In the original opportunistic routing ExOR (Biswas and Morris 2005), the MAC layer is tied with routing to provide opportunistic gain. However, due to the strict scheduling on forwarders' access to the medium, it actually prevents spacial reuse to a large extent. If multiple packets are received by the same receiver, those packets may contain duplicate information that wastes the precious network bandwidth. In the case of a large network with highly lossy wireless medium, this problem is aggravated because the strict scheduling and coordination among forwarders is hard to realize due to multipath fading and packet collisions. Thus, MORE was proposed by Chachulski et al. (2007) to solve this challenge. By integrating random linear network coding1 at the intermediate forwarders, nodes forward the coded packets randomly instead of using the structured scheduling approach in ExOR.
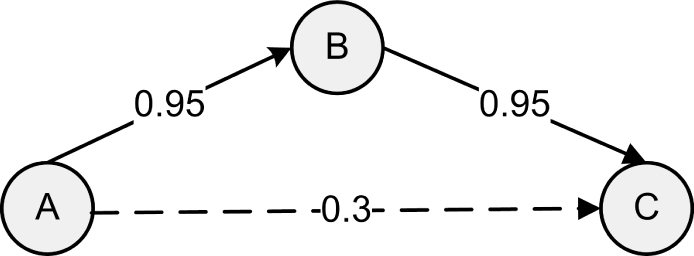
Here we illustrate the motivation of MORE using a simple example. Consider the topology in Figure 7.1 with a single unicast flow. Traditional routing first determines the best path before transmission, which is “A → B → C.” However, there is always a chance for the destination node C to receive packets from source A directly. If, in one transmission, B and C both receive packet p1, this will cause a wasted transmission at node B using traditional routing because B does not know C's reception status. ExOR solves this problem by enforcing a strict transmission coordination for node B, which is in A's forwarder list—B waits for C's feedback signal and only if C has not received a packet in B's queue will B transmit that packet. Such coordination reserves the wireless medium for a single forwarder at any time, as each node in a forwarder list needs to wait for the transmission by all the higher priority forwarders, which actually limits spacial reuse. On the other hand, to enforce such stringent coordination requires modifications at the MAC layer or even the PHY layer, as we can see from the previous chapters. A similar problem exists for multicast flows (Chachulski et al. 2007).
Figure 7.1 Motivating example for MORE. A unicast flow is from source node A to destination node C. The reception success probability of each link is denoted on that link.
Therefore, MORE adopts network coding (Ahlswede et al. 2000) as a remedy. Network coding basically breaks the store-and-forward packet forwarding paradigm. It allows intermediate nodes to combine received packets. Bandwidth efficiency can be improved because each coded packet could benefit multiple receivers simultaneously. Meanwhile, because each coded packet could be equally useful to the receiving node, the complicated coordination of retransmission can be eliminated, which in turn simplifies the protocol design.
In the above example, assume packet p1 is received by both node B and C while p2 is only received by B. As B is unaware of C's fortunate reception, B can simply forward the sum p1 + p2 to C, which can recover p2 since it has p1.
In fact, it is sufficient to generalize the above approach to random linear network coding (RLNC) (Ho et al. 2006). Using RLNC, the source broadcasts native packets, intermediate nodes perform random linear combinations of packets they receive (c1p1 +![]() + cmpm), where c1,
+ cmpm), where c1, ![]() , cm are random coefficients from a Galois field
, cm are random coefficients from a Galois field ![]() . The destination sends an acknowledgement (ACK) along the reverse path to the source once it receives all the native packets. In this way, node coordination is not required and spacial reuse is preserved, which essentially “trades off structure for randomness”.
. The destination sends an acknowledgement (ACK) along the reverse path to the source once it receives all the native packets. In this way, node coordination is not required and spacial reuse is preserved, which essentially “trades off structure for randomness”.
Next we describe the operation of MORE in more detail.
- Source. The source generates K coded packets as a batch, from uncoded packets p1,
 , pK, which are called native packets. A coded packet is generated as follows:
, pK, which are called native packets. A coded packet is generated as follows:

where cji are random coefficients from a Galois field ![]() , and
, and ![]() is called a coding vector. The sender attaches the following information in the packet header: the packet's coding vector (which will be used in decoding), the ID of the current batch, the IP addresses of the source and destination, and the forwarder node list, which is computed from the ETX metric (De Couto et al. 2003).
is called a coding vector. The sender attaches the following information in the packet header: the packet's coding vector (which will be used in decoding), the ID of the current batch, the IP addresses of the source and destination, and the forwarder node list, which is computed from the ETX metric (De Couto et al. 2003).
- Forwarders. Each forwarding node listens to all transmissions opportunistically. Whenever a new packet arrives, and if the node is in the forwarder list specified by the packet, it checks whether this packet is innovative. A received coded packet is said to be “innovative” if the packet is linearly independent from the packets of the same batch that have already been received by the node, which could be done using Gaussian elimination (Koetter and Médard 2003). If so, the packet's arrival will trigger a broadcast of a new coded packet by the node. To generate the new coded packet, the node computes a random linear combination of all the received coded packets in its buffer (from the current batch), which can be easily shown to be a linear combination of the K native packets. Assume that the node has already received packets of the form
 . A a new coded packet is created as
. A a new coded packet is created as  , where αj are random numbers. p′′ can be expressed as:
, where αj are random numbers. p′′ can be expressed as:

where (∑jαjcj1, ![]() , ∑jαjcji,
, ∑jαjcji, ![]() , ∑jαjcjK) is the coding vector of p′′.
, ∑jαjcjK) is the coding vector of p′′.
- Destination. The destination checks each received a packet to see whether it is innovative. If K innovative packets are received, it can decode the native packets by solving a linear equation:

where ![]() is the coding vector of
is the coding vector of ![]() , the ith received packet. As soon as all the K native packets are decoded, the destination sends an ACK message to the source along the reverse path to inform the source to move to the next batch.
, the ith received packet. As soon as all the K native packets are decoded, the destination sends an ACK message to the source along the reverse path to inform the source to move to the next batch.
The design of MORE considers several practical issues, such as how many packets a node should forward, when a sender should stop and purge and how a node codes packets efficiently. Interested readers are referred to Chachulski et al. (2007) for more details.
Note that, MORE also includes an extension from unicast to multicast. The idea is to find a multicast tree that is taken as the union of the shortest paths to each destination, using the ETX metric. The forwarder list of the multicast flow is the union of all the forwarder lists of the unicast flows. Experimental results show that, for multicast, MORE has a higher average gain in throughput compared with ExOR and traditional routing. Nevertheless, MORE is considered as inefficient when applied to multicast or broadcast because almost every node in the network may become a forwarding node, which may cause heavy congestion and packet collision (Koutsonikolas et al. 2009). Moreover, in mobile MWNs such as VANETs, tree-based multicast schemes fall short in that they incur large overheads in maintenance of the tree structure as the topology changes very fast. This calls for new design rationales for broadcast protocols in mobile MWNs based on network coding and opportunistic listening. In what follows, we will first introduce the mobile content distribution problem in VANETs and then present CodeOn, a content broadcast scheme for VANETs, which solves the above challenge by trading off structure for even more randomness than MORE.
