APPENDIX D – INFORMATION RISK CONTROLS
It is often wrongly assumed that a single control of any kind is sufficient to resolve a risk. In fact, it is frequently the case that more than one control is required, and these may often be controls of different types. It is common that a risk may have been reduced by some means, but leaving some level of risk that is shared with a third party before the residual risk is accepted.
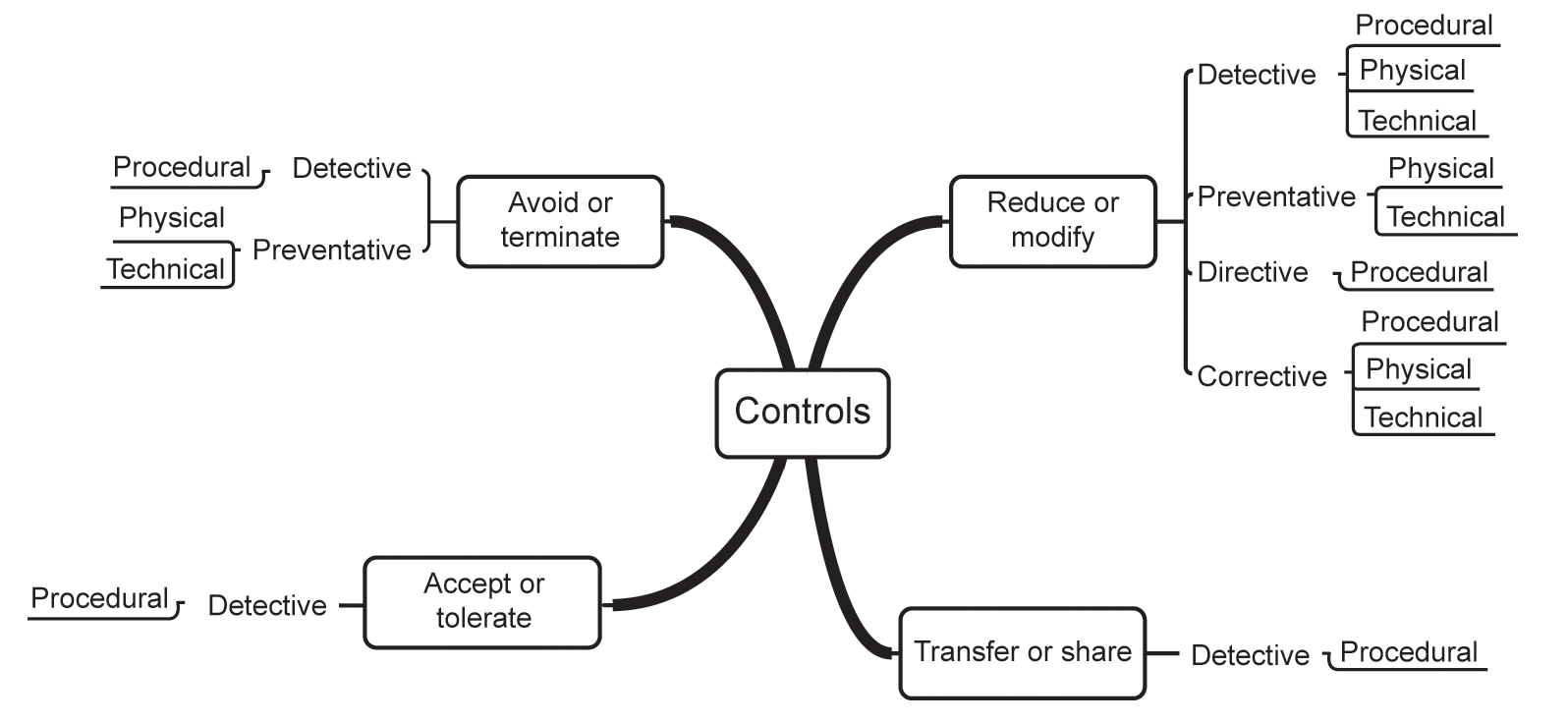
There are three levels of control: strategic, tactical and operational. Figure D.1 illustrates the overall structure of controls.
Figure D.1 Information risk controls
STRATEGIC CONTROLS
Strategic controls come in four flavours:
- Avoid or terminate – avoiding or terminating the risk can mean either stopping doing the activity, in which case there may well be some residual risk, or not commencing an activity, in which case the organisation may be left with an unsolved problem that the activity was intended to address.
- Reduce or modify – reducing or modifying the risk involves the application of suitable controls that result in a lower level of risk once they have been applied. There may remain some residual risk following treatment.
- Transfer or share – transferring or sharing the risk moves treatment of the risk to a third party who will take action if the risk materialises. Insurance is a common form of risk transfer. However, the organisation that transfers the risk still retains ownership of it.
- Accept or tolerate – when all other options have been discounted, acceptance of the risk is the final choice. This will also be the case when any of the other three options result in some degree of residual risk.
It must be remembered, however, that ignoring a risk is not the same as accepting it, and should never be an option.
TACTICAL CONTROLS
There are also four types of tactical control:
- Detective controls – detective controls are intended to identify and provide some form of alert when a threat is actually having a detrimental effect on an information asset or may be about to do so.
- Preventative controls – preventative controls are intended to stop a threat from having a detrimental effect on an information asset before the threat has any opportunity to do so.
- Directive controls – directive controls are intended to provide instruction on how to stop a threat from having a detrimental effect on an information asset or how to avoid activities that could initiate a detrimental result.
- Corrective controls – corrective controls are intended to prevent a threat from further detrimental activity, to recover from such activity or to prevent it from recurring.
OPERATIONAL CONTROLS
There are just three types of operational control:
- Procedural or people controls – procedural controls dictate the way in which actions must be taken and include such things as segregation of duties, change control mechanisms and the ongoing monitoring of risk.
- Physical or environmental controls – physical controls protect or change the environment in which information is stored and processed and include such things as locked doors and CCTV systems.
- Technical or logical controls – technical controls cover the technology-related aspects of information risk management and include such things as antivirus software and firewalls.
The following sections list the chief controls suggested by:
- the Centre for Internet Security Controls Version 8;
- ISO/IEC 27001:2017;
- NIST Special Publication 800-53 Revision 5.
THE CENTRE FOR INTERNET SECURITY CONTROLS VERSION 8
A number of organisations have published a list of the 18 most critical security controls. The list is based upon the Centre for Internet Security Controls Version 8. While this is not necessarily a comprehensive list of controls, it does provide a good starting point for organisations that have conducted their risk assessments but are unsure where to begin with risk treatment. The document may be downloaded from: https://www.cisecurity.org/controls/.
- Inventory and Control of Enterprise Assets (includes five sub-controls)
- Organisations should actively manage (inventory, track and correct) all enterprise assets (end-user devices, including portable and mobile, network devices, non-computing/IoT devices and servers) connected to the infrastructure physically, virtually, remotely and those within cloud environments to accurately know the totality of assets that need to be monitored and protected within the enterprise. This will also support identifying unauthorised and unmanaged assets to remove or remediate.
- Inventory and control of software assets (includes seven sub-controls)
- Organisations should actively manage (inventory, track and correct) all software (operating systems and applications) on the network so that only authorised software is installed and can execute, and that unauthorised and unmanaged software is found and prevented from installation or execution.
- Data Protection (includes 14 sub-controls)
- Develop processes and technical controls to identify, classify, securely handle, retain and dispose of data.
- Secure Configuration of Enterprise Assets and Software (includes 12 sub-controls)
- Establish and maintain the secure configuration of enterprise assets (end-user devices, including portable and mobile, network devices, non-computing/IoT devices and servers) and software (operating systems and applications).
- Account Management (includes six sub-controls)
- Use processes and tools to assign and manage authorisation of credentials for user accounts, including administrator accounts as well as service accounts, to enterprise assets and software.
- Access Control Management (includes eight sub-controls)
- Use processes and tools to create, assign, manage and revoke access credentials and privileges for user, administrator and service accounts for enterprise assets and software.
- Continuous Vulnerability Management (includes seven sub-controls)
- Develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure in order to remediate and minimise the window of opportunity for attackers. Monitor public and private industry sources for new threat and vulnerability information.
- Audit Log Management (includes 12 sub-controls)
- Collect, alert, review and retain audit logs of events that could help detect, understand or recover from an attack.
- Email and Browser Protections (includes seven sub-controls)
- Improve protections and detections of threats from email and web vectors, as these are opportunities for attackers to manipulate human behaviour through direct engagement.
- Malware Defences (includes seven sub-controls)
- Prevent or control the installation, spread and execution of malicious applications, code or scripts on enterprise assets.
- Data Recovery (includes five sub-controls)
- Establish and maintain data recovery practices sufficient to restore in-scope enterprise assets to a pre-incident and trusted state.
- Network Infrastructure Management (includes eight sub-controls)
- Establish, implement and actively manage (track, report, correct) network devices, in order to prevent attackers from exploiting vulnerable network services and access points.
- Network Monitoring and Defence (includes 11 sub-controls)
- Operate processes and tooling to establish and maintain comprehensive network monitoring and defence against security threats across the enterprise’s network infrastructure and user base.
- Security Awareness and Skills Training (includes nine sub-controls)
- Establish and maintain a security awareness programme to influence behaviour among the workforce to be security conscious and properly skilled to reduce cybersecurity risks to the enterprise.
- Service Provider Management (includes seven sub-controls)
- Develop a process to evaluate service providers who hold sensitive data or are responsible for an enterprise’s critical IT platforms or processes, to ensure these providers are protecting those platforms and data appropriately.
- Application Software Security (includes 14 sub-controls)
- Manage the security life cycle of in-house developed, hosted or acquired software to prevent, detect and remediate security weaknesses before they can impact the enterprise.
- Incident Response Management (includes nine sub-controls)
- Establish a programme to develop and maintain an incident response capability (for example, policies, plans, procedures, defined roles, training and communications) to prepare, detect and quickly respond to an attack.
- Penetration Testing (includes five sub-controls)
- Test the effectiveness and resiliency of enterprise assets through identifying and exploiting weaknesses in controls (people, processes and technology) and simulating the objectives and actions of an attacker.
ISO/IEC 27001:2017 CONTROLS
Although the primary ISO standard for information risk management is ISO/IEC 27005, it contains no detailed information on suitable tactical or operational controls for risk treatment, restricting itself instead to the strategic level only. Instead, ISO/IEC 27001:2017 provides an annex containing a comprehensive list of 114 separate operational level controls, grouped into 14 categories.
ISO/IEC 27001, 27002 and 27005 may be purchased from the BSI online shop at https://shop.bsigroup.com/.
A more detailed description of the controls can be found in ISO/IEC 27002:2017 in its sections 5 to 18. The categories and their associated controls are summarised below.
A.5 Information security policies (2 controls)
The information security policy controls specify that organisations should define, approve and communicate information security policies to all stakeholders both within and outside the organisation. They also state the need to review these policies at intervals, or if anything changes that might impact on the policies.
Policies for information security | Review of the policies for information security |
A.6 Organisation of information security (7 controls)
This area of controls introduces the need for defined responsibilities within the organisation, along with the segregation of duties in order to prevent misuse and abuse. Interestingly, this area introduces the concept that information security should be considered in all organisational projects, regardless of whether or not they are related to information security.
Additionally, this area deals with the need to address the security of mobile devices and teleworking options.
Information security roles and responsibilities | Segregation of duties |
Contact with authorities | Contact with special interest groups |
Information security in project management | Mobile device policy |
Teleworking |
A.7 Human resource security (6 controls)
This area deals with three distinct topics. Firstly, those controls required prior to employment, including background checks and the employment terms and conditions that relate to information security. Secondly, those controls that apply during a period of employment, including the requirement to adhere to the organisation’s information security policies, the need for security awareness training and the disciplinary procedures. Finally, those controls that apply to any employee’s change of responsibilities or when they leave the organisation.
Screening | Terms and conditions of employment |
Management responsibilities | Information security awareness, education and training |
Disciplinary process | Termination or change of employment responsibilities |
A.8 Asset management (10 controls)
Asset management controls are concerned with the identification of the organisation’s information assets, allocation of ownership of them, their information classification, labelling and handling, their acceptable use and their return when employees leave the organisation.
Additionally, this area specifies controls concerned with the management, transfer and disposal of media such as memory sticks and DVDs.
Inventory of assets | Ownership of assets |
Acceptable use of assets | Return of assets |
Classification of information | Labelling of information |
Handling of assets | Management of removable media |
Disposal of media | Physical media transfer |
A.9 Access control (14 controls)
One of the larger topic areas, access controls require a policy that provides for access to network resources to which users have been authorised, and the registration and deregistration and access provisioning processes. It goes on to cover the ongoing management of user access rights and their revocation or modification.
Additionally, access control covers the access to systems and application functions, password management and the access to privileged system utility software and source code.
Access to networks and network services | |
User registration and de-registration | User access provisioning |
Management of privileged access rights | Management of secret authentication information of users |
Review of user access rights | Removal or adjustment of access rights |
Use of secret authentication information | Information access restriction |
Secure log-on procedures | Password management system |
Use of privileged utility programs | Access control to program source code |
A.10 Cryptography (2 controls)
Cryptography controls include the provision of a cryptographic policy and the process for cryptographic key management.
Policy on the use of cryptographic controls | Key management |
A.11 Physical and environmental security (15 controls)
Physical and environmental controls begin with those for controlling the physical perimeter of premises together with controls for restricting entry to the premises and areas within it, including secure areas such as computer rooms and less secure areas such as loading bays. It also includes the need to protect the premises from environmental threats and hazards.
The controls continue by considering the siting of equipment, the utilities that support it and the processes for removing it from the premises. Finally, they cover the need for clear desks and screens.
Physical security perimeter | Physical entry controls |
Securing offices, rooms and facilities | Protecting against external and environmental threats |
Working in secure areas | Delivery and loading areas |
Equipment siting and protection | Supporting utilities |
Cabling security | Equipment maintenance |
Removal of assets | Security of equipment and assets off-premises |
Secure disposal or re-use of equipment | Unattended user equipment |
Clear desk and clear screen policy |
A.12 Operations security (14 controls)
Operational security controls focus on formal operating procedures, the need for change and capacity management and the separation of systems used for testing from those in the live environment. They go on to cover malware protection, event logging and the need to synchronise system clocks, the management of vulnerabilities and the requirement to restrict the installation of unauthorised software on systems.
Documented operating procedures | Change management |
Capacity management | Separation of development, testing and operational environments |
Controls against malware | Information backup |
Event logging | Protection of log information |
Administrator and operator logs | Clock synchronisation |
Installation of software on operational systems | Management of technical vulnerabilities |
Restrictions on software installation | Information system audit controls |
A.13 Communications security (7 controls)
Communication security controls deal with the provision of security for networks and network services, and in particular they highlight the need to segregate networks carrying different security classifications of traffic.
They continue by describing the need to manage the transfer of information across and between organisations and include electronic communications such as email and social networking and the requirement for non-disclosure agreements.
Network controls | Security of network services |
Segregation in networks | Information transfer policies and procedures |
Agreements on information transfer | Electronic messaging |
Confidentiality or non-disclosure agreements |
A.14 System acquisition, development and maintenance (13 controls)
This area deals both with the requirement for information security specifications to be included in the procurement process and how application services and their transactions passing over public networks require protection.
It continues by examining the need for development rules and change control procedures, technical reviews and secure design principles, whether development takes place within the organisation or outside it. Finally, it covers the security and system acceptance testing to be carried out on all systems.
A.15 Supplier relationships (5 controls)
Supplier relationships are key to many organisations’ day-to-day operations, and consequently the controls in this area relate to security policies and agreements between the organisation and its suppliers. In addition, the controls include the ongoing monitoring of the service delivery and how changes are carried out.
Information security policy for supplier relationships | Addressing security within supplier agreements |
Information and communication technology supply chain | Monitoring and review of supplier services |
Managing changes to supplier services |
A.16 Information security incident management (7 controls)
Dealing with security incidents requires its own set of controls, which include the allocation of responsibilities for the IM team and the reporting of both incidents and weaknesses within the organisation. The controls then focus on how incidents are assessed and dealt with, how lessons are learnt that can reduce future risk, and how the evidence (whether physical or electronic) of an incident should be collected, handled and stored.
Responsibilities and procedures | Reporting information security events |
Reporting information security weaknesses | Assessment of and decision on information security events |
Response to information security incidents | Learning from information security incidents |
Collection of evidence |
A.17 Information security aspects of business continuity management (4 controls)
In this section, the standard considers the controls required for the planning and implementation of continuity of availability of information services, which include BC, DR and the redundant operation of systems.
Planning information security continuity | Implementing information security continuity |
Verify, review and evaluate information security continuity | Availability of information processing facilities |
A.18 Compliance (8 controls)
The controls for compliance deal with legal and regulatory requirements and the protection of essential records, how personally identifiable information is handled and, in cases where cryptography is used, how this is managed to ensure compliance with legislation.
Finally, the compliance section deals with independent reviews of the information security position within an organisation, and how individual parts of an organisation comply with its defined security policies.
Identification of applicable legislation and contractual requirements | Intellectual property rights |
Protection of records | Privacy and protection of personally identifiable information |
Regulation of cryptographic controls | Independent review of information security |
Compliance with security policies and standards | Technical compliance review |
NIST SPECIAL PUBLICATION 800-53 REVISION 5
Although the primary NIST publication on information risk management is Special Publication 800-30, it contains no detailed information on risk treatment or the selection of controls. However, NIST Special Publication 800-53 Revision 5 lists more than 300 separate operational level controls, grouped into 20 categories in its Appendix F, and also maps them against ISO/IEC 27001 controls in its Appendix H. The document can be downloaded free of charge from https://csrc.nist.gov/publications/PubsSPs.html.
The categories and their associated controls are summarised below.
AC Access Control (24 controls)
Policy and procedures | Account management |
Access enforcement | Information flow enforcement |
Separation of duties | Least privilege |
Unsuccessful log-on attempts | System use notification |
Previous log-on notification | Concurrent session control |
Device lock | Session termination |
Suspension and review – Control incorporated into AC-2 and AU-6 | Permitted actions without identification or authentication |
Automated marking | Security and privacy attributes |
Remote access | Wireless access |
Access control for mobile devices | Use of external systems |
Information sharing | Publicly accessible content |
Data mining protection | Access control decisions |
Reference monitor |
AT Awareness and Training (6 controls)
Policy and procedures | Literacy training and awareness |
Role-based training | Training records |
Contacts with security groups and associations | Training feedback |
AU Audit and Accountability (16 controls)
Policy and procedures | Event logging |
Content of audit records | Audit log storage capacity |
Response to audit logging process failures | Audit record review, analysis and reporting |
Audit record reduction and report generation | Time stamps |
Protection of audit information | Non-repudiation |
Audit record retention | Audit record generation |
Monitoring for information disclosure | Session audit |
Alternate audit logging capability | Cross-organisational audit logging |
CA Security Assessment and Authorisation (9 controls)
Policy and procedures | Control assessments |
Information exchange | Security certification |
Plan of action and milestones | Authorisation |
Continuous monitoring | Penetration testing |
Internal system connections |
CM Configuration Management (14 controls)
Policy and procedures | Baseline configuration |
Configuration change control | Impact analysis |
Access restrictions for change | Configuration settings |
Least functionality | System component inventory |
Configuration management plan | Software usage restrictions |
User-installed software | Information location |
Data action mapping | Signed components |
CP Contingency Planning (12 controls)
Policy and procedures | Contingency plan |
Contingency training | Contingency plan testing |
Contingency plan update – Control incorporated into CP-2 | Alternate storage site |
Alternate processing site | Telecommunications services |
System backup | System recovery and reconstitution |
Alternate communications protocols | Safe mode |
Alternative security mechanisms |
IA Identification and Authentication (12 controls)
Policy and procedures | Identification and authentication (organisational users) |
Device identification and authentication | Identifier management |
Authenticator management | Authentication feedback |
Cryptographic module authentication | Identification and authentication (non-organisational users) |
Service identification and authentication | Adaptive authentication |
Re-authentication | Identity proofing |
IR Incident Response (10 controls)
Policy and procedures | Incident response training |
Incident response testing | Incident handling |
Incident monitoring | Incident reporting |
Incident response assistance | Incident response plan |
Information spillage response | Integrated information security analysis team |
MA Maintenance (7 controls)
Policy and procedures | Controlled maintenance |
Maintenance tools | Non-local maintenance |
Maintenance personnel | Timely maintenance |
Field maintenance |
MP Media Protection (8 controls)
Policy and procedures | Media access |
Media marking | Media storage |
Media transport | Media sanitisation |
Media use | Media downgrading |
PE Physical and Environmental Protection (23 controls)
Policy and procedures | Physical access authorisations |
Physical access control | Access control for transmission |
Access control for output devices | Monitoring physical access |
Visitor control | Visitor access records |
Power equipment and cabling | Emergency shutoff |
Emergency power | Emergency lighting |
Fire protection | Environmental controls |
Water damage protection | Delivery and removal |
Alternate work site | Location of system components |
Information leakage | Asset monitoring and tracking |
Electromagnetic pulse protection | Component marking |
Facility location |
Policy and procedures | Security and privacy plans |
System security plan update | Rules of behaviour |
Privacy impact assessment – Control incorporated into RA-8 | Security-related activity planning – Control incorporated into PL-2 |
Concept of operations | Security and privacy architectures |
Central management | Baseline selection |
Baseline tailoring |
PM Programme Management (32 controls)
Information security programme plan | Information security programme leadership role |
Information security and privacy resources | Plan of action and milestones process |
System inventory | Measures of performance |
Enterprise architecture | Critical infrastructure plan |
Risk management strategy | Authorisation process |
Mission and business process definition | Insider threat programme |
Security and privacy workforce | Testing, training and monitoring |
Security and privacy groups and associations | Threat awareness programme |
Protecting controlled unclassified information on external systems | Privacy programme plan |
Privacy programme leadership role | Dissemination of privacy programme information |
Accounting of disclosures | Personally identifiable information quality management |
Data governance body | Data integrity board |
Minimisation of personally identifiable information used in testing, training and research | Complaint management |
Privacy reporting | Risk framing |
Risk management programme leadership roles | Supply chain risk management strategy |
Continuous monitoring strategy | Purposing |
PS Personnel Security (9 controls)
Policy and procedures | Position risk designation |
Personnel screening | Personnel termination |
Personnel transfer | Access agreements |
External personnel security | Personnel sanctions |
Position descriptions |
PT Personally Identifiable Information Processing and Transparency (8 controls)
Policy and procedures | Authority to process personally identifiable information |
Personally identifiable information processing purposes | Consent |
Privacy notice | System of records notice |
Specific categories of personally identifiable information | Computer matching requirements |
RA Risk Assessment (9 controls)
Policy and procedures | Security categorisation |
Risk assessment | Risk assessment update – Control incorporated into RA-3 |
Vulnerability monitoring and scanning | Technical surveillance countermeasures survey |
Risk response | Privacy impact assessments |
Criticality analysis | Threat hunting |
SA System and Services Acquisition (20 controls)
Policy and procedures | Allocation of resources |
System development life cycle | Acquisition process |
System documentation | Software usage restrictions – Control incorporated into CM-10 and SI-7 |
User-installed software – Control incorporated into CM-11 and SI-7 | Security and privacy engineering principles |
External system services | Developer configuration management |
Developer testing and evaluation | Supply chain protection |
Trustworthiness | Criticality analysis – Control incorporated into RA-9 |
Developer-provided training | |
Developer security and privacy architecture and design | Tamper resistance and detection |
Component authenticity | Customised development of critical components |
Developer screening | Unsupported system components |
Specialisation |
SC System and Communications Protection (46 controls)
Policy and procedures | Separation of system and user functionality |
Security function isolation | Information in shared system resources |
Denial of service protection | Resource availability |
Boundary protection | Transmission confidentiality and integrity |
Transmission confidentiality – Control incorporated into SC-8 | Network disconnect |
Trusted path | Cryptographic key establishment and management |
Cryptographic protection | Public access protections – Control incorporated into AC-2, AC-3, AC-5, AC-6, SI-3, SI-5, SI-7 and SI-10 |
Collaborative computing devices and applications | Transmission of security and privacy attributes |
Public Key Infrastructure certificates | Mobile code |
Voice over Internet Protocol – Control withdrawn | Secure name / address resolution service (authoritative source) |
Secure name / address resolution service (recursive or caching resolver) | Architecture and provisioning for name / address resolution service |
Session authenticity | Fail in known state |
Thin nodes | Decoys |
Platform-independent applications | Protection of information at rest |
Heterogeneity | Concealment and misdirection |
Covert channel analysis | System partitioning |
Transmission preparation integrity – Control incorporated into SC-8 | Non-modifiable executable programs |
External malicious code identification | Distributed processing and storage |
Operations security | |
Process isolation | Wireless link protection |
Port and I/O device access | Sensor capability and data |
Usage restrictions | Detonation chambers |
System time synchronisation | Cross-domain policy enforcement |
Alternate communications paths | Sensor relocation |
Hardware-enforced separation and policy enforcement | Hardware-based protection |
SI System and Information Integrity (22 controls)
Policy and procedures | Flaw remediation |
Malicious code protection | System monitoring |
Security alerts, advisories and directives | Security and privacy function verification |
Software, firmware and information integrity | Spam protection |
Information input restrictions – Control incorporated into AC-2, AC-3, AC-5 and AC-6 | Information input validation |
Error handling | Information management and retention |
Predictable failure prevention | Non-persistence |
Information output filtering | Memory protection |
Fail-safe procedures | Personally identifiable information quality operations |
De-identification | Tainting |
Information refresh | Information diversity |
Information fragmentation |
SR Supply Chain Management (12 controls)
Policy and procedures | Supply chain risk management plan |
Supply chain controls and processes | Provenance |
Acquisition strategies, tools and methods | Supplier assessment and reviews |
Supply chain operations security | Notification agreements |
Tamper resistance and detection | Inspection of systems or components |
Component authenticity | Component disposal |
