Linux
Providing a summary of Linux in a few paragraphs is a difficult task. Unlike other operating systems, each of which has only a single variation, Linux has many different distributions, each offering a slightly different approach. Some of the most common Linux distributions include Red Hat, SuSE, Debian, and Caldera. In light of the many versions of Linux, if a command or an approach is listed in this section and is not available in the version of Linux you are using, you can look for an equivalent command or approach in your version, and you will very likely find one.
The history of Linux can be traced back to 1991, when Linus Torvalds, then a student at the University of Helsinki, set out to make a Unix-like operating system. After developing the original Linux kernel, the core of the operating system, he distributed it on the Internet and asked anyone who was interested to develop it. Many eager developers jumped on the programming bandwagon, and in a few short years, Linux had progressed into a viable alternative to the commercially available network operating systems.
Today, the development of Linux continues in much the same way as it always has: Anyone who wants to can develop Linux to further enhance its capabilities. To ensure that this is always the case, the Linux kernel is protected under a licensing agreement which implies that the source code will always be available to anyone who wants access. More information on Linux licensing and development can be found at www.gnu.org.
The following are some of the key features of the Linux operating system:
Multitasking— Linux supports multitasking, which is the ability for several programs to run simultaneously.
Multiplatform— Linux is able to operate on a number of different platforms, not just on Intel machines.
Multiprocessor support— Linux supports multiple processors, meaning that it recognizes multiple processors in a system.
Development— In all the noncommercial programs available for Linux, the source code is available. This allows you to customize and further develop Linux.
Virtual consoles— Linux supports virtual consoles, which are essentially independent logon sessions.
File system support— In addition to the Linux native file systems, such as EXT2, Linux supports a wide range of file systems, including FAT (for DOS), HFS (for Macintosh), VFAT (for Windows 95, Windows 98, and Windows Me), and CDFS (for CD-ROMs).
Network support— Linux has the ability to connect to a variety of network environments. Linux includes TCP/IP networking such as FTP, Telnet, and NFS; support for AppleTalk server; and Internetwork Packet Exchange/Sequenced Packet Exchange (IPX/SPX) and NetWare connectivity software.
Linux System Requirements
Linux is a very dynamic and diverse network operating system, and therefore, it is almost impossible to make a blanket statement about the hardware needed to get a Linux server up and running. You can be reasonably sure, however, that the minimum hardware requirements for a Linux system are lower than those for any other operating system. Linux users are quick to point out the limited hardware that is required for a Linux system, and it really is quite amazing. One of the many reasons that Linux has the ability to run on limited hardware is because it offers graphical utilities but is a command-line operating system. Windows, on the other hand, is a graphical operating system that offers some command-line utilities. It is the graphical nature of the operating systems that increases the need for faster and more extensive hardware.
You can find the minimum hardware requirements for each of the different Linux distributions at the distributors' respective Web sites, but they are all fairly similar. To give you an idea of the hardware requirements for a Linux system, Table 9.7 lists the system requirements for Red Hat Linux 7.
| Hardware | Minimum Requirement |
|---|---|
| Processor | 486 CPU |
| RAM | 32MB |
| Hard disk space | 650MB |
Linux File Systems
The number of file systems supported by Linux is really remarkable. The default Linux file system is called EXT2, but to coexist on the same partition as a Windows operating system, Linux also supports the FAT file system. The EXT2 file system is the most widely used on Linux systems and provides support for large hard disks.
Linux Monitoring and Performance Tools
Network administrators who are used to the slick graphical performance tools of the Windows server environments might be taken aback by the visual presentation of some of the Linux utilities used to monitor performance. Many Linux distributions do provide graphical tools, but many Linux servers are command-line driven and do not provide a graphical interfaces.
When you get past the appearance of the utilities, you will find that the actual performance and monitoring that these tools provide is second to none. Performance tools vary somewhat among Linux distributions, but they all offer a variety of performance-monitoring tools. The following sections discuss a few ways to view system resources and usage.
The Top Utility
Top is a command-line utility that displays the processes that are currently being run on the system and how much of the system's resources these processes are using. Similar information is provided in Windows 2000 on the Processes tab in the Task Manager utility. Also included in the display are various counters that show how physical memory is being used, the amount of swap space in use, and the total number of processes in use. One of the best features about the Top utility is that it is dynamic, and every few seconds, the information is updated, to give you the most current picture of your system.
Process File System
A Linux system has a /proc directory, which is a virtual directory that is used to view just about any aspect of a Linux system. All the mainstream Linux distributions include /proc directories, and as a network administrator, you can expect to be spending some time looking in this directory when working on Linux machines.
The components that can be viewed with the proc command are listed in the /proc directory. The most useful switches for the proc command include the following:
/proc/dma— Provides information on the Direct Memory Access (DMA) channels in use
/proc/apm— Includes information on power management, if it is supported
/proc/meminfo— Includes information on physical memory and the swap file
/proc/pci— Provides information on the Peripheral Component Interconnect (PCI) devices within the system
Graphical Utilities
The two most common Linux graphical interfaces, GNOME and the K Desktop Environment (KDE), provide a number of easy-to-use performance-monitoring utilities. Figure 9.13 shows a system-monitoring tool from a Linux system that uses the KDE graphical interface.
Managing Linux Disk Drives
Linux partitions are usually managed through the Fdisk utility. Administrators who are used to the cleaner Microsoft Disk Management utility might have to take some time to get used to Linux Fdisk. In inexperienced hands, Fdisk can be a dangerous utility; it should be used only by server administrators who are comfortable with it.
EXAM TIP
Command-Line Case-Sensitivity Unlike Windows and NetWare, command-line utilities in Linux are case-sensitive. This means that Fdisk is different from fdisk. When you first start working with Linux, this can be very frustrating, but you soon get the hang of it.
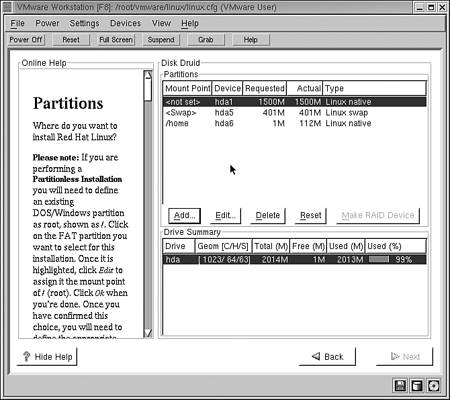
In addition to Fdisk, many of the major Linux distributions also have their own disk-management utilities. Red Hat uses Disk Druid, Mandrake Linux uses Disk Drake, and Caldera Linux uses LIZARD. Each of these utilities does essentially the same thing: partition and manage the hard disks. Figure 9.14 shows an example of the Disk Druid disk-management utility that is used in Red Hat Linux.
Linux User Management Basics
At first, the management of users' accounts in Linux might seem awkward, and compared to user management in other network operating systems, it is. You typically add users on a Linux system by using the useradd command from the command line, with the following syntax:
useradd <USERNAME>
The next step is to set a password for the user account that was created; to do this, you use the passwd command. After you type the command, Linux prompts you to enter the password and then to enter it again for confirmation. Various graphical utilities are available that can also be used for adding user accounts. If you prefer, you can use one of them instead of the command-line utilities.
NOTE
Linux Graphical Utilities Although many Linux administrators prefer to use command-line utilities for tasks such as adding users, there are a number of graphical utilities available.
User account information is stored in a file called passwd in the /etc directory. This file is a text file, and in a standard configuration, passwords are also stored in this file, in plain text. Because this represents a security issue, it is common to use a process called password shadowing in which the password is stored and encrypted in a separate file, called /etc/shadow. Group accounts are created in much the same way as user accounts, except the command used is groupadd.
Linux has a more distributed method of security than either NetWare or Windows, in that it relies more heavily on the security capabilities of applications than on the core user accounts. This is one of the features that makes Linux the most customizable of the operating systems described in this chapter.
Verifying Linux Network Settings
Network settings, much like anything else in Linux, are stored in text files that normally are located in the /etc/ directory or subdirectories of this directory. Network settings can be configured through a variety of command-line and graphical utilities.
The following are the commands that are most commonly used to verify and test network connectivity in a Linux environment:
ifconfig— ifconfig shows detailed information—including TCP/IP address, default gateway, and subnet mask—about all network interfaces. It also provides very basic usage statistics for each interface.
ping— ping works the same way as with the other network operating system server platforms: It tests network connectivity between two devices. The ping command in Linux uses a simple syntax: ping <IP address>.
traceroute— traceroute displays the network path between two nodes. At each hop, information about the hop, including the response time and IP address, is shown. The syntax for the traceroute command is traceroute <IP address>.
EXAM TIP
Linux Help You can access help for most Linux commands by using the <command> --help command.
Linux Authentication
People who are used to working on a Windows-based system will no doubt discover that administration on a Linux system is very different from what they are used to. For instance, authentication information such as a list of users is kept in a text file. This file, /etc/ passwd, controls who can and who cannot log on to the system.
For a user to log on to the system, a valid username and password combination must be supplied. Both of these pieces of information are case-sensitive.
Linux File and Print Services
Although it is not the most obvious choice for a file and print server platform, Linux can perform the role of a file and print server admirably. In a base configuration, the volumes on a Linux server are not available to network clients. To make them available, one of two file sharing services is commonly used:
NFS— NFS is the original file-sharing system used with Linux. NFS makes it possible for areas of the hard disk on a Linux system to be shared with other clients on the network. Once the share has been established from the client side, the fact that the drive is on another system is transparent to the user.
Samba— Samba provides Server Message Block functionality so that areas of the Linux server disks can be made available to Windows clients. In much the same way as on Windows servers, Samba facilitates the sharing of folders that can then be accessed by Windows client computers. Samba also makes it possible for Linux printer resources to be shared with Windows clients.
As with Windows NT/2000 and NetWare, Linux has a file system permission structure that makes it possible to restrict access to files or directories. In Linux, each file or directory can be assigned a very basic set of file rights that dictate the actions that can be performed on the file. The basic rights are Read, Write, and Execute. The rights can be expressed in an alphabetic format (that is, RWX) or a numeric format (777). The rights to a file can be derived from the file ownership, from a group object, or from an “everyone” designator, which covers all users who are authenticated on the server. The Linux file permission structure might not be as sophisticated as those found in other network operating systems, but it is still more than sufficient in many environments.
Printing on a Linux system occurs through a service called the Line Printer daemon. The Line Printer functionality can be accessed by any user on the network who is properly authorized and connected. Some distributions of Linux have started to provide a more enhanced printing system called the Common Unix Printing System (CUPS). Many people, however, still prefer to use the traditional Line Printer system because of its simplicity and efficiency.
Linux Application Support
If you can think of an application that you might need, chances are that it is available for Linux in some form. As well as highly sophisticated commercial applications produced by large software companies, you can find software for the Linux platform that is written by an equally enthusiastic army of small software development companies and individuals. This means that application support for Linux is on par with if not greater than that in other network operating systems, such as NetWare, even if it has not yet reached the levels achieved by Windows server platforms.
In a sense, all applications created for Linux are third-party applications in that Linux itself is only an operating system kernel. The applications that run on this kernel are what provide Linux with functionality.
On the assumption that a network server will have a number of requirements, it is common practice for the Linux kernel to be bundled with various applications and provided to customers as a package, which, as we discussed earlier, are called distributions.
One respect in which Linux certainly has the edge over the other operating systems discussed is that many Linux applications are free of charge. Developed in the same spirit as Linux itself, and in many cases governed by the same licensing types, these free applications can seriously reduce the cost of maintaining a network server. Although it can be said that there are also free server-type applications for Windows and NetWare, there are certainly not as many of them as there are for Linux. (Note that we are referring to server applications, not applications targeted at workstation or end-user applications.)
Linux Security
Considerable effort has been put into making Linux a very secure network operating system, and those efforts are evident. When it is configured correctly, Linux is a very secure operating system, and therefore it is often chosen to be used as a company's firewall server. The following are a few highlights of Linux security:
Resource access— As in the other network operating systems, access to resources on a Linux network is controlled through permissions. Access control lists identifying which systems and who can access what resources are held in text files such as hosts.deny and hosts.allow. Permissions for network resources and services can be assigned to an individual user or to a group of users.
User authentication— To access the local system resources or any network resources, user authentication, in the form of a username and a password, is required. The user account information is kept in a text file known as the /etc/passwd file in the Linux system.
File and directory security— The default file system used by Linux is the EXT2 file system. Like NTFS, which is used with Windows servers, EXT2 allows administrators to assign permissions to individual files and folders. These permissions are used to control who is allowed access to specific data on the server. A secure server should have permissions set on the important data in the system.
EXAM TIP
Logging on to Linux Servers To log on to a Linux server, the user must supply a valid username and password. Both of these values are case sensitive. You should know this for the exam.
As Linux continues to grow in popularity, it will become an increasingly common sight in server rooms of organizations of all sizes. As a network administrator, you should prepare yourself for when you encounter a Linux system—not if.