
Asset Security
Domain Objectives
• 2.1 Identify and classify information and assets.
• 2.2 Establish information and asset handling requirements.
• 2.3 Provision resources securely.
• 2.4 Manage data lifecycle.
• 2.5 Ensure appropriate asset retention (e.g., End-of-Life (EOL), End-of-Support (EOS)).
• 2.6 Determine data security controls and compliance requirements.
Domain 2, “Asset Security,” discusses one of the most important things an organization can do in terms of securing itself: protect its assets. As you will see in this domain, anything of value can be categorized as an asset, and an organization must manage its assets effectively by identifying them and protecting them according to how valuable they are to the organization. In this domain we will discuss how to identify and classify assets and how to handle their secure use, storage, and transportation. We will also talk about how to provision assets and resources securely to authorized users. As an asset, information has a defined life cycle, and we will examine this life cycle so that you understand everything involved with protecting critical or sensitive information. We’ll also discuss asset retention, as well as the security controls and compliance requirements that are levied as a part of protecting assets.
 Identify and classify information and assets
Identify and classify information and assets
As discussed in Objective 1.10, an asset is anything of value to the organization. Examples of assets include servers, workstations, network equipment, facilities, information, and people. The value placed on an asset depends on how much the organization needs it to fulfill its mission. How an organization places value on an asset depends on many factors, including the original cost of the asset, its depreciation, its replacement value, what it costs to repair, how much revenue it generates for the organization, and how critical it is to the organization’s mission.
We also discussed tangible and intangible assets in Objective 1.10. As a refresher, a tangible asset is an item that we can easily see, touch, interact with, and measure; examples are systems, equipment, facilities, people, and even information. Intangible assets are those that are difficult to interact with, and sometimes difficult to place a value on, but are still critical to the organization’s success. Examples of intangible assets include customer satisfaction, reputation, and standing in the marketplace. In this objective we will discuss how assets and data are identified and classified.

EXAM TIP Although the CISSP objectives sometimes seem to refer to information and assets as two different things, understand that in reality information is in fact one of the organization’s critical assets, and in this book, we will treat it as such and make reference to it as an asset, along with facilities, equipment, systems, and even people.
Asset Classification
Classifying assets means to categorize them in some fashion so that they can be managed better. Assets are generally classified in terms of criticality and sensitivity, both of which are discussed in the next section. Assets aren’t purchased or acquired for their own sake; they exist to support the mission of the organization, including its business processes. The organization can classify an asset according to criticality by determining how critical the business process is that the asset supports.
A common way to perform this criticality assessment is to perform a business impact analysis (BIA), introduced in Objective 1.8. A BIA is also one of the first steps in business continuity planning, which we will discuss later in the book. A BIA inventories the organization’s business processes to determine those that are critical to its mission and cannot be allowed to stop functioning. It also identifies the information assets used to support those processes, which are considered the critical assets in an organization.
Cross-Reference
We will discuss business impact analysis, as part of business continuity planning, in Objective 7.13.
Even before determining criticality, however, the organization must discover all of its assets. Normally, tangible IT/cyberassets fall into one of two categories: hardware or software. Hardware is normally inventoried and identified by its serial number, model number, cost, and other data elements. Software is tracked by its license number or key, business or process it supports, and specific function.
Data Classification
Like other assets, data can be classified in terms of criticality, or in terms of sensitivity. While often used interchangeably, data criticality and data sensitivity mean two different things. Data criticality refers to how important the data is to a mission or business process, and data sensitivity relates to the level of confidentiality of the data. For example, privacy data in an organization may not be critical to its core business processes and only collected incidentally to the human resource process of managing employees. However, it is still very sensitive data that cannot be allowed to be accessed by unauthorized entities.
Cross-Reference
Remember from Objective 1.2 that data and information are terms that are often used interchangeably, but they have distinct definitions. Data are raw, singular pieces of fact or knowledge that have no immediate context or meaning. An example would be an IP address, or domain name, or even an audit log entry. Information is data organized into context and given meaning. When given context, many pieces of data become information. Giving data context means correlating data—determining how it relates to other pieces of data and a particular event or circumstance. While individual pieces of data should be considered critical or sensitive, we normally classify information rather than pieces of data.
Also like other assets, information must be identified and inventoried. Although information is a tangible asset, sometimes it may seem more like an intangible asset because inventorying it is much more challenging than simply counting computers in an office. The organization has to determine what information it has before it can figure out its criticality and sensitivity. Identifying information usually involves looking at every system in the organization and recording what types of information are processed by them. This could be different sets of information that span privacy, medical, and financial information, or information that relates to proprietary processes the organization uses to stay competitive in the marketplace.
Once the different types of information are identified and inventoried, those different types are inventoried again by where they are located, on which system(s) they are processed, and how the systems process that data type. They can then be assigned criticality and sensitivity values. Remember from our discussion in Objective 1.10 that we can assign quantitative or qualitative values to different elements of risk. We can also assign quantitative or qualitative values to information. Quantitative values are normally numerical, such as assigning a dollar amount to the information type. Quantitative values in dollars are easy to assign to a piece of equipment, but not necessarily to the type of information it processes. Qualitative values may be better suited for information and can range, for example, from very low to very high.
The organization should develop a formalized classification system for its assets. Some assets may be assigned a dollar value for criticality to the organization, but other assets may have to be assigned a classification range that is qualitative in nature. Unlike quantitative values, qualitative values can be assigned for both criticality and sensitivity. This classification system should be documented in the organization’s data classification and asset management policies.
One of the good reasons for assigning assets to a classification system is to determine the cost effectiveness of assigning controls to protect those assets. We discussed the criteria for selection of controls and countermeasures in Objective 1.10. The value (in terms of cost, criticality, or sensitivity) of an asset, whether it is an individual server or an information type, must be balanced with the cost of a control that is implemented to protect it. If the protection is insufficient or the asset’s value is far less than the cost to implement and maintain the control, then implementing the control is not worthwhile. Implementing the control should also be balanced with the level of risk the control mitigates or reduces. If an asset’s classification is very high for criticality and/or sensitivity, then obviously it is more valuable to the organization and the cost/benefit analysis will support implementing a more costly control to protect it.
Various different classification systems are used across private industry and government. Private companies may use a classification system that assigns labels such as Public, Private, Proprietary, and Confidential to denote asset sensitivity, or subjective values of Very Low, Low, Moderate, High, and Very High to denote either sensitivity or criticality. Military classifications typically include the use of the terms Top Secret, Secret, and Confidential to classify information and other assets according to sensitivity. Regardless of the classification system used, the organization must formally develop and document the system, and apply it when determining the level of protection that assets require.
Cross-Reference
We will discuss classification labels in more detail in Objective 2.2 when we cover data handling requirements.
REVIEW
Objective 2.1: Identify and classify information and assets In this objective we reviewed the definitions of tangible and intangible assets. We also discussed the need for identifying and classifying assets, including information. Assets can be classified according to criticality and sensitivity. Criticality describes the importance of the asset to the mission or business, and may be determined by examining critical business processes and further determining which assets support them. Sensitivity relates to the need to keep information or assets confidential and away from unauthorized entities. Assets must be identified and inventoried before they can be classified according to criticality and sensitivity.
2.1 QUESTIONS
1. You are tasked with inventorying assets in your company. You must identify assets according to how important they are to the business processes and the company. Which of the following methods could you use to determine criticality?
A. Classification system
B. Business impact analysis
C. Data context
D. Asset value
2. Which of the following is the best example of information (data with context)?
A. IP address
B. TCP port number
C. Analysis of connection between two hosts and the traffic exchanged between them
D. Audit log security event entry
3. You are creating a data classification system for the assets in your company, and you are looking at subjective levels of criticality and sensitivity. Which of the following is an example of a subjective scale that can be used for data sensitivity and criticality?
A. Very Low, Low, Moderate, High, and Very High
B. Dollar value of the asset
C. Public, Private, Proprietary, and Confidential
D. Top Secret, Secret, and Confidential
4. Your company is going through the process of classifying its assets. It is starting the process from scratch, so which of the following best describes the order of steps needed for asset classification?
A. Classify assets, identify assets, and inventory assets
B. Identify assets, inventory assets, and classify assets
C. Classify assets, inventory assets, assign security controls to assets
D. Identify assets, assign security controls to assets, classify assets
2.1 ANSWERS
1. B Conducting a business impact analysis (BIA) can help you to not only identify critical business processes but also identify the assets that support them and assist you in determining asset criticality.
2. C Data are individual elements of knowledge or fact, such as an IP address, TCP port number, or audit log security event entry without context. An example of information (data placed into context) would be an analysis of a connection event between two hosts and the traffic that is exchanged between them, which would consist of multiple pieces of data.
3. A Subjective values are typically nonquantitative and offer a range that can be applied to both criticality and sensitivity, in this case a qualitative scale from very low to very high. Dollar value of the asset would be a quantitative or objective measurement of criticality and would not necessarily apply to sensitivity of assets. Commercial sensitivity labels, such as Public, Private, Proprietary, and Confidential, would not necessarily apply to criticality of assets. Top Secret, Secret, and Confidential are elements of government or military classification systems and do not necessarily denote criticality, nor would they apply to a commercial company.
4. B The correct order of steps is identify the assets, inventory the assets, and classify the assets by sensitivity and criticality. Assigning security controls to protect an asset comes after its criticality and sensitivity are classified.
 Establish information and asset handling requirements
Establish information and asset handling requirements
This objective is a continuation of our discussion on how to classify and handle sensitive information assets (both information and the systems that process it). In Objective 2.1 we discussed how assets in general, and information specifically, are categorized (or classified) by criticality and sensitivity. This objective takes it a little bit further by discussing how those classification methods affect how an asset is handled during its life.
Information and Asset Handling
An organization’s data sensitivity or classification policy assigns levels of criticality or sensitivity to different types of information (e.g., private information, proprietary information, and so on). Controls or countermeasures are assigned to protect sensitive and critical data based on those classification levels. Assets with higher criticality or sensitivity classification labels obviously get more protection because of their greater value to the organization. We’re going to further that discussion in this objective by focusing on how information is actually handled as a result of those classifications.

EXAM TIP Remember that assets are classified according to criticality and/or sensitivity.
Handling Requirements
Information has a life cycle, which we will discuss at various points in this book. For now, the stages of the life cycle that you should be aware of are those that involve how information is handled during storage (at rest), physical transport, transmission (in transit), and when it is transferred to another party. We will discuss other aspects of the information life cycle later, to include generating information as well as its disposal.
The following general handling requirements apply to information assets regardless of where they are in their life cycle:
• Encryption for information in storage and during transmission
• Proper access controls, such as permissions
• Strong authentication required to access information assets
• Physical security of information assets
• Positive control and inventory of assets
• Administrative controls, such as policies and procedures, which dictate how information assets are handled
We will now examine how these handling requirements apply to information assets in various stages, such as storage, transportation, transmission, and transfer.
Storage
Information in storage, often referred to as data at rest, is information that is not currently being accessed or used. Storage can mean that it resides on a hard drive in a laptop waiting to be processed or used, or stored in a more permanent environment for archival purposes or as part of a backup/restore strategy. It’s important to make the distinction between information that has been archived and information that is simply backed up for restoration in the event of a disaster.
Archived information is often what the organization may be required to keep for a specified time period due to regulatory or business requirements, but that information will not be used to restore data in the event of an incident or disaster. The organization’s information retention policies, articulated with external governance requirements, typically indicate how long information must be archived. In general, it is a good practice to archive information only to the minimum extent mandated by regulation or business requirements. Keeping information archived after it is no longer required to be retained is not a good practice because it may eventually be compromised or misused. Information that is backed up to restore data that is lost is stored on backup media locally on site or, preferably, off site, such as in the cloud or an offsite physical storage location.
Regardless of whether information is stored for archival or backup purposes, specific protections should be in place for handling:
• Encryption of backup or archival media
• Access permissions to backup or archival media
• Strong authentication required to access media
• Physical security of archived or backed up information, to include locked or secure storage, physical access logs, proper markings, and so on
• Inventory of information stored as well as the media and devices that store it
• Administrative controls, such as archival and backup/restore procedures, two-person control, and so on
Transportation
Physically transporting information assets, such as archival or backup media, decommissioned workstations, or new assets that are transferred to another geographic location within the organization, requires special handling. In addition to the controls we’ve already mentioned, such as encrypting media and requiring strong authentication to access media and devices, the physical transportation of information assets may include additional physical controls. Maintaining positive control by any individuals assigned to transport sensitive information assets is one such consideration; information assets may require constant presence of someone assigned to escort or guard the asset while it is being transported, as well as a strong chain of custody during transport.
Transmission
Information that is digitally transferred, also known as data in transit, is typically protected by the use of strong authentication controls and encryption. These measures ensure that information is not intercepted during transmission, and that it is sent, received, and decrypted only by properly authenticated individuals.
Cross-Reference
We’ll discuss transmission security in more depth in Domain 3.
Transfer
When information assets are transferred between individuals or parties, it usually involves a physical transfer of media or systems. However, logical transfer between entities, such as transmitting protected health data, also involves specific protections unique to transferring information assets. All of these protection methods have already been discussed but may apply uniquely to instances of transferring assets, such as:
• Encrypting storage or transmission media prior to transfer
• Implementing strong authentication controls to ensure that personnel are authorized to send or receive information assets
• Positive control and inventory of physical assets, such as systems
• Administrative, technical, and physical procedures for verifying identities of transferring parties
Information Classification and Handling Systems
As you can see from the previous discussion, information classification schemes directly dictate how information assets are handled, both physically and logically. Information classification and handling schemes are usually categorized in two ways for the CISSP exam: those that apply to commercial or private organizations and those that are used by government and military organizations. We will discuss both briefly, as well as offer examples of each.
Commercial/Private Classification Handling
Commercial and private organizations have a myriad of information classification and handling systems, so the classification levels we discuss here only serve as examples. Because of the wide variety of information types, organizations may have many of these classification levels, which apply to handling sensitive (but not necessarily critical) information assets. Table 2.2-1 lists some of these classification levels as examples.
TABLE 2.2-1 Examples of Commercial and Private Information Classification and Handling Labels
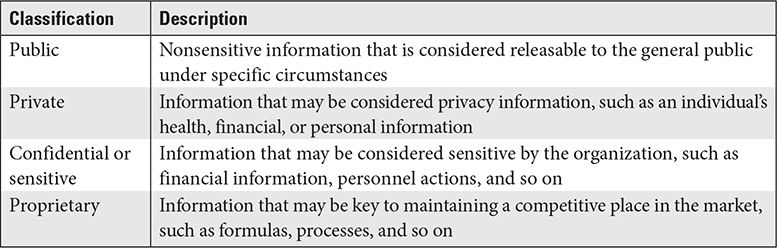
U.S. Government Classification and Handling
Many government agencies have their own classification and handling systems, and one of the most well-known is the system used by the U.S. government and the U.S. armed forces. Table 2.2-2 describes those classification and handling levels. Note that this system describes the relative sensitivity of information and systems, not criticality.
TABLE 2.2-2 U.S. Government Classification and Handling Levels
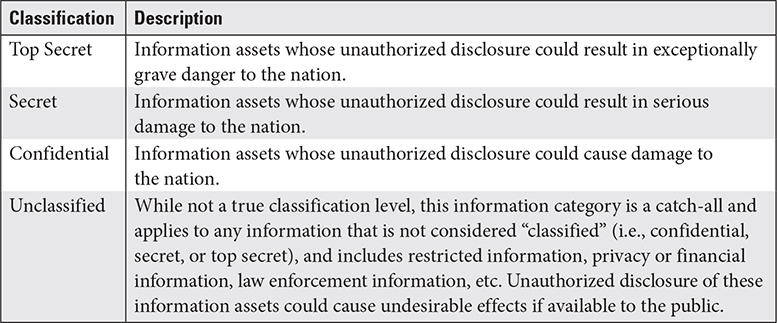
Note that different information types may have handling requirements prescribed based on their sensitivity levels and regulations that address those information types. For example, protected health information (PHI), which is addressed by the Health Insurance Portability and Accountability Act (HIPAA), has its own special handling requirements.
REVIEW
Objective 2.2: Establish information and asset handling requirements In this objective we looked at the different aspects of information asset handling, including storage, transportation, transmission, and transfer. We examined different methods of protecting information as it is being handled, such as encryption, strong authentication, access controls, physical security, and other administrative controls. We also discussed different information handling requirements, such as those that a private company may have and those of government agencies and military services. These include the different handling requirements for information designated as Public, Private, Confidential, and Proprietary (labels often used in the private or commercial sector) and information designated as Top Secret, Secret, Confidential, and Unclassified (used, for example, in the U.S. government and military services).
2.2 QUESTIONS
1. You are a cybersecurity analyst in your company and you have been tasked with ensuring that hard drives containing highly sensitive information are transported securely to one of the company’s branch offices located across the country for use in its systems there. Which of the following must be implemented as a special handling requirement to ensure that no unauthorized access to the data on the storage media occurs?
A. Handling policies and procedures
B. Storage media encryption
C. Data permissions
D. Transmission media encryption
2. You are a cybersecurity analyst working for a U.S. defense contractor, so you must use government classification schemes to protect information. Which of the following classification labels must be used for information that may cause serious damage to the nation if it is disclosed to unauthorized entities?
A. Top Secret
B. Proprietary
C. Secret
D. Confidential
2.2 ANSWERS
1. B While each of these is important, encrypting the storage media on which the information resides is critical to ensuring that no unauthorized entity accesses the data during the physical transportation process. Information handling policies and procedures should include this requirement. Data permissions are only important after the media reaches its destination since authorized personnel will then be able to decrypt the drive and, with the correct permissions, access specific data on the decrypted media. Since the media is being physically transported, transmission media encryption is not an issue here.
2. C Information whose unauthorized disclosure could cause serious damage to the nation is labeled as Secret in the classification scheme used by the U.S. government and military services.
 Provision resources securely
Provision resources securely
In this objective we discuss how to ensure that organizational information resources are made available to the right people, at the right time, and in a secure manner. This is only made possible through strong security of information assets and good asset management, both of which we will discuss in this objective.
Securing Resources
Asset security is about protecting all the resources an organization deems valuable to its mission. This is true whether the assets are data, information, hardware, software, equipment, facilities, or even people. Information assets (which consist of both information and systems) must be secured by a variety of administrative, technical, and physical controls. Examples of these controls include encryption, strong authentication systems, secure processing areas, and information handling policies and procedures. In order to secure these resources, we must consider items such as information asset ownership, the control and inventory of assets, and how these assets are managed.
Asset Ownership
Asset ownership refers to who is responsible for the asset, in terms of maintaining it and protecting it. Remember that information assets are there to support the organization’s business processes. The asset owner may or may not be the owner of the business process that the asset supports. In any event, the asset owner must ensure that the asset is maintained properly and that security controls assigned to protect the asset are properly implemented.
Assets can be assigned owners based on the critical business processes the assets support or other functional or organizational structures, such as the function of the business process or the department that funds the asset. In any event, asset owners must be aware of their responsibilities in maintaining and securing assets.

EXAM TIP Asset and business process owners may not be the same, as assets may be owned by another entity, especially when an asset supports multiple business processes.
Asset Inventory
As mentioned in Objective 2.1, an asset inventory can be developed by performing a business impact analysis, which identifies and inventories critical business processes and the assets that support those processes.
In their simplest form, inventories of equipment, particularly hardware and facilities, are relatively easy to maintain but must be consistently managed. Some aspects of maintaining a good asset inventory include
• Tracking assets based on asset value, criticality, and sensitivity
• Assigning to assets owners who are responsible for their maintenance and security
• Maintaining knowledge of an asset’s location and status at all times
• Giving special attention to high-value assets, including tracking by serial number, protection against theft or misuse, and more frequent inventory updates
There may be some differences in how the organization assigns value to, inventories, and tracks tangible assets versus intangible assets, as discussed next.
Tangible Assets
Tangible assets, as previously described, are those that an organization can easily place a value on and interact with directly. These include information, pieces of hardware, equipment, facilities, software, and so on. These assets can more easily be inventoried and should be tracked from multiple perspectives, including the following:
• Securing the asset from theft, damage, or misuse
• Ensuring critical maintenance activities are performed to keep the asset functional
• Replacing component parts when needed
• Managing the asset’s life cycle, which includes acquisition, implementation, and disposal phases
Intangible Assets
Managing intangible assets is not as easy as managing tangible ones. Remember that intangible assets are those that cannot be easily assigned a monetary value, counted in inventory, or interacted with. Examples of intangible assets include things that are nebulous in nature and may radically change in value or substance at a moment’s notice, such as consumer confidence, standing in the marketplace, company reputation, and so on. While there are many qualitative measurements that can be conducted to determine the relative point-in-time value of these intangible assets, such as statistical analysis, sampling, surveys, and so on, these measurements are simply good guesses at best. Additionally, since the value of intangible assets fluctuates frequently and sometimes wildly, these measurements must be constantly reassessed. An organization can’t simply “inventory” consumer confidence once and expect that it will be the same the next time it is measured; these assets must be measured constantly.
Asset Management
Asset management is not only about maintaining a good inventory. Overall asset management ensures that resources, including information assets, are provided to the people and processes that need them, when they need them, and in the right state, in terms of function and performance. A critical part of asset management is secure provisioning, which involves providing access to information assets only to authorized entities. Secure provisioning is the collection of processes that ensure that only authorized, properly identified, and authenticated entities (usually individuals, processes, and devices) access information and systems and can only perform the actions granted to them. Secure provisioning typically involves
• Verifying an entity’s identity (authentication)
• Verifying the entity’s need for access to systems and information (authorization)
• Creating the proper access tokens (e.g., usernames, passwords, and other authentication information)
• Securely providing entities with authentication and access tokens
• Assigning the correct authorizations (rights, permissions, and other privileges) for entities to access the resource based on need-to-know, job position or role, security clearance, and so on
• Conducting ongoing privilege management for assets
Note that secure provisioning is only one small part of end-to-end asset management. As mentioned, we will discuss the full asset management life cycle in later objectives.
REVIEW
Objective 2.3: Provision resources securely In this objective we further discussed managing information assets. We examined the concepts of information asset ownership and noted that the business process owner the asset supports is not always the same individual who owns the asset. Asset owners have the responsibility of maintaining and securing any assets assigned to them. Assets must be inventoried and tracked based on criticality, sensitivity, and value to the organization, whether that value is expressed in monetary terms or not. Tangible assets are much easier to manage because they can be physically counted, tracked, located, and assigned a dollar value. Intangible assets are more difficult to manage and can change in value frequently. Intangible assets include consumer confidence, company reputation, and marketplace share. Intangible assets can be measured using qualitative or subjective methods but must be measured constantly.
Asset management involves not only inventory of assets, but also providing assets to the right people, at the right time, and in the state they are required. This starts with secure provisioning of assets. Secure provisioning includes creating access tokens and identifiers, enforcing the proper identification and authentication of entities, and authorizing actions an entity can take with an asset.
2.3 QUESTIONS
1. Your supervisor wants you to assign asset values to certain intangible assets, such as consumer confidence in the security posture of your company. You consider factors such as risk levels, statistical and historical data relating to security incidents within the company, and other factors. You also consider factors such as cost of various aspects of security, including systems and personnel. Which of the following is the most likely type of value you could assign to these assets?
A. Quantitative values based on customer confidence surveys
B. Quantitative values related to cost versus revenue
C. Qualitative descriptive values of very low, low, moderate, high, and very high
D. Qualitative values related to cost versus revenue
2. You are a cybersecurity analyst who is in charge of routine security configuration and patch management for several critical systems in the company. One of the systems you work with is a database management system that supports many different departments and lines of business applications within the company. Which of the following would be the most appropriate asset owner for the system?
A. Information technology manager for the company
B. Asset owner who is chiefly responsible for maintenance and security of the asset
C. Multiple business process owners sharing asset ownership
D. Business process owner for the most critical line of business application
2.3 ANSWERS
1. C Any value assigned to intangible assets will be qualitative in nature; subjective descriptive values, such as very low, low, moderate, high, and very high are the most appropriate values for intangible assets since it is difficult to place a monetary value on them.
2. B Since the asset supports many different business processes and owners, the system should be owned by someone who is directly responsible for maintenance and security of the asset; however, they may be further responsible and accountable to any or all of the business process owners.
 Manage data lifecycle
Manage data lifecycle
In this objective we will discuss the phases of the data life cycle, as well as the roles different entities have with regard to using, maintaining, and securing data throughout its life cycle. We will also discuss different interactions that can occur with information, such as its collection, maintenance, retention, and destruction. Additionally, we will look at aspects of data that should be closely monitored, including its location and data remanence.
Managing the Data Life Cycle
Data has a formalized life cycle, which starts with its creation or acquisition. There are several data life cycle models that exist, but a commonly referenced one from the U.S. National Institute of Standards and Technology (NIST). NIST Special Publication (SP) 800-37, Revision 2, defines the information life cycle as “The stages through which information passes, typically characterized as creation or collection, processing, dissemination, use, storage, and disposition, to include destruction and deletion.” The rest of this objective discusses the roles that individuals and other entities play during the data life cycle and how they are involved in various data life cycle activities.
Data Roles
Managing an organization’s data requires assigning sensitivity and criticality labels to the data, assigning the appropriate security measures based on those labels, and designating the organizational roles responsible for managing data within the organization. While an organization may not formally assign data management roles, some regulations require formal data ownership roles (e.g., the General Data Protection Regulation, or GDPR, as covered later in this objective). Data management roles can be held legally accountable and responsible for the protection of data and its disposition. Note that many of these roles can overlap in role and responsibility unless governance specifically prohibits it.

ADDITIONAL RESOURCES NIST SP 800-18, Revision 1, details different data management roles.
Most data management roles must be formally appointed by the organization, and access to data may be granted only if an entity meets certain criteria, based on regulations, including the following:
• Security clearance
• Need-to-know
• Training
• Statutory requirements
Data Owners
A data owner is an individual who has ultimate organizational responsibility for one or multiple data types. A data owner typically is an organizational executive, such as a senior manager, a vice president, department head, and so on. It could also be someone in the organization who has the legal accountability and responsibility for such data.
The data owner and asset owner may not necessarily be the same individual (although they could be, depending on the circumstances); remember from Objective 2.3 that an asset owner is the individual who is accountable and responsible for assets or systems that process sensitive data. Both data and system (asset) owners typically have the following responsibilities:
• Develop a system or data security plan
• Identify access requirements for the asset
• Implement and manage the security controls for systems or data
Controllers, Custodians, Processors, Users, and Subjects
While there are many commonsense roles associated with managing data in an organization, there are some other key roles you should understand. Some roles are defined and required by regulation, such as a data controller. A data controller is the designated person or legal entity that determines the purposes and use of data within an organization. This is normally a senior manager in most organizations.
A data processor is a person who routinely processes data in the performance of their duties; this may be someone who performs simple data entry tasks, views data, runs queries on data, and so forth. Note that this is a generalized description of the data processor, but one regulation in particular, the European Union’s General Data Protection Regulation (GDPR), specifically defines a data processor as someone who provides services to and processes data on behalf of the data controller. Data processors don’t have to be individuals; a third-party service provider contracted to process data on behalf of a data controller also fits this definition.

NOTE Another role that GDPR requires is the Data Protection Officer, which is a formal leadership role responsible for the overall data protection approach, strategy, and implementation within an organization. This person is also normally accountable for GDPR compliance.
A data custodian is a more generalized role and is an appointed person or entity that has legal or regulatory responsibility for data within an organization. An example would be appointing someone in a healthcare organization as the custodian for healthcare data. This might be a data privacy officer or other senior role; however, all data management roles have some custodial responsibility to varying degrees.
Data users are simply those people or entities that use data in their everyday job. They could simply access data in a database, perform research, or conduct data entry or retrieval.

EXAM TIP Remember that a data user is someone who uses the data in the normal course of performing their job duties; a data subject is the person about whom the data is used.
Finally, a data subject is the person whose personal information is collected, processed, and/or stored. If a person submits their personal, healthcare, or financial information to another entity, that person is the subject of the data. The overall end goal of privacy is to protect the subject of the data from the misuse or unauthorized disclosure of their data.

NOTE The EU’s GDPR formally defines critical roles in managing data, including the controller, processor, and subjects.
Data Collection
Data collection is an ongoing process which occurs during routine transactions, such as inputting medical data, filling out an online web form with financial data, and so on. Data collection can be formal or informal and performed via paper or electronic methods. The key to data collection is that organizations should only collect data they need either to fill a specific business purpose or to comply with regulations, and no more. This constraint should be expressed in the organization’s data management policies (e.g., data sensitivity, privacy, etc.).
Data Location
Data location refers to the physical location where the data is collected, stored, processed, and even transmitted to or from. Data location is an important consideration, since data often crosses state and international boundaries, where laws and regulations governing it may be different. Some countries exert a concept known as data sovereignty, which essentially states that if the data originates from or is stored or processed in that country, their government has some degree of regulatory oversight over the data.
Cross-Reference
Objective 1.5 discussed data localization laws (also called data sovereignty laws), which touch on the legal ramifications of data location.
Data Maintenance
Data maintenance is a process that should be performed on a regular basis. Data maintenance includes many different processes and actions, including
• Validating data for proper use, relevancy, and accuracy
• Archiving, backing up, or restoring data
• Properly transferring or releasing data
• Disposing of data
Data maintenance actions should be documented and only performed by authorized personnel, in accordance with the organization’s policies and governing regulations.
Data Retention
Data retention comes in two forms:
• Backing up data so it can be restored in the event it is lost due to an incident or natural disaster. This is a routine business process that should be performed on critical data so that it can be restored if something happens to the original source of the data.
• Archiving data that is no longer needed. This involves moving data that is no longer used but is required for retention due to policy or legal requirements to a separate storage environment.
As a general rule, an organization should only retain data that it absolutely needs to fulfill business processes or comply with legal requirements, and no more; the more data that is retained, the higher the chances are of a breach or legal liability of some sort. The organization should create a data retention policy that complies with any required laws or regulations and details how long data must be kept, how it must be stored, and what security protections must be afforded it. Any retained data should be inventoried and closely monitored for any signs of unauthorized access or use.

EXAM TIP Understand the difference between a data archive and a data backup. A data archive is data that is no longer needed but is retained in accordance with policy or regulation. A data backup is created to restore data that is still needed, in the event it is lost or destroyed.
Data Remanence
Data remanence is that which remains on a storage media after the media has been sanitized of data. It could be simply random ones and zeros, file fragments, or even human- or machine-readable information if the sanitization process is not very thorough. Data remanence is a problem when data remains on media that is transferred to another party or reused. The best way to solve the data remanence problem is destruction of the media on which it resides.
Data Destruction
Data destruction refers not only to the process of destroying data itself by wiping data from storage media, but also destroying paper copies and any other media on which data resides. Media includes hard drives, USB sticks, optical discs, and so on. In the case of routine or noncritical data destruction, it may simply be enough to degauss hard drives or smash SD cards and optical discs. If the data is very sensitive, often the destruction must be witnessed and documented by more than one person, with the process recorded and verified. The following are common methods of destroying sensitive data and the media on which it resides:
• Burning or melting
• Shredding
• Physical destruction by smashing media with hammers, crowbars, etc.
• Degaussing hard drives or other magnetic media
REVIEW
Objective 2.4: Manage data lifecycle In this objective you learned about the data life cycle, as well as some of the activities that go on during that life cycle. We also discussed the different roles that entities play in the data life cycle, such as data owners, controllers, custodians, processors, users, and data subjects. We also covered various activities that are critical to managing data during its life cycle, including its collection, storage or processing, location, maintenance activities that must be performed on data, how data is retained and destroyed, and data remanence.
2.4 QUESTIONS
1. You are drafting a data management policy in order to adhere to laws and regulations that apply to the various types of personal data your organization collects and processes. Which of the following would be the most important consideration in developing this policy?
A. Cost of security controls used to protect data
B. Appointment of formal data management roles
C. Manual or electronic methods of collecting data from subjects
D. Background check requirements for data users in the organization
2. Your organization has developed formalized processes for data destruction, some of which require witnesses for the destruction due to the sensitivity of the data involved. Which of the following is the organization trying to reduce or eliminate?
A. Data collection
B. Data retention
C. Data remanence
D. Data location
2.4 ANSWERS
1. B While all of these may be important considerations for the organization and its data management strategy, to be compliant with certain data protection regulations the organization must appoint formal data management roles. Cost of security controls isn’t considered or addressed by policy, nor is the method of collecting data from subjects. Background check requirements for employees who use data in the organization are typically addressed by other policies.
2. C The organization, through a comprehensive destruction process, is attempting to reduce or eliminate any data remanence that may be compromised or accessed by unauthorized entities. Data collection is part of its business processes that it must also address, as is retention and location, but these are not addressed through data destruction.
 Ensure appropriate asset retention (e.g., End-of-Life (EOL), End-of-Support (EOS))
Ensure appropriate asset retention (e.g., End-of-Life (EOL), End-of-Support (EOS))
In Objective 2.4 we discussed data retention; in this objective we will expand that discussion to examine asset retention in general. There are issues that an organization must consider during its asset life cycle, including an asset’s normal end-of-life point and how to replace it and dispose of it.
Asset Retention
In our coverage of data retention in Objective 2.4 we discussed how the organization should only retain data that is necessary to fulfill business processes or legal requirements, and no more. Retaining unnecessary data presents a greater chance of compromise or unauthorized access. Similarly, an organization needs to consider retention issues related to its other assets, such as systems, hardware, equipment, and software, and develop a life cycle for those assets.

CAUTION Data should only be retained when required due to governance (i.e., laws, regulations, and policies) or to fulfill business process requirements. Retaining data unnecessarily subjects the organization to risk of data compromise and legal liability.
Asset Life Cycle
The asset life cycle is similar to the general data life cycle. Assets are acquired (software may be developed or purchased and hardware may be bought or constructed) and go through a life cycle that includes implementation, maintenance (sometimes called sustainment), and finally disposal. The asset life cycle typically contains the following phases (although there are many versions of the asset life cycle promulgated in different industries and communities):
• Requirements Establish the requirements for what the asset needs to do (function) and how well it needs to do it (performance)
• Design and architecture Establish the asset design and overall fit into the architecture of the organization
• Development or acquisition Develop or purchase the asset
• Testing Test the asset’s suitability for its intended purpose and how well it integrates with the existing infrastructure
• Implementation Put the asset into service
• Maintenance/sustainment Maintain the asset throughout its life cycle by performing normal activities such as repair, patching, upgrades, etc.
• Disposal/retirement/replacement Determine that the asset has reached the end of its usable life and replace it with another asset, as well as dispose of it properly
As mentioned, these are generic asset life cycle phases; different asset management and systems/software engineering methodologies have similar phases but may be referred to differently.
End-of-Life and End-of-Support
Assets normally have a prescribed life cycle, at the end of which they are often replaced or must be disposed of. Additionally, some assets may outlive their useful life cycle because organizations are reluctant to replace assets that are costly or have a specialized purpose. Often, replacing an asset involves retooling or re-architecting an entire infrastructure. New assets, especially complex systems, often require additional training on their use and maintenance.
In any event, some assets are also no longer supported by the manufacturer or developer. This may be because the asset has outlived its useful life and there is a newer asset that can perform its function far better, more efficiently, or more securely. An example is the Windows 7 operating system, which lost its official support from Microsoft in January 2020. End-of-support means Microsoft will no longer provide patches, updates, or support for issues that result from still running that particular operating system version. However, even in 2022, there are still legacy systems running Windows 7. This is a good example of the difference between the terms end-of-life and end-of-support. End-of-life means that the asset no longer fulfills its intended purpose, is obsolete, broken, or the organization’s need for it has passed. It must be replaced by a newer asset. End-of support, however, means that the asset may still be functioning as intended, it still serves its purpose, and the organization will still use it, albeit at a greater risk, however, since its vendor no longer offers maintenance, upgrades, and so on.

EXAM TIP End-of-life means that the item is no longer viable or functional as required. End-of-support simply means that its manufacturer no longer services it, regardless of its level of functionality.
When an asset, such as software or a piece of hardware, exceeds its end-of-life point or its end-of-support time, the organization must decide how to best handle replacing the asset, if its function is still needed, and then what to do with the asset. Some assets can be donated to other organizations, and some can be repurposed, but many assets must be destroyed.
Replacement, Destruction, Disposal
Replacing an asset with one that performs similar functions is not the only consideration when the asset reaches its end-of-life. In addition to being able to perform similar functions as the asset it replaces, the organization should consider performance factors when replacing an asset. The asset not only must perform the original function but, ideally, should perform it more efficiently, effectively, and securely. An organization may require new features when it replaces an asset or it may require the asset to have certain characteristics that make it interoperable with newer technologies
Once an asset is replaced, the organization has to decide how to dispose of it. Often, donating an asset, such as a general-purpose computer system, may be an option, particularly if another organization can use it for purposes that don’t require as much functionality or performance capability of the asset. (Think of an organization that replaces all of its desktops, and then donates those computers to a school or charity.) However, before the asset is repurposed or transferred to another organization, it must be cleared of all sensitive data; in fact, any data on the system should be purged so that it can never be accessed again by unauthorized entities, as discussed in Objective 2.4. This is where steps to remove all data remanence are performed; storage media such as hard drives are removed from the asset or, at a minimum, wiped to destroy data on the media.
Some assets can’t be transferred or repurposed. Assets that are typically specialized use items may have applications that the organization does not wish to allow someone else to make use of. Consider an outdated but still sophisticated system that performs a particular manufacturing process that the organization does not want to be repeated by a competitor. Or think of systems with military-specific applications that should not be transferred to the general public. These types of systems will likely be destroyed rather than repurposed. They will still go through the typical steps of being purged of sensitive data, but then the hardware will generally be destroyed so that it can no longer be used or reverse engineered.
REVIEW
Objective 2.5: Ensure appropriate asset retention (e.g., End-of-Life (EOL), End-of-Support (EOS)) In this objective you learned about general asset retention principles, including the asset life cycle and how an asset’s end-of-life and end-of-support points affect an organization’s decisions regarding whether to replace the asset, repurpose it, or otherwise destroy it.
2.5 QUESTIONS
1. Your company has requirements for a new piece of engineering software that must have specific characteristics. The software is replacing an older software package that was developed internally and, as such, lacks many new features and modern security mechanisms. The organization has determined that it is not cost-effective to employ teams of developers to create a new application. In which phase of the asset life cycle would the organization be when replacing the software package?
A. Acquisition
B. Disposal
C. Implementation
D. Maintenance
2. You work for a company that is replacing all of its laptops on a four-year cycle. The company has performed a study and concluded that no other organization could use the laptops to gain a competitive edge, as they are general-purpose devices reaching the end of their useful life for the requirements of the company. The organization has also taken the steps of removing all internal hard drives and other media containing data from the laptops. Which of the following would be the best means of disposal for the laptops?
A. Place them in storage in the hopes that they will be used again within the company
B. Contract with an outside company to destroy the laptops
C. Donate the laptops to a school or other charity
D. Dispose of them by placing them in the trash
2.5 ANSWERS
1. A The company would be at the acquisition phase of the asset life cycle. Since it has already created requirements for the new software and has decided not to develop software internally, the company is faced with purchasing or licensing the software from an outside source. The acquisition phase allows the organization to acquire software without expending efforts and resources toward development. The scenario does not mention how the organization wishes to dispose of its older software, and it is already past the implementation and maintenance phases with the older software package.
2. C The most cost-effective, efficient, and environmentally friendly method of disposal would be to donate the laptops to a school or other type of charity. Since they have already been stripped of the media that contain sensitive data, they can provide no competitive edge to anyone else, and schools and charities most likely have lesser computing requirements than the company. It may not be cost-effective to contract with a local company to destroy them, and storing them for later use within the company is impractical since they have already reached the end of their useful life. Placing them in the trash may not be cost-effective or efficient, as regulations likely exist regarding recycling or sanitary disposal of sensitive electronic components in the laptops.
 Determine data security controls and compliance requirements
Determine data security controls and compliance requirements
In this last objective for Domain 2, we will discuss the security controls implemented to ensure asset security, with a specific focus on data/information security. We will also discuss how compliance influences the selection of security controls and how security controls are scoped and tailored. Additionally, we will cover three key data protection methods specified in the CISSP objectives: digital rights management, data loss prevention, and the cloud access security broker.
Data Security and Compliance
The controls for securing and protecting information cannot just be randomly picked. Many factors go into control selection, some of which include the state the data is in, the type of data, and the governance requirements for the data. Data states influence which controls are used, and how controls are implemented to meet the specific needs of the data that requires protecting.
Data States
Raw data and, when placed in context, information are categorized as always being in one of three states: at rest, in use (or in process), and in transit. Many of the security controls that are selected to protect data are focused on one or more of these three states, which we will discuss next.
Data in Transit
Data in transit is simply data that is being actively sent across a transmission media such as cabling or wireless. Data in this state is vulnerable to eavesdropping and interception if it is not properly protected. Controls traditionally used to protect data while in transit include strong authentication and transmission encryption. Examples of protocols and other mechanisms used to protect data during transmission include Transport Layer Security (TLS), Secure Shell (SSH), hardware encryption devices, and so on.
Data at Rest
Data at rest is data that is in permanent storage, such as data that resides on a system’s hard drive. It is data that is not being actively transmitted or received, nor is it actively being processed by the system. In this state, data is subject to unauthorized access, copying, deletion, or removal. Controls typically used to protect data while at rest include access controls such as permissions, strong encryption, and strong authentication.
Data in Use
Data in use is data that is in a temporary or ephemeral state, characterized by data being actively processed by a device’s CPU and residing in volatile or temporary memory, such as RAM for example. During this state of being in use, data is transferred across the system bus to interact with various software and hardware components, including the CPU and memory, as well as the applications that use the data. Data in this state is destined to be read, transformed or modified, and returned back to storage.
This data state has been a traditional weakness in data and system security, in that data cannot always be fully protected by controls such as encryption. For example, different software and hardware components may not work with selected security controls because they need direct, unrestricted access to data. Only recently have efforts been made to protect data while it is being actively processed, and typically the controls that are used to protect it are now included in system hardware and software components. Advances in hardware and software have facilitated implementation of controls such as encrypting data between the storage device and the CPU on the system bus, memory protection, process isolation, and other security measures.

EXAM TIP Data exists in three recognized “states”: at rest (in storage), in transit (being transmitted), and in use (being actively accessed and processed in a device’s CPU and RAM).
Control Standards Selection
Selecting controls to protect information and other assets is not an arbitrary decision. Organizations use control standards such as the ISO/IEC 27000 series, the Center for Internet Security (CIS) Critical Security Controls (CIS Controls), or the National Institute of Standards and Technology (NIST) security controls (NIST SP 800-53, Revision 5, Security and Privacy Controls for Information Systems and Organizations) based upon several factors, including the data type (e.g., financial data, healthcare data, personal data, etc.), the level of protection needed (based on the sensitivity and criticality of the data), and, most importantly, compliance with governance. Very often, governance is the deciding factor, since some sensitive data types, such as credit card information, must be protected according to a specific control set.
Beyond governance, an organization may choose control standards because of the industry they are involved in or, data protection needs, or its management culture. For example, defense contractors providing services to the U.S Department of Defense typically follow the NIST controls by default because the U.S. federal government requires contractors to comply with those controls.
Scoping and Tailoring Data Security Controls
Regardless of the control standard that an organization chooses to protect its sensitive data, there are several factors that go into determining which controls the organization uses, and to what depth the organization implements the controls to protect its information. Controls are not simply implemented in a “one-size-fits-all” fashion; the controls selected, as well as their level of implementation, can be scoped and tailored appropriately to the organization’s information protection requirements.
Considerations in scoping and tailoring information security controls include factors we discussed in Objective 1.10 when we talked about risk management, including the criticality and sensitivity of the data. The more critical or sensitive the data, the more stringent the controls that must be put into place to protect it. Another issue is the overall value of the data or asset to the organization. The organization conducts a cost/benefit analysis to determine if the value of the asset to the organization is far less than the cost to implement and maintain a control to protect it.
Governance also figures into this scoping and tailoring effort. Some laws and regulations require a specific level of control implementation, in addition to the basic standard they impose. For example, financial regulations require that personal financial information be encrypted, using a specific encryption strength or algorithm.
In any event, selecting controls and tailoring them the right way to protect data in critical assets at the level the organization requires is an exercise in risk management, as we discussed in Objective 1.10.
Data Protection Methods
This exam study guide covers a variety of data protection methods, but exam objective 2.6 identifies three specific methods that you should be familiar with for the exam, as described in this section. For this objective we will focus on digital rights management (DRM), data loss prevention (DLP), and cloud access security broker (CASB).
Digital Rights Management
Digital rights management (DRM) refers to various technologies that help to restrict access to data so that it cannot be copied or modified by an unauthorized user. DRM most often is implemented to protect copyrighted material, such as music and movies, but it is also used to protect proprietary or sensitive information that an organization produces, such as trade secrets. DRM is regularly implemented in software, and there are some hardware-enabled DRM solutions, such as DVD and Blu-ray players, that won’t play copied or unencrypted discs. Software implementations include protections like watermarking, file or software encryption, licensing limitations, and so on. A popular form of DRM is steganography, which involves concealment of embedded information in computer files. Steganography can be used in a malicious way to hide malware in otherwise innocuous-looking files, but in the DRM arena, it is used to insert digital watermarking into files to protect intellectual property.
Data Loss Prevention
Data loss prevention (DLP) also refers to a wide variety of technologies. In this case, they are used to prevent sensitive data from leaving the organization’s infrastructure and control. Normally DLP is applied judiciously to only the most critical or sensitive data in an organization; using DLP to control every single piece of data that exits the network would be counterproductive and cost-prohibitive. DLP works primarily by assigning labels or metadata to files and other data elements. This metadata indicates the sensitivity of the data and serves as a marker so that devices and applications will not allow it to leave the network through e-mail, file copying, and so on.
The two main types of DLP are network DLP (NDLP) and endpoint DLP (EDLP).
• Network DLP is deployed as various network-enabled applications and devices that scan data leaving the network over transmission media and prevent data identified as sensitive from exiting over e-mail, HTTP connections, file transfers, and so on. NDLP can even intercept secure traffic leaving the company network, such as encrypted traffic, and decrypt that traffic to ensure that no sensitive data is leaving the company network.
• Endpoint DLP focuses on the end-user device, such as a workstation, and takes steps to ensure that data remains encrypted, is only accessible by authorized users, and cannot be copied from the device, such as through the use of USB and other removable media. EDLP prevents data from being copied from a centralized network storage location, which may even be the user’s workstation. More often than not, hybrid solutions featuring both of these types of DLP are typically implemented within an organization.
A necessary requirement for DLP to work in an organization is that data must be “inventoried” by type, criticality, and sensitivity. Also, data flows, data processing, and storage locations must be discovered and documented throughout the infrastructure. DLP can control the flow of data within and outside of the network, provided the DLP solution understands where data resides and where it is supposed to flow.
Cloud Access Security Broker
A cloud access security broker (CASB) is a solution that is being used more often as organizations migrate data, applications, and even infrastructure to cloud providers. A CASB is a combination of software and hardware solutions that exist to mediate connections, data access, and data transfer to and from the organization’s cloud storage and infrastructure. This mediation of access includes controls to implement strong authentication and encryption for both data at rest and data in transit. The CASB provides visibility into what users are doing in relation to the organization’s cloud services and applies security policies and controls for the data and applications in use.
The CASB uses two primary methods: proxying, with the use of a CASB appliance that sits in the data path between the organization and cloud assets, and application programming interfaces (APIs), which are integrated with cloud-enabled applications. While the organization may maintain some level of control over how the CASB solution controls access to the organization’s data, the cloud service provider itself is usually responsible for maintaining the technology from functional and performance perspectives.
The primary advantage of using a CASB is centralized control over access to the organization’s cloud-based resources, which provides easy, policy-based management. The disadvantages of using a CASB depend on the implementation method. Proxy-based CASBs must intercept traffic, including traffic that is encrypted by users. This means that encrypted traffic must be decrypted first and examined for security issues, such as data exfiltration, before it is re-encrypted and sent out to the cloud. This can introduce a variety of technical issues, as well as privacy issues, not to mention latency in the network connection. CASB APIs have their own vulnerabilities, which include ordinary software programming vulnerabilities that may be present in faulty code.
REVIEW
Objective 2.6: Determine data security controls and compliance requirements In this final objective of Domain 2 we closed out our discussion of asset security. We discussed various aspects of data security and compliance, including the three typical states of data. We covered the definitions and typical requirements for protection of data in transit, data at rest, and data in use. We also discussed the process for an organization to select security control standards used to protect assets. As part of this discussion, we covered key items an organization must consider when it is scoping and tailoring controls to protect information and other assets. We also covered three key data protection methods required by the exam objectives: DRM, DLP, and CASB.
2.6 QUESTIONS
1. You are a cybersecurity analyst in your company and have been tasked to explore which control standard the company will adopt to protect sensitive information. Your organization processes and stores a variety of sensitive data, including individual personal and financial information for your customers Which of the following is likely the most important factor in selecting a control standard?
A. Cost
B. Governance
C. Data sensitivity
D. Data criticality
2. Gary is a senior cybersecurity engineer for his company and has been tasked to implement a DLP solution. One of the solution requirements is that secure traffic leaving the company network, such as traffic encrypted with TLS, be intercepted and decrypted to ensure that no sensitive data is being exfiltrated. Which of the following must be included in the company’s solution to meet that particular requirement?
A. Network DLP
B. DRM
C. Endpoint DLP
D. CASB
2.6 ANSWERS
1. B Since the organization processes sensitive data that may include personal or financial data of its customers, governance is likely the most important factor to consider when selecting a control standard, since personal and financial data are protected by various laws and regulations. These laws and regulations may require specific control standards. The other factors mentioned are important, but the organization has some leeway when considering those factors.
2. A Network data loss prevention (NDLP) must be included in the company’s solution, since it is used specifically to protect against data being exfiltrated from an organization’s network. Network DLP can be used to intercept encrypted traffic, decrypt and analyze the traffic, and then re-encrypt it before it exits the network. Digital rights management (DRM) and endpoint DLP (EDLP) should also be used as part of a layered solution, but they do not intercept and decrypt network traffic for analysis. A cloud access security broker (CASB) is only required for mediating access control for cloud-based assets.
