THE LOCAL AREA NETWORK (LAN) ADMINISTRATOR oversees all aspects of Internet and Web security administration. This chapter is for those professionals who don't have enough time to dig into the more technical aspects of Internet and Web security, but need reliable options for Internet protection. Here are practical instructions to get a firewall up and running at your organization.
Say you want to protect the small office/home office (SOHO) network of about 25 computers. Many firewall products are available for small businesses and those working from home. SOHO VPN hardware firewalls are often built on a secure virtual private network (VPN) connection to the company network to transfer e-mail and sensitive files. (For more information about VPNs and how a VPN connection works, see Chapter 14, Fundamentals of Network Security, Firewalls, and VPNs.)
In many cases the SOHO firewalls have additional features such as an antivirus tool, IP filtering, Web content filtering, router options (router/firewall combinations), intrusion detection, and DDoS/DOS attack detection. Some of the firewalls come with a Linux or Linux-like operating system and use ipchains to manage their filter rules.
A SOHO VPN hardware firewall is the best solution when you already have a working network and want to provide remote access. For example, you may already connect your personal computers within your office. If you want to open a new office in another location, you could connect both offices with a SOHO VPN firewall at each office. It will create a secure connection to transfer sensitive data (bank information, customer information, or company-related information) from one office to the other. Another example is a mobile worker such as a salesperson working in the field. The salesperson could use the VPN's secure connection to access company files and presentations or customer-related information directly from the company office, even when working in the field.
Recall that firewall allows you to restrict unauthorized access between the Internet and an internal network. It exists to block unauthorized connections and keep outside attackers from penetrating the internal network. It also prevents inside connections from reaching out to the Internet without authorization. By monitoring inside users, firewalls can prevent them from sending out to the Internet sensitive information, such as personally identifiable information or sensitive corporate data.
You have many choices for firewall applications. This section discusses one possible choice: SmoothWall, which supports many different network types and is a practical solution for just about any organization. SmoothWall uses colors to differentiate networks. A green network interface card (NIC) is a private, trusted segment of the network, while an (optional) orangeNIC is not trusted, but does share the Internet connection. A red interface is a connection to the Internet. This could be a conventional Ethernet adapter, a dial-up modem, Integrated Services Digital Network (ISDN), or a USB Asymmetrical Digital Subscriber Line (ADSL) or a conventional Ethernet adapter. Figure 13.1 illustrates this scenario. A purple interface indicates a wireless connection.
Key features of the SmoothWall firewall include:
Compatible with wide range of hardware and systems
Flexible and easy to use
Multiple network zones—Client local network (green), demilitarized zone (DMZ) for hosting servers (orange), wireless client (purple), and external (red).
Comprehensive reporting and logging capabilities
POP3 e-mail antivirus proxy
Web proxy support
Snort IDS support
Remote access and VPN support
DHCP and network time server support
Powerful traffic graphs and bandwidth bars
Inline proxy support for Instant Messaging (MSN, ICQ, Yahoo!, AOL) and VoIP with logging capabilities
Bandwidth management
Real-time graphs and traffic stats per IP
System update
Outbound traffic blocking with time-based controls
According to the National Security Agency (NSA), attacks to systems connected to the Internet are becoming more and more complex and more dangerous. For instance, hackers can penetrate computer systems using a variety of techniques to exploit weaknesses hidden in the complex code of many operating systems and applications.
Note
Tim Berners-Lee started the World Wide Web while at CERN (the European Laboratory for Particle Physics). The project sought to build a "distributed hypermedia system." The Web is a large collection of interconnected Web pages providing dynamic content documents, accessible throughout the world. Berners-Lee is still working on this project, now under the auspices of the W3 Consortium at MIT.
Internet-facing servers are accessible to people anywhere in the world that have Internet access, and these servers are often targets of attacks. This includes Web servers, e-mail servers, File Transfer Protocol (FTP) servers, and more. If a server has a public IP address, it's a potential target for hacker attack. Firewalls provide protection for Internet-facing servers. Firewalls also provide protection for internal clients. They provide a layer of protection to limit the ability of attackers to exploit system weaknesses—both hardware and software.
Imagine an organization that sells products over the Internet and processes credit card transactions. Customers insist that the merchant protect their credit card data. To do this, organizations need to address two distinct security areas:
Network security—Computers, hard disks, databases, and other computer equipment attached directly or indirectly to the Internet need protection. Firewalls serve an important role in this aspect of network security.
Transaction security—Web servers must be able to securely complete private transactions with other entities in databases accessible on the Internet. Hypertext Transfer Protocol Secure (HTTPS) is an important tool used to encrypt the transactions. Additionally, firewalls provide protection for the data. For example, it's common for a Web server stand behind one firewall. The database server stands behind a second firewall that restricts access to the database to only the Web server. When the Web server stands between two firewalls like this, the area where the Web server operates is called a demilitarized zone (DMZ).
Network security and transaction security have four overlapping types of risk:
Risk that unauthorized individuals can breach the server's document tree. Depending on what data resides on the server, this threat can compromise the confidentiality of documents stored there.
Risk that transaction data can be intercepted. This threat can include personal data, financial data, or credit card information.
Risk that information about the server can be accessed. If attackers learn details about the server, such as type of server and its operating system, they may be able to identify and exploit its known vulnerabilities.
Risk of denial of service (DoS) attacks. Many different types of DoS attacks are possible. A simple SYN-flood attack withholds the third packet in the TCP three-way handshake, for example. Hundreds of these incomplete sessions in a short time can consume substantial resources on a server and even crash it.
If your organization conducts business on the Internet, you need to take steps to protect those transactions. E-commerce requires a zero tolerance for failure. Protection is not optional.
An organization must protect against attackers trying to access information and resources within the internal network, such as servers and workstations. Servers can host massive amounts of data that's invaluable to attackers. Database servers may host personally identifiable information (PII) about customers including their credit card data. Domain Name System (DNS) servers host information such as the IP addresses and names of all systems in the network.
Most organizations have a written security policy that outlines specific security requirements. A firewall can be useful in upholding the security policy by providing perimeter security. In other words, the firewall limits the risk of attack from hackers outside the internal network.
However, if you want to guarantee the security of an organization's network and protect its clients' and users' interests, you should do the following as well:
Treat private messages as confidential—Private messages should be encrypted to ensure the message remains confidential. Encryption prevents the unauthorized disclosure of the private message.
Maintain integrity of information—Integrity methods verify that data has not changed. For example, hashing is often used to verify integrity of messages. A hash is simply a number calculated using an algorithm on a message. No matter how many times you calculate the hash, it will always be the same as long as the data has not changed. The hash is calculated at the source and sent with the message. The hash is recalculated at the destination on the received message and compared with the hash sent with the message. If they're both the same, the integrity of the message is assured.
Use strong authentication and non-repudiation methods for all transactions—Digital signatures commonly accompany both authentication and non-repudiation. For example, a sender can sign a message with a digital signature. The receiver can use this signature to verify the identity of the sender. In other words, the digital signature provides authentication. Additionally, since it was digitally signed, the sender can't later deny sending it. In other words, the digital signature also provides non-repudiation.
It's more difficult to preserve a user's privacy on the Internet than in the physical world. Usually, you can close your door when seeking privacy or whisper something, so that others can't hear you. But the digital era has changed things. There's no such thing as whispering on the Internet.
When data is sent or received by a user surfing the Internet, that information can be intercepted and collected. Much of this data is stored in databases and can be made available for sale to others. Data mining methods are then used to help build customer preference profiles. From the perspective of an organization selling products, this data is valuable for identifying an individual's buying habits and targeting advertising. However, this data can be easily misused.
The Electronic Privacy Information Center (EPIC) was established in 1994, in Washington, DC. It's goal is to alert the public on emerging privacy issues relating to the National Information Infrastructure (NII), such as the Clipper Chip, the Digital Telephony Proposal, medical record privacy, and the sale of consumer data. EPIC's mission is to preserve the right of privacy in the electronic age as well as to give individuals greater control over personal information, and to encourage the development of new technologies that protect privacy rights. EPIC can provide valuable information to IT Professionals on emerging cyber laws and other privacy threats.
Tip
If you want to know more about EPIC, you can check out its Web page at http://epic.org/
Preserving privacy on a corporate network may require more stringent security if you have users accessing resources from all over the world. While administrators have the responsibility for setting up security policies to guarantee users' privacy, each user accessing the company's network is responsible for browsing the Web with ethical regard for others. They also should be aware of information they may reveal while accessing resources from outside of the network. This will be discussed in Chapter 14, which focuses on VPNs.
Typically, most network servers (and Web servers) log all the hits they receive. This log usually includes the IP address and/or the host name. If the site uses any form of authentication, the server will also log the username. If the user filled out any form during the session, all the values of any variable from that form will be also recorded. Status of the request, size of data transmitted, user's e-mail address and so on can also be logged. Moreover, Web servers can make all this information available to Common Gateway Interface (CGI) scripts. Since the majority of the Web browsers are running on single-user PCs, very likely all the transactions can be attributed to the individual using the PC.
Revealing any of this information can harm the user. This is especially true if the user has logged any PII. Attackers can use PII for identity theft. Some PII may allow an attacker to access bank accounts or fraudulently charge credit cards. As a subtler example, if a user researches a job opening opportunity at a site, it may indicate that the user is searching for a new job. Browser lists, hotlists, and caches can also reveal certain patterns about the user.
A proxy server, for instance, will track every single connection outside the Web by IP address and the URL requested. If you install a proxy server within an organization, data needs to be protected so that only authorized individuals have access to it.
When deciding to install a firewall, you should consider several basic decisions before going ahead with the project.
Before you start thinking about the type of firewall you want to use, where to install it, and how to deploy it, you should make sure you have a guideline in hand. You need a policy that will set the security standards for the network including the rules users and system administrators will follow, and the security strategy configuration you plan to deploy.
Many security policies have a special section just for the firewall, outlining how to configure and use it. For example, many organizations recognize that every service and protocol allowed through the firewall represents a risk. By blocking traffic that isn't needed to support the organization, these risks are eliminated. A simpler route is to just monitor the activity at the network and Web server, but it may subject the network to risks you can easily avoid.
Be prepared to face a situation where the final design of the firewall may involve political issues from upper management and other departments of the company. For example, the security policy may state that the Network News Transfer Protocol (NNTP) is not essential for the organization. You would then design the firewall to block all NNTP traffic. Even though it may not be essential, upper management may decide to allow the traffic.
Once you decide on the design, then you need to identify a firewall that can meet your needs. You'll need to consider several items including:
Suitability—Can the firewall implement the policy?
Flexibility—Is it easily reconfigurable?
Training—Is training required and if so, what is the cost?
Need—Make a list of traffic you want to allow, filter, or block. This is often derived from the organization's security policy.
Risk—Make a separate list of all the risks in the network based on the traffic allowed.
Cost—Last, you need to add the two lists up and find out how much it will cost to provide everything. You then need to divide this result by available financial resources and you will have a clear picture of how much it will cost to implement your ideal firewall system. The result may even point out the likely type of firewall you must purchase. Many times, you'll find you need to re-evaluate your needs so that the plan is more realistic, from both the security and financial perspectives.
You can recommend a firewall solution that costs almost nothing or a solution that may cost hundreds of thousands of dollars. You need to balance the security needs with the resources within your organization.
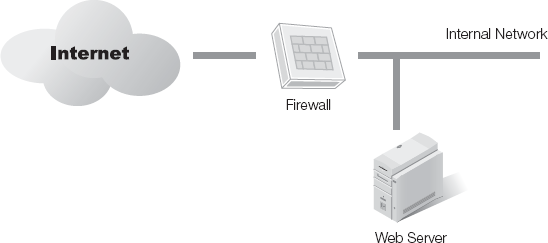
On the technical side, you need to decide how you to configure the firewall and what strategy you'll use. Figure 13-2 shows a simple firewall solution with one network firewall and all resources placed behind it.
This method is generally not recommended for organizations that host Internet-facing servers such as e-mail servers or Web servers. These servers can go behind this single firewall and you can configure the firewall to direct Internet traffic to the servers using port forwarding. However, this exposes the internal network to potential threats from the Internet. If you instead put your Internet-facing servers directly on the Internet, you expose them to threats of attack from anywhere in the world.
An alternative for organizations that have Internet-facing servers is to use a perimeter network. Figure 13.3 shows one example. The firewall has three connections: one to the Internet, one to the internal network, and one to the perimeter network. This is also known as a bastion host.
In this solution, the firewall will direct traffic destined for the Internet-facing servers to the servers on the perimeter network. Unrequested traffic from the Internet will be blocked from entering the internal network.
The third solution uses two firewalls to create a DMZ as shown in Figure 13.4. This provides several benefits. The two firewalls provide an additional layer of security for the internal network. If the Web server accesses a database, the database server can go in the internal server for better protection. Internet users won't be able to access the database server directly.
Many organizations use two different brands for their different firewalls. If a flaw or vulnerability appears in one, it's unlikely the second firewall will be vulnerable at the same time. Additionally, an attacker may be an expert on one brand of firewall, but it's less likely that the attacker has the same level of expertise for two separate brands.
Remember, though, you need to balance the needs of the organization with the security requirements. While it's a true a DMZ provides more protection than a single firewall, it also costs more.
Before you select a firewall, you should make sure that your organization has created a written security policy. You would then select the firewall that can fulfill and comply with the policy. When evaluating firewalls, take the time to evaluate the levels of security they provide. Quite simply, some are better than others, and a high cost doesn't necessarily mean high quality.
The basic concept of any firewall is the same, so you should evaluate a firewall based on the level of security and features it offers. First and foremost, the firewall should be able to fulfill and comply with your security policy. Some other characteristics to consider are:
Security Assurance—Independent assurance that the relevant firewall technology meets its specifications.
Privilege Control—The degree to which the product can impose user access restrictions.
Authentication—The ability to authenticate clients and allow different types of access control for different users.
Audit Capabilities—The ability to monitor network traffic, generate logs, and provide statistical reports. Logs may include both authorized traffic and unauthorized attempts and may be able to trigger alarms in response to certain events.
When considering the features, consider the product's ability to meet the needs of the organization. A good firewall product should provide:
Flexibility—The firewall should be open enough to accommodate the security policy of your organization, as well as allow for changes. Security policies can change, and security procedures should also be able to change and adapt to different needs.
Performance—A firewall should be fast enough that users don't notice the screening of packets. The volume of data throughput and transmission speed associated with the product should be reasonable and consistent with the organization's network bandwidth to the Internet.
Scalability—Firewalls should be able to handle additional workload. The additional workload can be due to growth within the organization or due to increased use of the Internet connection.
When considering integrated features, consider the ability of the firewall to meet your network and users' needs. This includes:
Ease of use—The firewall product should ideally have a Graphical User Interface (GUI), which simplifies the job of installing, configuring, and managing it.
Customer support—Vendors that sell firewalls provide support for them. This includes providing prompt access to technical expertise for installation, use, and maintenance. It also includes training.
As mentioned previously, one of the main advantages of SmoothWall is that it will run on a variety of hardware. It's recommended you use a machine that is 166 MHz or faster. In any case, you will need at least two network cards (NICs) in your SmoothWall machine, as firewalls traverse two or more network connections. You may or may not need a crossover cable as well. The Dell Powerconnect 2650 switch performs auto-sensing, so there is no need to use a crossover cable. This is common with many switches today. Figure 13.5 depicts the topology of SmoothWall.
The minimum requirements for a computer running SmoothWall are:
As a software appliance, SmoothWall will convert a computer server or PC into a dedicated hardware security appliance, running the security-hardened Linux operating system and all other necessary software. When planning a firewall, you should use standard hardware, typically from major manufacturers such Dell, HP, or IBM, which will provide you with considerable benefits including:
Flexibility—You can easily add RAID, redundant power supplies, additional RAM, and a range of network interface cards.
Performance and value for the money—The average desktop PC will have many times the processing power and memory complement of most mid-range hardware firewall appliances. Office PCs have become a commodity, offering exceptional value for the money.
Support—The major PC manufacturers can support their products virtually anywhere in the world, including rapid, on-site repair or replacement if the customer requires. Alternatively, in most major cities, several computer support companies also support such hardware. In contrast, the support available for smaller manufacturers' equipment is often limited to repairs done after you've had to ship the machine back to the factory.
What kind of firewall is right for an organization? Truthfully, no single correct and definite answer exists. A security policy developed by a Fortune 500 company certainly will not be suitable for a small business owner.
The following are brief fictitious scenarios, to illustrate different firewall designs to meet different needs.
Employees at Other People's Money, Inc. (OPM) access the Internet on a daily basis for a wide variety of different business purposes. Additionally, they host a Web server that has a high volume of access from OPM customers. Finally, mobile workers use a VPN server to access internal resources.
OPM might decide a DMZ with two application-level firewalls (see Chapter 14, Fundamentals of Network Security, Firewalls, and VPNs) and packet filtering adequate for its needs. The Web server and VPN server would go in the DMZ so that they are accessible from the Internet, but the internal network has additional layers of protection.
Imagine a smaller organization that requires Internet access by employees, but doesn't host a Web server or a VPN server. All users in the organization require access to the Internet, and they need a layer of protection against Internet-based attacks.
A proxy server or a firewall such as SmoothWall would be enough. All users could access the Internet through the SmoothWall firewall, and it would provide protection against external attacks. While SmoothWall was the example examined in depth in this chapter, many other products can provide the same level of service for a small organization.
Imagine a larger organization with multiple subnets. They may want to limit specific types of traffic within subnets. For example, they may want to ensure that traffic within a specific subnet is encrypted with IPSec. Additionally, they may want to allow NNTP traffic on one subnet, but not on others.
You can configure routers to provide basic packet filtering. In other words, they can block or allow traffic based on IP addresses, ports such as port 119 for NNTP, and some protocols such as ICMP or IPSec.
If the organization wants to protect subnets within the network, basic packet filtering provided by routers might be the most appropriate choice. This model supports each type of client and service within the internal network. No hardware or software modifications or special client software would be necessary. The access through the routers used as packet-filtering firewalls is transparent for both the user and the applications. The existing routers can handle the packet filtering. This solution doesn't require the purchase of a host or firewall product. Buying an expensive UNIX host or firewall product would be unnecessary.
The installation of SmoothWall is easy. As long as you ensure you have the computer BIOS set to boot from a CD, the installation process will begin automatically.
SmoothWall Express runs on a workstation with a bootable CD-ROM drive. After booting, it will automatically check the workstation and hardware components.
Warning
During the installation process SmoothWall will delete all data you may have on your hard disk. So, before you start the installation, ensure that all valuable data is safely backed up.
The common interfaces on the installation screen of SmoothWall are listed below:
Red—Internet. This interface is protected by the
iptablesfirewall rules.Orange—Filtered/Special Purpose. This is commonly used for a DMZ or other special section you want to allocate.
Green—Trusted network. All traffic is permitted to and from this interface.
Note the green + red configuration. The green interface card connects to the internal network and the red interface to the external network. If you have a different setup or hardware, please use the appropriate configuration.
At this point, you should read the information that appears on the following screen and hit the enter key on your keyboard.
At this point you should see the screen alerting you that your hard drive will be prepared for installing the firewall.
If you have two of the same NICs, you may want to pay attention to the Media Access Control (MAC) addresses so you know which cable to connect to the modem and which one goes to your switch. If your red interface connects to an ISP, ensure you configure it based on the requirements of the ISP. For example, some ISPs will assign manual IP addresses, while others use DHCP. When DHCP is used, all the Transmission Control Protocol/Internet Protocol (TCP/IP) configuration information such as DNS, gateway, and IP address happens automatically.
The green interface should have a static IP (such as 192.168.0.1) to connect to the internal network. Once you have the interfaces setup correctly, it's time to reboot the computer. Also, it's very important that you power-cycle the modem. Often ISPs will assign a different IP when the MAC address of the device attached to the modem changes.
Tip
An excellent Web site is available that will walk you step by step through SmoothWall installation. Just check http://www.linux-tip.net/cms/content/view/316/26/
When configuring the NICs for the green and red interfaces, you can use static IP addresses for both interfaces.
Now you will need to set up the DNS and Default Gateway accordingly.
Now enter the SmoothWall admin password. You will need it for logging into the Web interface later. Then, setup the root password.
At this point the setup of SmoothWall is now complete and your network should be protected. You should see a screen showing that the installation is complete. Now, remove the CD and restart SmoothWall.
Once you have finished installing SmoothWall, you will have to configure the firewall via a Web browser. The interface is clean and well laid out, and works well with Mozilla Firefox, Google Chrome, and Microsoft Internet Explorer. Once you reboot the computer, you can access it via a browser from a Web interface (usually https://192.168.0.1:441) to start configuring the firewall. SmoothWall Express version 2.0 added the ability to use HTTPS. You can also access it using port 81. Without logging in, you should be able to see part of the management menu, the version, and load averages.
Since the install connected the red interface to the Internet, your first access of the home page should lead you to the following message: "There are updates available for your system. Please go to the 'Updates' section for more information." You will find the Updates menu item under Maintenance.
At this point, if you want to verify or change anything, you must log in. During the configuration process you were asked to specify some passwords. To log in to the Web interface, you must use "admin" as the user name and the password you specified. Logging in as "root" will work only over Secure Shell (SSH) or from the console. You cannot log in as "root" using the Web interface.
For most scenarios, the out-of-the-box SmoothWall installation should work without any additional configuration. But additional customization can bring out the real power of SmoothWall features. The Services tab allows you to monitor each advanced feature, including time, remote access, intrusion detection, dynamic DNS updates, and proxy services. Some services such as SSH access services are not started by default. Interestingly, ICMP is configured to reply to both external and internal ping requests, making the firewall susceptible to DoS attacks.
The Networking tab exposes the interface settings, IP address blocking, timed access, and traffic rules. Incoming and outgoing rules are easy to create and maintain. You can view the status of the system at all times with various options. Configuration and resources appear in text form. You can also view a summary screen of all the services running on the SmoothWall system (computer).
In the quality of service (QoS) configuration section, you can use drop-down boxes to select upload and download connection speeds and enable the service. The QoS engine prioritizes different types of traffic to make the connection speed seem faster. The settings are combo boxes, which makes them understandable even to non-technical users. By default, instant messaging traffic is set to low priority, VPN traffic to normal, and gaming traffic to high.
At this point, you should start thinking about deploying the firewall and think about the services you want it to run. You should pay special attention to the services tab. You have the ability to run:
Web Cache/Proxy (SQUID)
DHCP Server
DDNS (for dynamic IPs)
Intrusion Detection System (Snort)
Secure Shell (Open SSH)
To enable the Web proxy, you must select it by checking the box. The Web proxy information needs to be changed.
The "Transparent" option simply means that every client on the network will be forced to connect through the proxy server. Browser settings will not need to be changed, and the clients will not even know they are using the proxy. You should change the cache size from 50 to 5000 MB. You shouldn't change the other options, as caching objects too large or too small can create problems.
One of the great features of SmoothWall is the ability to view network usage. You can view graphs of network traffic generated by Round-Robin Database Tool (RRDtool) every five minutes.
You can also view the logs of Web usage through the proxy. You can even dig further by filtering the log by IP. This way, you can see all the Web sites visited by a certain IP (or user).
To test SmoothWall's ability to mitigate attacks, you can enable Snort intrusion detection software and run a few attacks against the firewall over the red interface. For example, you can use NMap, the Metasploit framework, and some other port scanning and attacking tools. In all cases, the firewall should be able to deal with them. The Snort and firewall logs should identify most types of attacks, the IP address of the attacker, and the time and date of the attack. SmoothWall's IP lookup feature can determine and report the origin of an attacker.
Tip
ICMP may be blocked by the host you ping. If the ping fails, consider pinging another host that you know will respond.
Once SmoothWall is up and running, the next step is to test its ability to access Internet resources. You should first ensure you can access the Internet from the SmoothWall box. To do this, run the following command: ping www.google.com
If you get a successful reply, it means your host can access the Internet.
Now, if you have an internal client configured, try to ping one by running the command, substituting the actual IP address of an internal client. An example would be Ping 172.16.0.1.
You can also test a client's ability to traverse the firewall. Start a Web browser on a client system and enter the IP address of the SmoothWall router. For example, if the IP address for the green NIC on the SmoothWall machine is 172.16.1.95, then you would enter http://172.16.1.95 in the location bar of the browser. You should be able to see the SmoothWall startup screen. If you see the screen, then the firewall is up and running. Next, try to access any Web site to confirm that you can surf the Internet. If you encounter problems accessing the Internet, try checking the following:
Check the TCP/IP settings on the SmoothWall host. Make sure all of the addresses and subnet masks are correct.
Make sure the NIC accessing your ISP (red) is the correct card. Some ISPs will provide access only when the MAC address on the NIC is correct.
Check the TCP/IP settings on the client computer.
Sometimes, right after installing SmoothWall, you may have problems being able to SSH into the system. This is typically because port 22 is not open. In this case, you should make sure that SSH is enabled and that port 22 or 222 is open. This enables you to tunnel different SSH connections at the same time.
One small disadvantage with using SmoothWall from the console is that some traditional Linux tools are modified. For example, some shell commands such as whereis and locate are not included, which can make it a little hard to find items. Also, config files are stored in non-traditional Linux locations, and partitions are not named according to standards. For instance, the snort.conf file is stored in /etc and the squid.conf file is stored in /var/SmoothWall/proxy.
If you are still having trouble with the networking aspect of the firewall during the configuration process, you still have access to traditional tools such as ping, traceroute, and tcpdump. They are all useful in determining what your network problem may be. Another factor to watch for is the crossover cable. Some networking devices require a crossover cable when they are connected together, while others have auto-sensing capabilities and will automatically switch to crossover mode even when you're using a regular cable. The cable from your green interface may or may not need to be a crossover cable.
While SmoothWall does not natively contain an FTP server, you can still transfer files to and from the system via SCP/SFTP. To do so, you simply need to connect to port 22 or 222 with a client such as WinSCP3, which is nearly the same as using another FTP client.
SmoothWall is a versatile product that gives power to network security administrators, allowing them to decide how to control their networks by making it easy to do so. The Web-based GUI is clean, easy to read, and provides a wealth of information about the status of a network's traffic and security.
The Web-based interface is organized into broad areas with tabs that allow navigation for specific features. You can run SmoothWall as a proxy server, or a DHCP server, or forward ports to machines in the green zone, and more. You can even set up advanced proxy server features such as per-user authentication or delay pools. Larger organizations may want to use a dedicated proxy server to get these functions, however.
You can configure the address range, WINS server, and static hosts for the DHCP server. You can specify dynamic DNS, offer remote access for SHH, and synchronize with a Network Time Protocol server. SmoothWall also lets you enable Snort, a popular open-source intrusion detection system.
Some of the network settings you can control include:
Port forwarding—This allows you to forward a port from the firewall to a machine inside the green or orange zones. You can use this feature to hide your Web servers behind a single IP address.
External service access—You can access any services running on the SmoothWall machine by opening the ports you need.
DMZ pinholes—As the name implies, this allows you to open a pinhole from the DMZ to the green zone. This is useful if your external servers need to communicate with servers inside the green zone. For example, your Web server may need to communicate with a database server inside the green zone.
PPP settings—You can set up various profiles, configure up to four modems, and use dial on demand.
You must keep the firewall and your protected network logically secure. Sound security logic should be the starting point in putting together a security policy that will use secure systems such as Kerberos, IPSec, and many others. The requirements to run a secure firewall, such as SmoothWall, also include a series of "good habits" that administrators should cultivate. It's a good policy to try to keep the strategies simple, so that the system is easier to maintain.
Most bastion hosts and firewall applications, have the capability to generate traffic logs. You can record user-browsing patterns on these servers, this may include information about the users, their connections, their address, or even specifications about their organization. These logs usually include:
The IP address
The server/host name
The time of the access
The user's name (if known by user authentication or, with UNIX, obtained by the
identdprotocol)The URL requested
The data variables submitted through forms users usually fill out during their session
The status of the request
The size of the data transmitted
Firewalls provide protection to servers and work stations from Internet threats. They can be configured to allow only specific traffic based on what an organization wants to allow. Organizations typically define what traffic is acceptable in a comprehensive, written security policy. IT professionals then identify a firewall solution that can fulfill and comply with the policy within the established budget.
SmoothWall Express is an Internet firewall that can protect an organization's network. This chapter demonstrated how to configure and use a firewall such as SmoothWall using a Web-based GUI. SmoothWall is an open-source firewall, requiring no knowledge of Linux to install or use. SmoothWall purposely to turns any typical PC into a network appliance whose sole function is to route network traffic to and from the Internet, assign IP addresses, and protect the private side of the network from intrusion.
Asymmetric Digital Subscriber Line (ADSL)
Clipper Chip
Common Gateway Interface (CGI) script
Domain Name System (DNS)
Electronic Privacy Information Center (EPIC)
Integrated Services Digital Network (ISDN)
Kerberos
National Information Infrastructure (NII)
National Security Agency (NSA)
Round-Robin Database Tool (RRDtool)
Synchronous dynamic random access memory (SDRAM)
tcpdumptraceroute
The following are all key features of SmoothWall,except:
POP3
Static and dynamic DNS support
Cybercash support
Snort IDS support
DHCP and Network time server support
According to the _______ _______ _______, attacks to systems connected to the Internet are becoming more and more complex.
National Systems Agency
National Security Agency
Central Intelligence Agency
Navy Security Agency
Federal Bureau of Investigation
Firewalling involves two distinct areas that must be protected:
Network and transaction security
Access and controls
File sharing and printing capabilities
Access to the Internet and from the Internet
None of the above
The _______ was created to alert the public on the emerging privacy issues relating to the National Information Infrastructure.
EDIP
EPIC
NII
CERN
W3C
The following are characteristics we should be looking for in a firewall, except:
Security Assurance
Privilege Control
Digital Switches
Authentication
Audit Capabilities
A good firewall product should provide:
Flexibility
Performance
Scalability
All the above
A and C
The following are all characteristics of SmoothWall firewall, except:
It is a simple Linux kernel
It cannot use iptables to control and route traffic
It is built to run as a dedicated firewall/router
It provides a way to gain extra capability with NAT
It runs on a variety of hardware
The following are all common interfaces used by SmoothWall, except:
green: Trusted network
blue: DMZ connection
red: Internet
orange: Filtered/Special Purpose
The following are attributes of a minimum hardware specification to run SmoothWall, except:
512 MB PC133 SDRAM
20 GB hard drive
10/100 on-board NIC
AMD Duron 1100
Flat LCD screen
To install SmoothWall, you need to make sure the computer BIOS is set to boot from a CD. True or False? _______
In a typical SmoothWall firewall installation the green interface should have:
A static IP
Software bugs but not flaws
Dynamic addressing
Proxy servers connected to it
Internal code connecting to an external
When configuring the NICs for the green interface, it is advisable to use _______.
capacity planning
maximum utilization
a static IP address
wirespeed settings
factory defaults
Which of the following is not related to SmoothWall offered services?
Web Cache/Proxy
Fingerprint authentication
DHCP Server
DDNS
Intrusion Detection System
What does the "Transparent" option means when configuring Web proxying in SmoothWall?
It allows you to create a tunnel mode
Every client on the network will be forced to connect through the proxy server
Every client on the network will be waived access to the network
The proxy server is on stealth mode
Collisions on the network are not seen
SmoothWall does not work well with Mozilla Firefox and Google Chrome. True or False?
The following are services found in the service tab of SmoothWall, except:
SQUID
Web Cache/Proxy
DDNS
Diskcopy
SSH
The following are tools we can use when troubleshooting a firewall installation, except:
pingtracerouterobocopyipconfigtcpdump