Password Hacking
Anton Mobley, data scientist at GE Healthcare
Major breaches causing huge financial and brand damage have occurred in recent years. The attackers are varied, including hacktivists, nation‐states, and cyber criminals. The targets and data types breached include Target and Home Depot (personal credit information), Anthem/Wellpoint (personal health information), the US Office of Personnel Management, Booz Allen Hamilton and HBGary (military and intelligence information), and Ashley Madison and Adult Friend Finder (private information). Malware and phishing attacks are typically the focus of cybersecurity professionals, but these breaches pose a secondary risk to enterprises due to credential loss. The credential databases from these breaches often find themselves posted on hacker forums, TOR, and torrents.
Using the 2013 Adobe breach as a case study, enterprise exposure can be modeled as a function of enterprise size and password policy. In October 20134 Adobe announced that hackers had stolen source code for major Adobe products and customer credentials for over 153 million users. The credential database became very easily accessible. Some amount of users in the dataset are likely made up or missing passwords, but the dataset was still one of the largest known credential dumps to date.
The database contained email addresses, encrypted passwords, and a cleartext password hint if the user chose to use one. Note that the passwords were not hashed or salted; they were 3DES block‐encrypted. This implies that a key loss would compromise the entire database; however, the key is not publicly known as of now. Since no salt was used, the same password encrypts to the same encrypted password. The password hints were stored in cleartext, meaning that an attacker can aggregate on an encrypted password to get all applicable hints for the same password. Frequently in the database, password hints such as “work,” “sso,” “outlook password,” and “lotus notes password” are given, implying password reuse, and pivoting off the encrypted password to the set of applicable hints makes guessing the password trivial. Additionally, the passwords were block‐encrypted, meaning that an attacker could breach pieces of passwords and use them to attack other users’ credentials in the database.
To model enterprise exposure, we define an enterprise to be exposed if the following criteria are met:
- The password used by an employee email is the same password used by the employee for a critical type of work function.
- The password can be easily backed out of the Adobe database by aggregating hints on encrypted passwords.
It follows, then, that the probability of exposure for an enterprise of n employees can be modeled as the following assuming that employees are independent and that password reuse rate is independent of the employee password being vulnerable.

Security experts have varying opinions on the rate of password reuse between accounts. Some studies put the rate in the 12% to 20% range,5 but a Princeton study using limited data put the reuse rate at 49%.6 Using previous results in this type of analysis, a rate of Uniform(0.15,0.25) is used for this model.
Modeling the likelihood that a single password is vulnerable to hint aggregation is a bit more difficult. To be able to do this, an understanding of how users choose passwords must be developed. Since many password leaks have happened in the past, we choose a former leak with minimal password restrictions to model the password selection space. We use the 2009 hack of RockYou, a company that developed plugins and widgets for social media sites and from which 34 million passwords were leaked. The aggregated password set (no user information) was taken from https://wiki.skullsecurity.org/Passwords. The parameter for the rate at which a hint is given that breaks a password is chosen as 0.0001. This parameter is unknown, however; this is a very conservative estimate. Typically only 10 to 20 hints are needed before a password becomes easy to guess. This parameter is also a function of the number of people sharing passwords, but for simplicity the point estimate is used. By conditioning on the number of users that share a password and the RockYou password space as the probability mass function of how people choose passwords, we can model the single employee exposure as following:

These results are dependent on the RockYou password space PMF. Taking password policy into account by taking the conditional distribution from RockYou that is compliant with the password policy, the initial set of passwords that a user will pull from comes from a much higher entropy distribution.
A simulation of various password policies and number of matches is run using replacement for the number of matches to a password to empirically estimate the cumulative distribution functions under various password policies. The number of vulnerable passwords—that is, passwords that have a weak hint associated with them, based on the number of people sharing the password and the event that the password is reused—is used to calculate the maximum likelihood estimate and 95% CIs for the single employee's rate of compromise.
Combining the reuse rate distribution with the single‐employee exposure distribution results in a range of outcomes (given in Figure B.14). The solid lines show the MLE of the probability of exposure and the dotted lines show the lower and upper bounds when using the 95% CI results with the low and high values of the reuse rate distribution.
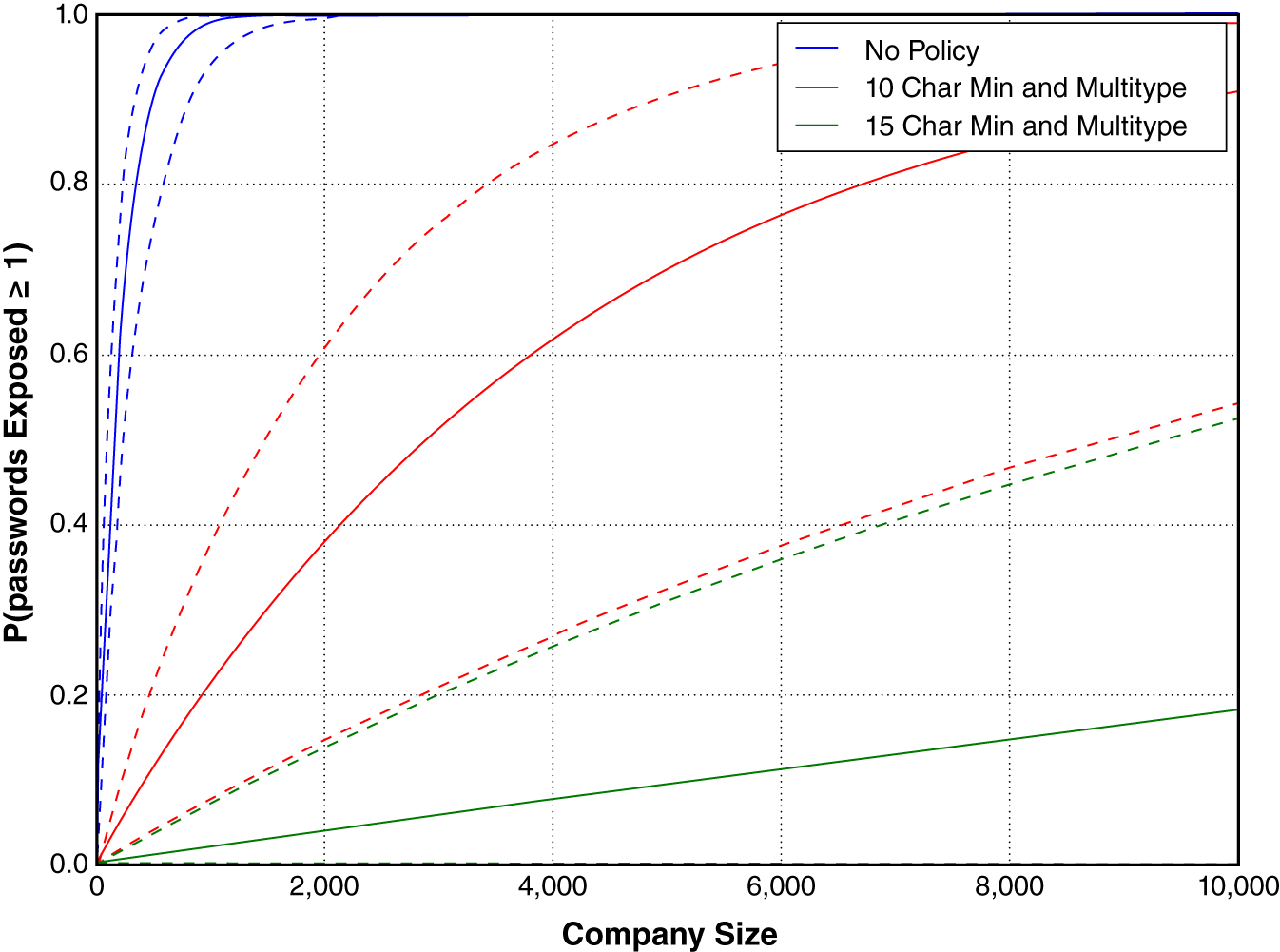
FIGURE B.14 Probability of compromise by company size and password policy
This model gives an idea of the risk of compromised credentials for an enterprise given employee accounts and password policies. There are a few points that can and should be corrected to improve the fidelity of the model, including the following two:
- The password‐hint reuse rate is definitely a function of password complexity; that is, people who choose good passwords don't give them away in hints as often, and this isn't corrected for. Additionally, combining hints makes weak hints very valuable, and this isn't accounted for.
- Forcing a password policy on a user base would likely result in a lower entropy distribution than the RockYou conditional distribution. For example, I imagine an increase in passwords that look like the following if a length/character type policy is implemented: P@ssw0rd123, pr!ncess123, and TrustNo0ne!
Notes
- 4 Brian Krebs, “Adobe to Announce Source Code, Customer Data Breach,” Krebs on Security, October 13, 2013, http://krebsonsecurity.com/2013/10/adobe-to-announce-source-code-customer-data-breach/.
- 5 Keir Thomas, “Password Use Is All Too Common, Research Shows,” PC World, February 10, 2011, www.pcworld.com/article/219303/password_use_very_common_research_shows.html.
- 6 Anupam Das et al., “The Tangled Web of Password Reuse,” paper presented at the Network and Distributed System Security Symposium, February 23–26, 2014, www.jbonneau.com/doc/DBCBW14-NDSS-tangled_web.pdf.
