Chapter 11 Intelligence Resources
![]() Identifying the Information an Enterprise/University Should Try to Gather
Identifying the Information an Enterprise/University Should Try to Gather
![]() Places/Organizations Where Public Information Can Be Found
Places/Organizations Where Public Information Can Be Found
![]() Membership Organizations and How to Qualify
Membership Organizations and How to Qualify
![]() What to Do with the Information When You Get It
What to Do with the Information When You Get It
![]() The Role of Intelligence Sources in Aggregating Enough Information to Make Law Enforcement Involvement Practical
The Role of Intelligence Sources in Aggregating Enough Information to Make Law Enforcement Involvement Practical
Introduction
Intelligence is information about a threat or enemy. Generally, when people discuss intelligence gathering, they are referring to information that’s been collected about a human threat or enemy. Since the birth of the computer age and cyberspace, intelligence has extended to include information about electronic threats such as botnets. If you’re reading this book, you’re already aware of the value of intelligence. The more information you’ve acquired about a threat, the better able your organization will be to combat it.
Fortunately, over the last number of years, there has been a growing increase in the number of intelligence resources available on the Internet. Rather than floundering to determine what to look for on a system, or how to protect yourself, numerous organizations on the Internet have done much of your work for you. Using these resources, you can determine what to check on your systems, be informed of new threats, and identify existing bots that may be affecting your network.
In reviewing information available through various groups, you should consider joining membership organizations that limit information to professionals who meet certain criteria. These may be people who are involved in security for a certain type of organization, or meet specific standards required in the membership. These organizations will allow access to privileged information that cannot be discussed with third parties, and allow you to discuss topics with other security professionals.
Such information is vital to repairing and improving security, and may be necessary in situations where your network becomes the victim of a botnet attack. As we’ll discuss, during such attacks, you’ll need to determine whether it will remain an internal matter, or if it is necessary to inform the public and involve law enforcement. While this is never an easy decision, it is always important to understand the ramifications of not responding to an attack in this way.
Identifying the Information an Enterprise/University Should Try to Gather
Botnets are designed to allow botherders remote control of other computers, thereby hiding the botherders’ identity by providing false information on who is sending spam, attacking systems, or providing services like pirated software and files. Despite the inherent nature of a botnet, this doesn’t mean there isn’t data available that leads back to the botherder. In fact, a considerable amount of information can be gathered when a botnet resides on a network, or when a site is victim to an attack. The intelligence you gather can be used to identify what botnet is running on systems, and may be used to ultimately identify and prosecute the botherder.
One of the first indications of a botnet problem will be revealed in log files from firewalls and those generated by scans of hosts and network traffic. If the botnets are being used to send spam, logs will provide information on excessive e-mails being sent from computers on the network. Similarly, simultaneous requests being made to a specific Web site will appear in the logs if the bot’s purpose is to perform a denial-of-service (DoS) attack. Scans may also indicate elevated network traffic, and reveal altered behaviors in how computers are functioning. For example, if the computers are being used to store pirated software or files, they may exhibit the functionality associated with a server. These computers may listen for requests on the same ports, respond to incoming HTTP and FTP connections, or have ongoing communication with servers outside your network. Such abnormal network traffic can provide information that allows a quick-and-easy way to shut down a botnet attack. If the computers are communicating with an IRC server, blocking traffic to and from that server will often deny remote access to computers on your network, and prevent the bots from communicating with the botherder.
Once you’ve identified something is going on, you’ll need to identify exactly what’s going on. If computers on your network are infected with botnets, they are there to perform specific actions on behalf of the botherder, so you should try what the bots have been doing. If they have been sending spam, you should try to acquire copies of the e-mails sent by the botnet. Doing so may aid in identifying the botherder, serve as evidence that may lead to his or her conviction, and assist in finding information on how to remove the botnet. If the e-mail includes a hyperlink to take the receiver of the e-mail to a Web site, this will aid in identifying the botherder. For example, if the spam took the recipient to a Web site under the guise of updating the person’s banking profile, it would then be possible for police to identify who owns the site and arrest them. Even if the spam didn’t directly lead to the botherder, it would provide information that could be used to identify how to remove the botnet. Since it would be the same e-mail being sent out by multiple computers, searching Google or other search engines with text from the e-mail may provide results on others who’ve been infected, and possibly steps to properly remove the bot from systems.
Identifying what a botnet is doing may also show that more files than just the botnet are being stored on infected machines. As we’ve mentioned, some botnets act as distribution servers, and may be used to store illegal copies of software, music files, movies, or other copyrighted material. In some cases, more disturbing files may be distributed by the botnet, such as child pornography or malicious software that’s used to infect other computers. You’ll want to remove such material from your network, but it is important that the data remains preserved if there is a criminal investigation. In such cases, it is often best to remove the hard disk from the computer, and replace it with one that has a clean installation of the operating system and software. The infected hard disk can then be given to law enforcement, and reformatted when it’s of no further use to them.
In the U.S., all cases of child pornography must be reported to the FBI. Mere possession of child pornography is a federal crime, so the original hard drive and any copies or images you make must be turned over to the FBI. In this case you must not retain a copy of the evidence for your files.
Anything gathered could be used as evidence in an investigation, so it is important that you don’t dismiss information on the botnets as irrelevant. Having log files that show hundreds or thousands of messages were sent from computers, copies of the spam that was sent, and precise documentation on how this evidence was acquired can all be useful in subsequent criminal or civil proceedings. Once it is apparent that your network has been attacked or compromised, it is important that you keep records of what actions were taken and when they occurred. You never know where the information you gather will take you, so it is important to document the process of what occurred.
It is also important to identify the scope or extent of an attack on your network, and what information (if any) has been accessed. Because botnets could be used to access data on a computer or pose as the user currently logged on to the network, it is possible the bot has been used to access client information, credit card numbers, or other information stored on the computer or a network server.
It is imperative that you determine who has been logged on to the machine, what access they had, and what data that machine or user has accessed. If client information has been accessed, you may need to contact clients to inform them that their personal or corporate information has been compromised.
The files making up the botnet should also be isolated to identify how to properly remove it. Identifying the files used by the botnet will allow you to look up removal methods on antivirus or security sites, as we discussed in Chapter 5 and will discuss further in this chapter. Acquiring copies of the botnet will also allow you to disassemble it to review information that is hard coded into it.
Disassemblers
In addition to other tools and techniques mentioned elsewhere in the book for gathering intelligence about botnets, including the tools and techniques in Chapter 5, and the very promising sandbox technique mentioned in the previous chapter, one additional tool for extracting botnet intelligence is a disassembler.
Disassembling is the process of translating an executable program into its equivalent assembly (machine code) representation. Using disassemblers, one may more closely analyze the functions of code segments, jumps, and calls. Through these analyses, one can better understand the inner workings of a given binary program and assess portions that may afford one the opportunity to exploit the target program. Using a disassembler, you can view any information that is hard coded into the program, inclusive to any IP addresses a botnet sends information to, or data that might reveal its originating source. At the very least, it will give you an indication of how the botnet was using hosts on your network.
Several types of Windows-based disassemblers are available via the Web, among the more popular being Hackman Disassembler, PE Explorer, and DJ Java Decompiler. These disassemblers offer an intuitive graphical user interface by which many aspects of the disassembled program in question can be determined quickly.
PE Disassembler
As seen in Figure 11.1, PE Explorer is a tool from Heaventools Software (www.heaventools.com), and is used to disassemble Win32 executables, so you can analyze and edit them—be it EXE, DLL, ActiveX, or other Windows portable executable (PE) formats. Using this tool, you can quickly open an executable, analyze its procedures, libraries and dependencies, change its data/time stamp, and edit other information. The program provides a wide range of information for those reviewing their own programs, or those written by others.
DJ Java Decompiler
The DJ Java Decompiler runs on Windows machines, and is used to decompile and disassemble Java programs. Using this tool, you can reconstruct the source code of an applet or binary file, and review its methods, constants, interfaces, attributes, and other features that would normally be unavailable to anyone other than the original programmer.
Hackman Disassembler
As seen in Figure 11.2, Hackman Disassembler is part of the Hackman Suite, and comes in three versions: Lite, Standard, and Pro. The Pro version of this tool has the capability to open any file size, and work with any instruction set, enabling you disassemble any Windows program and view its code.
Themida
Oreans Technology has a product called Themida that may be used to protect software by using features like data hiding, encryption, code replacement, and others that make it difficult to analyze malicious software protected by this product. When software protected by Themida runs on a computer, it will take control of the CPU and check for any disassemblers on the computer. If none exists, Themida decrypts the software and allows the program to be executed. Features in Themida make it difficult to reverse engineer and crack a botnet protected by this product, and makes the botnet more difficult to detect using antivirus software. Themida is available for download from www.oreans.com, as are other tools designed for security that could be used for protecting malicious software from analysis.
Using such tools to view the code is a task a number of organizations on the Internet use to gather intelligence on botnets. This type of reverse engineering can provide information on the botherder, provide understanding of how it works, and may be used in designing methods to remove botnets from systems. If you’re uncomfortable with disassembling and viewing the botnet’s code, a number of these organizations allow you to upload the botnet to them, where they will analyze the botnet and be better able to monitor similar botnets on the Internet.
Places/Organizations Where Public Information Can Be Found
Numerous organizations and Web sites on the Internet provide up-to-date information, forums, and mailing lists dealing with botnets. Some organizations are highly involved in the capture, analysis, monitoring and/or reporting of malicious software, while others focus on warning users of particular botnets and provide information on their removal. The level of detail provided such sites varies from basic to advanced, and may also provide the means to interact with other security professionals, which is useful in allowing users to advance from novices to experts.
The Internet is a resource for information, and a source of disinformation. Try to only use reputable sources for information. If you’re unsure, try to verify the information by using secondary sources. It’s a simple thing to create a Web page suggesting you install a tool to improve security, and embed a botnet within the installation of that tool. You don’t want to use bad information to accidentally lower security or install Trojans and viruses that will impact your network.
Antivirus, Antispyware, and Antimalware Sites
The obvious sources of information are often overlooked when dealing with a relatively new problem like botnets. Because bots have been around for years, those that have been previously discovered on systems have already been submitted to antivirus, antispyware, and antimalware software vendors. As such, their software can remove numerous botnets residing on a computer, and their sites provide whitepapers, articles, forums, and information on individual Trojans (inclusive to botnets). Some of the major sites providing these services include:
![]() Grisoft (www.grisoft.com) AVG antivirus, antimalware, antispyware, personal firewall software, and other tools to safeguard systems.
Grisoft (www.grisoft.com) AVG antivirus, antimalware, antispyware, personal firewall software, and other tools to safeguard systems.
![]() Lavasoft (www.lavasoft.de) Ad-aware spyware removal tool and a personal firewall.
Lavasoft (www.lavasoft.de) Ad-aware spyware removal tool and a personal firewall.
![]() McAfee (www.mcafee.com) McAfee Antivirus.
McAfee (www.mcafee.com) McAfee Antivirus.
![]() Microsoft Security (www.microsoft.com/security/) The Microsoft Malicious Software Removal Tool, created by Microsoft to remove malware from systems. Because most botnets are designed to attack Microsoft systems, their security section shouldn’t be overlooked as a resource, nor should the updates and patches provided on the Windows Update site (http://windowsupdate.microsoft.com).
Microsoft Security (www.microsoft.com/security/) The Microsoft Malicious Software Removal Tool, created by Microsoft to remove malware from systems. Because most botnets are designed to attack Microsoft systems, their security section shouldn’t be overlooked as a resource, nor should the updates and patches provided on the Windows Update site (http://windowsupdate.microsoft.com).
![]() Symantec (www.symantec.com) Norton Antivirus and other tools for safeguarding systems and removing malicious software and viruses.
Symantec (www.symantec.com) Norton Antivirus and other tools for safeguarding systems and removing malicious software and viruses.
![]() Spybot Search & Destroy (www.safer-networking.org) Spybot Search & Destroy, RunAlyzer, FileAlyzer, and RegAlyzer for removing and analyzing spyware and malicious software.
Spybot Search & Destroy (www.safer-networking.org) Spybot Search & Destroy, RunAlyzer, FileAlyzer, and RegAlyzer for removing and analyzing spyware and malicious software.
Viewing Information on Known Bots and Trojans
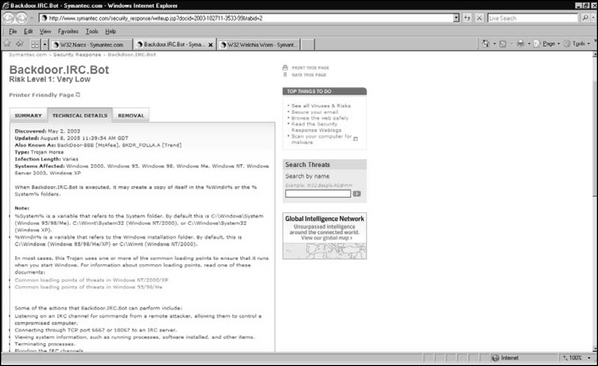
Sites like Symantec provide information on known viruses and Trojans that its software protects against. As seen in Figure 11.3, by looking through their online database for information on a particular botnet that’s found on your system, you can obtain significant information on its origin, what it does, removal procedures, and other information. Because botnets can modify the Windows registry, download and use multiple files, and make other modifications to a computer, it is important to follow proper removal procedures to fully eliminate the botnet’s presence from a system.
Professional and Volunteer Organizations
In addition to the organizations that are in the business of virus, malware, and spyware removal, numerous professional and volunteer organizations provide noteworthy and comprehensive information on security issues like botnets. Some of the groups on the Internet that provide useful, timely information on botnets and other security-related issues, and/or provide access to intelligence gathered by other security professionals, include:
![]() EDUCAUSE www.educause.edu
EDUCAUSE www.educause.edu
![]() North American Network Operators Group (NANOG)
North American Network Operators Group (NANOG)
![]() Shadowserver www.shadowserver.org
Shadowserver www.shadowserver.org
EDUCAUSE
EDUCAUSE is an organization whose membership consists of those who service or are part of educational organizations. Membership includes colleges, universities, and other educational groups, and corporations that serve the Information Technology needs of higher education. They host conferences and provide discussion groups, documents, and other resources that deal with a wide variety of topics.
NANOG
The North American Network Operators Group (NANOG) is an organization that focuses on backbone/enterprise network technologies and their operational practices. They provide conferences, tutorials, mailing lists, and other resources that allow the dissemination of security information to reach its membership. Links to tutorials and other information available for the public to view can also be accessed through their site.
Shadowserver
Shadowserver is a volunteer organization that focuses on gathering intelligence on electronic fraud, malware, and botnets, inclusive to collecting, analyzing, tracking, and reporting on their activity. They are highly involved in acquiring information on these threats, to the point of disassembling viruses and Trojans, reporting attackers, and alerting other professionals of these threats. Up-to-date statistics, whitepapers, and other information are available to the public on their site, and mailing lists that send reports and other information to your e-mail address. There are also discussion lists that allow you to discuss security topics with other professionals.
The History of Shadowserver
Of the different organizations that provide information on botnets and deal with security on the Internet, Shadowserver has one of the most interesting histories. Shadowserver began in 2004, as the result of a personal tragedy compounded by the victimization of online criminals. Shortly after Nicolas Albright’s father committed suicide, he noticed that his father’s computer was being used by botnets as part of a distributed network to store pirated software and movies. After shutting down the network of botnets by getting the criminal’s Internet access removed, he proceeded in gathering volunteers to assist in combating the growing increase of botnets that are used for malicious purposes. The intelligence they acquire is used to disseminate information to security professionals, report criminal activity to law enforcement, and assist in shutting down and prosecuting those who use these tools for illegal purposes.
Other Web Sites Providing Information
While the Internet is filled with information on a variety of security-related topics, a number of sites have repeatedly been useful for gathering intelligence on botnets. Some of these include:
![]() Blackflag (http://blackflag.wordpress.com) Information and articles on botnets, hacking tools, malware, and other potential threats and tools.
Blackflag (http://blackflag.wordpress.com) Information and articles on botnets, hacking tools, malware, and other potential threats and tools.
![]() Bleeding Edge Threats (www.bleedingthreats.net) Virus signatures available for download, mailing lists, feeds, and other features to their site that are useful in intelligence gathering.
Bleeding Edge Threats (www.bleedingthreats.net) Virus signatures available for download, mailing lists, feeds, and other features to their site that are useful in intelligence gathering.
![]() Securiteam (www.securiteam.com) A security Web site owned and maintained by Beyond Security (www.beyondsecurity.com) and provides a wide variety of information on security-related topics, inclusive to known exploits, tools for download, news, reviews and other features like the ability to submit questions to a security expert.
Securiteam (www.securiteam.com) A security Web site owned and maintained by Beyond Security (www.beyondsecurity.com) and provides a wide variety of information on security-related topics, inclusive to known exploits, tools for download, news, reviews and other features like the ability to submit questions to a security expert.
Mailing Lists and Discussion Groups
There are also a number of mailing lists, in which information can be sent to you via e-mail on a regular basis, and message groups that allow you to post and view messages online. Some of these are mentioned in previous discussions of sites and what they offer, but the following are mailing lists and discussion groups you can join to discuss security issues and ask questions:
![]() Edu-Ops http://isotf.org/mailman/listinfo/edu-ops
Edu-Ops http://isotf.org/mailman/listinfo/edu-ops
![]() Anti-Phishing Working Group www.apwg.org
Anti-Phishing Working Group www.apwg.org
![]() Botnets www.whitestar.linuxbox.org/mailman/listinfo/botnets
Botnets www.whitestar.linuxbox.org/mailman/listinfo/botnets
![]() Shadowserver www.shadowserver.org/mailman/listinfo/shadowserver
Shadowserver www.shadowserver.org/mailman/listinfo/shadowserver
![]() University Security Operators Group (UNISOG) https://lists.sans.org/mailman/listinfo/unisog
University Security Operators Group (UNISOG) https://lists.sans.org/mailman/listinfo/unisog
Membership Organizations and How to Qualify
While many of the organizations we’ve discussed so far are open to the public with minimal or no requirements for joining, some have stringent requirements that must be met to qualify for membership. These groups provide intelligence about botnets, but only to those who are in the current membership, and often include the condition that information isn’t shared outside the group. The exception to sharing information, of course, is when it is used to protect your own network or for the security of your own organization.
The requirements of joining such organizations vary. Some may be limited to educational institutes, medical organizations, government funded research, or other types of organizations. A membership organization like the Institute of Computer Forensic Professionals (www.forensic-institute.org) is an example of one that limits membership to those in a specific profession. If a person works in the field of digital evidence processing, and passes tests and meets certain criteria, membership is given. Other organizations may not limit membership to those in a specific field or area of employment, such as those working for universities or colleges, but will require specific requirements to be met. The specific requirements are available on the organizations’ Web sites, but often share similar characteristics in determining who may be a member.
One such organization that limits membership is the Research and Education Network—Information Sharing and Analysis Center (REN-ISAC). Visiting their Web site at www.ren-isac.net, you will find limited information available to the public. The real source of information is limited to those who are members of the organization. To become a member of an organization like REN-ISAC, requirements like the following need to be met:
![]() The person must be affiliated with a certain organization, and act as a representative of that organization. In other words, one or a limited number of people from each organization may join.
The person must be affiliated with a certain organization, and act as a representative of that organization. In other words, one or a limited number of people from each organization may join.
![]() The candidate must work in an official capacity dealing with computer security and/or incident response, and have responsibility for the security of that organization or part of it.
The candidate must work in an official capacity dealing with computer security and/or incident response, and have responsibility for the security of that organization or part of it.
![]() The person must be permanently employed with the organization. This is mainly because students, temporary employees, and those working under contract aren’t suitable representatives of the organization, so they don’t meet the previous criteria.
The person must be permanently employed with the organization. This is mainly because students, temporary employees, and those working under contract aren’t suitable representatives of the organization, so they don’t meet the previous criteria.
![]() A current member must vouch for the candidate.
A current member must vouch for the candidate.
![]() The candidate must agree to a confidentiality agreement and policies of the organization.
The candidate must agree to a confidentiality agreement and policies of the organization.
Vetting Members
Vetting is a process that involves a critical examination of those seeking membership with an organization. When a person applies to the organization, a select panel or current members will review a candidate’s information and decide whether they want that person to join. The organization may also confirm employment or other information included in the application. If any members decide they don’t want a person to join, or information in the application is found to be false, the application is denied.
The membership organization may also reconfirm the status of members to determine if the information in their initial application has changed. This is to confirm that the person is still working for the same employer and in the same capacity. For example, if the person has been fired, or has changed to a position that doesn’t involved security, the organization may revoke the person’s membership because he or she no longer meets the criteria of joining.
Confidentiality Agreements
Confidentiality agreements are used to prevent information from being disclosed outside an organization. They are used to limit the types of information that may be discussed with third parties, and are often used in environments where security is an issue. After all, what is the point of having network security if the people using the network are free to discuss anything they have access to on a blog or in a bar? Depending on where you work, you may have signed a confidentiality agreement upon being hired. If you’ve joined a membership organization that deals with security, you will almost certainly need to abide by one.
What Can Be Shared
In World War II, there was an adage that “Loose lips sink ships,” meaning that talking about what you know to the wrong person could cause significant damage. The same holds true today, especially when it comes to security issues, which is why confidentiality agreements are used to deter revealing information to the wrong person. In any confidentiality agreement, you should restrict information on a need-to-know basis.
In membership organizations that expect information to be kept in confidence, members are allowed to share information with other members, and the peers and subordinates within their own organization. However, allowing you to discuss information with your peers at work doesn’t mean discussing something at the water cooler. The reason for sharing information with others in your organization should be solely for the purpose of dealing with threats and improving security.
What Can’t Be Shared
If you do discuss information with someone, many membership organizations require you not to identify their organization, other organizations, or name individuals. Releasing information about a third party could provide details the organization doesn’t want revealed, such as the servers they’re using, firewall information, and other aspects of their network infrastructure. In the wrong hands, this information could provide some elements that could be used to attack the system. Additional problems could result if the source was wrong, and you were spreading false rumors about the third party. At the very least, it could lead to embarrassment for the third party, if they didn’t want the information released. If you do name a third party, you should get consent from the source and get permission from the organization being mentioned.
If you don’t have permission to use a person or organization’s name and information, you shouldn’t discuss it outside an organization with which you have a confidentiality agreement. If you do, you should use hypothetical situations and names. For example, saying “a company last year was affected by a botnet, and disassembled it and found the IP address information was being sent to X” provides enough information to colleagues without mentioning specifics about who was involved. Similarly, using false names like “Jane Doe” or “Widgets Inc.” allows you to convey a scenario without identifying who was involved.
Potential Impact of Breaching These Agreements
The same limitations on releasing information should also apply to discussing aspects of your own company. At a minimum, breaking a confidentiality agreement where you work could result in your employment being terminated. In some situations, that may be a best-case scenario. Records dealing with patients in medical facilities, criminal backgrounds in police departments, personal information on clients, and other privileged information need to be secure, and are controlled through policies and laws. There are strict regulations to control the release of information in such situations, and breaking these rules could result in fines, compensation to clients and other third parties, and imprisonment.
Membership organizations also have policies that determine what will occur when someone breeches a confidentiality agreement. If the agreement is broken, the person who broke the rules can have his or her membership revoked. If the situation is serious enough, that person’s company may be blacklisted, preventing anyone from the company from joining the membership organization in the future.
The exception to being released from the confines of a confidentiality agreement is when you are legally required to do so. During a criminal investigation, you may be required to provide information to law enforcement or while testifying. If a confidentiality agreement prevents you from providing information, you can request a warrant or subpoena issued, or you may be ordered during testimony to provide the information. In such cases, any confidentiality agreement becomes secondary, as you can be charged with contempt of court or other charges by failing to comply.
Because confidentiality agreements can be limiting, it is important that when you create ones for your clients or employees, you outline the specifics of what information is kept in confidence, when it can be discussed, what information is available to the public, and other issues that may impact the agreement at a later time. The confidentiality agreement works as a contract between you and another party, so you should specify that information may be released as part of a criminal investigation or other instances where you deem it may be necessary.
Conflict of Interest
Before joining membership organizations, you should determine whether information about your network can be exchanged with people in that organization. If you were dealing with a security problem and posted information to such a site, you could possibly break a confidentiality agreement with your own company. In such a situation, you may be abiding by one agreement but breaking another. Have a clear understanding as to what information you can provide when posting questions about your site online, or when discussing issues with other security professionals.
Don’t get too stressed over what you can disclose and what you can’t. Requesting permission from a decision maker at your place of employment will allow you to discuss information to improve security. If you have questions as to what you can discuss outside of a membership organization, ask them. In all cases, however, never reveal more information than necessary.
What to Do with the Information When You Get It
Through memberships, mailing lists, and other information available on the Internet, you should be able to keep relatively up to date on what threats can impact your network. Using this information, you can discover new vulnerabilities that can be exploited, patches and updates that need to be applied, and apply measures to limit the botnets that could infect your systems. Performing system integrity checks, using personal firewalls, encryption software, and running antivirus, antispyware, and antimalware tools on your computers will prevent botnets from infecting a system. Making such repairs, improvements, and hardening systems are the best steps toward minimizing botnets from infecting computers and limiting the damage caused by a botnet attack.
If you discover botnets on a computer, and determine through reverse engineering, log analysis, and a review of the hard disk’s contents what the botnet has been doing, you will need to decide whether your organization will need to go public with the attack. If client information has been compromised, you will need to contact the people whose information may have been obtained by an attacker. However, if computers were being used to send spam or distribute innocuous files on the hard disk, you may decide to fix the problem and keep it quiet. Unfortunately, even though ethics may lead you to involve law enforcement, decision makers in the organization may decide that announcing their systems were insecure is bad for business and decide to keep the incident an internal matter.
The Stealing of Personal Information
In October 2006, Brock University experienced the embarrassing situation of its systems being hacked, and the personal information of upwards of 70,000 alumni and other donators being stolen. The information of possibly every person who had ever donated to the university was accessed, including credit card and banking information. The university contacted police to investigate the incident, and contacted those people whose information may have been stolen. Within 24 hours, people were contacted via telephone and thousands of letters were sent to inform donators of this breach in security. While the investigation continues at the time of this writing, the university followed by having the security of their systems reviewed and improvements made. Damage control also involved responding to the media, and informing the public that steps were being taken to repair vulnerabilities and improve security. Although the university was caught in a bad situation, the handling of it is a textbook case of how to properly respond to an incident.
Throughout the process, you should document what actions were taken, the dates and times, and who was involved. This information is useful for reviewing the process of repairing vulnerabilities that were exploited, and may be required if third-party security professionals or law enforcement become involved. Documentation will aid security professionals in reviewing the before and- after of the systems as repairs were made, and may become evidence of what occurred.
The dates and times appearing in log files are important in determining when events occurred during an attack. As such, it is important that your servers and other devices on the network have their time synchronized. Services are available to synchronize the system clocks of servers and workstations on your network, and the Network Time Protocol can be used to synchronize them.
While the confidentiality agreements discussed earlier may have seemed like overkill when thinking of discussing another organization, you will feel some security that they exist when it comes to your network being attacked. It is important to determine whether information will be shared with other security professionals through membership organizations or other groups. The information may assist in making repairs to systems, and prevent others from experiencing similar attacks.
The Role of Intelligence Sources in Aggregating Enough Information to Make Law Enforcement Involvement Practical
The decision to involve law enforcement can be a difficult one, especially as it may involve the incident becoming public knowledge. In addition, anyone involved in responding to the attack or working with law enforcement may be required to testify at a later date. These issues may dissuade members of your organization from wanting a police presence, but catching the botherder or hacker who attacked your network will prevent further attacks in the future.
Preserving evidence of the attack is essential to a successful investigation. Keeping the server up and running is a goal of IT staff, while keeping evidence intact is the goal of an investigation. Specialists in law enforcement may request computers aren’t touched until they are analyzed. To avoid modifying any of the contents of the drive, it may be necessary to remove the drives of any systems that were affected by the attack, which may contain the bot or other related files (such as pirated software, movies, or other items stored on the drive). As mentioned previously, the hard drive may be required as evidence if law enforcement is contacted. Once the hard drive is removed, replace it with a clean version of the drive that doesn’t contain the bot. This may involve restoring information to the drive from a backup, or making a copy of the existing drive and removing the botnet and restoring any items it may have altered (such as registry entries). If your organization is the victim of a DoS attack, such actions would be overkill, as you would only need to gather log files, router statistics, and other samples of the network traffic during the attack. In any situation, however, it is vital that you provide law enforcement with as much access as they require, even if it is supervised by a member of your IT staff. If there is information that will require warrants or a subpoena to release, you should try to identify it early, so the investigators can obtain them early.
It is also important to remember that the first officers to respond to an incident may not necessarily be the ones performing an investigation. When a call is made to police, an officer is sent to respond to the incident. If the incident requires special investigation skills, other units specializing in these areas will be called. Most police departments in North America have a Technology Crime Unit or a partnership with larger law enforcement organizations to perform computer forensic investigations. In some cases, local police may refer the case to federal law enforcement if it involves computers or suspects in other states, provinces, or countries.
Summary
The intelligence you gather about a threat like botnets is vital to your ability to prevent or recover from an attack. Although botnets have been around for years, the incidents involving this method of attack have increased. Information gathered from sources like vendor sites, membership organizations, public sites, mailing lists, and other sources will better enable your organization to combat threats and improve security.
Using the resources available on the Internet will provide you with a wide variety of tools. As we saw earlier in this chapter, disassemblers will take apart malicious software to review how it works, and may provide information on who is communicating with a botnet. In addition, log files and other samples created by devices on your network will indicate botnet attacks, and provide important information on how the attack occurred.
Membership organizations are another important resource, and allow you to discuss situations with other professionals. Membership organizations provide privileged information to those who have met specific criteria to join, and protect members through confidentiality agreements to ensure that what’s said to the group stays with the group. These groups will also provide alerts to threats, and information that may not be readily available elsewhere.
If an attack occurs on your site, you should seriously consider the involvement of law enforcement. By having an investigation performed, the botherder or hackers involved in an attack may be apprehended, and subsequent attacks may be prevented. If a decision is made to involve the police, it is important that evidence be preserved so a case can be made against the attacker. While the involvement of law enforcement was limited in previous years, most law enforcement agencies now have specialists or entire units that deal in investigating computer-related crimes and electronic fraud.
Solutions Fast Track
Identifying the Information an Enterprise/University Should Try to Gather
![]() Log files from firewalls, scans, and other sources on your network can provide the first indications that a botnet resides on computers. They can be a valuable source of information, and be used as evidence in possible criminal investigations or civil suits against an attacker.
Log files from firewalls, scans, and other sources on your network can provide the first indications that a botnet resides on computers. They can be a valuable source of information, and be used as evidence in possible criminal investigations or civil suits against an attacker.
![]() Copies of spam being sent by the botnet, files stored by the botnet, and even the hard disk itself may be useful as evidence and provide information on what the botnet is doing with hosts on your network.
Copies of spam being sent by the botnet, files stored by the botnet, and even the hard disk itself may be useful as evidence and provide information on what the botnet is doing with hosts on your network.
![]() Tools like disassemblers can be used to disassemble a botnet and view its code. Using these tools, you can find a significant amount of intelligence regarding the botnet, including how it works, what it accesses, and who it’s communicating with.
Tools like disassemblers can be used to disassemble a botnet and view its code. Using these tools, you can find a significant amount of intelligence regarding the botnet, including how it works, what it accesses, and who it’s communicating with.
Places/Organizations Where Public Information Can Be Found
![]() Numerous organizations and sites on the Internet provide information on botnets that have been active on the Internet. These include vendors that manufacture tools to safeguard systems or remove viruses and malware, security sites that provide information, mailing lists, and discussion groups.
Numerous organizations and sites on the Internet provide information on botnets that have been active on the Internet. These include vendors that manufacture tools to safeguard systems or remove viruses and malware, security sites that provide information, mailing lists, and discussion groups.
![]() Sites that provide antivirus, antimalware, and antispyware tools often provide additional information on known botnets. Information includes proper removal procedures, how the botnet works, and its purpose or functions.
Sites that provide antivirus, antimalware, and antispyware tools often provide additional information on known botnets. Information includes proper removal procedures, how the botnet works, and its purpose or functions.
![]() Public organizations provide whitepapers, articles, statistics, and other information that can aid in protecting systems, and understanding the threat botnets pose. They often provide additional methods of discussing botnets with other security professionals and those who are dealing or have dealt with botnet problems.
Public organizations provide whitepapers, articles, statistics, and other information that can aid in protecting systems, and understanding the threat botnets pose. They often provide additional methods of discussing botnets with other security professionals and those who are dealing or have dealt with botnet problems.
Membership Organizations and How to Qualify
![]() Some organizations require incumbents to meet specific criteria before membership is given. The requirements may include working in a specific field, for a certain type of organization (such as a university, college, law enforcement, etc.), or other criteria that limits the number of people who may join.
Some organizations require incumbents to meet specific criteria before membership is given. The requirements may include working in a specific field, for a certain type of organization (such as a university, college, law enforcement, etc.), or other criteria that limits the number of people who may join.
![]() Membership organizations limit all or the bulk of information to those who have acquired membership in the organization.
Membership organizations limit all or the bulk of information to those who have acquired membership in the organization.
![]() Vetting is a process that involves a critical examination of those seeking membership with an organization. Members determine whether a person may join, or should be removed from membership.
Vetting is a process that involves a critical examination of those seeking membership with an organization. Members determine whether a person may join, or should be removed from membership.
Confidentiality Agreements
![]() Confidentiality agreements are used to limit information from being disclosed outside an organization. They are often used in membership organizations or environments where security is essential.
Confidentiality agreements are used to limit information from being disclosed outside an organization. They are often used in membership organizations or environments where security is essential.
![]() Unless you are in a situation where you have been ordered by the courts to reveal information, you should only release information on a need-to-know basis to prevent breaking any confidentiality agreements.
Unless you are in a situation where you have been ordered by the courts to reveal information, you should only release information on a need-to-know basis to prevent breaking any confidentiality agreements.
![]() Releasing information to third parties may result in membership to an organization being revoked. In some situations, breaking a confidentiality agreement could result in fines, civil damages, and possible imprisonment.
Releasing information to third parties may result in membership to an organization being revoked. In some situations, breaking a confidentiality agreement could result in fines, civil damages, and possible imprisonment.
What to Do with the Information When You Get It
![]() Identify methods that can be used to improve security.
Identify methods that can be used to improve security.
![]() Use information on botnet removal procedures to properly restore systems to a secure state.
Use information on botnet removal procedures to properly restore systems to a secure state.
![]() Document all actions taken to restore systems, and gather evidence that may be required by security professionals or law enforcement at a later time.
Document all actions taken to restore systems, and gather evidence that may be required by security professionals or law enforcement at a later time.
![]() Determine what information may have been compromised, and whether clients or other individuals and organizations need to be contacted about the incident.
Determine what information may have been compromised, and whether clients or other individuals and organizations need to be contacted about the incident.
The following Frequently Asked Questions, answered by the authors of this book, are designed to both measure your understanding of the concepts presented in this chapter and to assist you with real-life implementation of these concepts. To have your questions about this chapter answered by the author, browse to www.syngress.com/solutions and click on the “Ask the Author” form.
Q: Are the best sources of intelligence on the Internet?
A: Not necessarily. Many sites can provide disinformation, and some hacking sites may attempt to install malicious software on your computer when you visit them or install a program from their site. You need to be careful wherever you visit on the Net, and attempt to verify information as true. This isn’t really a problem with established sites that work hard to disseminate accurate information. Of course, you also shouldn’t underestimate the value of a book, which is obviously free of anything that will infect your system.
Q: I’d like to take a more serious role in combating botnets. What steps should I take?
A: Visit sites like Shadowserver to view how to capture data and become involved in gathering intelligence. Information on the Shadowserver site provides instructions on creating honeypots, and (like numerous other sites dealing with Trojans and viruses) the ability to upload a botnet you’ve discovered.
Q: I’d like to join a membership organization, but I’m unsure if I have the qualifications?
A: Membership organizations aren’t only for topnotch security professionals. They provide a forum for professionals to exchange information, ask questions, learn from the experience of others, and expand the capabilities of combating botnets and other threats. Check the Web sites of membership organizations and see if you meet their criteria. Some organizations will even make exceptions on a case-by-case basis.
Q: I’ve heard that the police generally don’t help with computer crimes. Should I bother calling?
A: Cyber-crimes are a recent field of investigation, and it has taken law enforcement a significant amount of time to catch up. Today, most police departments have their own Technology Crime Units, or partnerships with departments that specialize in this field. Police colleges have increased their curriculums to include courses on electronic fraud, computer forensics, and other investigative techniques involving cyber-crimes.
Q: If law enforcement becomes involved, will I need to testify in court?
A: It is always important to remember that’s a possibility. In criminal investigations, the names of everyone involved in the incident will need to be documented, and depending on what your role was in responding to the incident and the information you can provide, your testimony may be required.