NETWORK SECURITY IS UNDER CONSTANT ATTACK by threats both internal and external, ranging from disgruntled employees to world-wide hackers. There's no perfect defense because hackers are able to bypass, compromise, or evade almost every safeguard, countermeasure, and security control. Hackers are constantly developing new techniques of attack, writing new exploits, and discovering new vulnerabilities. Network security is a task of constant vigilance, not a project to complete. It's a job that's never done.
Why is understanding hacking, exploitation, vulnerabilities, and attacks critically important? As the sixth century B.C. Chinese general and author Sun Tzu stated in his famous military text The Art of War: "If you know the enemy and know yourself you need not fear the results of a hundred battles." Once you understand how hackers think, the tools they use, their exploits, and their attack techniques, you can then create effective defenses to protect against them. Understanding hacking not only improves network security; it also maintains security at a high level of readiness.
What motivates hackers to attack computer networks? Why does anyone get involved in illicit activity outside the mainstream? The motives are as numerous as there are ways of conducting the computer attacks: Many do it for the sheer thrill of hacking, for the sport of it. Some hackers consider hacking their hobby. Some love a challenge. Some are victims of peer pressure or are seeking social validation. To still others, hacking is a status trip. And finally, many hackers pursue their exploits for power and financial gain. Take a look at some of these motives in more detail to see if you can begin to understand the hacker mentality.
Many criminal hackers are in it simply for the money. There are many ways of gaining financially from attacking computer networks. These range from theft of credit cards and financial statements to blackmail and black markets. Some monetary gain is immediate. Hackers might be able to transfer funds out of a target account, for example. Other methods are more involved, such as stealing corporate documents and selling them to competitors or hijacking data using encryption and holding it for ransom. Hackers can become involved in selling their services, including distributing spam, eavesdropping, cracking passwords, and generating DoS events.
Demonstrating the ability to compromise a target, especially if the target is reasonably secure, is a way for a hacker to prove they are more powerful than the defenders. If you can control something, you have power over it. If a hacker can control your computer remotely, then the hacker has power over your computer, and in some ways has power over you as well. Hackers sometimes hack as an ego boost. If they can wage a successful attack, then they are showing dominance over their target.
For many hackers, it's an exciting challenge to find new vulnerabilities, develop new attack code, or discover new security breaches. Some hackers attack targets for the same reasons some people climb mountains - because it's there, because they can, and because they want to beat it. Some hackers continually seek out new more difficult targets to improve their skills and increase the level of the challenge.
Some hackers enjoy the sheer risk of attacking a network. As with any crime, the risk of being caught is always a possibility. A target network might have honeypots, IDS, IPS, firewalls, and other technical defenses that the hacker will need to detect and evade. Security professionals are always looking to discover new attack techniques and learn the identity of hackers. Every attack by a hacker, therefore, poses a risk of getting caught and prosecuted.
Hacking can be thrilling. Think of the way a treasure hunter on private property feels. The combination of power, challenge, risk, and potential pursuit along with discovering potentially valuable assets is a thrill for some hackers. The thrill of "getting away with it" motivates many hackers to continue their attacks once they figure out how to successfully hack into a network.
Some hackers have few exciting or engaging aspects of their life and they resort to hacking as an attempt to be entertained or distracted from their boredom. A successful system breach will usually initiate a response, often a cat-and-mouse game that is more entertaining for the hacker than anything else they can think of at the moment.
Hackers have peers and social groups just like everyone else. Peer pressure can be a powerful motivator to fit in, show off, or demonstrate loyalty to a group. Peer pressure is often a motivator for those in the lower levels or rankings of hacker communities. New or inexperienced hackers feel encouraged to perform attacks to maintain their membership in their peer group.
Hacking can also be a mechanism to validate someone socially, such as proving a qualification to join a group. Some attacks are performed as an initiation or rite of passage from a potential hacking group member to an actual full member.
Hacking can help the hacker achieve or maintain status. Hackers may be seeking to achieve status in the eyes of hacking peers, in the judgment of other hacking groups, or in the perspective of the world at large. Some hackers try to cause a media story and to get their name in the news. Other hacks are performed to instill fear and compliance in current and future targets.
Hackers perform hacks for many reasons, and this list is likely incomplete. These motivations drive them to do unethical activities. You might or might not completely understand the hacker mindset. It's important for you to try, however; the results, regardless of the motivation, can be devastating for companies and individuals alike.
In terms of security, the things you want to protect are known as assets. An asset is anything used to conduct business over a computer network. Any object, computer, program, piece of data, or other logical or physical component employees need to accomplish a task is an asset.
Among a hacker's favorite targets are easy assets—ones that pay off quickly. Easy targets are IT infrastructures and elements not properly secured. Systems with well-known, exploitable holes exposed to the world are "easy pickin's" for hackers.
Targets that pay off quickly are those that earn the hacker some form of monetary or barter gain. Credit cards and bank accounts can be a solid monetary score. In other cases, access and control of networks, especially those with high-speed Internet links, are valuable targets. Such a network could be saddled with malicious code that transmits spam, eavesdropping, file exchange, encryption cracking, and so on. The hacker can then trade or sell these services to others.
Some hackers, however, do not seek the easy targets; instead they look for unique targets, new challenges, and complex infrastructures to test and improve their skills. Expert and highly experienced hackers often want to continue to improve their abilities, rather than waste their time on targets that any amateur hacker—or "script kiddie"—could compromise.
What valuable assets do attackers most frequently target? Every hacker is different, just as with any individual member of any sub-culture. While many agree on what is valuable, such as money and access, others might find corporate finances, secret formulas, medical history, credit reports, court records, accounting logs, and so on more preferable as their target of choice. For example, why do some people collect toys while others collect cars, or coke bottles, or pictures of Elvis?
To better understand of possible targets hackers might choose, review the seven domains of a typical IT infrastructure (Figure 4-1):
User Domain—Any user, worker, employee, contractor, consultant, or individual can be a target. Social engineering is a hacker attack against people. This type of attack attempts to fool people through clever wording, lying, misdirection, relationship manipulation, fear, psychological tricks, and confidence games. The results of social engineering attacks can include users giving away private information or performing actions on a computer that causes a reduction in network security.
Workstation Domain—The workstation, client, or standalone home system can be a target. These types of hosts are often less secure than LAN servers. This is not on purpose, because most security focuses on core components of the infrastructure, rather than those seemingly on the periphery. Many times the security measures on a workstation are often old, out-of-date, or improperly installed and configured.
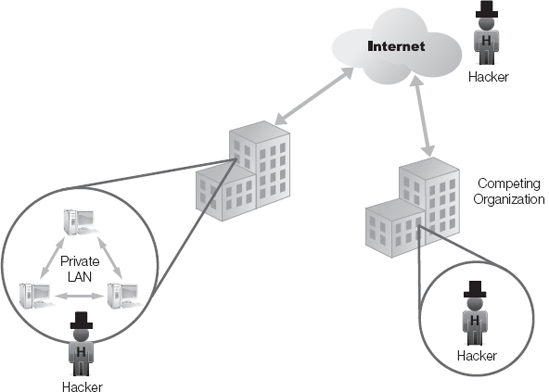
LAN Domain—The private LAN, from SOHOs to large corporations, is a common target. A LAN often consists of dozens to thousands of hosts. The odds that all individual systems are highly secure are unlikely. Once a hacker gains access to one system on the network, the rest of the LAN is vulnerable to attack. The compromise of a single host can lead to the compromise of the entire infrastructure.
LAN-to-WAN Domain—The WAN connections between LAN locations, especially those controlled by third-party entities, are targets. Transition interfaces between a private LAN and a WAN connection can be potential weak points. If a compromise is successful against a WAN connection, the malicious traffic inbound across the WAN/LAN interface is unlikely to be filtered.
Remote Access Domain—Remote access is always a popular target of hackers. Remote access removes the need for the hacker to be physically present to access and attack the LAN. Hackers anywhere in the world with an Internet or telephone connection can still reach out to attack any seemingly isolated target. Remote access is an invitation to hackers to try to breach your defenses.
WAN Domain—WAN domains are networks, such as ATMs or Frame Relays, owned by a telco or a carrier network company that leases access to corporations. Often, the privacy of these WAN connections is electronic isolation rather than encryption. Hackers focusing on a specific target may attempt to breach the electronic isolation of the carrier network rather than focusing on the end-point LANs themselves.
Systems/Applications Domain—Collections of servers hosting applications, virtualized systems, or databases are valuable targets. Sometimes the data hosted is the target. Sometimes the computing power of the servers is the resource the hacker wishes to seize.
Assets do not have to be expensive, complicated, or large. In fact, many assets are relatively inexpensive, commonplace, and variable in size. For most organizations, including SOHOs (small office, home office) environments, the assets of most concern include business and personal data. If this information is lost, damaged, or stolen, serious complications can result. Businesses can fail. Individuals can lose money. Identities can be stolen. Even lives can be ruined.
Valuable resources abound on individual computers as well as on IT infrastructures comprised of interconnected LANs. Hackers seek out targets based on a variety of goals and motivations, as well as perceived value of a resource. But who are the hackers?
What violates network security? The answer includes accidents, ignorance, oversight, and hackers. Accidents happen, including hardware failures and natural disasters. Poor training promotes ignorance. Workers with the best of intentions damage systems if they don't know proper procedures and lack the necessary skills. Overworked and rushed personnel overlook issues that can result in asset compromise or loss. Malicious hackers can launch attacks and exploits against the network, seeking to gain access or just to cause damage.
"Hacking" originally meant tinkering or modifying systems to learn and explore. However, the term has come to refer to malicious and possibly criminal intrusion into and manipulation of computers. In either case, a malicious hacker or criminal hacker is a serious threat. Every network administrator should be concerned about hacking.
Time and time again, research has shown that most of the security violations an organization experiences originate from within—from their own or internal personnel. Nearly 80 percent percent of breaches are caused by insiders, while only 20 percent are attributed to outsiders (source: 2001 CSI/FBI Computer Crime and Security Survey, http://www.gocsi.com/). This doesn't mean you should focus on employees and ignore outsiders. Instead, take a balanced approach, focusing on all vectors of compromise. Hackers can reside inside as well as outside the perceived boundaries of your organization or network.
Hackers are people. Misguided, unethical, ingenious, and criminal, but still people. The major threat to network security is mostly because of human intervention. While designing security, keep in mind that the threat is ultimately and mostly human. This awareness should lead to better selections of deterrent, detection, and response.
Employees and external entities represent differing levels of risk you need to address. An external entity does not start off intrusion attempts with physical or logical access. Initially the risk from an external attacker is low. Outside attackers must seek out and discover methods of gaining logical or physical access. Without access, hackers must resort to attacking external interfaces such as Web servers, VPN devices, firewalls, and RAS. If these are secure, then their default or fall-back position is to wage a DoS attack, attempt a burglary, or perform social engineering against insiders.
An on-site employee has physical access to the facility and logical access to the network. An employee may only have a standard or normal user account, but some level of logical access can be parlayed into greater levels of access (known as privilege escalation). Threats from insiders, whether physical or logical, are serious. You must address such threats in your security policy, network design, infrastructure deployment, and ongoing system and security management.
The people who represent the most common threats to an organization's network security include: disgruntled employees, contract workers, recreational hackers, opportunistic hackers, and professional hackers.
Disgruntled employees believe that they have been wronged somehow by the organization. Whether the wrong is real or perceived, their actions can cause severe disruption of mission-critical operations. Disgruntled employees may attempt to embezzle, steal supplies, waste time, deposit malicious code, leak confidential data, interrupt other workers, or derail projects. You can find a good example of this mindset in the movie Office Space.
Contract workers are outsiders brought in to perform work on a temporary basis. Contract workers can be consultants, temporary workers, seasonal workers, contractors, even day-laborers. Outsiders do not necessarily share the same loyalty to the organization that most full-time employees exhibit. Thus, if the opportunity affords itself to compromise the organization for personal gain, contract workers are more likely to act unethically. Such criminal outsiders don't worry about long-term stability or viability, or the fate of regular employees. Instead, they take advantage at the expense of others.
Recreational hackers are those who enjoy learning and exploring, especially with computing technology. However, they might make poor choices as to when to use their newfound skills. Bringing in unapproved software from home, experimenting on the company network, or just trying out an exploit to "see if it works" are all potential problems recreational hackers cause. Some hackers might not fully consider that their hobby can be dangerous and their actions are in violation of the company security policy.
Opportunistic hackers are hackers who are timid and not likely to initiate an attack. For whatever reason, they are unwilling to purposefully plan out and wage intrusions. However, if the circumstance presents itself for an attack that can be easily performed with little potential for discovery or consequence, the opportunistic hacker may take advantage of the fleeting moment. That moment could arrive when they happen to work late and end up being the only one left in the building. That moment could be when a fire drill that drives everyone else out of the facility. Or it could be when a random power outage occurs and half the workforce leaves for home. That moment could arrive when he or she notices a certain office door is left open and no-one else is watching ...
Professional hackers are criminals whose sole career objective is to compromise IT infrastructures. Whether operating as individuals, offering mercenary hacking services, or functioning as a member of a criminal ring, professional hackers focus all their time and energy on conducting the best security assault possible. When someone spends years learning and practicing in one primary area of interest, they can develop expertise and skills to rival all defenses. The perfect unbreachable security solution does not exist. Professional hackers have the time, stamina, skill, patience, and backing to keep up an assault against a target until they succeed. They are to a network what termites are to a wooden building. You can deter them; you can keep them out most of the time. But they will always be nearby and eager to gnaw into the foundations if you drop your guard for a moment.
These descriptions are not meant to imply that all humans are by nature malicious. Instead, they offer a realistic perspective on who might be an unethical person, where potential human-based compromises exist, and what precautions you should take to protect your organization from both internal and external threats.
As much as IT professionals dislike the practice, hacking can be a fascinating process. Hackers' activities often appear chaotic and random, at least when observed from the mainstream IT industry. A hacker doesn't have to follow any fixed procedures or recognize any established boundaries. Instead, they are seeking out vulnerabilities on a selected target using any and all means at their disposal. For them chaos is both a methodology and a defense mechanism.
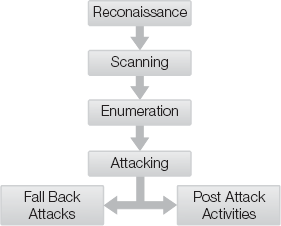
Generally, hacking falls into five main sub-groupings of events or activities. This categorization can represent hacking, but does not actually control or prevent hacking. These five categories are (Figure 4-3): reconnaissance, scanning, enumeration, attacking, and post-attack activities. This order of phases occurs if an attack is successful. If an attack is not successful, the hacker can instead attempt a fall-back position.
The initiation of the whole process of hacking is called reconnaissance. Reconnaissance means the act of inspecting or exploring and can also be called footprinting, discovery, research, and information gathering. This phase is the first of three pre-attack phases hackers use to learn as much as possible about a target before attempting the first actual attacks. Reconnaissance consists of collecting data about the target from all possible sources online and offline. The hacker is careful to avoid tipping off the target that it's being probed for information.
Reconnaissance can include:
Researching old versions of a target organization's Web site at archive.org
Examining search engine contents
Reviewing the live Web site
Investigating the background of personnel
Performing location mapping
Reading job postings
Checking insider information leak sites
Looking at newspaper and magazine articles or mentions
Perusing press releases
Searching USENET newsgroups, chat archives, blogs, and forums
Auditing financial records or reviewing public filings
Reviewing court cases and other public records
Querying whois, domain registrations, and public IP assignments
Eavesdropping on e-mail and other conversations
Visiting a physical location
These are just a few of the possible reconnaissance activities a hacker can use. Information gathering is only limited by the time, resources, and imagination of the hacker. Once the hacker has built and organized a reasonable portfolio of information about the target, the next step is scanning.
Scanning is the activity of using various tools to confirm information learned during reconnaissance and discover new details. Scanning is aimed at discovering live and active systems. Scanning can include war dialing, war driving, ping sweeps, and port scanning.
War dialing is an older tactic using the telephone system to locate any active and answering modems. Using a modem, a hacker's computer automatically dials target phone numbers. The hacker obtains phone numbers during reconnaissance, or by dialing all the numbers in an area code or prefix.
War driving is the technique of using a wireless detector to locate wireless networks. Originally derived from the term war dialing, as hackers used the early techniques to drive around a city with a laptop computer to discover wireless networks. Today, driving is not necessary and many smart phones can detect wireless networks. The presence of a wireless signal usually indicates the presence of computers or network access.
Ping sweeps are used to discover systems over network connections that will respond to Internet Control Messaging Protocol (ICMP) echo requests. Hackers commonly use ICMP for network health and testing. The ping command, or network mapping utilities, sends ICMP echo requests to all possible recipients within an IP address range or subnet. ICMP echo responses from system indicate their IP address and that they are up and running.
Hackers perform port scanning by sending various constructions of TCP or UDP packets to ports (Figure 4-4). If the system is not already known to exist, then a port scan can determine both the existence of a system at a specific IP address as well as whether a port is open, closed, or filtered. A TCP port is known to be open if a full TCP three-way handshake can establish a virtual circuit. A UDP port cannot be confirmed being open since the default response from an open port is always silence.
Scanning is the process of sending out probes to elicit responses. When a hacker performs scanning, it's detectible. Reconnaissance is generally silent, secretive, and unobtrusive. You are also unlikely to detect scanning to verify individual data items, such as a single open or closed port. But when hackers scan to discover all possible IP addresses in use and all possible open and closed ports, it's very noticeable. Scanning for confirmation is to scanning for discovery as a sniper firing a single bullet is to a Gatling gun destroying a forest. One activity might or might not draw attention, but the other will be hard to ignore.
Note
For more information on scanning, especially on advanced techniques, please consult the books listed in the references section at the end of the book.
Hackers perform scanning until they discover one or more targets. Since scanning uncovers only a system and the open ports, hackers learn very little about the targets. Hackers stop scanning and move on to enumeration whenever they want, based on the purpose of their attacks. Keep in mind that an attacker only needs a single vulnerability to gain access. Once hackers can access one machine, moving on toward attacking it quickly is the most common escalation. The next step toward attacking is called enumeration.
The enumeration phase is the third pre-attack phase. Enumeration is the hackers' process of discovering sufficient details about a potential target to learn whether vulnerability exists that they can successfully attack. Enumeration often starts with operating system identification, followed by application identification, then extraction of information from discovered services. Enumeration, then, is the discovery and listing of potential attack targets.
Hackers perform OS identification by probing an open and closed port of a target. The responses from these ports identify the OS. This ID is possible because of the idiosyncrasies of different programmers writing interoperable code. Each OS uses a different group of programmers to write their network protocol stack. Even though the resultant protocol stack may be in compliance with IEEE standards, the defaults and reactions of the stack often differ from one OS to the next. These differences are known and maintained in a small database, which is coded into most network scanning and probing tools, such as nmap.
Each open port has a service running behind it. Banner grabbing is the activity of probing those services to obtain information (Figure 4-5). Once a connection has begun, a service may send an announcement of connection or communication confirmation. This announcement is called the banner. The banner may contain additional details such as the product name and version number of the service.
Once hackers have identified the service, they can request additional information. The information request may be secure and nothing goes out. But if insecure, the service may return volumes of data to the hacker. Depending upon the service and the queries the hacker performs, the extracted information could include system name, network name, user names, group names, share names, security settings, resources available, access control settings, and more.
Enumeration provides the hacker with identified, potential attack points. After reviewing vulnerability databases, such as MITRE (http://cve.mitre.org) or National Institute of Standards and Technology (NIST) (http://nvd.nist.gov), hackers evaluate the potential vulnerabilities. Once the hacker selects an attack target, he collects exploit tools and wages the attack.
Attacking is the fourth phase of hacking. Although this seems to be the phase that attracts most of the hype about hackers, in fact, it's the briefest phase of the overall hacking process. A successful attack, based on solid research and preparation, can take just seconds.
If an initial attack fails, hackers can modify their exploits, tune their payloads, adjust their shell code, and reset their vectors, and re-launch the attack. Once hackers figure out that an assumed vulnerability doesn't exist or has been secured, they return to their enumeration results to select a new point of assault. Again, think of termites: if they can't get into the house structure through a door jamb, they will just as eagerly try to enter through a window sill. They are relentless.
Repeated attacks will either lead to an eventual successful breach or to the frustration of a successful defense by the target. If successful, the attacker moves on to post-attack activities. If unsuccessful, the attacker can elect to move to alternative fallback attacks.
In a successful attack, the hacker usually has breached the target's security to gain some level of logical access. This could be the credentials of a standard user account or a command shell accessed through a buffer overflow exploit. In any case, some common post-attack activities usually take place. These include privilege escalation, depositing additional hacker tools, pilfering data, and removing evidence.
Privilege escalation is the action of attempting to gain higher levels of access or privilege over the target. This can occur using a keystroke logger, known OS exploits to steal administrator or system access, manipulation of scheduled tasks, social engineering, Trojan horses, remote control programs, and potential other mechanisms. The result is that the hacker gains access to a user account or a command shell that operates as an administrator, root, or the system itself. With privileged access, the remaining post-attack activities are much easier.
Depositing additional hacker tools gives the hacker more power over the compromised system. Tools may enable additional abilities unavailable through the current connection method. Tools may assist in pilfering data. Tools may also assist in removing evidence. Or tools may assist in maintaining or regaining access in the future.
Pilfering data is just that: scouring storage devices looking for files of interest. Hackers look for anything they can turn into cash immediately. They also look for things that would be fun or interesting to disclose to the public. They look for items they can use to blackmail or coerce users. And, of course, they are on the lookout for potentially valuable information for bartering or trading with other hackers or criminals. Dumping the user account database and password hashes is often a priority as well. Cracking the passwords of other users will help in re-accessing the system in the future.
Removing evidence of the compromise and subsequent activities is an important step for the hacker. Failing to cover their tracks could lead to apprehension and prosecution. Allowing the IT and security staff to discover the intrusion will only lead to heightened levels security. Discovery makes future returns more difficult, if not impossible, depending on the hacker's skill set.
Once the hacker performs evidence cleanup, the attacker can claim to have owned (or "pwned," in leetspeak, hackers' secret code language) a system. He has demonstrated his skills through the discovery, tracking, and penetration of a target. This is often the goal of a hacker: to successfully penetrate a target. However, such successes are not always easy, or common. If the attacks fail, the hacker always has fall-back attack options.
Fall back attacks are the other options for mayhem a hacker can deploy after unsuccessful breach attempts against a target. Common alternatives to intrusion include DoS, eavesdropping, breaking and entering, social engineering, malicious code, session hijacking, man-in-the-middle attacks, wireless hacking, SQL injection, Web site attacks, and more. The following sections of this chapter discuss these and other attacks.
Some important aspects of security stem from understanding the techniques, methods, and motivations of hackers. Once you learn to think like a hacker, you may be able to anticipate future attacks. This enables you to devise new defenses before a hacker can successfully breach your organization's network.
So how do hackers think? Hackers think about manipulation or change. They look into the rules to create new ways of bending, breaking, or changing them. Many successful security breaches have been little more than slight variations or violations of network communication rules.
Hackers look for easy targets or overlooked vulnerabilities. They seek out targets that provide them the most gain, often financial rewards. Hackers turn things over, inside out, and in the wrong direction. They attempt to perform tasks in different orders, with incorrect values, outside the boundaries, and with a purpose to cause a reaction. Hackers learn from and exploit mistakes and anomalies, especially mistakes of network security professionals who fail to properly protect an organization's assets.
The more you understand about the various threats and risks to network security, the more defenses you can mount against attacks. Threats to network security include hacker exploits, as well as Mother Nature, device failures, and even normal business activities.
Network security is not just about protection against hacking. Many other threats face computer systems on an ongoing basis. Computer equipment is complex and sometimes fragile. Hardware failures are the most common cause of unexpected downtime. Most equipment operates well beyond its expected lifetime in normal environments. Some forms of technology, however, are more prone to failure than others.
One of the most commonly discussed causes of unexpected downtime is hard drive failure. A hard drive is one of the few common computer components that has moving parts. While optical drives, tape drive, mice, and keyboards have moving parts, these devices seem to outlast hard drives by a significant margin. Hard drive failure can occur unexpectedly or with reasonable warning. The warning is usually a grinding, whining, or clicking noise coming from the drive as it begins to fail. These noises are clear signs that the end is near.
The best defense against hard drive failure, as well as hardware failure in general, is to be prepared. Being prepared includes consistent periodic backups, using redundant array of independent disks (RAID), performing general cleaning and maintenance, and having spare parts on hand for the inevitable. Another method to avoid downtime and a loss of availability is to replace equipment before it fails. Most devices have a mean time to failure (MTTF) or mean time between failures (MTBF) that can determine the statistical likelihood of a failure. It is a good practice to replace the device before that period expires. While you will be replacing some devices long before their actual failure, this technique keeps the statistics on your side. When downtime is costly, preventing downtime, even at the expense of functioning hardware, is often worthwhile.
Another physical threat is heat. Too much heat damages computer equipment. Systems that experience severe temperature cycles, such as very hot to very cold, can have incidents of chip creep or warping and cracking of materials. Chip creep is caused by the expansion and contraction of metal because of temperature changes. Severe temperature cycling can even break soldered connections. The traditional debate about turning computers off at night or over weekends and leaving them in a running state speaks to the effects of these temperature changes. A running computer is at its optimum functioning temperature.
Static electricity discharge (SED) from dry conditions can destroy most circuits. Frayed wires caused by rubbing against sharp metal edges can cause a short circuit. Moisture due to high-humidity, weather, or liquid spills is always bad for electrical devices. Excessive vibration can be damaging to computer equipment. Vibrations caused by nearby heavy construction or regular passing of trains, subways, and airplanes can cause damage over time. Any obvious physical damage caused by devices falling, being knocked over, having heavy objects dropped on them, and so on can result in broken equipment.
You can eliminate or significantly reduce most physical risks and threats with reasonable precautions and common sense in proper handing, care, and storage of electronic equipment.
One final physical threat is theft. Physical facility protections ensure that an IT infrastructure is not threatened by unauthorized outsiders (or insiders) walking away with storage devices or other critical components.
Mother Nature is unpredictable and seemingly quite powerful. All sorts of serious weather events damage or destroy IT infrastructures. Knowing the types of severe weather common in your area will suggest the correct precautions, such as special insurance, structural reinforcements, lightning protection, surge protectors, bilge pumps, and so on. No matter what the potential disaster, the best protection for data is a reliable regular backup stored in a secured, offsite facility.
Accidents happen. Whenever humans are involved, things will go wrong. Murphy's Law states that "anything that can go wrong will."
An IT infrastructure is a large, complex, but fragile entity. And it is completely at the mercy of human beings. Accidental damage in the wrong location or at the wrong time can have devastating results. Accidents include spilling liquids on equipment, tripping over cables, pulling out the wrong power cord, tripping the building's circuit breaker, setting off the water sprinklers, placing candles on top of warm devices, knocking over a computer, turning off a system prematurely, installing the wrong driver, removing the wrong cable, and so on.
The best precautions and protections against accidents are backups, configuration documentation, and training. With some common sense adjustments to worker activity, paying closer attention to activities they perform, and watching out for precarious circumstances, you can avoid many "common" accidents.
Unfortunately, accidents are not the only concern when humans are around. Another threat to network security is intentional damage or sabotage. Disgruntled employees, dismissed contract workers, opportunistic janitorial staff, unhappy managers, and even careless visitors can wreak havoc in moments if they have access to sensitive equipment or information. Proper personnel screening, perceptive supervisory oversight, escorts, background checks, security cameras, training, paying attention to the corporate culture, giving in on some indulgences (such as an occasional long lunch or casual Fridays), and providing competitive pay scales can go a long way toward preventing intentional disruption or destruction of IT equipment and resources.
Malware is the shortened term for malicious software. Malware is unethical code hackers write to cause harm and destruction. Malware gains access to a system through a myriad of ways, usually without the consent or knowledge of the user. The most common vectors of this computer contaminant are portable storage devices and Internet communications. A wide range of types of malware exist, including virus, worm, Trojan horse, keystroke loggers, spyware, adware, rootkit, logic bomb, trapdoor, backdoor, dialers, URL injectors, and exploits. The number of unique malicious code examples is astounding. As of December 2009, AVG Anti-Virus reported 2,472,859 infection definitions (Figure 4-6).
Just like a biological virus, a computer virus needs a host object to infect. Most viruses infect files, such as executables, device drivers, DDLs, system files, and sometimes even document, audio, video, and image files. Some viruses infect the boot sector of a storage device, including hard drives, floppies, optical discs, and USB drives. Viruses spread through the actions of users. As users open infected files, the virus spreads to other files. As users send infected files to other systems, the virus spreads there, as well.
Unlike viruses, which spread from file to file, worms spread from system to system. Because human interaction isn't necessary for propagation, they can (and do) spread much more quickly than viruses. Today, nearly every threat described as a "virus" is really a "worm." Hackers design worms around specific system flaws. The worm scans other systems for this flaw, and then exploits the flaw to gain access to another victim. Once hosted on another system, the worm spreads itself by repeating the process. Worms can be carriers to deposit other forms of malicious code as they multiply and spread across networked hosts.
A Trojan horse is actually a mechanism of distribution or delivery more than a specific type of malware. During the Trojan War, the Greeks built a huge, hollow wooden horse, hid warriors inside, and seemingly departed the area. The Trojans took the horse into their citadel and were massacred overnight when the Greek warriors emerged from hiding. The concept now embeds a malicious payload within a seemingly benign carrier or host program. When the host program runs, the malware is delivered.
The gimmick of a Trojan horse is the act of fooling someone (a type of social engineering attack) into accepting the Trojan program as safe. Any program can be converted into a Trojan horse by embedding malware inside it, in the same way that any food can be poisoned by adding a toxic substance to it. In fact, hackers have specialized tools designed for the express purpose of building Trojan horses called wrappers or Trojan horse construction kits.
Keystroke loggers record the keyboard activity of a user. Hackers can deposit software keystroke loggers onto a victim's system through a variety of techniques, including a worm or a Trojan horse. Once a system is infected, the keystroke logger periodically transmits key logs to the originating hacker through e-mail, FTP, or instant message (IM). Hardware keystroke logger attacks can come through the keyboard cable. These are hard to detect because they are so small and are a parasitic link to the keyboard cable.
Spyware is an advancement of keystroke logging to monitor and record many other user activities. Spyware varies greatly, but can collect a list of applications launched, URLs visited, e-mail sent and received, chats sent and received, names of all files opened, recording of network activity, periodic screen captures, and even recordings from a microphone or images from a Web cam.
Adware infiltrates advertisements. Spyware and adware are often linked together in a symbiosis, since the information learned about a target from spyware helps in selecting materials the adware will push through. Adware can push advertisements as pop-ups, as e-mail messages, or by replacing existing legitimate ads on Web sites as they display in the browser.
Rootkits are malicious camouflage that function as invisibility shields for anything a hacker wants to hide on a computer. A rootkit acts like a device driver and positions itself between the kernel (the core program of an operating system) and the hardware. From there, the rootkit can selectively hide files on storage devices and active process in memory from being viewable, accessible, or detectible by the OS. Rootkits hide other forms of malware or hacker tools. Rootkits can include other malware functions in addition to their stealth abilities.
A logic bomb is an electronic land mine. Once a hacker embeds a logic bomb in a system, it remains dormant until a triggering event takes place. The trigger could be a specific time and date, the launching of a program, the typing of a specific keyword, or accessing a specific URL. Once the trigger occurs, the logic bomb springs its malicious event on the unsuspecting user.
Trapdoor and backdoor malware are two terms for the same type of malware. A backdoor or trapdoor program opens an access pathway for a hacker to gain easy access into a compromised system. The access could be the creation of a new user account with credentials the hacker has defined; a rogue Web, telnet, or SSH server that gives the hacker remote command prompt access; or a source that enables full remote-control over the victim's machine (sometimes just by turning on Remote Desktop on a Windows host). Many other possible trapdoor or backdoor manipulations can grant access to external hackers.
A dialer is a rogue program that automatically dials a modem at a pre-defined number. Sometimes this process auto-downloads additional malware to the victim or uploads stolen data from the victim. In other cases, the dialer calls premium rate telephone numbers to rack up massive long distance charges. If the user normally connects to the Internet over a dial-up link, the dialer to could dial a rogue proxy site instead of the ISP. This site would act as a man-in-the-middle and be able to eavesdrop on all communications.
URL injectors replace URLs in HTTP GET requests for alternative addresses. These injected URLs cause a different Web page to appear in the browser than the one requested by the user's click. These replaced Web pages could present advertisement sites, generate traffic to falsify SEO, or lead to spoofed sites.
Exploits are any form of malware designed to take advantage of a flaw in programming, timing, communication, or storage. Hackers often embed exploits into other forms of malware to assist in their infection and distribution. Exploits also exist on their own, usually as tools employed by hackers to wage attacks, cause damage, and perform intrusions.
Spam is any unwanted and unsolicited message. Spam is not technically malicious software, but spam can have a series negative effect on IT infrastructures. Experts estimate that from 80 percent to 95 percent of e-mail Internet traffic is spam and other forms of malicious messages. Hackers can easily use spam to wage DoS attacks through flooding and commonly use it to wage social engineering attacks such as phishing.
Malware is spread through the same communication channels as legitimate, benign data. The difference is that hackers design malware to cause distress and destruction. A growing area of risk for the spread of malware is mobile code. Mobile code is software hackers write for easy distribution over communications networks, such as the Internet and mobile phone networks. Hackers design mobile code to download to a host, then execute on the host. Because of a lack of proper precautions and awareness by IT professionals, malware under the guise of mobile code is spreading more rapidly than ever.
Even with all the variations of malware that currently exist and those that will exist in the future, you can choose from few common defenses: antivirus software, anti-malware scanners, integrity checking scanners, and user awareness. Antivirus software actively searches for virus, worms, Trojan horses, and other similar infection and destruction forms of malware in memory and on storage devices. Anti-malware scanners look for spyware, adware, dialers, and so forth that an antivirus software might not address. An integrity checker keeps a database of hash values for all system and application files and reports when unauthorized changes occur to those files. You can improve user awareness by offering training that encourages security- responsible actions. Training will also encourage users take reasonable precautions against infection and attack both at work and at home.
Granted, network security is not always an organizational priority. Some organizations are more concerned with profits and rapid growth than spending time on network security. Security is sometimes viewed as an annoying overhead expense that consumes resources without actually any return to compensate for the outlay. While this mindset is common among senior management, it's a poor and incorrect understanding of the return on investment (ROI) of the crucial investment in network security.
Network security—in fact, most forms of security—protect the organization so that its profit centers can function without interruption or interference. Without network security, the capability and availability of the IT infrastructure would be unstable, especially during periods of accident, infection, attack, or hardware failure. Network security reduces the occurrences of downtime and damaged or lost resources. What could be more important to an organization's bottom line?
Organizations that fail to address security issues as they experience explosive growth are more likely to experience catastrophic failure. By failing to protect assets (communications, data stores, intellectual property, customer data, financial records, and private personnel data), any level of hacker breach could result in organizational implosion.
Racing to get ahead, without proper planning and preparation, usually ends in failure. When constructing a skyscraper, the top of the structure isn't built until each floor below it is properly erected. Growing a company too fast without adequate network security protections is like attempting to build the penthouse before the lower floors are completed. The rise to the top floor may be exhilarating, but the subsequent crash will be unavoidable. What goes up too fast will inevitably come down faster.
A slightly slower growth rate to build network security, concurrently with the expansion of the organization, is a much smarter plan. Such deliberate growth is more likely to provide sustained growth and longevity, than one based on an unbridled push for forward momentum without considering the risks.
Another potential oversight is an organization's pushing equipment, software, and connectivity beyond a reasonable load level. Trying to pull a yacht with a sports car comes to mind. It looks sexy, but what's at risk? Modern IT equipment is able to perform at astounding levels. But even the best equipment can only perform so far before it exceeds its peak operational limitations—and starts trending toward failure.
The growth of most organizations is predictable. Predictable growth can help plan for expansion of infrastructure before the infrastructure becomes a bottleneck. As growth passes 60 percent capacity of the current infrastructure, you should already be planning for expansion. As growth passes 80 percent capacity, take steps to implement expansion. As growth passes 90 percent, accelerate your efforts to complete the expansion.
If the company reaches 100 percent capacity before it completes expansion, a bottleneck inhibiting growth will result. This obstacle can create a bounce-back effect, in which interrupted growth could shrink the organization, making the return to growth more difficult. Equipment, storage space, memory capacity, backup capabilities, communication bandwidth, and processing capabilities should never reach maximum use or consumption. You should reserve sufficient overhead for the occasional spike above normal "maximum" activity.
The security implications of a wireless network compared to a wired network are often exaggerated. The biggest difference is the mechanism and proximity of the attack. With wired networks, a hacker must gain physical proximity to a target to make direct contact with it. Once connected to the wired network, then the hacker can attempt various attack and exploits.
With wireless networks, the hacker doesn't have to be physically close. Hackers can attempt network breaches from a mile or more away from the access point (Figure 4-7). In most real-world situations, however, the range is often under a thousand feet with a small, but powerful directional antenna.
In either case, wired or wireless, the hacker must first obtain a network connection with the target network to attack, if the hacker's goal is to gain access to user accounts or data stored on the network. If the hacker is mainly interested in destruction and DoS, then logical network access isn't necessary.
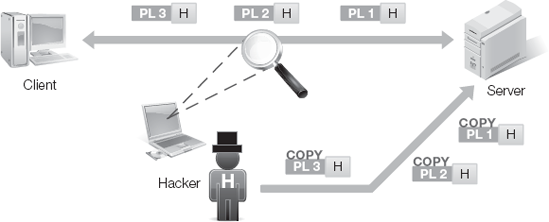
Eavesdropping is listening in on communications. Eavesdropping can be the recording of network traffic using a packet capturing tool, generically known as a sniffer (Figure 4-8). Hackers can eavesdrop against data packets or against voice traffic. Eavesdropping can occur over wired or wireless connections.
Any communication performed in plain and directly usable data forms is subject to interception and recording. You can prevent eavesdropping by using encrypted protocols. Only cryptographically encoded messages are safe from outsiders learning the content of the conversation.
Replay attacks are also known as playback attacks. A replay attack is the re-transmission of captured communications. The goal of a replay attack is to gain interactive or session access to a system. The traffic captured and re-transmitted for a replay attack is authentication packets (Figure 4-9). In this type of attack, the hacker captures traffic between a client and server, and then later re-transmits it against the same server as the original communication.
The goal of this attack is to replay the credential packets so that the hacker gains access to the user's account on the target host. Another type of replay attack is resending a transaction, such as "Send a $10 refund check."
Fortunately, you can thwart most replay attacks by using one of several common communication improvements. Many authentication transactions include a non-replayable random challenge-response dialog. This dialog consists of one endpoint generating a random seed value sent to the other endpoint. The second endpoint uses a mutual secret known by both endpoints to compute a response using a one-way computation. The response returns to the original endpoint, where the response was predicted. If the received and predicted responses match, the user is authenticated.
Another defense against replay attacks is time stamps. Some authentication exchanges have encoded time details that are difficult to reproduce or modify without detection. Additionally, the use of one-time pad or session-based encryption can make replay attacks impossible.
Insertion attacks come in many forms, all of them involve the introduction of unauthorized content or devices to an otherwise secured infrastructure. Three common insertion-based attacks include SQL injection, IDS insertion, and rogue devices.
SQL injection is an attack that inserts a hacker's code into a script hosted on a Web site. SQL injection attacks can give the hacker access to the back-end database of a Web application. The technique exploits a weakness in common Web communications that treats certain characters differently because they are assigned a special meaning or purpose rather than just treated as text. These are called metacharacters and act as programming markup. If you don't write a script defensively to block out or ignore metacharacters, then injection attacks can effectively re-write the script based on content a hacker submits. The injected code can perform just about any possible command line task imaginable.
IDS insertion is a form of attack that exploits the nature of a network-focused IDS to collect and analyze every packet to trick the IDS into thinking an attack took place when it really hasn't. The common purpose of IDS injection attacks is to trick signatureor pattern-matching detection of malicious network events. By interspersing attack traffic with packets that the target host will reject, but the IDS will view, the IDS fails to see the attack pattern, but the attack still takes place. For example, an attack is composed of four packets: A, B, C, and D and the IDS signature is a packet stream of ABCD. If the hacker transmits the attack as AXBCYD, where X and Y are invalid packets rejected by the target, then the IDS doesn't recognize the pattern. After X and Y are discarded, the ABCD attack occurs against the target.
Rogue device insertion is a physical form of insertion attack where a hacker inserts an imposter device into an infrastructure. The most common example of this is the insertion of a rogue wireless access point configured similarly to the real, authorized access point. Some users might be fooled into connecting to the rogue access point. This would constitute a man-in-the-middle attack where the hacker would intercept all transactions from the compromised system.
Each insertion attack method requires that you create a unique defense. You can prevent SQL injection attacks by defensive programming and filtering input. Squelch IDS insertion attacks by using modern IDS techniques such as anomaly, behavioral, and heuristic detection. You can derail a rogue device insertion through encrypted communications, pre-configured network access, prohibited wireless networking, user training, and regular site surveys.
Fragmentation attacks are an abuse of the fragmentation offset feature of IP packets. Fragmentation consists of many different network links connected to construct a global infrastructure. Some network segments support smaller datagrams (another term for packet or frame) than others, so larger datagrams are fragmented into the smaller, more compatible size. When the fragmented elements of the original datagram reassemble, manipulations of fragmentation can cause several potentially malicious reconstructions, such as overlapping and overrun. Think of the transporter on "Star Trek:" if anything gets in the way of the reassembly of the person being transported, you might end up with an evil Mr. Spock with a goatee.
Overlapping can cause full or partial overwriting of datagram components creating new datagrams out of parts of previous datagrams. Overrun can result in excessively large datagrams. Other fragmentation attacks cause DoS or confuse IDS detection and firewall filtering.
Protections against fragmentation attacks include modern IDS detection and firewall filtering features, as well as performing sender fragmentation. Sender fragmentation queries the network route to determine the smallest maximum transmission unit (MTU) or datagram size. The sender then pre-fragments the data to ensure that no in-route fragmentation needs to occur. "Beam me up, Mr. Scott-and make sure I get back all in one piece."
A buffer is an area of memory designated to receive input. Buffers are of a specifically determined size set by the programmer, since only a finite amount of memory resides on a host. A buffer overflow is an attack against poor programming techniques and a lack of quality control. Hackers can inject more data into a buffer than it can hold, which may result in the additional data into the next area of memory.
This overflow could be totally ignored, could trigger an overflowing crash or freeze, or could result in arbitrary code execution. In the event of the latter situation, the hacker will craft the input stream so the overflowed data is a command-line code statement executed with system-level privileges. This process is known as arbitrary code execution.
Programmers can prevent buffer overflows. Using defensive programming techniques, such as input limit checks and avoiding programming language functions that do not check boundary limitations, buffer overflows become a useless form of attack.
Cross-site scripting (XSS) is similar to SQL injection, but the results attack future visitors to a Web page rather than grant the hacker access to the back-end database. An XSS attack submits script code to a Web site. XSS can result in persistent malicious modification of Web source files. This causes all future visitors to the site to receive compromised content.
XSS attacks can include e-mails to victims with falsified hyperlinks that point the script injection to a target site when the victim clicks on the e-mail's embedded links. Such an attack can grant the hacker access to the seemingly secured Web transaction of the victim. This form of attack is non-persistent since it only affects those who click on the links in the malicious e-mail.
XSS attacks are generally preventable if you use defensive coding techniques and metacharacter filtering. For end users, defenses include cookie management and disabling scripting support in browsers and e-mail clients.
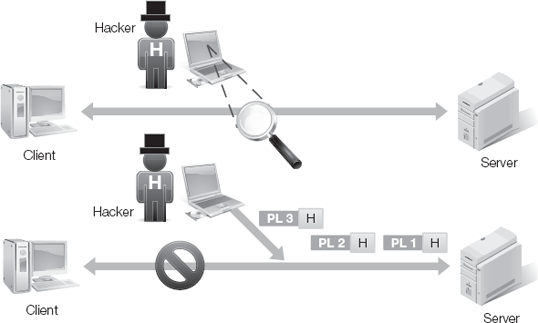
Man-in-the-middle (MitM) attacks occur when a hacker intervenes in a communication session between a client and a server. The attack usually involves fooling or tricking the client into initiating the session with the hacker's computer instead of with the intended server (Figure 4-10). This form of attack is also called interception attack, proxy attack, and monkey-in-the-middle.

Figure 4-10. Man-in-the-middle attacks fool clients into initiating sessions with the hacker instead of the target server.
MitM attacks involve a pre-attack element, in which the client is given false information that leads the client to request a session with the hacker's computer rather than the real server. The hacker can accomplish this using one of several methods:
ARP spoofing—ARP is a non-authenticating broadcast query service that requests the MAC address from a system using a specific IP. If a hacker running an ARP spoofing tool sends a false response to the requester before the real response returns, then the sender will use the false MAC address. Subsequent frames go to the rogue MAC address, which the hacker's computer uses. ARP spoofing must occur within a subnet.
MAC spoofing—The hacker's computer uses a server's MAC address; while the server is flooded, the hacker's system receives traffic instead of the intended server. MAC spoofing must occur within a subnet.
DNS poisoning—A hacker compromises a DNS server and plants false FQDN to IP mapping records. The DNS source will feed subsequent user queries false data.
DNS spoofing—DNS is a non-authenticating query service that requests the resolution of a FQDN into its related IP address. A hacker hosting a rogue DNS spoofing tool can send back false DNS responses.
ICMP redirect—On subnets with multiple routers, ICMP redirects can cause a host to alter its routing table. This attack could redirect traffic along a different route than the default, expected, or optimal one.
Proxy manipulation—A hacker re-configures a client's proxy configuration. Requests for services go to the hacker's system that acts as a MitM proxy.
Rogue DHCP—A false DHCP server can provide IP address configuration leases for a unique subnet and define the default gateway since the hacker's computer acts as a MitM router/proxy.
Rogue access point—A hacker configures a rogue wireless access point similarly to the real authorized access point that can fool users into connecting, which then serves as a MitM proxy.
Defenses against MitM attacks include IDS and IPS solutions that monitor for common network abuses or abnormal network activity. Additionally, strong multifactor authentication and mutual authentication can reduce the success of MitM attacks.
Session hijacking occurs when a hacker is able to take over a connection after a client has authenticated with a server. To perform this attack, a hacker must eavesdrop on the session to learn details, such as the addresses of the session endpoints and the sequencing numbers. With this information, the hacker can desynchronize the client, take on the client's addresses, and then inject crafted packets into the data stream. If the server accepts the initial false packets as valid, then the session has been hijacked.
In a session hijack, the attacker does not directly learn the credentials of the client. If the hacker loses the connection, he will have to look for another session to hijack. The client who lost the session will be aware that the connection was lost, but will not necessarily be aware that the disconnect was a hijack attack.
Session hijacking sometimes employs DNS spoofing, poisoning, ARP spoofing, ICMP redirects, and rogue DHCP to alter the route or pathway of a session. The hacker uses this pathway alteration to make the session hijacking attack easier by forcing the target session to travel over a more accessible network segment.
Any host that uses TCP/IP without encryption is vulnerable to session hijacking. Even with complex or pseudo-randomized packet sequence numbering, a little eavesdropping is all that is necessary for hackers (or the hacker's tools) to predict future sequence values. The only true protection against session hijacking is encryption, such as a VPN.
Spoofing is falsification of information. Most spoofing is a falsification of the identity of a source. E-mail addresses, MAC addresses, and IP addresses are all easily spoofed. Spoofing tricks a user or a host into believing a communication originated from somewhere other than its real source. This is a common tactic in the transmission of spam. Spoofing impersonates an authorized entity, such as MAC spoofing to bypass wireless access-point MAC filtering.
Spoofing is difficult to prevent and only moderately detectible. Most spoofing detection occurs when you watch normal traffic and look for addressing anomalies. For example, if a switch sees that a specific MAC address as the source address for frames received on switch port #6, then that MAC address appears as the source address for frames received on switch port #9, that's a symptom of MAC spoofing (Figure 4-12). In another example, if a firewall receives a packet on its external interface and the source IP address is an internal LAN address, spoofing could be going on.
Spoofing is something to watch and filter for, but no real or direct prevention of spoofing exists. Additionally, hackers can intercept and modify data already in transit from a real source if it's not encrypted. Thus, spoofed data does not always originate as falsified communications.
Covert channels are hidden, unknown, unique, atypical pathways of information transfer. The channel is covert because it is unknown and unseen. Hackers use covert channels for secretive communications, often to leak data out of a secured environment. Covert channels are insecure pathways of transmission. If the pathway were known, it would be an overt channel and likely blocked, filtered, or otherwise secured.
Two main forms of covert channels exist: timing and storage. A timing channel conveys information through timed and synchronized activities. A few potential examples of timing covert channels include:
Blinking lights to distribute information in Morse code.
Manipulating a fan's speed so the higher and lower pitched noise creates binary transmission.
Throttling the bandwidth consumption on an Internet link so that at a specific interval a utilization measurement reads a value below 60 percent as a zero and a value above as a one for binary communications.
A storage covert channel conveys information through unseen or undiscovered storage locations. A few potential examples of storage covert channels include:
The best defenses against covert channels include IDS and IPS, as well as thorough monitoring of all aspects of an IT infrastructure for aberrant or abnormal events of any type. Predicting covert channels is difficult because by their very nature they are unknown and unseen.
To be successful, many exploits and attacks require special access on a private network. Some exploits will function against an Internet facing Web server, but such a server might not directly connect to a private network. If a hacker is unable to find an exploitable vulnerability that gains access or control over the targeted systems, a fall back or final resort option is to launch availability attacks.
An availability attack aims at preventing legitimate access or use of resources to delay or interrupt business. Generally, this is known as denial of service (DoS).
A denial of service (DoS) attack interrupts the normal patterns of traffic, communication, and response. A DoS interferes with timely processing and reply to legitimate requests for resources. A DoS can be of two primary forms: flaw exploitation or traffic generation.
Flaw exploitation DoS attacks take advantage of a programming bug, flaw, or convention. The DoS exploit results in the system freezing, crashing, rebooting, or failing to respond to external communications. You can mitigate flaw exploitation DoS attacks through the application of a patch and the use of an IDS or IPS system. Once you apply a patch, the DoS will no longer be effective. Flaw exploitation attacks are usually specific to a software version.
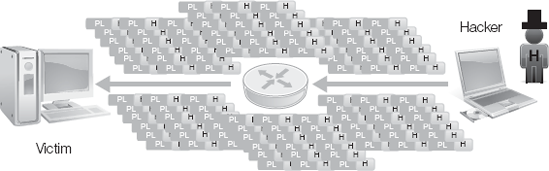
Traffic generation DoS attacks flood a target with traffic (Figure 4-14). The traffic consumes available bandwidth and processing, preventing legitimate communications. No patches exist to mitigate traffic generation DoS attacks. Instead, traffic filtering is the only effective response. Upstream filtering, however, is more effective than edge device filtering.
Upstream filtering occurs when a parent network, usually the ISP, provides filtering for traffic before it enters the child network to which individual and business customers connect. Edge device filtering will prevent malicious traffic from entering the private network, but not prevent a successful DoS. Only upstream filtering will reduce or eliminate the DoS traffic and allow legitimate communications to continue.
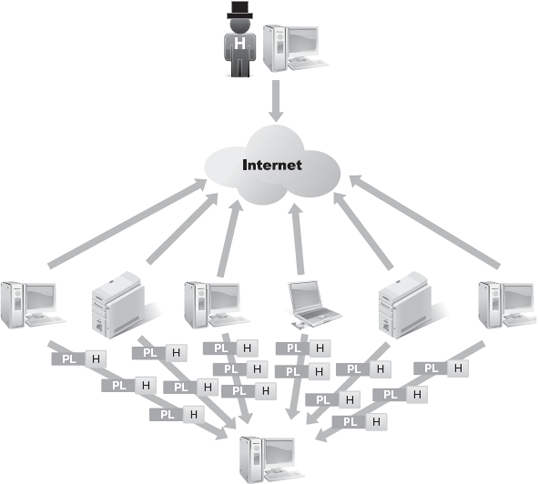
Distributed denial of service (DDoS) attacks advance DoS attacks through massive distributed processing and sourcing. The foundation of DDoS is the agent, bot, or zombie. Agents, bots, and zombies are malicious code implanted on victim systems across the Internet. These mobile agents may create their own peer-network interaction or connect into a public communication medium, such as an Internet relay chat (IRC) channel. The resultant network is known as a botnet army or zombie army.
The hacker remotely controls the botnet and directs it to perform various malicious activities, including flooding attacks, against selected targets. Generally, the main targets of the botnet are known as primary victims, while the compromised systems hosting the botnet's agents are known as secondary victims. This form of DoS is distributed because the bots are disseminated across numerous secondary victims and the resulting attacks originate from a plethora of source vectors.
A hacker distributes the bots, agents, zombies to many secondary victims located throughout the Internet. The bots then connect back to some form of communication server, commonly a chat service like IRC, where they can receive instructions from the hacker. Once the hacker sends attack instructions, the bots launch attacks against the primary target (Figure 4-15).
A botnet can perform a wide range of malicious actions including flooding, spamming, eavesdropping, intercepting, MitM, session hijacking, spoofing, packet manipulating, malware distributing, phishing site hosting, passwords stealing, encryption cracking, and more.
Several botnets have appeared in the last few years, such as Storm and Conficker, which had an estimated secondary victim base of 75 to 100 million systems.
Defenses against DDoS focus on either avoiding becoming a secondary victim or protecting against primary victim onslaughts. To avoid becoming a secondary victim you should use measures including current antivirus and anti-malware scanning, user behavior modification, firewall filtering, and use of IDS/IPS solutions. Protection against primary victim onslaughts includes firewall filtering, honeypots, and use of IDS/IPS solutions.
Hacker tools include a wide variety of software from mundane native OS utilities to commercial applications to custom coded exploits. Generally, any software put to a malicious or unauthorized (according to company security policy) use is a hacking tool.
Hacking tools perform hacking activities. All of the exploit concepts mentioned in this chapter are possible through a wide variety of hacking tools and utilities.
No master list of hacker tools exists to search for or block access to protect IT systems. Just about every legitimate program can be put to some illicit task. To defend generally against hacker tools, consider using a white list restriction system.
A white list restriction system incorporates a list of software executables authorized for use. A user can launch any application on the list. You block from running all executables not on the list. A white list cannot focus on just authorized filenames; this process uses a hash value, as well, to prevent easy bypassing of the limitation through simple file renaming.
In addition to white listing, you can reduce the threat of hacking tools through limiting Internet downloads and file exchanges, controlling use of portable storage devices (especially those used on external systems), filtering e-mail attachments, installing IDS/IPS solutions, and providing user education.
Social engineering is the art of manipulation and exploitation of human nature. Social engineering is the craft of manipulating people into performing tasks or releasing information that violates security. Social engineering is an exploit that can almost always be performed against a target organization. This is due to the presence of humans. Humans are the primary targets of social engineering.
Humans are the weakest link in most security solutions because humans are the only element in an organization with free will. Every other element can only perform within its programming and design. In addition, humans can be tricked or fooled, while hardware and software can only perform in accordance with its design and programming.
Social engineering can take place over any communication method, including face-to-face, telephone, e-mail, IM, and Web sites. Social engineering may focus on extracting information from a target or convincing the target to take action that alters the security status of a host or network.
Many social engineering attacks stem from some form of relationship, from initial and casual to business professional to long-term and highly developed. The more in-depth and long-term the relationship, the more leverage the hacker can exploit to turn, trick, or abuse the target.
Social engineering can employ a wide range of techniques, including impersonating a position of authority, reciprocating favors, using social validation, and creating urgency through scarcity. Often these attacks become more successful if the hacker can impersonate an insider.
Gaining access to inside information is often the first element of a social engineering attack. Dumpster diving, using reconnaissance, and cold calling are techniques to learn about the internal culture of the target. As a hacker learns more and more terminology, processes, organizational hierarchy, policies, events, gossip, social occurrences, calendars, project scheduling, and so on, the more he is able to simulate being an insider. Once a hacker fools a target into believing that he is just another employee, the initial attack is successful. With the standing gained, the hacker manipulates the target into revealing more internal information, reconfiguring systems, or downloading tools from questionable Internet locations.
Social engineering may be the first wave of hacker attacks or could be the last resort fallback plan if attempts to perform logical intrusion or physical burglary fail. Some hackers are naturally gifted at social engineering, while others must practice to obtain workable competency at the craft. These skills of social engineering are not unique to this unethical activity; instead they are the same skills most people use in normal social situations when trying to get their way, convince someone to go out on a date, ask for help, improve social status, get out of trouble, lead a group, sell and market, create advertising, and so on. The difference is that hackers have an unethical goal in their use of these skills.
Social engineering, primarily attacks against people, is invulnerable to typical IT countermeasures. Instead, the best defense against social engineering is thorough user training and awareness. Once personnel are aware that they are, have been, and will be targets of attack, they can adopt a slightly suspicious and cautious outlook. Employees should skeptically evaluate any activity, question, interaction, or relationship that seems odd or out of place.
You can help reduce the threat of social engineering by using security policies that employ information classification with related restrictions on communication methods. If you limit the communication channels that specific classes of information traverse, you will reduce information leakage caused by social engineering. For example, you restrict the use of passwords over the telephone or by e-mail, then anyone who requests a password will be obviously attempting to violate security. Employees should be trained to report all such requests to the network security staff.
Hackers are consistently seeking to take advantage of anyone or any system not prepared or properly secured. Understanding the various means of attacks hackers commonly employ directly improves awareness and overall network security.
Hackers often seek monetary gain through attacks against individuals and organizations. Hackers can be employees or outsiders. Compromising situations are not limited to hacker attacks, but can also include accidents, oversights, hardware failure, rapid growth, and severe weather. Hacker tools and techniques include malicious software, exploiting wireless connections, eavesdropping, replay, insertion, fragmentation, buffer overflow, XSS, man-in-the-middle, session hijacking, spoofing, covert channels, and the availability attacks of DoS and DDOS. You should take action to restrict or limit hacker tools and use caution and training to avoid social engineering.
Other attacks and techniques than those listed here are likely by hackers. This chapter offers a generic description of the hacking process, not a definitive or exhaustive examination. However, from this foundation, you can develop a greater understanding of hacking and the threats posed by hackers (as well as other sources of threat and risk), leading to improved security design, policy, and implementation.
Adware
Alternate data stream (ADS)
Arbitrary code execution
ARP spoofing Banner
Banner grabbing
Blog
Botnet army
Buffer overflow
Chip creep
Cluster
Cold calling
Command shell
Contract workers
Covert channel
Cross-site scripting (XSS)
Deterrent
Dialer
Disgruntled employees
Distributed denial of service (DDoS)
DNS poisoning
DNS spoofing
Domain registration
Dumpster diving
Eavesdropping
Enumeration
Flaw exploitation
Flooding
Footprinting
Hierarchical file system (HFS)
Honeypot
ICMP redirect
IDS insertion
Insertion attack
Instant message (IM)
Interception attack
Internal personnel
Internet relay chat (IRC)
Keystroke logger
Leetspeak
Logic bomb
MAC spoofing
Maximum transmission unit (MTU)
Mean time between failures (MTBF)
Mean time to failure (MTTF)
Metacharacter
MITRE
Mobile code
Monkey-in-the-middle
National Institute of Standards and Technology (NIST)
New technology file system (NTFS)
Nmap
Non-authenticating query service
Opportunistic hackers
OS/2
Partition
Phishing
Ping sweep
Playback attack
Port scanning
POSIX
Privilege escalation
Professional hackers
Proxy attack
Proxy manipulation
Pwned
Reconnaissance
Recreational hackers
Redundant array of independent disks (RAID)
Replay attack
Return on investment (ROI)
Rogue access point
Rogue DHCP
Rootkit
Scanning
Script
Kiddie Sector
Session hijacking
Shell code
Slack space
Social engineering
Spam
Spyware
SQL injection
Static electricity discharge (SED) or Electrostatic discharge (ESD)
Traffic generation
Trapdoor
Trojan horse
Unpartitioned space
Upstream filtering
URL injector
USENET newsgroups
Virus
War dialing
War driving
Whois
Worm
Wrapper
Zombie army
All of the following are common or likely motivations for a hacker except which?
Ego boost
Social validation
College credit
Challenge
Adventure
Which of the following potential hackers represents the greatest threat because they likely already have physical and logical access to a target?
Consultant
Competitor
Overseas black hat for hire
Customer
Recreational hackers under 16 years old
Which of the following is not a significant threat to availability?
Natural disasters
Hardware failure
Accidental spills
Stateful inspection filtering
Lack of proper training
Which of the following is not a potential consequence of a malware infestation?
Corruption of data
Leaking of confidential information
Crashing of systems
Identity theft
Improved throughput
What is the primary difference in network security between a wired connection and a wireless connection to a private LAN?
Inability to access all network resources
Lack of realistic throughput
Needing to be inside the building to access the network
Ability to support encrypted sessions
Support for multi-factor authentication
Most exploits are based on the existence of which?
Encryption
Filtering
Humans
System anomalies
Synchronization
What is the first stage or step in the hacking process?
Scanning
Penetration
Enumeration
Privilege escalation
Reconnaissance
Which form of attack captures authentication packets to retransmit them later?
Insertion
Hijacking
Replay
Interruption
Spoofing
Which form of attack can potentially evade an IDS?
Virus
Insertion
Man-in-the-middle
ARP poisoning
Rogue DHCP
Which exploit takes advantage of variable MTUs?
Spoofing
Hijacking
Covert channels
DoS
Fragmentation
Which form of attack submits excessive data to a target to cause arbitrary code execution?
Buffer overflow
DDoS
Insertion
Interruption
Fragmentation
Which attack exploits a Web site to poison its dataset so future visitors receive corrupted content?
Cross-site scripting
Proxy manipulation
Rogue DHCP
SQL injection
Hijacking
Which attack uses rogue DHCP, ARP poisoning, or ICMP redirect?
Fragmentation
Injection
Man-in-the-middle
Social engineering
Buffer overflow
Which attack is preceded by eavesdropping?
SQL injection
Hijacking
IDS insertion
Covert channel
XSS
Which attack is based on the impersonation of a legitimate host?
DoS
Replay
Fragmentation
Spoofing
Hijacking
Which method of communication is unseen, unfiltered, and based on timed manipulations?
Buffer overflow
Man-in-the-middle
DDoS
Covert channel
IDS insertion
Which form of attack is based on malware distributed by Trojan horse or worm and that can generate massive levels of traffic toward a primary target from numerous source vectors?
Fragmentation
Hijacking
DDoS
Playback
XSS
Which attack uses non-technical means to achieve results?
Spoofing
SQL injection
Buffer overflow
Covert channels
Social engineering
A hacker writes an exploit to compromise targets due to the presence of which?
A vulnerability
Multi-factor authentication
Sufficient throughput
A bot army
Traffic filtering
What is the primary benefit to network security of knowing hacker attacks and exploits?
Training contract workers
Improved antivirus detection mechanisms
Defending against specific threats
Alterations of network subnet organization
Reduced infrastructure cost