8
The Contributions of Biometrics and Artificial Intelligence in Securing the IoT
Amal SAMMOUD1, Omessaad HAMDI2, Mohamed-Aymen CHALOUF3 and Nicolas MONTAVONT4
1 SYSCOM, ENIT, University of Tunis El Manar, Tunisia
2 IEEE, IMT Atlantique, Rennes, France
3 IRISA, University of Rennes 1, Lannion, France
4 IRISA, IMT Atlantique, Rennes, France
8.1. Introduction
The Internet of Things (IoT) appears today in many domains such as surveillance, health, agriculture, etc. This new technology is based on connected physical objects able to communicate with one another, and also with other devices. The services offered thanks to the IoT are accessible to a user anywhere at any time (Dhillon and Kalra 2017). Security and protection of user privacy are a priority for this new technology to be fully accepted. To meet these security imperatives, biometrics as well as artificial intelligence could make it possible to provide fairly robust security solutions, well-adapted to the IoT.
In this chapter, we focus on the contributions of biometrics and artificial intelligence in optimizing the security of some IoT applications. In particular, we will study the most reliable security approaches, which are based on using biometric methods and artificial intelligence techniques to ensure safe authentication in the IoT.
This chapter is structured as follows. Section 8.2 presents the security requirements of the IoT and connected objects. In section 8.3, we introduce the principles of authentication based on biometrics. In section 8.4, we present multifactor authentication techniques based on biometrics, especially for the IoT. Section 8.5 details authentication techniques based on biometrics and machine learning. Indeed, in this section we present security approaches using artificial intelligence techniques, such as machine learning, to ensure authentication based on a biometric factor (ECG: electrocardiogram). Section 8.6 describes the challenges and limits of authentication based on biometrics. Section 8.7 concludes the chapter.
8.2. Security and privacy in the IoT
The IoT, which integrates a variety of connected objects to provide services to users, should ensure security services and protect user privacy by ensuring protection against attacks such as identity theft, Denial of Service (DoS), passive listening and unauthorized access to personal and sensitive data (Xiao et al. 2018). With the development of new technologies, the IoT is now faced with intelligent attacks. To resist this type of attack, IoT devices should choose a defense policy and set key security parameters in the protocols used (Xiao et al. 2018). This task can prove complicated, since connected objects often have restricted resources (in terms of calculation, memory, bandwidth and battery), which do not allow them to run the necessary processing correctly in a reasonable time and without compromising lifespan (Xiao et al. 2018). To do this, most security solutions proposed for the IoT demand optimization of the computational load and communication to be used in connected objects.
Security in the IoT happens mainly by protecting connected objects by ensuring mechanisms such as authentication, access control and detection of malware:
- – authentication helps objects to distinguish the source node and to protect against identity theft type attacks;
- – access control prevents unauthorized users from accessing information and data stored on the objects;
- – malware detection makes it possible to protect objects from malicious software such as viruses, worms and Trojans, and so to avoid the consequences that may occur, such as data leaks, exhaustion of the power supply and the degradation of performances.
In this chapter, we focus mainly on authentication protocols intended for the IoT. In this fairly vulnerable environment, authentication mechanisms should consider the vulnerabilities of connected objects by guaranteeing the following security requirements (Lee et al. 2020):
- – user anonymity: ensuring that it is impossible for an attacker to discover the real identity of the user;
- – untraceability: preventing an attacker from being able to follow the user’s activities;
- – mutual authentication: guaranteeing mutual authentication between different communicating entities to verify the legitimacy of each;
- – resistance to diverse attacks: ensuring high-level protection against known attacks such as replay attacks, identity theft attacks and insider attacks.
Among the robust authentication methods that are at the same time adapted to the IoT environment, we find authentication based on biometric methods. This type of authentication can be used in various IoT domains such as health and smart homes. With the development of artificial intelligence techniques such as machine learning, we today find authentication mechanisms based on biometric methods that are processed using machine learning techniques.
8.3. Authentication based on biometrics
8.3.1. Biometrics
The word biometric comes from the Greek words bios (life) and metrikos (measurement). Biometric authentication is a technique that calls on the statistical analysis of biological characteristics. It consists of using physical characteristics to identify a person. These characteristics should be reliable, unfalsifiable, universal, unique for each individual, measurable and recordable.
Biometrics is therefore used in many applications entering a location, accessing work station, etc. It is even beginning to replace classical methods, which depend on what the user knows (password, PIN, etc.) or possesses (key, card, etc.), that can be discovered, modified or stolen.
8.3.2. Biometric techniques
In the main, there are two types of biometric techniques that are used for identification applications (see Figure 8.1):
- – physiological techniques, based on identifying physical characteristics that are unique. This category includes the iris, the retina, handshape, fingerprints, facial features, etc.;
- – behavioral techniques, based on analyzing people’s behavior. This category includes voice recognition, signature dynamic, key stroke dynamic, etc.
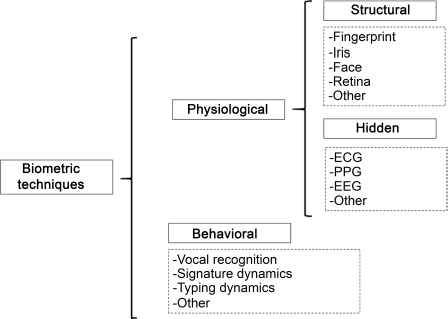
Figure 8.1. Biometric techniques (Cabra et al. 2018)
There is another technique, called biological or anatomical, which is the study of biological traces such as DNA, blood, saliva, urine and odor. Today, this technique is not used in authentication.
8.3.3. The different properties of biometrics
Biometric characteristics making it possible to verify the identity of an individual should have the following properties (Ometov et al. 2018):
- – universality: the biometric should be present in each person;
- – uniqueness: the biometric should differ sufficiently between one person and another;
- – stability: the properties of the biometric should remain invariable throughout the person’s life;
- – collectability: the biometric should be easy to measure in an individual;
- – performance: the biometric should be sufficiently robust, reliable and easy to analyze when it is used to verify a person’s identity;
- – acceptability: use of the biometric should be socially acceptable;
- – identity theft: the biometric should not be easy for an attacker to steal.
Biometric characteristics possess these properties to different degrees as Table 8.1 shows. None of these different biometric characteristics is ideal, but each of them can be taken and adapted to particular applications.
Table 8.1. Comparison of biometric characteristics according to the following properties: universality (A), uniqueness (B), collectability (C), performance (D), acceptability (E) and identity theft (F) (Ometov et al. 2018)
| Biometrics | A | B | C | D | E | F |
| Voice | A | L | A | L | H | H |
| Face | H | L | A | H | H | A |
| Fingerprint | A | H | A | H | A | H |
| Handshape | A | A | A | A | A | A |
| Vein | A | A | A | A | A | A |
| Behavior | H | H | L | L | L | L |
| OCS | NA | L | L | L | L | A |
| ECG | L | H | L | A | A | L |
| EEG | L | H | L | A | L | L |
| DNA | H | H | L | H | L | L |
8.3.4. Operating a biometric system
A biometric system makes it possible to sense biometric information, analyze it and extract characteristic elements from it and compare these with others memorized in a database.
Using a biometric system requires two stages:
- – an enrollment stage (also called a learning stage), which consists of sensing, modeling (constructing a model of the individual) and storing biometric data in the database;
- – a reconnaissance stage, which consists of comparing the new sensing with the assumed model of the individual.
The reconnaissance will differ depending on the mode of identification or verification:
- – identification mode: to guess the identity of the person, the system answers the question “Who am I?”. In this mode, the system compares the signal measured with the models stored in the database. We often speak of a closed problem (each person using the system has a model in the database);
- – verification mode: to verify the person’s identity, the system answers the question “am I the person I claim to be?”. The person proposes an identity to the system and the system verifies that the identity of the person is really the one proposed. We call it an open problem (we suppose that a person who has no model in the database may seek to be recognized).
8.3.5. System performances
It is impossible to obtain a “signature” signal created during verification that is similar to a “signature” signal created at the moment of learning. It is impossible to reproduce original elements identically (an image, an ECG signal, a sound, etc.).
The performances of biometric authentication systems are measured by:
- – FRR (False Rejection Rate): this is the proportion of legitimate users wrongly rejected;
- – FAR (False Acceptance Rate): this is the proportion of users accepted/identified erroneously.
8.4. Multifactor authentication techniques based on biometrics
A robust authentication protocol plays a very important role in guaranteeing the security and privacy of users of the IoT. Today, security protocols based on biometrics are much used to ensure authentication or verification of identity in environments that demand a fairly high level of security such as e-health. One of the most significant advantages of technology based on biometrics is that the characteristics used as identifiers cannot be lost or replaced, and it is very difficult to falsify them. Unlike other authentication technologies, biometric characteristics cannot be forgotten, nor stolen. For example, passwords are easily forgotten, and smart cards can be lost or stolen (Hamidi 2019). On the contrary, using different authentication technologies at the same time (password, smart card and biometric) can only strengthen the level of security.
8.4.1. Multifactor authentication
In general, authentication is the procedure that enables a system (e.g. an IoT device) to verify whether an entity (e.g. another IoT device or even a user via their terminal) is authorized or not to access resources controlled by this system. Authentication methods are based on authentication factors such as the password, smart card and/or biometrics (Figure 8.2). There are two authentication categories:
- – simple authentication, which requires only a single authentication factor (e.g. a password and badge);
- – strong authentication (also called multifactor authentication), which calls on many factors simultaneously (at least two).
In general, a reliable authentication protocol is based on three security factors (Table 8.2):
- – a memory factor (what you know): information that is known only by the user (e.g. passwords and PIN codes);
- – a material factor (what you have): a physical key that belongs only to the user (e.g. smart card or mobile phone);
- – a bodily factor (who you are, biometrics): biometric data are unique for each individual (e.g. voice, fingerprints and ECG).
Table 8.2. Description of authentication factors
| Authentication factor | Advantages | Drawbacks |
| Material factor (token, card, etc.) | A new token can be supplied in case of loss |
Can be stolen A fake token can be sent Can be shared The same person can be registered with different identities |
| Memory factor (password, PIN, etc.) |
Simple and economic method Can easily be replaced by a new one |
Can be guessed Good passwords are difficult to remember Can be shared |
| Bodily factor (biometrics) | Cannot be guessed, forgotten, stolen or shared Offers a higher level of security compared to others | Impossible to replace it |

Figure 8.2. The evolution of authentication methods from simple authentication to strong authentication (Ometov and Bezzateev 2017). For a color version of this figure, see www.iste.co.uk/chalouf/intelligent.zip
In this context, many researchers have developed authentication protocols based on three factors (a password, a smart card and biometrics) to ensure security of communications in an IoT network (Dhillon and Kalra 2017; Ali et al. 2018; Ahmed and Ahmed 2019; Li et al. 2019; Sammoud et al. 2020c).
In fact, authentication protocols based on a single factor (e.g. a password) do not provide reliable authentication (Sammoud et al. 2020c). We also note that the majority of authentication protocols that are based on two factors, memory and material, have not managed to guarantee good resistance to some significant attacks such as identity guessing attacks, insider attacks and password guessing attacks (Sammoud et al. 2020c). To do this, authentication protocols based on three factors have been proposed. They have the objective of improving security of authentication in the IoT.
8.4.2. Examples of multifactor authentication approaches for securing the IoT
Several pieces of research focus on the security of the IoT via multifactor authentication approaches. In this context, in 2017, Dhillon and Kalra proposed a multifactor authentication approach based on biometrics, dedicated to services offered by the IoT. Formal and informal analysis of this proposition demonstrates its robustness in terms of security. In 2019, Ahmed and Ahmed proposed a multifactor authentication approach to securing the IoT. The authors show that the proposed approach is robust against many types of attack and also guarantees the integrity, authenticity and availability of detected data for legitimate devices in the IoT.
The IoT has contributed to the dramatic evolution of services offered in the healthcare sector. It is very important to guarantee the protection of sensitive data exchanged in this domain. In 2018, Ali et al. proposed an authentication protocol based on three factors for securing the IoT in the context of e-health systems. They have demonstrated the robustness of the security of their protocol using BAN (Burrows-Abadi-Needham) logic and security analysis with the formal verification tool, AVISPA. In 2019, Li et al. proposed a multifactor authentication protocol for the wireless medical sensor network. The security of this protocol has been demonstrated by the formal verification tool ProVerif. Recently, Sammoud et al. (2020c) proposed an optimal protocol for multifactor authentication and generation of session keys to secure direct communications between healthcare professionals and the patient’s medical sensors. Using analysis of formal and informal security, they have demonstrated that their protocol is robust enough against the most well-known attacks such as password attacks, replay attacks and attacks on the gateway or sensor, or attacks that involve stealing the user’s identity. In addition, the authors of Sammoud et al. (2020c) have shown that their protocol is more efficient in terms of the resources required (calculation, memory and energy) than the protocols proposed by Ali et al. (2018) and Li et al. (2019).
8.4.3. Presentation of the approach of Sammoud et al. (2020c)
Sammoud et al. (2020c) have proposed a multifactor authentication protocol with generation of a session key to secure a direct communication between medical personnel and a patient’s network of wireless body sensors (WMSN: Wireless Medical Sensors Network). In this type of communication, with a terminal (wired, wireless or cellular) and Internet access, a doctor (or more generally, a healthcare professional) can access a medical sensor situated in the patient’s WMSN network via a gateway. This access is generally achieved in the following way. First of all, a smartcard is delivered to the healthcare professional by the administration system. This smart card is then used to verify the legitimacy of the healthcare professional and to send a connection message to the gateway via a public channel (e.g. the Internet). Then, via the gateway, the healthcare professional and the medical sensor agree on a session key to secure later communications.
The authors of Sammoud et al. (2020c) have shown that the proposed protocol ensures a robust protection against known attacks while still ensuring low consumption of resources (CPU, memory and energy). Indeed, formal and informal security analysis of the protocol has demonstrated its robustness against password guessing attacks, user identity guessing attacks, gateway impersonation attack, sensor impersonation attack, insider attacks and replay attacks, as well as maintaining user untraceability and protection of the symmetric key generated, which will be used later to secure communications between the healthcare professional and the medical sensor against illicit disclosure. In addition, by comparing the protocol with other multifactor authentication protocols, the authors of Sammoud et al. (2020c) have demonstrated that their proposition has the advantage of resisting a large number of attacks while still minimizing consumption of resources (calculation, memory and energy).
Like most work in this domain (defining multifactor authentication), this approach has five phases: setup, healthcare professional registration, login, authenticating and password change phase.
8.4.3.1. Notation
Table 8.3 introduces the notations that will be used to describe the approach of Sammoud et al. (2020c).
Table 8.3. Notation table
| Notation | Explanation |
| Ui | Healthcare professional (user) i |
| GW | Gateway |
| SNj | Sensor node j |
| IDi | User identifier Ui |
| PWi | User password Ui |
| Bi | Biometric characteristic of the user Ui |
| IDg | Gateway identifier GW |
| SIDj | Sensor node identifier SNj |
| SK | Symmetric key, generated to secure communication between Ui and SNj |
| Gen, Rep | Probabilistic generation procedure and deterministic reproduction procedure of the fuzzy extractor |
| h(⋅) | Hashing function |
|
| XOR Operator |
| || | Concatenation operator |
8.4.3.2. Setup phase
First of all, the administration system SA selects an identity SIDj for each sensor node and calculates Ksnj = h (SIDj ∥ K), where K represents a secret key belonging to the gateway GW. Then, SA stores Ksnj in the sensor node memory SNj. Thus, each sensor node shared a unique symmetric key Ksnj with the gateway.
8.4.3.3. Healthcare professional registration phase
At first, a user Ui who is a healthcare professional should register at the gateway, through an administration system SA, so as to be authorized to access the wireless medical sensor network. The following steps are needed for registration (see Figure 8.3).
- – Step 1: Ui chooses an identity IDi and a password PWi. Then, they imprint their personal biometric data Bi (fingerprint) on a specific device and calculate (B*i, Pi) = Gen (Bi). Gen () is a probabilistic generation procedure by the fuzzy extractor. B*i represents the biometric key and Pi designates the public reproduction parameter that will be used later to reproduce B*i. Then, Ui calculates BPWi = h(PWi ∥ B*i) and IPWi = h(PWi ∥ IDi). The user then sends the message {IPWi, BPWi} to the system administrator, and this transmits the message received at the gateway GW. Indeed, to resist insider attacks as well as password guessing attack (e.g. a brute force attack) and user identity guessing attack, Ui uses a hashing function to ensure that their personal information, such as a password, their personal identity and their biometric data, are masked when they are transmitted to the system administrator and then to the GW.
- – Step 2: after having received the message from Ui, the gateway GW produces a dynamic identity DIDi for Ui and then calculates Ai = h (DIDi ∥ k ∥ IDg), Ci = Ai ⊕ BPWi, Di = DIDi ⊕ BPWi and Fi = Ai ⊕ IPWi. In fact, the reason to use a dynamic identity DIDi is to strengthen user untraceability. Then, GW sends {Ci, Di, Fi, h(⋅)} to SA. The system administrator then sends a smart card containing the information {Ci, Di, Fi, h(⋅)} and transmits this to Ui via a secure channel (e.g. hand to hand or via a registered post).
- – Step 3: after they have received their smart card from the SA, the healthcare professional Ui stores Pi in SCi. So, after this update, the smart card SCi finally contains parameters {Ci, Di, Fi, Pi, h(.)}.

Figure 8.3. Registration phase of Sammoud et al. (2020c). For a color version of this figure, see www.iste.co.uk/chalouf/intelligent.zip
8.4.3.4. Login phase
- – Step 4: Ui inserts their own SCi into the smart card reader and re-enters his IDi and his PWi. Then, he imprints his biometric data (fingerprint) B' with the help of a specific sensor (Figure 8.4). Then, the smart card SCi reproduces B*i = Rep (B'i, Pi) where Rep(.) is a deterministic reproduction procedure of the fuzzy extractor. Finally, SCi calculates BPWi = h(PWi ∥ B*i), Ai = Ci ⊕ BPWi and F'i = Ai ⊕ h(PWi ∥ IDi), and compares F'i with stored Fi. Where they match, Ui passes identity verification and SCi passes to the following operation stage. Where this does not happen, the connection request is refused.
- – Step 5: SCi recovers DIDi = Di ⊕ BPWi and generates a random number (nonce) Mi. Then, it calculates M1 = Mi ⊕ Ai , M2 = h(IDi ∥ SIDj), M3 = Eh(Mi) (IDi ∥ SIDj ∥ M2∥ T1) and transmits {DIDi, M1, M3} to GW via a public channel (e.g. the Internet). The random number generated Mi as well as the timestamp T1 helps to protect this approach against replay attacks. Furthermore, Mi is used, masked by a hashing function, as a symmetric key for the message M3. In fact, this random number is known only by the user. To recover Mi, an attacker needs to be able to guess the user’s biometric data and password, which are well protected. This approach therefore guarantees a high level of resistance against user impersonation attack.

Figure 8.4. Login phase of Sammoud et al. (2020c). For a color version of this figure, see www.iste.co.uk/chalouf/intelligent.zip
8.4.3.5. Authentication phase
To ensure mutual authentication and secure sharing of a session key between Ui and SNj, the following steps should be carried out (Figures 8.5(a) and 8.5(b)).
- – Step 6: after having received the connection request message from Ui, GW should, first of all, recover Mi = M1 ⊕ h(DIDi ∥ K ∥ IDg). Then, GW decrypts M3 by using h(Mi) as a decryption key to retrieve {IDi ∥ SIDj ∥ M2 ∥ T1} and verifies, afterward, if T2 - T1 ≤ △T. Where they do not match, GW ends the session. Otherwise, GW calculates M'3 = h(IDi || SIDj) and compares M'3 to M3. Where they do match, Ui is correctly identified by the GW and the following steps will be carried out. Where they do not match, the session is terminated.

Figure 8.5. a) Authentication phase of Sammoud et al. (2020c); b) Protocol authentication stage of Sammoud et al. (2020c) (the continuation). For a color version of this figure, see www.iste.co.uk/chalouf/intelligent.zip
- – Step 7: the gateway GW generates a random number (nonce) Ni and calculates M4 = Ni ⊕ h(Ksn), M5 = h (IDi ∥ Ni ∥ T3∥ IDg) and M6 = Eh(Ksn||Ni) (IDg ∥ IDi ∥ Mi ∥ M5 ∥ T3). Then, GW transmits {M4, M6} to SNj via a public channel. The random number generated Ni and the timestamp T3 are used to protect this approach against replay attacks. The message M6 is encrypted using h(Ksn ∥ Ni) as a symmetric key, where Ksn is a symmetric key known only by the gateway GW and the sensor SNj concerned. Furthermore, Ni is very difficult for an attacker to predict. This approach is therefore well protected against gateway impersonation attack.
- – Step 8: after having received the message from GW, SNj recovers Ni = M4⊕ h(Ksn) to decrypt M5 and can extract {IDg ∥ IDi ∥ Mi ∥ M5 ∥ T3}. Then, it verifies whether T4 - T3 ≤ △T. Where they do not match, SNj ends the session. Otherwise, SNj calculates M'5 = h(IDi ∥ Ni ∥ T3∥ IDg) and compares M'5 with the M5 received. Where they match, GW is correctly authenticated by SNj and other steps will be carried out. Where they do not match, the session will be terminated.
- – Step 9: SNj proceeds to generate the random number (nonce) Vi and calculates M7 = Vi ⊕ h (Mi ∥ Ni), the session key SK = h(IDi ∥ IDg ∥ SIDj ∥ Mi ∥ Ni ∥ Vi) and M8 = h (SK ∥ IDi ∥ IDg ∥ T5). Then, SNj transmits {M7, M8, T5} to GW via a public channel. Use of a random number Vi and the timestamp T5 helps us to protect this approach against replay attacks. M7 and M8 will both be used by GW to verify the identity of the sensor SNj. Both messages will be generated on the basis of data known only by GW and SNj. To do this, we can say that this approach is fairly robust against sensor node impersonation attack.
- – Step 10: after having received the message from SNj, GW first verifies whether T6 - T5 ≤ △T. Where they do not match, GW ends the session. Otherwise, it recovers Vi = M7 ⊕ h (Mi ∥ Ni) and calculates SK' = h(IDi ∥ IDg ∥ SIDj ∥ Mi ∥ Ni ∥ Vi) and M'8 = h (SK ∥ IDi ∥ IDg ∥ T5). Then, GW compares M'8 with M8 received. Where they match, SNj is correctly authenticated by the GW and other stages will be carried out. Where they do not match, the session will be terminated.
- – Step 11: GW produces a new dynamic identity DIDni for the user Ui and calculates Ani =h (DIDni ∥ k ∥ IDg). Then, it calculates M9 = h(SK ∥ Ani ∥ DIDni) and M10 = Eh(Mi) (Ani ∥ Ni ∥ Vi ∥ DIDni ∥ M9 ∥ T7) before transmitting M10 to Ui >via a public channel. The message M10 contains the information needed for Ui to be able to generate the symmetric key SK and update the parameters stored in their smart card. It is impossible for the attacker to obtain this secret data because the message M10 is encrypted with the help of a symmetric key h(Mi) which is the result of hashing the secret information Mi.
- – Step 12: after receiving the message M10 from GW, Ui (via their smart card) applies the decryption function on M10 using h(Mi) as a symmetric key to recover {Ani ∥ Ni ∥ Vi ∥ DIDni ∥ IDg ∥ M9 ∥ T7}. Then, they verify whether T8 - T7 ≤ △T. Where they do not match, Ui ends the session. Otherwise, Ui calculates SK' = h(IDi ∥ IDg ∥ SIDj ∥ Mi ∥ Ni ∥ Vi) and M'9 = h(SK' ∥ Ani ∥ DIDni) and then compares M'9 to M9. Where they match, GW is correctly authenticated at Ui and other stages will be carried out. Where they do not match, the session will be terminated. We should note that the secret session key SK generated will later be used to encrypt/decrypt sensitive medical data between the user Ui and the sensor node SNj. Indeed, this session key SK is unique for each user/gateway/sensor authentication session.
- – Step 13: Ui calculates Cni = Ci ⊕ Ai ⊕ Ani, Dni = DIDni ⊕ BPWi and Fni = Fi ⊕ Ai ⊕ Ani to replace Ci , Di and Fi stored in the smart card by the new values Cni , Dni and Fni. Indeed, updating the secret parameters stored in the smart card is carried out to guarantee the untraceability of the healthcare professional (user) in this approach.
8.4.3.6. Password change phase
This phase is necessary to enable a legal user Ui wanting to update their password in complete security. In this case, the following stages should be executed.
- – Step 1: after having inserted his smart card SCi into a specific card reader, the user Ui enters their identity IDi, and password PWi. The user then imprints their biometric data Bi at the corresponding sensor.
- – Step 2: to verify the user’s identity, just like in the login phase, the smart card SCi reproduces B*i = Rep (B'i, Pi). Then, SCi calculates BPWi = h(PWi ∥ B*i), IPWi = h(PWi ∥ IDi), Ai = Ci ⊕ BPWi and F'i = Ai ⊕ h(PWi ∥ IDi) and compares, afterward, F'i to Fi stored in SCi. Where they match, the user Ui passes their identity verification and SCi requires this user to enter the new password. Where they do not match, SCi refuses the request to change password and ends this stage.
- – Step 3: using the new password PWi(new), SCi should modify the registered parameters Ci, Di and Fi. Then, SCi calculates BPWi(new) = h(PW(new)i ∥ B*i), IPWi = h(PW(new)i ∥ IDi), Ci(new) = Ci ⊕ BPWi ⊕ BPWi(new), Di(new) = Di ⊕ BPWi ⊕ BPWi(new) and Fi(new) = Fi ⊕ IPWi ⊕ IPWi(new). Finally, SCi will replace the parameters already stored by the new {Ci(new), Di(new), Fi(new), Pi, h(.)}.
8.4.3.7. Discussion
The multifactor authentication protocol proposed by Sammoud et al. (2020c) is robust in terms of security against known attacks (password attacks, replay attacks, user impersonation attack, gateway impersonation attack and sensor node impersonation attack) while still ensuring low resource consumption. But it still remains vulnerable due to certain drawbacks linked to use of the password and the smart card. Unlike biometrics, a password can be forgotten and the smart card can be lost. The protocol proposed in Sammoud et al. (2020c) is robust against password attacks, and even when they know data stored in the smart card, an attacker is still unable to access the user’s sensitive data. But it is impossible for the user to be authenticated correctly if they forget their password or do not have their smart card. Biometric characteristics cannot be forgotten nor stolen, nor lost. Because of this, for the remainder of this chapter we present the possibility of using authentication mechanisms based on biometric methods that are processed using machine learning techniques.
8.5. Authentication techniques based on biometrics and machine learning
8.5.1. Machine learning algorithms
Several machine learning algorithms are used for identification/authentication. In this section, we present the most powerful machine learning algorithms compared to other algorithms for biometric applications (Yeh et al. 2016):
- – Neural networks: networks of artificial neurons are inspired by biological neural systems in the human brain (Negnevitsky 2005). They are characterized by their capacity to handle large quantities of information. These networks are formed of a set of neurons working simultaneously. Multilayer (MLP: MultiLayer Perceptron) networks are the most widely used classifiers for neural networks. They are formed using supervised algorithms. RBF (Radial Basis Function) networks derive from the approximation theory of functions that have a powerful architecture (Feedforward). This type of network was introduced for the first time by Hardy (1995), and the corresponding theory was developed by Powell (1999). Afterward, this type of network was known by the “term” neural networks. This type of network uses Gaussian functions. The learning is based essentially on the least squares algorithm and the K-means algorithm.
- – Support-vector machines (SVMs): are supervised learning techniques intended to solve problems of regression and discrimination. SVMs were developed during the 1990s and are characterized by their capacity to work with large dimension data. SVMs use linear separators that maximize the margin between two different classes with the aim of providing an optimal classification (Nguyen and Armitage 2008).
- – k-nearest neighbors: the k-nearest neighbors (KNN) method is a supervised learning method that can be used when searching for new biomarkers for diagnostics (Bhatia and Vandana 2010). KNN is a non-parametric method in which the model memorizes observations from all the learning to classify data from all the tests. This machine learning algorithm is called Lazy Learning because it learns nothing during the training stage. To estimate the output linked to a new input, the KNN method consists of considering (identically) the k learning samples whose input is closest to the new input, depending on a distance to be defined (e.g. Euclidean distance) (Bhatia and Vandana 2010).
- – Decision tree: the decision tree (DT) method is one of the most popular supervised learning methods for data classification problems. This tool to aid decision-making makes it possible to represent a set of choices in graph form in the shape of a tree. Indeed, a DT models a hierarchy of tests to predict a result. The possible decisions are situated at the extremities (the leaves of the tree) and are reached depending on the decisions at each stage. A DT works by applying very simple logical rules iteratively; these rules are chosen depending on the result of the preceding rule. DTs have the advantages of being simple to interpret and quick to use, of being non-parametric and of requiring very little data pre-processing (Phyu 2009).
8.5.2. Examples of authentication approaches based on biometrics and machine learning
These days, mobile phones with touch screens represent an increasingly substantial part of the mobile market. Users often also use their mobile phones to store personal and sensitive data. It is therefore important to protect mobile phones by authenticating legitimate users and by detecting intruders. Authentication on mobile devices often occurs using iris recognition. However, these authentication systems can be attacked. The authors of Gragnaniello et al. (2015) used an LBP (Local Binary Pattern) model to evade these attacks. To improve the discrimination capacity of LBP and better explore image statistics, a linear SVM classification schema is proposed in Gragnaniello et al. (2015).
In Mondal and Bours (2015), the authors used continuous authentication based on biometrics using mouse dynamics and SVM and ANN algorithms for classification. In Meng et al. (2012), the authors proposed a new authentication scheme, based on touch dynamics, that uses a set of behavioral features linked to touch dynamics for a precise authentication. To evaluate their system’s performances, they collected and analyzed touch gesture data from 20 Android phone users by comparing several known classifiers. Experimental results show that an optimized neural network classifier (ANN) is well adapted to authenticate different users with an average error rate of around 3% for the selected features.
8.5.3. Authentication approaches based on ECG and machine learning
8.5.3.1. Overall schema for authentication by ECG
The electrocardiogram (ECG) is a graph representing the electrical activity of the heart. The device used to obtain and display the ECG is called an electrocardiograph (or quite simply an ECG device). This device registers electrical cardiac currents (voltages or potential) by means of selective conductive nodes at the surface of the body and provides a voltage-time graph of the heart’s rhythm.
There are two approaches for human identification:
- – Fiducial approach: the ECG signal is formed of three waves P, QRS and T (Figure 8.6). The fiducial characteristics describe the peaks and intervals between the three waves. Fiducial methods detect, process and classify these characteristics to identify individuals.
- – Non-fiducial approach: to avoid the cost of detecting peaks or intervals, the non-fiducial approach uses signal processing based on the shape of the waves in the frequency domain.

Figure 8.6. An ECG sequence (Sammoud et al. 2020a). For a color version of this figure, see www.iste.co.uk/chalouf/intelligent.zip
In general, authentication by ECG happens in four stages (Figure 8.7).
- – Stage 1: acquiring an ECG signal (Figure 8.8). The ECG is acquired via three electrodes placed on the right and left upper limbs and the lower right limb.

Figure 8.7. Overall structure of an authentication system based on ECG

Figure 8.8. Acquiring an ECG signal. For a color version of this figure, see www.iste.co.uk/chalouf/intelligent.zip
- – Stage 2: pre-processing the ECG signal. Usually, the ECG contains noise. Consequently, a pre-processing stage is carried out using filters (Wang et al. 2007).
- – Stage 3: extracting characteristics. Several methods have been used such as the Fourier Transform (FT), the Discrete Cosine Transform (DCT) and the Discrete Wavelet Transform (DWT).
- – Stage 4: classification. The question is asked: “Is the signal really an ECG graph of an individual or not?” To solve this problem, several approaches try to use machine learning algorithms that can make it possible to predict the data from different types of databases. These ML algorithms are used to discover a set of rules in the database to carry out a precise classification (Wang et al. 2007).
8.5.3.2. Authentication approaches based on ECG
Use of ECG in biometrics is a recent development. The first method was proposed in 1999 by Biel et al. (2001). This method is based on analysis of the ECG using fiducial points and has made it possible to implement the SIMCA (Soft Independent Modeling of Class Analogy) method for classification. Later, in 2006, Wang et al. proposed a new method of biometric identification. It is based on fiducial detection using the DCT and the autocorrelation function. This method consists of integrating analytical characteristics and appearance characteristics extracted from the ECG signals for human identification. The latter method, without fiducial detection, called AC/DCT, was proposed by Plataniotis et al. (2006).
Recently, researchers have focused on improving classification methods. Several pieces of research are based on machine learning algorithms. Sidek et al. (2012) used an MLP algorithm to classify the individuals to be identified. Tantawi et al. (2015) also introduced RBF neural networks to classify signals. Tang and Shu (2014) also used Quantum Neural Networks (QNN). Melgani and Bazi (2008) use the SVM classifier and the results obtained confirm that the SVM approach is better than the traditional kNN approach.
Kim et al. (2019a) proposed a machine learning framework used for biometric authentication based on the ECG. To evaluate their proposition, they used the three ML techniques: SVM, DT and the neural networks. Al Alkeem et al. (2019) proposed a biometric authentication protocol based on ECG and machine learning algorithms. The authors tested the performances of their proposition with two ML protocols: SVM and DT. Kim et al. (2019b) proposed a biometric authentication protocol based on machine learning using ECG R-R intervals. The authors analyzed performances of the proposed protocol using two ML techniques: SVM and DT.
Moreover, thanks to the random character of the ECG signal, this sequence can also be used to generate fairly robust symmetric keys, as demonstrated in Sammoud et al. (2020a, 2020b). Indeed, ECG represents a good alternative compared to other classical methods based on cryptographic mechanisms to generate cryptographic keys (Sammoud et al. 2020a, 2020b).
8.6. Challenges and limits
8.6.1. Quality of biometric data
Authentication using biometrics is less precise than that based on what a person knows or possesses. Indeed, comparison of two biometric vectors is expressed in similarity, which never reaches 100%. The quality/precision of sensors has an impact on the quality and performances of biometric authentication systems.
8.6.2. Non-revocability of biometric data
Unlike a code, biometric data cannot be modified after falsification or theft. The existence of these vulnerabilities has given rise to a need to protect biometric data.
8.6.3. Security of biometric systems
A biometric system can present security failures against attacks on the sensor, attacks on transmission channels, direct attacks on stored data and attacks during the enrollment stage.
In addition, the use of biometrics presents risks in terms of respecting privacy. The capturing, processing and preservation of biometric data can be an invasion of privacy. Biometric data are sensitive in nature and no international standard protects these data. Several solutions can be imagined, such as anonymization or consideration of respect for privacy from the stage of designing the biometric system (Privacy by design).
8.7. Conclusion
Most of the data processed in the IoT environment are sensitive and personal and should be well protected to ensure security and the protection of user privacy.
In this chapter, we have studied the contribution of biometrics and artificial intelligence to strengthening security in the IoT. First, we presented security problems in the IoT. Indeed, our interest was in studying authentication techniques in the IoT, based on biometrics. We have therefore presented multifactor authentication protocols as well as authentication approaches based on biometrics and machine learning. In particular, we studied approaches that use artificial intelligence techniques such as machine learning to ensure authentication based on ECG.
8.8. References
Ahmed, A.A. and Ahmed, W.A. (2019). An effective multifactor authentication mechanism based on combiners of hash function over Internet of Things. Sensors, 19(17), 3663.
Al Alkeem, E., Kim, S.K., Yeun, C.Y., Zemerly, M.J., Poon, K.F., Gianini, G., Yoo, P.D. (2019). An enhanced electrocardiogram biometric authentication system using machine learning. IEEE Access, 7, 123069–123075.
Ali, R., Pal, A.K., Kumari, S., Sangaiah, A.K., Li, X., Wu, F. (2018). An enhanced three factor based authentication protocol using wireless medical sensor networks for healthcare monitoring. Journal of Ambient Intelligence and Humanized Computing, 1–22.
Bhatia, N. (2010). Survey of nearest neighbor techniques. International Journal of Computer Science and Information Security, 8(2). arXiv:1007.0085.
Biel, L., Pettersson, O., Philipson, L., Wide, P. (2001). ECG analysis: A new approach in human identification. IEEE Transactions on Instrumentation and Measurement, 50(3), 808–812.
Cabra, J.L., Mendez, D., Trujillo, L.C. (2018). Wide machine learning algorithms evaluation applied to ECG authentication and gender recognition. In 2nd International Conference on Biometric Engineering and Applications. CBEES, Amsterdam.
Dhillon, P.K. and Kalra, S. (2017). A lightweight biometrics based remote user authentication scheme for IoT services. Journal of Information Security and Applications, 34, 255–270.
Gragnaniello, D., Sansone, C., Verdoliva, L. (2015). Iris liveness detection for mobile devices based on local descriptors. Pattern Recognition Letters, 57, 81–87.
Hamidi, H. (2019). An approach to develop the smart health using Internet of Things and authentication based on biometric technology. Future Generation Computer Systems, 91, 434–449.
Hardy Sr., R.L. (1995). U.S. Patent No. 5,452,863. Patent, Washington.
Kim, S.K., Yeun, C.Y., Damiani, E., Lo, N.W. (2019a). A machine learning framework for biometric authentication using electrocardiogram. IEEE Access, 7, 94858–94868.
Kim, S.K., Yeun, C.Y., Yoo, P.D. (2019b). An enhanced machine learning-based biometric authentication system using RR-Interval Framed Electrocardiograms. IEEE Access, 7, 168669–168674.
Lee, H., Kang, D., Ryu, J., Won, D., Kim, H., Lee, Y. (2020). A three-factor anonymous user authentication scheme for Internet of Things environments. Journal of Information Security and Applications, 52, 102494.
Li, X., Peng, J., Obaidat, M.S., Wu, F., Khan, M.K., Chen, C. (2019). A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems. IEEE Systems Journal, 14(1), 39–50.
Melgani, F. and Bazi, Y. (2008). Classification of electrocardiogram signals with support vector machines and particle swarm optimization. IEEE Transactions on Information Technology in Biomedicine, 12(5), 667–677.
Meng, Y., Wong, D.S., Schlegel, R. (2012). Touch gestures based biometric authentication scheme for touchscreen mobile phones. In International Conference on Information Security and Cryptology. ICISC, Seoul.
Mondal, S. and Bours, P. (2015). A computational approach to the continuous authentication biometric system. Information Sciences, 304, 28–53.
Negnevitsky, M. (2005). Artificial Intelligence: A Guide to Intelligent Systems, 2nd edition. Pearson Education, London.
Nguyen, T.T. and Armitage, G. (2008). A survey of techniques for internet traffic classification using machine learning. IEEE Communications Surveys & Tutorials, 10(4), 56–76.
Ometov, A. and Bezzateev, S. (2017). Multi-factor authentication: A survey and challenges in V2X applications. In 2017 9th International Congress on Ultra Modern Telecommunications and Control Systems and Workshops (ICUMT). IEEE, Munich.
Ometov, A., Bezzateev, S., Mäkitalo, N., Andreev, S., Mikkonen, T., Koucheryavy, Y. (2018). Multi-factor authentication: A survey. Cryptography, 2(1), 1.
Phyu, T.N. (2009). Survey of classification techniques in data mining. Proceedings of the International MultiConference of Engineers and Computer Scientists, 1(5), 727–731.
Plataniotis, K.N., Hatzinakos, D., Lee, J.K. (2006). ECG biometric recognition without fiducial detection. In 2006 Biometrics Symposium: Special Session on Research at the Biometric Consortium Conference. IEEE, Baltimore.
Powell, M.J. (1999). Recent research at Cambridge on radial basis functions. In New Developments in Approximation Theory, Müller, M.W., Buhmann, M.D., Mache, D.H., Felten, M. (eds). Birkhäuser, Bâle.
Sammoud, A., Chalouf, M.A., Hamdi, O., Montavont, N., Bouallegue, A. (2020a). A new biometrics-based key establishment protocol in WBAN: Energy efficiency and security robustness analysis. Computers & Security, 96, 101838.
Sammoud, A., Chalouf, M.A., Hamdi, O., Montavont, N., Bouallegue, A. (2020b). A secure three-factor authentication and biometrics-based key agreement scheme for TMIS with user anonymity. In 2020 International Wireless Communications and Mobile Computing (IWCMC). IEEE, Limassol.
Sammoud, A., Chalouf, M.A., Hamdi, O., Montavont, N., Bouallegue, A. (2020c). A secure and lightweight three-factor authentication and key generation scheme for direct communication between healthcare professionals and patient’s WMSN. In 2020 IEEE Symposium on Computers and Communications (ISCC). IEEE, Rennes.
Sidek, K.A., Khalil, I., Smolen, M. (2012). ECG biometric recognition in different physiological conditions using robust normalized QRS complexes. In 2012 Computing in Cardiology. IEEE, Krakow.
Tang, X. and Shu, L. (2014). Classification of electrocardiogram signals with RS and quantum neural networks. International Journal of Multimedia and Ubiquitous Engineering, 9(2), 363–372.
Tantawi, M.M., Revett, K., Salem, A.B., Tolba, M.F. (2015). A wavelet feature extraction method for electrocardiogram (ECG)-based biometric recognition. Signal, Image and Video Processing, 9(6), 1271–1280.
Wang, Y., Plataniotis, K.N., Hatzinakos, D. (2006). Integrating analytic and appearance attributes for human identification from ECG signals. In 2006 Biometrics Symposium: Special Session on Research at the Biometric Consortium Conference. IEEE, Baltimore.
Wang, Y., Agrafioti, F., Hatzinakos, D., Plataniotis, K.N. (2007). Analysis of human electrocardiogram for biometric recognition. EURASIP Journal on Advances in Signal Processing, 2008(1), 148658.
Xiao, L., Wan, X., Lu, X., Zhang, Y., Wu, D. (2018). IoT security techniques based on machine learning: How do IoT devices use AI to enhance security? IEEE Signal Processing Magazine, 35(5), 41–49.
Yeh, K.H., Su, C., Hsu, C.L., Chiu, W., Hsueh, Y.F. (2016). Transparent authentication scheme with adaptive biometrie features for IoT networks. In 2016 IEEE 5th Global Conference on Consumer Electronics. IEEE, Kyoto.
