Chapter 8
Connecting to Wi-Fi Networks
In This Chapter
![]() Connecting to Wi-Fi networks from iPhones, iPads, and Android devices
Connecting to Wi-Fi networks from iPhones, iPads, and Android devices
![]() Configuring Wi-Fi settings and policies for mobile devices
Configuring Wi-Fi settings and policies for mobile devices
Mobile devices such as iPhones, iPads, and those running the Android operating system have sophisticated Wi-Fi capabilities, allowing them to connect to public and private networks for Internet access. Device users can connect to networks at public places, such as coffee shops, airports, and hotels, and to private networks, including corporate and home networks.
This chapter explores the world of Wi-Fi on mobile devices and describes ways users can connect to networks and how you can manage policies and settings for Wi-Fi access. We also discuss the risks of users connecting to certain public Wi-Fi networks, especially those that are open and allow any device or user to connect to them. Finally, we look at options for securing your corporate Wi-Fi network.
What’s Wi-Fi, and Why Bother?
Smartphones today have access to the wireless carrier’s data network, enabling them to send and receive data such as e-mails and text messages. Wireless carriers have built elaborate networks to handle the load of millions of smartphone users. In many cases, these are 3G (or third-generation) networks, and some carriers have even built more sophisticated 4G or LTE (Long Term Evolution) networks. 4G or LTE networks have greater capacity and bandwidth than the older third-generation networks.
In many cases, however, such networks have inadequate strength, causing devices to either lose network coverage or experience slow network access. Most people have experienced network outages of this sort, especially in crowded cities or downtown locations where many devices compete with one another for access to the carrier’s network.
Enter Wi-Fi technology, which is designed to connect computers or other devices within short distances without needing cables. Wi-Fi allows the connection of multiple devices into a single network, all of which can then browse the web, send e-mail, and connect to the Internet. In your organization, you can create a corporate Wi-Fi network to which employees connect their various devices, including laptop computers, smartphones, and tablets.
Wi-Fi networks provide a sigh of relief to smartphone users in counteracting the unpredictability of carrier networks. Wi-Fi networks provide Internet access in various locations, such as hotels, airports, and coffee shops. Users at these locations can get off their 3G networks and connect to a typically more stable, and often faster, Wi-Fi network. Many Wi-Fi networks are public or insecure, meaning that any device or user can connect to them. Insecure networks come with some risk, exposing users to the possibility that their data (such as e-mail or web pages) could be read by other people who are connected to the same network.
Which Wi-Fi Networks Should Users Connect To?
Not all Wi-Fi networks are secure. Some are open networks, requiring no authentication of the devices or the users connecting to them. These open networks may be deployed at airports or coffee shops. All it takes for a user to connect to such a network is to detect the open network by name (or Service Set Identified [SSID]) and connect to it. No password is required, thereby letting anyone connect to the network.
Wi-Fi networks can be secured by requiring a password or using other techniques. Such networks are relatively more secure to connect to. But depending on the nature of security deployed in the Wi-Fi policy, these networks can also be snooped on. In the following sections, we look at the two broad categories of Wi-Fi networks to which users can connect their smartphones and tablets.
Open or insecure networks
Open networks can be joined by any user and from any device without the user needing to enter a password. These networks are typically the riskiest for users to connect to, because the data transmitted and received by users can be viewed by other users connected to the same network. People conversant with networking technology can read traffic over the network sent by other users from laptop computers, tablets, or smartphones.
Traffic that is easy to snoop on includes open or unsecured browsing traffic, such as visiting a website that does not require SSL encryption. Unfortunately, many popular websites like Facebook, Yahoo!, and Twitter do not need SSL encryption, so when users browse these sites over an open Wi-Fi network, they’re vulnerable to being snooped on.
Websites or applications that require SSL encryption are more secure from being snooped on by users on the same Wi-Fi network. While browsing to any website, users can easily see if SSL encryption is turned on. It usually appears as a padlock on the browser itself, sometimes along with the name of the server the user is connecting to. When users browse to websites that do not need SSL encryption, their information is visible and readable by others if they are on an open Wi-Fi network.
Encrypted Wi-Fi networks
Wi-Fi networks can be secured using techniques called WEP (Wired Equivalent Privacy), WPA (Wi-Fi Protected Access), or WPA2 (a more recent form of WPA). Among these three, WEP employs the weakest encryption, because it relies on a preshared password key, which is used to encrypt network traffic. WEP-secured networks are more secure than open networks, but anyone who has successfully connected to a WEP-encrypted network can view traffic generated by other users or devices on the same network.
WPA and WPA2 employ stronger encryption than WEP. WPA2 uses stronger encryption and is more recent than WPA. WPA2 comes in two flavors: WPA2-enterprise and WPA2-personal. For private networks, such as home networks, WPA2-personal is the ideal security to deploy. For corporate Wi-Fi networks, WPA2-enterprise is the best possible security to deploy.
VPN on a Wi-Fi network
If your users do happen to connect to open an Wi-Fi network, make sure they use VPN on their devices to connect to your corporate VPN gateway. VPN results in a secure tunnel being built from the device to the VPN gateway, through which all traffic is encrypted and invisible to network snoopers. VPN comes in IPSec and SSL flavors, both of which have their pros and cons. Most laptop PCs, Apple Macs, smartphones, and tablets include VPN support for leading networking vendors.
Chapter 7 describes VPN in greater detail and runs down the corporate options to use VPN on various devices.
Wi-Fi Connections from Mobile Devices
In this section, we look at how users can connect to Wi-Fi networks from their mobile devices. We focus on the most popular types of devices available: Apple iOS, Google Android, and BlackBerry. We run down some techniques you may want to use when instructing your corporate users. We include signs that users need to watch out for, such as the absence of security on a Wi-Fi network. Make sure that users are wary and cautious of connecting to open networks.
Apple iPhones, iPads, and iPods
The Apple iPhones, iPads, and iPods all run a single operating system, called the Apple iOS, which makes the configuration of Wi-Fi identical on each of them.
Here are the steps that your users need take to connect to a Wi-Fi network — at home, at a public location, or at work — from devices running the Apple iOS operating system:
1. Navigate to Settings⇒Wi-Fi on the iOS device. Make sure Wi-Fi is On.
If you don’t see any networks listed, that means you and your device aren’t close to any Wi-Fi networks. If there are Wi-Fi networks in your vicinity, those should be displayed on this page, as shown in Figure 8-1.
Figure 8-1: Browsing Wi-Fi networks on an iPhone.

2. Tap the network that you want to connect to.
If the network is open or public, you don’t need to enter a password; you should be able to connect right after you tap the network.
If the network is secure, you’re prompted to enter the password to connect.
![]() If you don’t see a padlock symbol displayed next to the network, that network is open or insecure. You can click the blue arrow at the end of each row to find more information about the network and the encryption technique used.
If you don’t see a padlock symbol displayed next to the network, that network is open or insecure. You can click the blue arrow at the end of each row to find more information about the network and the encryption technique used.
3. If prompted, enter the password to connect to the network.
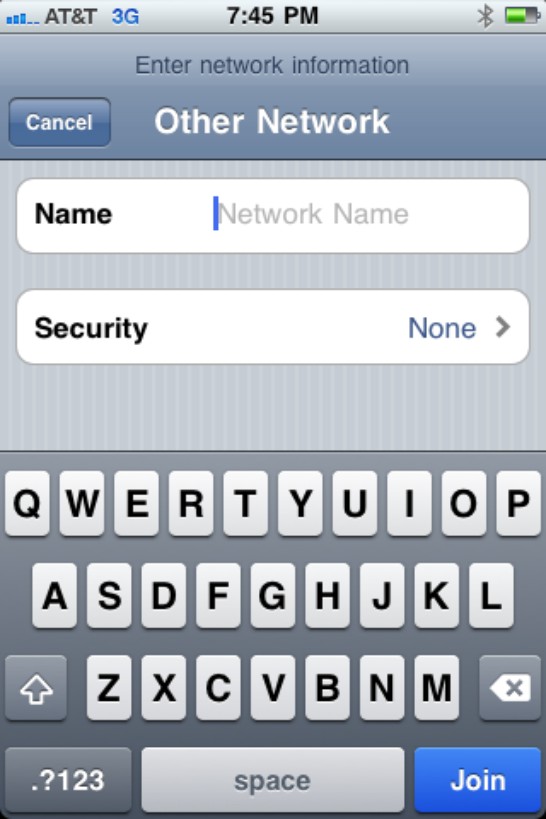
In most cases, the preceding steps should connect you to the nearest Wi-Fi network. If, however, you’re trying to connect to a hidden network that isn’t displayed on the device, tap Other in Wi-Fi Networks Settings to manually enter the network’s information on the screen shown in Figure 8-2.
Figure 8-2: Entering a hidden network using the Other option on an iPhone.
![]() You need decent signal strength to connect to a Wi-Fi network. If the network isn’t close by or the signal isn’t strong enough, you may not be able to connect to it.
You need decent signal strength to connect to a Wi-Fi network. If the network isn’t close by or the signal isn’t strong enough, you may not be able to connect to it.
![]() Many public networks require you to accept a legal agreement to use them. For example, if you connect to a Wi-Fi network in a hotel, more than likely a web page will be displayed with legal disclaimers, asking you to accept or decline the agreement. The disclaimer usually indicates that you choose to use the network at your own risk, and that the network owner isn’t liable for damages or losses that you may incur on their network. Unless you accept the agreement, the network will prevent you from browsing the Internet.
Many public networks require you to accept a legal agreement to use them. For example, if you connect to a Wi-Fi network in a hotel, more than likely a web page will be displayed with legal disclaimers, asking you to accept or decline the agreement. The disclaimer usually indicates that you choose to use the network at your own risk, and that the network owner isn’t liable for damages or losses that you may incur on their network. Unless you accept the agreement, the network will prevent you from browsing the Internet.
Connecting to Wi-Fi with Android devices
A number of devices on the market run the Android operating system, including the Motorola Droid, HTC Desire, and Droid Incredible.
Here are the steps that your users need to follow to connect to a Wi-Fi network from devices running the Android operating system:
1. On your Android device, tap the Settings icon.
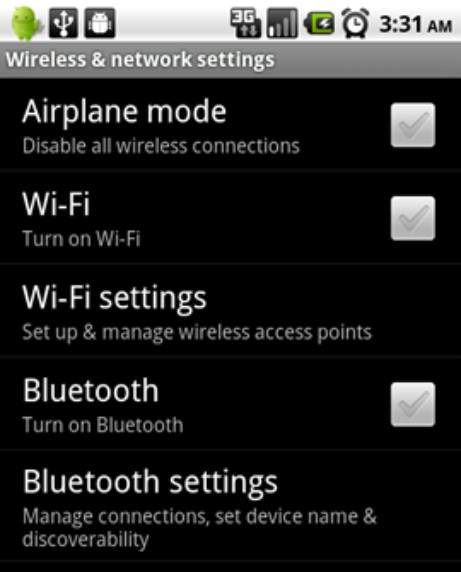
2. Tap Wireless & Networks under Settings.
The Wireless & Network Settings screen appears, as shown in Figure 8-3.
Figure 8-3: Browsing Wi-Fi networks on an Android device.
3. Tap Wi-Fi Settings.
Note that Wi-Fi needs to be turned on for the device to be able to detect Wi-Fi networks. If necessary, tap Wi-Fi to turn it on.
When Wi-Fi is enabled, you should see a list of networks on this page. (If you don’t see any Wi-Fi networks, it simply means that you aren’t near any.)
![]() Networks that are open and insecure appear without a padlock icon. Beware of connecting to such networks. At the very least, start up a VPN tunnel to your corporate VPN gateway as soon as you connect to such an open network.
Networks that are open and insecure appear without a padlock icon. Beware of connecting to such networks. At the very least, start up a VPN tunnel to your corporate VPN gateway as soon as you connect to such an open network.
4. Select a network to connect to.
5. If necessary, enter the password to connect.
![]() Many public networks require you to accept a legal agreement to use their network. Be sure to glance through the disclaimer before you accept the policy offered to you.
Many public networks require you to accept a legal agreement to use their network. Be sure to glance through the disclaimer before you accept the policy offered to you.
BlackBerry devices
Users can easily configure their BlackBerry devices to connect to public and private Wi-Fi networks. Like Apple iOS and Google Android devices, BlackBerry devices can deliver the same data services over Wi-Fi as on the user’s cellular network and potentially faster download speeds. That means users can access their e-mail and browse the Internet just like on the cellular network.
Here are the steps that your users need to follow to connect to a Wi-Fi network from devices running the BlackBerry operating system:
1. Select the Manage Connections option on the main menu.
2. Select the Set Up Wi-Fi Network option.
3. Select the option to Scan for Networks.
The device should automatically detect Wi-Fi networks in the vicinity. If not, you need to manually enter the network’s information.
4. Select a network to connect to.
5. Enter a password if the network requires one.
If you connect to an open network, it won’t prompt for a password.
Implementing Wi-Fi Policies
In most cases, once a smartphone has been used to connect to a particular Wi-Fi network, it remembers the network for future use. This means that whenever that network is in the vicinity of the device in the future, the device will connect automatically.
Private Wi-Fi networks, such as home networks, are best secured using WEP or WPA/WPA2 encryption. If your users are setting up a Wi-Fi network at home, they need to be sure to use these techniques to set up a suitably secured Wi-Fi environment.
If you’re deploying a corporate Wi-Fi network for many users, you should be looking for an enterprise-grade Wi-Fi with WPA2-enterprise encryption. This form of encryption may require you to deploy other infrastructure servers, so be sure to investigate the options from your networking vendor.
As an enterprise administrator managing policies for many users, you want to set policies that push out names and security keys of secure Wi-Fi networks that you want users to connect to, which may include your corporate Wi-Fi networks worldwide. When users bring their devices into the work environment, their devices will then detect and connect to the network, without needing the user’s intervention. This setup is ideal because it forces users to be on the corporate Wi-Fi network whenever available. When users move out of reach of the Wi-Fi network, their devices fall back to the carrier network.
In the following list, we look at the choices available to deploy Wi-Fi policies to smartphones from an enterprise perspective:
![]() iPhone and iPad: An application called iPhone Configuration Utility, shown in Figure 8-4, enables you to configure policies to enforce on corporate users’ iOS devices. These policies include Wi-Fi configuration as well. When you create a policy, the iPhone Configuration Utility produces a profile that can be sent out to all users at once. Users need to install the profile from their iOS devices to activate the policies and settings you’ve set up.
iPhone and iPad: An application called iPhone Configuration Utility, shown in Figure 8-4, enables you to configure policies to enforce on corporate users’ iOS devices. These policies include Wi-Fi configuration as well. When you create a policy, the iPhone Configuration Utility produces a profile that can be sent out to all users at once. Users need to install the profile from their iOS devices to activate the policies and settings you’ve set up.
Figure 8-4: The iPhone Config-uration Utility allows configuration of Wi-Fi policies for iPhones and iPads.

Mobile Device Management (MDM) vendors offer the feature of deploying such policies to Apple iOS devices centrally. You can utilize an MDM solution to define Wi-Fi policies, passcode settings, and many other policies, and deploy them centrally to all iOS devices with one click. We discuss these solutions in more detail in Chapter 15.
![]() BlackBerry: The BlackBerry Enterprise Server manages the configuration and deployment of Wi-Fi policies across all BlackBerry devices used in an enterprise.
BlackBerry: The BlackBerry Enterprise Server manages the configuration and deployment of Wi-Fi policies across all BlackBerry devices used in an enterprise.
The BlackBerry Enterprise Server supports a variety of policies, including device encryption, passcode compliance, and browsing preferences. You can centrally administer these policies and deploy them to all BlackBerry devices at once.
![]() Android and Windows Phone 7 smartphones: Google and Microsoft provide no solutions to manage corporate Wi-Fi policies. If you need to configure policies for all types of mobile devices, including iPhones, iPads, and Android devices, look for Mobile Device Management (MDM) solutions, which are available from vendors such as Juniper, Good Technology, and MobileIron. For a detailed review of MDM solutions, be sure to read Chapter 15.
Android and Windows Phone 7 smartphones: Google and Microsoft provide no solutions to manage corporate Wi-Fi policies. If you need to configure policies for all types of mobile devices, including iPhones, iPads, and Android devices, look for Mobile Device Management (MDM) solutions, which are available from vendors such as Juniper, Good Technology, and MobileIron. For a detailed review of MDM solutions, be sure to read Chapter 15.
