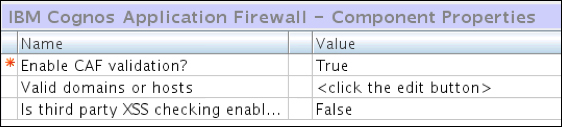
IBM Cognos Application Firewall (CAF) is configured in the Cognos Configuration window to supplement security. If it is enabled, all requests (HTTP and XML) are analyzed, modified, and validated before being processed by gateways or dispatchers. Buffer overflows and cross-site scripting attacks are the most common forms of malicious data. IBM Cognos Application Firewall is enabled by default, and it is recommended against disabling it. The following screenshot shows the configurations of Firewall, where we can enable or disable the firewall:
Every organization, of course, has multiple divisions and departments with a focus on one area. In an environment where Cognos BI has been implemented and all teams do not want other teams to access their data, Cognos BI security permissions are implemented. Permissions and credentials are used to secure the organization's data. Permissions are assigned to users, groups, or roles for content.
For implementing IBM Cognos Security, the users, groups, or roles are selected from either the namespace provided by the authentication provider or from the Cognos namespace. There are five different types of permissions that may be granted or revoked. If both granted and revoked are selected, then revoke/deny will be overridden. The permissions are explained as follows:
- Read: With this permission granted, properties for content may be viewed
- Write: With this permission granted, users can modify the properties of an entry, create entries in a container, delete an entry, and modify report specifications
- Execute: Users with this permission granted can process/run the entry
- Set Policy: Users with this permission granted may read and change the security options of an entry
- Traverse: Users with this permission granted can access the contents of a folder but cannot change or run anything
Users must have the Traverse option set in order to see the entries in a folder. Inheritance to child entries in the Cognos connection is also supported, and is a core feature for security implementation. Assign a read, write, and execute permission for a Cognos group or role, and assign that group or role the required permission to run, execute, or modify the content. The following screenshot shows items included in the built-in Cognos namespace:
In the preceding screenshot, you can see the built-in Cognos roles along with a self-created folder.
