Chapter 3
Planning for Mobile Devices in the Enterprise
In This Chapter
![]() Protecting mobile devices from malware
Protecting mobile devices from malware
![]() Remotely managing mobile device policies
Remotely managing mobile device policies
![]() Enabling application access to mobile users
Enabling application access to mobile users
![]() Adapting your corporate policy for mobile devices
Adapting your corporate policy for mobile devices
Most corporate mobility policies allow for employee usage of one, or maybe two, approved devices for corporate use. Recent increases in the choices of mobile devices, and their increasing popularity, present challenges with today’s mobility policies.
Enterprises that are used to issuing corporate-approved assets like laptop PCs are tempted to account for smartphones in the same manner, by issuing corporate-approved tablet computers and smartphones. The challenge therein is to qualify and approve these kinds of devices as quickly as they appear in the market.
Other enterprises look to migrate to a “bring-your-own-device” model, where they allow employees to bring their own devices to work, as long as the enterprise policies can be reliably deployed and enforced on these devices.
Such challenges require revisiting your existing corporate mobility policies to account for smartphones and other new mobile devices. It seems obvious that the latest generation will revamp mobility in the enterprise as we knew it. Gone are the days when employees relied solely on their corporate-standard BlackBerry device to check corporate e-mail. Today, employees have more choices for devices, many of which are not approved or, worse, evaluated by their IT departments. It therefore has become important to devise security policies for not just the corporate-approved mobile devices, but also the devices that are owned by employees and bound to be used for corporate access. These devices may include the latest gadgets available in the market.
Some devices in the market are as computationally powerful as laptop computers used to be just a few years ago. The developer platforms available for leading platforms like the iPhone and Android also facilitate a thriving ecosystem of apps, including ones that can be used for corporate access. These apps allow users to not only check e-mail but also use other applications, like client-server applications such as SAP or Oracle. This necessitates creating policies to allow users to access only those applications that they are authorized for.
The latest mobile devices are also vulnerable to viruses, malware, and other types of threats that typically are known to affect Windows PCs. This makes the security of mobile devices just as important as securing regular desktop or laptop computers. Be sure to check out Chapter 6, where we discuss the protection of mobile devices from various threats like malware, viruses and spam.
Managing the New Wave of Mobile Devices
The success of the Apple iPhone set off a trend of similar smartphones from other vendors, including Motorola, Google, LG, Samsung, Nokia, and others. Of course, the erstwhile king of the corporate phone market — the BlackBerry — still remains widely used in workplaces worldwide. Such a plethora of these phones are available in the market that competition is forcing rapid innovation from several vendors; therefore, these devices and the platforms they run on are evolving rapidly.
Just when you thought smartphones were the only hot things in the market, Apple unleashed what appears to be another game-changer: the iPad. And following suit, several other vendors either released their own tablets or announced their intentions to release tablets.
Many enterprises find that employees are abandoning their corporate-standard devices in favor of the latest and greatest new gadgets available in the market. As you can imagine, this wrecks your company’s carefully laid out mobility management and security policies.
Keep in mind these two key ideas regarding the impact of today’s increasing usage of smartphones:
![]() Not all devices are created equal. Smartphones are available from various device manufacturers, including Apple, Google, Nokia, Motorola, RIM, and Samsung. However, these devices are not similar in many respects. They run different operating systems, have vastly different capabilities and features, and present their own unique challenges to being managed or secured for enterprise usage.
Not all devices are created equal. Smartphones are available from various device manufacturers, including Apple, Google, Nokia, Motorola, RIM, and Samsung. However, these devices are not similar in many respects. They run different operating systems, have vastly different capabilities and features, and present their own unique challenges to being managed or secured for enterprise usage.
![]() Smartphones are very different from regular Windows and Mac computers. Smartphones and tablets are very different from regular computers running Windows, Mac, or Linux operating systems. Mobile operating systems like Apple iOS, Google Android, Nokia Symbian, BlackBerry and Windows Mobile are designed specifically for these smaller and more portable devices. So you’ll need to give them a closer look, because your traditional enterprise policies for managing Windows and Mac systems will most likely not apply to these mobile devices.
Smartphones are very different from regular Windows and Mac computers. Smartphones and tablets are very different from regular computers running Windows, Mac, or Linux operating systems. Mobile operating systems like Apple iOS, Google Android, Nokia Symbian, BlackBerry and Windows Mobile are designed specifically for these smaller and more portable devices. So you’ll need to give them a closer look, because your traditional enterprise policies for managing Windows and Mac systems will most likely not apply to these mobile devices.
Support the cutting-edge devices
Lots of people today are mobile enough that they don’t make a distinction between work and home. Such people are technically savvy and use the newest gadgets for work as well as for personal use. These are the expert users who don’t constrain themselves to using the corporate-assigned BlackBerry devices to check e-mail, but instead bring the latest available tablet or smartphone to work.
Such expert users abound in today’s enterprise environment, representing the employees who buy their own mobile devices, download business apps from the market place or application store, and productively work on these devices. They like to be on the cutting edge of technology, leveraging the latest and best the industry has to offer. IT departments scramble to keep up with these users and their devices because many are simply not equipped to constantly evaluate all the latest mobile devices in the market.
Interestingly, it is difficult to ignore this kind of usage or deem the latest devices as being unsupported. Often these expert users are executives who shop for the latest gadgets and find ways to use them for corporate access. As the mobile market heats up with multiple vendors, prices become competitive, and many of these devices become affordable to mass consumers.
The bottom line is that mobile-savvy users are here to stay, and they are rapidly growing in number. Your enterprise needs to revisit your policies of handing corporate devices to employees, and analyze how you will adapt to this new trend of using personal devices for work. Here are some questions to consider:
![]() How do existing mobile security policies evolve?
How do existing mobile security policies evolve?
Would you allow employees’ personal devices into the network? How would you handle the employees who bring the latest consumer gadgets into the workplace?
![]() How do you manage these personal devices?
How do you manage these personal devices?
Would you continue assigning corporate-approved devices with custom applications and “locked-down” policies? Doing so would necessitate you to stay at the cutting edge of the smartphone market by evaluating the coolest and newest devices available in the market. This requires a lot of time and investment in both devices and personnel.
![]() How can enterprises protect themselves from losing corporate data, such as e-mail, when these devices are lost or stolen?
How can enterprises protect themselves from losing corporate data, such as e-mail, when these devices are lost or stolen?
What type of security software would you consider deploying on these devices to protect them from viruses, malware, and other threats? There are mobile security solutions available in the market today that you need to evaluate and shortlist for deployment.
More than just e-mail
For each of the leading smartphone platforms available — such as the iOS, Android, Windows Mobile, BlackBerry, and Symbian — there are application stores supporting a variety of business apps.
Smartphone users can now easily access corporate e-mail, with sophisticated integration with Microsoft Exchange servers. They can also access web pages on the intranet using mobile browsers that support SSL encryption. Many business apps found in application stores provide functions such as Remote Desktop Protocol (RDP) or Virtual Network Computing (VNC). Several application vendors have also released client applications that enable users to access server applications in the enterprise data center.
So employees are using these devices not just to check e-mail but also to check the latest company news on the intranet, watch company videos, update blogs on the intranet, and also access server applications like SAP and Oracle. It is therefore not just corporate e-mail that ends up on modern mobile devices, but a lot more content. Mobile devices can establish VPN (virtual private network) tunnels (connections) to your corporate VPN gateway, thereby getting on to the network.
As devices grow more sophisticated in screen resolution and processing, this trend will only grow because application access will become ubiquitous. Although RDP on the small screen of the iPhone is cumbersome to use, it is now an order of magnitude better and more usable on the larger iPad. And if a couple of application vendors have client apps in the App Store, you can rest assured that their competitors will quickly follow them with their own apps.
Most employee mobile usage can broadly be classified into the following types of application access:
![]() E-mail
E-mail
![]() Web-based applications on the mobile browser
Web-based applications on the mobile browser
![]() Full network access, including using client-server apps such as Oracle or SAP
Full network access, including using client-server apps such as Oracle or SAP
When you think of enabling remote access for mobile devices, think of which types of applications you want to enable for access from mobile devices. In many cases, depending upon the user’s role in the company (such as “employee,” or “finance,” or “IT contractor,” or “executive”), a single application type or maybe two might be sufficient.
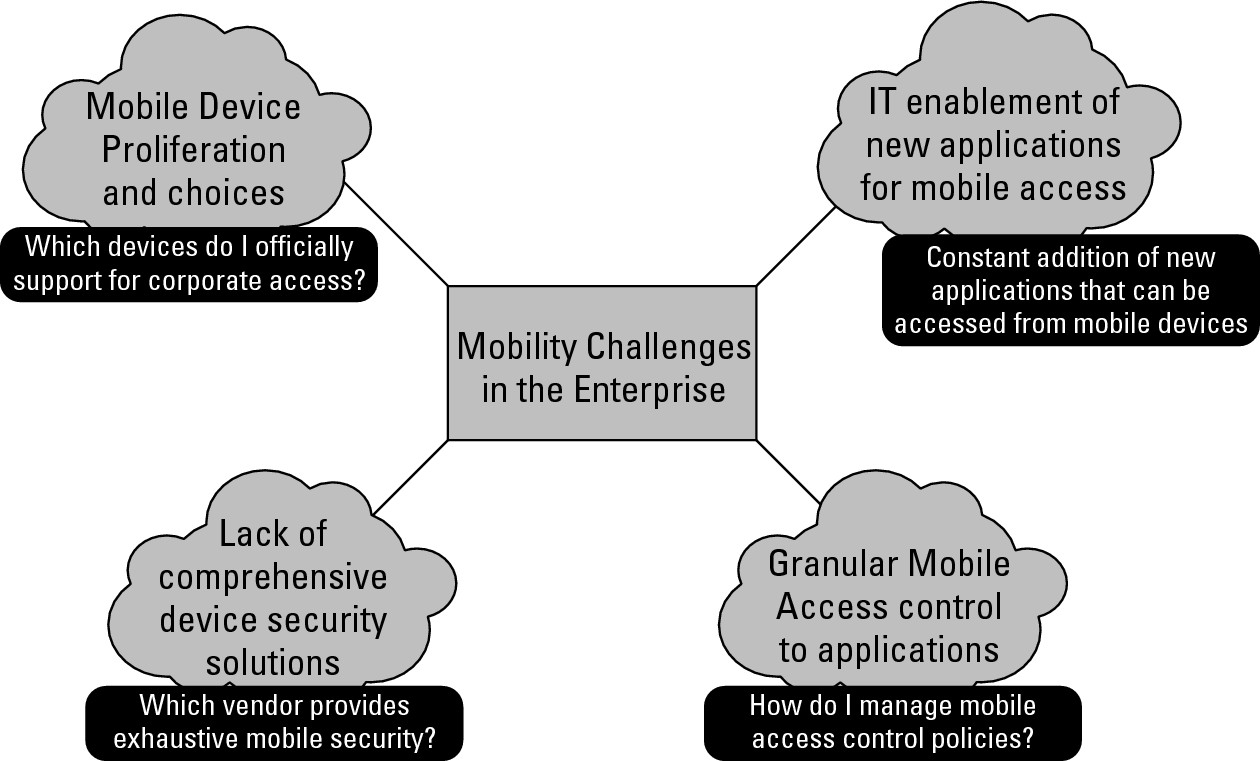
And so, it goes on. Business applications are growing rapidly in the app stores, and devices are growing more sophisticated for users to do real work on them. If everything seems to collide, take a look at Figure 3-1, which will help you visualize the challenges in the following distinct arenas:
![]() Mobile device choices: What types of devices should be allowed into the workplace and which ones should not?
Mobile device choices: What types of devices should be allowed into the workplace and which ones should not?
![]() IT enablement of new applications: How would new applications being developed by IT be enabled access from mobile devices?
IT enablement of new applications: How would new applications being developed by IT be enabled access from mobile devices?
![]() Mobile security: What type of security needs to be enforced on the mobile devices, and what types of threats should they be protected from?
Mobile security: What type of security needs to be enforced on the mobile devices, and what types of threats should they be protected from?
![]() Granular access control: What type of VPN access should be enforced on the mobile devices?
Granular access control: What type of VPN access should be enforced on the mobile devices?
Figure 3-1: Mobility challenges in the enterprise.
Who moved my application?
Along with rapid mobile device innovation, there are changes happening on the application side as well. With an increasing number of applications being developed or used within the corporate workplace, the economics of cloud computing are beginning to resonate with enterprises. It has become cost-effective for many enterprises to move certain applications to the cloud, from earlier deployments on physical servers in their data centers.
It is now common to hear examples of enterprises deploying their applications in private cloud or public cloud infrastructures:
![]() Private cloud: An environment hosted within enterprise premises, but managed and operated by a different vendor, such as a service provider.
Private cloud: An environment hosted within enterprise premises, but managed and operated by a different vendor, such as a service provider.
![]() Public cloud: An environment that is hosted, managed, and operated in a data center accessible to the general public. Applications such as Gmail, Google Apps, and Amazon S3 are examples of public clouds.
Public cloud: An environment that is hosted, managed, and operated in a data center accessible to the general public. Applications such as Gmail, Google Apps, and Amazon S3 are examples of public clouds.
As applications move to the cloud, access to them is often facilitated by simple web browsers. This makes access from smartphones easier, but more challenging for the enterprise. No matter where the application is hosted, you need to secure access to it and allow access to only those users whose roles permit it. Managing access policies when you own the application and the server it runs on is relatively simple. But managing access to publicly hosted applications on employees’ personal mobile devices is a different proposition.
Enforcing access control to applications has to depend upon the user’s privileges and possibly change depending upon what device or location the user is connecting from. You may want to consider limiting the users’ privileges to just e-mail access when they are using that latest new gadget in the market, but grant them full network access — including application access — while connecting from their corporate laptop computers.
Updating your mobility policies
To keep up with today’s environment, you need to update your mobility policies as well as think about supporting more than one device platform. Here are some of the areas in which to consider modifying your current mobility policy and ways that you can do it:
![]() Current policy: You have a single-device policy; only one device is corporate-approved.
Current policy: You have a single-device policy; only one device is corporate-approved.
Solution: Evolve to a multiplatform and multivendor policy, allowing devices of various platforms to access your corporate data. Allow more employee choice, while at the same time protecting your network. Explore mobile device management (MDM) solutions that support multiple mobile platforms, including Apple iOS, Google Android, Windows Mobile, Nokia Symbian, and BlackBerry.
![]() Current policy: Your IT department manually downloads software to each mobile device, thereby increasing the deployment costs of pushing software to mobile devices.
Current policy: Your IT department manually downloads software to each mobile device, thereby increasing the deployment costs of pushing software to mobile devices.
Solution: Explore solutions that allow the user to download software, such as the VPN application, from an app store without needing IT to intervene.
![]() Current policy: You deploy endpoint security only for Windows.
Current policy: You deploy endpoint security only for Windows.
Solution: This is no longer a sufficient security solution. Look for solutions that can protect mobile devices from malware, viruses, and other threats. For more information, be sure to read Chapter 6, which describes the types of threats from which you should protect these devices, and the solutions that offer the appropriate form of protection.
![]() Current policy: You have application policies in place only for Windows.
Current policy: You have application policies in place only for Windows.
Solution: Most enterprises have systems in place that can deploy applications to Windows PCs. You need to scale (adapt) this ability to mobile devices as well, to manage and control the apps that are installed on them. Explore solutions that give the ability to restrict apps on mobile devices to a list that you can manage.
![]() Current policy: You have no loss and theft-prevention policy for mobile devices.
Current policy: You have no loss and theft-prevention policy for mobile devices.
Solution: Mobile users are vulnerable to losing valuable data on mobile devices when those devices are lost or stolen. Many enterprises lack the policies to mitigate the risk of losing sensitive data on such devices. Look for solutions that allow you to take immediate preventive action on lost or stolen devices. Actions include remotely locating a device via GPS, remotely setting off an alarm, or remotely wiping selective device contents, such as personal data or corporate data, or both.
Adapting to the New Challenges of Mobile Devices
Most enterprises today have designed mobility policies centered around the usage of just one type of corporate device, which in many cases happens to be the BlackBerry. Some have recently adapted to include popular Apple devices in their corporate policy as well. As you ponder migrating from this model to a more flexible one, supporting many of the latest devices, here are the aspects of mobility policies you should revisit:
![]() Protecting mobile devices from malware and viruses: This should be the most fundamental requirement for allowing any device to access e-mails, applications, and data on your corporate network. No device running any kind of malware should be allowed onto your corporate network. Protecting the devices is paramount to protecting your own network from attacks originating from such devices.
Protecting mobile devices from malware and viruses: This should be the most fundamental requirement for allowing any device to access e-mails, applications, and data on your corporate network. No device running any kind of malware should be allowed onto your corporate network. Protecting the devices is paramount to protecting your own network from attacks originating from such devices.
Part of preparing your network for mobile devices is having the means to protect all the mobile devices on your network from malware, viruses, and other threats. Key items here include installing endpoint security software (software to protect the network when accessed remotely), ensuring that the software remains updated with the latest virus signatures, and ensuring that you can deploy this on the latest devices hitting the market.
![]() Remotely controlling device security policies: The ability to remotely set device policies (including password policies, inactivity timers, application policies, and so on) enables you to control and change device policies from a central application on your network.
Remotely controlling device security policies: The ability to remotely set device policies (including password policies, inactivity timers, application policies, and so on) enables you to control and change device policies from a central application on your network.
Imagine you log on to a management console within your network and set a new password policy, requiring users to have a certain password strength. This policy should then propagate to all the connected mobile devices in your network, requiring all users to conform to your new password policy.
Other items in this area include planning for backing up and restoring corporate data on the device, encrypting sensitive content, controlling the types of applications installed on the device, and taking action when the device is lost or stolen.
![]() Enforcing granular access control for users connecting from mobile devices: After you’ve put a plan in place to secure mobile devices, think about what types of applications you want users to be able to access from their mobile devices, and for what groups or users. For example, you should grant application access only to those users who absolutely need access to those applications. Granular access control refers to policies that control access to finance-related applications only to your corporate finance group, and HR applications only to the HR group, and so on. Managing and enforcing granular access to applications and data are critical for a successful mobile policy implementation.
Enforcing granular access control for users connecting from mobile devices: After you’ve put a plan in place to secure mobile devices, think about what types of applications you want users to be able to access from their mobile devices, and for what groups or users. For example, you should grant application access only to those users who absolutely need access to those applications. Granular access control refers to policies that control access to finance-related applications only to your corporate finance group, and HR applications only to the HR group, and so on. Managing and enforcing granular access to applications and data are critical for a successful mobile policy implementation.
Sophisticated smartphones can be used to access corporate e-mail, web-based applications on browsers such as the intranet, or even client-server applications such as Oracle or SAP. You might want to consider which of these applications you are willing to enable on mobile devices, and for which users.
This also includes enforcing strong authentication and authorization policies for users when they log in from mobile devices. Ideally, you want to enforce the same authentication methods from mobile devices, including multifactor authentication (authentication based on two or more factors), as you do on regular laptop or desktop computers.
We discuss these areas of your mobility policy in more detail in the sections that follow.
Protecting mobile devices from malware
Applications are deployed to mobile devices such as tablets and smartphones from respective app stores or markets. The number of app downloads from such markets now ranges in the billions on smartphones worldwide.
When your company’s employees use third-party apps for applications like online banking, checking corporate e-mail, and playing interactive games with their friends, these devices become appealing targets for hackers. Because many of these devices run relatively new operating systems like Android, Symbian, and iOS, hackers fancy their chances of exploiting platform vulnerabilities to steal information from these devices.
Market research shows a rapidly increasing occurrence of mobile malware from 2008 to 2010. This increase is in line with the corresponding rapid increase in device options available in the market. So, if you are going to allow smartphones to access your critical corporate data, it would be prudent to plan for a scalable (adaptable) and reliable way of protecting them and your network from malware.
There are two broad options available for providing threat protection on smartphones and other mobile devices:
![]() Client-based mobile endpoint security software
Client-based mobile endpoint security software
![]() Cloud-based software
Cloud-based software
We discuss these options in more detail in the following sections.
Client-based mobile endpoint security software
In this type of deployment, an actual client software app protects the device from viruses, malware, spam, and other threats. This is similar to how client endpoint software is deployed on regular Windows computers. Software available for mobile devices is usually designed to run in the background, scan the device periodically for threats, and introspect (analyze) data received on the device for viruses and malware. Such software typically alerts the user when a threat is detected, and automatically quarantines or deletes the source of the threat as well. Symantec, Trend Micro, F-Secure, McAfee, and Juniper offer client software–based mobile security solutions.
![]() Downloaded via the app store by the users themselves or deployed via a mobile device management system by the IT department.
Downloaded via the app store by the users themselves or deployed via a mobile device management system by the IT department.
![]() Deployed automatically over the air (OTA) from a server that the device connects to. This approach typically happens with no user intervention.
Deployed automatically over the air (OTA) from a server that the device connects to. This approach typically happens with no user intervention.
Virus signatures are typically updated in a central system periodically. Then devices either download the signatures at regular intervals or they’re pushed out to devices periodically.
With client-based software, there are some basic things to watch out for while shopping for a suitable mobile endpoint security solution:
![]() Determine what device resources are used by the software. You certainly do not want to deploy client software that drags down the performance of the device. So look for the following attributes while narrowing your options:
Determine what device resources are used by the software. You certainly do not want to deploy client software that drags down the performance of the device. So look for the following attributes while narrowing your options:
• Size of the client software: Needless to say, the smaller the client, the better.
• CPU utilization: The software should run as unobtrusively as possible, reducing any impact on the user’s activity on the device. If running the application slows down the entire device, then it is apparent that the application is taking up a lot of system resources to function.
• Memory utilization: The software should consume as little memory as possible. Again, like the impact on CPU utilization, when an application consumes too much memory, it drags down the performance of the device in general.
![]() Avoid software that is ported to a mobile platform from Windows. Beware of software options that are essentially desktop endpoint software ported for the mobile platforms. Porting in the software development world refers to the process of customizing software for a different platform than what the software was initially designed for.
Avoid software that is ported to a mobile platform from Windows. Beware of software options that are essentially desktop endpoint software ported for the mobile platforms. Porting in the software development world refers to the process of customizing software for a different platform than what the software was initially designed for.
Several vendors offer endpoint security software for Windows platforms. When you shop for mobile endpoint security software, make sure that the mobile endpoint software was designed from the ground up for each specific mobile platform.
Cloud-based security
In this type of deployment, the actual threat protection happens in the cloud or centralized data center of the endpoint software vendor. Traffic to and from the mobile devices is redirected on the device to the cloud for malware detection.
Typically, this option includes no client-side software and relies instead on each application to take appropriate action when a threat is detected. For example, content downloaded from websites is inspected in the cloud before it’s delivered to the mobile device browser. If a threat is detected in the web content, the cloud service indicates so, and the browser displays an appropriate message to the user. Zscaler, ScanSafe (now owned by Cisco), Symantec, and McAfee offer cloud-based mobile security solutions.
If this cloud model of endpoint security is what you need, make sure you analyze the following aspects of the solution:
![]() Security between the mobile device and the cloud service: If both Internet traffic and corporate traffic (such as e-mail and intranet browsing) are sent to the cloud, you should make sure that the traffic is flowing over a secure tunnel. You don’t want anyone sniffing on the traffic that may carry sensitive data. Be sure to check with the cloud service vendor regarding the security between the mobile device and the cloud service.
Security between the mobile device and the cloud service: If both Internet traffic and corporate traffic (such as e-mail and intranet browsing) are sent to the cloud, you should make sure that the traffic is flowing over a secure tunnel. You don’t want anyone sniffing on the traffic that may carry sensitive data. Be sure to check with the cloud service vendor regarding the security between the mobile device and the cloud service.
![]() Latency introduced by the cloud service: If data sent and received by the device hits the cloud service before heading to its destination, make sure that the cloud service is rapid in its response. Otherwise, the user experience on the mobile device will be adversely affected. The latency is apparent from the user experience when the cloud service is enabled, compared to the situation when it is not enabled. If the cloud service adds a lot of latency, then the user’s browsing and other application access are slower.
Latency introduced by the cloud service: If data sent and received by the device hits the cloud service before heading to its destination, make sure that the cloud service is rapid in its response. Otherwise, the user experience on the mobile device will be adversely affected. The latency is apparent from the user experience when the cloud service is enabled, compared to the situation when it is not enabled. If the cloud service adds a lot of latency, then the user’s browsing and other application access are slower.
Managing device policies remotely
Now that you’ve thought about securing the mobile devices on your network from threats like viruses and malware, it’s time to plan for remotely enforcing policies for device management or security.
No matter how powerful the endpoint security software is on the device, the following types of user behavior pose direct risks of losing valuable data on the device:
![]() Not locking the device
Not locking the device
![]() Not setting a secure password (for example, having “1234” or “abc123” for a password!)
Not setting a secure password (for example, having “1234” or “abc123” for a password!)
![]() Storing passwords in third-party apps, such as online banking apps or an Oracle app that can directly access the latest sales pipeline
Storing passwords in third-party apps, such as online banking apps or an Oracle app that can directly access the latest sales pipeline
You get the idea. We’re talking about device security etiquette, about taking the simple yet often-ignored steps for protecting vital data stored on the device.
There are two broad categories of actions you will need to take on mobile devices in your network:
![]() Mobile device management: Remotely managing the devices, including enforcing the need for a passcode or deploying a set of corporate-approved mobile apps to them.
Mobile device management: Remotely managing the devices, including enforcing the need for a passcode or deploying a set of corporate-approved mobile apps to them.
![]() Remote device security: Remotely securing the devices, including taking preventive action when the devices are lost or stolen.
Remote device security: Remotely securing the devices, including taking preventive action when the devices are lost or stolen.
Configuration and application management
Similar to how you deploy software systems to manage desktop and laptop computers, you need to think of software that can manage the diversity of mobile devices available in the market.
For example, the BlackBerry Enterprise Server is an excellent candidate, but it falls short on one major area: It is a solution only for the BlackBerry. It doesn’t help manage other types of devices, such as those running iOS, Android, or Windows Mobile.
Remote device management policies typically include configuration management and application management as follows:
![]() Configuration management: Involves deploying IT-approved software versions of supported mobile platforms. It is ideal to find a single solution that can manage the configuration for a heterogeneous mix of mobile devices. If you cannot find a single solution that can do so, try to minimize the number of systems you would need to deploy. Configuration management includes things like managing the OS version of mobile devices and application and security patches, or supporting any other desired corporate policy.
Configuration management: Involves deploying IT-approved software versions of supported mobile platforms. It is ideal to find a single solution that can manage the configuration for a heterogeneous mix of mobile devices. If you cannot find a single solution that can do so, try to minimize the number of systems you would need to deploy. Configuration management includes things like managing the OS version of mobile devices and application and security patches, or supporting any other desired corporate policy.
![]() Application management: Involves controlling the apps deployed on mobile devices. If you’re worried about mobile devices on your network running apps that you’ve never heard of or apps that are known to be insecure, plan for deploying application control policies to those devices. Such policies include viewing an inventory of all applications installed on devices in your network and being able to view the details of each application and the devices running it. You should also be able to select a particular application and either uninstall it from users’ devices or send messages to users that those applications are not corporate-approved and must be uninstalled.
Application management: Involves controlling the apps deployed on mobile devices. If you’re worried about mobile devices on your network running apps that you’ve never heard of or apps that are known to be insecure, plan for deploying application control policies to those devices. Such policies include viewing an inventory of all applications installed on devices in your network and being able to view the details of each application and the devices running it. You should also be able to select a particular application and either uninstall it from users’ devices or send messages to users that those applications are not corporate-approved and must be uninstalled.
This is similar to certifying certain applications as safe applications, depending upon the criteria of your choice. This could enable you, for example, to deem certain apps forbidden within your network, or restrict all mobile apps to a predefined list you come up with. If you desire some level of application enforcement and control, be sure to evaluate vendors that can restrict applications installed on mobile devices to a predefined set.
![]() Backup and restore: Make sure you think of a way that you can back up contents of mobile devices running in your network. This is as important as backing up contents of desktop and laptop computers. Having a sound system in place for this critical function could make a great difference in improving the productivity of mobile device users, who should be able to replace devices easily if you back up their data.
Backup and restore: Make sure you think of a way that you can back up contents of mobile devices running in your network. This is as important as backing up contents of desktop and laptop computers. Having a sound system in place for this critical function could make a great difference in improving the productivity of mobile device users, who should be able to replace devices easily if you back up their data.
This function enables backing up data from employees’ mobile devices and allows seamless restoration of data, potentially to a replacement device running a different mobile platform. If your enterprise IT can do so, it’s a valuable service for employees, as well as an assurance to you that users will be productive immediately after moving from one device to another. This is like replacing laptop computers for users, with their data restored immediately to the new laptop.
Chapter 12 describes the backup and restore policies in more detail, including the selective backup of certain content on corporate-issued versus employee-owned devices.
Security of lost and stolen devices
There are various actions you need to take when an employee reports a lost or stolen device. You should be able to do the following:
![]() Remote lock: Remotely lock the device so nobody can log in to it.
Remote lock: Remotely lock the device so nobody can log in to it.
![]() Remote alarm: Remotely set off an alarm so that the device makes itself heard!
Remote alarm: Remotely set off an alarm so that the device makes itself heard!
![]() Remote location: Remotely find the device using its GPS capabilities.
Remote location: Remotely find the device using its GPS capabilities.
![]() Remote wipe: If all else fails, and if you are sure the device is lost, you should be able to wipe the device clean of all or selective data.
Remote wipe: If all else fails, and if you are sure the device is lost, you should be able to wipe the device clean of all or selective data.
So protection against loss and theft is an example of securing devices remotely when corporate data is at risk of being lost on them. Other types of security policies include setting password policies, such as the required strength of the password, or setting an inactivity timer to automatically lock the device.
Enforcing granular access control
If you’ve taken the advice we give earlier in the chapter, you’ve begun to devise a plan to secure mobile devices from malware and viruses, and you’ve also planned on managing these devices remotely, including being able to remotely wipe or lock them. The third step of ensuring that these devices are corporate-ready is to enforce granular access control on users connecting from these devices.
You may not want to enable all mobile device users to have the same access privileges as they do on their regular Windows or Mac computers. For example, you may not want all mobile users to have full network access, including access to your corporate customer relationship management application that tracks the latest sales deals. You may want to enable only access to e-mails or certain web-based applications to some groups of users.
Another key item of access control is the authentication policy itself. To allow users to access corporate stuff from mobile devices, you should not relax any security policies of enforcing strong authentication on these users. You should think of the authentication methods to enforce on mobile device users and the backend systems you will need in place accordingly.
Finally, the key to a scalable mobile infrastructure is to have a single place of managing all your policies of access control, authentication, and policy enforcement. If you have a VPN solution in place, you probably already have policies in place that control the access to applications to specific groups of users. This is the key piece that binds it all together: How should you leverage the policies on such a centralized VPN system to mobile security?
The following sections discuss the key elements of implementing a flexible access control solution for mobile devices.
Authenticating users
The most fundamental requirement to allowing mobile devices within the enterprise is to have a solution in place to authenticate the users of those devices. It is common to use the following methods to authenticate mobile device users:
![]() Authenticate using username and password.
Authenticate using username and password.
![]() Authenticate using a certificate deployed to the mobile device.
Authenticate using a certificate deployed to the mobile device.
![]() Authenticate using one-time passwords or security tokens. One-time passwords expire after a single usage, thereby preventing hackers from attempting to use a password after it has already been used once. Such passwords are usually deployed using tokens, either hardware dongles from vendors like RSA or software applications that issue a unique password every time.
Authenticate using one-time passwords or security tokens. One-time passwords expire after a single usage, thereby preventing hackers from attempting to use a password after it has already been used once. Such passwords are usually deployed using tokens, either hardware dongles from vendors like RSA or software applications that issue a unique password every time.
![]() Authenticate using smart cards.
Authenticate using smart cards.
Many enterprises implement dual-factor or multifactor authentication systems, which means that multiple authentication methods are cascaded one after the other, to enforce strong authentication. For example, a user may be prompted to authenticate using her username and password, and then prompted again to authenticate using her one-time password and PIN.
If you need to enforce certificate authentication on mobile devices, you need to look for management solutions that can deploy certificates to devices at scale. Look for such capabilities in the management systems you already have in place for deploying certificates to Windows PCs, for example. Several existing management solutions have recently added mobile features to manage certificate deployments on all types of devices.
Authorizing users to see only the data they are allowed to see
Once users authenticate successfully from mobile devices, allow them to access only the data or applications that you want them to. You may not want all users to be able to access any or all types of applications by default. Many mobile device users want access to only corporate e-mail, whereas others use these devices to check the intranet web pages. Yet another type of users, power users, want to log in to their remote desktops and remotely operate their desktop applications from their mobile devices.
Here is a broad categorization of application types that you may want to restrict access from or allow access to, depending on the group that a user belongs to:
![]() Web-based applications: Users can access intranet pages from mobile device browsers.
Web-based applications: Users can access intranet pages from mobile device browsers.
![]() E-mail: Users can send and receive e-mail and schedule meetings on the calendar.
E-mail: Users can send and receive e-mail and schedule meetings on the calendar.
![]() Full network access: Users can access not only web-based apps and e-mail but also any other corporate client apps on the mobile device downloaded from an app store.
Full network access: Users can access not only web-based apps and e-mail but also any other corporate client apps on the mobile device downloaded from an app store.
You can allow mobile users to access web-based applications and e-mail without letting those devices into the corporate network, such as by assigning them an IP address within the network. Web-based applications can be accessed by most sophisticated mobile browsers supporting SSL encryption. E-mail access can be enabled via Microsoft Exchange or ActiveSync, which also does not need the mobile device to have an IP address within the network. Full network access, on the other hand, needs the device to be within the corporate network. This type of access allows the user to access pretty much any application within the network, just as if they were in the office. Accordingly, your security policies need to be at their strictest for granting full network access.
Integrating with existing VPN policy infrastructure
If you allow your users VPN access to the corporate network, you likely already have a policy in place that describes what types of users are allowed access, including the applications that are allowed to be accessed remotely. VPN policies are typically enforced on a VPN gateway device at the perimeter of the network, with access for external users.
![]() Wide range of supported mobile platforms for corporate access, such as these:
Wide range of supported mobile platforms for corporate access, such as these:
• Apple iOS
• Google Android
• Windows Mobile and Windows Phone 7
• Nokia Symbian
• BlackBerry OS
• Others such as HP Web OS
![]() Wide range of supported authentication methods:
Wide range of supported authentication methods:
• Username and password–based
• Certificate-based
• Multifactor authentication (for example, cascading username and password-based authentication followed by certificate-based authentication, or vice versa)
• VPN on demand (setting up a VPN tunnel automatically when the user attempts to access a corporate resource)
![]() Ability to assign role-based access to users, depending on their role within the enterprise
Ability to assign role-based access to users, depending on their role within the enterprise
![]() Ability to assign granular access to any or all of the following types of applications:
Ability to assign granular access to any or all of the following types of applications:
• Web-based intranet content
![]() Full network access
Full network access
VPN gateways are typically either dedicated VPN appliances that enable IPsec or SSL VPN access, or firewall devices that include VPN functionality in addition to a host of other security features. In either case, most VPN solutions should have a well-defined policy infrastructure to define role-based access to corporate data and applications.
Depending upon your corporate policy and need for application control, you should choose between an IPsec VPN solution or an SSL VPN solution. Here is some information that can help you choose between the two:
![]() IPsec VPN solutions: Enable full network access to remote users. That means users who connect over traditional IPsec VPN tunnels are granted full network access to the corporate network, including getting an IP address within the network.
IPsec VPN solutions: Enable full network access to remote users. That means users who connect over traditional IPsec VPN tunnels are granted full network access to the corporate network, including getting an IP address within the network.
![]() SSL VPN solutions: Usually allow more granular access control, enabling you to control application access to any of all of the various application types: web-based, e-mail, or full network access.
SSL VPN solutions: Usually allow more granular access control, enabling you to control application access to any of all of the various application types: web-based, e-mail, or full network access.
Choose a solution that allows you to manage mobile access control policies on this kind of a centralized VPN system that already manages remote access policies. It would be counterproductive (and very costly!) to manage duplicate or redundant policy systems, one for traditional remote access from home PCs and another for mobile devices.
To integrate your existing VPN policies with mobile access control, here are the key decision areas you need to consider:
![]() Your mobile security solution: Depending upon what security features you need on your users’ mobile devices, choose a solution that spans a broad range of mobile platforms. As discussed earlier, you may choose any or all of the security features to enforce on mobile devices, including protection against viruses, malware, Trojans, and spam.
Your mobile security solution: Depending upon what security features you need on your users’ mobile devices, choose a solution that spans a broad range of mobile platforms. As discussed earlier, you may choose any or all of the security features to enforce on mobile devices, including protection against viruses, malware, Trojans, and spam.
![]() Your endpoint security posture (level of risk): You may already have an endpoint security solution on your VPN gateway allowing network access only to devices that have a sufficient security posture. This policy may include checking for installed antivirus or antimalware software, or verifying that the device is a corporate-assigned computer before granting VPN access. You may want to extend this policy to mobile devices, allowing VPN access only to those mobile devices that are secured by the security software of your choice.
Your endpoint security posture (level of risk): You may already have an endpoint security solution on your VPN gateway allowing network access only to devices that have a sufficient security posture. This policy may include checking for installed antivirus or antimalware software, or verifying that the device is a corporate-assigned computer before granting VPN access. You may want to extend this policy to mobile devices, allowing VPN access only to those mobile devices that are secured by the security software of your choice.
![]() Your access control policies: The access control policies enforced on the VPN appliance should follow the user, meaning that no matter where the user logs in, the policies applicable to that user must be enforced. Choose a VPN solution that can enforce a single set of access control policies, irrespective of where users connect from, or what devices they use to connect. Having a single set of policies that span across device and application types will make your life simpler.
Your access control policies: The access control policies enforced on the VPN appliance should follow the user, meaning that no matter where the user logs in, the policies applicable to that user must be enforced. Choose a VPN solution that can enforce a single set of access control policies, irrespective of where users connect from, or what devices they use to connect. Having a single set of policies that span across device and application types will make your life simpler.
![]() Easy enforcement of mobile device security as an endpoint posture assessment check, prior to granting VPN access to users
Easy enforcement of mobile device security as an endpoint posture assessment check, prior to granting VPN access to users
![]() Easy enforcement of access control policies that are already defined on the VPN gateway
Easy enforcement of access control policies that are already defined on the VPN gateway
![]() Easy integration into the management capabilities of the VPN solution, thereby offering insights into the mobile device inventory and assets within the enterprise
Easy integration into the management capabilities of the VPN solution, thereby offering insights into the mobile device inventory and assets within the enterprise
