Chapter 6. UNIX Forensic Analysis
Cory Altheide and Eoghan Casey
Contents
Introduction to UNIX301
Boot Process304
Forensic Duplication Consideration306
File Systems306
User Accounts326
System Configuration328
Artifacts of User Activities329
Internet Communications339
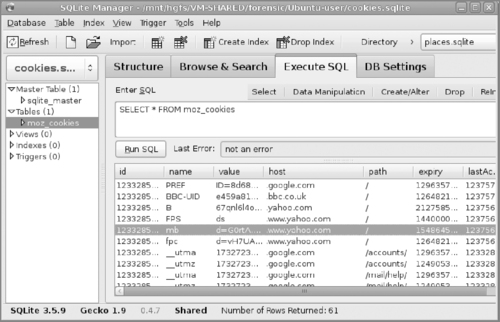
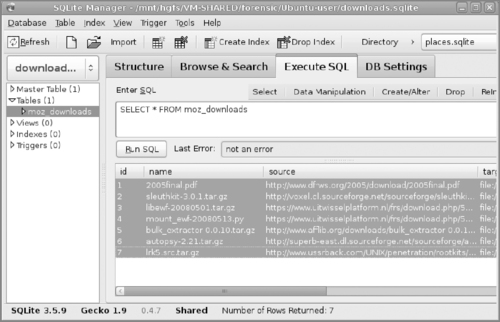
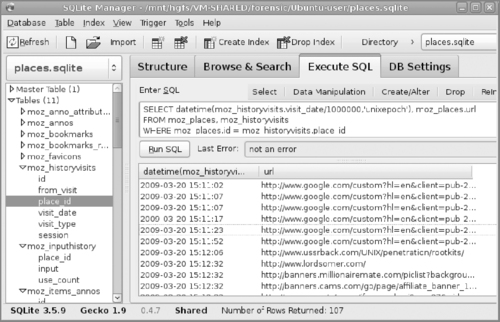
Firefox 3339
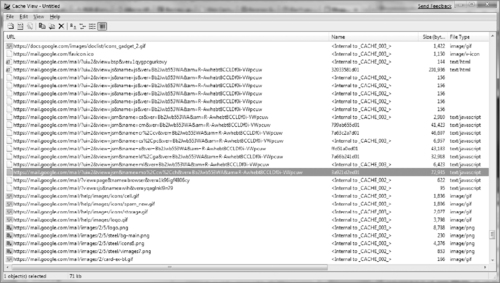
Cache344
Saved Session344
E-Mail Analysis345
Chat Analysis350
Memory and Swap Space351
References351
Introduction to UNIX
UNIX originated in the depths of Bell Labs in the late 1960s. During the 1970s it became widely used in academia, and in the 1980s AT&T released UNIX System V, which saw widespread commercial use. Meanwhile, researchers at UC Berkeley were developing a plethora of useful code additions to the UNIX core, including core networking code that is still in use in modern operating systems. Over time, the licensing costs of these later releases of AT&T's UNIX led the maintainers of the Berkeley Software Distribution to release a UNIX derivative completely free from any AT&T code—the first such release was 4.4BSD-Lite, the precursor of all modern BSD operating systems.
Around the same time, an enterprising Finn named Linus Torvalds released a free Unix clone that would run on the cheap, ubiquitous Intel 386 platform. Together with the GNU userland utilities it became the system known as Linux (or GNU/Linux).
Today, UNIX and Unix-like systems are used for many purposes, from low-end embedded systems to the most powerful supercomputing clusters in the world. In addition to the two main “open” Unix-like systems, several commercial UNIX systems derived from System V are still in use today. Before we discuss them, let us clarify some terminology.
Unix vs. UNIX vs. Unix-like
Today the UNIX trademark and specification are controlled by the Open Group (www.unix.org/what_is_unix.html). There is a certification program to determine if an operating system (or portion thereof) meets the specification. As there is a cost associated with this process, the free Unix variants are not UNIX certified, and thus are not “UNIX.” To avoid confusion, we will refer to all systems that share common Unix characteristics as Unix-like.
Linux
Linux is used to describe any number of operating systems based upon the Linux kernel. These systems generally use code from the GNU project for the core of their userland utilities, and thus you may hear the term GNU/Linux used as well. It can be argued that the more cumbersome GNU/Linux is a more correct description of the total system, however Linux is the more common usage. Linux systems are packaged in distributions. A distribution generically refers to a collection of applications and a Linux kernel. These are usually wrapped together on installation media, and will often come with specific branding, distribution-specific modifications, and a package management system to enable the addition of new or updated software. Popular general purpose distributions include RedHat/Fedora, Ubuntu, Slackware, and SuSE.
Many purpose-specific distributions exist. These are generally stripped down compared to their general-use counterparts, and include distributions designed to operate as web application platforms, wireless routers, firewalls and intrusion detection systems, digital video recorders, and many more. Linux also powers large clusters of low-end computers that operate as a single super-computer. Examples of this setup include the most powerful ranked supercomputing cluster in the world at Los Alamos National Laboratory (www.top500.org/system/9707) and the infrastructure behind Google (http://highscalability.com/google-architecture). At the other end of the scale, Linux powers the current generation of ultraportable netbooks, including the ASUS Eee PC and the One Laptop per Child project.
Given the steady increase in use, it is increasingly probable that at some point in your career you will need to investigate a Linux-based system. Fortunately, familiarity with Linux will transfer over to the other Unix-like systems to varying degrees. At the very least you will be better off knowing Linux than not knowing any Unix-like systems at all.
The BSDs
“The BSDs” refers to the line of Unix-like systems that can trace their origins (directly or indirectly) to the 4.4BSD lineage. Today, this includes FreeBSD, NetBSD, and OpenBSD, FreeBSD being the most widely used of the three. To make very broad generalizations, FreeBSD is used in applications where network throughput and stability is the highest priority, OpenBSD is used in applications where security is the paramount concern, and NetBSD is used when hardware portability is desired. This is not to say that OpenBSD or NetBSD are any less reliable than FreeBSD—after all, NetBSD originated as a fork of the FreeBSD code, and OpenBSD originated as a fork of NetBSD. However, OpenBSD is designed with security as its priority, and NetBSD is designed to be as portable as possible, with ports existing for the Sega Dreamcast and the DEC VAX.
BSD-based desktops and laptops are few and far between, but they do exist (www.pcbsd.org). You are most likely to encounter a BSD-based machine if your investigation involves a web server; particularly of a hosting provider or other enterprise-level web service.
Commercial Unix Operating Systems
There are a number of Unix-like systems developed by computer companies for their specific hardware, including Sun, IBM, Hewlett Packard (HP), and Silicon Graphics, Inc. (SGI).
Solaris is Sun Microsystem's commercial Unix offering that originated in 1992 and is still used extensively in corporate data centers. Originally developed for Sun's own SPARC processor, modern Solaris runs capably on both 32- and 64-bit Intel x86 processors. Additionally, Sun moved to an open source model in 2005 with the release of OpenSolaris. Strengths of Solaris include the ZFS file system, which is capable of holding a 16 exabyte file (should this ever become physically possible), and robust clustering and virtualization support. Solaris systems are not commonly used by individuals, but can be found in business use. If your investigation brings you to one Solaris system, there is a good chance you will end up investigating many more.
AIX is IBM's commercial Unix, which runs on IBM systems using POWER processors. AIX systems are often deployed to run a specific application or applications that leverage the DB2 database and robust availability. AIX is closely tied to the IBM hardware it runs on, and has a reputation for incredible reliability. Due to the cost of the required hardware, AIX systems are almost never seen outside of corporate use. As with Solaris systems, if you need to investigate one system, be prepared to encounter many more.
HP-UX is HP's commercial Unix, which is tied closely to the HP hardware on which it runs. It has similar positives (reliability, clustering) and negatives (cost) compared to the other commercial Unixes. It is also not usually found outside of corporate data centers, and is also generally found in large deployments.
IRIX is a commercial Unix developed by SGI for their hardware that was widely used to support computer animation and graphical rendering.
In this chapter we will focus primarily on Linux but will make an effort to point out differences and caveats when dealing with other systems where applicable. For the most part, userland utilities are either identical or have interoperable analogs on all the Unix-like systems—dealing with kernel-level information and hardware access is where things diverge quickly.
An organization found that intruders had gained unauthorized access to one of their SGI IRIX systems and were using it to store credit card data stolen from various e-commerce sites. Although the computer contained useful evidence relating to the group that was stealing data, no law enforcement agency was equipped to examine an IRIX system. After several weeks of confusion, information security personally in the organization were asked to mount the file system read only from another Unix system and extract the stolen data for law enforcement and credit card companies. To this day, there is very limited support for IRIX in most forensic tools, making recovery of deleted files a challenge.
Boot Process
It is important for forensic examiners to understand the Unix system startup process. Knowledge of startup files can help forensic examiners determine which version of the operating system was running and when it was installed. In addition, when an evidentiary Unix system is inadvertently booted, it may be necessary to explain which files were involved in the startup process and assert that no user-created files or other data of evidentiary significance were modified. Furthermore, because of its open design, almost any aspect of the boot process can be altered, so you need to know where to look for malicious modification.
On system boot, after BIOS checks are performed, bootloader code in the Master Boot Record (MBR) is run. The bootloader loads and executes the kernel, which subsequently spawns the first process identifier (PID 1), called init. From this point the boot process differs between Linux and BSD. There are two major styles of system initialization in the Unix world, and these are unsurprisingly tied to Unix's bifurcated lineage. The two styles are System V and BSD. At the time of this writing BSD systems only ever use BSD style initialization; however, Linux systems may use either style depending upon the distribution.
The first step in the Linux boot process is loading the kernel. The kernel is generally found in the /boot directory and will be referenced by the boot loader. Next, the initial ramdisk (initrd) is loaded to device drivers, file system modules, logical volume modules, and other items that are required for boot but that aren't built directly into the kernel.
Once the boot loader loads the kernel, the kernel proceeds to initialize the system hardware before starting /sbin/init (PID 1). The init process starts all other processes on the system. Once init starts, there are two distinct ways in which it will proceed to bring up a Unix-like system—System V[1] style and BSD[2] style. Linux distributions generally follow System V examples for most things, including init’s tasks and processing runlevels.
When investigating a Solaris system that was being used to break into other computers on the victim network, we found more subtle remnants of an earlier intrusion. Taking advantage of the fact that system administrators infrequently inspect or alter the kernel on their system, an intruder placed a sniffer startup file in the kernel directory on a Solaris system. The startup file contained the following lines, ensuring that the sniffer, named update and update.hme for redundancy, would be executed each time the system was rebooted.
# more /kernel/pssys
1 “./update -s -o output”
1 “./update.hme -s -o output.hme”
Forensic examination of the system revealed that various executables placed on the system by the intruder had been compiled with a non-Solaris compiler. In addition, we found the sniffer files and associated output files in /usr/share/man/tmp, another location that system administrators rarely visit.
| # ls -altc | |||||
| total 156 | |||||
| -rw-r--r-- | 1 | root | root | 23787 | Jun 12 07:52 output.hme |
| drwxr-xr-x | 2 | root | root | 512 | Jun 6 17:20 . |
| drwxr-xr-x | 40 | bin | bin | 1024 | Jun 6 17:20 .. |
| -rw-r--r-- | 1 | root | root | 50 | Jun 6 17:20 output |
| -rwxr-xr-x | 1 | root | root | 25548 | Jun 6 17:20 update |
| -rwx------ | 1 | root | root | 25996 | Jun 6 17:20 update.hme |
The sniffer files contained usernames and passwords, and also captured the intruder logging into the compromised server remotely. These logs showed the intruder taking the sniffer logs and other sensitive files from the system.
System V
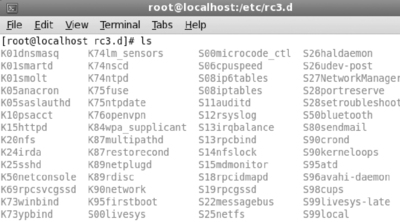
In addition to being the most common init style across Linux distributions, System V init is also used by Solaris and HP-UX. System V init reads the /etc/inittab file to determine the default runlevel. A runlevel is a numeric descriptor for the set of scripts a machine will execute for a given state. On most Linux distributions, runlevel 3 is synonymous with a full multi-user console (i.e., command line) environment, whereas runlevel 5 is a graphical environment.
Note that each entry in a runlevel directory is actually a symbolic link to a script in /etc/init.d/ that will be started or stopped depending on the name of the symlink. Each script contains myriad variables and actions that will be taken to start or stop the service gracefully.
As you can see in Figure 6.1, there are numerous places an intruder can set up a script to help them maintain persistent access to a compromised system. Careful review of all of the scripts involved in the boot process is mandatory in such a scenario.
BSD
The BSD init process is a bit less complex. BSD init reads the script at /etc/rc to determine what system services are to be run, configuration information is read from /etc/rc.conf, and additional services to run from /etc/rc.local. This is the extent of init configuration for OpenBSD, whereas current FreeBSD and NetBSD also read additional startup scripts from the /etc/rc.d/ directory.
Forensic examination of a compromised Linux server revealed that it had the t0rnkit rootkit installed. To ensure that a component of the rootkit was restarted whenever the system was rebooted, the following lines were added to the “/etc/rc.d/rc.sysinit” file.
# Xntps (NTPv3 daemon) startup..
/usr/sbin/xntps -q
# Xntps (NTPv3 deamon) check..
/usr/sbin/xntpsc 1>/dev/null 2>/dev/null
Closer inspection of the xntps executable revealed that it was part of the rootkit and not a legitimate part of the system.
Forensic Duplication Consideration
The dd command has existed on Unix systems long before digital forensics was a twinkle in the eye. Now this utility has become a de facto standard for creating forensic duplicates of storage media and volatile memory, and has been ported to other operating systems. This simple concept has evolved into specialized tools like dcfldd, which maintains audit and integrity log for forensic documentation purposes, and ddrescue, which has more flexibility in dealing with damaged media.
Acquiring a forensic image of a hard drive using these utilities provides a raw copy of the data that can be viewed using forensic tools like TSK, X-Ways, EnCase, and FTK. However, Unix systems that use Logical Volume Management (LVM) to enable resizing of partitions present a challenge for forensic practitioners. A forensic duplicate of a hard drive in such a system cannot be parsed by most forensic tools currently because the tools do not understand LVM. Therefore, it is necessary to activate the LVM and create a forensic duplicate of each partition individually.
File Systems
Although volatile data collection and analysis has recently received more mainstream attention than in the past, analysis of the contents of the file system remains as important as ever. To properly understand the “magic” taking place behind the curtains of many forensics tools, the examiner must first understand how a given file system functions. Additionally, understanding where these functions diverge from what the user expects enables exploitation of these gaps to the advantage of the examiner—this is the basis for recovery of “deleted” data.
The presence of an LVM configured disk will become immediately apparent when you look at the partition type (8e), which is displayed as Linux_LVM as shown here using fdisk.
# fdisk –l
Disk /dev/sda: 8589 MB, 8589934592 bytes
255 heads, 63 sectors/track, 1044 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Disk identifier: 0x0006159f
| Dvice Boot | start | End | Blocks | Id | Systen |
| /dev.sdal * | 1 | 25 | 200781 | 83 | Linux |
| /dev/sda2 | 26 | 1044 | 8185117+ | 8e | Linux LVM |
The next step is to scan all disks and display the name associated with the LVM as shown next for a volume group named “VolGroup00.”
# pvscan
PV /dev/sda2VG VolGroup00lvm2 [7.78 GB / 32.00 MB free]
Total: 1 [7.78 GB] / in use: 1 [7.78 GB] / in no VG: 0 [0 ]
In order to access the individual volumes it is necessary to activate the Volume Group as shown here:
# vgchange -a y VolGroup00
2 logical volume(s) in volume group VolGroup00 now active.
# lvs
LV VG Attr Lsize Origin Snap% Move Log Copy%
LogVol00 VolGroup00 -wi-a- 7.25G
LogVol01 VolGroup00 -wi-a- 512.00M
Image each logical partition as usual:
# dd if=/dev/VolGroup00/LogVol00 bs=4k of=/mnt/images/LogVol00.dd
# dd if=/dev/VolGroup00/LogVol01 bs=4k of=/mnt/images/LogVol01.dd
Most current Linux systems use the Ext3 file system. Ext3 is the successor of Ext2, which added journaling but retained Ext2’s underlying structure otherwise. In fact, an Ext3 volume will happily mount as Ext2 if the user issues the mount command appropriately. Many other file systems are available via the Linux kernel, including ReiserFS, XFS, and JFS. For the purposes of brevity, we will discuss Ext3 (and indirectly Ext2). For a detailed examination of various file systems we recommend File System Forensic Analysis (Carrier, 2006). We will be using the same abstraction model presented in Carrier 2006, as it presents a clear and accurate view of the file system without resorting to inaccurate analogy.
The logical progression of file system layers (as described by Carrier) from lowest to highest is as follows (Figure 6.2).
A disk refers to a physical storage device—a SCSI or SATA hard drive, for example. A volume is created using all or part of one or more disks. A single disk may contain several volumes, or a volume may span several disks, depending on configuration. The term “partition” is often used interchangeably for a volume—Carrier makes a distinction wherein a partition is limited to a single physical disk, and a volume is a collection of one or more partitions. Put simply, a volume describes a number of sectors on a disk or disks in a given system. A file system is laid down on a volume, and describes the layout of files and their associated metadata.
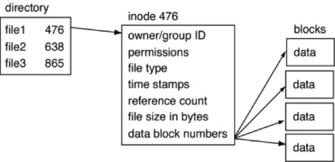
So, on a simple single-disk Linux system, the partition table describes the division of the disk into two partitions/volumes—one for swap and one for the actual file system. This file system is divided into blocks that contain the content of the files. These blocks in turn are described by inodes, and these inodes are described by directories containing filenames.
The lowest level data contained within a file system is content. Content is what is in the file—the data. Metadata is data about data—date and time information, ownership, and other data dependent upon the specific file system in question. The filename layer is the layer at which human users are most comfortable operating—this includes directories and filenames.
Unix Date-time Stamps
The Unix date-time format is a 32-bit value representing the number of seconds since 00:00:00 on 1st January 1970.
In addition to seeing Unix date-time stamps represented in hexadecimal format, forensic examiners will encounter Unix date-time stamps in a numeric format, which is a string of 10 digits. For instance, the Unix date-time stamp 0x45C08766 is equivalent to the digital value 1170245478, which is easily converted using Perl as shown here:
$ perl -e “print scalar(gmtime(1170245478))”
Wed Jan 31 12:11:18 2007
Some applications running on Windows systems use the Unix date-time format. For instance, Firefox maintains records of web browsing activity in a file named history.dat with dates in Unix format.
A utility developed for Windows systems called DCode can interpret Unix date-time stamps (www.digital-detective.co.uk/freetools/decode.asp).
On Unix systems, file system date-time stamps are set in UTC, making it necessary to adjust file system dates to the correct time zone. The time zone settings on most Unix systems are stored in a file that is referenced by the /etc/localtime symbolic link. For instance, the following Perl command converts a Unix date-time stamp to local time (e.g., US Eastern time zone).
Date-time Stamp Analysis
Unix systems maintain up to four date-time stamps. Each of the four timestamps stored in an Ext inode are updated by different actions. We'll address them in their most commonly referenced order: (M) A C (and D).
The M-time (modification) is updated when the content of a file or directory is modified. For a file, this is triggered by any alteration of the content. The content of a directory's blocks is filenames, so the deletion or creation of a file in a directory will cause its M-time to update.
The A-time (access) is the most frequently updated—this will change whenever the content of a file or directory is read. Actions that cause the content of a file to be read include copying, moving from one volume to another, or simply opening the file. As mentioned previously, directories are simply files that have filenames as their content, so listing the contents of a directory is sufficient to cause that directory's A-time to be updated. Additionally, reading the content of any file will cause the A-time of that file as well as the directory containing that file to be updated.
The C-time (change time) is updated when the inode is altered. This happens when any of the metadata for a file or directory is changed, including either of the previously mentioned timestamps, a file or directory being copied or moved, or the permissions of a file or directory being modified. The C-time is not to be mistaken with the creation date of a file.
Finally, the D-time is updated when a file was deleted. This timestamp will only be set in deleted inodes.
Macintosh systems running Unix operating systems have additional date-time stamps as detailed in Chapter 7, “Macintosh Forensic Analysis.”
On Unix systems, altering the modification or access time of any file is trivially done using the touch command. However, altering either of these timestamps in this manner updates the C-time. Additionally, preventing the updating of access times at all can be achieved using the noatime option to the mount command. When examining a machine possibly controlled by a savvy adversary, keep a healthy skepticism if you encounter strange (or strangely convenient) timestamps.
The C-time is of particular interest, as this timestamp cannot be easily altered to a specific value. In an investigation where the timing of events is key this may be your truest source of temporal information.
All file system activity can be conveniently displayed as a timeline using the mactime utility from TSK. This program is used to create a log-style listing sorted by each timestamp entry in a supplied “body” file. A “body” file is a listing of files in a particular format, often referred to as “mactime” format. An appropriate body file can be generated using the fls program, also a part of TSK, as demonstrated here:
#fls -r -m / {image_file} > bodyfile
Alternatively, the output from fls can be piped directly to mactime to avoid the creation of an intermediary file as demonstrated here:
#fls -r -m / {image_file} | mactime –b -
The mactime utility can be instructed to present timestamps only for a certain time period as shown here:
#mactime -b bodyfile 04/01/2009-04/12/2009
We can combine these to generate a timeline that only shows the activity on the “/home” volume occurring on May 30, 2009. Note that in this example we are running fls against the volume (/dev/sda9) directly as opposed to creating a raw image file first.
fcculive:~# fls -r -m /home /dev/sda9 | mactime -b - 05/30/2009 > timeline.txt
The resultant file has 200 lines—all this activity was generated during a very simple graphical logon session. Timeline investigations of intrusions occurring over a period of months or years on heavily used systems can grow into the millions of entries!
Sat May 30 2009 18:54:22 4096 m.c d/drwx------ 100010003694600/home/user/.gnome2
Sat May 30 2009 18:54:23 4096 m.c d/drwxr-xr-x 100010003694637/home/user/.nautilus
919 mac -/-rw------- 100010003695648/home/user/.gnome2/update-notifier-Cl885d
(deleted-realloc)
919 mac -/-rw------- 100010003695648/home/user/.nautilus/saved-session-3BVPUU
Sat May 30 2009 18:54:27 818 m.c -/-rw------- 1000 10003695590/home/user/.bash_history
Sat May 30 2009 18:56:15 4096 .a. d/drwx------ 100010003694597/home/user/.gconf
4096 .a. d/drwx------ 100010003694599/home/user/.gconf/apps
4096 .a. -/drwx------ 100010003694599/home/user/.gnome2/panel2.d/default/launchers/gnome-terminal.desktop (deleted-realloc)
Sat May 30 2009 18:56:16 4096 .a. d/drwx------ 100010003694601/home/user/.gnome2/keyrings
15267 .a. -/-rw-r--r-- 100010003694603/home/user/.xsession-errors
105 .a. -/-rw------- 100010003694604/home/user/.gnome2/keyrings/.keyringT8QNQU (deleted-realloc)
105 .a. -/-rw------- 100010003694604/home/user/.gnome2/keyrings/login.keyring
217 m.c -/-rw------- 100010003695646/home/user/.Xauthority
Sat May 30 2009 18:56:17 675 .a. -/-rw-r--r-- 100010003694594/home/user/.profile
3116 .a. -/-rw-r--r-- 100010003694595/home/user/.bashrc
28 m.c -/-rw------- 100010003694712/home/user/.dmrc
Sat May 30 2009 18:56:18 463 m.c -/-rw-r--r-- 100010003694608/home/user/.dbus/session-bus/4aa19355324ed7c15b5f3dfc49b05af9-0
4096 .a. d/drwx------ 100010003694625/home/user/.gconf/desktop
4096 .a. d/drwx------ 100010003694627/home/user/.gconf/desktop/gnome
Sat May 30 2009 18:56:19 4096 m.c d/drwxr-xr-x 100010003694593/home/user
159 m.c -/-rw------- 100010003694614/home/user/.ICEauthority
4096 .a. d/drwx------ 100010003694682/home/user/.gconf/desktop/gnome/screen
4096 .a. d/drwx------ 100010003694735/home/user/.gconf/desktop/gnome/screen/default
259 .a. -/-rw------- 100010003695645/home/user/.gconf/desktop/gnome/screen/default/0/%gconf.xml
259 .a. -/-rw------- 100010003695645/home/user/.gconf/desktop/gnome/screen/default/0/%gconf.xml.new (deleted-realloc)
Sat May 30 2009 18:56:20 4096 .a. d/drwxr-xr-x 100010003694593/home/user
4096 .a. d/drwxr-xr-x 100010003694615/home/user/.gnome2/share/fonts
4096 .a. d/drwxr-xr-x 100010003694616/home/user/.gnome2/share/cursor-fonts
2 mac -/-rw-r--r-- 100010003694617/home/user/.gnome2/share/cursor- fonts/fonts.dir
2 mac -/-rw-r--r-- 100010003694618/home/user/.gnome2/share/fonts/fonts.dir
0 .a. -/-rw------- 100010003694628/home/user/.gconf/desktop/gnome/%gconf.xml
4096 .a. d/drwx------ 100010003761585/home/user/.gconf/desktop/gnome/peripherals
4096 .a. d/drwx------ 100010003761647/home/user/.gconf/desktop/gnome/peripherals/keyboard
0 .a. -/-rw------- 100010003761648/home/user/.gconf/desktop/gnome/peripherals/keyboard/%gconf.xml
4096 .a. d/drwx------ 100010003761650/home/user/.gconf/desktop/gnome/peripherals/keyboard/host-quincy
Sat May 30 2009 18:56:21 4096 .a. d/drwx------ 100010003694629/home/user/.gconf/desktop/gnome/accessibility
2087 .a. -/-rw------- 100010003694632/home/user/.gconf/desktop/gnome/accessibility/keyboard/%gconf.xml
2087 .a. -/-rw------- 100010003694632/home/user/.gconf/desktop/gnome/accessibility/keyboard/%gconf.xml.new (deleted-realloc)
Sat May 30 2009 18:56:22 4096 m.c d/drwx------ 100010003694611/home/user/.gnupg
28 .a. -/-rw------- 100010003694612/home/user/.gnupg/gpg.conf
4096 .a. d/drwx------ 100010003694619/home/user/.ssh
40 .a. -/-rw------- 100010003694620/home/user/.gnupg/trustdb.gpg
0 .a. -/-rw------- 100010003694621/home/user/.gnupg/pubring.gpg
0 .a. -/-rw------- 100010003694623/home/user/.gnupg/secring.gpg
594 .a. -/-rw------- 100010003762203/home/user/.gconf/desktop/gnome/remote_access/%gconf.xml
594 .a. -/-rw------- 100010003762203/home/user/.gconf/desktop/gnome/remote_access/%gconf.xml.new (deleted-realloc)
594 .a. l/-rw------- 100010003762203/home/user/afflib-3.3.4/conf26974 (deleted-realloc)
Sat May 30 2009 18:56:23 4096 m.c d/drwx------ 100010003694597/home/user/.gconf
181 mac -/-rw------- 100010003694606/home/user/.gconf/.testing.writeability (deleted-realloc)
181 mac -/-rw------- 100010003694606/home/user/.gconf/desktop/gnome/applications/window_manager/%gconf.xml
181 mac -/-rw------- 100010003694606/home/user/.gconf/desktop/gnome/applications/window_manager/%gconf.xml.new (deleted-realloc)
181 mac -/-rw------- 100010003694606/home/user/.gnupg/.#lk0x8287c60.quincy.3495 (deleted-realloc)
4096 .a. d/drwx------ 100010003694633/home/user/.gconf/desktop/gnome/applications
4096 m.c d/drwx------ 100010003694635 /home/user/.gconf/desktop/gnome/applications/window_manager
4096 .a. d/drwx------ 100010003694657/home/user/.gconf/apps/panel
2010 .a. -/-rw------- 100010003694688/home/user/.gconf/apps/panel/objects/object_1/%gconf.xml
2010 .a. -/-rw------- 100010003694688/home/user/.gconf/apps/panel/objects/object_1/%gconf.xml.new (deleted-realloc)
4096 .a. d/drwx------ 100010003694689/home/user/.gconf/apps/panel/objects/object_0 (deleted-realloc)
4096 .a. d/drwx------ 100010003694689/home/user/.gconf/apps/panel/toplevels
4096 .a. d/drwx------ 100010003694697/home/user/.gconf/apps/panel/objects/object_0/bottom_panel_screen0
1961 .a. -/-rw------- 100010003694698/home/user/.gconf/apps/panel/objects/object_0/bottom_panel_screen0/%gconf.xml
778 .a. -/-rw------- 100010003694700/home/user/.gconf/apps/panel/objects/object_0/bottom_panel_screen0/background/%gconf.xml
778 .a. -/-rw------- 100010003694700/home/user/.gconf/apps/panel/objects/object_0/bottom_panel_screen0/background/%gconf.xml.new (deleted-realloc)
4096 m.c d/drwx------ 100010003761652/home/user/.gconf/desktop/gnome/peripherals/keyboard/host-quincy/0
134 mac -/-rw------- 100010003761742/home/user/.gconf/desktop/gnome/peripherals/keyboard/host-quincy/0/%gconf.xml
134 mac -/-rw------- 100010003761742/home/user/.gconf/desktop/gnome/peripherals/keyboard/host-quincy/0/%gconf.xml.new (deleted-realloc)
Sat May 30 2009 18:56:24 4096 .a. d/drwx------ 100010003833980/home/user/.gconf/desktop/gnome/connected_servers
0 .a. -/-rw------- 100010003833981/home/user/.gconf/desktop/gnome/connected_servers/%gconf.xml
4096 .a. d/drwx------ 100010003833982/home/user/.gconf/desktop/gnome/connected_servers/1
455 .a. -/-rw------- 100010003833983/home/user/.gconf/desktop/gnome/connected_servers/1/%gconf.xml
455 .a. -/-rw------- 100010003833983/home/user/.gconf/desktop/gnome/connected_servers/1/%gconf.xml.new (deleted-realloc)
Sat May 30 2009 18:56:25 82 mac -/-rw-r--r-- 100010003694636/home/user/.metacity/sessions/117f000101000124370978300000034170001.ms
4096 m.c d/drwx------ 100010003694641/home/user/.metacity/sessions
1917 .a. -/-rw------- 100010003694656/home/user/.gconf/apps/panel/applets/clock_screen0/%gconf.xml
1917 .a. -/-rw------- 10001000 3694656/home/user/.gconf/apps/panel/applets/clock_screen0/%gconf.xml.new (deleted-realloc)
4096 .a. d/drwx------ 100010003694659/home/user/.gconf/apps/panel/applets
1929 .a. -/-rw------- 100010003694662/home/user/.gconf/apps/panel/applets/workspace_switcher_screen0/%gconf.xml
1923 .a. -/-rw------- 100010003694666/home/user/.gconf/apps/panel/applets/window_list_screen0/%gconf.xml
1924 .a. -/-rw------- 100010003694670/home/user/.gconf/apps/panel/applets/show_desktop_button_screen0/%gconf.xml
1924 .a. -/-rw------- 100010003694670/home/user/.gconf/apps/panel/applets/show_desktop_button_screen0/%gconf.xml.new (deleted-realloc)
1917 .a. -/-rw------- 100010003694672/home/user/.gconf/apps/panel/applets/mixer_screen0/%gconf.xml
1917 .a. -/-rw------- 100010003694672/home/user/.gconf/apps/panel/applets/mixer_screen0/%gconf.xml.new (deleted-realloc)
1922 .a. -/-rw------- 100010003694674/home/user/.gconf/apps/panel/applets/window_menu_screen0/%gconf.xml
1922 .a. -/-rw------- 100010003694674/home/user/.gconf/apps/panel/applets/window_menu_screen0/%gconf.xml.new (deleted-realloc)
4096 .a. d/drwx------ 100010003694683/home/user/.gconf/apps/panel/objects
1878 .a. -/-rw------- 100010003694686/home/user/.gconf/apps/panel/objects/object_2/%gconf.xml
1878 .a. -/-rw------- 100010003694686/home/user/.gconf/apps/panel/objects/object_2/%gconf.xml.new (deleted-realloc)
1910 .a. -/-rw------- 100010003694692/home/user/.gconf/apps/panel/objects/email_launcher_screen0/%gconf.xml
1910 .a. -/-rw------- 100010003694692/home/user/.gconf/apps/panel/objects/email_launcher_screen0/%gconf.xml.new (deleted-realloc)
1909 .a. -/-rw------- 100010003694694/home/user/.gconf/apps/panel/objects/browser_launcher_screen0/%gconf.xml
1909 .a. -/-rw------- 100010003694694/home/user/.gconf/apps/panel/objects/browser_launcher_screen0/%gconf.xml.new (deleted-realloc)
1812 .a. -/-rw------- 100010003694696/home/user/.gconf/apps/panel/objects/menu_bar_screen0/%gconf.xml
1812 .a. -/-rw------- 100010003694696/home/user/.gconf/apps/panel/objects/menu_bar_screen0/%gconf.xml.new (deleted-realloc)
4096 .a. d/drwx------ 100010003694701/home/user/.gconf/apps/panel/objects/object_0/top_panel_screen0
2193 .a. -/-rw------- 100010003694702/home/user/.gconf/apps/panel/objects/object_0/top_panel_screen0/%gconf.xml
778 .a. -/-rw------- 100010003694704/home/user/.gconf/apps/panel/objects/object_0/top_panel_screen0/background/%gconf.xml
778 .a. -/-rw------- 100010003694704/home/user/.gconf/apps/panel/objects/object_0/top_panel_screen0/background/%gconf.xml.new (deleted-realloc)
1925 .a. -/-rw------- 100010003694763/home/user/.gconf/apps/panel/applets/notification_area_screen0/%gconf.xml
1925 .a. -/-rw------- 100010003694763/home/user/.gconf/apps/panel/applets/notification_area_screen0/%gconf.xml.new (deleted-realloc)
Sat May 30 2009 18:56:26 4096 .a. d/drwx------ 100010003694661/home/user/.gconf/apps/panel/applets/workspace_switcher_screen0
4096 .a. d/drwx------ 100010003694663/home/user/.gconf/apps/panel/applets/workspace_switcher_screen0/prefs
4096 .a. d/drwx------ 100010003694665/home/user/.gconf/apps/panel/applets/window_list_screen0
4096 .a. d/drwx------ 100010003694667/home/user/.gconf/apps/panel/applets/window_list_screen0/prefs
4096 .a. d/drwx------ 100010003694669/home/user/.gconf/apps/panel/applets/show_desktop_button_screen0
Sat May 30 2009 18:56:28 5515 .a. -/-rw-r--r-- 100010003694653/home/user/.gnome2/panel2.d/default/launchers/gnome-terminal-1.desktop
Sat May 30 2009 18:56:35 4096 .a. d/drwx------ 100010003694673/home/user/.gconf/apps/panel/applets/clock_screen0
4096 .a. d/drwx------ 100010003694675/home/user/.gconf/apps/panel/applets/clock_screen0/prefs
4096 .a. d/drwx------ 100010003694677/home/user/.gconf/apps/panel/applets/clock_screen0/prefs/timezones
Sat May 30 2009 18:56:36 4096 .a. d/drwx------ 100010003694679/home/user/.gconf/apps/panel/applets/mixer_screen0
4096 .a. d/drwx------ 100010003694681/home/user/.gconf/apps/panel/applets/window_menu_screen0
Sat May 30 2009 18:56:37 318749 .a. -/-rw------- 1000 10003694624 /home/user/.gnupg/secring.gpg.lock/registry.i486.bin
318749 .a. -/-rw------- 100010003694624/home/user/.gnupg/secring.gpg.lock/registry.i486.bin.tmp017CQU (deleted-realloc)
4096 .a. d/drwx------ 100010003694671/home/user/.gconf/apps/panel/applets/notification_area_screen0
Sat May 30 2009 18:57:26 4096 m.c d/drwx------ 100010003694663/home/user/.gconf/apps/panel/applets/workspace_switcher_screen0/prefs
4096 m.c d/drwx------ 100010003694667/home/user/.gconf/apps/panel/applets/window_list_screen0/prefs
445 mac -/-rw------- 100010003694668/home/user/.gconf/apps/panel/applets/workspace_switcher_screen0/prefs/%gconf.xml
445 mac -/-rw------- 100010003694668/home/user/.gconf/apps/panel/applets/workspace_switcher_screen0/prefs/%gconf.xml.new (deleted-realloc)
4096 m.c d/drwx------ 100010003694675/home/user/.gconf/apps/panel/applets/clock_screen0/prefs
156 mac -/-rw------- 100010003694676/home/user/.gconf/apps/panel/applets/clock_screen0/prefs/timezones/%gconf.xml
156 mac -/-rw------- 100010003694676/home/user/.gconf/apps/panel/applets/clock_screen0/prefs/timezones/%gconf.xml.new (deleted-realloc)
4096 m.c d/drwx------ 10001000 3694677/home/user/.gconf/apps/panel/applets/clock_screen0/prefs/timezones
670 mac -/-rw------- 100010003694678/home/user/.gconf/apps/panel/applets/window_list_screen0/prefs/%gconf.xml
670 mac -/-rw------- 100010003694678/home/user/.gconf/apps/panel/applets/window_list_screen0/prefs/%gconf.xml.new (deleted-realloc)
1823 mac -/-rw------- 100010003695651/home/user/.gconf/apps/panel/applets/clock_screen0/prefs/%gconf.xml
1823 mac -/-rw------- 100010003695651/home/user/.gconf/apps/panel/applets/clock_screen0/prefs/%gconf.xml.new (deleted-realloc)
Sat May 30 2009 18:57:45 4096 m.c d/drwx------ 100010003694598/home/user/.gconfd
Sat May 30 2009 19:00:24 15267 m.c -/-rw-r--r-- 100010003694603/home/user/.xsession-errors
Sat May 30 2009 19:00:59 58 mac -/-rw-r--r-- 100010003694648/home/user/.gnome/gnome-vfs/.trash_entry_cache
4096 .a. d/drwxr-xr-- 100010003694650/home/user/.gnome2/nautilus-scripts
28 .a. -/-rw------- 100010003694712/home/user/.dmrc
268 .a. -/-rw------- 100010003694778/home/user/.nautilus/metafiles/file:///home/user/Desktop.xml
818 .a. -/-rw------- 100010003695590/home/user/.bash_history
35 .a. -/-rw------- 100010003695643/home/user/.lesshst
4096 .a. d/drwx------ 100010003761663/home/user/.thumbnails/normal
Sat May 30 2009 19:01:00 8328283136 .a. -/-rwxr-xr-x 100010003695636/home/user/Ubuntu-desktop.raw.img
563784 .a. -/-rw-r--r-- 003695641/home/user/.fonts.cache-1
Sat May 30 2009 19:01:09 4096 .a. d/drwxr-xr-x 100010003694638/home/user/Desktop
4096 .a. d/drwxr-x--- 100010003694754/home/user/Desktop/Downloads
555 mac -/-rw------- 100010003695652/home/user/.nautilus/metafiles/x-nautilus-desktop:///.xml
4096 .a. d/drwxrwxrwx 5015013760134/home/user/bloom-1.0.1
4096 .a. d/drwxr-xr-x 003768760/home/user/vmware-tools-distrib
Sat May 30 2009 19:01:10 4096 .a. d/drwxrwxrwx 5015013694743/home/user/sleuthkit-3.0.1
15042 .a. -/-rwxr-xr-x 100010003694766/home/user/mount_ewf-20080513.py
5269 .a. -/-rw-r--r-- 100010003695609/home/user/patches.txt
2613248 .a. -/-rw-r--r-- 100010003695647/home/user/fls
26721262 .a. -/-rw-r--r-- 100010003695649/home/user/err
4096 .a. d/drwxrwxrwx 5015013760159/home/user/aimage-3.2.0
4096 .a. d/drwxrwxrwx 5015013760189/home/user/ataraw-0.2.0
4096 .a. d/drwxrwxrwx 5015013760217/home/user/bulk_extractor-0.0.10
4096 .a. d/drwxrwxrwx 5015013760246/home/user/fiwalk-0.4.3
4096 .a. d/drwxrwxrwx 21252212523760292/home/user/afflib-3.3.4
4096 .a. d/drwxr-xr-x 003760298/home/user/ptk
4096 .a. d/drwxrwxrwx 100010003760699/home/user/pyflag-0.87-pre1
4096 .a. -/drwxrwxrwx 100110013761589/home/user/fiwalk-0.4.3/confdefs.h (deleted-realloc)
4096 .a. d/drwxrwxrwx 100110013761589/home/user/fiwalk-0.5.1
4096 .a. -/drwxr-xr-x 100010003762204/home/user/afflib-3.3.4/conftest.undefs (deleted-realloc)
4096 .a. d/drwxr-xr-x 100010003762204/home/user/forensics
Sat May 30 2009 19:01:20 112 mac -/-rw------- 100010003695584/home/user/.nautilus/metafiles/file:/// home.xml
Sat May 30 2009 19:01:28 0 ma. -/-rw-r--r-- 100010003695653/home/user/new file∼
Sat May 30 2009 19:01:40 4096 ..c d/drwx------ 100010003694609/home/user/.gnome2_private
159 .a. -/-rw------- 100010003694614/home/user/.ICEauthority
217 .a. -/-rw------- 100010003695646/home/user/.Xauthority
4096 .a. d/drwx------ 100010003760283/home/user/.gconf/apps/gedit-2
4096 .a. d/drwx------ 100010003761656/home/user/.gconf/apps/gedit- 2/preferences
0 .a. -/-rw------- 100010003761657/home/user/.gconf/apps/gedit- 2/preferences/%gconf.xml
4096 .a. d/drwx------ 100010003761658/home/user/.gconf/apps/gedit- 2/preferences/ui
0 .a. -/-rw------- 100010003761659/home/user/.gconf/apps/gedit- 2/preferences/ui/%gconf.xml
4096 .a. d/drwx------ 100010003761660/home/user/.gconf/apps/gedit- 2/preferences/ui/statusbar
Sat May 30 2009 19:01:41 7450 .a. -/-rw-r--r-- 100010003694774/home/user/.gnome2/accelsgedit
Sat May 30 2009 19:01:45 553 .a. -/-rw-r--r-- 100010003695023/home/user/.gnome2/gedit-metadata.xml
67895 mac -/-rwx------ 100010003695650/home/user/.gconfd/saved_state
67895 mac -/-rwx------ 100010003695650/home/user/.gconfd/saved_state.tmp (deleted-realloc)
Sat May 30 2009 19:01:48 4096 m.c d/drwx------ 100010003694655/home/user/.gconf/apps/gnome-screensaver
143 mac -/-rw------- 100010003694772/home/user/.gconf/apps/gnome-screensaver/%gconf.xml
143 mac -/-rw------- 100010003694772/home/user/.gconf/apps/gnome-screensaver/%gconf.xml.new (deleted-realloc)
141 mac -/-rw------- 100010003761653/home/user/.gconf/apps/gedit- 2/preferences/ui/statusbar/%gconf.xml
141 mac -/-rw------- 100010003761653/home/user/.gconf/apps/gedit- 2/preferences/ui/statusbar/%gconf.xml.new (deleted-realloc)
4096 m.c d/drwx------ 100010003761660/home/user/.gconf/apps/gedit- 2/preferences/ui/statusbar
4096 mac d/drwx------ 100010003981318/home/user/.gconf/apps/nautilus
4096 mac l/drwx------ 100010003981318 /home/user/.mozilla/firefox/8u20d7t5.default/lock (deleted-realloc)
137 mac -/-rw------- 100010003981364 /home/user/.gconf/apps/nautilus/%gconf.xml
137 mac -/-rw------- 100010003981364 /home/user/.gconf/apps/nautilus/%gconf.xml.new (deleted-realloc)
137 mac -/-rw------- 100010003981364 /home/user/.mozilla/firefox/8u20d7t5.default/places.sqlite-journal (deleted-realloc)
Sat May 30 2009 19:02:17 58 m.c -/-rw-r--r-- 100010003694664 /home/user/.gedit-save-PDO8UU (deleted-realloc)
58 m.c -/-rw-r--r-- 100010003694664/home/user/new file
0 ..c -/-rw-r--r-- 100010003695653/home/user/new file∼
Sat May 30 2009 19:02:18 4096 m.c d/drwx------ 100010003694649/home/user/.nautilus/metafiles
215 mac -/-rw------- 100010003695031/home/user/.gconfd/saved_state.orig (deleted-realloc)
215 mac -/-rw------- 100010003695031 /home/user/.nautilus/metafiles/file:///home/user.xml
215 mac -/-rw------- 100010003695031 /home/user/.nautilus/metafiles/file:///home/user.xmlDHPsbV (deleted-realloc)
Sat May 30 2009 19:02:21 7450 m.c -/-rw-r--r-- 100010003694774/home/user/.gnome2/accelsgedit
553 m.c -/-rw-r--r-- 100010003695023/home/user/.gnome2/gedit-metadata.xml
18516 m.c -/-rw-r--r-- 100010003695654/home/user/.recently-used.xbel
18516 m.c -/-rw-r--r-- 100010003695654/home/user/.recently-used.xbel.33P1UU (deleted-realloc)
75 mac -/-rw-r--r-- 100010003695655/home/user/.gnome2/gedit-2
75 mac -/-rw-r--r-- 100010003695655/home/user/.gnome2/gedit-2.HET1UU (deleted-realloc)
Sat May 30 2009 19:02:2518516 .a. -/-rw-r--r-- 100010003695654/home/user/.recently-used.xbel
18516 .a. -/-rw-r--r-- 100010003695654/home/user/.recently-used.xbel.33P1UU (deleted-realloc)
Sat May 30 2009 19:02:29 58 .a. -/-rw-r--r-- 100010003694664/home/user/.gedit-save-PDO8UU (deleted-realloc)
58 .a. -/-rw-r--r-- 100010003694664/home/user/new file
(Carrier, B. (2005). File system forensic analysis. Addison-Wesley Professional.)
Root Directory
The primary data structures that make up ext2/ext3 are simply data streams with a defined format. The following example of an ext2 formatted floppy disk is provided to demonstrate the simplicity of these structures and their relationships. A forensic duplicate of this floppy disk is available at www.disclosedigital.com/DiscloseDigital/Digital_Evidence_files/ext2-floppy-02132004.zip.
The root directory's inode is always inode 2 and is shown here in WinHex:
Offset0123456789ABCDEF
0000700002 00 00 00 0C 00 01 022E 00 00 00 02 00 00 00.................
000070100C 00 02 02 2E 2E 00 000B 00 00 00 14 00 0A 02.................
000070206C 6F 73 74 2B 66 6F 756E 64 00 00 0C 00 00 00lost+found.....
0000703014 00 0A 02 64 69 72 6563 74 6F 72 79 31 00 00....directory1..
000070400E 00 00 00 14 00 09 0169 6E 64 65 78 2E 64 61........index.da
0000705074 00 00 00 15 00 00 0020 00 05 01 66 69 6C 65t............file
0000706033 70 00 00 00 00 00 0010 00 05 01 66 69 6C 653p..............file
0000707032 32 2E 73 11 00 00 0024 00 05 01 66 69 6C 6522.s....$…file
0000708034 34 2E 73 00 00 00 0014 00 0A 01 68 61 6E 6444.s........hand
000070906C 65 2E 70 64 66 00 0013 00 00 00 68 03 0C 01le.pdf.......h...
000070A044 43 50 5F 31 37 32 322E 4A 50 47 00 00 00 00DCP_1722.JPG….
000070B054 03 0A 01 2E 66 69 6C65 33 2E 73 77 70 00 00T.... file3.swp..
000070C000 00 00 00 40 03 0B 012E 66 69 6C 65 33 2E 73...@...file3. s
000070D077 70 78 00 00 00 00 0000 00 00 00 00 00 00 00wpx.................
Using the following format, we can translate these directory entries.
| bytes | Directory Entry |
|---|---|
| 4 | Inode number |
| 2 | This directory entry's length |
| 1 | File name length in bytes |
| 1 | File type (1=regular file 2=directory) |
| x | File name |
The root directory translated into the following, where unknown metadata associated with deleted files are indicated with a question mark.
| Inode | Entry length | Name length | TypE | Name |
|---|---|---|---|---|
| 11 | 20 bytes | 10 bytes | dir | lost+found |
| 12 | 20 bytes | 10 bytes | dir | directory1 |
| 14 | 20 bytes | 9 bytes | file | index.dat |
| 21 | 32 bytes | 5 bytes | file | file3 |
| ? | ? | 5 bytes | file | file2 |
| 17 | 36 bytes | 5 bytes | file | file4 |
| ? | ? | 10 bytes | file | handle.pdf |
| 19 | 872 bytes | 12 bytes | file | DCP_1722.JPG |
| ? | ? | 10 bytes | file | .file3.swp |
| ? | ? | 11 bytes | file | .file3.swpx |
This information, and the contents of subdirectories, can be extracted from a forensic duplicate with TSK using “fls -f linux-ext2 -r -p -u ext2-floppy-021304.dd” (the –r option recurses through folders and –p provides full path names). Although knowing just the filename may be useful in some investigations, having just filenames without their associated metadata is generally of limited value.
Locating File Metadata and Content
To determine important details about the file, including where the content of a file is stored, first we must get information about the overall structure of the disk from the superblock. This structure is located after the boot block, 1024 bytes from the beginning of the disk (offset 1024 = 400 hex).
The superblock is a dense structure with many fields and looks like this in raw form:
| Offset | 01234567 | 89ABCDEF | |
| 00000400 | B8 00 00 00 A0 05 00 00 | 48 00 00 00 F5 01 00 00 | ... ... H...õ... |
| 00000410 | A5 00 00 00 01 00 00 00 | 00 00 00 00 00 00 00 00 | ¥.................. |
| 00000420 | 00 20 00 00 00 20 00 00 | B8 00 00 00 B6 5E 2C 40 | . ... .. ...^,@ |
| 00000430 | B6 5F 2C 40 05 00 1A 00 | 53 EF 01 00 01 00 00 00 | _,@....Sï... ... |
| 00000440 | 47 CE 26 40 00 4E ED 00 | 00 00 00 00 01 00 00 00 | GÎ&@.Ní......... |
| 00000450 | 00 00 00 00 0B 00 00 00 | 80 00 00 00 00 00 00 00 | .........€......... |
| 00000460 | 02 00 00 00 01 00 00 00 | 65 7E FD E6 C4 DF 41 2F | .......e~ýæÄßA/ |
| 00000470 | AE 5D A8 88 70 E0 0F DF | 00 00 00 00 00 00 00 00 | ®]..^pà.ß......... |
The values in this data can be interpreted using the defined format of the superblock.
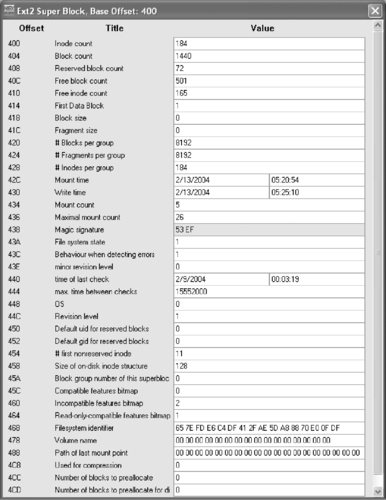
The format of the ext2 superblock is as follows:
| Bytes | Meaning | Value |
|---|---|---|
| 4 | Total number of inodes | 000000B8 = 184 |
| 4 | Filesystem size in blocks | 000005A0 = 1440 |
| 4 | Number of reserved blocks | 00000048 = 72 |
| 4 | Free blocks counter | 000001F5 = 501 |
| 4 | Free inodes counter | 000000A5 = 165 |
| 4 | Number of first useful block (always 1) | |
| 4 | Block size (as a power of 2, using 1024 bytes as the unit) | |
| 4 | Fragment size | |
| 4 | Number of blocks per group | 2000 = 8192 |
| 4 | Number of fragments per group | 2000 = 8192 |
| 4 | Number of inodes per group | 000000B8 = 184 |
| 4 | Time of last mount operation | B65E2C40=Feb 13 2004 05:20:54 GMT |
| 4 | Time of last write operation | B65F2C40=Feb 13 2004 05:25:10 GMT |
| 2 | Mount operations counter | 05=5 |
| 2 | # mount operations before check | 1A |
| 2 | Magic signature | 53EF |
| 2 | Status flag | 01 |
| 2 | Behavior when detecting errors | 01 |
| 2 | Minor revision level | 00 |
| 4 | Time of last check | 47CE2640=Feb 9 2004 00:03:19 GMT |
| 4 | Time between checks | ED4E00=15552000 |
| 4 | OS where filesystem was created | 00 |
| 4 | Revision level | 01 |
| 2 | Default user ID for reserved blocks | 00 |
| 2 | Default group ID for reserved blocks | 00 |
| 4 | Number of first nonreserved inode | 0B=11 |
| 2 | Size of on-disk inode structure | 80=128 bytes |
| 2 | Block group number of this superblock | |
| 4 | Compatible features bitmap | |
| 4 | Incompatible features bitmap | |
| 4 | Read-only-compatible features bitmap | |
| 16 | 128-bit filesystem identifier | |
| 16 | Volume name | |
| 64 | Path of last mount point | |
| 4 | Used for compression | |
| 1 | Number of blocks to preallocate | |
| 1 | Number of blocks to preallocate for directories | |
| 818 | Nulls to pad out 1024 bytes |
To facilitate the interpretation process, X-Ways has an ext2 superblock template that can be applied to the preceding data as shown in Figure 6.3.
Immediately following the superblock is the first Group Descriptor structure that contains the location of the inode table (there is only one group on a floppy disk).
| Offset | 01234567 | 89ABCDEF | |
| 00000800 | 03 00 00 00 04 00 00 00 | 05 00 00 00 F5 01 A5 00 | ........õ.¥. |
| 00000810 | 03 00 00 00 00 00 00 00 | 00 00 00 00 00 00 00 00 | .............. |
The format of the group descriptor is as follows, and can also be viewed using the ext2 Group Descriptor template in X-Ways.
| Bytes | Meaning | Value |
|---|---|---|
| 4 | Block number of block bitmap | 000003 |
| 4 | Block number of inode bitmap | 000004 |
| 4 | Block number of first inode table block | 000005 |
| 2 | Number of free blocks in the group | 01F5=501 |
| 2 | Number of free inodes in the group | 00A5=165 |
| 2 | Number of directories in the group | 0003 |
| 2 | Alignment to word | 0000 |
| 4 | Nulls to pad out 24 bytes | 00000000 |
Some of this information can be obtained with TSK using fsstat -f ext2-floppy-021304.dd.
This tells us that the inode table is located in block 5, and we know from the superblock that each block is 1024 bytes (offset 5120 = 1400 hex). In raw form, the beginning of the inode table looks like this:
Offset0123456789ABCDEF
0000140000 00 00 00 00 00 0000 49 CE 26 40 49 CE 26 40.....IÎ&@IÎ&@
0000141049 CE 26 40 00 00 0000 00 00 00 00 00 00 00 00IÎ&@...........
0000142000 00 00 00 00 00 0000 00 00 00 00 00 00 00 00.................
0000143000 00 00 00 00 00 0000 00 00 00 00 00 00 00 00.................
0000144000 00 00 00 00 00 0000 00 00 00 00 00 00 00 00.................
0000145000 00 00 00 00 00 0000 00 00 00 00 00 00 00 00.................
0000146000 00 00 00 00 00 0000 00 00 00 00 00 00 00 00.................
0000147000 00 00 00 00 00 0000 00 00 00 00 00 00 00 00.................
00001480ED 41 00 00 00 04 0000 77 5F 2C 40 AA 5F 2C 40íA...w_,@a_,@
00001490AA 5F 2C 40 00 00 0000 00 00 04 00 02 00 00 00a_,@...........
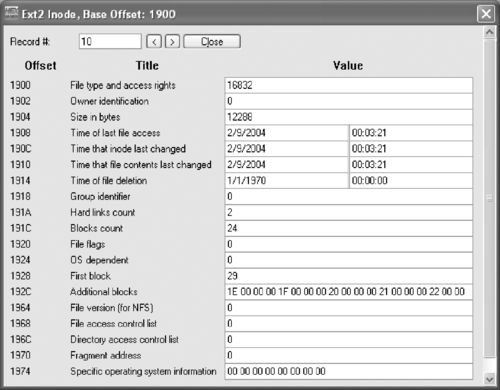
The format of inodes is as follows:
| bytes | value |
| 2 | File type and access rights |
| 2 | Owner identification |
| 4 | File size in bytes |
| 4 | file last accessed time |
| 4 | inode last changed time |
| 4 | file last modified |
| 4 | file deletion time |
| 2 | Group identifier |
| 2 | Hard links counter |
| 4 | Number of data blocks of the file |
| 4 | File flags |
| 4 | Operating system specific |
| 4 | Pointer to first data block |
| 56 | 14 more pointers to data blocks |
| 4 | File version (for NFS) |
| 4 | File access control list |
| 4 | Directory access control list |
| 4 | Fragment address |
| 8 | Operating system specific |
Applying the X-Ways ext2 inode template enables us to view this information in a more readable form as shown for inode 11 in Figure 6.4.
The metadata associated with individual files on a forensic duplicate can be displayed with TSK using the istat command (e.g., istat -f linux-ext2 ext2-floppy-021304.dd 11).
Using this information, such as filenames and block numbers, you can locate and extract the active files on this disk. For example, the entry in the root directory tells us that the text file named file3 is associated with inode 21, which in turn tells us that it starts at block 1034 and is 61 bytes in length. Going to offset 102800 (1034 blocks x 1024 bytes/block = 1058816 = 102800 hex) brings us to the start of the file as shown here:
Offset0123456789ABCDEF
0010280054 68 69 73 20 66 69 6C65 20 77 61 73 20 63 72This file was cr
0010281065 61 74 65 64 20 61 7420 61 72 6F 75 6E 64 20eated at around
0010282030 30 3A 32 33 20 6F 6E20 46 72 69 64 61 79 2C00:23 on Friday,
0010283020
Useful Features of UNIX File Systems
When performing a forensic analysis of Unix file systems, there are features that should be inspected beyond just the file date-time stamps. As shown in Figure 6.3, the last time a Unix file system was mounted is recorded, which should be consistent with other activities on the system.
File permissions can also be revealing in a case, enabling digital investigators to determine which user account was used to create a particular file, or which group of users had access to data of concern.
Because Unix systems break portions into the disk into block groups, data of similar types are often stored in the same area of the disk, facilitating more efficient and focused searching for deleted data. For instance, efforts to recover deleted logs can focus on the /var/logs partition.
Unix systems in an Enterprise are often configured with some remote storage locations, which can be seen in /etc/fstab as shown here:
| /dev/hda1 | / | ext2 | defaults | 11 |
| /dev/hda7 | /tmp | ext2 | defaults | 12 |
| /dev/hda5 | /usr | ext2 | defaults | 12 |
| /dev/hda6 | /var | ext2 | defaults | 12 |
| /dev/hda8 | swap | swap | defaults | 00 |
| /dev/fd0 | /mnt/floppy | ext2 | user,noauto | 00 |
| /dev/hdc | /mnt/cdrom | iso9660 | user,noauto,ro | 00 |
| none | /dev/pts | devpts | gid=5,mode=620 | 00 |
| none | /proc | proc | defaults | 00 |
remote-server:/home/accts/home/acctsnfs
bg,hard,intr,rsize=8192,wsize=8192
remote-server:/var/spool/mail/var/spool/mail nfs
bg,hard,intr,noac,rsize=8192,wsize=8192
In this instance, all files in user home directories are stored on a remote server named remote-server along with spooled e-mail. Therefore, preserving just the hard drive of the single system would not preserve all potentially relevant files associated with the use of that system. It would also be necessary to preserve files stored on the remote server.
Deleting and Recovering Data
When a file is deleted, its inode link count is set to zero, the directory entry is removed (and may be added as slack to a previous entry). In addition, the inode table is updated to show that the inode is no longer in use, and the block bitmap is updated to release blocks. In some versions of Linux file systems, the inode reference is set to zero and an additional deleted date stamp is updated. This process allows forensic examiners to recover deleted filenames and deleted inodes (and the associated data on disk) but makes it difficult to associate deleted filenames with deleted inodes.
The most effective strategy to recover deleted data is to examine deleted inodes, which are listed in the inode tables. Although the deleted inode does not contain a filename, it does provide useful metadata including dates, attributes, and location of data on disk. For smaller files, the inode contains a list of the actual blocks that contains data from the deleted file. The inode for larger files reference indirect blocks, which are simply lists of the actually allocated blocks.
Deleted files can be listed with TSK using fls with the -d option (deleted) as shown here for the same floppy disk used in previous examples:
% fls -f linux-ext2 -r -p -d ext2-floppy-021304.dd
r/- * 0:file2
r/- * 0:handle.pdf
r/- * 0:.file3.swp
r/- * 0:.file3.swpx
There is no date-time information associated with these files because we do not know with which inode they were associated. Older versions of the ext2 file system did not zero out the inode numbers making it easier to associate a deleted filename with its associated inode. Because the inode is not available in newer versions of ext2, the fls output does not give us much information, so let us look at the associated inodes in more detail using ils.
% ils -f linux-ext2 ext2-floppy-021304.dd
class|host|device|start_time
ils|raven|ext2-floppy-130204.dd|1077912300
st_ino|st_alloc|st_uid|st_gid|st_mtime|st_atime|st_ctime|st_dtime|
st_mode|st_nlink|st_size|st_block0|st_block1
1|a|0|0|1076285001|1076285001|1076285001|0|0|0|0|0|0
15|f|0|0|1076285446|1076285446|1076649861|1076649861|100644|0|47|58|0
18|f|500|500|1076648869|1076648869|1076649898|1076649898|100664|0|80117|
626|627
How do we associate the filenames with the appropriate inodes? We compare the metadata in each inode with metadata associated with each file to determine links. The preceding results show us that inode 15 referred to a 47-byte file and inode 18 referred to a 80117-byte file (in bold). By extracting the contents of inodes 15 and 18 using icat and determining what type of data they contain, we can make an educated guess about at least one of the files.
% icat -f linux-ext2 ext2-floppy-021304.dd 15 > unknown-file-inode15
% file unknown-file-inode15
unknown-file-inode15: ASCII text
% cat unknown-file-inode15
This file was created on Feb 8 at around 19:10
Note that cat is a standard UNIX command that is used to concatenate and print files, whereas icat is part of TSK and is used to print inodes.
% icat -f linux-ext2 ext2-floppy-021304.dd 18 > unknown-file-inode18
% md5sum unknown-file-inode18
MD5(unknown-file-inode18)= 490ab7557538a4c4b5d6f75ce51384ff
% file unknown-file-inode18
unknown-file-inode18: PDF document, version 1.2
% ls -l
-rw-r--r-- 1 user wheel47 Feb 27 15:19 unknown-file-inode15
-rw-r--r-- 1 user wheel80117 Feb 27 15:17 unknown-file-inode18
Ordering the date-time stamps of unallocated inodes using the mactime utility combined with the ils -m option, we can see when the inodes were last modified, last accessed, and deleted.
% ils -f linux-ext2 -m ext2-floppy-021304.dd | mactime
Feb 08 2004 19:030 mac ----------001<alive-1>
Feb 08 2004 19:1047 ma. -rw-r--r--0015<dead-15>
Feb 08 2004 00:0780117 ma. -rw-rw-r--50050018<dead-18>
Feb 08 2004 00:2447 ..c -rw-r--r--0015<dead-15>
Feb 08 2004 00:2480117 ..c -rw-rw-r--50050018<dead-18>
The only item with activity around 19:10 on Feb 8 is inode 15, indicating that it was named file2.
Another useful phenomenon on Unix file systems from a forensic perspective is the persistence of deleted inodes. When a file is deleted, the corresponding inode will retain some metadata associated with the file until the inode is reused. Therefore, deleting a file effectively freezes its metadata until that inode is overwritten by a new file, which may not occur for months or longer (Farmer & Venema, 2005). When large numbers of files are created and deleted, such as when an intruder installed malicious code on a compromised system, these traces can remain in the inode table for a long time.
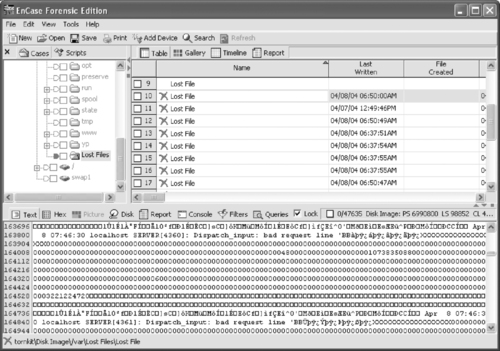
When a file system is damaged on a Unix-like system, an automated process may place recovered files in a directory named lost+found at the root of the damaged volume. The contents of files within these lost+found directories may be of interest in a forensic examination, but it may be difficult to determine where they were originally located on the system. Confusingly, EnCase places a list of recoverable deleted files in an area called Lost Files within the user interface of the forensic tool (see Figure 6.6b later in this chapter). There is no relation between the lost+found directory on a Unix system and the Lost Files area in EnCase.
Out-of-Place Inodes
In findings first described in Forensic Discovery by Farmer and Venema (2005), the authors made the discovery that inodes are typically allocated in fairly linear fashion, and that wildly outlying inodes may be used to find replaced binaries, and trace them back to their original creation location. You can list the inode number of a file using the –i flag to ls as demonstrated here:
[root@localhost /bin]# ls -fli
…
1278043 -rwxr-xr-x 1 root root 61 2007-08-28 20:43 gunzip
1278002 -rwxr-xr-x 1 root root7316 2007-10-04 22:45 dbus-uuidgen
1277976 -rwxr-xr-x 1 root root 18476 2007-10-30 12:52 env
1278058 -rwxr-xr-x 1 root root 53036 2007-10-30 12:52 chown
164019 -rwxr-xr-x 1 root root 99564 2007-10-30 12:52 ls
1277988 -rwxr-xr-x 1 root root 19200 2007-10-30 12:52 basename
1278034 -rwxr-xr-x 1 root root 19804 2007-10-29 03:41 alsaunmute
1278027 -rwxr-xr-x 1 root root 52044 2007-10-05 11:15 sed
1278030 -rwxr-xr-x 1 root root 84780 2007-10-17 06:30 loadkeys
Note that the ls binary's inode number is not in the same range as the other items in the “/bin” directory. Where did it come from? Searching for other files with similar inodes reveals the answer as shown:
find / -xdev -print | xargs ls -id | sort -n
164017 /tmp/toolkit.tgz
164018 /tmp/.toolkit/eraser.tar
164019 /bin/ls
164020 /tmp/toolkit/.chroot
…
We can be pretty certain at this point that ls wasn't modified as part of a standard system update.
User Accounts
The “/etc/passwd” file contains a list of users and the full path of the associated home directories. The passwords for user accounts are generally stored in “/etc/shadow” (provided a centralized authentication mechanism is not in use).
A typical entry in the “/etc/passwd” file is shown here with a description of each field:
user:x:500:500::/home/user:/bin/bash
1. username
2. Hashed password field (deprecated in favor of “/etc/shadow”)
3. User ID (UID)
4. *primary* group ID (GID)—note that a user can belong to any number of groups. This information is stored in “/etc/group.”
5. GECOS comment field, generally used for a full username or a more descriptive name for a daemon account
6. User's home directory
7. Shell/program to run upon initial login
The “/etc/passwd” file will usually be fairly lengthy even on a single user system. An old trick that is still occasionally seen in the wild is to add an additional UID 0* user somewhere in the middle of these default accounts—an attempt to fade into the noise. (Note that any user with UID 0 is the functional equivalent of root.)
The “/etc/group” file has a somewhat similar format, with fewer fields. A typical selection of entries will look like the following:
root:x:0:root
bin:x:1:root,bin,daemon
daemon:x:2:root,bin,daemon
wheel:x:10:root
The first field is the group name, second is the hash of the group password (password protected groups are not typically used), the third is the GID, and the fourth is a comma-separated list of the members of the group. Additional unauthorized users in the root or wheel groups are suspicious and warrant further investigation.
The /etc/shadow file is the final piece of the authentication puzzle. It stores encrypted user passwords and related information.
root:id=”l0330”$gsGAI2/j$jWMnLc0zHFtlBDveRqw3i/:13977:0:99999:
7:::
bin:*:13826:0:99999:7:::
…
gdm:!!:13826:0:99999:7:::
user:id=”l0330”$xSS1eCUL$jrGLlZPGmD7ia61kIdrTV.:13978:0:99999:7:::
Again, the fields are as follows:
1. Username
2. Encrypted password
3. Number of days since the epoch (1 Jan 1970) that the password was last changed
4. Minimum days between password changes
5. Maximum time password is valid
6. Number of days prior to expiration to warn users
7. Absolute expiration date
8. Reserved for future use
One item to note is that the daemon accounts bin and gdm don't have an encrypted password. Since these are not user accounts they have a null or invalid password field to prevent them from being used for an interactive login. Any nonuser accounts that do have encrypted password fields should be investigated.
The root user is all-powerful on a standard Linux system. As such, gaining access to this user's privileges is usually of paramount importance to an intruder. For this and other reasons, access to root is usually strictly controlled. Unfortunately, some users may require root privileges to run certain programs or perform specific tasks beyond the capabilities of a normal user. The two interactive methods are via the su and sudo commands.
The su command requires that the user knows the root password—the user is literally logging in as root from within their current session. Nothing is to stop the user from logging in directly as root in the future. In a shared-root password environment, you have no accountability in the event that the root user does something disastrous, malicious or not. This problem is solved by sudo, which allows for fairly fine-grained distribution of root powers to nonroot users. This is controlled by the “/etc/sudoers” file. You should examine this file for spurious or otherwise unauthorized entries or modifications if the particulars of your investigation indicate that an existing user was operating beyond their authority.
Even when a user account is deleted from a Unix system, the home directory can be left behind. Therefore, it can be fruitful to look in the “/home” directory for user data.
System Configuration
Unix does not have the equivalent of a Registry in Microsoft Windows. Instead, Unix systems use configuration files that are generally text-based. Although this transparency has the potential of making forensic examinations more straightforward, reducing the need to interpret data stored in proprietary formats, it is necessary to understand what information these configuration files contain.
Scheduled Tasks
There are two methods of scheduling a command to be executed automatically at a preset time: at and cron. The cron process is the main method for scheduling a task to run at some point (or points!) in the future on a Linux system. Intruders may create a cron job on a compromised system to periodically launch a backdoor or beacon to enable them to regain entry.
There are two primary locations where cron will look for jobs to process: “/var/spool/cron,” which will contain the user IDs of any users who have entered cron jobs using the crontab command, and “/etc/crontab”, which will list additional locations for systemwide cron jobs. Generally these are found in the directories “/etc/cron.hourly,” “/etc/cron.daily,” “/etc/cron.weekly,” and “/etc/cron.monthly.”
These locations (and any others referenced in /etc/crontab) should be examined for unauthorized jobs. This is an old but still extremely popular and effective way to maintain access on a compromised Unix system.
The at command provides similar functionality to cron and creates job files in “/var/spool/cron.”
Artifacts of User Activities
When conducting a forensic examination of a computer system, it is often necessary to determine how a specific user accessed the system and what that user did. Unlike Microsoft Windows with its wide array of artifacts of system usage, Unix systems record relatively little information beyond some common log files.
Unix systems can keep extensive logs of the activities of individuals within the system. The degree of detail in these logs varies depending on the configuration of the machine, but all Unix systems have some basic logs described here.
Logging onto (and off of) a System
When a user logs into a Unix system, they may be presented with information about the previous logon to that account, which is stored in the lastlog file. At that point, the lastlog and utmp files are updated with information about current logon session, including the time and host name. The utmp file contains information about active login sessions that can be displayed using the who or w command. The same information that is entered in the utmp file is appended to the wtmp log file, which is a simple user logon/logoff database common on most forms of Unix, including Mac OS X. The difference between these two files is that utmp entries are cleared when the user logs off, whereas the entries in wtmp are retained indefinitely.
On Unix systems, the default locations are “/var/run/utmp” and “/var/log/wtmp”. Each entry in the wtmp database includes the user login name, device name, and host name, if remote. In addition, the wtmp database will generally have the time of logon and logoff, which can be helpful when trying to determine which user accounts were connected to the system at the time of interest.
The last command is used to query the wtmp database to determine who logged into a system and when they logged out. However, as can be seen in the first line of Table 6.1, the last command on most systems truncates the host name, making it necessary to use a customized version of last to process the wtmp file or obtain the host name from somewhere else.
The wtmp database can also be parsed using an EnScript as shown in Figure 6.5.
There are a number of potential problems to be aware of when it comes to these logon records. Not all programs make an entry in wtmp in all cases. For instance, sshd does not make an entry in wtmp when someone connects using scp or using the port forwarding feature of SSH. Also, because different systems have slightly different wtmp formats (as defined in the system's “/usr/include/utmp.h” include file), programmers sometimes create programs that create improperly formatted entries in the wtmp database. For instance, some versions of MIT's Kerberized Telnet daemon create logout entries with the same time as the corresponding logon entry, causing sessions to be displayed as 0 minutes long. Additionally, the wtmp database can be corrupted by an incomplete write, making it necessary to analyze each log entry carefully using customized programs (Blank-Edelman, 2000).
Syslog
Unix also maintains system logs (a.k.a. syslog) that can either be stored locally or sent to a remote system. These logs show incoming connections to servers and outgoing connections to WiFi. The following log entries show a Linux computer connecting to a WiFi Access Point named AWPERUCES.
Oct 29 23:02:41 twinklingstar NetworkManager: <info> Will activate
connection ‘eth1/AWPERUCES’.
<cut for brevity>
Oct 29 23:02:41 twinklingstar NetworkManager: <info> Activation (eth1)
New wireless user key for network ‘AWPERUCES’ received.
Oct 29 23:02:41 twinklingstar NetworkManager: <info> Activation (eth1)
Stage 1 of 5 (Device Prepare) scheduled…
Oct 29 23:02:41 twinklingstar NetworkManager: <info> Activation (eth1)
Stage 1 of 5 (Device Prepare) started…
Oct 29 23:02:41 twinklingstar NetworkManager: <info> Activation (eth1)
Stage 2 of 5 (Device Configure) scheduled…
Oct 29 23:02:41 twinklingstar NetworkManager: <info> Activation (eth1)
Stage 1 of 5 (Device Prepare) complete.
Oct 29 23:02:41 twinklingstar NetworkManager: <info> Activation (eth1)
Stage 2 of 5 (Device Configure) starting…
Oct 29 23:02:41 twinklingstar NetworkManager: <info> Activation (eth1/
wireless): access point ‘AWPERUCES’ is encrypted, and a key exists.
No new key needed.
Unix systems can be configured to send syslog entries to a remote system by adding the following line to /etc/syslog.conf configuration file:
*.* @remote-server
Figure 6.6 shows the buffer overflow attack against a Linux server using two forensic analysis tools. The Sleuth Kit (TSK) has strong support for examining Unix file systems and was able to recover the name of the deleted log file as shown in Figure 6.6(a). Although EnCase recovered the deleted log file as shown in Figure 6.6(b), it was not able to recover the file name.
Notably, syslog uses an unreliable mechanism to send information to a central logging host, since it relies on the connectionless UDP protocol. In other words, a computer sends its log entries over the network to the syslog server on a remote computer but has no way of determining if the log entries reach their destination. If the syslog server is fortunate enough to receive the log entry, syslog timestamps the log entry with the date and time of the syslog server, not the sending host. Therefore, even if the clock on the sending host is accurate, the syslog server can introduce a time discrepancy. Also, the syslog server has no way of confirming the origin of a given log entry. So, it is possible to forge a log entry and send it to the syslog server, giving the false impression that a certain event occurred on a certain computer.
Command History
A command history file is maintained for each user account on a Unix system, and contains recent commands executed under that account. The name of the command history files depends on the shell being used. It is most common to find .bash_history files in user home directories on a Linux system, and .history or .sh_history files on other Unix systems.
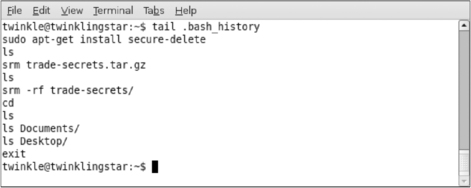
Command history files can be very useful for determining what a user or intruder did on a Unix system. The sample command history in Figure 6.7 shows the use of a secure deletion program (srm) to destroy the contents of a file named trade-secrets.tar.gz and a related folder.
Observe in Figure 6.7 that the command history does not show the date that each command executed. However, by examining the last accessed dates of files referenced in a command history file, it may be possible to determine when some of the activities occurred.
A system administrator found a suspicious file on a Linux server within her organization and reported the problem to us. The file she had found contained the following, which turned out to be a rootkit.
| % tar tvf aniv.tar | |||||
| drwxr-xr-x | 2 | 512 | Mar | 8 17:02 | rkb |
| -rw-r--r-- | 1 | 358400 | Mar | 8 17:02 | BeroFTPD-1.3.3.tar.gz |
| -rw-r--r-- | 1 | 326 | Mar | 8 17:02 | readmeformountd |
| -rw-r--r-- | 1 | 757760 | Mar | 8 17:02 | root.tar.gz |
| -rwxr-xr-x | 1 | 8524 | Mar | 8 17:02 | slice2 |
| -rw-r--r-- | 1 | 6141 | Mar | 8 17:02 | mountd.tgz |
| -rw-r--r-- | 1 | 849920 | Mar | 8 17:02 | rkb.tar.gzb |
By the time we reached the location to examine the compromised system, the system administrator had restored the system from backup. As a result, there was limited information available about the intrusion. Fortunately, forensic examination of the system revealed the following command shell history, showing commands executed by the intruder:
% more .bash_history
w
pico /etc/passwd
mkdir /lib/.loginrc
cd /lib/.loginrc
/usr/sbin/named
ls
w
ls
/usr/sbin/named
ls
cd ~
ls
mv aniv.tar.gz /lib/.loginrc
cd /lib/.loginrc
tar zxf aniv.tar.gz
ls
cd aniv
ls
tar zxf rkb.tar.gz
ls
cd rkb
./install
Using this information, we were able to find aspects of the compromise that had not been obliterated when the system was restored from backup, including a user account that had been added by the intruder and would have allowed continued unauthorized access. In addition, we were able to look for similar signs of intrusion on other systems within the organization.
Application Traces/Recently Opened Files
In addition to the earlier records of activities maintained by Unix systems, individual applications generate artifacts of user activities that can be useful in an investigation. Examples of traces that applications leave behind on Unix systems relating to user activities are provided here.
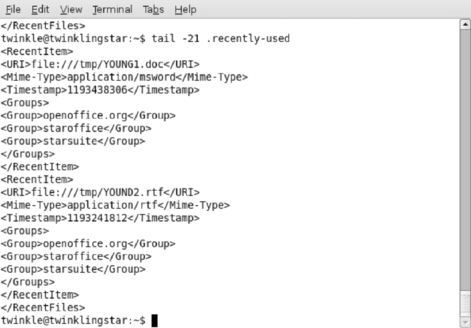
Gnome is the default desktop environment on some versions of Linux (e.g., Ubuntu), and is available for other versions of Linux. Gnome maintains lists of recently opened files in a number of locations, providing digital investigators with information about user account activities. For instance, Gnome maintains a list of recently opened files in a file named .recently-used.xbel in the home directory of each user account. In addition to the full path of the opened files, the entries in .recently-used.xbel contain the date-time stamp the file was opened and the application used to open the file. A sample of entries from this file are provided here.
grep “bookmark href” .recently-used.xbel
<bookmark href=”file:///home/eoghan/Desktop/PTK_readme.pdf”
added=”2008-04-01T13:43:01Z” modified=”2008-04-01T13:43:01Z”
visited=”2008-04-01T14:11:07Z”>
<bookmark href=”file:///media/MAXTOR160MB/Morgue/tornkit-image/tornbin.bmp” added=”2008-04-01T14:52:04Z” modified=”2008-04-01T14:52:04Z” visited=”2008-04-01T14:52:11Z”>
<bookmark href=”file:///media/disk/Chapter10%20Mobile%20Network%20Investigations-20090408.pdf” added=”2009-05-22T17:52:01Z” modified=”2009-05-22T17:52:02Z” visited=”2009-05-22T17:52:01Z”>
<bookmark href=”file:///media/disk/Chapter4- IntrusionInvestigation_05122009.doc” added=”2009-05-22T18:38:16Z” modified=”2009-05-22T18:38:16Z” visited=”2009-05-22T18:43:25Z”>
<bookmark
As this example demonstrates, this information can reveal the use of removable media.
Additional information about files that were opened using a particular user account can be found in files under the .gnome2 directory. For instance, the gnome2/gedit-metadata.xml and gnome2/evince/ev-metadata.xml files may contain names of files opened under a specific user account.
Some application like Open Office maintain their own list of recently used files. Figure 6.8 shows entries in a .recently-used file under a specific user account, providing the full path of files that were opened and the associated dates.
Similarly, the GIMP graphics viewing and editing program maintains a list of recently opened files in .gimp/documents under each user account as shown in Figure 6.9.
The Wireshark program for capturing network traffic as detailed in Chapter 9, “Network Analysis” maintains a list of recently used files and filters in the .wireshark/recent file under each user directory as shown in Figure 6.10.
Forensic examiners should experiment with the specific programs found on a subject computer to determine whether the application maintains historical details of usage. The possibilities are limited only by the number of applications that are available. For instance, the Nautilus file manager application can retain some information about files that were in use under a specific user account in the .nautilus directory, and a program called Midnight commander has similar information (see the DFRWS2008 Forensics Challenge at www.dfrws.org).
Printing
Printing on Unix systems often is handled by the Common Unix Printing Solution (CUPS), which creates printer spool files in “/var/spool/cups” by default.
It is also possible to direct print spool files to a remote location by modifying the “/etc/printcap” configuration file.
When a file is printed, CUPS creates two files, a control file containing metadata and a data file containing the contents of the printed file in PostScript format. Figure 6.11 shows the contents of the “/var/spool/cups” folder on a Linux system, with control files starting with a “c” and data files starting with a “d” (deleted in this case).
The lower panel Figure 6.11 shows a CUPS control file with the username and other attributes associated with the print job. Control files are deleted only periodically (e.g., after 500 print jobs), but data files are deleted immediately after a document is printed.
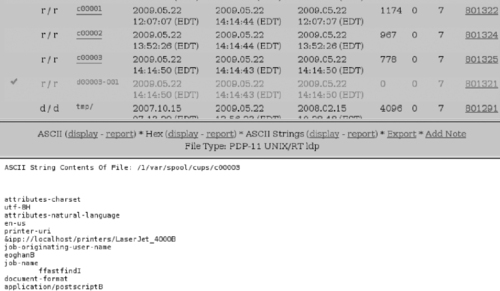 |
| Figure 6.11 |
An ex-employee of a company was suspected of stealing trade secrets. Although he admitted viewing documents of concern, he claimed that this was part of his job and that he had not taken them when he left the company. However, forensic examiners were able recover printer spool files from his Unix workstation, revealing that he had printed the documents of concern the day before he left the company. Faced with this evidence, the ex-employee admitted to taking printouts of the proprietary data.
Although the spool file containing the PostScript version of the document is generally deleted after printing is complete, it may be possible to recover these deleted spool files by carving in unallocated space of the “/var” partition for PDF documents. The beginning of a spool file (“/var/spool/cups/d00006-001”) associated with the printed document “Chapter4-IntrusionInvestigation_05122009” is show here with the username eoghan, document name, and date of printing:
%!PS-Adobe-3.0
%%BoundingBox: (atend)
%%Creator: (OpenOffice.org 2.3)
%%For: (eoghan)
%%CreationDate: (Fri May 22 14:38:34 2009)
%%Title: (Chapter4-IntrusionInvestigation_05122009)
The items in this header provide useful signatures for file carving, as well as keyword searching of unallocated space for specific documents or all items printed by a specific user account.
For accounting purposes, the “/var/log/cups/page_log” records the number of pages (and sometimes the associated filenames) that each user printed at specific times. Although this log does not provide the contents of printed documents, it shows that a user account was in use at a particular time.
Removable Media
Attaching a USB storage device of any kind will create a handful of entries in the syslog.log file. These entries will occur each time the device is connected to the system.
Oct 29 23:16:12 securesrv kernel: Initializing USB Mass Storage driver…
Oct 29 23:16:12 securesrv kernel: scsi2 : SCSI emulation for USB Mass
Storage devices
Oct 29 23:16:12 securesrv kernel: usbcore: registered new interface
driver usb-storage
Oct 29 23:16:12 securesrv kernel: USB Mass Storage support registered.
Oct 29 23:16:17 securesrv kernel: scsi 2:0:0:0: Direct-Access Sony
Storage Media 0100 PQ: 0 ANSI: 0 CCS
Oct 29 23:17:52 twinklingstar gnome-keyring-daemon[5463]: adding
removable location: volume_uuid_5B72_E2E9 at /media/disk
Oct 29 18:43:14 twinklingstar sudo: twinkle : TTY=pts/2 ; PWD=/tmp ;
USER=root ; COMMAND=/bin/umount /media/disk
In addition, there may be references to files stored on removable media that were opened using applications on a Linux system.
Deleting and Destroying Data
There are many userland utilities for obliterating data on Unix-like systems. Although these tools are generally effective at destroying data, forensic practitioners may be able to detect traces of their use as noted in the section on command history earlier in this chapter (see Figure 6.7).
Realizing the value of log files in a digital investigation, some offenders simply delete them. Some intruders will also clear entries from the wtmp database using specialized utilities to make it more difficult for digital investigators to reconstruct events relating to an intrusion. Fortunately, forensic practitioners may be able to recover deleted files or references to files that have been obliterated. Recall the example in Figure 6.6 earlier in this chapter, showing a recoverable deleted syslog file.
In addition, similar to the Recycle Bin concept in Microsoft Windows, when a user deletes a file within a graphical environment, the file is simply moved to a directory. For instance, the Gnome environment places files deleted by a user in the .Trash directory under the home directory. This feature enables users to restore files that were deleted accidentally, but also provides forensic examiners with useful information relating to user deletion activities.
Internet Communications
Unix systems provide a wide range of methods for accessing resources on the Internet. In addition to having web browsers and e-mail clients, Unix systems come with logon programs like SSH that are run from the command line to connect to other systems. This section details the remnants that such programs leave behind that can help digital investigators determine which remote systems were accessed.
Secure Shell
Every time a user connects to a remote host using Secure Shell (SSH), that host's IP/host name and key are added to the known_hosts file, which can be helpful if an intruder used SSH to connect to another host, either on the local LAN or on the Internet as shown here:
$ cat .ssh/known_hosts
192.168.1.103 ssh-rsa
AAAAB3NzaC1yc2EAAAABIwAAAQEA4RjYT7I+f49a70MY6S/1YT63tCUDOz5Yt4N1RpeOtiV
Q9BBG23YO3/N+byoLs7dLPxuR+YR/Gg57YmNiF5 xu2EHM0ewoKL2Y3adjFTUoDhJTYaKg7u
3fqb1TxSERlEeHP2K1i0LaDxl6uDLOvNqy4H/f2Xt RuwXMDViysmjWPR0dCaTbj+D3jbO1U
cg5MIqRlctcM/AH3kF50xiBfamgINtsiJ/jDz9IEDUCXaN9/D+LBT/sw3PS8kWghYlyIyHN
LruWQtp3heFekw2P/1eKqtaZHZuzf5QzUUyvLQhdQ60fOQmr3JN0jWIruIgRTSDORACHkVy
8YQUBbw2WbaC/Hw==
Firefox 3
Firefox 3 stores the bulk of its internal data in SQLite 3 format database files. This is particularly useful for the forensic examiner because querying SQLite databases for information is easily performed with freely available tools (Tito, 2008). On Linux systems, Firefox profile information is stored under the user's home directory in the .mozilla/firefox directory.
In this directory you will find one or more folders and a file named profiles.ini. The content of this file will be similar to the following:
[General]
StartWithLastProfile=1
[Profile0]
Name=default
IsRelative=1
Path=u2wmsy3p.default
On launch, Firefox will read and process this file. In a multiple profile environment, StartWithLastProfile=1 tells Firefox to begin with the last used profile by default. The following stanza describes the first (and on this system, only) Firefox profile. In most normal uses a single profile named default will be present. The Path variable points to the directory under ~/.mozilla/firefox where this profile's data is stored.
Inside of each profile directory you will find numerous files and subdirectories. The most important files here will be the .sqlite files, which are the aforementioned SQLite 3 databases. We will be examining four of these databases in detail.
■ Cookies.sqlite: stores data about cookies
■ Downloads.sqlite: stores data about downloaded files
■ Formhistory.sqlite: stores data about form submission inputs—search boxes, username fields, etc.
■ Places.sqlite: stores the bulk of what would generally be considered “Internet history” data
Since these files are simply SQLite 3 databases, an investigator has many options when dealing with them. For our purposes we will use the SQLite Manager tool, available as a Firefox plug-in or a standalone XULRunner application (http://code.google.com/p/sqlite-manager/).
After exporting the user's Firefox profile, choose Connect Database from the Database menu, and browse to the exported profile directory as shown in Figure 6.12.
Next, select the database you'd like to examine and click Open. From here, you can browse the database structure, execute SQL queries, and export findings. You can also write data to the database, so you should use this tool only on working copies of data. A full discussion of the intricacies of SQL queries is outside of the scope of this book. However, most of these databases have simple schemas with one table of interest. For example, to view the data held in the cookies.sqlite database, you would execute the following command:
SELECT * FROM moz_cookies;
An example of the results from this query are shown in Figure 6.13.
Entries in the cookies database may yield information as to the last time the user visited a site that requested a specific cookie, whether or not the user was registered or signed in at a particular site, and other state information.
The next Firefox database of interest is the downloads.sqlite database shown in Figure 6.14. As the name suggests, this file contains records of the files downloaded by the user. Based on the author's experimentation, the files that show up in this database are those that are handled by the Firefox Download Manager. Multimedia files handled by browser plug-ins and other items that end up in the browser cache will not show up in this database. The most important aspect of this particular database is that it allows the investigator to tie items found on the file system to specific URLs of origin—this could be the make or break point in a “Trojan defense” case.
The formhistory.sqlite database contains entries typed into Form submission fields by the user. Key items of interest here may include addresses and subject lines of web mails, and search terms submitted to search engines.
The database that contains the items most regularly thought of as Internet history is places.sqlite. Unlike the previously discussed single-table databases, places.sqlite has a fairly involved schema, which has been detailed in its entirety by Chris Cohen at www.firefoxforensics.com/research/firefox_places_schema.shtml. For now, knowing that the id field in the moz_places table corresponds to the places_id in the moz_historyvisits table enables us to build a query that will produce relevant browsing history output.
The information of immediate concern in most web-related investigations is the URL visited and the time of that visit. These two items are found in the url field in the moz_plazes table and the visit_date in the moz_historyvisits table, respectively. The visit_date is stored in a modified Unix epoch time with an additional six digits of precision, so the data needs a bit of massaging before it appears to be anything remotely human-readable. The following sqlite statement will retrieve these two values from their respective tables and convert the visit_date to a more readable format:
SELECT
datetime(moz_historyvisits.visit_date/1000000,’unixepoch’),
moz_places.url
FROM moz_places, moz_historyvisits
WHERE moz_places.id = moz_historyvisits.place_id
An example of the output from the above query is provided in Figure 6.15.
Various tools are available to assist in performing examinations of Firefox artifacts. The Firefox 3 Extractor is a command line tool that automates the process of extracting relevant data from the previously mentioned sqlite databases (www.firefoxforensics.com/f3e.shtml). In addition, as shown in Figure 6.16, FoxAnalysis is a GUI tool that simplifies and abstracts much of the database querying we've performed and supports date restrictions, keyword filtering, and various reporting options (http://forensic-software.co.uk/foxanalysis.aspx). Both tools are available free of charge.
Cache
In addition to browser history files, a user's browser cache may be of investigative importance. The cache files are stored under the user's profile in a directory called Cache. Opening this directory for viewing will usually yield a stream of numbered unidentifiable files along with one cache map file (_CACHE_MAP_) and three cache block files (_CACHE_00x_). These are binary files that contain information regarding the URLs and filenames associated with the cached data, as well as timestamp data. This information can be readily parsed and displayed by Cache View (www.progsoc.uts.edu.au/~timj/cv/) as shown in Figure 6.17, or MozillaCacheView (www.nirsoft.net/utils/mozilla_cache_viewer.html).
Saved Session
In some cases, a file named sessionstore.js will be present in the user's profile directory. The function of this file is to recover the user's environment in the case of a crash or other unexpected shutdown. By replaying this file, Firefox is able to reopen the browser windows and tabs the user last had open. An excerpt from a sample sessionstore.js follows.
{state:{entries:[{url:”http://www.engadget.com/2009/02/06/intel-ships-atom-n280-for-720p-netbooks-nvidias-ion-points/”, title:”Intel shipsAtom N280 for 720p netbooks -- NVIDIA's Ion points, laughs”, ID:1001, scroll:”0,1258”}], index:1}, title:”Intel ships Atom N280 for 720p netbooks -- NVIDIA's Ion points, laughs”,image:”http://www.blogsmithmedia.com/www.engadget.com/media/favicon-v2.ico”, pos:10}], _hosts:{‘google.com’:true, com:true,‘www.google.com’:true, ‘fedex.com’:true, ‘www.fedex.com’:true,‘ups.com’:true, ‘wwwapps.ups.com’:true, ‘archlinux.org’:true, org:true,‘wiki.archlinux.org’:true, ‘eeebuntu.org’:true,‘www.eeebuntu.org’:true, ‘colinux.org’:true, ‘www.colinux.org’:true,‘168.0.1’:true, ‘0.1’:true, 1:true, ‘192.168.0.1’:true, ‘168.1.11’:true, ‘1.11’:true, 11:true, ‘192.168.1.11’:true}, width:1396, height:1027, screenX:0, screenY:19, sizemode:”normal”, cookies:[{host:”.google.com”, value:”105027”, path:”/”, name:”GMAIL_RTT”},
E-Mail Analysis
Analysis of e-mail from Unix systems is, in general, fairly easy. Nearly all Unix e-mail clients and servers store mail on-disk in one of two plain-text formats— mbox or Maildir. The older mbox format consists of a single flat file, containing numerous e-mail entries, whereas the Maildir format stores each e-mail as a discreet file in a directory.
Both formats are plain text, so quickly searching for specific content can be performed without the need for any particular e-mail forensics utility. The key pieces are identifying the location of the mail files, identifying the format, and choosing your examination method. I will present two means of examining collected e-mail data.
User mail files are generally stored under the user's home directory; Mozilla Thunderbird stores its mail files in .mozilla/thunderbird directory in each user's home directory. In this directory you will find one or more profile directories, very similar to those discussed in the Firefox analysis section. In this profile directory there will be a folder named Mail that will have one or more subfolders—Thunderbird creates a separate folder for each mail account configured under a profile. Drilling down into one of these folders you should find a handful of files—those without extensions are the mbox format mail files which contain mail content. For example, the Inbox from the author's test machine begins with the following:
From - Thu Jan 29 20:54:02 2009
X-Account-Key: account2
X-UIDL: GmailIdfeefa85b3eb8620
X-Mozilla-Status: 0001
X-Mozilla-Status2: 00000000
X-Mozilla-Keys:
X-Gmail-Received: 5e94fca9d660f8b9699e9a72fa54265243126ada
Delivered-To: [email protected]
Received: by 10.65.153.7 with SMTP id f7cs8807qbo;
Wed, 30 Nov 2005 12:22:58 -0800 (PST)
Received: by 10.64.150.8 with SMTP id x8mr440592qbd;
Wed, 30 Nov 2005 12:22:57 -0800 (PST)
Received-SPF: fail
Return-path: <[email protected]>
The mail continues on with additional headers, then the mail body. This is followed by another “From ” line. (Note: The capitalization as well as the trailing space is important.) The “From ” line is the defined message delineator for the mbox format. Any line beginning with “From ” is counted as a new mail.
Many of the commercial mail forensics tools utilized during examinations of Windows mail formats will be able to easily process any mbox or Maildir files. However, due to their simple and open natures, many free tools exist that will allow the examiner to quickly hone in on the specific data they are after. We examine two of these next—grepmail (http://grepmail.sourceforge.net) and Mairix (www.rpcurnow.force9.co.uk/mairix/).
Grepmail
As its name implies, grepmail is a utility for searching for e-mail items that meet specific criteria, much in the same way the grep utility searches for lines or files that match certain patterns. The grepmail program has built-in knowledge of mail formats and thus gives the examiner more precision when defining search parameters. Although grepmail works only on mbox format mailboxes, it can parse compressed mailboxes, and can search through a number of mailboxes at once. The grepmail options of particular interest to examiners are noted as follows:
-b Search must match body
-d Specify a required date range
-h Search must match header
-H Print headers but not bodies of matching emails
-j Search must match status (A=answered, R=read, D=deleted,
O=old, F=flagged)
-Y Specify a header to search (implies -h)
One particularly interesting feature of grepmail is its date searching capabilities. Dates can be entered in a number of nonstandard formats. “02/21/09,” “4:00am October fourth,” and “today” are all valid date entries. Additionally, date searches can be constrained by keywords like “before,” “since,” or “between.” This level of granularity may prove to be invaluable if your investigation revolves around specific times or dates.
For example:
grepmail -H -d “before 12:30am” 2009-February.mbox
This command will print the headers of all mail found in “2009-February.mbox” sent before 12:30 am each day (the default date field to match is the “sent” date).
grepmail –j –a -d “after Feb 19” 2009-February.mbox
This will display the full content of all mail with a “deleted” status that was received after February 19.
Although certainly flexible and powerful, grepmail tends to slow down when dealing with very large mbox files (I have attempted to use grepmail on ~30GB mbox files). The grepmail program is well suited for queries against relatively small mailboxes and queries where a specific set of keywords, dates, and other search criteria are fixed before the search begins. Many legal discovery cases would fit this description. For investigations that don't have a fixed keyword list from the beginning, and those that may deal with very large mailbox, Mairix is a better choice.
Mairix
The Mairix tool is quite a bit more complex than grepmail, but it is also quite a bit more powerful. We recommend a thorough read through the main page for a full understanding of the tool's capabilities, but hopefully this section will provide you with enough information to get started.
The key difference between Mairix and grepmail is that Mairix first builds an index, which is subsequently queried as the examiner performs searches. Additionally, Mairix is able to search both mbox and Maildir mail files. Unlike grepmail, you won't be able to simply jump into a shell and begin making queries. Searching with Mairix requires several steps. First, you need to create an rcfile that defines some variables Mairix needs to operate. Next, you build the index from your mailbox. Last, you query the index.
Our very minimal Mairix rcfile follows:
base=/forensics/mairix
mbox=2009-February.mbox
database=/forensics/mairix/.database
mfolder=mairix-out
Base defines the base path that Mairix will treat as its root; mbox points to the mbox file we'll be processing. This can be a colon-delimited set of mbox files. Database tells Mairix where to build its index. Finally, mfolder defines where Mairix will store the output from any subsequent queries. Search results are stored in Maildir format by default but this can be configured as necessary.
Next, we tell Mairix to build the index. This is achieved with a simple mairix –f rcfile, but adding a -v flag will increase verbosity and give you some progress information to watch while you wait. Indexing time will obviously increase with larger amounts of data.
root@ubuntu:/forensics/mairix# mairix -f rcfile -v
mairix 0.21, Copyright (C) 2002-2007 Richard P. Curnow
mairix comes with ABSOLUTELY NO WARRANTY.
This is free software, and you are welcome to redistribute it
under certain conditions; see the GNU General Public License for details.
Finding all currently existing messages…
Starting new database
Scanning mbox /forensics/mairix/2009-February.mbox : 100% done
0 newly dead messages, 0 messages now dead in total
Scanning /forensics/mairix/2009-February.mbox[0] at [54,34758137)
Checking message path integrity
Checking to
Checking cc
Checking from
Checking subject
Checking body
Checking attachment_name
Wrote 1 messages (20 bytes tables, 0 bytes text)
Wrote 1 mbox headers (16 bytes tables, 37 bytes paths)
Wrote 16 bytes of mbox message checksums
To: Wrote 0 tokens (0 bytes tables, 0 bytes of text, 0 bytes of hit encoding)
Cc: Wrote 0 tokens (0 bytes tables, 0 bytes of text, 0 bytes of hit encoding)
From: Wrote 6 tokens (48 bytes tables, 39 bytes of text, 12 bytes of hit encoding)
Subject: Wrote 7 tokens (56 bytes tables, 42 bytes of text, 14 bytes of hit encoding)
Body: Wrote 112781 tokens (902248 bytes tables, 1056554 bytes of text, 225562 bytes of hit encoding)
Attachment Name: Wrote 0 tokens (0 bytes tables, 0 bytes of text, 0 bytes of hit encoding)
(Threading): Wrote 1 tokens (8 bytes tables, 45 bytes of text, 4 bytes of hit encoding)
Now we can query the index. Mairix supports a broad range of search operators. Chaining these together allows the investigator to quickly hone in on a small number of interesting e-mails that can be reviewed manually.
expr_i :search expression (all expr's AND'ed together):
word:match word in message body and major headers
t: word:match word in To: header
c:word: match word in Cc: header
f:word: match word in From: header
a:word: match word in To:, Cc: or From: headers (address)
s:word: match word in Subject: header
b:word: match word in message body
m:word: match word in Message-ID: header
n:word: match name of attachment within message
F:flags: match on message flags (s=seen,r=replied,f=flagged, -=negate)
p:substring: match substring of path
d:start-end: match date range
z:low-high: match messages in size range
bs:word: match word in Subject: header or body (or any other group of prefixes)
s:word1,word2: match both words in Subject:
s:word1/word2: match either word or both words in Subject:
s:~word: match messages not containing word in Subject:
s:substring=: match substring in any word in Subject:
s:^substring=: match left-anchored substring in any word in Subject:
s:substring=2: match substring with <=2 errors in any word in Subject:
We'll issue a query for a known-bad domain. Any mail arriving from this domain is suspicious at best.
root@ubuntu:/forensics/mairix# mairix -f rcfile f:hackerdomainz
Created directory /forensics/mairix/mairix-out
Created directory /forensics/mairix/mairix-out/cur
Created directory /forensics/mairix/mairix-out/new
Created directory /forensics/mairix/mairix-out/tmp
Matched 11 messages
The resulting mail files can be found in the “new” subdirectory.
Chat Analysis
Unix-like systems generally come with simple chat utilities like talk and wall that enable users on a multiuser system to exchange messages. Because these chat programs will not generally work between computers that are separated by a firewall, they are not commonly used. Furthermore, these programs do not have an option to save log files. Therefore, forensic examiners will rarely encounter remnants of such chat activities.
A more common program used on Unix systems for chatting with others is Internet Relay Chat (IRC). There are a multitude of clients for accessing IRC, including BitchX and XChat. There are also bot programs like Eggdrop that provide access to IRC. Most IRC clients and bots can be configured to maintain logs that can be useful to forensic examiners. For instance, the XChat program will maintain logs of chat sessions in the .xchat/xchatlogs directory under a user's home directory.
One of the most commonly used Instant Messaging clients on Unix systems is Pidgin. This program enables users to communicate on most of the major IM systems on the Internet, including Yahoo, AOL, and MSN. All configuration files associated with Pidgin are stored in the .purple directory in each user's home directory. For example, Figure 6.18 shows an accounts.xml file that contains the IM accounts that the Pidgin program is configured to use.
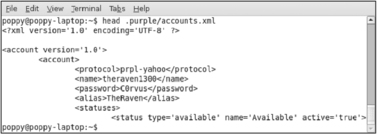 |
| Figure 6.18 |
In addition to logs that are intentionally saved by chat programs, forensic examiners may find traces of chat sessions in swap space on a Unix system as noted in the next section.
Memory and Swap Space
Unix systems reserve a specific storage area for virtual memory, called swap space. Because this area is used to store data from memory temporarily, it can contain passwords, references to files that have been deleted from the system or were stored on removable media, and remnants of user activities such as chat logs and command history.
In one intrusion investigation, remnants of an old .bash_history file were recovered from swap simply using the strings command. This included items that were never written to the actual on-disk .bash_history file as shown here:
ls -lath .config/aweseome/rc.lua
vim .config/aweseome/rc.lua
xmodmap ~/.Xmodmap
ls -lath
less .config/aweseome/rc.lua
vim .config/aweseome/rc.lua
ls -lath
mkdir .config/awesome
mv .config/aweseome/rc.lua .config/awesome/
xmodmap ~/.Xmodmap
vim .xinitrc
kazehakase
mount /dev/sdb1
mkdir /mnt/thumb
sudo mkdir /mnt/
cd hachoir-core-1.2.1
python setup.py
./setup.py
python setup.py install
cd ../hachoir-regex-1.0.3
cd hachoir-parser-1.2.1
In some cases, it may be fruitful to search for remnants of web pages fetched (on clients) or rendered and served up (on servers).
Additional information can also be obtained from memory of Unix systems as detailed in Malin, Casey, and Aquilina (2008).
References
Blank-Edelman, D.N., Perl for system administration: Managing multi-platform environments with Perl. O'Reilly Media. (2000) .
Carrier, B., File system forensic analysis. (2005) Addison-Wesley Professional.
Farmer, D.; Venema, W., Forensic discovery. (2005) Addison-Wesley Professional.
Malin; Casey; Aquilina, J.M., Malware forensics. (2008) Syngress Media.
Tito, M., Journal of Digital Investigation 5 (1–2) (2008).
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.