Chapter 11: CISO
In this chapter, you will learn what a chief information security officer (CISO) is and the average salary range for this career in the US. Additionally, you will learn about the options for career progression and learn common interview questions for the role.
In this chapter, we will cover the following topics:
- What is a CISO?
- How much can you make in this career?
- What other careers can you do?
- Common interview questions for a CISO career
What is a CISO?
A CISO is a leader who is responsible for driving the information security program of an organization. Being a CISO is more than just understanding information security technologies and how the systems work together. It also involves understanding the business, including how the company operates, its regulatory and compliance environment, and its evolving external threat landscape.
As you can see, at this level in the organization, you require more than just technical expertise to be successful; you also need to have mastered working with the business and its different stakeholders, along with external parties from vendors to regulators.
The core aspect of any CISO's role is to shape the company's information security program. However, before you can do that, you must understand the organization's people, processes, and technology, and pair it with leadership, culture, and strategy. You need to be able to use this strategy to inform, communicate, and coordinate how you are going to achieve this across the different parts of the business.
How much can you make in this career?
The CISO compensation range greatly depends on the locality of the role, industry, and organization size. I have seen salaries ranging from $150,000 to $2.5+ million in total compensation, with many salaries averaging between $350,000 and $450,000. At this stage in your career, salaries start to separate into multiple buckets to include base compensation, bonuses, restricted stock units, company stock, and other items designed to tie compensation to the company's performance. Another form of payment is vested rewards such as stock or stock options, which are granted based on longevity with the company.
What other careers can you consider after becoming a CISO?
A career as a CISO means that you have mastered the ability to understand the business, its risk drivers, and its vulnerabilities, and you can design mitigation programs around it. CISOs have a broad offering of careers to consider, including board advisors, other CxO roles, consultancies, vCISOs (either virtual or fractional CISOs), and more. Sometimes, CISOs will leave their positions at mature companies and go back to start-ups as head of information security due to the potential upside of joining an early-stage start-up before it becomes public or acquired.
Common career questions for a CISO
The following is a list of interview questions that could prove useful in preparing for a CISO interview:
- Why are you in cybersecurity?
While this might seem like a simple question, part of being at the leadership level is being able to easily communicate with stakeholders and other leaders who might not understand how these terms relate to them in the organization.
Cybersecurity is the space of protecting organization assets (such as data, processes, and infrastructures) in digital form from unintended actions that affect the confidentiality, information, and integrity of those assets. It is often considered a subset of information security, which also includes the protection of information in analog form.
- What is a threat and what is a risk?
A threat is something that has the potential to negatively impact an organization. These can range from a variety of different sources, including natural disasters (such as hurricanes, earthquakes, and floods), threat actors (an individual or group that wants to impose damage or harm to a person or organization), or other categories such as economic and regulator impacts to an organization. A risk is a function of that threat, exposure to that threat, the likelihood of occurrence, and any response or lack of response to the threat.
- How do you measure risk as a CISO?
First, to be able to measure risk, you must be able to define it. Risk is the potential for something to affect an organization or business. This can be both positive and negative. Usually, risk is defined as a function of the potential impact of adverse events times the likelihood of that event. Ryan Leirvik mentioned in his book, Understand, Manage, and Measure Cyber Risk, that technology is inherently flawed because it is created by humans, and humans create technology.
I would like to make a calculation of risk from another field of study, as it is more inclusive of all the elements that we need to think about:

Figure 11.1 – Risk and it relations to its variables
A vulnerability in technology is the first element of risk that a CISO will measure. One of the ways to measure the size of a vulnerability is by using the Common Vulnerability Scoring System (CVSS) score (https://nvd.nist.gov/vuln-metrics/cvss). This uses Common Vulnerabilities and Exposures (CVE), which is a list of publicly disclosed computer security flaws. The CVSS score uses several aspects of the vulnerability to produce a standardized score. Please refer to the CVSS calculator at https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator. The following diagram shows the elements used to calculate it:

Figure 11.2 – CVSS score matrix (Source: https://www.balbix.com/app/uploads/CVSS-Score-Metrics-Blog-e1592596353700.png)
As a CISO, the vulnerability is just one aspect of the overall calculation; the threat of that vulnerability impacting the organization (or the hazard) or its likelihood of impacting the organization is next. As we translate this to cybersecurity, we need to think about how a vulnerability, which requires physical access, can only impact one machine and requires knowledge of the COBOL coding language. This might be something that occurs rarely and its impact might be limited. On the other end of this scale is a wormable vulnerability (this requires no human interaction), which is common on a majority of systems and allows threat actors to have full control of the machines. This has a high likelihood/impact rating. This is not world-ending as there are other aspects of the calculation that we can include:
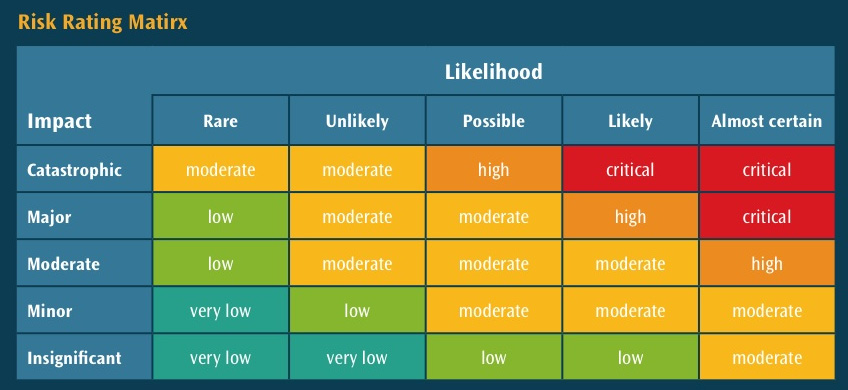
Figure 11.3 – Risk rating matrix (Source: https://focusergonomics.files.wordpress.com/2013/06/risk_matrix.jpg
Exposure is the next aspect of that vulnerability that needs to be considered. For example, do you only have one secret server machine, which is not exposed to the internet, physical access, or connected to the network? This might be an offline machine host, with sensitive information such as crypto wallet keys or PKI root CA certificates. On the other end of the scale, there might be a vulnerability in the base image of your web hosts that are publicly exposed to the internet and scale to millions of machines to handle the increase in web traffic.
The final part of this risk calculation is your response to the situation. In terms of cybersecurity, this could be things such as compensating controls (for example, firewalls, network segmentation, hardening standards, and more), incident response (IR)plans to initiate additional changes, or control of the environment to minimize the effect on the environment. These actions will help reduce, minimize, or eliminate the vulnerability and/or any potential exposure to it.
This is just a simple way to calculate it, but these calculations and any corresponding monetary valuation of the risk will vary based on your knowledge of the environment, the assets, the impact on the business, and exposures.
- How would you evaluate or develop a new security program at a new organization?
Your approach could be to use something such as a strengths, weaknesses, opportunities, and threats (SWOT) analysis or a threat model either at the organizational level or even at a particular departmental level. I would look at the organization starting with the business mission, understanding the people and processes currently in place from the business, and how they function to generate and produce results for the organization. Then, I would start to look at internal and external factors that could be a threat to those businesspeople/processes (these could range from inside threats to external threat actors or even regulatory and compliance). The following diagram is an example of a SWOT assessment that you might want to consider. In this case, we are considering whether the threat is internal/external to the organization and whether it might have a helpful or harmful impact on the organization:

Figure 11.4 – SWOT analysis example
The following diagram is an example of the outcome of a threat modeling exercise, where you would try to understand the potential threats that might face a specific application or service from an organization:

Figure 11.5 – Threat modeling framework
Before making any technology recommendations for your organizations, consider the existing technologies, current capabilities, and potential capabilities of additional modules, licenses, or features. Additionally, you can do a return on investment (ROI) assessment by adding a new solution to the organization or replacing the existing software with a unique solution. Do not forget to think about the people and processes, how these changes will affect them, and whether any user awareness or user training will be needed as a part of the modification process.
A significant part of the CISO's role is becoming a business enabler. It is not the goal of the CISO to implement security for the sake of security; it focuses on the business mission. As you think about implementing security technologies or solutions, you have to think about the people and processes involved, the risk that it helps mitigate, the residual risk that is left over, the user or customer friction introduced by the solution, and the value that it adds to the business in the long run. The value or ROI that the solution adds to the company must outweigh the user friction and your ability to mitigate risk to the business. Without this buy-in, end users in the company might not adopt or actively work to circumvent any of the implemented solutions. Alternatively, they might create the business case to their leaders that it is slowing them down too much and costing the business more money than the risk is mitigating. Situations at this stage end up getting resolved by the business leader with the most political capital and value to the business.
- What are your views on a CISO focused on the first line of defense (security operations) versus a CISO focused on the second line of defense – GRC (governance, risk, and compliance)?
Depending on the organization's business mission, the role of the CISO can differ. As a start-up, a company will usually not have a CISO as its first couple of employees. Usually, the founders will try to do as much as they can on their own before potentially hiring someone who can help them build the company's structure, and most of the time, they will start with IT first. The IT engineer might implement some security technologies to build the infrastructure. The growth continues; sometimes, their customers, their investors, or their industry start to require more structure around regulations and compliance.
As you can see, based on this growth path, in the beginning, organizations might start with CISOs with a GRC focus and a secondary focus on security operations. As the security program is built and the program matures, the direction of the CISO begins to shift away from the GRC focus toward starting to build out the rest of the security program, including operations (identification and detection), response, and recovery.
Once the program has been built, there is an ingrained conflict of interest regarding what prioritizes a security program – operations versus governance. This conflict of interest is very similar to IT versus security, where IT focuses on the availability of the equipment, and security is focused on the confidentiality of the program. In this case, GRC focuses on ensuring that the rules are followed, and there isn't too much risk, while operations are trying to collect signals and logs on the users, compute resources, and applications to ensure that there isn't any malicious activity. Sometimes, the amount of data being collected, the speed, or how things are being done in order to support the business might collect too much data in the logs or deploy things without following the policies and procedures. Once organizations get to this size or maturity, the CISO might be in charge of operations while reporting to a CIO/CEO or other CxO, and second-line functions such as GRC and audit might report to another CxO.
For more information on the security line of defense, please visit https://www.isaca.org/resources/isaca-journal/issues/2018/volume-4/roles-of-three-lines-of-defense-for-information-security-and-governance.
- What are some of the cybersecurity frameworks that you're familiar with? Which one is your favorite and why?
This helps you to show knowledge of the different frameworks within the industry, and whether you, as a candidate, are comfortable with one of the frameworks that the organization is already using. While it is not impossible to introduce a new framework to an organization, the time required to educate all the stakeholders on getting up to speed could potentially be spent elsewhere. One example is the NIST Cybersecurity Framework (https://www.nist.gov/cyberframework), which allows you to easily communicate what is needed to the leadership and acts as a Rosetta Stone to other commonly used frameworks such as the ISO 27001 (https://www.iso.org/isoiec-27001-information-security.html).
- What are some of the key components that your third-party risk management program should address?
Some of the key components that should be addressed are the products and systems (both off the shelf and open source), the custom applications built by the third party, the cloud services and shared responsibility, and the third-party consultants.
- As a CISO, what are some ways that you can use to help map business goals to security decisions for a broad range of stakeholders?
Some of the techniques you can use are tabletop exercises around risk management, informal meetings, and enterprise architecture frameworks such as the Zachman Framework, the Federal Enterprise Architecture Framework (FEAF), and The Open Group Architecture Framework (TOGAF).
- Tell me about a time when you had to modify an existing security policy and why you had to make the adjustment.
One example could be to determine that the current password policy of the organization did not require long, complex passwords. However, ultimately, this led to privilege escalation and lateral movement in a prior data breach. As the CISO, you then implemented a new policy that required long, complex passwords and that required the use of two-factor authentication, which helped mitigate future attacks.
- Tell me about an audit you went through and the outcome.
Years ago, I worked in a consulting (virtual CISO) role at a healthcare organization that underwent an audit that discovered multiple vulnerabilities in the endpoints and some of the web servers. We identified that the critical vulnerabilities in the endpoints were caused by poor patch management and a lack of an antivirus solution. This was coupled with poor password management and open network shares of sensitive data. I worked with their team to implement new policies for passwords, change management, and data security. The network shares were locked down and sensitive data encrypted. The endpoints were also hardened against attacks. During a follow-up audit 6 weeks later, the auditors identified only a few minor security issues remaining.
- Can you tell us about your leadership style?
For this question, the organization is assessing your capabilities to empower your team and delegate appropriately. The worst executive to hire is someone who wants to micromanage everything.
Personally, I combine multiple leadership styles, such as coaching, delegation, visionary, servant, and being emotionally supportive. My approach focuses on setting a high-level objective for the team and then providing them with the space to be creative and play to their own strengths to meet or exceed the objective. I couple this with supporting the team as needed. The result of this approach has been team members who consistently exceed the key performance indicators (KPIs) and team members who have invented a new technology that has generated more revenue for the organization.
- How do you handle situations where you have to tell someone "no," particularly when they don't report to you?
One of the challenges of being a CISO is that, often, you need to be able to collaborate with stakeholders across the organization, some of whom might not be directly reporting to you. How you deal with these situations is a critical aspect of your ability to collaborate and resolve potential disagreements in differing approaches. Would you work through the no with that individual to understand their points of view? Would you escalate the situation to their peer on your level to influence them to have their stakeholder comply? Or would you potentially come to a compromise in approach with that stakeholder because it was the most efficient way to tackle the situation?
Rather than directly saying "no" as it relates to protecting the organization's risk, our compliance posture is saying "while doing xxx seems like an effective approach, I would ask you to consider xxx."
The only time I would say "no" is when something is deliberately unethical or illegal, and I would remove myself from the situation.
- Can you share an experience where you had to collaborate with stakeholders across the organization to implement a security risk management program?
This question is assessing your ability to successfully champion security initiatives across the organization.
An example for me is an organization I worked with that had suffered a ransomware attack. I was brought into the organization following the attack and worked with stakeholders across the organization to design, build, and implement a new security risk management program. Key parts of this new program included better detection and response of incidents, proactive security controls, an organization-wide security awareness training program, scheduled risk assessments, and new security policies. A key aspect of getting buy-in across the organization for this initiative was interviewing each stakeholder to identify what was critical to their team and then identifying the commonalities among teams, along with building out an implementation roadmap that implemented the most critical items first.
- How do you train your teams?
Typically, I assess any skill gaps of my team members based on the role and the needs of the organization. Then, I schedule the more traditional training programs. In some instances, the team will need just-in-time training. For example, if a major ransomware attack hits the organization and it could have been detected and responded to faster, I will work to train the team in the latest detection and response best practices and work with them to identify any additional security controls that we could implement to protect against similar attacks in the future.
As a CISO, I would also look to develop a pipeline of potential candidates who might be in different parts of the organization. Developing a security champion program helps you drive security awareness and drive the impact of your initiatives deeper into the organization. A by-product of this is that you now have individuals who are knowledgeable of the various lines of business and are also passionate about cybersecurity. Having security-related topics and training as part of the organizational budget versus department budgets also allows you to provide these security champions with training to help prepare them for potential roles in your organization.
- Are there any new technologies that you plan to implement after coming on board this organization?
This is an open question that is used to determine your ability to think toward the future. For example, you might answer this question with something such as artificial intelligence (AI) and discuss how you plan to leverage AI capabilities to help improve the organization's security posture.
- How would you describe a strong information security program?
A strong information security program is one that has a solid foundation of information security policies and procedures. Your information security program needs to align with the business objectives to empower the business and not block it from operations.
- How do you measure the effectiveness of your information security program?
You should measure the effectiveness of your information security program by its ability to enable the business to improve productivity and security, without negatively impacting the business operations. For example, enable them to securely share information with clients, as it allows them to become more efficient in their communications to drive sales or customer retention. If the program is being measured in terms of effectiveness, I maintain a scorecard to track it. In a large enterprise, it is important to measure and communicate the effectiveness of programs. Additionally, I use metrics and dashboards that are easy for executives to quickly read.
- Let's say you find a development team has numerous unpatched vulnerabilities that are considered high risk. How would you influence those individuals to remediate those vulnerabilities? ~ Ross Young
This question focuses on your ability to influence individuals who are outside your control while also doing it without using authority as a potential driver unless absolutely necessary. You should be able to show those outside the organization why something might be important to them and, in turn, impact the organization. Additionally, you should be able to demonstrate to them why resolving it on their own would be more efficient than letting it wait until later.
- Do you think the size of an organization affects whether security should be outsourced?
Yes; it often costs less to outsource security to a managed security services provider (MSSP) that already has the in-house talent than it is to try and hire full-time employees into a smaller organization. The other advantage of outsourcing is the ability to pull in different specialties when you need them. For example, if you need specialists that can conduct advanced malware analysis, it is usually more cost-effective to leverage the existing talent in your third-party service provider.
Larger organizations also outsource, but often, they will have internal security teams.
- Tell me about a top executive decision you have made in the past, the circumstances around the decision, and the outcome of that decision.
As an executive, I had to determine the best way to continue scaling the organization while needing to reduce the department's overall spending. I made the difficult decision to remove some of the contract workers we had and temporarily spread their workload around, including assigning some to myself, for a short period of time.
- Can you describe zero trust to a non-technical stakeholder?
Zero trust is a concept that assumes attackers are already within your network and endpoints. To explain this to a child (or a non-technical stakeholder), I would mention it in the old way of thinking, "Would you trust me with all of your candy because your mom let me in the house?" I would then explain the risk associated with this is that I might take all of your candy and not give you any of it. With zero trust, even though your mom let me inside the house, you would still ask me questions before allowing me access to any candy, and you would have each type of candy segmented from the other types, so I would be unable to get all of your candy in one try.
- How does compliance affect your decision-making process?
Compliance will drive the security program for the organization based on the industry. For example, if the organization is in healthcare, the Health Insurance Portability and Accountability Act (HIPAA) of 1996, the Health Information Technology for Economic and Clinical Health (HITECH) Act, which was enacted as part of the American Recovery and Reinvestment Act of 2009, and the Health Information Trust (HITRUST) Alliance are key considerations for compliance, which we will need to address across the organization.
- What do you define as the key attributes every CISO should have?
Some of the key attributes I think every CISO should have are effective communication skills, adaptability, effective negotiation skills, active listening skills, and the ability to collaborate effectively with other stakeholders across the organization.
- Give me an example of how you balance the cost of your information security program.
Typically, I start with the available budget, review the security controls we need to implement, work with the team to identify the higher-priced options and cost-effective options for controls, and then consider the value of each solution. We conduct a trade-off analysis to determine what we can implement and through what period of time.
Additionally, by tying the security program to business enablement, we can work with other lines of business/departments to enable their own initiatives through the security program and have them sponsor a part of the budget for their solutions.
- What do you see as some of the emerging risks that enterprises will face?
At the time of writing, some of the emerging risks that enterprises will face include the increased use of AI in attacks, the increase in ransomware-as-a-service operators, the increase of cybersecurity insurance policy premiums or the lack of insurability, quantum computing and its ability to break current encryption algorithms, and cybersecurity attacks from space assets.
- How would you handle a situation in which all your critical systems have been encrypted by a group of hackers? Describe the steps and decisions that need to be made.
Firstly, I wanted to recommend remaining calm in situations such as this to ensure that you are properly considering all the aspects of the situation. I would recommend that I let the system owners verify the health of all the mentioned systems to see how they might be potentially impacted. It should be pretty obvious if the machines or storage systems of these systems are encrypted.
If something seems off, it is time to spin up an investigation team, to start gauging the extent of the event. Then, I would start working with the security team to potentially look at the indicators of attack (IOAs), as well as bringing in threat intelligence to start validating chatter that might be on the internet. As the teams start to potentially discover indicators of compromise (IOCs), you will need to start assessing the severity of the potential incident. (More information about IOAs versus IOCs can be found at https://www.crowdstrike.com/cybersecurity-101/indicators-of-compromise/ioa-vs-ioc/.)
Once you have declared the incident, you will want to bring out the IR plan to be able to communicate the status to the business and respond to the incident. Hopefully, at this point, there is a well-defined and tested IR plan. The detection and analysis have already started with the IOAs and IOCs. The next phase would, typically, be focused on the containment and rededication phase. You would not want the threat to spread to other systems to cripple the organization further. This containment and rededication should block off communication to these infected systems. Digital Forensics Incident Responders (DFIR) should clone images from these infected systems to start the DFIR investigation process. Part of any IR plan is to ensure that you are able to continually update business leaders, which might include legal and public relations, on the status of the situation.
Backup and restore is likely the next phase of the response. One of the challenges with the backup and restore phases is that many companies only end up doing backups or partial restores. Often, the complexities of backing up and restoring prevent companies from completely validating the backup and restore. Once you have contained the incident within your system, you should start the restore process.
One of the challenges is that threat actors are aware of this process and have now started to target backup processes in order to corrupt or delete backups.
If the backups are unaffected, you should choose the last authentic backup and start the restore process. Once the restore is completed, you should validate that there are no IOCs in the newly restored system. Additionally, the business will also need to validate the restore to ensure that business functionality is fully restored.
Lastly, it is recommended that a post-mortem is conducted so that the teams can learn lessons from the incident. This helps them to update their system configurations regarding detection, IR, backup, and restore and recovery.
- How do you communicate the business impact of a breach to other executives? Focus on cost and the cost of solutions to mitigate in the future.
In my experience, cost and compliance are the two main areas of focus. I focus on the cost of the attack or breach, followed by the cost of solutions to mitigate a similar attack in the future, and finally, the compliance concerns the organization has.
Another approach you can take is to align your security program to the business mission and demonstrate how security helps drive business revenue. For example, if a particular attestation or resiliency capability can drive sales or customer retention, work with business leaders to demonstrate that ROI.
- How do you empower members of your team in their cybersecurity careers?
I meet with each team member to identify their short- and long-term goals and then identify how I can help each of them within the allotted budget to grow their career.
Using their career drivers, I can work to assign them to projects that align with their career interests and organizational needs. Providing them with ownership over these initiatives allows them to grow in those areas, and they are likely to deliver more value than if they were just assigned to them as part of their role and be of no interest to them.
- How do you balance risk to the business and security controls?
I balance the risks to the business and security control implementation by conducting a trade-off analysis of the risk to the daily business operations of each security control and the risk of not implementing those security controls.
- How do you stay current on legislation that may affect the organization's security initiatives?
In order to stay current on the legislation that might affect the organization's security strategy, I create Google alerts and monitor Really Simple Syndication (RSS) feeds for these topics to ensure that I can see when they are being introduced and the progress they make.
- What would you implement to manage endpoints on the network that do not meet minimum security requirements?
An overarching answer here would be zero trust, but specifically, you could use something such as a network access control (NAC) policy that blocks devices from the network that do not meet minimum security requirements.
- You are the new CISO for a healthcare organization and need to review the policies and procedures of the organization to ensure the organization is compliant with HIPAA and other healthcare laws. What type of security assessment would you perform?
In this situation, you would perform a regulatory compliance assessment.
- What is your elevator pitch?
Everyone needs to be able to summarize the value that they would bring to an organization in a maximum of one or two sentences. For example, mine is "I translate between people and processes and the technology that helps enable those business missions. I use a consultative and coaching approach to drive overall cybersecurity maturity, the strategy needed, and the people development that achieves organizational success."
As you can see, the role of a CISO can vary dramatically from needing to be tactical regarding the different technical threats that an organization might face to being able to interact and help enable the business mission with counterparts in different departments. The CISO needs to have a varying balance of hard and soft skills in order to be successful in their role.
Summary
In this chapter, you learned what a CISO is, the average salaries in the US for a CISO, and common questions you might be asked during an interview.
In the next chapter, you will learn some of the most common behavioral interview questions that are asked in these interviews.
