CHAPTER
13
Implementation and Validation

Now that you have worked through the book and made your plans, you may need to define some level of success metrics or assurances for the stakeholders of your organization that you will be able to use to demonstrate that your operation succeeded. Or perhaps you’ve implemented your solution and need to know whether your planning, operations, and activities have been successful. In this chapter, we will wrap up what you’ve learned with the validation of your implemented operations.
However, not all threats or criminals operate in the same way. For the purpose of this book, we are focusing on what is in the public domain to keep the authors out of jail due to the combined in-depth knowledge we have of actual attribution of specific targeted threats and the players behind each campaign. I (Sean Bodmer) have digital images of numerous criminals and state-sponsored threats and can tie them directly to specific events that have occurred over the past several years. Some of these individuals have even approached the authors at overseas conferences and vacations in order to learn more about what we know about them.
One of the first key steps to identifying whether this tradecraft has been successful is validating your own knowledge of what could be occurring on the network. Another factor is validating that your entire deception plan was implemented in a manner that is successful and at the point “was” a part of your planned operation. Finally, the overall outcome of the operation and the observed events prior to, during, and after operations need to be validated.
Vetting Your Operations
When working on an operation, you need to know whether it is working. Well, how do you go about checking this?
You perform the overall vetting of your operation using a bottom-up approach. You start at the bottom (tactical or what you need to address first) because that is where all the magic happens, and then work your way up to the overall management and executive level.
For the purpose of continuing with our pseudo-military terminology, we are going to approach this using the observe, orient, decide, and act (OODA) model for the sake of breaking down your operation into a digestible framework.

By using the OODA loop process, your operations will be easier to conduct, maintain, and manage from the technical implementation level up to the highest levels of your effort.
If you think about an operation surrounding a persistent threat, a human (your focus) on the other end of the keyboard reacts the same way another human might. The people who are controlling the active campaign against your enterprise will also be interpreting data the same way, as follows:
Act on those decisions and continue actions as planned. Your effort’s processes will be logically similar in nature:
When validating an operation, one of the first rules to follow is not to look at your focus (the target of your operations) through a mirror. What the focus may or may not do is very likely not the actions you would take in the same situation. Therefore, in order to validate your operation, you must keep in mind your goals, which led you down this path.
As we consider how the operation has proceeded, it is also useful to view the OODA loop through the eyes of the adversary/focus. This will provide you with a greater understanding of whether your operation is going as planned or you need to make modifications to meet your objective.
Vetting Deceptions
It has been one week since you set your plan in motion. You noticed a problem on your network, conducted an analysis to determine what you thought was your focus’s goal, and set up an environment in which your focus would be successful, or so he thought. You had a wide range of options, but chose to establish a honeypot, populating it with information you assessed the focus would find desirable. The honeypot you set up with a plethora of supposedly valuable documents has been successfully compromised by the attacker. Now it is necessary to see if your focus has taken the bait.
Monitoring the logs of your analysis system allows you to view exfiltration activity, providing you with immediate feedback of whether your deception operation is proceeding as planned. If you view the log and notice that your focus took only one of your “priceless” documents on one day, don’t despair. The focus may be the cautious type, determining if the document contained anything he thought was valuable and deciding if his newfound gold mine was legit. If the focus keeps coming back to grab more documents, then you can feel reasonably assured that your deception operation is proceeding as you desired. On the other hand, don’t be surprised if the focus grabs all of those documents in one fell swoop. This is not uncommon, as he may be worried that he will lose access before all the items could be obtained. If this happens, still keep watch to see if the focus returns, as this may be an indicator that he believes the environment and documents are real.
The information you placed on your honeypot is only one aspect of your deception operation though. It may be that the focus doesn’t desire your sensitive information (though given the nature of adversarial operations these days, that’s unlikely). You still have the opportunity to monitor the logs and learn how your focus operates. If the attacker stays focused on this honeypot, he may be convinced that this was his target. The longer he stays in the honeypot, the more you can learn, and the more time you will have to shore up the defenses on your real network based on your newfound knowledge of the attacker. If the threat is not seeking your sensitive information, and is simply looking to use your corporate resources for further nefarious activity, then you will have a better understanding of the threat and the knowledge that this is possibly an opportunistic threat. The biggest caveat about honeypots is that the focus may use them to move further through your network and into a partner’s network or other trusted networks that your enterprise is connected to.
If the documents were the threat’s target, how you vet the success of your deception now depends on the type of information you put in those documents. Unfortunately, this may take a little patience. If you placed information related to your company strategy or your latest product, you will need to keep an eye on your competitors. If you notice they have announced a new product or a change in their own strategy that loosely matches where your company was going, this may be an attribution indicator. A military organization may take a different approach. If the military unit placed false defense plans on the honeypot, it could watch and see if any friends or foes have taken measures to counteract the discovered plans. Once again, this can provide clues that the deception operation is working, while also helping determine the culpable party.
Vetting your deceptions may be a short-term proposition, may extend to be a long-term observation activity, or both. Whatever the case, when working your deception operation, be prepared to constantly evaluate your successes and failures.
Vetting Perceptual Consistency in a Deception
When building a deception, you need to ensure all facets of the deception are timely and in place in order to make sure your focus does not identify the deception and move away from it. Your goal is to have the focus of your deception welcome the information being fed to him in order for your operations to successfully continue.
Here is a quick list of things to think about when you are vetting the perceptual consistency of a deception against a focus:
You want to ensure your focus sees what you expect him to see in the time allotted for the operation. With the proper host layout on each honeypot and several systems running a host-based tool to generate standard user-based traffic (such as sending e-mail and surfing to predefined websites that the identity/role of the profile on the honeypot would perform during daily workflow), the perceptual consistency is increased.
In a blind (black box) assessment of a network, a professional penetration testing team attempted to test a custom network of four network segments of various production and counterintelligence systems (honeypots). The team spent a two-day period laying down network noise to congest and confuse any network security (IDS/IPS) systems, and began scanning and rummaging through the network. This highly skilled penetration team found that many of the systems on the private segment appeared to be real, rather than honeypots.
The network penetration team easily gained access to every system they targeted and attempted to compromise. The network itself was a complete lab environment; each node had its own enterprise architecture, including mail, active directory, firewalls, and workstations.
Through this two-day test, the penetration team identified several honeypot systems that were intentionally made to look like honeypots, with no content and indicators of honeynet tools on two segments of the network. The identification of these systems showed them these segments were being monitored, and the team immediately halted any actions and focused on the other portions of the network where they believed there to be no honeypots. In their out briefing, they explained that any professional offensive team would immediately back out of any network or system they believed to be a honeynet or honeypot. Even the slight detection of one honeypot indicated to them that the specific segment was to be ignored completely unless it was critical to their mission. In the event of the criticality of the network segment, they would need weeks to slowly probe that segment before proceeding further.
In the end, perceptual consistency of your entire operation is one of the most important components of a cyber counterintelligence operation against an active threat.
When it comes to OSINT, you must maintain specific identities that need to be believable and capable of being trusted by the underground community. When building an alternate identity or persona, spend some time setting up various accounts on the underground security sites listed in Chapter 3 (and any of the thousands of sites out there that we did not list). Just remember that the more you put your persona out there and the longer it is posted online in underground forums, showing you are an active participant and poster in the underground culture, your persona’s perceptual consistency and reputation will increase. Over time, criminals will come to you asking for help in their campaigns, and you will be able to spot the campaigns before they start. Some of the authors of this book actively engage the online underground in order to learn in-depth intelligence on active threats, criminals, motives, and their intent. This is one powerful weapon for your program to be able to know about campaigns and attacks before or precisely when they kick off.
Vetting Engagements
Ensuring the operation was used by your focus and not another threat/actor is another important component of validating your operation. When you are running your operation and actively monitoring a threat, how do you know another threat has not entered your analysis node (honeynet) where you are engaged in active analysis? This can occur when an opportunistic threat sells off for a portion of time (subleases) a criminal infrastructure to another criminal. This provides the original criminal additional income and is very common in today’s criminal underground ecosystem.
A great example of subleasing is the common distribution providers (infector groups) who operate and maintain exploit kits that exploit a victim upon visiting a website. The website may have an embedded malicious object/advertisement (malvertising) or a redirection to a purely malicious page via a link commonly found in e-mail. Once the browser begins to load the webpage, the exploit kit downloads a stage-one sample of crimeware, which in turn downloads another criminal’s bot or crimeware that actually performs the theft of personally identifiable, financial, and other information from a victim’s system.
Although this is a common practice among opportunistic threats, targeted threats have been known to leverage these distribution providers to gain internal access to an enterprise or network, and then have their crimeware downloaded for a predefined fee. It is very difficult to identify these types of scenarios. The following table illustrates how this would look over the network in a layered approach.
| myapps-ups.org/track.php?id=934faf2562b5a9c6 | Blackhole exploit kit |
| myapps-ups.org/w.php?f=28&e=2 | zeustrojan |
| adhyocymvtp.com/index.php?tp=001e4bb7b4d7333d | Blackhole exploit kit |
| adhyocymvtp.com/w.php?f=26&e=2 | trojanSinowal |
The table shows two different Blackhole exploit kits. Upon hitting myapps-ups.org or adhyocymvtp.com, you are exploited by the kit, and then both sites push down different bots to the victim—in this case, the Zeus bot or the Sinowal Trojan.
These examples are from common opportunistic criminal groups that are tracked by one of the authors on a daily basis. These two different groups, code-named Zeus Group D and Sinowal Group C, are both Eastern European organized criminal groups.
If within your enterprise you see commonly used crimeware, that does not mean it is an opportunistic attack. We’ve seen purported state-sponsored hackers using tools just like those employed by common criminals to avoid direct attribution of their operation.
Consider the Night Dragon event where there were purported Chinese state-sponsored hackers exfiltrating information from global energy firms. One thing that can be said about these so-called state-sponsored groups is that they were not creative when it came to the naming conventions of their CnC. Take a look at the public list of domains used by the Night Dragon threat during the campaign that pillaged natural energy firms around the world and reportedly stole an unknown volume of data from each network and organization. You will see that the third-level domain (3LD) is also the name of the host involved in the attack.
The actors behind this threat were comfortable enough with what they were doing that they actually named every 3LD after each victim. This has been seen in use for well over ten years: the bad guys get in and use the name of the victim as the 3LD.
Based on the following list, which was extracted from more than nine samples of the Night Dragon intrusion set malware, isn’t it easy to identify which firms were involved in the attack? The objective of the focus behind this campaign was to infiltrate each of the listed firms and steal as much sensitive information as possible.
This is a highly common pattern involved in reportedly Chinese-backed attacks. Whoever it was didn’t go through much trouble to hide what they were targeting (and after this book is published, they may change their pattern, but it will only be a matter of time until that new pattern is deciphered as well).
The most important note when validating your engagement is to understand what type of threat you are engaging and if that is the right threat to engage. We are not stating that every targeted attack will actually implement a network infrastructure that will leverage the name of the victim. There are many targeted attacks that use raw IP addresses versus domain names.
Consider the GhostNet incident discussed in Chapter 1, where there was an IP address that resolved back to a Chinese PLA signals intelligence base on the east coast of China. Now, by law, an IP address does not relate to a person. However, having data sent and accepted by a remote destination (an IP address) is highly suspicious, and the burden of proof resides with the Chinese for the activity of that IP address, since it was on their network, under their control, and data was being accepted by the remote system. If data had been dropped or rejected by the remote destination IP address hard-coded into GhostNet, we would have seen it bounce back after connection attempts, although they were fully established sessions transmitting data.
It’s critical to watch what goes in and out of your network. You can almost never completely trust what your host-based tools tell you. When you validate an engagement, you need to ensure the right avenues of your network and protocols your focus is using match up with what you have observed and continue to monitor.
If you are leveraging a real deception network deployment or honeynets, you will be able to maintain control of your engagement and validate what is occurring in that sanitized environment. You will be able to leverage that observable intelligence across your enterprise and identify other infected hosts across your network, and increase your mitigation and removal of the threat’s campaign. You will need to leave a trail of digital bread crumbs across your network over time during the operation to ensure your focus will head into that portion of the network. You can do this in many ways, such as by redirection of flows and sessions. Also, numerous network devices can be used to redirect enterprise traffic to specific predefined destinations.
Putting This Book to Use with Aid from Professionals
If you have read this book in its entirety, by now you should understand that there are numerous types and levels of threats, ranging from simple to sophisticated. Your job is to understand which threats are within your network and which threats deserve more of your resources to engage or deter them from continuing to further penetrate your network. You also need to understand you are not the only one dealing with these threats. There are communities, forums, teams, and working groups that can help augment your capabilities. There are also security researchers out there like Steven K Xylitol and Abram E N@rrat0r, who both do a lot of research into the blackhat community and the latest and greatest happenings in the cyber criminal underground.
To extend a hand out to those facing threats, a very niche community of professionals have volunteered to be listed here. These professionals work diligently and are subject matter experts in the field. They have a deep understanding of the latest in cyber criminal trends, tools, and tactics, and how to counter the activities surrounding the cyber criminal underground.
| Abuse.ch | Roman Hussey |
| Arbor Networks |
Jose Nazario Curt Wilson |
| CERT-LEXSI | Vincent Hinderer |
| Team Cymru | Steve Santorelli |
| Ecrimelabs.dk | Dennis Rand |
| Damballa |
Sean M. Bodmer Jeremy Demar |
| Defence Intelligence | Matt Sully |
| Dell SecureWorks (Counter Threat Unit) | Joe Stewart |
| DeepEnd Research | Andre M. DiMino |
| Group-IB US director | Alex Kuzmin |
| INFIGO IS | Bojan Zdrnja |
| iSightPartners |
Ken Dunham Marc Vilanova |
| Kaspersky Labs | Alexander Gostev |
| Mandiant | Aaron LeMasters |
| Mullen Scientific Software | Patrick Mullen |
| Mysterymachine.info | Ned Moran |
| NetWitness |
Shawn Carpenter Michael Zeberlein |
| SANS Internet Storm Center | Pedro Bueno |
| Savid Technologies | Michael A. Davis |
| Shadowserver Foundation |
Freed0 Steve Adair |
| Sourcefire | Joel Esler |
| Symantec | Vikram Thakur |
| Treadstone71 | Jeff Bardin |
| Trend Micro |
Paul Ferguson Kevin Stevens Ivan Macalintal |
| Vigilant | Lance James |
| Other specialists |
Brent Wrisley MacLeonard Starkey Mark Seiden |
No one organization can do this alone in today’s world of modern computing and threat landscape. Many firms specialize in helping with the latest threat intelligence and attribution of threats. These companies also sell products and services like those offered by many other firms who are in IT security. They offer services similar to those covered in this book as professional services or incorporated into their product offerings.
The professionals and firms listed here will help if and where possible. However, we have left a lot of firms out of the list, so we highly recommend that you do your own research on which firms or solutions fit your organization.
How to Evaluate Success
This is the question on the lips of almost every executive or manager: Were we successful in mitigating the threat? How to evaluate success is always a management metric used to justify funding and expenses for a specific effort or program.
As we’ve said before, there are no silver bullets when it comes to security. The bad guys will always get in. The best thing you can do is be prepared and understand the options (tools, tactics, and procedures) available to your organization when dealing with targeted or advanced threats.
The best metric to use is whether your team is capable of identifying each specific campaign and movements of each threat traveling across your enterprise. Based on the identification of the different campaigns of a threat, you will have a foundation for beginning attribution.
You also want to understand exactly what a specific threat was doing while within your network. Here’s a short list of questions to ask about a specific event:
Of course, there are more questions you can come up with on your own. All of these questions are used to understand the threat. They are part of the success metrics of your organization’s ability to engage and mitigate a threat to your protected assets and information.
Defining success is one of the most difficult pieces next to direct attribution, but it can also be used as a jumping board for growth of your organization’s capabilities. You want to develop the ability to identify, understand, and mitigate each threat in the desired path of your choosing.
Sometimes it is easier to get law enforcement involved, but then there are the majority of the incidents that you or your management want to be handled internally. Your organization will more often than not know which incidents should have law enforcement involved and which shouldn’t. Sometimes it is easier to engage the threat on your own terms without the convoluted processes of law enforcement. We’re not saying contacting law enforcement is a bad thing, but there are times when the effort does not equal the expenditure of resources to get law enforcement involved.
This book walked you through tactics and tools that can be used to successfully handle an intrusion on your own. If your leadership desires to contact law enforcement, you should revisit Chapter 5 and read through what needs to be done in order to work with law enforcement agencies and their legal procedures before they will be able to fluidly help you through the events at hand.
In the end, only you can measure the success of a specific engagement of a threat, and whether you were able to mitigate their actions and continue to identify and track their attempts or continued movement throughout your enterprise.
Getting to the End Game
In this final section, we will walk through a combination of measures that were developed by Xylitol and implemented by ep0xe1. This information was passed on to us to discuss the actual active engagement of the SpyEye group, who targeted numerous victims in the United Kingdom in late 2011. (SpyEye was introduced in Chapter 9.)
This SpyEye operator launched a campaign:
faterininc.ru:9564/formg/uk/index.php SpyEye CnC 194.247.12.39
According to jsunpack.jeek.org (a website that checks for malicious executable code upon visiting a website), this domain is a benign or safe URL, and is of no concern to be exploited upon visiting the control panel for this SpyEye botnet. This means the botnet operators did not set up any traps for unauthorized visitors to their control panel (which is common). If an exploit is present at the control panel URL, this is a very sophisticated threat and should be handled with extreme caution. Any indicator of an unauthorized visitor may cause the attacker to back away or discontinue use of this botnet, which is also common. For this example, you can find the full report of this site at http://jsunpack.jeek.org/?report=331b99fae236fe3bfe25b53b0e2dd0d968a290cf.
This domain had the following pages, which were identified by jeek.org by scanning the domain for pages and files accessible or being served up to those who visit the site:
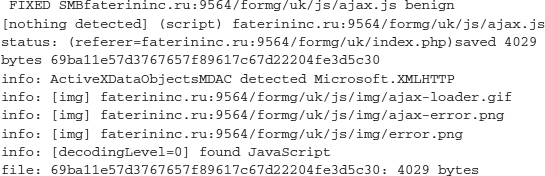
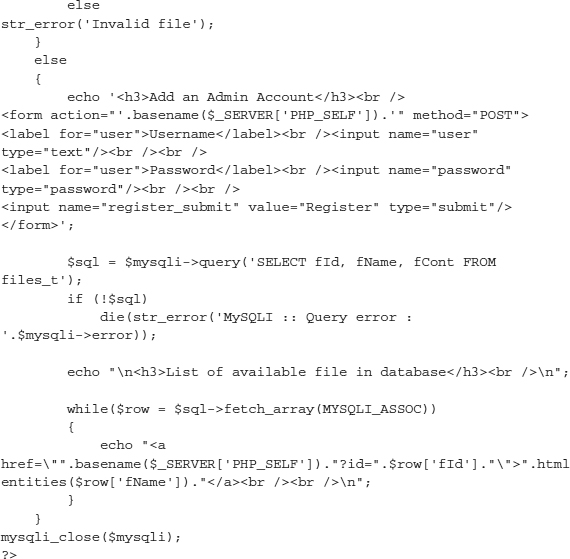
Now that you have seen the external analysis of this page, let’s look into the actual inner workings of this SpyEye botnet. As almost every security professional knows, the use of default passwords is inexcusable. Well, in the world of cyber crime and criminals, it is far more prevalent than one would think. The following script was developed by security researchers/hackers Xylitol and EsSandre, and modified by ep0xe1.



After chatting with Xylitol and ep0xe1, we learned that they were both able to create the same style of attacks for numerous exploit kits and botnets by examining and exploiting criminal systems in almost the exact same manner criminals attempt to gain access to various victims around the world. ep0xe1 asked us to convey that his approach to exploiting criminal infrastructures was spawned by an idea of a former colleague. After working with Xylitol, he was able to improve on his initial tactics and techniques. This is becoming a common practice among gray hat security researchers who secretly go the extra mile by doing what law enforcement or the victims of the crimes cannot do themselves: stemming or stopping the threat as quickly as possible. Both have stated that by hacking into criminal infrastructures, they are able learn more about the who, what, how, and why behind each criminal. This is an interesting aspect for independent researchers breaking some of the rules to make the world a safer place one criminal network or campaign at a time. Researchers like these professionals are where security is heading, with countries like Japan, China, and Russia recruiting patriotic hackers to help defend their country’s global and foreign interests.
For this example, we will use the preceding SpyEye CnC SQL injection code to add a secret administrative account to the SpyEye control panel. We’ll demonstrate the capability of this script against a “dumb” criminal who didn’t go through the trouble of making each default password unique. Just remember that when thinking about how to engage threats, the most important part of their network to target is their CnC server, where they store stolen information.
The following shows what the control panel for a SpyEye CnC server looks like upon connection.
Once you have used the preceding script to inject your own user account, you are able to log in to the CnC server covertly without the knowledge of the criminals (unless they check their server or connection logs often). There is always a chance of getting caught by the criminals. In our practical usage of these techniques, we have found that if we simply log in and modify a criminal’s infrastructure—by banning, deleting, or altering settings in a way that will cause some level of damage to their campaign—they often back off from the CnC server. This may be because they fear that their true identities, or ties to their real-life identities through private e-mail or names, could lead to attribution to that specific crimeware support infrastructure. Again, this is not always the case, but it has been a very effective tool when attempting to manipulate a remote adversary without tying up any personnel beyond a few smart network ninjas for a few hours.
Note that the legality of these techniques depends on which country you live in. This is probably illegal, and if you get caught, you will be in trouble (although we never worry about a specific criminal trying to file charges against us for infiltrating their infrastructure). You may run into a law enforcement agency that is actively working against that criminal, and you have just tainted their evidence (bad mojo on the receiving end). This generally does not end up well for the security professional with the good intentions.
In almost every country around the world, hacking is illegal. There are a handful of countries that allow it, or look the other way as long as you don’t hack anything in your own country. These include Brazil, Russia, China, Iran, and Holland (where Wi-Fi hacking is legal). So again, if you perform actions like these, you can open yourself up to legal turmoil. Many highly skilled professionals have been caught performing these proactive defensive actions against advanced or organized cyber threats over the years, and they have lost their jobs and permanently marred their careers. Please be aware of the fact that every action has a reaction, and some have very serious consequences if you step on the wrong toes.
Now back to our analysis of an exploited criminal. Upon first logging into the SpyEye control panel shown earlier, we dig into the following credit card information page.

We see that this criminal has not collected any of his victims’ credit card information. That’s interesting. So it appears that this criminal campaign does not have any focus on financial information. What is this criminal campaign after? This threat was monitored for over six months, so we were able to come back again and again to see the increase and decrease of victims and what information was stolen. Now we check the Bank of America credit card grabber, and we see the criminal has not used any of the credit card grabbing tools.

This observable information tells us that our hypothesis is correct: this criminal is not interested in financial information, or this criminal did not have the funds to purchase the credit card grabber add-on for the SpyEye malware builder, which generally goes for over $1,000. As you can also see, there are several other options and features available to our counterintelligence team to learn about this specific threat’s campaign. You may wonder why we look to the financial information first. The reason is very simple: the faster security professionals can discern whether a crime was financially motivated, the faster they can react. It has the following benefits:
Now let’s move on to the actual statistics page.

Here is where we get to the meat of this threat’s activity. Based on the activity of the statistics page, we can see that numerous accounts were stolen, ranging from social networking site accounts to personal and professional online accounts. We can see that this criminal is seeking additional access to exploitable accounts that can be sold in bulk on underground forums all over the world (those mentioned in Chapter 3 and others springing up every day).
Scrolling down the statistics page, we see more information.

All of these domains have accounts (username and password combinations, along with any data accessible with those credentials) associated with them that were stolen from various victims. In the control panel on the top-right side, you can see the number 83k, which is the number of bot victims this criminal had at the time of our latest analysis of this campaign.
The analysis team who worked on this criminal’s dossier has thousands of accounts we simply do not have the time or space to cover in the book. Just know there were originally 254,000 victims on this threat’s CnC server before ep0xe1 banned and deleted access to over 150,000 of the threat’s bots. He removed victims of countless Fortune 500 firms in order to minimize this threat’s ability to sell off specific accounts on the black market to criminals who are interested in more than simple financial theft or continued infection campaigns.
In the following screen, we can see that this same criminal was also focused on collecting e-mail certificates and e-mail account information from each victim.

This information is important, as it can be used in targeted attacks such as spear phishing, whaling, or other e-mail-based attacks, where a victim’s account and reputation or identity can be exploited through the trust others have in this individual. For the safety of each victim, we will not disclose the information about the actual certificates, as they are directly attributable to a specific individual or international organization. As you can see in the screenshot, there is a hefty list of more than 100,000 e-mail accounts and e-mail certificates collected by this threat that are possibly exposed and actively being sold on the black market. The final item we check is the information page of each specific SpyEye victim and the associated information the bots running on their systems are sending to the threat. Again, for the sake of the victims, we have analyzed and deleted from the criminal’s infrastructure well over 100,000 entries of victim data.
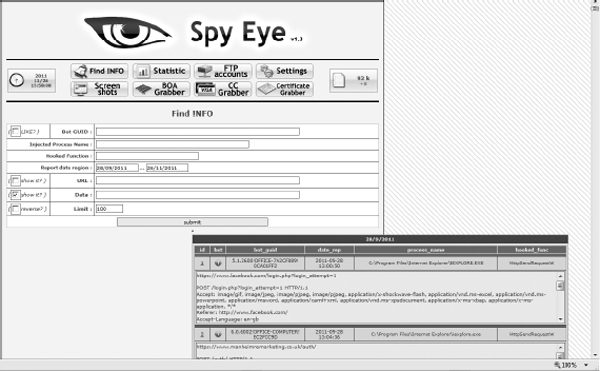
This page shows the following information:
Practically every bot or remote Trojan collects and reports information similar to SpyEye. Although not all criminal control panels have as pretty a user interface as this one, the functionality is still there.
Since this initial attribution work was performed, SpyEye has begun to wane in popularity among criminals. Newer variants of Zeus—such as Ice-IX, Citadel, and Zeus version 3 (Gameover)—and thousands of other bot kits, crimeware builders, remote-access Trojans, and worms that report back victim information are being sold on the underground markets. Knowing there are proactive defensive tactics that go beyond your own enterprise and engage the threat directly is important. If you cannot allow this yourself, get law enforcement agencies involved, and they can help in shutting down the infrastructure.
The attribution outcome of this specific threat was that it was targeting large organizations and individuals who worked for big international firms and stealing their e-mail credentials. So this threat was ranked with a reputation score of 8 based on the observables list presented in Chapter 3.
Conclusion
This book has led you through many paths of analysis and operational techniques that can improve your security posture beyond the traditional antivirus, basic perimeter defenses, crimeware detection and mitigation, and security firms who deal with these issues on a daily basis. We have walked through different scenarios involving enemy engagement, exploring the tactics that allow your adversary to be successful, and discussed how these new skills can be useful when you face your enemy.
As you begin to conduct operations yourself, some will be successful and some will not meet the desired end. That is the nature of the beast. One key to success is to share the information about your attackers and the measures you took to fend them off with the rest of the security community, to the extent allowed. One person will not win the war, but the security community can win many battles together, propelling it to victory.
There are hundreds of security professionals who work in the same circles to be aware of the latest threats. Their tools and techniques can be countered or engaged in order to mitigate a threat. Between the resources in this book and the specific individuals named in this chapter, you are a member of an organization. No matter where in the world you are, subject matter experts are available to work with you in private or with law enforcement to engage, mitigate, or exploit threats and prevent further hemorrhaging of your infrastructure.
The overall goal of this book is to empower you and your organization to better handle advanced cyber threats in the future and increase the security posture of your organization from targeted or opportunistic cyber threats. We hope you walk away from this book feeling empowered and informed on some of the latest techniques from some of the professionals who do analysis and attribution as a way of life to better protect their organization, customers, and the global Internet. Advanced cyber threats emerge almost every day, and knowing which are specific to your organization or enterprise is much more important than the total volume of infections across your enterprise. We highly recommend that you contact one of the authors or professionals listed in this chapter to learn more about threats before they’re actually within or working against your organization.
Working in unison is the only way we can reverse the enemy’s deception, seeing that there is nothing we can do to stem the encroachment of organized or advanced cyber threats. It is your network and our infrastructure. Prepare yourself and attempt to take the fight to the enemy (focus). You will walk away from your office at the end of the day feeling much better, knowing you had a hand in identifying and attributing criminal campaigns back to a specific group or individual.
What’s next? Who knows? We continuously see evolutions and variants of criminal tools and tactics. We’re sure that after reading this book, some criminals will alter some of their techniques and attempt to counter the counterintelligence tactics conveyed here. To date, honeypots have been widely distributed only by a handful of private organizations and vendors. There are small groups within international governments, like the United States, United Kingdom, China, and the United Arab Emirates, who have a national-level based honeygrid (a massive network of connected honeynets), a term coined by one of the initial thought leaders and one of the Honeynet Projects within the US government, US Marine Corps Major Allen Harper (now retired).
Deception is a way of life for some and either a state of mind or practice that can also be used as a weapon. Just read up on your Art of War by Sun Tzu. Deception and the countering or reversing of one’s deception are some of the most important capabilities that should be applied to every defense-in-depth security model.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
