THE FOCUS OF THIS BOOK thus far has been to look at the tools, technologies, processes, and procedures you can use as a security professional to secure your organization's IT assets, networks, and systems. You've learned about using firewalls to secure the perimeter of the network and VPNs for securing data in transit. You've learned how malicious people might try to attack your network. An understanding of these topics and the others discussed here is critically important for success in the information security field. In this chapter you'll learn about what's next.
Today's information security professionals face a daunting task. Not only do you need to understand how to secure a complex, diverse, and rapidly changing IT environment, but you also need to be aware of the challenges and threats to come. An in-depth understanding of security technologies such as VPNs and firewalls and of threats like malware or social engineering provides the foundation of your arsenal. To be truly successful, however, you also need the ability to identify and respond to trends in both the technologies and the threats under development. To keep up with attackers, you need to know what's coming and where to get reliable, current information.
Throughout your career as an information security professional, you will encounter situations in which you will need to apply security best practices to new technologies or new architectures. You may find that you are conducting investigations, trying to determine how your infrastructure was compromised. You may be monitoring new attacks and trying to develop new defenses. Whatever challenges you face in the future will require that you leverage the experience, understanding, and best practices you've learned to ensure you are effective against new risks and threats.
Throughout this book you have learned about the present state of network security, firewalls, and VPNs. In this chapter you will be looking to the future.
How does a security expert discern what the future holds? A number of factors should influence your planning as you try to draw a road map for your information security strategy:
Historical progression of threats—If you are familiar with how threats have progressed over time, you have a better understanding of where those threats may be headed in the future. For example, 10 years ago virtually all malware attacks were focused on operating systems. Today malware attacks go after applications far more than operating systems. Browsers are a particularly popular target for attacks today.
Your industry—Each industry has different focuses when looking to the future. A bank will have very different requirements from a shoe store, for example. Understand your industry, network with your peers, and make sure you are looking at the proper framework for your planning.
Experts—It's always a good idea to see what the people who predict the future of the industry think before doing your planning. While experts can disagree over certain specific predictions, if you keep an eye on the major information sources (some of which are provided later in this chapter) you will find you can develop a pretty good idea of where information security is headed.
Vendors—Since they are frequently trying to sell you their next-generation solution, vendors usually have a biased view of the future; they can also provide valuable information for your planning, however. If the vendors you work with or follow are all targeting a particular threat or technology, they view it as an area to generate revenue. If an industry targets a specific area as a source of revenue, it's a good bet that a threat lurks there somewhere.
Here are some of the areas you should pay attention to as you plan your information security strategy.
One area evolving almost faster than you can imagine is the variety of threats to your infrastructure. Several years ago the threats most prevalent were from unsophisticated attackers whose main goal was to accomplish something they could brag about in chat rooms with their buddies. Today, organized crime has zeroed in on the huge amounts of money to be made in computer hacking. We now see targeted attacks against specific industries and companies, viruses that target credit card numbers, bank account information and Social Security numbers, and rootkits that, once installed on a computer, turn it into a host the attacker can control remotely to attack other systems and networks. Some attackers will threaten to crash networks with denial of service attacks, unless the system owner pays extortion money—the high-tech equivalent of a protection racket.
In the future, you will see more resilient networks that will mitigate the risk of traffic-based attacks, more secure operating systems and applications to resist malware, and intrusion prevention systems that will respond instantly to attacks, choking them off before they can damage your infrastructure.
Firewalls have been adding capabilities since they were first introduced. Early firewalls contained some limited filtering and NAT capabilities and not much else. You will learn about the wide range of today's firewall capabilities and specialties later in this chapter.
Encryption is a constantly evolving standard. In 1977, the Data Encryption Standard (DES) was specified in the Federal Information Processing Standards (FIPS) Publications. It became a national standard. We have gone from DES, a 56-bit algorithm, to 3DES, an effective 168-bit algorithm, to the algorithm encryption standard (AES), which supports a 256-bit algorithm. The problem with encryption is the constantly improving processing power of computers. As computers get faster and more capable, with bigger and bigger memory space, encryption algorithms become easier and easier to break, through brute force and other techniques.
Encryption's popularity has grown as concerns about protecting data at rest, in transit, and while archived have come to the forefront of many industries. How many stories have you seen about the stolen laptop with 100,000 Social Security numbers on it or an application compromised by an attacker able to read data directly from a hard drive because it was stored in clear text? Today, some government agencies (the Department of Defense, for example) require full-drive encryption for all laptops.
Recognizing the growing need for encryption, the industry is responding quickly. The AES standard was designated as the replacement for DES. It is designed to scale upward with longer keys. Keep in mind as you look into encryption solutions whether they support AES or an equivalent algorithm and be sure that you encrypt your data everywhere it's vulnerable. The days of relying on your VPN as the only data protection are gone. You need to secure data with encryption everywhere it can be accessed.
Another area where you can expect to see dramatic changes in future capabilities is in authentication, especially with respect to identity and access management. In the past, much of user security was based on a user ID and password. Years were spent trying to teach users what a strong password is, why they need a strong password, and why they need to change their passwords every 90 days. The effort has been largely ineffective. Users still choose poor passwords, and even when they select strong passwords, the passwords can still be cracked with sufficient computer power.
The other challenge associated with authentication is actually a user-management issue. All too often in a complex environment, the creation, permissioning, management, and eventual retiring of user accounts doesn't work. Accounts retain permissions long after users move on to other roles, accounts remain on systems long after employees have left the organization, and, in many cases, no auditing of actions using privileged accounts takes place. Collectively, these critical tasks are known as identity and access management.
How will these challenges evolve in the future? One trend is moving away from passwords to tokens, smart cards, and biometric authentication as a replacement to user ID and password solutions.
On the identity and account management front, a number of solutions automate these activities, providing full account life-cycle management and the associated auditing capabilities many companies look for. The one challenge with these solutions is that, due to the sophistication of most corporate computing environments, they are very complex to install and maintain. It's not just a matter of automating the creation of Active Directory accounts in most cases. Companies have multiple application systems and authentication requirements. Making all of these components work together is not easy. Once you get them working together, however, you've removed a significant threat to your security landscape.
One of the biggest complaints from CIOs about information security is the lack of measures for the success of a program. Information security has moved from being an esoteric discipline practiced by a few misunderstood experts to a core business function vital to support the bottom line. While this evolution has been long overdue, today management expects you to quantify your contribution to the company and justify the expenditures they make to support security.
The good news is that the industry has been moving this direction for some time and has developed a number of performance metrics. The most popular is the Information Technology Infrastructure Library (ITIL), which is a set of concepts you can use to formalize your security management practice and the associated reporting. In addition, a number of solutions allow you to automate not only these processes, but also the associated measurements.
Another area of significant evolution in information security is in the nature of what you are trying to protect. Initially, information security was all about keeping the bad guys out of your network. As a result, companies invested significant amounts of money in firewalls and other network security technologies.
Then focus shifted from the network to the host, however, and organizations focused more on managing patches, hardening operating systems, and installing host-based firewalls.
Once the industry secured the host, attackers shifted to threatening the applications running on those hosts. IT then started focusing on integrating security into the software development lifecycle, testing and evaluating code, hiring penetration testers to try to break our code deliberately, and deploying firewalls and proxy servers specifically to secure applications.
The next shift in focus for information security is a growing focus on what is truly valuable—the data itself. Ultimately, all the measures developed to date, from the network firewalls, to the host hardening, to the penetration testing, have all been about securing the data. The industry is now moving toward a data-centric security model, which is a significant paradigm shift from previous models. A data-centric model will force companies to focus on classifying and applying values to their data. While this will undoubtedly be a painful process for many companies, this approach will ultimately yield a much more secure environment.
Cloud computing is a relatively new phenomenon in computing infrastructure that involves moving computing resources out to the Internet. Resources are then shared by multiple applications and, in many cases, shared by multiple corporations. Think of how the phone networks or the electrical grid operates. These clouds are typically built using virtualization that allows for exceptional efficiencies, but also opens up a number of new security challenges.
First, to leverage the true benefits of cloud computing, you have to trust the vendor providing your cloud. This requires a shift in focus from deploying security technologies to ensuring that your vendors are contractually obligated and physically able to keep your data secure. You also need to be able to evaluate vendors to determine how trustworthy they are. If you have the available resources, you should be auditing the vendor(s) to ensure they consistently keep your data secure.
You'll learn about the security challenges specific to virtualization later in the chapter.
A rapidly growing sector of the end user computing space is the use of mobile devices like smart phones, netbooks, or tablet computers. These devices present some unique challenges. Think about how many people today receive e-mail on their smart phone. Or ran out to get a new iPad and are now reviewing confidential documents while riding the train to work. How do you secure these devices?
The good news is that once the industry identifies issues like these, it concentrates resources to work and ultimately solve the problem. The computer security industry has very few "unsolvable" issues. Already virus protection, mobile device management, and encryption applications are available for mobile devices. The challenge you'll typically see in both current and future technology is that these types of devices are frequently overlooked or discounted when documenting security risks. Be sure to keep these devices on your list of risks. They possess an alarming amount of storage and processing capacity, which makes it easy for an employee to inadvertently place confidential information on them.
A variety of resource sites are available to you for more information on network security, firewalls, and VPNs. While this list of online and offline resources provides a good start to for finding additional information, it's impossible to cover every source. Here are some sites and books covering the critical topics just to get you started. If you need additional information, you are only a search engine click or a bookstore trip away from the answer.
At press time, all Web sites listed here were valid; however, with the mergers, acquisitions, and other changes in the industry, some of these links may change over time.
Many of the vendors listed here have products in multiple areas—so they are listed once to avoid confusion.
Firewall Vendors
Check Point Software—
www.checkpoint.comCisco—
www.cisco.comJuniper Networks—
www.juniper.netFortinet—
www.fortinet.comMcAfee—
www.mcafee.comPalo Alto Networks—
www.paloaltonetworks.comAstaro—
www.astaro.comSonicWall—
www.sonicwall.comWatchguard—
www.watchguard.com
Virtual Private Network Vendors
Microsoft—
www.microsoft.comCitrix—
www.citrix.comF5 Networks—
www.f5.comNortel—
www.nortel.comOpenVPN—
www.openvpn.netOpenswan—
www.openswan.org
National Institute of Standards and Technology/Computer Security Research Center—
csrc.nist.govHackerWhacker (Firewall Testing Website)—
www.hackerwhacker.comGibson Research Corporation (Security testing and tools)—
www.grc.comHack Yourself (Security Testing and Tools)—
www.hackyourself.orgCERT (Security Research)—
www.cert.orgSANS (Security Research and Training)—
www.sans.orgISACA (Standards/Certifications)—
www.isaca.org(ISC)2 (Standards/Certifications)—
www.isc2.orgSymantec (Security Vendor)—
www.symantec.com
Network Security Magazine Web Sites
SC Magazine—
www.scmagazineus.comInformation Security Magazine—
searchsecurity.techtarget.comCSO Magazine—
www.csoonline.com
As you review the information security technologies that you may encounter as your information security career progresses, one of the questions you'll probably have is, where will you find these tools?
In the previous chapters you've learned about a number of commercial and open-source solutions for network security. A wealth of both commercial and open-source solutions for network security tools, firewalls and VPNs are available. Where will you find the tools of the future?
Commercial software remains the choice of corporations everywhere, and this won't be changing any time in the future. A number of reasons account for the dominance of commercial solutions in the information security industry. They include:
The popularity of combining hardware and software into an appliance. Many of the most popular firewall, VPN, vulnerability management, intrusion detection and other security applications will be developed and distributed in an appliance format. While some open-source solutions will allow you to use standard server hardware to create an appliance-like solution, a truly open-source appliance will probably be distributed as a commercial solution.
Companies rely on solutions they can support. One of the ongoing challenges with open-source software is the lack of commercial support for the solutions. Highly technical people can work well within the open-source support community. Support from an open-source community is typically better than what comes from a commercial help desk, but corporations are generally reluctant to trust security-related solutions to that model.
Many of the most popular open-source solutions are being commercialized, as their developers look to generate revenue off the products. Two examples would be the Snort intrusion detection solution as well as the Nessus vulnerability scanner. Both tools were widely used and extremely popular open-source security solutions, and both are now available commercially.
While it is pretty common to see companies embrace commercial tools in their production environments, you can't discount the sheer innovation available in the open-source community. Most of the tools referenced in this book are open-source, and you can expect to see continued development on most of them.
Keep in mind a couple of other advantages to open-source tools as you build your security tool kit. First, working with open-source tools is a great way to build your information security skill set. Most security professionals cannot afford to purchase multiple commercial security applications to learn with, so leveraging open-source is a cost-effective career builder.
The other value that open-source security tools bring to a security professional is that these are the same tools many of the people attacking your network will use. One of the most important skills you can develop is the ability to understand the people trying to get into your systems. Learning the tools and techniques they may use by developing parallel expertise will take you far in your career. Commercial applications seldom offer the same learning opportunities. Attackers generally are not using commercial applications in their attacks, and they typically don't draw from the same community available with open-source solutions as you will to help your learning.
No chapter on the future of information security would be complete without a discussion of the influence of wireless connectivity on security technologies. The first thing to realize as you think about wireless is that you need to consider a variety of wireless technologies. Be sure not to focus too narrowly and miss something critical.
Consider the types of wireless technologies that impact your environment:
Wireless deployed as a LAN technology—The original wireless nightmare for information security professionals, deploying of wireless as part of the office LAN caused constant sleepless nights for security departments. Security departments used to invest countless hours test-driving their locations, searching for unsecured wireless access points on their networks. The real challenge with this technology, other than the fact that it permitted the bypassing of your perimeter security controls, was that it was so convenient. Setup was so easy for an employee—at least to set up in the default configuration, with all the attendant security issues.
The good news is that the industry has made great strides in wireless security. Stronger authentication technologies like 802.1x, which requires connecting systems to be authenticated using PKI machine certificates, stronger encryption technologies, and significant improvements in user awareness have made wireless LAN in the office a viable replacement for the wired LAN, while still affording the security you need to keep your data secure.
Public and Home Office Wireless—Public/Home Office wireless is a great thing for your employees. Take out your laptop, connect to the wireless, and you're on the Internet ready to surf. You can connect to the corporate network, do your banking, shop online, or just catch up on the news. What could be more convenient? As is often the case, convenience is the enemy of security. A number of security challenges present themselves with public/home office wireless. First, any unencrypted traffic sent over these wireless networks can be intercepted. Counting on Starbucks (or an employee's cable company) to configure their wireless with the most advanced security capabilities enabled is not reasonable. Work with your users to make sure they understand the risks associated with these types of wireless.
The good news from a corporate network perspective is that you are probably running a VPN for business connections, so that data should be secure.
Mobile Wireless—The ubiquity of smart phones and other devices that can connect to the cellular networks presents the third challenge when discussing the impact of wireless connectivity on information security. Now employees don't need to search for a wireless hot spot before connecting to the network—they can access their mail from just about anywhere. The best defense against these risks is a combination of policy and technology. First, your policy should restrict access to company systems and e-mail to company-owned devices. That allows you some level of control over the types and configurations of devices with access to your data. Next, make sure the devices you're using leverage the appropriate security technologies like encryption and antivirus scanning. While it's virtually impossible to physically secure something as portable as a smart phone, you can ensure that the data on the device can't be recovered if it is stolen or lost.
One ever-expanding area of discussion when looking at security technologies like firewalls, VPNs, intrusion detection, honeypots, vulnerability management, and others is the many uses for this technology. Obviously you use security technologies to secure your data, networks, and systems. And that is certainly the primary use for security technologies. But you should be aware of some additional uses for this technology.
The core security concepts can be summed up with the acronym "CIA." This stands for confidentiality, integrity, and availability.
Confidentiality—Confidentiality deals with keeping information, networks, and systems secure from unauthorized access. This issue is particularly critical in today's environment in light of the high-profile leaking of people's personal information by several large companies. These breaches in confidentiality made the headlines largely because the thefts exposed people to the potential of identity theft.
Several technologies support confidentiality in an enterprise security environment. These include:
Strong encryption
Strong authentication
Stringent access controls
Integrity—Integrity is the consistency, accuracy, and validity of data or information. One of the goals of successful information security is to ensure that the information is protected against any unauthorized or accidental changes. The architecture should include processes and procedures to manage intentional changes, as well as the ability to detect changes.
Availability—Availability is the third core security principle, defined as a characteristic of a resource being accessible to a user, application, or computer system when required. In other words, when users need information, it's available to them. Typically, threats to availability come in two types: accidental and deliberate. Accidental threats include natural disasters such as storms, floods, fire, power outages, earthquakes, and so forth. This category also includes outages due to equipment failure, software issues, and other unplanned system, network, or user issues. The second category is related to outages that result from the exploitation of a system vulnerability. Some examples of this threat include a denial of service attack, or a network worm that impacts vulnerable systems and their availability. In some cases, one of the first actions you need to take following an outage is determining which category an outage fits into. Companies handle accidental outages very differently from deliberate ones.
As you continue to work in the information security field, another acronym you will encounter is "GRC." This stands for governance, risk, and compliance. This is the best way to look at your security technologies from a business perspective. Look at how the security technologies you're deploying provide much more than just securing data:
Governance—Governance is the processes and procedures that ensure employees are following your organization's security policy. For example, you have a policy that says that data in transit across a public network must be secured with at least 56-bit encryption. You would ensure that the only way to connect to the network is through a VPN that uses at least 56-bit encryption. This mechanism would be part of your governance efforts.
Governance is generally used to demonstrate to management, customers, and auditors that your information security program is operating as outlined in your policies, procedures, and practices. If you are a service provider, you can leverage your governance capabilities to show that you can be trusted to keep clients' information secure.
Risk—One of the foundations of any information security program is a robust risk management practice. If you don't identify your risks, how do you know which security technologies to deploy and where? A risk is the likelihood or potential for a threat to take advantage of a vulnerability and cause harm or loss. Risk is a combination of an asset's value, exposure level, and rate of occurrence. A goal of security is to recognize, understand, and eliminate risk.
A risk management process starts with a risk assessment of your environment. Start with your critical data, applications, systems, and networks. Document the risks associated with them in a risk matrix. A typical risk matrix will contain the following:
A description of the risk
The likelihood that the risk will actually occur
The impact of the risk
A total risk score
The relevant business owner for the risk
Which of the core security principles the risk impacts: confidentiality, integrity, and/or availability.
The appropriate strategy or strategies to deal with the risk
The last bullet is the one that's critical with respect to security technologies—you leverage security technologies as part of the strategy to deal with the risks. One of the fastest-growing sectors in the information security career field is compliance. Compliance means ensuring your company obeys internal policies, as well as any applicable laws or other regulatory requirements. A good example of this is the Sarbanes-Oxley act, which requires publicly traded companies to validate the controls securing all financial data. You will find that your security program, in conjunction with the security technologies supporting it, are critical to ensuring compliance with a growing number of regulations.
If you look back to the first uses of network security, security professionals essentially put a firewall between the corporate network and the Internet. That firewall marked the perimeter of the network. As networks have become more complex, companies started finding they were connecting to the Internet in more locations, so more firewalls were installed. The perimeter remained the demarcation between the Internet and the corporate network. Today, the vanishing perimeter has been the subject of many presentations, white papers, and sales pitches, as vendors try to convince organizations to invest to protect their perimeter-less environments.
VPNs extended the internal network outside the nice, neat network perimeter defined by the firewall/Internet interface. Suddenly your network could be in any hotel or coffee shop in the country, as your employees discovered the benefits of mobile computing. To make matters worse, high capacity drives and portable storage meant that not only was your network being extended into places that you had never imagined, but you data storage was no longer contained within your office space. Critical information could be stored easily anywhere your employees wanted.
Unfortunately, that wasn't the end of the challenges you face as an information security professional. In addition to your employees taking your network and data anywhere they wanted, your business discovered the benefits of interconnecting with customers, vendors, suppliers, and partners. Each of these groups needed varying levels of access to your systems, networks, and data.
In addition to all the challenges with connections and data beyond your network, businesses also discovered the benefits of online commerce over the Internet. That seems harmless enough, until you realize that to do business on the Internet, you need to punch holes in the network perimeter to provide access from the Internet to your systems, networks, and data. It's a little like installing skylights in your roof: you want the benefit of the sunlight in the house, but you don't want leaks when it rains.
In a perfect world, your upper-level management would have consulted with you before they embarked on these projects. They would have given you an unlimited budget to deploy network zones separating each of the different types of data, with firewalls and intrusion detection deployed at each level, and enough staff to monitor all the infrastructure to ensure nothing is getting past your security measures.
In reality, the first few connections were most likely put in without input from security, and these might not even be firewalled. It's so much easier than having to justify purchasing firewalls, setup firewall rules, monitor logs, and all the other things an organization needs to do as it opens holes in its protective perimeter.
What's needed in this case is a clear, well-established policy with strong senior management support. The appropriate controls should be put in place to re-establish your perimeter. If you treat the risk of all these new technologies connecting to your network the same way you treat the risks posed by the Internet, you'll mitigate the risks associated the increasingly fluid perimeter you will be dealing with.
In this chapter you'll learn about some of the specialized firewalls that are available—or are coming soon, such as:
Hybrid—A hybrid firewall combines a number of different functions in a single appliance. You learned about firewalls with integrated VPN capabilities, but you can also expect to see firewalls combined with vulnerability management, intrusion detection and prevention, antivirus/anti-spyware, content filtering, or a variety of other network and security-related technologies. The key when looking into hybrid firewalls is ensuring that they will meet your specific security needs while not creating a performance bottleneck. The more functions you put on a single system, the more chances you'll run into a performance bottleneck.
Data Protection—A data protection firewall is a hybrid firewall, but deserves some additional explanation. The focus of a mature security program is to ensure that data is secure. An emerging technology is data leakage prevention (DLP), which is a technology specifically designed to ensure that your data stays within your network. When combined with firewall technologies at the perimeter of the network, a data protection firewall becomes an invaluable tool in keeping your data out of Gmail and Facebook accounts and within the internal network where it belongs.
Application—An application firewall is specifically designed to control input, output, and/or access to an application. This type of firewall became very popular when the focus of attacks shifted from operating systems to applications. An application firewall operates by monitoring the input, output, and system calls made in an application, and blocking any that do not conform to the firewall rules. An application firewall can block buffer overflow attacks, SQL injection attacks, and the majority of other application-focused attacks.
Application firewalls are either network-based or host-based applications. One drawback of application firewalls is they are typically designed for specific types of applications (i.e., Web applications or databases), whereas a standard firewall can secure many different types of applications, though not to the level an application firewall provides.
Database—A database firewall is an application designed to control the input, output, and system calls made to a database. While limited to database security, this firewall offers very granular security for databases.
Ubiquitous—This is ultimately the direction that firewalls will likely take in the future. The industry current supports a variety of firewalls integrated into the network and the host, that run on the perimeter and the core to protect demarcation between network zones. Now firewalls are moving into the virtualization area. Eventually this intelligence and control will be pushed directly into the infrastructure and managed from a single console. Instead of controlling isolated ports on a firewall-by-firewall basis, you'll be able to manage secure data as it flows into, out of, and through your environment from the originating host to the perimeter of your network and at all connections in between. This will allow you to re-establish the perimeter that disappeared with all the external connections to your network.
Two other security technologies available to secure networks are intrusion detection systems (IDS) and intrusion prevention systems (IPS). An IDS detects unauthorized user activities, attacks, and network compromises. IDSs come in two types, host-based and network-based.
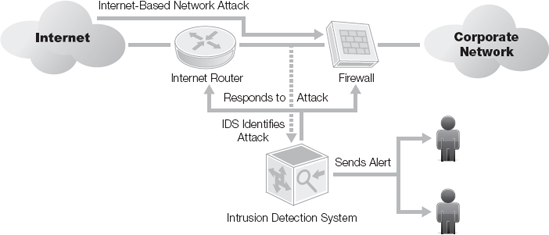
Figure 15-2. IPS detects attack, alerts operators, and then modifies firewall and router configuration to address the attack.
Note
IDS/IPS is used largely on Internet connections, since those connections typically present the largest threat to the network. You can also deploy IDS/IPS in strategic locations on the internal network. This is an excellent idea if your internal network has connections to third-party networks such as customers, vendors, or business partners.
An intrusion prevention system (IPS) is very similar to an IDS, except that in addition to detecting and alerting, an IPS can also take action to prevent a breach from occurring.
Two common deployment methods are used when placing an IDS/IPS for protecting a network from the Internet. Each has its own advantages and disadvantages.
An unfiltered IDS/IPS installation examines the raw Internet data stream before it crosses the firewall. This provides the highest amount of visibility to attacks, but also means that a significantly higher volume of data will be monitored, with a higher possibility of false positives. During periods of high traffic, the IDS/IPS might not be able to process all the packets, and attacks can be missed.
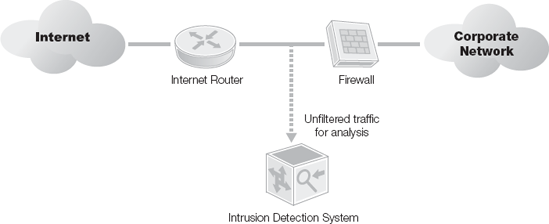
Figure 15-3. Placement of the Intrusion Detection System so it gets unfiltered traffic for analysis.
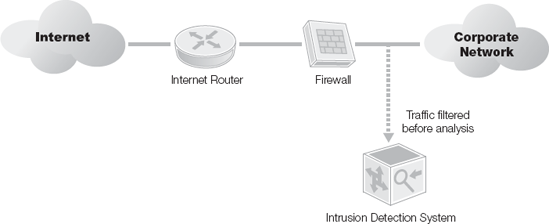
A screened IDS/IPS solution monitors traffic that gets through the screening firewall. The advantage to this model is it dramatically reduces the amount of traffic to be monitored, reducing the chances of false positives and lost packets during high traffic volumes. A loss of visibility accompanies this model, as you cannot see attacks blocked by the screening firewall.
Honeypots, honeynets, and padded cells are complementary technologies to IDS/IPS deployments. A honeypot is a trap for hackers. A honeypot is designed to distract hackers from real targets, detect new exploitations, and learn about the identity of hackers. A honeynet is just a collection of honeypots used to present an attacker an even more realistic attack environment. A padded cell is a system that waits for an IDS to detect attackers and then transfers the attackers to a special host where they cannot do any damage to the production environment.
While these are all extremely useful technologies, not many corporate environments deploy them. You generally see these deployed by educational institutions and security research firms. Generally corporate information security professionals are so busy securing their environment from attacks that they don't spend time researching attack patterns. As long as the attack doesn't succeed, they are satisfied.
In addition to these future enhancements to security technologies, you should also be aware of three more areas of emerging security technology:
Data Leakage Prevention (DLP)—DLP technologies are systems that identify, monitor, and protect data in use, data in motion, and data at rest from inappropriate use, distribution, transmission, or other unauthorized actions. DLP technologies perform deep-content inspection within a scope defined by a central management console and are usually deployed at multiple locations within the environment to ensure full coverage. As the value of data continues to climb, this technology should see wider implementation. The technology is already used heavily in the financial industry. New government regulations will help drive the implementation in other sectors, most likely healthcare. HIPAA, HITECH, and PCI have specific data protection requirements.
Biometrics—Identifies a user based on anatomical characteristics such as fingerprint, voice print, or iris patterns. These methods of identification have a number of advantages over passwords, tokens, or ID cards.
First, biometric authentication requires the person being authenticated be physically present. Second, biometric security removes the need to remember complicated passwords. No more passwords taped under keyboards—you carry your password with you wherever you go. Finally, biometrics remove the need to carry a token or ID card with you—you don't have to worry about not being able to work when you leave your token on the kitchen table at home.
The areas where biometrics are currently being investigated include ATMs, laptops, and computer networks.
Virtualization Security—As virtualization and cloud computing continue to gain ground, a new generation of virtualization-aware security tools are under development. Antivirus, vulnerability management, data leakage prevention, and IDS/IPS technologies are all being developed to run against the underlying hypervisor layer. This gives the security applications direct access to the underlying data transport layer of the virtual environment rather than forcing them to run against each virtual server, dramatically improving performance, visibility to security issues, and ease of use.
In multi-tenant environments (multiple companies sharing the same virtual environment) additional security tools are being developed to ensure that no access occurs between the virtual environments.
You learned about IPv6 in some detail in Chapter 12, VPN Technologies, so you should be aware that IPv6 is the next-generation IP version and the successor to IPv4. While the main driving force for the redesign of Internet Protocol was the rapidly approaching exhaustion of IPv4 addresses, IPv6 has significant implications to future information security professionals.
IPv6 includes a native information security framework (IPsec) that provides for both data and control packets. This means that what you currently do with a traditional VPN you will be able to do natively with any IPv6 device. At a high level, that means you can run your IPsec VPN without requiring a client, but the implications are significantly more profound than just that.
In a fully IPv6 environment, any connection can use an IPsec connection. This means that any connection from a user to an application, host-to-host, or even peer-to-peer connection authenticate and encrypt as it passes across the network.
While the thought of a network featuring nothing but secure connections seems like a security professional's dream configuration, you should also consider some drawbacks before kicking off your IPv6 migration project. One of the challenges with encryption is that it not only secures data from the bad guys, but it also secures the data from the good guys. A number of security technologies like IDS/IPS, content filtering, network-based antivirus, data leakage prevention, and even firewall technologies rely on being able to look at packets as they cross the network to determine how to handle them. Once those packets are encapsulated in a secure IPsec connection, all the security tools you have relied on stop working.
With the limited deployment of IPv6, significant development on solutions to overcome these challenges hasn't occurred yet, but it will be a subject of great interest as the use of IPv6 expands.
Chapter 12, VPN Technologies, looked at some of the types of virtualization and how they impact the current use of VPNs. You should think about some additional areas that look to the future of virtualization.
Virtualization and VPN deployment are examples—some SSL VPNs have the ability to provide a unique virtual VPN configuration for each individual user group. Much like other types of virtualization, a virtualized SSL VPN allows you to separate the physical and logical use of the VPN. In the future, this capability could extend to IPsec VPNs, as well. While this technology offers some unique abilities when configuring secure VPN contexts for different user groups, the additional complexity is something you need to know. A misconfigured virtual VPN context could expose parts of your network to groups that should not have access to them. For example, if you are using a virtualized VPN to provide customers access to a help desk ticketing system, and you inadvertently grant that context access to your intranet where all your pricing information resides, you expose the organization's proprietary data to unnecessary risk.
Firewalls are another technology that is starting to permit virtualization. Currently some firewalls on the market can partition into multiple virtual firewalls. Each virtual firewall appears to be a separate firewall with its own security policy, interfaces, and configuration. This allows you to use your firewall hardware more efficiently than you might otherwise, but once again additional risks occur with the deployment of virtual firewalls.
First, while firewalls exist that support this technology, not all of them support all their features in the virtualized environment. Before you deploy a virtualized firewall, be sure it supports all the features you need to meet your business and security requirements. While this is a very promising technology, it's also very new, and sometimes early adopters can find themselves encountering issues the vendor didn't discover during their quality assurance processes.
Next, you are relying on logical segregation of firewalls rather than the physical separation offered by multiple physical firewalls. While this technology remains new, do some testing before deploying virtual firewalls into a critical environment. Finding that there's a way to bypass the virtual security and move from one virtual environment to another would not be good if you are using the firewall to separate two customers connected to your network.
Finally, this model suffers from the same complexity challenges with respect to the virtual VPNs. Any time you have a solution that offers greater flexibility, you also open the possibility for greater complexity. Complex environments are almost always more difficult to secure, monitor, and manage than simple environments.
However, assuming all the challenges associated with virtualizing security technologies like VPN and firewalls, a compelling business case exists for leveraging hardware more effectively in a virtualized environment. Be sure you understand the technology thoroughly before deploying it. Information security is seldom a forgiving field for learning as you go.
Steganography is the art and science of writing hidden messages so that only the sender and intended recipient know a message exists. Steganography is the ultimate security through obscurity technology.
Probably the most well known technique for steganography in the modern era is the embedding of additional information in a digital image. An image before and after a message has been embedded in it appears unchanged to the naked eye. In reality, run the image through the proper program and the secret message appears. However, steganography has been around a lot longer than digital images, and it can take many forms. Simply writing a message in invisible ink on the page of a book is a form of steganography.
The main advantage of steganography is that messages do not arouse suspicion. If you encrypt an e-mail message and send it, and the message is intercepted, then whoever intercepted the message assumes there's something sensitive in the message. If however, you send a copy of a picture of your kids at the amusement park with a message embedded in the photo, unless the intercepting party knows the coded message is coming, they will not give it any special attention. Encrypted messages protect the message. Steganographic messages protect the data as well as the intentions of the sender and the receiver.
The final topic for discussion in this chapter is the use of anti-forensics. Anti-forensics are a series of techniques designed to try to frustrate forensic investigators and their digital forensic techniques.
Forensic techniques are well known to the information security community, and by extension, to the hacker community, as well. As a result, hackers have developed an arsenal of counter-techniques they use to foil investigations. If they can prevent the investigator from recovering usable evidence, they stand a better chance of avoiding discovery or prosecution. Some of these techniques are also used to hide rootkits and other malware.
Some examples of anti-forensic tools and techniques include:
Securely overwriting data
Overwriting metadata
Designing code that won't run when the system is in debugging mode
Designing code that won't run in a virtual machine
Preventing a system from entering safe mode or debugging mode
Running all code from an external device like a USB drive
Tampering with file system date and time stamps
Running in read-only mode to prevent the system from updating file information.
You should be familiar with the concepts associated with anti-forensics, but unless you are planning on becoming a forensic investigator you probably won't encounter any of these except possibly securely overwriting data.
In this chapter you learned about a number of topics dealing with the future of security technologies and some of the significant emerging security threats. Future information security tools may come from the commercial or the open-source communities, and you learned about the pros and cons of both of those areas of development.
Governance, Risk, and Compliance are the pillars of good policy for guiding your use of security technologies. While the obvious use for security technologies is to provide security, when all is said and done, information security needs to be a business enabler, created with an understanding of the business requirements and the bottom line. The days of deploying information security technologies based solely on management's fear of security incidents are long gone.
Changes in networking technologies on the security perimeter can affect how network security operates. Firewall specialization includes hybrid, data protection, application, database, and ubiquitous firewalls. IDS, IPS and other complementary technologies, such as honeypots, honeynets, and padded cells, steganography, and anti-forensics are essential elements in modern secure networks.
Anti-forensics
Data leakage prevention (DLP)
Digital forensic techniques
Information Technology Infrastructure Library (ITIL)
Padded Cell
Pick the two most common IDS/IPS deployment models:
Bypass
Unfiltered
Tunneled
Intranet
Screened
Which of the following are types of specialized firewalls?
Data protection
Host
Application
Hybrid
Network
Two technologies used to identify attack techniques and patterns include _______and _______.
Techniques used to counter digital investigations are known as: _______.
Pick the two changing areas to watch when developing your information security road map.
Security industry focus
Vendors
Computer processing power
Cloud computing
Network design
The technique of hiding a secret message in plain sight is known as _______.
Which of the following is a potential disadvantage of IPv6 from a security perspective?
Additional address space
Less flexible than IPv4
Industry support
Maturity of the standard
Ubiquitous encryption
Identifying a user based on anatomical characteristics is known as _______.
Which of the following are biometric characteristics?
Default password
Fingerprint
Iris pattern
Voice print
Token
Which of the following are considered complementary technologies to an IDS/IPS implementation?
Honeypot
Encryption
VPN
Padded cell
Virtual firewall
A device that monitors network traffic and alerts during an attack is an _______.
A device that monitors network traffic and alerts and takes action without manual intervention during an attack is an _______.
Which of the following contribute to the erosion of the network perimeter?
Specialized firewalls
VPN
IPS/IDS
Cloud computing
Business partner connections
The act of ensuring your company obeys internal policies and any applicable laws is known as _______.
The processes and procedures used to ensure employees are following corporate security policies are known collectively as _______.
Identify one risk associated with the use of a public wireless connection.
Encryption
Virus
Data interception
Data corruption
Social engineering
What is one advantage to commercial security solutions that might make a company select them over open-source equivalents?
Flexibility
Support
Cost
Availability
Value
Which of the following might be included in a risk register?
Risk description
Impact
Cost
Business owner
Continuity planning
Which of the following are considered core security principles when discussing the uses of security technologies?
Confidentiality
Governance
Integrity
Risk
Compliance
When an IDS detects an attack it can direct the attacker to a host where the attacker cannot do any damage. This host is known as a _______.