIPA assigned address will not be able to access the Internet.
C. Systems with an APIPA assigned address will not be able to access the Internet.
![]() D. Each system with an APIPA assigned address will not be able to communicate with any other system on the network.
D. Each system with an APIPA assigned address will not be able to communicate with any other system on the network.
63. Which of the following protocols are not part of the TCP/IP protocol suite? (Choose all that apply.)
![]() A. AFP
A. AFP
![]() B. FTP
B. FTP
![]() C. DHCP
C. DHCP
![]() D. HTTP
D. HTTP
![]() E. DNS
E. DNS
64. You are attempting to configure a client’s email program. The user can receive mail but is unable to send any. In the mail server configuration screen of the mail application, you notice that the Type of Outgoing Mail Server field is blank. This explains why the client is unable to send mail. Which of the following protocols are you most likely to enter as a value in the Type of Outgoing Mail Server field?
![]() A. NMP
A. NMP
![]() B. POP3
B. POP3
![]() C. SMTP
C. SMTP
![]() D. IMAP
D. IMAP
65. Which of the following is a configurable client identification setting used to differentiate one WLAN from another?
![]() A. SID
A. SID
![]() B. WEP
B. WEP
![]() C. SSID
C. SSID
![]() D. Wireless channel
D. Wireless channel
66. Which of the following is a valid MAC address?
![]() A. 00:D0:59:09:07:51
A. 00:D0:59:09:07:51
![]() B. 00:D0:59
B. 00:D0:59
![]() C. 192.168.2.1
C. 192.168.2.1
![]() D. 00FE:56FE:230F:CDA2:00EB:32EC
D. 00FE:56FE:230F:CDA2:00EB:32EC
![]() E. 00:DG:59:09:07:51
E. 00:DG:59:09:07:51
67. Which of the following best describes 802.1x?
![]() A. Port-based access control
A. Port-based access control
![]() B. A wireless standard specifying 11Mbps data transfer
B. A wireless standard specifying 11Mbps data transfer
![]() C. A wireless standard specifying 54Mbps data transfer
C. A wireless standard specifying 54Mbps data transfer
![]() D. Integrity-based access control
D. Integrity-based access control
68. Which of the following is not a commonly implemented feature of a firewall system?
![]() A. NAT
A. NAT
![]() B. Packet filtering
B. Packet filtering
![]() C. Proxy
C. Proxy
![]() D. NAS
D. NAS
69. Which command produces the following output?
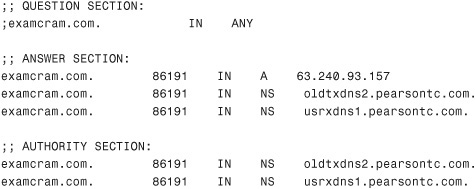
![]() A.
A. nslookup
![]() B.
B. nbtstat
![]() C.
C. dig
![]() D.
D. netstat
70. When a system running TCP/IP receives a data packet, which of the following does it use to determine which service to forward the packet to?
![]() A. Port number
A. Port number
![]() B. Packet ID number
B. Packet ID number
![]() C. Data IP number
C. Data IP number
![]() D. IP protocol service type
D. IP protocol service type
71. What command would generate the following output?

![]() A.
A. ipconfig
![]() B.
B. netstat
![]() C.
C. ping
![]() D.
D. tracert
72. Which layer of the OSI model is responsible for placing the signal on the network medium?
![]() A. Physical
A. Physical
![]() B. Data link
B. Data link
![]() C. MAC
C. MAC
![]() D. LLC
D. LLC
Answers to Practice Exam 1
Answers at a Glance
1. D
2. B
3. A
4. C
5. C
6. C
7. D
8. A, B
9. C, D
10. E
11. C
12. A
13. A
14. B
15. C
16. D
17. D
18. D
19. B, C
20. B
21. A, B, C
22. A
23. A
24. B, D
25. D
26. B
27. D
28. A
29. A, C
30. B
31. B
32. C
33. D
34. A
35. B
36. D
37. D
38. C
39. A
40. A
41. D
42. A
43. B
44. A
45. A
46. C
47. D
48. C
49. D
50. D
51. B
52. D
53. A
54. D
55. B
56. B, D
57. B
58. C
59. B
60. A
61. A, C
62. A, C
63. A
64. C
65. C
66. A
67. A
68. D
69. C
70. A
71. D
72. A
Answers and Explanations
Question 1
D. Of the devices listed, only a router operates at the network layer of the OSI model. Answers A and B are incorrect because an AP and a switch are both considered data link layer devices. Answer C is incorrect because a hub is considered a physical layer device.
Question 2
B. A wireless AP has a limited range in which it can send and receive data signals. When a client system moves out of this range, client network access will either fail or be inconsistent. Answers A and C are incorrect because a misconfigured SSID or incompatible WEP settings would prevent communication between the wireless AP and client. Answer D is incorrect because an omnidirectional antenna is the type of antenna that would be used in this setting.
Question 3
A. The ifconfig command is used on a Linux system to determine the system’s IP configuration. Answer B is incorrect because with NetWare, you use the
config command to obtain information about network addresses. Answer C is incorrect because on a Windows system, the ipconfig command is used to view the networking configuration, including the IP address. Answer D is incorrect because the ifconfig command can be used on UNIX/Linux platforms to view the networking configuration.
Question 4
C. FTP can be used to transfer files between Windows and UNIX systems. FTP is part of the TCP/IP protocol suite and is platform-independent. The Telnet utility is used to open a virtual terminal session on a remote host (answer A). PPP (answer B) is used to establish communications over a serial link. PPTP (answer D) is used to establish a secure link over a public network such as the Internet.
Question 5
C. tracert is a Windows command that can be used to display the full path between two systems, including the number of hops between the systems. The ping utility (answer A) can be used to test connectivity between two devices, but it only reports the time taken for the round-trip; it does not give information about how long it takes to complete each hop in the route. The Telnet utility (answer B) is used to open a virtual terminal session on a remote host. The nbtstat command (answer D) is used to view statistical information about a system’s NetBIOS status.
Question 6
C. Because the system errors are over the entire network, it is likely that the cause of the problem lies with the virus suite, because it is installed on all computers. To troubleshoot such a problem, it would be a good idea to check for patches or updates on the vendor’s website. A problem with a RAID array (answer A) would affect only the server on which it is installed, not the entire network. Because the office suite (answer B) was installed on only some of the systems, it can be eliminated as a problem, because all the systems are affected. The virus software (answer D) appears to be the cause of the problem, but reinstalling it is unlikely to help.
Question 7
D. The ipconfig utility can be used to view the TCP/IP configuration on a Windows 2000, Windows XP, Windows Vista, or Windows Server 2003 system. None of these operating systems support the graphical winipcfg utility (answer B). The netstat utility (answer A) is used to view protocol statistics information. The ping utility (answer C) is used to test the connectivity between two systems on a TCP/IP network.
Question 8
A, B. Secure Shell (SSH) technology is used by both Secure Copy Protocol (SCP) and Secure File Transfer Protocol (SFTP). Answer C and D are incorrect because Simple Network Management Protocol (SNMP) and Simple Mail Transfer Protocol (SMTP) do not use SSH technology for additional security.
Question 9
C, D. Both the full and incremental backup methods clear the archive bit to indicate which data does and does not need to be backed up. In a differential backup (answer A), the archive bit is not cleared. Sequential (answer B) is not a type of backup.
Question 10
E. The netstat -s command can be used to display per-protocol statistics. The
arp command (answers A and B) is used to view a list of the IP address-to-MAC address resolutions performed by the system. The nbtstat utility (answers C and D) is used to view protocol statistics for the NetBIOS protocol.
Question 11
C. DNS is a platform-independent protocol used to resolve hostnames to IP addresses. TCP (answer A) is a network-layer connection-oriented protocol. ARP (answer B) resolves IP addresses to MAC addresses. The UDP protocol (answer D) is a connectionless protocol and is part of the TCP/IP protocol suite.
Question 12
A. In this scenario, your first step is to gather information by examining the server log files. When you have that information, you can proceed with the rest of the troubleshooting process. Rebooting the server (answer B) is unlikely to cure the problem. Before you reinstall the printer (answer C) or printer software (answer D), you should examine the log files to see if they report any problems.
Question 13
A. The 100Base-TX standard specifies twisted-pair UTP cable. Answer B is incorrect because 10Base-FL is a fiber standard and uses fiber-optic cable. There is no standard called 100Base-UX (answer C). 10Base2 (answer D) is an Ethernet networking standard that specifies thin coaxial cable.
Question 14
B. The netstat -a command can be used to display the current connections and listening ports. The ping utility (answer A) is used to test connectivity between two devices on a TCP/IP network. Telnet (answer C) is an application-level protocol that allows a virtual terminal session on a remote host. The tracert utility (answer D) allows a path to be traced between two hosts.
Question 15
C. The various 10Mbps 802.3 networking standards have different maximum cable lengths. With 10Base-FL, a segment can be up to 2,000 meters. Using thin coaxial cabling, the 10Base2 standard specifies a maximum segment length of 185 meters. 10Mbps implementations of Ethernet on UTP are limited to 100 meters. All Ethernet standards use a Collision Sense Multiple Access/Collision Detection media access method. The 10Mbps 802.3 standards use a logical bus topology, although they can use physical star or physical bus topology.
Question 16
D. UDP is a connectionless protocol. TCP (answer A) is a connection-oriented protocol. IP (answer C) is also a connection-oriented protocol. THC (answer B) is not a valid protocol.
Question 17
D. 10Base-T has a maximum segment length of 100 meters. The maximum length of a 10Base2 segment (answer A) is 185 meters. The maximum length of a 10Base-FL segment (answer B) is 2,000 meters. Answer C is not a valid networking standard.
Question 18
D. Category 6 high-performance UTP cable can transmit data up to 10Gbps. Category 6 has a minimum of 250MHz of bandwidth and specifies cable lengths of up to 100 meters, with 10/100/1000Mbps transfer, along with 10Gbps over shorter distances. Answers B and C are incorrect because they are not copper-based media, but fiber. Answer A is not a valid standard.
Question 19
B, C. To verify the local IP configuration, you can either ping the localhost or use the IP address 127.0.0.1. The default hostname for a system is localhost, not host, which means that answer A is incorrect. Answer D is incorrect because this is the network address for the Class A loopback address, not a valid node loopback address.
Question 20
B. A network hub operates at the physical layer of the OSI model. A router operates at the network layer of the OSI model. A bridge operates at the data link layer of the OSI model. A NIC operates at the data link layer of the OSI model.
Question 21
A, B, C. With two hard disks and two controllers, you can implement RAID 0, RAID 1, and disk duplexing. RAID 5 (disk striping with parity; answer E) requires a minimum of three disks to be implemented. RAID 10 (answer D) is a combination of RAID 1 (disk mirroring) and RAID 0 (disk striping). RAID 10 requires a minimum of four disks.
Question 22
A. The first octet of a Class B address must be in the range 128 to 191. Answers B and C represent Class A addresses, which run from 1 to 126. Answer D is not a valid IP address; it is the subnet mask for a Class C network.
Question 23
A. The netstat utility can be used to display protocol statistics and TCP/IP network connections. The nbtstat utility (answer B) shows statistical information about the NetBIOS over TCP/IP connections. The ping utility (answer C) is used to test the connectivity between two devices on a TCP/IP network. The tracert utility (answer D) traces the path between two hosts on a TCP/IP network.
Question 24
B, D. TCP/IP port 25 is used by SMTP. TCP/IP port 110 is used by POP3. Because SMTP is used to send mail and POP3 is used to retrieve mail, ports 25 and 110 would need to be allowed for incoming and outgoing Internet email. TCP/IP port 20 (answer A) is used by FTP. TCP/IP port 80 (answer C) is used by HTTP. TCP/IP port 443 (answer E) is used by HTTPS.
Question 25
D. The default subnet mask for a Class B network is 255.255.0.0. Answer A is incorrect because it is not the default subnet mask for a Class B network. Answer B is not the default subnet mask for a Class B network; it is the default subnet mask for a Class C network. Answer C is the local loopback address.
Question 26
B. TCP operates at the transport layer of the OSI model. TCP does not operate at the network, session, or presentation layers.
Question 27
D. The purpose of a firewall system is to protect one network from another. One of the most common places to use a firewall is to protect a private network from a public one such as the Internet. Answer A is incorrect because although a firewall can provide a single point of access, that is not its primary purpose. Answer B more accurately describes the function of a proxy server. Answer C describes the function of a DNS server.
Question 28
A. Both email and FTP work at the application layer of the OSI model. Email and FTP are application-layer protocols, not session or presentation layer protocols. User (answer D) is not a layer of the OSI model.
Question 29
A, C. The IPv4 address 127.0.0.1 is reserved as the loopback address. IPv6 has the same reservation. IPv6 address 0:0:0:0:0:0:0:1 is reserved as the loopback address. The address can also be shown using the :: notation with the 0s removed, resulting in ::1.
Question 30
B. To prevent unauthorized access to a private network from the Internet, you can use a firewall server to restrict outside access. Implementing a more secure password policy (answer A) is a good idea, but it is not the best choice. Implementing a file-level encryption system (answer C) is a good idea, but it is not the best choice. Kerberos (answer D) is an authentication system, not a method to prevent unauthorized access to the system.
Question 31
B. The NetBIOS computer name is not supplied to client systems by a DHCP server.
Question 32
C. Because the NIC is functioning at half-duplex 10Mbps, the transfer rate is 10Mbps.
Question 33
D. IPv6 uses a 128-bit address, which is expressed as eight octet pairs in hexadecimal format, separated by colons. Because it is hexadecimal, only numbers and the letters A through F can be used.
Question 34
A. The arp -a command is used to display the IP addresses that have been resolved to MAC addresses. The nbtstat command (answer B) is used to view protocol statistics for NetBIOS connections. arp -d (answer C) is used to delete entries in the ARP cache. The arp -s command (answer D) allows you to add static entries to the ARP cache.
Question 35
B. A RAID 5 array consists of at least three hard disks, and it stripes parity information across all disks in the array. Answer A is incorrect because RAID 5 (disk striping with parity) requires at least three drives. Answer C is incorrect because the parity information is stored in a stripe across all three drives in the array, not on a single drive. RAID 5 requires only three drives, which makes answer D incorrect.
Question 36
D. CSMA/CD relates to the IEEE specification 802.3. The 802.11b standard (answer A) describes wireless LAN networking. The 802.2 standard (answer B) defines the media access methods for various networking standards. The 802.5 standard (answer C) defines token ring networking.
Question 37
D. The ping -t command is used to send continuous ping requests to a remote system. The ping request continues until it is stopped manually. The traceroute utility (answer A) shows the route taken by a packet to reach the destination host. The ping command (answer B) shows how long a packet takes to complete the round-trip from the host to the destination. Answer C is incorrect because the ping command with the -n switch allows the number of ping messages to be specified.
Question 38
C. The IEEE 802.11a wireless standard specifies 5GHz as the RF transmission range. Answers A and D are incorrect because the IEEE wireless standards 802.11b/g both use the 2.4GHz RF range. Answer B, infrared wireless transmissions, also use the 2.4GHz RF.
Question 39
A. The figure shows a star topology.
Question 40
A. In this scenario, you would first check the remote-access gateway to see if it is running and operating correctly. Because the user can browse web pages, this is not a connectivity problem. Answer B is incorrect because, although rebooting the system might help, the system appears to be working correctly, so rebooting it is unlikely to cure the problem. The IP address configuration appears to be working, because the user can access web pages, so answer C is incorrect. The Internet connection appears to be working, so cycling the power on the DSL modem, as described in answer D, is unlikely to help.
Question 41
D. To specify a TCP/IP port other than the default of 80, simply append the port number to the end of the address, using a colon (:) to separate the two.
Question 42
A. The IEEE 802.3ae standard defines 10Gbps networking standards such as 10Gbase-LR and 10Gbase-SR. Answer B is incorrect because there is no IEEE 802.3xr standard. Answer C, 802.3z, defines gigabit Ethernet standards such as 1000Base-LX and 1000Base-SX. 802.3u (answer D) defines fast Ethernet standards such as 100Base-TX and 100Base-FX.
Question 43
B. The purpose of Power over Ethernet (PoE) is to allow electrical power to be transmitted over twisted pair Ethernet cable. The power is transferred, along with data, to provide power to remote devices. These devices may include remote switches, wireless access points, Voice Over IP (VoIP) equipment, and more.
Question 44
A. IPv6 link-local addresses are automatically configured on all interfaces in an IPv6-based network. This automatic configuration is equivalent to the 169.254.0.0 automatically assigned IPv4 addressing using APIPA. The prefix used for a link-local address is fe80::.
Question 45
A. Fiber-optic cable provides the most resistance to EMI and therefore is often used in environments that have a risk of interference. Although it is inexpensive, UTP cable (answer B) and thin coax (answer C) have very low resistance to EMI; therefore, they should not be run near high-voltage electric cables. STP (answer D) has a good level of resistance to EMI, but it is still not as resistant as fiber-optic. Not factoring in the cost, fiber-optic is the most suitable solution.
Question 46
C. IPv4 broadcast addresses are IP address that can target all systems on a subnet or network instead of single hosts. In other words, a broadcast message goes to everyone on the network or to a specific network segment. Answer A, multicast, sends data to an entire identified group of network users. Answer B, unicast, sends data to a specific system. Answer D is incorrect because anycast is not a valid networking term.
Question 47
D. The most likely cause of the problem is that the default gateway is not configured. Answer A is incorrect because from the output it appears that the DNS servers are on the same subnet as this system. Answer B does not apply because addressing is configured statically, so there is no DHCP service. This is not a problem, however. Answer C is incorrect because the subnet mask is the correct default subnet mask for a Class C network.
Question 48
C. DNS allows hostname resolutions to occur internally. In most cases, companies use a DNS server provided by the ISP. In some cases, however, it might be appropriate to have a DNS server on the internal network. Answer A is incorrect because NAT is normally a function of firewall or proxy servers. Answer B describes the purpose of a WINS server. Answer D describes the function of a proxy server.
Question 49
D. Private address ranges are designed for use on private networks. The ranges are 10.x.x.x, 172.16.x.x to 172.32.x.x, and 192.168.x.x. Therefore, answers A, B, and C are all valid private IP address ranges.
Question 50
D. RIP is a distance-vector routing protocol used on TCP/IP networks. Answer A is incorrect because ARP is a component of the TCP/IP protocol suite used to resolve MAC addresses to IP addresses. Answer B is incorrect because NLSP is a link-state routing protocol used on IPX networks. Answer C is incorrect because OSPF is a link-state routing protocol used on TCP/IP networks.
Question 51
B. The Internet Assigned Numbers Authority (IANA) is responsible for assigning IP addresses for systems on public networks—specifically, the Internet. Answer C is incorrect because domain names are administered by domain registry organizations. Answer D is incorrect because you don’t need to apply for a network address for use on a private network.
Question 52
D. A VLAN is implemented on a switch to create multiple separate networks. A proxy server (answer A) is used to control access to the Internet. Subnet masking (answer B) is not a valid method of creating separate networks. NAS (answer C) describes storage devices that are attached directly to the network medium.
Question 53
A. IP is responsible for network addressing. SSH, HTTP, and TCP are not responsible for network addressing.
Question 54
D. In a typical configuration, a wireless antenna can be either omnidirectional or directional. An omnidirectional antenna provides a 360-degree dispersed wave pattern. This provides an even signal in all directions. Directional antennas are designed to focus the signal in a particular direction. Omni-dispersed and directional-dispersed are not valid types of antennas.
Question 55
B. Internet Group Multicast Protocol (IGMP) is used by systems within the same multicast group to communicate registration information. Internet Control Message Protocol (ICMP) works with IP to provide error checking and reporting functionality on a network. Network News Transfer Protocol (NNTP) is used to access Internet newsgroups. Network Time Protocol (NTP) is used to synchronize system time with Internet servers.
Question 56
B, D. Fiber-optic cable can use either SC- or ST-type connectors. RJ-11 connectors (answer A) are associated with telephone cable, RJ-45 connectors (answer C) are associated with UTP cable, and BNC connectors (answer E) are associated with thin coaxial cable.
Question 57
B. USB interfaces have a number of connectors associated with them, but the most common are called Type A and Type B. FireWire interfaces use either a four-pin or six-pin connector; neither is referred to as Type A or Type B. RJ-11 is a type of connector associated with phone system wiring. Fiber-optic interfaces use a wide range of connectors, but none are called Type A or Type B.
Question 58
C. The WPA wireless security protocol uses TKIP (Temporal Key Integrity Protocol), which scrambles encryption keys using a hashing algorithm. Then the keys are issued an integrity check to verify that they have not been modified or tampered with during transit. Answers A and B are incorrect because TKIP encryption is not used with WEP. Answer D is not a valid encryption protocol.
Question 59
B. The most likely explanation is that port 443, the HTTPS default port, is being blocked by a corporate firewall. Port 80 (answer A) is used by HTTP. All modern web browsers support HTTPS automatically; therefore, answer C is incorrect. Port 110 (answer D) is used by POP3.
Question 60
A. Class A subnets use the range 1 to 126 for the value of the first octet. Answer B is the loopback address, which allows the IP stack functionality to be tested. Answers C and D are both addresses in the Class B range (128 to 191).
Question 61
A, C. Infrared (IrDA) and Bluetooth are wireless technologies commonly used to create personal area networks. They remove the need for peripheral cables. 802.11a is a wireless standard used for LAN-based networking and is not designed for attaching peripheral devices. Ethernet wireless is not a wireless standard.
Question 62
A, C. Systems that have APIPA-assigned addresses can talk to each other (answer A), but not with any other systems (answer B). Systems with APIPA-assigned addresses cannot access the Internet (answer C), because the APIPA-assigned information does not include default gateway information. Therefore, communication is limited to the local network. Answer D is incorrect because the systems with APIPA addresses can talk to each other, even though they cannot communicate with any other systems.
Question 63
A. Of the protocols listed, only AFP (AppleTalk Filing Protocol) is not part of the TCP/IP protocol suite. Answers B, C, D, and E are all used in TCP/IP networks.
Question 64
C. SMTP is used to send email and is a protocol within the TCP/IP protocol suite. Answer A is not a valid protocol. Answers B and D are incorrect because POP3 and IMAP are email retrieval protocols, not protocols for sending email.
Question 65
C. The Service Set Identifier (SSID) is a unique identifier sent over the WLAN that acts as a simple password used when a client attempts to access an access point. The SSID is used to differentiate between networks; therefore, the client system and the AP must use the same SSID. WEP represents a form of wireless security, and the wireless channel is the band of frequency used for the wireless communication.
Question 66
A. The MAC address is a 6-byte address expressed in six pairs of hexadecimal values. Because it is hexadecimal, only the letters A through F and numbers can be used. Answer B is incorrect because MAC addresses are expressed as six hexadecimal pairs. Answer C is an example of an IPv4 address. Answer D is an example of an IPv6 address. Answer E is incorrect because MAC addresses are expressed in hexadecimal; therefore, only the letters A through F and numbers can be used.
Question 67
A. 802.1x is an IEEE standard specifying port-based network access control. Port-based network access control uses the physical characteristics of a switched local area network (LAN) infrastructure to authenticate devices attached to a LAN port and to prevent access to that port in cases where the authentication process fails.
Question 68
D. A firewall can provide several services to the network, including NAT, proxy services, and packet filtering. NAS is not a function of a firewall server; the acronym stands for network attached storage.
Question 69
C. The output shown is from the dig command. dig is used on UNIX and Linux systems to run manual DNS lookups. The nslookup command (answer A) also performs this function, but it produces different output. The nbtstat command (answer B) provides information on NetBIOS name resolutions. The netstat command (answer D) shows what TCP/IP protocol connections have been established on a system. These commands produce different output from dig.
Question 70
A. The service for which a data packet is destined is determined by the port number to which it is sent.
Question 71
D. The output displayed in this question is from the Windows tracert utility. The utilities in answers A, B, and C produce different output from what is shown.
Question 72
A. The physical layer of the OSI seven-layer model is responsible for placing the signal on the network medium. The data link layer (answer B) is responsible for physical addressing and media access. MAC and LLC (answers C and D) are sublayers of the data link layer.
