Chapter 7: Linux Proxy Enhancements
At the heart of Veeam Backup & Replication are the workhorses – proxies. This chapter will look at proxy servers and what's new in v11a, including Linux proxy enhancements. We'll discuss how these new enhancements will help security, among other things, in your environment. You will learn about the persistent data mover, which also contains enhanced security. Finally, we will dive into how credentials are a thing of the past – machine certificates are the future.
By the end of this chapter, you will understand what proxy enhancements are new in v11a. You will also know how they fit into your environment and use cases. Finally, you will have a better understanding of job settings and configuration best practices.
In this chapter, we're going to cover the following main topics:
- Understanding Linux proxy enhancements and what's new in v11a
- Understanding how the latest enhancements can help your organization
- Discovering the persistent data mover with enhanced security
- Discovering how credentials are the past and certificates are the future
- Special section by Rick Vanover from Veeam – future Linux capabilities and industry direction
Technical requirements
For this chapter, you should have Veeam Backup & Replication installed. If you followed along through the book, then Chapter 1, Installing and Upgrading Veeam, covered the installation and optimization of Veeam Backup & Replication, which you can use in this chapter. If you have access to an Ubuntu Linux 20.04 server, it will help reinforce many of the concepts covered in this chapter.
Understanding Linux proxy enhancements and what's new in v11a
Within the Veeam Backup & Replication system, you have the backup server, which is the one that handles administering tasks, and the proxy servers sit between it and the rest of the backup infrastructure components. The proxy servers are the ones that process jobs and deliver the backup traffic to the rest of the infrastructure; you could say they are the workhorse of all components.
Based on the following diagram, you can see that the proxy server performs many tasks before finally sending data to the backup repository:

Figure 7.1 – Backup infrastructure with proxy server
The proxy servers will perform many tasks during a backup job, including the following:
- Retrieving virtual machine (VM) data from within the production storage
- Compressing the data – during transit to the repository
- Deduplicating the data – deduplicate the data before sending it to the repository
- Encryption of the data – encrypt data in transit to the repository
- Sending of data to the backup repository (backup job) or possibly another proxy server (replication job)
- Performing restores
In a typical small deployment scenario, the proxy server is deployed on the backup server and is helpful for low-traffic loads. When it comes to larger enterprise installations, a distributed structure is better at deploying proxy servers separately.
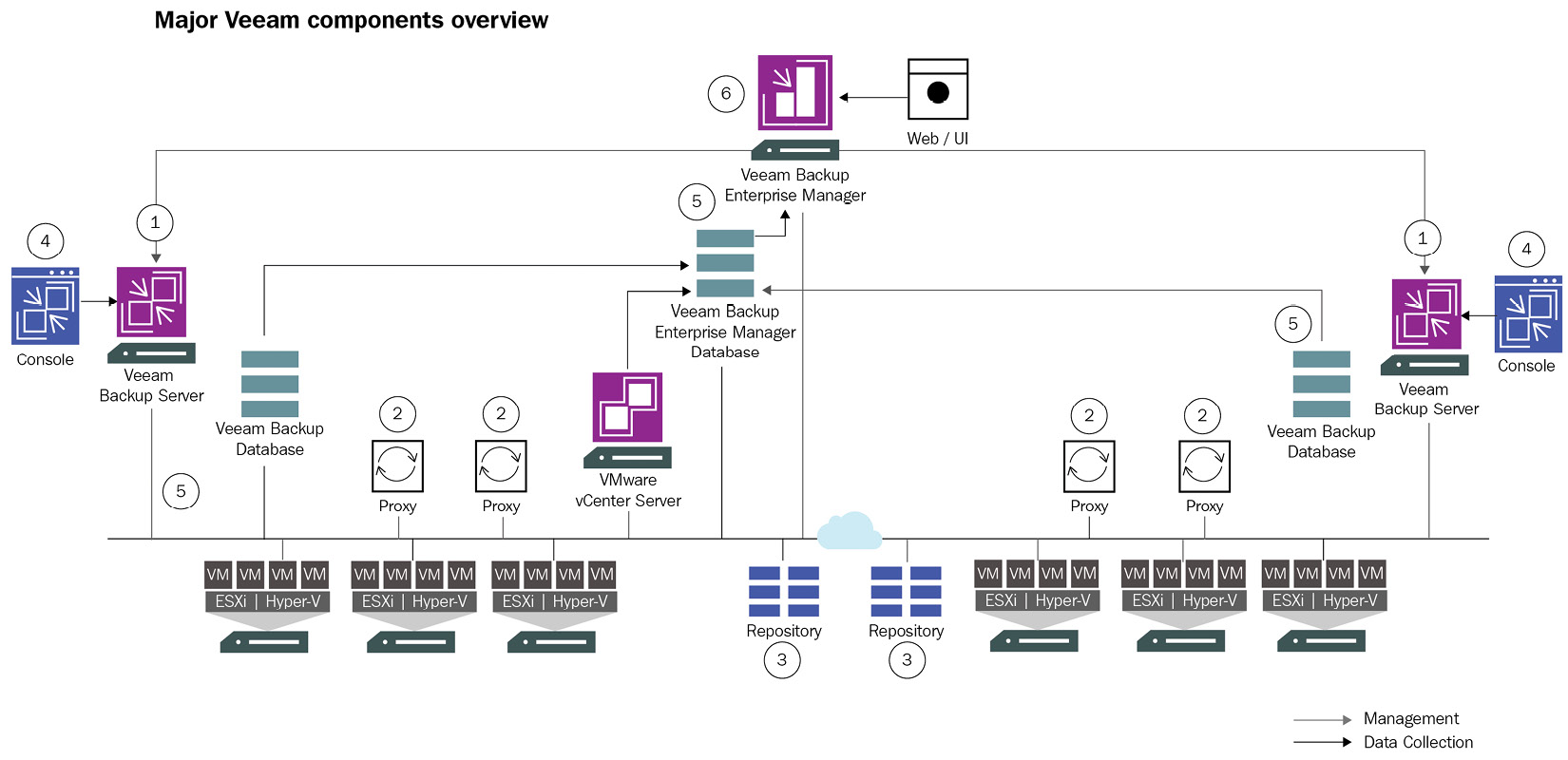
Figure 7.2 – Veeam components with a distributed architecture
This diagram shows an enterprise environment infrastructure where the proxy servers are deployed separately on the network. Note that a proxy does not explicitly need a dedicated system, but this becomes a natural choice for larger environments.
Within the new Veeam Backup & Replication v11a, some significant enhancements put the Linux proxy on par with the Windows proxy capabilities. Some of those changes are as follows:
- A Linux proxy server can be physical or virtual.
- More transport modes – NBD, Direct SAN, and Hot-Add. With the Hot-Add transport mode, Veeam now uses the enhanced data fetcher technology, which was only used in Windows previously.
- Backup from storage snapshot (iSCSI, FC).
- Allows quick rollback/CBT restore.
- Persistent data movers are now deployed when Linux servers are added the first time and are not to be redeployed during backups.
- Enhanced security with the data mover process.
- Certificate-based authentication instead of saved Linux credentials.
- New elliptic curve (EC) cryptography – adds EC-based SSH key pairs such as Ed25519 or ECDSA
Now, with enhancements, there also come some limitations, which are as follows:
- Linux cannot be used as a guest interaction proxy.
- Linux cannot be used with VMware Cloud on AWS.
- The Open-iSCSI initiator must be enabled for Direct SAN access.
- The NFS protocol is not supported for integration with storage systems.
- The VM copy scenario is not supported when Hot-Add transport mode is used.
Now that you understand the proxy server enhancements and what has changed in v11a, we will now look at how these can help you in your environment.
Understanding how the latest enhancements can help your organization
With all the newest enhancements, you may be wondering how these can help you in your backup environment. The following sections will look at the improvements from the previous section, Understanding Linux proxy enhancements and what's new in v11a.
A Linux proxy server can be physical or virtual
With the proxy transport modes changing, you can now have the Linux proxy server as either a physical server or a VM within your virtual infrastructure. By deploying a Linux proxy in your virtual infrastructure, you will save the cost of physical hardware, maintenance, and support. Instead, it becomes part of your virtual environment, allowing for easier maintenance, updating, and so on. However, if you choose a physical server, this allows for storage integration with iSCSI or Fiber Channel and faster network backups when using a 10 GB network or higher. There is added cost for physical hardware to replace failed parts, support, and so on, and should a critical component fail, this might take the server out of commission until fixed.
More transport modes – NBD, Direct SAN, and Hot-Add
Initially, when the Linux proxy server was introduced in Veeam Backup & Replication v10, you had to run it in appliance mode (Hot-Add). This, at the time, effectively required the server to be a VMware VM to run the proxy role. Veeam Backup & Replication v11a has made the transport modes equal to the Windows proxy servers by adding both NBD and Direct SAN.
Network Block Device (NBD) allows you to take advantage of a fast network such as 10 GB or higher and works well when using a physical Linux proxy server. Do note that the network mode will operate over the management VM kernel network configured on your hosts.
Direct SAN allows you to use something such as iSCSI to connect to the datastores where the VM files reside and back up directly from there, avoiding most of the virtualization layer. Direct SAN is one of the faster backup modes.
When adding a Linux proxy server, you must add the Linux server itself to the Veeam console under the Backup Infrastructure tab in the Managed Servers section.

Figure 7.3 – Managed servers adding Linux server to be a proxy server
Once you have the Linux server added, you can go under the Backup Proxies section to add it as a proxy server.

Figure 7.4 – Adding a Linux proxy server
Selecting Add VMware backup proxy will start the New VMware Proxy wizard, as shown in Figure 7.5. You have the option to choose the Transport mode setting, at the first step of the wizard, using the Choose… button:

Figure 7.5 – Transport mode selection of Linux proxy
After completing the wizard, the new Linux proxy will be shown and ready to use within your backup jobs.
Backup from storage snapshot (iSCSI, FC)
The Linux proxy can now integrate and complete backups from storage snapshots in your storage infrastructure. This mode is known as Direct SAN access mode, and the performance is very good, with less traffic placed on your other infrastructure, primarily if virtual.
Allow quick rollback/CBT restore
Previously, the quick rollback feature with Changed Blocks (CBT) restore could only be accomplished with the Windows proxy, but now you can do this with your Linux proxy.

Figure 7.6 – Using quick rollback with CBT
It allows you to perform the quick rollback feature of Veeam Backup & Replication, which takes a server to the desired restore point. It also uses CBT to be restored, allowing you to get your server operational much quicker.
Persistent data mover deployed
When you install your Linux server to get used as a proxy, the transport components get deployed persistently when registered in Veeam. This process will improve performance and scalability, as data movers are not required to get pushed to the server at each task start. Veeam also automatically creates the rules needed for the built-in Linux firewall for the duration of the backup jobs.
Enhanced data mover security
When using the single-use credentials, the persistent data mover will run as a limited user from the credentials set it was deployed with. This security prevents vulnerabilities by not allowing hackers to use the API to overtake the operating system.
Certificate-based authentication instead of saved Linux credentials
When setting up a Linux proxy server using credentials, those will now not get saved, and Veeam will use the public key infrastructure (PKI) technology for authentication instead. The backup server and transport components used during backup tasks will communicate using key pairs generated during transport deployment.
New elliptic curve (EC) cryptography – adds EC-based SSH key pairs such as Ed25519 or ECDSA
Within v11a now, Veeam has achieved an unprecedented level of security by using EC-based SSH key pairs, such as Ed25519 or ECDSA, when communicating with the Linux servers. Think of it this way, if cracking a 228-bit RSA key requires less energy than boiling a teaspoon of water, a 228-bit EC key takes enough energy to boil all the water on Earth! This security provides the equivalent of a 2,380-bit RSA key!
Now that we have covered the proxy server enhancements for Linux, let's look directly at the persistent data mover with enhanced security.
Discovering the persistent data mover with enhanced security
When you deploy a proxy server, two components get installed on the server:
- Veeam Installer Service: This is an auxiliary service installed and started on any Windows server once added to the managed servers within the Veeam Backup & Replication console. It analyzes the system and installs or upgrades components and services dependent on role selection.
- Veeam Data Mover: This is the heart of the proxy server and is the component that performs the data processing of tasks on behalf of the backup server.
When it comes to the data mover on the Linux proxy server, this component is now persistent during the deployment in v11a. Previously in v10, when using a Linux proxy, the data mover component was deployed each time the proxy was used for backup jobs, which would degrade the performance somewhat.
Now, in v11a, the data mover gets deployed to the Linux proxy server when first added to the console and does not require redeployment at each backup task run when used. This saves time and also increases the performance since deployment is not needed.
Important Note
For Linux hosts not yet supporting the persistent data mover, such as storage appliances with Veeam Data Mover integration, v11a will continue using the runtime data mover.
Further to this, Veeam has been able, as noted previously, to achieve an extremely high level of security for the data mover using the EC-based SSH key pairs. An explanation of each is as follows:
- ECDSA – Elliptic Curve Digital Signature Algorithm
- Ed25519 – Edwards-curve Digital Signature Algorithm
Now that we have looked at the persistent data mover and enhanced security, let's see how Veeam uses certificates instead of credentials.
Discovering how credentials are the past and certificates are the future
When adding servers to the Veeam Backup & Replication v11a environment using Linux, you will need to provide credentials to be used. This method was and still is used with most products, including Veeam. However, Veeam will discard those credentials once the server connects and use the PKI environment certificates for all communications.
When adding a Linux server, you will also use the single-use credentials used when adding to the Veeam console and then discarded for certificates.
So, you might be asking yourself – how does this help me or add security to my environment? Credentials get stored in the Veeam database and configuration backups. So, if your Veeam server is compromised and the hacker gets hold of your configuration backups, they can retrieve your passwords only if they know the encryption password! This is an excellent reminder to set the encryption password for your configuration backups to add an extra layer of security.
The following is the Credentials dialog within the Veeam console:
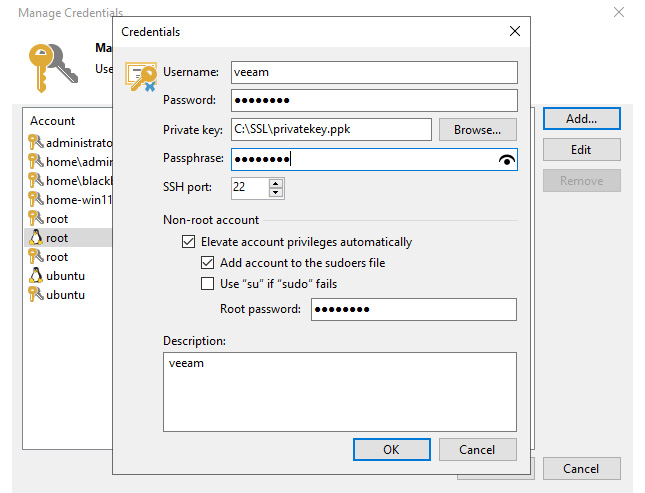
Figure 7.7 – Credentials dialog with certificates for Linux
We have now covered the section on credentials and certificates. The following section is a guest spot from Rick Vanover at Veeam with his take on future Linux capabilities before we wrap this chapter up with our summary.
Special section by Rick Vanover from Veeam – future Linux capabilities and industry direction
Veeam has been on a journey with Linux. One of the most significant positive movements for Linux was the addition of the Linux proxy, but this was one of many moves. Everything from the XFS block cloning (a storage efficiency) for backup repositories, NFS repositories, the Veeam Agent for Linux, and the certificate enhancements explained earlier; it is relatively straightforward that Linux is a priority at Veeam.
Additionally, Veeam's three newest products are based on Linux (Veeam Backup for AWS, Microsoft Azure, and GCP). The upcoming Veeam Salesforce backup product will also be based on Linux. New products for Nutanix AHV and Red Hat Virtualization also provide a special proxy based on Linux.
While this book is focused on actionable information for the administrator for deployments now with v11a, it is reasonable to expect more Linux capabilities from Veeam across the spectrum.
Summary
This chapter has reviewed the Linux servers as proxies. We took a look at what was new within v11a of Veeam Backup & Replication. We reviewed the enhancements made for the unique features of the Linux proxy. We then took a look at how these latest enhancements can play a significant role in your backup infrastructure. We discussed the persistent data mover used now on a Linux proxy, along with the enhanced security for this. Also discussed was how credentials get replaced with certificates for communication between the backup server and Linux proxy.
After reading this chapter, you should now have a much deeper understanding of the proxy enhancements and what's new in v11a. It would help if you also understood how many of these new features could help benefit your environment, from security to performance.
Hopefully, you will now have a better idea of Linux proxies. The next chapter will look at the newest enhancements for the recovery of SQL Server and Oracle databases. Also, we will cover instant publishing of NAS backups and recovery of anything to Microsoft Hyper-V.
Further reading
- Linux backup proxy requirements: https://helpcenter.veeam.com/docs/backup/vsphere/backup_proxy_requirements.html?ver=110
- EC cryptography explanation: https://xilinx.github.io/Vitis_Libraries/security/2021.2/guide_L1/internals/ecc.html
