The Hard Part
SUMMARY
For a business or other organization, deciding to use a cloud implementation and then choosing a cloud service model and how the cloud will be deployed are difficult problems. The decision depends on the role of the cloud service within the organization and the relationship between the cloud consumer and provider and the service provided. The decision is financial, managerial, and technical. It requires an understanding of what a cloud is, the benefits from cloud deployments, and the risks and obstacles to a successful deployment. And it requires an understanding of the unique requirements of managing a service deployed on a cloud.
Individual consumers are in a different position. Cloud services are usually offered to consumers as complete services that they either accept or reject. They may seem to be less concerned about the details of the implementation. However, the choice to use a service is often an architectural choice and means placing some aspect of their affairs into the hands of a third party, whether the consumer realizes it or not. To be an informed consumer, some knowledge of the underlying architecture and management is required.
This chapter addresses the concerns of both businesses and individual consumers.
What Is a Cloud?
Like any service, two groups participate in cloud services: consumers and providers. ITIL defines service providers as suppliers of outcomes that consumers want while avoiding the risk or direct costs of producing the outcome themselves. Providers generate outcomes that consumers are willing to pay for.1 For consumers, the alternative to using a service provider is to do the job themselves. In the case of clouds, providers supply computing services. These services can take several forms. Cloud service models are a high-level classification of cloud services based on the type of resources the cloud provider offers.
NIST CLOUD DEFINITION
The National Institute of Standards and Technology (NIST) published a definition of cloud computing2 in 2011. The industry has widely accepted this definition although any definition in the lively and developing cloud arena dates quickly.
According to NIST, cloud computing is a model for easy and wide network access to computing resources that can be rapidly configured, provisioned, and released.
The NIST definition lists a number of characteristics of cloud computing, including the following:
- Self-service: A cloud consumer can provision cloud services without the intervention of the cloud provider.
- Broad access: Connecting with a cloud does not require a private network connection or special, dedicated devices.
- Resource pools: The provider presents resources to the consumer as an undifferentiated pool that can be configured and provisioned by the consumer’s request.
- Elasticity: The resources used by the consumer can be expanded and contracted automatically to respond to varying consumer loads. The resources appear unlimited to the consumer.
- Metered service: Service use is metered, and consumers are charged for the services used.
NIST delineates three service models.
- Software as a Service (SAAS)
- Platform as a Service (PaaS)
- Infrastructure as a Service (IaaS)
NIST also lists four deployment models.
- Private cloud
- Community cloud
- Public cloud
- Hybrid cloud
Cloud Service and Deployment Models
The NIST cloud definition addresses several service and deployment models for clouds. (See the “NIST Cloud Definition” sidebar.) Service models describe the service that is provided by the cloud. Deployment models describe the relationships between the consumers and providers of the cloud.
Service Models
NIST defines three service models that are based on three basic types of services: infrastructure, platform, and software. The standard NIST definition of cloud computing is well known, and most cloud practitioners know the definitions and classifications well. In the intervening years since NIST published the definition, the field has evolved. Many cloud services and implementations have appeared, and the number of “aaS” acronyms has burgeoned. These new services are specializations or extensions of the basic NIST models. See Figure 5-1.

Figure 5-1. IaaS, PaaS, and SaaS each address a different level of IT management
Infrastructure as a Service
The most basic cloud service is Infrastructure as a Service (IaaS), which offers virtual computers, storage facilities, and networks to consumers.3 An IaaS architecture is at the bottom of most PaaS cloud architectures. SaaS architectures are sometimes based on an IaaS architecture and sometimes not. See Figure 5-2. Consumers use these virtual cloud resources as if they were physical hardware on their own premises. The consumer acquires software and installs it on the cloud virtual devices and then administers running the software. This software includes utilities such as database management software and HTTP servers as well as applications. Some IaaS providers offer preconfigured machine images that already have some software installed, eliminating some of the effort involved in standing up a system on an IaaS platform. Some software vendors offer their software in packages ready to install as complete or partial systems on designated IaaS provider clouds.

Figure 5-2. A typical IaaS architecture
Platform as a Service
A Platform as a Service (PaaS) cloud provider supplies more than bare virtual hardware to the consumer. In addition to virtual infrastructure, the PaaS provider offers software utilities and services. For example, they may offer development environments that supply design tools, specialized code editors, compilers, testing tools, and a framework for moving the resulting production application into production on the PaaS cloud. Utilities such as databases and load balancers are another frequent offering. The range of platform facilities offered by PaaS providers is varied and extensive. However, the core of an application running on a PaaS cloud is usually still owned and maintained by the consumer. For example, the Microsoft Azure PaaS platform supplies several utilities, including SQL Server. Azure consumers can code applications on Azure and use the included SQL Server instance, but the code is theirs, and they must maintain it themselves.
Software as a Service
Software as a Service (SaaS) moves the ownership and administration of software applications to the cloud provider. The provider supplies the software, manages the underlying hardware (or delegates the hardware to an IaaS or PaaS provider), and administers system backups, patches, and updates. Aside from a limited consumer-specific configuration that the consumer must perform, the consumer is not involved in provisioning, configuring, or maintaining the service. Some SaaS applications support customization, but SaaS customization is typically much more limited than traditional enterprise application customization, which sometimes is so extensive that the customer writes some application code. To use a SaaS service, the consumer uses the application and usually pays based on usage. Some SaaS are offered without direct charge. These are often stripped-down versions meant to attract customers to full-featured pay versions or other paying products. Some SaaS applications, like Facebook, are offered without charge because the provider wants to collect information on the clients or use the application as a platform for advertising or similar activity.
Other Service Models
Software developers and providers have not hesitated to expand and specialize the three NIST service models. A specialized cloud service that home consumers are likely to use is Storage as a Service. A typical storage service will provide storage resources, reminiscent of an IaaS service and an SaaS interface. The result is an easy-to-use service that backs up data to a remote site and makes the data available anywhere with an Internet connection. This is convenient for users who use several different devices but want to access the same data on each device. A music service like Apple iTunes is a form of Storage as a Service in which a consumer stores specialized data, audio files containing recorded music, and can access their stored files from many different devices through an Internet connection.
For businesses, Storage as a Service often takes the form of a remote backup service that performs backups and stores the data or a cloud storage facility. Other forms of business Storage as a Service is storage of data that is not frequently needed but must be retained. Unlike home consumers, business consumers are usually more interested in secure storage of large quantities of data rather than convenient access from multiple devices and locations. Of course, bring your own device (BYOD) and off-premises workers have added multidevice access requirements in many business situations.
Other service models that have appeared are Network as a Service, Backup as a Service, IT as a Service, and many others. Each is a specialization, extension, or combination of the basic NIST models. The rapid proliferation of service models is a sign of the growth and entrenchment of the cloud concept.
Deployment Models
Clouds are also classified by deployment model. Ownership and consumer groups characterize the public, private, and community deployment models. The fourth model is different and is discussed next. The public cloud provider that offers cloud services to the public is at one extreme in the deployment spectrum. Private clouds are at the other end of the spectrum in which an organization owns and offers a cloud service limited to its own organization. There are advantages and disadvantages to each deployment model. See Figure 5-3.

Figure 5-3. Private, community, public, and hybrid clouds are NIST deployment models
Public clouds are often thought of as the archetype for clouds. They probably are closest to the notion of utility computing that has been discussed almost since computers began. Utility computing was discussed in detail in Chapter 2. A public cloud resembles a public utility like an electricity supplier. Both deal directly with the public and are open to all comers. Public clouds differ from classical utilities in that they are not regulated like many public utilities, and although the services of each public cloud are similar to other public clouds, the services are not as interchangeable as you usually expect from commodities. When you fuel your car from different gas stations, you do not expect to adjust your car’s engine to accommodate the new gasoline or connect a hose adapter to fill your car’s tank. Public clouds are open to all consumers willing to accept the terms of use, but consumers cannot now expect switching from one public cloud to another to be transparent. Some adjustment, perhaps substantial changes, may be required.
Market forces may compel public clouds to evolve to be closer to utilities in the future. Standardization efforts, such as the Distributed Management Task Force (DMTF) Cloud Infrastructure Management Interface (CIMI),4 promise to speed this process. OpenStack5 is an open source project with wide support in the industry. It appears poised to become the default cloud implementation stack, just as Linux has become the default non-Windows operating system.
For most public cloud users, metered usage is an important characteristic of a public cloud shared with the classic utility model. If cloud resources sit idle, public cloud users do not expect to pay for the resources, just as homeowners do not expect to pay for electricity they do not use.
For all their advantages, the jump to deploying on a public cloud is not easy for many enterprises. Security and governance issues can prevent delegating responsibilities to third-party public cloud providers. Many enterprises are cautious and want to test the cloud waters before they commit to relying upon a cloud provider. A private cloud is often a good alternative. In its simplest form, a private cloud is built on the organization premises, often by the IT department, perhaps from equipment already owned by the organization. If the goal is IaaS, the equipment is configured as a cloud by isolating it from the rest of the environment and then providing a virtualization layer and a set of utilities that provide an interface for creating, configuring, controlling, and metering virtual infrastructure on the designated cloud hardware. The interface to the cloud is offered to the rest of the organization. There may be a chargeback system, only usage reports, or no metering at all.
Metering in a private cloud owned and operated by a single organization is not a necessity, but it can be useful. When business units or departments are aware of their computing resource usage, they are better able to gauge the efficiency their usage and become more cost effective.
IaaS is not the only service model that private clouds can support. A SaaS application implemented on a private cloud can provide easy access and maintenance for applications used across an organization. PaaS deployed on a private cloud can be particularly well suited to providing flexibility for software development and quality assurance testing.
Private clouds do not have to be built by the private consumer or hosted on the owner’s resources. Third parties can operate private clouds on an organization’s premises or operate them on premises not owned by the cloud owner. The necessary and sufficient characteristic that differentiates a private cloud from other deployment models is that it is not shared with other organizations or unrelated consumers.
Community Cloud
A community cloud is an intermediate deployment model between public and private clouds. Similar to a private cloud, the consumers of a community cloud are limited, but instead of limiting consumption to consumers from one organization, a community cloud is offered to members of an associated group of organizations. Often, community clouds are owned by consortiums, such as groups of educational or scientific institutions. Like private clouds, they can be built and hosted by third parties.
A hybrid deployment model is not an ownership model like public, private, and community clouds. A hybrid cloud is defined by a relationship with other clouds. A typical example of a hybrid cloud is cloud bursting, in which one cloud reaches capacity for some activity and “bursts” by transferring some of the load to a different cloud. The load may stem from any activity.
A common hybrid cloud bursting scenario supports a large web site that is heavily used for short periods, such as a site that appears in a Super Bowl halftime ad. During or immediately after the ad, the site could get millions of hits, far more than normal load.6 The number of hits depends upon many factors and is hard to predict with any accuracy. One solution is to provision a server farm with enough capacity to handle the highest estimates, but a hybrid cloud presents a more elegant solution. The site starts out during the low-usage pregame period deployed on a single cloud implementation. As the hits increase, the first cloud bursts to a second cloud. If the number of hits soars beyond all but the most optimistic estimates, the system could burst to a third cloud. At that point, three clouds would be supporting the site. The second and third clouds are decommissioned when the demand diminishes. Flexibility and scalability are crucial to services that are offered to national or global consumers, and hybrid clouds are a way of providing flexibility and scalability with excess capital investment in infrastructure.
The ability to transfer between clouds characterizes hybrid clouds. Bursting is a popular example, but other hybrid clouds may not involve bursting. An application that has processes running on several separate clouds runs on a hybrid cloud. An application that runs on one cloud and stores data on another cloud is also running on a hybrid. An important requirement for hybrid clouds is for interfaces that support rapid and efficient transfer of loads, events, and data from cloud to cloud.
Cloud Benefits
The many benefits from cloud implementations justify the effort required for cloud service management. Individual consumers, small organizations, and large organizations benefit, although the benefits are not the same.
Separation of Consumer and Provider
One key to understanding the benefits of clouds is to understand the value of separating cloud consumers from providers into distinct roles. This separation is the essence of the concept of a service. Cloud services separate the consumers of a computing service, such as the users of an application, from the providers of a computing service, such as the system administrators who install and maintain the application. When an organization both uses and maintains an application, one group has to be organized and trained to support the application, and another, usually much larger, group has to be organized and trained to use the application; and infrastructure must be available to support the application. In some organizations, this may not be a problem because they have the resources to support the application efficiently.
Until the advent of clouds, organizations—especially startups and other small-to-medium businesses—had little choice: either administer complex and demanding applications or find less demanding alternatives, which were likely to be weak compromises. Today, cloud implementations are a viable and powerful alternative. Organizations can use SaaS management tools like sophisticated sales force and service desk management applications that they do not have the personnel or infrastructure to support. These applications used to be reserved for larger organizations. Using SaaS, these smaller organizations can skip ahead to large organization efficiencies while still small. In addition, these smaller organizations may be able to gain large organization efficiencies while forestalling the bureaucratization that restricts the agility of large organizations.
Larger organizations benefit also, but they have the option of implementing the service on their own premises in addition to a cloud implementation. In this, larger organizations have a range of choices. They can implement on IaaS and avoid ownership and administration of infrastructure but retain control of all the software. Organizations with in-house written applications or highly customized off-the-shelf applications often opt for IaaS. PaaS offers similar software flexibility, but some software utilities are handed off to the cloud provider. SaaS moves the most responsibility to the cloud provider and works best where there is little or no customization of the application. Often, when an organization is spread over a wide geographic area, a centralized cloud provider offers additional benefits because the implementation can be concentrated in a small area offering additional efficiencies.
The individual consumer also benefits from the separation of consumer and provider. It may seem odd to think this way, but until networking and network applications appeared, users were their own providers. Any resource they wanted to use had to be present on their personal computer. As networking became more prevalent, more resources came from the network. For example, network file servers and client-server applications were a way of providing resources to the consumer without the consumer owning the hardware or the complete software. Employees connected to a corporate network were the main beneficiaries of these remote resources.
For individual consumers, current cloud implementations are mainly an extension of the benefits of those that used to be limited to corporate networks. Instead of keeping terabytes of photographs and videos on personal hard drives, consumers today delegate storage to a cloud storage service, just as corporate users stored files on corporate file servers. Instead of having dozens of processors on their laptops, they play games using the banks of processors on a cloud implementation. The consumer now can consume cloud services in place of services they provide themselves. Typically, the SaaS nature of these services is transparent to consumers. It does not matter to them if an application runs on their tablet or phone or on a remote cloud. They only know that they are enjoying a service that they did not have before.
Consumers also benefit from IaaS and PaaS. The benefits are indirect and hidden but still important. The SaaS products used by consumers are often implemented on IaaS or PaaS clouds. For example, the popular entertainment streaming application Netflix is implemented on an IaaS public cloud, not on on-premises company servers. Because Netflix relies on a cloud provider with huge computing resources, Netflix subscribers can reasonably expect that they will have a pleasant and pause-free experience watching a movie at a peak time on a Saturday night.
Economic progress is often associated with specialization. When a person or an organization narrows its focus and becomes proficient at supplying a specific good or service that a supplier of many services supplied at lower quality or efficiency, the result is often improved quality and decreased cost. The specialist acquires tools and skills to perform the work quicker and better and can therefore offer a superior value for lower cost. When a vital good or service is supplied at dramatically improved quality or decreased cost, major changes may occur in the economy and society. For example, during the Industrial Revolution, many costs were lowered by the application of steam power to specialized manufacturing, replacing unspecialized village workshops. Consequently, economies changed, populations moved, and society was transformed.
Computing clouds are also specialization. The operator of a large public or community cloud can afford to develop skills and acquire equipment that one person or a single organization cannot. Large cloud installations are deployed in specialized data centers that are built for energy and computing efficiency. A large cloud operator can design and have manufactured special computers, storage units, switches, racks, and other gear to optimize their systems. They can design and implement high-speed interconnects between their computing units that may number in the hundreds of thousands. They can locate their data centers where energy and cooling costs are low. These efficiencies are not possible without the large scale that clouds achieve by supporting large numbers of consumers. At the same time, by specializing, the cloud suppliers develop the skills and assets necessary to scale to the levels that offer these efficiencies. By becoming specialized suppliers of computing capacity, cloud providers have, and continue to develop, expertise that would not otherwise exist.
Enterprise cloud consumers benefit from their own specialization. Each organization has its core capacities, skills, and assets that they alone possess and enable them to compete in their own business area. Management experts often urge businesses to focus on their core capacities and avoid investing in auxiliary efforts that do not offer competitive advantages. Using a cloud is one way that business can do this. Instead of developing IT expertise and investing in a large data center to track parts and inventory, an equipment manufacturer might decide to invest more in new product design and leave the data center infrastructure management to a cloud supplier.
In addition to specialization, the scale of clouds has benefits. A common problem in smaller datacenters is spare hardware capacity. Service desk systems provide a good example. They have hours of peak usage, perhaps one early in the week, a lesser peak near the beginning of the weekend, and monthly and yearly peaks when books are closed or other periods of elevated activity. These peaks are exactly the time when the service desk is most critical and has to be most reliable and perform best. In the past, organizations would buy a server or servers big enough to handle the largest expected load with an additional percentage of “headroom,” usually an additional 20 to 50 percent capacity. Most of the time, the server would run at below 20 percent of its total capacity. In other words, 80 percent of the investment would yield benefits only a few days a year.7
A private cloud helps avoid some of these sunk investments. If different applications have different peak periods, a private cloud that shares capacity among the applications allocates the spare capacity of one application to other applications that need it. If the organization happens to span time zones, they may be able to garner further efficiency.
A large public cloud is in an even better position. This supports the applications of a large number of consumers with all different consumption patterns and locations, which offers greater opportunities for load leveling and efficient utilization. In addition, large clouds, through economies of scale, have lower energy and equipment costs, and therefore large clouds, can operate more efficiently and reduce the cost of spare capacity.
Usage-based charges are financially beneficial to business in many ways. The benefits of being charged by the service used rather than the fixed cost of implementing and operating the service are clear. However, Chapter 4 discussed some of the difficulties in internal chargebacks for IT services in which chargebacks may increase rather than decrease when use of a service decreases because of inelastic IT costs. Public or community cloud implementations with metered usage-based billing can increase the elasticity of IT costs, which makes IT service chargebacks more practical.
But metering is not the only benefit. Much has been made of the benefits of transferring capital expenditures (CAPEX) in IT infrastructure to operational expenses (OPEX), and there are undoubted benefits. However, most organizations agree that reducing expenses is more beneficial than transferring expenses from capital to operations.
There are some areas where clouds are especially effective in reducing expenses. Software development is one of these. Software development often requires hardware and software that are not needed after a project is complete. Traditionally, this equipment is leased. In addition to the cost of the lease, there are transportation, cabling, setup, and takedown costs. These fixed costs may exceed the cost of a short lease. The fixed cost of leasing 10 servers for a week is not much different from the fixed cost of leasing 50 servers for a year. In contrast, a virtual machine from a public cloud provider can be used for a few minutes at a time at a low cost.
Software quality assurance (QA) testing is also a beneficiary. Marshalling 1,000 client machines to test an application is a formidable job if the machines are physical computers in a test lab, but the same test is much easier and less expensive if the test machines are virtual machines deployed on a cloud. Tests can be performed using cloud implementations at a lower cost and less effort compared to the expensive and laborious physical hardware tests of the past.
In these areas where usage is highly fluid, cloud computing comes into its own. The capital required for a technical startup drops considerably when equipment does not have to be purchased or leased, and software development projects within large enterprises become cheaper and more agile with this kind of flexibility. This is especially significant for startups. They are always strapped for cash, and they struggled to scrape up the capital to provision even a modest development lab. By using cheap computing power from public cloud providers, they are now able to undertake development that would have been possible only with massive venture capital or in a well-funded established development house. This has changed the dynamics of software development in general.
Clouds also provide benefits from their connection through the Internet. In some cases, this is good; in other cases, it’s not so good. The Internet is all about global connectivity. Data stored in a cloud and applications running in a cloud become accessible outside the enterprise perimeter. The accessibility raises the possibility that illegitimate access may be obtained from outside the enterprise perimeter. On the other hand, external connectivity can be useful. For example, data on roving employee laptops can easily be backed up remotely using a cloud-based application. SaaS applications that are available outside the corporate network can make remote employees more productive. However, despite these advantages, security issues increase.
ON-PREMISES
On-premises8 is a term used frequently in cloud discussions. The term derives from telecommunications terminology. The term was used to distinguish between wiring and other infrastructure owned by the customer and wiring and equipment owned by the communications provider. The term was later used for software running on equipment on the consumer’s premises and software running remotely on a cloud. The term is anomalous when used in combination with private cloud because the software is still running on the customer’s premises even though running on a cloud.
Large organizations spread over wide areas may find that cloud architectures help them provide uniform services to remote offices by replacing local on-premises implementations with cloud implementations that serve all locations. Both private and public clouds can be used for these implementations. A private cloud owned and implemented on the organization premises can consolidate services without inserting a third-party cloud provider. If the organization is comfortable with a community or public cloud, the organization can offload more of the administration.
Most mobile apps have at least portions implemented as SaaS. Many basic products, like office suites, have cloud implementations such as Google Docs or Microsoft Office 360. Other products, such as Dropbox and Carbonite, use cloud storage to provide file synchronization and remote backup. Other services such as Apple iTunes and Amazon Kindle sell music and e-books that can be accessed from all the consumer devices. These patterns permit consumers to perform activities that require more computing power or storage than they have on their own machines and avoid intricate installations and maintenance that some of these products require when they are implemented locally.
Often individual consumers have more issues with connectivity than businesses because individuals are usually more dependent on public networks than businesses. Networks are no faster than their slowest link, which is often the “last mile.” The last mile is the final connection between the user and the network. For consumers, the last mile is usually a telecommunications copper wire or a coaxial cable, originally for television. Residential users do not often have much choice in their last mile, and that often means restricted bandwidth and high latency.
This is changing somewhat with mobile devices that can use the cellular network for connecting to the network. Connection speeds are getting faster, although a cellular connection is usually more expensive than a land home Internet connection.
When one looks at a map of broadband availability in the United States,9 metropolitan areas are covered, but much of the country is not supplied or under-supplied. This limits the market for consumer cloud applications and affects some cloud product development decisions.
Cloud services provide a user with a kind of connectivity that was previously unavailable or difficult to achieve, and cloud services give users access to computing power that governments and the largest corporations would have been hard-pressed to amass only a few years ago. They all rely on a pool of shared resources that contains private data and supports private processes. These private data and processes are entrusted to the cloud provider.
There are many privacy and security risks in IT. Privacy can be compromised, resulting in identity theft, loss of intellectual property, and a whole range of other losses. Security breaches can interrupt and subvert processes; outcomes may be far from desirable. Before clouds, users relied on the isolation of their devices to establish ownership of their data and control of processes. Cloud complicates the challenge.
Prior to the cloud, data security and privacy were easier to understand but not as convenient as the data services provided through a cloud. When ownership of data was tied to ownership of devices, consumers could depend on their own diligence to keep their data out of the wrong hands. When their data is in the cloud, consumers are dependent on the integrity of their cloud provider.
Processes are equally vulnerable. They can be halted, overwhelmed with input, given incorrect input…the list is long. On-premises applications rely on operators who are answerable to enterprise management. The competency of these operators can be verified, and other measures can be taken to assure the enterprise that its interests will be maintained. When an application is deployed on a third party, the enterprise loses this level of assurance and control.
The cloud can be safer than private implementations. Cloud providers can and do build datacenters that are orders of magnitude more difficult to break into than the best secured private residence and many private datacenters. The providers know more about protecting data from remote intrusion and can take better protective measures than a private person or an enterprise without a large IT staff. Providers can require background checks on every person on their sites. Only a rare homeowner requires a background check on their furnace repairman. Cloud providers are in the business of providing security and privacy, and they have, or should have, substantial incentives to do their job well. None of this guarantees safety, but it does undermine the assertion that cloud implementations are inherently unsafe.
Nevertheless, the fact that a provider can protect data and processes does not mean that a provider will protect the data and processes entrusted to them. It is up to the consumer to require an appropriate level of security. The level of security of any given provider changes often, generally for the better, and is reported with alacrity in the trade press. Consumers would do well to pay attention.
The most important task of the enterprise architect in security and privacy is to understand the vulnerable points in the system. This requires an understanding of both the technical construction of the application and its business role. Technical knowledge is required to identify what is vulnerable. For instance, a process that uses TCP/IP sockets rather than HTTP for some incoming data has different technical vulnerabilities than a process that uses only HTTP.10 However, this fact is not enough. The criticality of the data passing through the socket also is important for evaluating security and privacy, and the criticality is a usually a business decision rather than a technical decision.
Audits play an important role for verifying the governance of any enterprise. An audit is a systematic and planned review of the records and processes of an enterprise. An audit has defined goals and methods that are often sanctioned by an independent certification organization. Audits may be performed internally or by an independent external team. For many enterprises, audits of various aspects of their finances and operations, including IT operations, are required. Processes that cannot be audited may not be permitted in sensitive areas by statute, regulation, boards, or management.
Cloud implementations can present challenges to auditing. Cloud implementations have varying degrees of transparency and accessibility to audits. Private clouds are not more difficult to audit than other forms of on-premises computing. Public clouds, on the other hand, bring a third party into the situation and delegate some control to the third party. Consequently, the third party may have to participate in the audit. Unless provisions for auditing access are included in the contract between the consumer and provider, the cloud provider may be unwilling or unable to provide the desired access. Audit agreements have become more common, and auditors have become more cloud aware; so, auditing has become less of a problem than it was a few years ago, but it is still frequently cited by businesses as a reason not to proceed with public cloud projects.
Enterprise architects should keep in mind that auditing issues will stop a project summarily. When designing for cloud implementations, especially systems that either are targeted at a public cloud implementation or are likely to be ported to a public cloud, the systems must meet audit requirements when deployed on a cloud. Audit requirements vary from organization to organization and may even change over time as business practices and the regulatory environment changes. Architects should make it a practice to be aware of audit requirements in their business and act accordingly. In some businesses, audit requirements may be limited to a few important financial reports. In other businesses, such as pharmaceuticals, audit requirements may be much more stringent and touch many aspects of IT.
Reliance on remote resources that are not under the direct control of the consumer reduces the independence of the consumer of computing resources. In the days when mainframes and timesharing were the primary source of computing resources, users were accustomed to working in an environment they did not own. That all changed with the personal computer. Users became accustomed to owning their hardware and the software on the hardware.
One of the goals of the open source movement was to increase the autonomy of computer users by giving them access to the source code of the processes running on their hardware so they could determine exactly what their software did and change it if they wanted. Of course, few personal computer users took time to read the code of the open source software, and even fewer changed the code. For most, the attraction of open source software is the low price. Nevertheless, the transparency is there.
SaaS, as Richard Stallman has pointed out,11 reduces the software user’s control of the software that processes their data in return for ease of maintenance and setup. Users should realize that they have delegated a share of control, and they must trust the integrity of their provider. Sometimes trust can be problematic. Providers may be constrained by law, for example, to reveal information to legal authorities that the consumer might rather keep private. Less threatening, but still problematic, a provider may reveal usage information, which is then put to target marketing use or other purposes.
Performance and Outages
Many consumers, especially businesses, are concerned about performance and outages of public cloud providers. A lapse in performance or a complete outage can become a finger-pointing match. The consumer blames the provider, the provider blames the network, and so on. Usually, outages and performance are handled in a service level agreement (SLA) that spells out penalties and incentives for meeting performance and availability12 requirements. In many cases, SLAs are written by public cloud providers and offered on a take-it-or-leave-it basis, which leaves the consumer in an undesirable position.
Good enterprise architecture can alleviate performance and availability issues. One way is to configure cloud implementations to take advantage of options for distributing virtual machines for performance and availability. For example, some providers allow the consumer to designate that two virtual machines must run in different data centers for availability. For performance, the consumer may be able to designate that two processes must run on blades in the same rack. There are other ways to tailor architectures to the requirements of cloud implementation. More of these will be discussed in Chapter 12.
Consumer Clouds
When the cloud consumer is an individual, the benefits gained from clouds differ from those obtained by business. Although there are exceptions, individual consumers now get cloud services that have no previous equivalent. Businesses, on the other hand, more often use clouds to more efficiently implement services they have had in the past.
Individual consumers receive connectivity and mobility from clouds, which were previously available only in limited forms on corporate networks. Consumers are able to share data and access it from different devices and locations. For example, most social networking depends on storing data in a central space that is accessible to a designated group of fellow consumers.
Consumer cloud services depend more on the availability of broadband and high-speed network services than business cloud services. Enterprises are more often prepared to invest in leased or owned network infrastructure to ensure adequate support for their cloud applications. Individual consumers usually depend on public service providers such as cable and telecommunications companies. If there is not adequate network capacity available in an area from a service provider, individual consumers will not fully appreciate cloud services such as streaming video. This limits the reach of cloud service providers.
Social networking applications are significant consumer applications that could not exist without cloud implementations. One reason is the bulk of information that these applications store. Without enormous cloud storage facilities, the constant flow of text, audio, photographs, and video could not be sustained. In addition, social networks assume that data will be available on any desktop, laptop, tablet, or phone the user cares to use. This too would not be possible without clouds.
End consumer–oriented services frequently involve some form of cloud storage and often blend into other kinds of services. For example, users of Amazon’s Kindle books use a cloud service for storing their books and notes, although they may not think about the storage aspect.
It’s worthwhile considering the Kindle service for a moment. It is more complex than may be immediately apparent. A user purchases a Kindle book from Amazon. A copy of the file that represents the book is downloaded to a device. The device may be one of several models of Amazon Kindles, reader software on a desktop or laptop, or reader software on a non-Kindle tablet or other mobile device. The download is from the Amazon cloud. After the book is downloaded, the user reads the books, makes notes on it, and sets bookmarks at important spots. If the user gets a new device, such as a new smartphone, the user need only register the new device, select books from those they have already purchased, and begin reading. If the sun on the beach is too bright for their smartphones, they can read their book on screens that use technology better suited to sunlight.
The downloaded file on the reader remains joined to the Amazon cloud. For example, if the book is revised, Amazon may offer to revise the books on the user devices. Usually, this is with the user’s permission, but permission is not technically necessary. In one startling licensing case, Amazon deleted books from Kindles without permission from the owners.13 Perhaps the most surprising part of this service is the simplest: no matter where or on which device a book is opened from, it is always on the last page read. In addition, the user’s notes and bookmarks travel with their books to every device the user chooses to read from. This is accomplished through a cloud implementation.
Paper books exist in the user’s hand; an electronic book, as implemented by most electronic book services, does not. A file of data does exist on the device, but that is only a temporarily cached representation. If the network were faster and connections more reliable, that copy would not need to exist. When the user goes to another device, a similar representation with notes and bookmarks either already is present and updated or is created from the prototype in the cloud. The book with its notes is detached from the device held in the user’s hands and exists in an abstract sense in the cloud.
The book in the cloud like this is also a virtual entity; it usually does not exist as a single physical record that embodies the book. In theory, only one copy of the file containing the book need exist on the book service cloud, with auxiliary copies propagated on the cloud for backup and caching for more rapid download. Each book owned14 by a consumer references that single master copy. On the cloud, each book owned by a user is a reference to the master copy and to data specific to the user’s copy of the book, such as their notes, bookmarks (including an implicit bookmark at the point where the reader was last reading), a list of all the devices from which the reader reads, and so on. The real situation is no doubt more complex than this. An electronic book service would certainly maintain more than one copy of the master copy both for insurance against disaster and perhaps for performance. The data on a person’s books would be also copied as a backup and cached for performance.
Music services that store music libraries for users to access from different devices and permit them to have much larger libraries than any device they own could store are similar to electronic book services, storing music files rather than book files. Similar to an electronic book service, these services can use master copies of music files.
Backup and storage services are different but still similar. These services offer storage for any kind of data, and they do not have master copies that are shared among consumers. Each file or block of data is the unique to the user who stored it with the service. These services take various forms. One variety designates a directory or group of directories as linked to a master directory tree in a cloud. Files placed in these directories are automatically uploaded to the cloud master. From the cloud master, the files are downloaded to other corresponding directories on other designated devices. Whenever any device modifies or creates a new file in one of these directories, the change is automatically propagated to the other devices. Using this kind of service, an author can have an upstairs and a downstairs desktop and a laptop for excursion, all with synchronized manuscripts and notes so he can work upstairs, downstairs, or at the library and always have the latest copies in front of him.
Other consumer cloud services operate at a somewhat higher level. For example, backup services install an agent that automatically sends backup copies to a cloud server. The user does not have to do anything until the day they need a restore and the backup is automatically restored on request. Other services are built into applications, such as a note-taking service that can be configured to store data on a cloud and make notes available to copies of the application installed on other devices. Unlike the storage service described earlier, the user may not be aware that files are involved. They only see that their virtual notebook is accessible to more than one device.
File synchronization and sharing services, such as Dropbox or Microsoft’s OneDrive, use cloud storage to store master copies of files. When a synchronized file changes, the master is updated, and the changes are sent to the owner’s designated devices. The file owner can also offer a link to other users with whom the owner wants to share. The master copies stored in the cloud can also act as backups or archival storage.
Streaming video services are also examples of using shared cloud storage to share videos. Streaming video is particularly susceptible to variations in network speed and capacity.
Yet another type of consumer cloud service is SaaS. Many SaaS applications make some use of cloud storage, but they also process data remotely on computers in cloud data centers. These applications range from massive efforts to turn over the status quo of a major product, such as Google Docs and Microsoft Office 360, moving office software from the personal computer to the cloud. Cloud gaming services, such as Nvidia Grid, offer games that run on a central server and stream video to the user browser. Almost all mobile apps use some form of cloud storage for user profile information, which allows consumers to switch from device to device. These patterns permit users to perform activities that require more computing power than the user has available on their own machine.
There are two main benefits to consumers. Like cloud storage, these applications promote collaboration. A group of users can work on the same application at the same time when the application is hosted on a cloud. Users of cloud office suites can collaborate on documents. Gamers interact with each other in cloud-hosted games.
Enterprise Clouds
Enterprises can be both cloud consumers and cloud providers. As cloud providers, they may provide private clouds to their own organization, or they may be a cloud giant like Google or Yahoo that offers public services to vast numbers of users.
Enterprise Cloud Consumers
Enterprises use many of the same cloud services that individual consumers use, although the services are often tailored to business purposes. Many business use backup services similar to consumer backup services for backing up the data on their employee’s computers and other devices; the business edition of these tools often have features such as centralized administration of many individual accounts and support for departmental structures. Microsoft Office 360 is an example of a service that is used by individual consumers but is also tailored toward business use with business-oriented features and licensing.
However, enterprises and other organizations also approach clouds in ways that are conceptually different from most individual consumers’ usage. Enterprises may have requirements that render one-size-fits-all SaaS applications unacceptable.15 Typical enterprises have many legacy applications that either were written in-house or are heavily customized versions of commercial packages. These enterprises have trained and skilled IT departments that develop, implement, and support computing for the enterprise. Although they may be interested in converting to cloud-based versions of these applications, conversion is a slow and expensive process. These enterprises may prefer to deploy their applications on IaaS and PaaS clouds to gain some of the benefits of cloud computing without giving up the advantages of their bespoke and in-house software.
Another view of enterprise cloud is from providers of cloud services. These are represented by the giant search engines such as Google and Yahoo, the social network providers such as Facebook, the public cloud providers and others who view clouds as opportunities to provide services rather than a better and more cost-effective way to consume services. Unlike individuals and other businesses, their goal is not to offload some of the computing infrastructure to another entity. Instead, their goal is to convince others to make use of their services by designing and deploying efficient cloud services with sufficient capacity to offer high-quality services to all comers at competitive prices.
Cloud Management
Managing services supplied by a cloud has challenges, even for individual consumers. Some challengers are similar to the management of locally installed applications and services supplied on the premises; others are quite different. The challenges faced by individuals and business are also different because individual consumers and businesses use clouds in different ways. Individuals seldom interact with a cloud directly. Instead, they engage with applications that have cloud implementations. Businesses, on the other hand, frequently deal with clouds directly. Although they use SaaS applications in the same way as individual consumers, they also run applications on IaaS or PaaS clouds and use cloud storage directly.
Cloud Service Management for Individual Consumers
Individual cloud consumers are faced with relatively simple decisions. Almost all cloud services offered to individual consumers are forms of SaaS because the consumers ordinarily don’t concern themselves with platforms or infrastructure.16 They must decide whether to use Dropbox or OneDrive or whether to use Google Docs or Microsoft 360.
Consumers should realize that the price and features of the service provided are only one part of their decision. For example, Word 360 may provide features that a consumer wants that are not available on Google Docs. An informed consumer may base their decision on those features, but they should also realize that they delegate responsibility and management of their documents to the provider when they choose the service. Just like businesses, they should ascertain the reliability and integrity of the provider. In this example, both third parties are well-known, reputable, and financially sound enough to meet their obligations. However, consumers should realize that they could be damaged if the service provider fails to perform as they expect.
Consumers should also realize that the click-through agreement17 on a cloud service is not the same as the click-through license for software. A software license usually spells out the limits on the consumer’s use of the vendor’s software and spells out the responsibilities of the vendor if the software fails. For most consumer software, the consequences of a failure, say the crash of a word processor, are annoying but not catastrophic.18
A click-through on a cloud service describes, among other things, the limits on the provider’s responsibility for delegating the consumer’s property to the vendor. This trust relationship goes beyond ordinary use of a vendor’s software product. With software licenses, vendors protect themselves from users. Users might get less out of the software than they were expecting, but they ordinarily don’t bear a great risk of losing substantial assets. Cloud service users do risk losing substantial assets. For instance, if a backup service were to lose backups and the consumer lost their primary copy, valuable documents or data could be lost. If the provider does not maintain adequate security, damaging breaches of privacy or data tampering may occur.
For both software and services, the vendor writes the click-through agreement, and the customer can only accept or reject it. In the backup service example, backup service agreements typically limit the provider’s liability for consumer losses; some even accept no liability. Therefore, blithely clicking through a cloud service agreement, more so than a software license, could result in a serious misunderstanding and loss of significant assets or treasures.
As important as these questions are to individual consumers, they are not as far-reaching as the management decisions that business cloud users typically make.
Business Cloud Service Management
Business cloud users must decide on service and deployment models. These decisions have greater reach than choices between services. A decision to port existing applications to run on an IaaS cloud can involve significant ongoing investment and may be difficult to reverse.
An alternative is to switch to a SaaS service. That too has implications. Switching from an existing highly customized application to a generic SaaS application will force groups of users to reconsider the requirements that drove the customizations, modify their processes, and retrain personnel to use the new application. This is expensive, time-consuming, and likely to generate resistance. On the other hand, organizations often find that reduced maintenance and availability of third-party training programs make up for the lack of customization and conversion costs.
Further complicating the decision, SaaS applications are typically easy to set up and use, and the cost per user is often low. If individuals or departments are dissatisfied with an application supplied by the corporation, they may simply start to use the SaaS application and pay for it from the department budget. This may work for the department, but divergent processes can be difficult to manage and inefficient on the corporate level. For example, using an on-premises corporate customer relations management (CRM) system and a SaaS CRM system at the same time could cause embarrassment if a customer appears in only one system and the person who responds to a customer’s call has the wrong system.
In addition, cloud services often present integration challenges. For example, a SaaS service desk that does not integrate with on-premises network management will not automatically generate tickets on network failures. This can result in slow incident recognition and resolution.
Cloud management is a more complex topic than it may appear. It can mean both managing services deployed on clouds as well as managing the operation of clouds themselves. To make matters more confusing, clouds provide services that are platforms for providing other services.
Cloud as a Form of Outsourcing
The practice of contracting with a third party to replace an in-house service is called outsourcing. It has become common practice in both IT departments and other business functions. Outsourcing can involve supplementing or replacing employees with contractors, such as outsourcing the job of answering customer service calls to an outside contractor. Sometimes, the contractor may hire a former employee to perform the work they previously performed supporting the outsourced service.
ITIL addresses cloud implementations as a form of outsourcing. Each of the cloud service models outsource some aspect of IT management. An IT department usually manages on different levels. At the most technical level, they are responsible for the acquisition, maintenance, and operation of hardware and software. On a higher level, they are responsible, with the cooperation and guidance of the business and upper management, for modifying existing services and designing and implementing new services. Finally, they are responsible for the day-to-day operation of services. The three basic cloud service models—IaaS, PaaS, and SaaS—roughly correspond to these three levels of IT management. See Figure 5-1.
The decision to deploy on a cloud must take into consideration the position of the IT department as a service provider within an organization. IT service providers are often described as Type I, II, or III. See Figure 5-4.
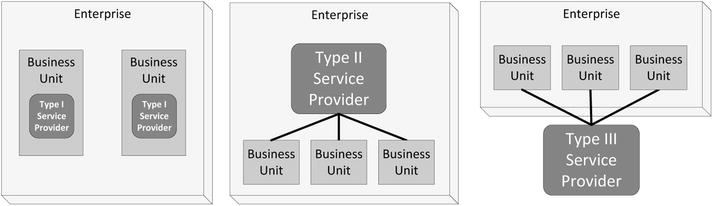
Figure 5-4. Service providers are divided into three types
A Type I provider is an internal provider. An IT department that is part of a business unit and is a provider of services only to its own business unit is a Type I provider of services to a single business unit. A Type 1 IT department may offer a private cloud services to their business unit, or they may use external cloud providers to provide services to their business unit. See Figure 5-4.
An IT department that provides services to more than one business unit is a Type II shared service provider. A private cloud implemented by this type of IT department could be used to implement services shared among several business units. A Type II provider may also use external clouds to implement shared services.
A Type III service provider is an external provider. A Type III IT department might provide a public cloud open to all comers, a community cloud offered to a limited set of organizations, or remotely hosted private clouds limited to the organization that request a private cloud services. A Type III IT department could be a business unit of an enterprise or an entire business devoted to providing external services.
IT departments are often mixtures of the types. For example, a Type I department might supply some services to other business units while its primary role is to supply services to its own business unit. A Type III department might also be a Type II or even Type I provider to business units within its own enterprise.
Depending on the IT department’s type of service provider, the decision for outsourcing to a cloud occurs on different levels in the enterprise. A cloud deployment for a Type I department may well be only a business unit decision. For a Type II provider, the decision often requires approval on the corporate or even board level. Type III service providers are a different case, depending on their relationship with their own enterprise.
All outsourcing delegates some responsibility for a service to a third party. When the outsourced service contributes to a mission-critical service, delegation of responsibility can be extremely important. Although outsourcing decisions are often based on cost, the decision to outsource should always be preceded by the analysis of the implications for privacy and security, auditability, and accountability as well performance, reliability, and suitability. These aspects of the decision may often be more significant than outright cost savings.
From the viewpoint of a software engineer or software architect, these decisions may seem remote. Nevertheless, the decision to move a service to a cloud is both technical and managerial. Some considerations require technical expertise to evaluate, such as network latency, bandwidth issues, failover and disaster recovery plans, and architectures. The IT department needs to be prepared to assist the business and financial sides of the house in evaluating the costs and significance of an outsourcing decision.
Management of Services Deployed on Clouds
Managing cloud services differs from on-premises services because a cloud service adds a third party, the cloud provider, to the management of the service. For example, the participants in an on-premises help-desk service are the end user and the help-desk staff who operate and administer the help desk.19 The help-desk staff is responsible to their users for providing acceptable service. If the help desk is deployed on a cloud—SaaS, PaaS, or IaaS—the help-desk staff is still responsible for providing service to their consumers, but they are now dependent on the cloud provider for some aspects of the help-desk service. For example, in an IaaS deployment, if there is an outage in the provider datacenter, help-desk operations will be interrupted. See Figure 5-5.

Figure 5-5. Managing an application deployed on an IaaS cloud adds another layer to management and transfers some responsibility to a third party
The picture in Figure 5-5 may be even more complex. The consumer may use performance and other management tools to monitor cloud-deployed application activity. These tools could run either on-premises or with the application on the cloud.
This is a management problem because the help desk is responsible to their users for delivering service, but the cause of interruption is in the hands of a third party, a situation that would not occur in an on-premises scenario where the entire service is provided by the same organization. When the deployment is on premises, there is a single management responsible for all aspects of the help-desk service. A cloud deployment requires coordination of the consumer management and the provider management. Therefore, a cloud deployment requires careful attention to the relationship with the third-party cloud provider. Often, the best practice is to designate a single point of contact between the cloud management and local management. The relationship manager is responsible for being familiar with the cloud provider’s operations and the obligations in the relevant service contract. The contract between the cloud provider and the help desk is crucial because it sets down the obligations of the provider and consumer when an outage occurs. Providers often provide guidance for avoiding or minimizing outages that the staff must be aware of.
Service Contracts and Service Level Agreements
SLAs are usually part of a service contract. Usually, a service contract contains typical contractual elements such as the names of the entities to the contract, length of the contract, and renewal provisions. The SLA is part of the contract that specifies the service itself: the mutual obligations of the provider and consumer, exactly what the service is to deliver, the levels of service to be delivered, and the penalties and incentives for compliance and noncompliance to the agreed-upon service levels. The service levels themselves are usually metrics and thresholds that can be objectively determined. A service level agreement may also describe disaster recovery, auditability, inspection, security, and privacy provisions. Sometimes the SLA provides for periodic reevaluation of the SLA to adjust for changing conditions and requirements.
The service contract and service level agreement are crucial to any successful cloud public or community cloud deployments. Even purely internal deployments on private cloud get benefits for clearly describing the service and service levels in an explicit document.20 They are the instruments with which the consumer is able to come to terms with the delegation of responsibility to a service provider.
The decision to deploy on a cloud is an important management decision, similar to outsourcing decisions. Although moving to a cloud is often a technical decision made in the IT department for temporary access to resources not available on the local premises, the decision should always be made with awareness of the managerial complications that can ensue and the service contract and SLA. If the cloud will support services that the IT department offers to other business units or externally, attention to the contract and SLA is even more important.
Service Models and Management
Cloud management challenges vary by service model. In one sense, they all face the same challenge (dealing with the third-party manager of the cloud), but what is managed by the third party varies with the service model. Consumers managing applications deployed on an IaaS cloud service delegate infrastructure management to the cloud provider but nothing else. This arrangement yields great flexibility to the consumer in what they deploy. In many cases, they are able to deploy exactly the same software on the cloud as they deploy on their premises. The inverse of this is that the consumer is left with the same software management tasks as they have on premises.
PaaS consumers sacrifice some of the flexibility of the IaaS model for a reduction in their share of software management tasks. Depending on what the PaaS provider offers, the consumer may no longer have to maintain databases, firewalls, web servers, load balancers, and other software utilities. Reduced responsibility for maintenance also brings with it some reduction in control of resources supplied by the PaaS provider. For example, the user of a database owned by the enterprise on their premises can decide for themselves which security patches to apply to the database and when to apply them. When a database is a PaaS service, the PaaS provider usually makes those decisions. In most cases, leaving those decisions to the PaaS provider is a convenience, but in some cases, the consumer may want or need more fine-grained control of a resource. This is a management trade-off that the consumer must be aware of.
SaaS consumers relinquish more control of the software they use to the SaaS provider. SaaS consumers must choose software offered by a SaaS provider and cannot develop their own modifications to the SaaS software. If their SaaS provider offers options for customization, these options are usually limited compared to traditional applications running on-premises or on IaaS or PaaS services.
In each case, the consumer offers a service to their own consumers by using the services of the cloud provider. The consumer reduces the risk, management commitment, and expertise required to offer the consumer’s own service by delegating aspects of the implementation to the cloud provider. Consumers of cloud services lose some flexibility and control of the service they provide. The loss of control is often mitigated by a service contract and service level agreement. The consumer is often also willing to trade flexibility for the decrease in manpower and expertise needed to provide the service.
Conclusion
There are many benefits to using cloud applications and implementing on cloud services. But there are also many pitfalls. The benefits come in the form of increased efficiency, lowered costs, and features that would not be available without clouds. The pitfalls are a loss of control and a dependence on resources and third parties over whom the consumer has only limited control. To be safe, the consumer is obliged to balance the benefits and pitfalls. Often, with the aid of the basic tools of service management, the service contract, and the SLA, cloud services are satisfactory for both consumers and providers.
EXERCISES
- Describe the three NIST service models.
- Describe the four NIST deployment models.
- What are some of the risks involved in a cloud deployment for a business? For an individual consumer?
- What is the most important way that individual and enterprise consumers can protect themselves from a provider that fails to deliver a service?
1Note that consumers do not always pay with money. Often, using a service yields valuable information about the consumer to the provider of the service. The provider then uses that information for a profit. For example, a search engine may use information it obtains about consumer interests for a directed advertising service and charge the users of the advertising service.
2Mell, Peter; Grance, Timothy. “The NIST Definition of Cloud Computing.” Recommendations of the National Institute of Standards and Technology. September 2011. Accessed November 2013. http://csrc.nist.gov/publications/nistpubs/800-145/SP800-145.pdf
3Clouds do not always supply only virtual resources; they can offer physical resources as well. However, many of the advantages of cloud implementations are dependent upon the speed and flexibility of virtual deployment. Therefore, clouds only rarely are used to supply physical resources.
4See http://dmtf.org/standards/cloud for a discussion of CIMI and other DMTF cloud initiatives.
5See www.openstack.org/ (accessed August 24, 2015) for more information.
6Advertisers’ site hits during the 2014 Super Bowl were reported to average nearly a two-thirds increase over normal traffic levels. See www.cmo.com/articles/2014/2/6/mobile_the_real_winn.html. Accessed March 25, 2014.
7Organizations have tried in some ways to use some of this spare capacity. Hardware virtualization has been the most successful of these ways but works well only when there is a substantial pool of hardware and loads with different peak usages. Virtualization is one of the first steps toward a private cloud implementation.
8On-premise is also used frequently. Sticklers point out that this is contrary to standard English in which premise refers to a proposition that is agreed upon as the basis for a succeeding argument. Premises refers to the facilities that house a business.
9See www.fcc.gov/maps/broadband-availability. Notice how quickly service drops off away from metropolitan areas. A Federal Communications Commission report (www.fcc.gov/reports/eighth-broadband-progress-report) reports that 19 million Americans do not have minimal broadband connectivity.
10Transmission Control Protocol/Internet Protocol (TCP/IP) is the protocol used for most computer-to-computer network communications. Hypertext Transfer Protocol (HTTP) is used for most Internet communication. HTTP uses TCP/IP as its lower-level transmission protocol. Read more about TCP/IP and HTTP in Chapter 10 of Cloud Standards (Apress, 2012).
11Richard M. Stallman. “What Does That Server Really Serve?” Boston Review, March 18, 2010. Accessed January 13, 2014. www.bostonreview.net/richard-stallman-free-software-DRM. Stallman is the founder of the open source movement and holds strong opinions about access to software. Many disagree with his views.
12Availability refers to the percentage of the total time a system is expected to be available that is actually available. A system that is supposed to be available for 100 hours but is unavailable for 1 hour of the 100 hours has 99 percent availability. 99.999 percent (4 seconds down in 100 hours) availability is often held up as a high level of availability. This level is commonly called five nines. One hour down out of 100 hours is called two nines, and so on.
13The deleted books were, ironically, written by George Orwell. See www.nytimes.com/2009/07/18/technology/companies/18amazon.html. Accessed August 24, 2015. In another case, Amazon deleted the entire contents of the Kindle of a consumer suspected of objectionable activity. See www.theguardian.com/money/2012/oct/22/amazon-wipes-customers-kindle-deletes-account. Accessed August 24, 2015. In both cases, the company later admitted to making a mistake.
14Owned when applied to e-books is not traditional possession. In fact, the relationship between the reader of an electronic book and its supplier is more accurately characterized as licensed or leased than owned, but having a book on your reader at least feels like you own it.
15This is changing. Heavily customized and carefully tailored applications used to be the hallmark of a large application installation, but many enterprises have acknowledged that the maintenance and support of bespoke software is a burden. This has led to a reevaluation of requirements and often a decision to use off-the-shelf or SaaS solutions.
16This situation may be changing. Network as a Service (NaaS) is being offered to businesses, and wireless networks as a service for home networks may not be far behind.
17A click-through agreement is a license or other legal document that a user accepts by clicking a screen, typically when a system is installed.
18Operating systems may be the exception here.
19This example posits a service in which the help-desk technicians are not outsourced but the help-desk software and storage are deployed on a cloud provider. The cloud service could be SaaS, PaaS, or IaaS depending on how much of the help-desk implementation is delegated to the cloud provider.
20Internal SLAs are often called operating level agreements (OLAs).
