Chapter 9
Device Security Component Overview
In This Chapter
![]() Identifying the various components of device security
Identifying the various components of device security
![]() Protecting devices with on-device Anti-X protection
Protecting devices with on-device Anti-X protection
![]() Knowing in advance your backup and restore capabilities
Knowing in advance your backup and restore capabilities
![]() Incorporating loss or theft protection
Incorporating loss or theft protection
![]() Controlling user behaviors (yeah, right)
Controlling user behaviors (yeah, right)
![]() Managing devices in the enterprise
Managing devices in the enterprise
This chapter introduces the various on-device security components that provide a fairly robust security envelope when used smartly. You (and your users) need to understand these various components to be well equipped to harness the capabilities of these features, making your collective lives easier and more manageable.
Knowing Smartphone Security Components
Each of this chapter’s smartphone security components brings with it a unique and distinct capability that, when used wisely, provides you with ammunition to counter the various nefarious forces that are battling to gain access and compromise these devices.
We call to your attention to six discrete areas: device-based Anti-X protection, backup and restore capabilities, loss or theft protection, application control and monitoring, enforceable encryption, and enterprise management.
These six components are different enough in the type of protection that they provide that it’s not just a question of whether to use one or the other, but how to use them all. This chapter helps you understand specifically what type of protection these components provide so you can turn and twist their dials and create something that makes sense to your organization. Not to mention what to implement first.
Consider these six components of device security (shown in Figure 9-1):
Figure 9-1: Smartphone security components.
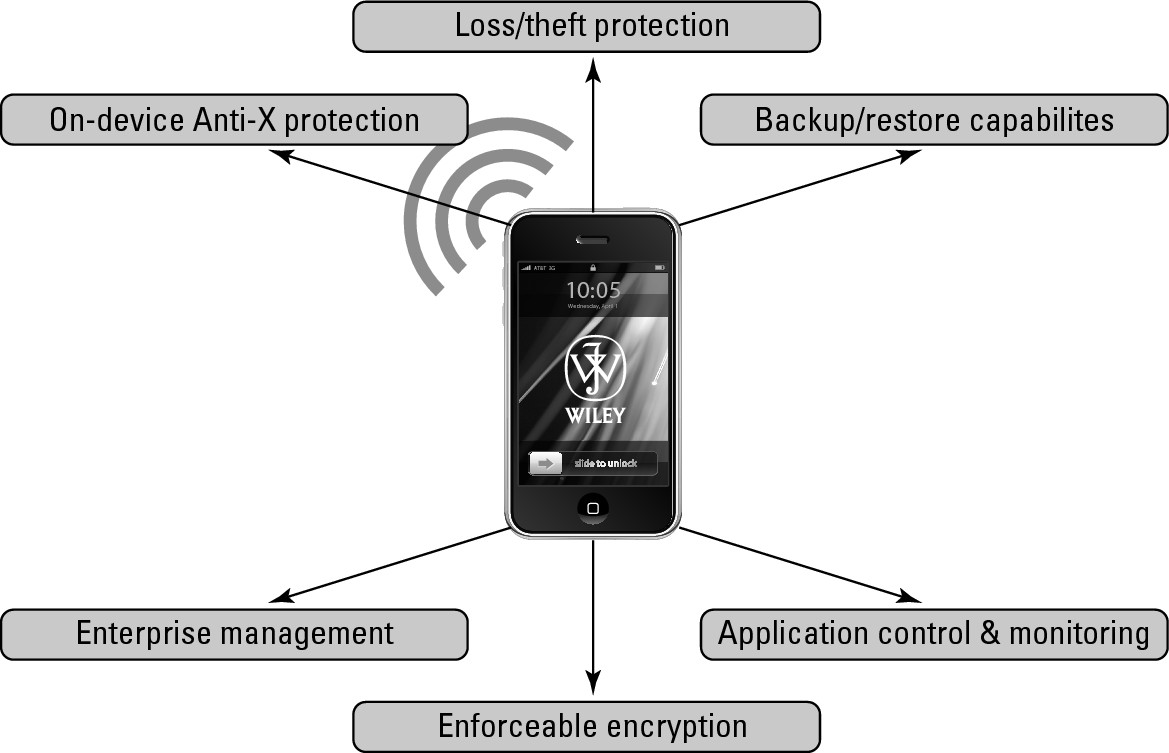
![]() On-device Anti-X protection: The security software actually running on the smartphone device itself
On-device Anti-X protection: The security software actually running on the smartphone device itself
![]() Backup and restore capabilities: The ability to back up the information resident on the smartphone, including applications and data and their configurations
Backup and restore capabilities: The ability to back up the information resident on the smartphone, including applications and data and their configurations
![]() Loss or theft protection: The remediation and recovery capabilities in the event of loss or theft of the smartphone itself
Loss or theft protection: The remediation and recovery capabilities in the event of loss or theft of the smartphone itself
![]() Application control and monitoring: The enforcement of corporate policy as it relates to the usage of applications by users of smartphones
Application control and monitoring: The enforcement of corporate policy as it relates to the usage of applications by users of smartphones
![]() Enforceable encryption: The ability to compel obfuscation of data — both resident on the smartphone as well as in-transit to the enterprise
Enforceable encryption: The ability to compel obfuscation of data — both resident on the smartphone as well as in-transit to the enterprise
![]() Enterprise management: The overall provisioning, troubleshooting, upgrade and monitoring of these smartphones
Enterprise management: The overall provisioning, troubleshooting, upgrade and monitoring of these smartphones
Understanding On-Device Anti-X Protection
When you are responsible for the device in the enterprise, this includes all of the associated applications, data, and the security posture of the smartphone or device. One of the key security components that is relevant to the security on the physical smartphone device is the “Anti-X” protection on the device. Anti-X refers to the family of security components that includes antispyware, antivirus, antiphishing, and antispam, as shown in Figure 9-2, and as the name suggests, can be extended to other threats that may arise in the future. So what exactly are these various subcomponents? Let’s delve into each one. You’re probably familiar what they are in terms of laptops and desktop computers, but mobility changes everything, including the equation that X equals security risk.
Figure 9-2: Smartphone security components.

Antispyware
In the term antispyware, the anti- refers to the essential component of the protection afforded against malicious spyware that installs itself on mobile devices. As a mobile device is always on the go — and with the plethora of interfaces supported by these smartphones — the likelihood that the smartphone is connected to one or more wireless networks most of the time is very high. This constant nomadic behavior and propensity to tethering means that the exposure level to unknown networks is very high, and therefore the likelihood of intrusions that can happen on these devices is far greater than a fixed desktop.
There are some unique dimensions to mobile spyware that make it different from the traditional desktop spyware that you might be used to. For instance, there have been cases of spyware that manipulate SMS messages and expose them so that they can be read by others in the near vicinity, as shown in Figure 9-3.
Figure 9-3: Mobile spyware in operation.

In the figure, an unsuspecting user is tricked into reading an SMS message that has spyware associated with it. This could be as simple as a URL in the SMS that the user clicks, which lands him on a malware-infested website. In this instance, the spyware scrolls through the contact list on the mobile device and starts spamming the contacts using every means possible — SMS, e-mail, IM, and so on.
So any antispyware solution for mobile devices — in addition to protecting against traditional spyware, such as keyloggers, data leakage, botnet membership (membership in a group of infected devices that have been taken over surreptitiously by hackers), and so on — needs to provide specific protection against mobile threats to mobile applications (such as SMS-based spyware), contacts database protection, location information spoofing (masquerading the device location to be any place of choice), and the like. If you think that’s still science fiction, think again. Do a Google search of the word spy phone, and the top hits you’ll get undoubtedly include ads for spyphone software intending to turn innocent devices into recording devices that send the records of all activities to a designated place. Yikes.
The market is there for the asking, and that means that hackers will be coming after your users’ devices in a big way, if not now, at some point in the near future. The simple solution: Be prepared to address the future with smart devices that have an antispyware solution.
Antivirus
Antivirus is a technology that has been available for decades, and many of your users would never consider operating a computer without some antivirus solution running on it. They get it when it comes to their desktop computers. However, a majority of mobile devices — which are all derivatives of computers in one way or another — go around without any sort of antivirus protection on them whatsoever! What is even more surprising is the despite this fact, your users (and you) increasingly rely more heavily on and become more personally attached to the smartphone. It’s like wearing a sweater at home on a cold day, but ignoring your coat when you go outside.
You need to take a stand and ensure that you’re providing adequate mobile antivirus coverage to your users on their mobile (and desktop) devices. The breadth of antivirus solutions is ever-increasing. Just as with traditional antivirus solutions, you should be looking for upfront costs; per-seat license renewals; automatic signature updates; and more uniquely mobile features, such as battery life recognition, memory requirements, and broadest mobile operating system coverage.
One tried-and-true antivirus solution comes from the traditional client-server model. In this scenario, an antivirus agent is downloaded to the device, but a bulk of the intensive processing that antivirus demands is actually performed on the server (either locally hosted by you or by a hosted cloud service). The client collects information about the mobile device and delivers a certificate of authority. In this model, shown in Figure 9-4, there may also be a clone (or virtual smartphone, as shown in the figure) of the actual enterprise phone maintained by you in the enterprise (maybe in the form of a virtual machine), and the agent informs you of any changes to the end device, such as new applications installed, SMSs received, and so on, and then syncs with the virtual phone in the enterprise.
Figure 9-4: Virtual device antivirus solution.

This is not real-time protection of the device, but it’s reasonably close and has the advantages of not causing performance or battery drain issues. In addition, because the antivirus solution is hosted on a server, there’s a lot more horsepower than is available for antivirus checking on the device.
Antiphishing
Phishing attacks on mobile devices are likely to be far greater than they are on your standard laptops and desktops. The reasons for that, as follows, are fascinating to consider.
![]() Unsecured wireless networks: Users are more likely to connect to unsecured wireless networks because of their nomadic nature and the ubiquity of wireless connectivity. This affords a very rich target for phishing-based attacks using a variety of attack vectors, such as browser-based, spurious proxies (rogue intermediaries that purportedly provide a legitimate function like a web proxy, but in fact are designed to steal information), SMS, and the like.
Unsecured wireless networks: Users are more likely to connect to unsecured wireless networks because of their nomadic nature and the ubiquity of wireless connectivity. This affords a very rich target for phishing-based attacks using a variety of attack vectors, such as browser-based, spurious proxies (rogue intermediaries that purportedly provide a legitimate function like a web proxy, but in fact are designed to steal information), SMS, and the like.
![]() Typing errors: Because of the limited real estate on the keyboard, users are prone to errors while typing URLs and therefore could be landing on spyware-infested websites that could launch phishing attacks.
Typing errors: Because of the limited real estate on the keyboard, users are prone to errors while typing URLs and therefore could be landing on spyware-infested websites that could launch phishing attacks.
![]() Small-screen display: The small screen size demands that the browser rendering of pages be optimized, and important information might be abbreviated or missing.
Small-screen display: The small screen size demands that the browser rendering of pages be optimized, and important information might be abbreviated or missing.
• Lack of security alerts and warnings: On a small screen, detailed security alerts and warnings may never be rendered. Check your smartphone right now and try to verify the appearance of a website and its content.
• Lack of e-mail source headers: E-mail clients often obfuscate the source headers of the e-mails for better rendering of the message. This kind of interface is ripe for phishing attacks because the headers are usually a dead giveaway for forged e-mails, and if this key indicator is missing, your users will be easily fooled.
• Lack of complete URLs: See Figures 9-5 and 9-6 for the URL obfuscation that happens in portrait mode in an iPhone versus landscape mode, which happens to display the entire URL in this case. Even your most alert users are easy prey to a phishing attack when they browse in portrait mode because the URL isn’t fully visible.
With this level of exposure to potential phishing attacks, it’s critical that you have an antiphishing solution available. Antiphishing solutions for mobile devices can have a similar approach as the antivirus solution: All of it can be localized on the device itself, or you could take a hybrid approach by leveraging the hosted server in addition to installing a lightweight agent on the device.
Figure 9-5: An iPhone in landscape mode with no URL obfuscation.

Figure 9-6: An iPhone in portrait mode with URL obfuscation.

A variant of the hybrid approach is the cloud-based approach where the antiphishing arsenal, e-mail, messaging and URL filtering, is entirely cloud-based. While this approach has a lot of appeal, without a smart agent running on the smartphone or device, an exclusive cloud-based approach falls short of the mark because of all the different interfaces it must maintain, which means that it has many different attack vectors.
Antispam
Antispam is the ability to identify and stop spam — typically in the form of e-mail — to the device, but note that for today’s mobile devices, the spam vectors increasingly include SMS as well. From your users’ perspective, the one distinct difference between e-mail–based spam and text-messaging–based spam is the latter sometimes costs your users (especially those in certain geographies; more on that in a moment) because some cellphone plans impose charges for messages received over a specified limit. Unlike e-mail spam, which is a major irritant (and a potential phishing mechanism), at least it doesn’t cost the user money.
In response to this, carriers have been pretty active. In the United States, for instance, AT&T advertises a service called AT&T Smart Limits, which allows the user to block or allow text messages from certain users. Yes, it’s an opt-in, paid service that users have to subscribe to. But according to research conducted by Ferris Research, in the United States users typically receive a couple of SMS spam messages per year, in Europe the frequency jumps to a couple per week, and in India it’s a couple a day, while in China users are bombarded with 5 to 10 spam messages a day! So it’s coming to a location near you. The geographical disparities in the SMS spam are a direct reflection of the SMS usage. In Asia and Europe where SMS usage is rampant, the spam frequency is also high, whereas in the United States, where SMS usage is relatively muted, the spam usage lags.
The other point is that there is a global uniformity component that needs to be factored in with any sort of solution you roll out. On the standards front, the GSMA (GSM Association), a consortium of nearly 800 members, has kick-started an initiative called GSM spam reporting service whereby users who receive spam can forward those messages to a standardized number. (It’s currently proposed as #7726, which spells SPAM on the handset.) This is a neat way to build a database of blacklists for the spam operators and eventually use this information to build an in-network spam-blocking solution! Information about spammers will also be shared among participating members who will receive correlated reports with data on misuse and threat to their networks.
Antispam solutions — for e-mail or messaging — have more value if they’re handled by the server rather than the client. This enables you to centralize the antispam solutions and apply remediation at the e-mail servers that you host — or apply it at your outsourced arm. For SMS-based spamming, the service is typically provided by the carrier, so you should actively work with your user’s carrier, or educate your users about their carriers’ services, to arrive at a solution that satisfies your needs.
A new variant of mobile spam is the use of applications on the mobile device to expose a new threat vector. For example, the Facebook app on your users’ devices is one of the most popular applications in use. A clever spammer recently discovered a vulnerability to autoreplicate links so that unsuspecting users clicking any of the application spam links, shown in Figure 9-7, is enough to “share” (publicly post) the application on the user’s Wall, and it spreads virally from there. Even though this isn’t a mobile-specific spam vector, it’s one that’s growing in popularity using the social network applications for posting for spam and phishing attempts.
Figure 9-7: Facebook spam.

These kinds of social engineering–based spam are the hardest to mitigate and prevent, as these are predominantly tied to user behavior and tap into the psychology that the spammers become expert in exploiting.
![]() Constant vigilance
Constant vigilance
![]() Security posture adaptation
Security posture adaptation
![]() Relentless education of your users
Relentless education of your users
Using Backup and Restore Capabilities
Many smartphone OS vendors already offer some version of backup and restore. For instance, iPhone already comes with backup and restore capabilities whenever the device syncs with iTunes. But this is ultimately designed for end users, and the backup destination is anywhere the user chooses it to be. It also relies on diligent users who turn on this functionality in the first place. So this isn’t something you can rely on. You need an enterprise-grade backup and restore capability that you can control.
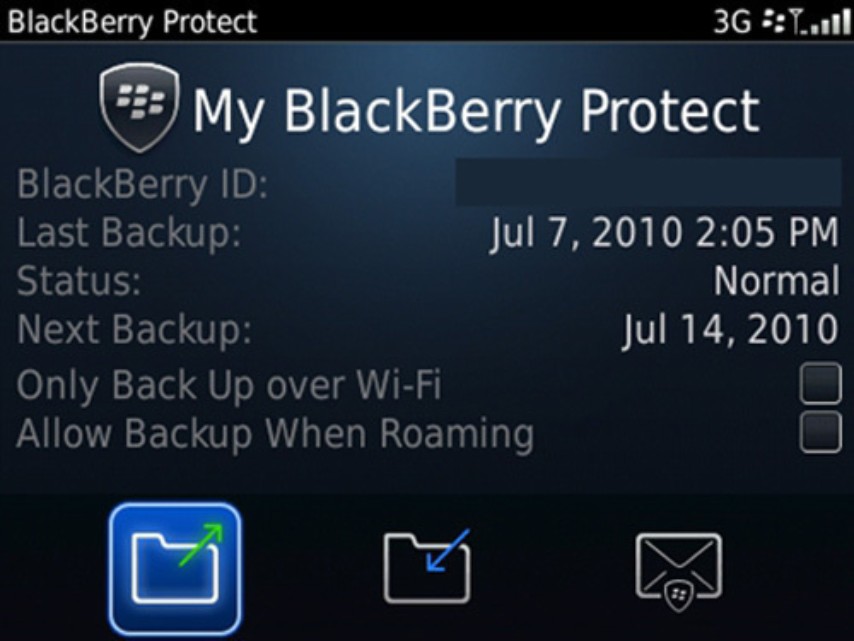
A top-grade enterprise solution that RIM (Research In Motion) offers as part of their BlackBerry Enterprise Server automates backup and restore, as the BlackBerry Enterprise Server automatically syncs over the air with the BlackBerry devices and provides you with the ability to back up the BlackBerry Enterprise Server. (Typically, it’s on secure premises.) In fact, RIM is even extending this traditional enterprise server–based backup to the actual individual users so the users can take the matter into their own hands. Figure 9-8 shows one of the backup and restore management screens in the BlackBerry Protect user interface.
Figure 9-8: My BlackBerry Protect.
The basic components of any backup and restore capability should
![]() Be able to do backups of smartphone data at a predefined frequency using over-the-air technology (as well as local backups when possible).
Be able to do backups of smartphone data at a predefined frequency using over-the-air technology (as well as local backups when possible).
![]() Be able to do restore of smartphone data on demand using both over-the-air technology as well as a local connection.
Be able to do restore of smartphone data on demand using both over-the-air technology as well as a local connection.
There are a variety of ways you can provide this support, depicted in Figure 9-9 and explained as follows:
Figure 9-9: Backup and restore solutions.

![]() Vendor supported: The BlackBerry fits nicely into this category, and very little mental exercise is required from you when you adopt this option. However, other smartphones and most devices don’t support this option.
Vendor supported: The BlackBerry fits nicely into this category, and very little mental exercise is required from you when you adopt this option. However, other smartphones and most devices don’t support this option.
![]() Provider supported: Increasingly, carriers are starting to provide this as a service offering, and you may be able to capitalize on this by entering into agreements with operators and getting this provided as a managed service offering.
Provider supported: Increasingly, carriers are starting to provide this as a service offering, and you may be able to capitalize on this by entering into agreements with operators and getting this provided as a managed service offering.
![]() End-user supported: This relies on end users regularly using the supported options to back up their smartphones. However, as noted earlier, the backup is typically local to their desktops and laptops only, so this solution in turn relies on your (hopefully) existing enterprise backup of their local machines to enterprise backup servers thereby backing up their smartphone backups. Wow! That sounds convoluted, and it is.
End-user supported: This relies on end users regularly using the supported options to back up their smartphones. However, as noted earlier, the backup is typically local to their desktops and laptops only, so this solution in turn relies on your (hopefully) existing enterprise backup of their local machines to enterprise backup servers thereby backing up their smartphone backups. Wow! That sounds convoluted, and it is.
![]() You should not adopt an end-user–supported option as your primary backup solution because it relies on end-user best practices, and while the workforce education is getting better all the time, relying on an informed workforce to guarantee backups is simply not recommended. Ultimately, you are responsible for protecting your company asset — the intellectual property — and need to exercise controls to do so. Therefore, you need to have backup solutions that can be scheduled, archived, and audited by you (and your stakeholders).
You should not adopt an end-user–supported option as your primary backup solution because it relies on end-user best practices, and while the workforce education is getting better all the time, relying on an informed workforce to guarantee backups is simply not recommended. Ultimately, you are responsible for protecting your company asset — the intellectual property — and need to exercise controls to do so. Therefore, you need to have backup solutions that can be scheduled, archived, and audited by you (and your stakeholders).
Adding Loss and Theft Protection
Your users are wedded to their mobile devices, perhaps more than they realize. A brief divorce from their beloved smartdevice is enough to cause heart palpitations and sweaty palms. These devices have become an extension of the owners themselves, so protecting them becomes a necessity — not a luxury!
The most fundamental defense against loss or theft of mobile devices is over-the-air (OTA) disabling. With enterprise-friendly devices like the BlackBerry, this is a breeze, but with most mobile devices, including the iPhone, iPod, iPad, Android-based devices, and others, this is a trickier proposition.
Thankfully, loss and theft protection is a rapidly evolving area, and all the leading device security vendors are rolling out various OTA device-disabling solutions to cater to this security need. Their antitheft solutions can be classified into these three broad categories:
![]() Encryption and authentication techniques
Encryption and authentication techniques
![]() Immobilizing techniques, including active data obfuscation following the loss of the smartphone
Immobilizing techniques, including active data obfuscation following the loss of the smartphone
![]() Recovery techniques to locate the smartphone
Recovery techniques to locate the smartphone
The following sections cover each of these categories in greater detail.
Encryption and authentication techniques
As the name suggests, this technique obfuscates critical data on the device itself using encryption technologies. As you see in earlier chapters, extensible memory on the devices, including removable storage, makes the loss of the device quite dangerous. One mechanism that can mitigate this is encrypting the data on these memory cards so that in the event of a loss, the perpetrator can’t access the memory card data using a card reader. Likewise, for onboard memory as well, using strong authentication techniques should be mandatory.
Immobilizing techniques
Here are the two most common immobilizing techniques:
![]() Remote lockdown: This technique involves an over-the-air kill message that is issued by the enterprise to the smartphone, which will essentially render the smartphone lifeless.
Remote lockdown: This technique involves an over-the-air kill message that is issued by the enterprise to the smartphone, which will essentially render the smartphone lifeless.
![]() Remote wipe down: This technique involves wiping out the critical smartphone data — contacts, local files, e-mails, SMS, and memory card.
Remote wipe down: This technique involves wiping out the critical smartphone data — contacts, local files, e-mails, SMS, and memory card.
Recovery techniques
These are the most common recovery techniques:
![]() Smartphone locator: Most of the modern day smartphones have a GPS chip built in. Using location software, the ability to track down the smartphone is becoming increasingly practical.
Smartphone locator: Most of the modern day smartphones have a GPS chip built in. Using location software, the ability to track down the smartphone is becoming increasingly practical.
![]() SIM snooping: One of the first things that a stolen smartphone is subject to is swapping the SIM out. This provides an insertion point to use a technique called SIM snooping, which surreptitiously sends the newer SIM’s telephone number to the original user, and this key piece of data can be used to locate the user with the carrier’s assistance.
SIM snooping: One of the first things that a stolen smartphone is subject to is swapping the SIM out. This provides an insertion point to use a technique called SIM snooping, which surreptitiously sends the newer SIM’s telephone number to the original user, and this key piece of data can be used to locate the user with the carrier’s assistance.
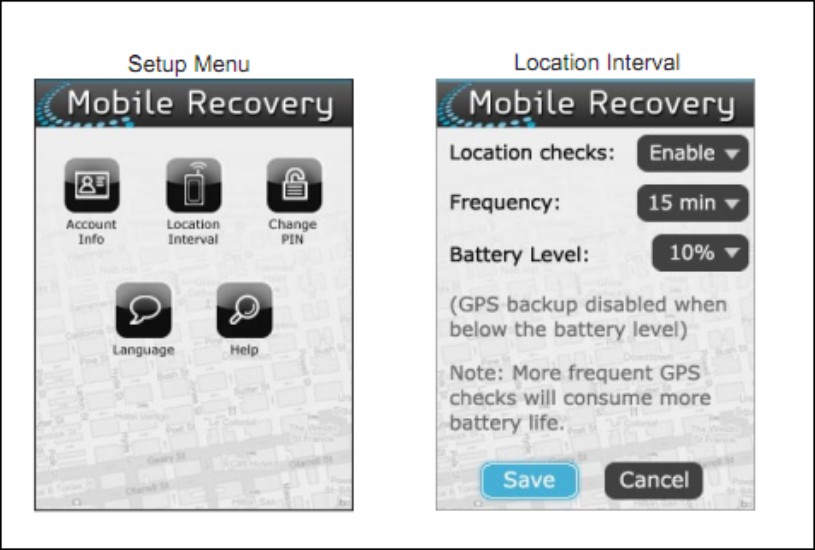
Carriers are getting into the act as well to provide protection against loss and theft. For instance, Verizon Wireless now offers to its customers the Mobile Recovery app shown in Figure 9-10.
Figure 9-10: Verizon Wireless’s Mobile Device recovery app.
Controlling and Monitoring Applications
Applications, or apps, are fast becoming the de facto user interface for mobile devices. Therefore, you need to be in sync with this trend and be able to provide adequate monitoring of these applications using various approaches (which we discuss in this section), identifying harmful applications in a timely manner and intervening when necessary.
Let’s get real: Your users will download content (willfully or involuntarily) that is in violation of your enterprise policies. It’s in your best interests — and your users’ best interests, even though they may not embrace this notion right away — that you have good visibility into their application usage behavior and intervene where appropriate.
Methods to control and monitor applications
Now that you understand the importance of monitoring and controlling applications on your users’ devices, you need to determine what type of solution you want to deploy.
There are two approaches to application control and monitoring:
![]() Client-only: In a client-only approach, you have a monitoring application running on every mobile device that you need to configure in the enterprise. While daunting, it provides you with an unparalleled degree of individual control, and you can set up policies that are unique to every user in the enterprise. More impressive is that you can take into account the real-time characteristics of the device — such as location, battery life, and other applications running — to make a much more customized strategy.
Client-only: In a client-only approach, you have a monitoring application running on every mobile device that you need to configure in the enterprise. While daunting, it provides you with an unparalleled degree of individual control, and you can set up policies that are unique to every user in the enterprise. More impressive is that you can take into account the real-time characteristics of the device — such as location, battery life, and other applications running — to make a much more customized strategy.
![]() Server-based: At the other end of the spectrum is a server-based approach that employs a centralized gateway to which all device traffic is backhauled and generic policies are applied. While user and device identification are still possible in this approach, and policies can be tailored to cater to the individual smartphone, the specific characteristics that an agent could supply in the previous approach are no longer available here. However, the economies of scale are evident, as you can have a centralized console for configuration, monitoring, and enforcement without having to worry about connecting to every individual device.
Server-based: At the other end of the spectrum is a server-based approach that employs a centralized gateway to which all device traffic is backhauled and generic policies are applied. While user and device identification are still possible in this approach, and policies can be tailored to cater to the individual smartphone, the specific characteristics that an agent could supply in the previous approach are no longer available here. However, the economies of scale are evident, as you can have a centralized console for configuration, monitoring, and enforcement without having to worry about connecting to every individual device.
A more common hybrid approach is to tie in a lightweight agent with a server back end that can benefit from the agent providing the instrumentation and lightweight policy enforcement, with the server doing more complex application usage analysis and determination of policy changes that can then be relayed to the agent when appropriate.
Identifying harmful applications
You have to be on the lookout for seemingly harmless applications that your users download to solve a business issue. The application might seem innocent, but it could have an underlying security loophole that when exploited can cause all kinds of issues.
For example, an increasing number of new laws are mushrooming that ban automobile drivers from using their cellphones while driving. This has given rise to a number of text-to-voice applications that convert your text messages and e-mail into voice and play it back to you while you’re driving. Seems like a very useful function. Bad idea! A number of these applications also use the “hybrid approach” whereby their app is actually a lightweight agent, and a bulk of the transcription happens in the cloud. So your users may actually be compromising valuable corporate data in the quest to be more productive while they’re driving.
Enterprise Management of Mobile Devices
There is a lifecycle to which a mobile device in an enterprise needs to adhere to allow you a predictable process to get enterprise-ready mobile devices into and out of the workplace.
Enterprise management of mobile devices can be broken down into the following activities:
![]() Device deployment
Device deployment
![]() Device discovery
Device discovery
![]() Device provisioning
Device provisioning
![]() Device monitoring
Device monitoring
![]() Compliance enforcement
Compliance enforcement
The following sections give you a complete overview of enterprise mobile devices lifecycle management. We delve into detail about each of these important phases of the mobile lifecycle.
Device deployment
Device deployment is relevant only if you intend to issue enterprise devices to your employees. If on the other hand (as is becoming the norm), the devices in your enterprise are predominantly owned by the employees themselves, this activity can be easily skipped.
An effective device deployment strategy involves providing a limited selection of devices from which your users can choose from (providing a large selection would entail a broader support burden that in most cases is unnecessary). Additionally, the strategy entails negotiating with carriers about bulk pricing (including pooling data, text, and voice across your user base) and shorter contract length to allow you sufficient flexibility to evaluate effectiveness and pricing periodically.
If, however, you’re tasked with deploying devices in the enterprise, you need to take the following factors into consideration:
![]() Device selection(s): Opt for a limited set of devices to cater to a basic voice user as well as to the more advanced mobile device user. Device characteristics should reflect the enterprise policies we discuss earlier (device encryption, remote wipe capabilities, and so on).
Device selection(s): Opt for a limited set of devices to cater to a basic voice user as well as to the more advanced mobile device user. Device characteristics should reflect the enterprise policies we discuss earlier (device encryption, remote wipe capabilities, and so on).
![]() Carrier selection(s): Depending on the size of your enterprise and whether or not roaming is needed, your carrier selection may vary. Typically going with a larger carrier provides better worldwide coverage, but if you require local roaming only, some of the tier 2 and tier 3 carriers have very good promotions and service.
Carrier selection(s): Depending on the size of your enterprise and whether or not roaming is needed, your carrier selection may vary. Typically going with a larger carrier provides better worldwide coverage, but if you require local roaming only, some of the tier 2 and tier 3 carriers have very good promotions and service.
![]() Pricing terms: You need to negotiate bulk pricing that allows you to aggregate data, text, and voice across your users to give you better pricing based on consolidated usage and your users better flexibility by not having to carefully monitor their individual usage.
Pricing terms: You need to negotiate bulk pricing that allows you to aggregate data, text, and voice across your users to give you better pricing based on consolidated usage and your users better flexibility by not having to carefully monitor their individual usage.
![]() Contract lengths: You should negotiate contract lengths down to the smallest possible terms to allow you periodic evaluation of effectiveness and pricing from the carrier.
Contract lengths: You should negotiate contract lengths down to the smallest possible terms to allow you periodic evaluation of effectiveness and pricing from the carrier.
![]() Warranty terms: Negotiate extended warranty terms for mobile device replacement as well as periodic upgrade terms because your users will expect reasonable upgrade cycles as technology and offerings advance.
Warranty terms: Negotiate extended warranty terms for mobile device replacement as well as periodic upgrade terms because your users will expect reasonable upgrade cycles as technology and offerings advance.
Device discovery
Discovering mobile devices as they come into your network isn’t a difficult activity to perform. Depending on how the device connects to the enterprise, there are various techniques to authenticate the user and the device. For instance, if a smartphone is using Wi-Fi to connect to the enterprise network, user authentication is a good first step to identify the employee. To further qualify the device, the ISAPI filters or Network Access Control (NAC) techniques can be used to zero in on the device type itself.
If the user is using the carrier’s wireless network to connect to the enterprise, typically this is over a VPN connection like SSL, and the SSL appliance can be used to elicit the user and device information.
If the device isn’t recognized, you can choose whether to block all access to the enterprise or limit the user access to noncritical systems. This is dependent on the strictness of your enterprise policy that you choose to enforce.
Device provisioning
Provisioning devices involves delivering configuration data and policy settings to the mobile devices. (Chapter 4 covers these policies in detail.) The leader in this space is clearly Research In Motion, with its BlackBerry Enterprise Server that, with a few mouse movements, can remotely configure these devices. Other device and OS vendors are catching up to this crucial enterprise requirement. For instance, Apple’s configuration and security settings can be deployed wirelessly through a user self-enrollment portal. While not as transparent to your user community as the BlackBerry solution, it does provide similar levels of granular configuration and policy deployment to iPhones and iPads.
Device monitoring
Device monitoring is a constant activity that’s needed to ensure that the mobile device is in compliance with your enterprise policies at all times. Note that this is different from application control and monitoring, which have more to do with user behavior and being able to control what the end user is trying to accomplish. For more information on application control and monitoring, see the section “Controlling and Monitoring Applications,” earlier in this chapter.
Typically, an enterprise agent is installed in the provisioning process (described in the preceding section), and it’s your eyes and ears for every enterprise mobile device. This agent has some unique characteristics — it needs to consume very little CPU and battery power, and it needs to be as unobtrusive as possible until a violation is detected.
And unobtrusively means that when the device discovers a known enterprise wireless access point and connects to it, the device monitoring agent monitors this connection to ensure that all communication thereafter stays encrypted.
Compliance enforcement
The next step in the flow, once your device-monitoring agent detects a violation of your enterprise policy, is enforcement, which comes in these three flavors:
![]() Automated correction that’s transparent to the user
Automated correction that’s transparent to the user
![]() Automated correction (through redirection to a self-service portal) that requires user interaction
Automated correction (through redirection to a self-service portal) that requires user interaction
![]() Manual remediation that requires your intervention (highly undesirable — see the following warning)
Manual remediation that requires your intervention (highly undesirable — see the following warning)
![]() The last option of manual remediation should be your “have no other recourse, therefore I am going to resort to this” option. This is a highly intrusive, labor-intensive, and user-unfriendly option. But in certain situations, this may be the only option available to you, so we cover this as well in the subsequent sections.
The last option of manual remediation should be your “have no other recourse, therefore I am going to resort to this” option. This is a highly intrusive, labor-intensive, and user-unfriendly option. But in certain situations, this may be the only option available to you, so we cover this as well in the subsequent sections.
Automated correction
As the name suggests, automated correction is the most painless of approaches, as it doesn’t require any intervention by you or the user, and the device automatically self-corrects. This intelligence is embedded in the monitoring application itself.
For instance, consider the previous example for device monitoring where the smartphone connects to an enterprise wireless access point and the monitoring agent’s job is to verify that all traffic is encrypted. When a device is found to be in violation, it could be easily self-corrected to enable encryption on the smartphone (IPSec or equivalent) without affecting the end user and still ensure that your enterprise policies are met at the same time!
Semi-automated correction
The semi-automated remediation capability requires the user to be involved. Typical violations are applications that are downloaded that violate enterprise policies. An example of this could be an application that provides cloud storage as an extension to local device storage. Clearly, for data that is stored locally, you would have policies such as local encryption, but once this data extends to the cloud, there’s no way you can enforce such policies.
Your only resort at that point is to disable these classes of applications. However, since you can’t willy-nilly delete applications on your employees’ devices, your only resort is to redirect them to a remediation portal where they’re presented with the facts. Perhaps, a notice such as this would work:
“Your Foo app is in violation of enterprise storage policies. You will not be allowed access to the enterprise network until you disable or delete the Foo app from your device. Have a nice day.”
Be succinct yet comprehensive so the user is faced with the choice of either deleting the app or choosing to retain the application but not connecting to the enterprise any more.
In either case, there is active user involvement, and giving users a choice offloads the burden from you and your staff having to deal with these errant users!
Manual remediation
Manual remediation is the most intrusive as it involves you — the IT department — having to play a part in enforcing the enterprise policy. Typically, this happens if automated correction isn’t possible or there have been recurring violations that need active intervention on your part.
An example where automated or semi-automated correction isn’t possible is when a new vendor’s device is introduced to the network. As discussed earlier, you have a choice of blocking all access or limiting it to noncritical systems. But a third choice is to meet with the user to learn about the device and its capabilities — and maybe even add that to your catalog of supported devices and adapt your policies based on this device’s unique capabilities. This keeps you ahead of the game, and more importantly, you are viewed as a trusted and flexible partner who is constantly working with your user community to make them more productive!
