In this section, we will analyze a sample capture file covering the details of an attack on a WPA2 network. Loading the file in Wireshark, we can see that we have 3,818 packets, as shown in the following screenshot:

Let's clear the noise by filtering out only management frames using the wlan.fc.type filter and the value 0x0, as follows:
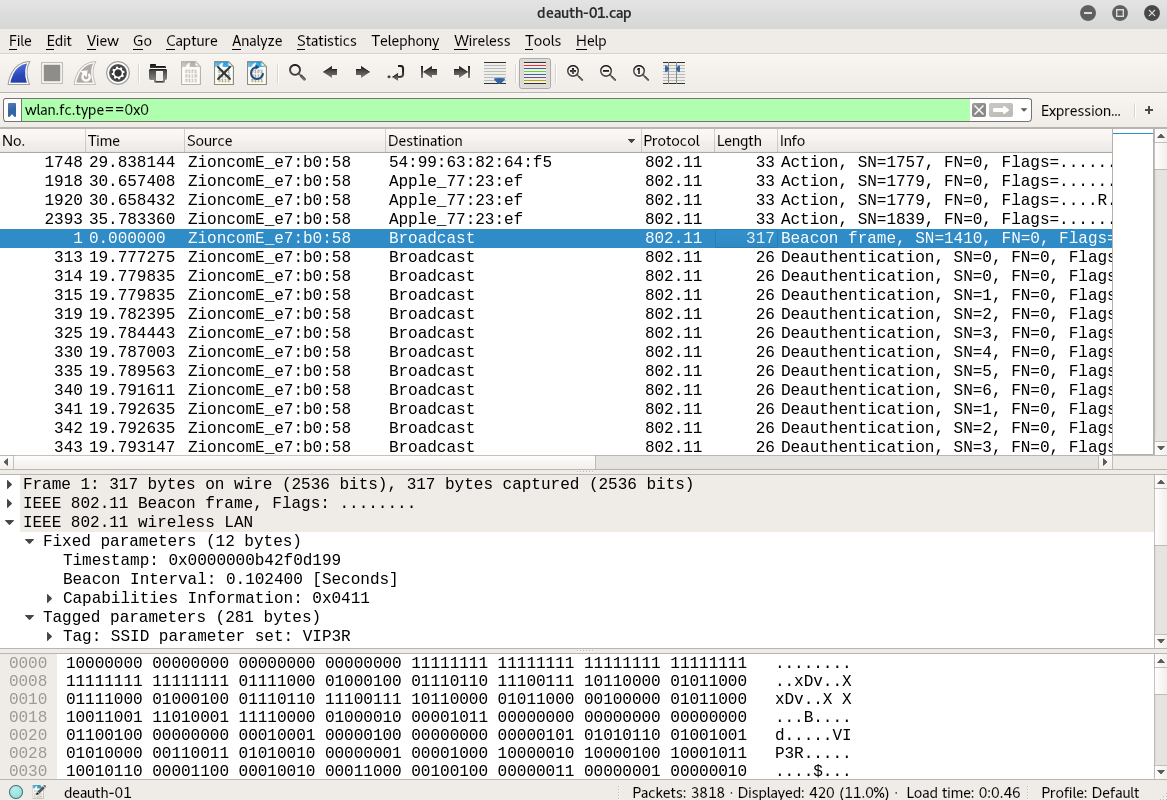
We can see that we are left with only 420 packets, and we can also see plenty of deauthentication packets in the screenshot. Let's find out which device got affected by this deauthentication attack and reinitiated the key handshake:

It looks as though b0:10:41:c8:46:df was deauthenticated and reinitiated the key exchange. We can see that the authentication packets started at frame number 377. Let's look at what happened before this:

We can see that plenty of deauthentication packets started arriving, which caused the device with the MAC address b0:10:41:c8:46:df to reinitiate the connection. However, we can't see the key packets anywhere. Let's find out where they are:

Simply putting a filter on eapol allows us to see that the key is exchanged between the devices. An attacker with access to this file needs to brute-force it to find the network key. We saw how we could gather details on the deauthentication attack; however, we also saw that we were not able to find the original attacker's MAC address, as they pretended to be one of the victims or the AP itself.
