CHAPTER
7
Operational Deception

Today’s computer network security industry operates like this: They go up into the observatory and look at the stars. They look into the night skies and see the stars and refuse to accept what they are looking at happened billions of years ago, not just a few moments ago. Computer security “experts” today sit and look at the activities that have happened on their network and refuse to accept that the damage is done and the event is over. Once they see it, it is too late. They look at defending their networks all wrong.
—Angelo Bencivenga, Chief of the Army Research Lab Computer Incident Response Team
By now you have come to understand how counterintelligence and deception have been used in traditional military and corporate life. You have even learned about some of the tools and methods you can use to engage an active threat within your or your customer’s enterprise. Now we need to switch gears a little and give you some tales that were interpreted by two individuals based on professional experiences.
There are ways for you to construe a perfectly perceptually consistent deception plan for the enterprise you are defending, and as long as it is written on paper offline, cyber threats would almost never have access to that information until they have moved into your deception (or if someone spills the beans in an e-mail—executives and line managers are infamous for these type of ego trips among peers).
Deception can come in the form of a single e-mail from a compromised system all the way up to the creation of an entire program that cost billions of dollars to build just to deceive adversaries into backing down or expending their resources in the wrong ways. Misdirection, diversion, and engaging of a threat are essential when working with deception.
In this chapter, we are going to talk lightly about some recent events where misdirection, diversion, or engaging a cyber threat would have resulted in success instead of epic failure, waste, and abuse. OPSEC is also a factor in whether threats can walk into your organization unquestioned, social engineer their way in, or simply dive through your trash looking for anything of interest.
NOTE
The ideas, conclusions, and opinions expressed in this chapter are those of the author. They do not reflect the official position of the US government or the Department of Defense. You also need to be aware that the tales that are included in this chapter are true stories that have been rewritten to protect the names of the innocent and guilty (even though we know who both of you are).
Deception Is Essential
The computer security business in both the public and private sectors is led by an important and influential group of people who know so little about so much. Vendors and governments worldwide parade such terms as governance, enterprise solutions, and compliance, pushing products, solutions, and regulations to try to protect us from all manner of viruses, spyware, hackers, and APTs. We are courted and married off into long-term commitments with antivirus and spyware companies promising the best protection against every kind of known and unknown threat you could find on the Internet today and tomorrow. The problem is that all these computer network defense tools are lagging and responsive defense products, meaning that they operate on what has already occurred. Something must have occurred in order for the company to build a signature or identify an IP address and label it as “bad,” or the detection engine must have enough anomalous information for the heuristics to compute a solution.
Companies do not have premonitions regarding the next exploit that is going to wreak havoc on the multitude of devices connected to the digital world compassionately called the Internet. There is no soothsayer on staff at McAfee or Kaspersky Lab, and no fortune-tellers at Symantec to warn the industry about the next logic bomb or zero-day attack. The truth is that reactive defense can offer only so much protection. Is it important? The answer is unequivocally yes. Does any antivirus company guarantee that you will not get infected? Does any company promise that if you use its product, you will not get hacked? Is there a money-back guarantee if a virus destroys your computer, router, network, product line, or corporation? What guarantees are given at all, and what good would a guarantee be if you got one from these folks anyway?
More often than not, the computer defense and IT security industry offer a “feel good” product line of solutions. Most nations around the world spend billions of dollars on security each year, only to be repeatedly hacked and exploited. Private corporations who offer solutions and are industry leaders in computer security are not exempt either. HBGary suffered a big loss when the company’s system was hacked and had thousands of internal proprietary e-mail messages posted on the Internet. In 2009, both Kaspersky and Symantec had their secure sites penetrated by a SQL injection attack. These are some of the international leaders in computer security succumbing to fairly rudimentary attacks. How secure are they? How secure can they make you? Who really knows?
In September 2007, the US Department of Homeland Security (DHS) made headlines when hackers compromised its unclassified systems. In 2008, DHS made headlines again when a hacker broke into its Voice over IP (VoIP) phones and made more than 400 calls using the Federal Emergency Management Agency (FEMA) PBX. And what was the response from the agency with the charter to protect our digital homeland? It was the same as the rest of the US federal government and every other government out there. They will agree that it is an issue, allocate more money, and pat each other on the back for solving the problem once again. The end result is diminished resources and no reduction in exploitation of vulnerabilities. When was the last time a CEO or CIO was fired because a company lost significant proprietary information? Most don’t think they have ever seen that, but the day is long overdue to really get serious and stop throwing money at a problem that is very difficult to fix with our current network defense mindset.
There’s no such thing as “secure” any more… The most sophisticated adversaries are going to go unnoticed on our networks… We have to build our systems on the assumption that adversaries will get in…
—Deborah Plunkett, Director of the National Security Agency’s Information Assurance Directorate (in comments at a Cyber Security Forum held by The Atlantic and Government Executive)
In January 2002, Bill Gates, the then CEO of Microsoft, declared that Microsoft would secure all its products and services, and initiated a massive training and quality control program. Just seven short years later, the Conficker virus infiltrated and devastated millions of Microsoft PCs around the world.
Here is a network defender at his best—imagine a town in the Wild West, the streets are empty and two lone gunmen face off. The first is the net defender, the second is the adversary. As the clock strikes high noon, the adversary draws his revolver, the net defender waits for something to happen. Once the adversary fires the first six shots, he reloads and shoots six more shots, the net defender is mortally wounded but is now ready to draw. He raises his revolver with great speed and loads his arrows. With blurred vision and eyesight failing, he takes aim and wildly fires off a round or two before collapsing.
—Angelo Bencivenga, Chief of the Army Research Lab Computer Incident Response Team
Over the past few decades, as society strives to push the bar ever higher for connectivity and accessibility, computers and other components of information technology are further interconnected into a global network we call cyberspace. In doing so, computers are able to reach and access more information in more corners of the world than was thought possible a generation ago. Someone from Berlin can research and discover the lives of the Betsilego (indigenous peoples of Madagascar), just as easily as they can walk to the kitchen to get a drink of water. Our vast digital world has much to offer the casual participant, but it is also a playground for those who have other nefarious designs. The magnitude of threats from random attacks is eye-opening; the threat from targeted attacks is alarming. To counter the known and unknown threats, many different technologies and concepts have been employed, with billions spent each year by private companies and governments around the world.
Everyone should and must have an identification, or internet passport … The Internet was designed not for public use, but for American scientists and the US military. Then it was introduced to the public and it was wrong … to introduce it in the same way.
—Yevgeniy Valentinovich Kasperskiy (Eugene Kaspersky), The Register article (October 2009)
Inherently, the overall design of how hardware and software are integrated is flawed because of the origins of the Internet. The intent was never to bring it to the public. It was designed for government use to facilitate collaboration among scientists. The designers of the ARPANET could not have foreseen how it would evolve over 40 years later into what it has become today. When the first message was sent in 1969, security was not a discernable blip on the radar. How things have changed so drastically over the years.
The bottom line is that the playing field is not level. Computers and the Internet operate in such a way that they are easily exploited. Everything from the configuration of a desktop CPU to the connections that link our computers with those in Pakistan or Brazil fosters an environment that is uncontrollable. Is that not obvious? Tracking someone who has infiltrated your home computer is akin to putting on a blindfold and chasing someone in the snow when its 95 degrees outside. Let’s face it: unless we think differently, network defenders will keep reading the newspaper articles and blogs in which smart people pontificate, opine, and admire the adversary. They are amazed at the adversary’s exploits and stand in awe of what has been accomplished, imagining what will come next with a haughty, strange, disgusted, doomsday-ish astonishment. Network defenders ogle at the techniques, and discuss, analyze, and digest the components of an attack as if they were living vicariously through the adversary. Why is this? Why don’t we unleash hell on our aggressors and do to them what they are doing to us?
Another drawback in operating unfettered on your own network or on your company network is management. In many ways, an organization’s real problem is understanding the situation. Most people think that the problem is the problem; however most managers, through a lack of technical or leadership skills, cannot even define the problem. This leads to a schism between frontline workers and management addressing the problem. Now that we understand what the real problem is, we must then understand and accept that management is ill-equipped to design a functional solution to the problem.
Much may be said and done, even before the first solution is out of the gate. This may work well in some environments; however, with deception, there is an inherent danger in portraying the wrong information. Facts are facts, and they do not change. If a deception story is played out, it may be received by the COG (target of the deception) in one way or another. How the COG receives the message, how it is interpreted, and how it is perceived play a huge role in what the next step will be. Perception may change what a piece of information means to the deception target, but it will not change the information itself.
Deception is about psychology, not technology. Of course, technology is an enabling capability, as are numerous other vehicles, but the real answer comes from the deception theme: the message you want brought forward and the actions you want the adversary to take. No special technology is needed to influence a person’s decision-making process. Deception is also cultural, as are all types of information operations. This is a concept that Deborah Plunkett (Director of the IAD at the National Security Agency), the private sector, and governments around the world are not grasping. Hacker groups can be great at technical exploits, and many are. They also are very good at the psychological aspect: the rich Nigerian banker who needs help in cashing in a fortune, a dying child suffering from a rare case of cancer, and countless others that have made their rounds in inboxes around the world. These appeal to the human side and entrap the recipient with a strong urge to know what it is all about.
Additionally, private industry is great at getting people to pay for things they can get for free. Many people are overwhelmed, intimidated, lack the technical skills, or are just too lazy to research possible solutions on their own. They are more than happy to rely on a third party to tell them what they need or don’t need to solve the problems they may or may not have. In these cases, different companies will happily collect as much of your capital as you will part with to do something most people could do on their own. Few are good at operational deception because it goes beyond our everyday little white lies and self-preservation comments of half-truths, incomplete truths, and facts of omission.
The computer security industry is in dire need of a true leader—not a CEO or federal figurehead, but someone who can stand up and knock the ball out of the park. Operational deception is an art, and as such, must weather the scientific storm of analysis, scrutiny, and exposure to achieve its goal.
Simple is best. There is no need to create an elaborate story when a simple one will do. You do not want a very complicated story that the target and everyone who has his ear (conduits) can misunderstand, and then perhaps act in a way detrimental to your situation. Besides, when people are faced with a complicated situation or problem, they simplify it in order to understand it. If you create a complex deception message, it will just get translated into a simplified version and reassembled later on.
Here’s a game you might remember. As children, we played a game where a message initiated from a note was to be verbally passed on from person to person. We had roughly ten children, so the story was told and retold time and time again. When everyone told the story, we all turned to the last person to receive the message. This unlucky child had to recite the message in front of everyone. Unfortunately for him, the message did not resemble the initial message in any way, shape, or form. How did that happen? How bad would it be if your deception message needed to go through five or six people to get to the COG? How much worse if you had developed a complex story! Your intentions may not be realized by the deception target because the target may never hear what you are really saying.
Tall Tale 1
Bob liked Alice. Alice knew it, but no one else at Network Unconventional Threat, Inc. (NUTS, Inc.) knew about the office romance. They had worked for several months on closing a deal that had the potential of landing them big promotions and a life on easy street. The Security of Utopian Practitioners (SOUP) Corporation from Nagasaki, Japan, a partner of NUTS, Inc., was very impressed with their effort and extended them a warm welcome when they arrived at SOUP Corporation headquarters to finalize the proposal. The two companies had worked on a proprietary project on improved widget technology and its effect on clean coal. They took every security precaution possible, including working on the proposal on a closed network with two-person authentication for login. Both companies in cooperation created an active OPSEC program, and used their corporate offices of security to help with countersurveillance and other threats to the program.
Very few people knew of the program details, let alone its existence. Key components to the technology were protected even further. The very formulas that calculated widget thermodynamics were considered critical to the success of the program. Although NUTS executives were comfortable with their colleagues from Japan, they did not want to lose their intellectual property; to do so could cause financial ruin.
Bob and Alice’s contact at SOUP Corp was an up-and-coming junior executive named Adolf Hirohito. Adolf was a bright man with a very promising future at SOUP Corp. His keen wit and sharp mind made him the most dreaded man in the corporation, because if there were a shortfall in your program, he would find it.
Adolf, Bob, and Alice had spent many hours together over the course of the past six months. They had worked long hours many late nights. As the minutes ticked away, they worked harder and harder to complete the requirements of a very complex proposal. With the time difference between Nagasaki and Atlanta, the three engaged in many late night and early morning teleconferences. Even then, they took every precaution and ensured their video teleconferences were point-to-point and encrypted. They took no chances in an environment where other corporations would jump at the opportunity to scoop up their misplaced or unsecure misfortunes and turn them into their success.
Bob and Alice spent the entire 15-hour trip from Atlanta to Nagasaki together with their laptop, which contained their precious information. They felt sluggish but overall pretty good when they arrived and were greeted by their friend, Adolf. Back in Atlanta, the project had been a success, and NUTS executives were very excited about the proposal. Tomorrow was the big day for Adolf and his executive board at SOUP. As the three finished a late afternoon rehearsal, they all eventually agreed that they would meet for an early dinner because they were first up in the morning. None of them wanted anything to go wrong at the meeting. Dinner was great. They all shared a common favorite of Lebanese cuisine and had a couple of drinks. Then Bob and Alice went back to their hotel, and Adolf went home for the night.
It seemed like the sun rose too early the next morning for Bob and Alice. They scurried to get dressed and quickly moved downstairs for breakfast. Today was going to be a great day, Bob could tell. As he and Alice sat to start their breakfast, Bob was alarmed when he noticed that neither he nor Alice had brought down their laptop. In the early morning shuffle, they had simply forgotten to grab it. He told Alice, and the two headed back up to retrieve their computer with their golden nuggets of information. When they arrived, they both sat down and immediately checked for tampering. Noticing none, they opened the case and turned on the computer. Needing two-person authentication was not a problem since they both had access. As they brought up the screen, they noticed nothing out of the ordinary, and they quickly shut it down after they agreed no one had accessed the information it contained.
This time, with their computer in hand, they went back downstairs and finished eating their breakfast. A bit unnerved that their laptop had been left in the room for ten minutes without them, they pressed on and finished. They packed the rest of their belongings, and headed off to SOUP to meet Adolf and get set up for the presentation.
As they arrived at SOUP, they were met at the gate by a guard. Showing their ID and giving the name of their point-of-contact, Adolf Hirihito, always ensured speedy processing through the normally weary process of gaining facility access. This time, however, they were met with a refusal. The guard did not acknowledge them on the access list that day. Frantically, they tried to call Adolf, but to no avail. He was unreachable. They dialed until the batteries on their phones nearly died, and they were left with no recourse but to return to Atlanta. Their flight, only a couple of hours away now, and an unhappy phone call were the only things between them and almost certain dismissal from the firm.
The flight seemed twice as long as the 15-hour flight from Atlanta and much less jovial. Bob and Alice lamented about the events of the day and were very confused about what had actually happened. NUTS would need to rectify or pull out of the proposal with SOUP. Concurrently, inside the SOUP executive boardroom, corporate leadership was getting treated to the latest market innovation in widget technology. The team prepared the rest of their proposal. Without NUTS, the team would be able to complete the proposal alone and keep 100 percent of the profits. The team members were fixated on how completely they had acquired key information from the NUTS representatives. Having Alice on their side was truly the key, and they were prepared to reward her well.
When they arrived back in Atlanta at NUTS headquarters, Bob and Alice were whisked away to the CEO’s office to explain what happened in Japan. As they entered, all in the room were witness to a news release from the president of SOUP stating that his company was preparing a unilateral proposal because of conflict or some other problem with NUTS. Bob didn’t listen.
Thankfully, the NUTS CEO decided that all was not lost, but swift action was needed. After a stern session with Bob and Alice, the CEO called in the Director of Security for a chat. It seemed that the information security posture of the company was such that the CEO and CIO authorized a deception program to bolster the overall protection of NUTS information. The company did this through a simple technology. The CEO called for Bob and Alice again to give statements to the Director of Security, but Alice was gone. She was nowhere to be found. CCTV revealed that she left right after the meeting with the CEO. Bob was dumbfounded.
As the interview went on, the security team found out that, although Bob and Alice had different passwords for their two-person authentication, Alice had socially engineered Bob’s out of him by establishing a close relationship with him. Once she was close, he let down his guard. He would look away when she entered her password, but when he entered his, she did not. All it took was for Bob to walk away to the bathroom for a minute, and she could get all the data she wanted from the laptop. One thumb drive was all she needed to copy the files with the critical formulas—the priceless nuggets of information that were her objective. The critical technology that was key to the success of the proposal now resided with the SOUP Corporation.
The SOUP Corporation operated on a closed network, as did NUTS. There was no way to get the technology back. The NUTS CEO did not want it back; he wanted a coup de grace. And within the next day, he got it. He had developed a good OPSEC plan, but an even better deception plan. Alice did not steal the files with the critical information; it just appeared that way to her. The security settings of the computer would not allow downloads of any kind, and any attempt to download files would have grave consequences for the user.
Back in SOUP’s corporate headquarters, the CEO and his executives were preparing for their final rehearsal before they submitted their proposal for improved widget technology. They thanked Alice again for her fine work and began to extol her. It was a strange scene in the boardroom when, as Alice was receiving such a grand reception, the screen with all the information from NUTS went blank. The computer crashed, and then the other computers on the network started malfunctioning in the same manner. Finally, the SOUP server farm with the company’s most critical information crashed, leaving SOUP executives questioning why they had not gotten the offsite backups as they had discussed the previous week. Alice wondered what was to become of her, deceived by the unwitting Bob who was planted with the story a long time ago. Not only was the file not the real information containing the data she sought, it turned out that the “critical information” that NUTS executives talked about was not so critical after all.
It seems all the luck had gone from SOUP to NUTS, and that proposal was going to be made after all. Bob was going to get a good talking to about information security, but it was to be a happy day in the Peach State.
Postmortem
Security is not a single facet of protection. When implementing a security plan for a corporation, due diligence must go into vetting people (personnel security), IT systems (computer security), and all the data (information security). Of course, every aspect of how a company operates, including program management (operations security) must be scrutinized. Too often, leadership and management do not realize that all it takes is a single person—perhaps a contracted cleaning person or maintenance person—to introduce media like a thumb drive to do keylogging in a very simple way. Something like this can bring down a company. Vetting of individuals is an ongoing process and cannot be taken lightly. NUTS security team members might have done all they could, but everyone needs to be involved. Bob should have been more aware and not ignored security details. There is a reason why they are in place.
The computer security community is a curious lot of folks. Corporations are even more curious. Companies go to great lengths to protect their proprietary information. They identify critical information and scrutinize the security posture used to protect it even further and in more depth. It is completely logical to take extraordinary measures to do that, since the loss of this information would be fatal to certain programs and could end any hopes of being competitive in that market.
Private industry and governments alike spend billions each year on security—not just on computer security, but also on the much bigger picture. It is all about their information. Information is power. Information is key. Information drives everything. Economic espionage is a great example of one entity pursuing another’s information. Technology theft is only information that is sought by the adversary, which is actualized, tested, and sometimes tied to an operational test program.
Security comes in many forms. Not only is computer security important, but physical security is also critical to successfully protecting information. Guard forces, gates, and locks add levels of protection that complement things like computer security. Alone, each is good; together, they are better. Does that mean if all disciplines of security are implemented that a panacea has been created and information will be secure? Absolutely not. There are several reasons that prove this line of reasoning is flawed. The primary one is that there is no such thing as perfect security. Only true utopians could ignore the vulnerabilities and threats inherent to their programs and systems. To attempt to truly secure information, an organization must face reality and focus efforts on situational awareness.
A second reason information can never be totally secure is that things change. What was secure yesterday may not be secure today, due to updates, patches, fixes, and so on. The guard might have become susceptible to a bribe because he has bills to pay and the economic downturn has hit his family. Computer software could be outdated, or even worse, be up to date but not installed correctly (or not installed at all).
The most frightening aspect of all this consistently eludes all but the shrewdest of security professionals. Many computer security professionals regurgitate the party line: antivirus programs, firewalls, intrusion detection systems (IDSs), spyware, and so on. A security professional does not operate within the existing paradigm, nor does he shift a paradigm. An honest-to-god security professional makes a paradigm materialize from chaos and large volumes of data into something tangible and identifiable. There is intuitive thought and creative expression put to paper, with functional results appropriate for the given conditions. The bottom line is that this is not business as usual. How can a defender expect to parlay an adversary if the professional does not know where the adversary is coming from, what the adversary is looking for, or what the adversary’s intentions are? How can a defender expect to have any impact if he has just given away the keys to the castle?
Network defenders are at a deficit even before their computers are loaded with software and hooked up to the network. Imagine building a house from the ground up. You take great care in selecting the best land, strongest equipment, and finest resources. A crew is chosen who has the best reputation and is the most trustworthy. The architect and crew even guarantee that they will safeguard the blueprints and layout for the home to ensure security is optimized for you and your family. That sounds like a great situation—you have taken care of every aspect of security for your family home. You are confident beyond any doubt that things will be fine.
Just as construction commences, you arrive with a small group of well-known thieves. You allow them great latitude in examining the grounds as well as the blueprints. You even provide them a copy of the blueprints. Leaving no stone unturned (literally), you give them a full set of keys to the house, along with the security codes for the new, top-of-the-line alarm system. The coup de grace is delivered in the form of a complete list of your family’s personal information, including Social Security numbers, credit card information, and all of your banking information. Even allowing access to your most critical systems and the information stored within is an example of giving up the keys by not protecting your critical assets to the best of your ability.
That’s how we do it in the network defense business. We give away the farm before we set up our networks. We give everything away before we establish a defined architecture. Do you think your adversary knows you have Symantec antivirus software? Perhaps he is aware that you’re running VMware or using cloud computing. Do you think he knows you are running Microsoft Office? How about hardware—does he know whether you have a Dell or HP box? Do you think the adversary knows you are running Juniper routers?
So when does that new paradigm appear? What does it take for us to break the mold and think differently? Does your company still post its information about new programs or structures on the Internet? Does it post information about the staff on the Internet, perhaps in booklets? How much information do employees publish about the company, their processes, their programs, and their proprietary information?
So, you have done your due diligence. You have telegraphed all the hardware and software you are using for your corporation, and in case that wasn’t enough, you have published nearly everything about your company on the Internet and solidified it in paperback. Then, strangely enough, corporate security officers are surprised when something happens on their networks. It is not a matter of if something is going to become compromised; it is a matter of when.
Organizations use the conventional approach. They structure their networks the way they are told, with the software and hardware they are advised to use. So why do they have problems? The answer is simple: the adversaries have everything you do. Surprise! They have the hardware, software, and network diagram, and even understand and know how and when you will do patching. They know what you are doing and how you are doing it, and then they sit back, waiting for the right time to strike.
Tall Tale 2
As Bill milled through log after log, he was thinking that it was about time for a break. After all, he deserved one—he was doing a great job. He was never a night person, but since he took the job reviewing net flow (the base network information IP, port, protocol, and volume of data sent) from the corporate sensors, he was getting used to it. Still, it was probably time for a cup of coffee. As he walked to the break room, he thought it was a rather robust defense the IT staff had established at Fundamentals Unlimited (FU). The CIO was big on securing the enclave at the headquarters, and he had just implemented a huge initiative to lock down all the out stations—all 14 of them. Bill was happy to do his part in what he thought was a minimal way.
As he took a cup, he thought of being the team chief. Bill put cream and sugar in his coffee. His dream expanded, and he was not the section manager anymore. By the time he was pouring his coffee, he was fully entrenched in the CIO position. What would he do? How would he lock down the network? As he walked back to his desk, he envisioned a corporate environment where only a few select machines would even be connected to the Internet. He would have most of the company on an internal network—a stand-alone network.
Heck, that’s how they got in trouble in the first place, and the CEO was none too happy. Most of the staff had already opened the e-mail first thing in the morning, and the damage was done. The spear phishing was successful and took FU offline for almost two days. Who didn’t want to read about the boss’s plan to take everyone for an off-site meeting on a four-day cruise? The Caribbean was a great choice, and the perfect place to have a serious off-site working weekend. Who cared that it didn’t sound like something the CEO would do? They all believed it and wanted it to be true. It sounded great, and looked like the boss had sent the e-mail. The CEO was still fuming about that—not the cruise part, but the fact that they all thought he was that benevolent, and he never did understand how it was that the e-mail had come from his account in the first place.
Bill’s thoughts drifted back to running the IT shop, and he imagined creating a quick reaction triage and mitigation team. He would create a team that could digitally maneuver as needed to defend the network. The team would take direction from him and the CEO, and be a special cyber force. The cyber force would move quickly and stealthfully. It would be a highly trained unit, with freedom of movement throughout the company networks. This cyber force could move through the networks and set up defenses at will, and perhaps confuse adversaries. It was not a perfect answer, but something to help. Four years of school and all the professional literature implored IT professionals to use defense-in-depth strategies. There were no guarantees, but it was considered a best business practice. Bill thought that there had to be more he could do. As he sat back at his desk, he started running through the logs again, and his dreams of being CIO faded as he encountered some strange traffic he had never seen before.
Bill started to sink deeper and deeper into an impenetrable pensive state. He studied the screen more closely as the sound of the CD player faded into nothingness. He did not even hear his coworker clumsily approach, spilling his coffee as he stumbled into his seat. Sunil had been with FU for 12 years. Sunil spoke, but his words were lost to Bill, who was so deeply protected inside his wall, no noise would reach him. Sunil reached out and grabbed Bill’s shoulder, saying “I said, are you all right?” Bill faded back in. Sunil continued, “Christ, I’ve been talking to you for five minutes. You’d think I could get something out of you—even a grunt would be good. Stay in a job too long and everyone takes you for granted. I should have left years ago and taken that CIO job with Technology, Inc. Yep, just ignore the old-timer.” Bill was silent, and Sunil went on for a few more minutes, until he looked up and straight at Bill. The confusion on Bill’s face told Sunil a different story. Sunil and Bill had never had a situation where they could not talk. They had worked together for quite a while. Sunil was proud of the fact that he could get along with anyone, so Bill’s silence unnerved Sunil something terrible.
Again, Sunil asked Bill what was going on, but Bill just returned a blank stare and turned to the screen again. After a moment, Bill spoke. He showed Sunil some strange traffic on a very high port that he couldn’t explain. He thought that they had everything locked down. Sunil studied the screen, as he also became entranced. Never before had he seen such strange traffic. He turned to check all his sources for anything that matched the signature of the traffic they were witnessing, but nothing matched. He would never admit it, but every time something strange was going on in the network, it was because he had forgotten to apply the updates from the patch server. Unpatched machines were FU’s biggest vulnerability, but this time, all the patches were up to date. Sunil was at wit’s end, while Bill stared in a confused cloud of admiration. Bill had never before been confronted with such a situation, and he assumed that whoever did this must be very good. In a strange way, he found himself actually impressed with what he saw.
They read on, reviewing log after log into the early hours of the morning. Nothing specifically led them to a definitive conclusion, but one thing was for sure: there was big trouble. Their team had been successful in almost every encounter with the adversary (except for that little spear phishing incident). Their track record was good, and they were thorough at finding problems on the network. Sunil and Bill did what they could, but when morning rolled around, they knew they were going to have a long meeting with their supervisor and the CIO.
As the morning shift arrived, employees were individually briefed, and many had thoughts and ideas as to how they should pursue the problem. By now, most of the IT staff was busy with analysis. The CIO directed that they were to give him hourly updates on their progress until the problem was found, and then they could institute their mitigation program. He ordered a complete review of the status of every server, router, switch, and client, starting with the headquarters. Almost all of the company’s proprietary information was stored on the servers and encrypted. The thing that bothered the CIO was that he did not know how many client boxes were compromised and in which enclaves the intruder had entrenched itself.
All available resources were dedicated to identifying the strange activity. FU had never before been faced with such a big threat. Bill and Sunil stayed throughout the morning, but as evening approached, they felt as helpless as the once fresh morning team. New people arrived and continued processing the network traffic and logs as the two previous shifts had done. The updates to the CIO were becoming a sublime brief interaction between two parties drawn together by a common goal. The increased level of frustration and impatience was evident in FU—not only at the headquarters, but at the field locations as well. Everyone knew that something important was going on, but not everyone knew exactly what that was. Anxiety and tension grew throughout the corporation.
As the sun rose the next morning, it seemed as if a sense of calm fell over FU. Bill and Sunil worked throughout the night on cracking the code on the strange traffic, but there was not really such a heightened sense of imminent danger. That morning, the CIO looked refreshed and was quite jovial. The IT staff rolled in carrying coffee and donuts. Of course, they had Bill’s jelly donut and Sunil’s coffee cake, just as they had brought every Tuesday morning for months.
The sense of urgency and sharpness that had ruled the previous day seemed to have lost a bit of its edge. Conversely, there was still high tension throughout the workforce. They knew less than the IT staff, and that lack of information played out in decreased job performance. Productivity was down, people were taking longer breaks to gossip, and speculation was high.
Meanwhile, over at the other company, a man and a woman were chatting.
“Did you finish?” the man said.
“No, not yet,” replied the woman, “I still have some to go.”
“Let me know when you’re done,” the man stated, “the boss is looking for a status.”
“Will do,” she answered.
The man walked back into the boss’s office and sat down.
“Now explain this whole thing to me,” said the boss. “I’ve kind of been in the dark the last week or so.”
“Well, we started looking at our competitors for the Davis contract and found out that there are only a couple of real threats for the bid. The first was Technology, Inc., but they are trying to win the bid on a different contract. We felt they would not pose a threat to us because, although they have the technology, they lack the required manpower to do it. The other threat was FU. They have both the technology and the manpower to execute the proposal and contract.”
The boss asked more about the technology and got some background of the contract. Then he wanted to know how they took FU out of the picture to ensure they would be the only ones bidding on the contract.
“Simple,” explained the man. “First we had to identify the critical information they were trying to protect. That was pretty easy, considering they were working toward the same goal as us: the Davis contract. Then we took a good, long look at what they thought were their threats. We analyzed to see what made sense. They never thought of us as a threat—intrusions, viruses, and botnets, sure, but not us. They never saw it coming. Next we looked at their vulnerabilities. Let me tell you, they had IDS, IPS, and firewalls. They ran updated virus protection and spyware, and even trolled their networks. They had good physical security, too. They had ID badges with passcodes, swipe assess, two-person authentication, and more. They did a good job technically and physically, but not psychologically. That’s where we identified what their risks were. We knew their soft spot. Do you remember a few months ago when they got hit with that scam e-mail about a vacation? Well, that was our folks.”
“How’d you do that?” inquired the boss.
“It was easy. We masqueraded their CEO’s e-mail, and when their folks opened the ‘Important Offsite Cruise’ note from the boss, we infected almost every computer they owned. To keep their IT staff off balance, we laid low for a while and let them clean up what they saw. It was too late. We had already created administrator accounts on everything with an IP address. At that point, we waited until they reimaged all the boxes, but because they didn’t take everything offline at once, we just jumped from box to box. We maintained access the whole time.”
“That’s incredible!” exclaimed the boss.
“Not quite. Here’s the best part. So we fast-forward a few weeks, and everything’s going along okay for FU, right? Not so much, boss. Remember I said we were going to lay low? Now we are ready for action. We jump up and cause a big ruckus. We get them really interested in some ‘anomalous’ activity happening in a strange way. They start looking at it and realize it’s something big. We planned it out over a long period, with lots of prep to make it look convincing. See, boss, we have to sell them on this thing as being real, or the whole thing is shot.”
“I get it,” said the boss.
“So now, we give them the knockout blow. While they are looking at this strange computer traffic, we sneak back in and grab their proposal. We corrupt the files with the same name, and all the data related to the proposal is gone. All done—they don’t have any data, and they are no longer a threat to us. We win the proposal; game over. The team is about finished in the other room right now. It sure will be great to see them try to figure this one out.”
“It sure will. Ha ha!”
Postmortem
That benign spear phishing episode you encountered yesterday may be the initial foothold into your network. This episode was sponsored by a corporation and was readily financed to ensure success. It was part of a long-term plan and was broken into several phases. Obviously, the first phase was to gain access, but the plan did not have a determinate timeline, and success was based on events.
ATPs are activated by time and events. Of course, that information is not known to the network defenders. Every event should be questioned and taken in context at the time it happened, as well as contrasted against the larger picture of what is going on.
Tall Tale 3
Paul and Rick worked a regular job like anyone else. They took pride in their work and felt they were on the cutting edge. They were engaged, and committed themselves and their staff to ongoing educational opportunities, both within the country and abroad. They promoted technical forums and research opportunities whenever possible. They knew that if they took a break, time would pass them by, and they would be a dinosaur in the computer security arena. This strategy, although rigorous, paid off time and time again.
They were the industry leaders in computer security. They had contracts with NATO, Russia, China, Australia, India, and numerous other international powers. They straddled the fence and offered solutions to anyone who could pay, despite the high-risk stakes. Business was good, and they did everything necessary to keep it that way. Their products were in demand around the globe, and although many countries were concerned that Paul and Rick were dealing with their adversaries, they all believed it was in their best interest to use the solutions provided.
Each solution Paul and Rick provided was custom-made, so technically, no two countries running their products or applications could ever be compromised by another due to a security flaw in one of their products. They went through great pains to ensure everything was locked down tight. They had numerous production quality controls, along with a final and personal check by one or both of them.
There was no doubt that Paul and Rick were the best at what they did. They were conservative and deliberate, and planned out everything. They left nothing to chance. One could say that if the computer security world was drinking Scotch, it would come out of a plastic bottle off the grocery store bottom shelf. That was reserved for Paul and Rick, the top of the line. They used state-of-the-art techniques, as well as in-house developed proprietary software and hardware solutions to secure their rather diverse customer base. When they got the call to go to Germany to improve the network security of the Bundeswehr, it was business as usual—another big contract opportunity and the potential for another big payday.
Germany had drifted into unfamiliar territory. There was a growing uneasy feeling on its border with the Swiss. Diplomats had exchanged harsh words and stabs at each other’s human rights record. That, of course, was just a distracter from the real problem. And there was a growing concern over the border dispute. Germany had recently declared that the Canton of Schaffhausen in Switzerland appeared to belong to the Germans. The Germans cited a 1330 decision by the emperor Louis of Bavaria to give the city to the Hapsburgs. Although Schaffhausen was able to buy its freedom in 1418, the German government said the transaction was not legitimate because the people of Schaffhausen had tricked the Hapsburgs by filing in a neutral court in Switzerland, and not through the German system at all, and sought to annex the canton from Switzerland.
The impetus for all this was a joint research project that included students and faculty from both the Universities of Zurich and Berlin. It was a four-year-long project, but the results were phenomenal. It showed that there was an oil reserve directly accessible by drilling directly through the courtyard in front of the All Saints Abbey in Schaffhausen. It was worth fighting over for sure. The oil, deemed high quality, showed the potential for a reserve roughly 20 times larger than what was discovered in the Middle East—an economic gold mine for any country trapped in such a desperate financial crisis. The eyes of every world leader turned from the Middle East toward central Europe.
Paul and Rick arrived in Germany at a time when many nations around the world were cutting defense spending. The threat from international terrorism was expanding almost daily, but defense spending was getting cut, again. International economics was tepid at best, with depression looming on the horizon like a dark, pendulous cloud approaching from the west. Politicians promised recovery, and people raised their guard. The politicians made more promises, and the people cowered in fear for their personal property and livelihood.
In the advent of all this, Paul and Rick keyed in on the fact that market share was getting smaller and competition was getting more ferocious, and they were more resolute than ever to ensure they got that big payday they sought. They were determined to increase their share, but still provide superior security and the high-quality products their customers had come to rely on. Paul and Rick were oblivious to the politics of it all, as they had to be for corporate preservation. They consistently rose above any scrutiny, and instilled a sense of loyalty and trust in each client. They had to, or they would be out of business.
Discussions with the German defense officials went well, and before too long, there was a contract and a well-developed road map of the way ahead. Paul and Rick felt pretty good, as did the German brass. Paul and Rick had always delivered on time, and things looked good for this network solution to be implemented on time and on budget. The recent unauthorized network activity and exploitation of their information had unnerved the German generals to the point just short of ripping out all the old infrastructure and installing new systems from the ground up. Of course, the budgetary constraints made this prohibitive, so they made the most of it and retrofitted their network with some of the most sophisticated products money could buy. The best part was that the software was proprietary, so there was the extra layer of protection to make sure that nothing was going to be able to affect it in a malicious way.
In a move that shocked the world, the Swiss broke their long-standing pledge of neutrality and took up arms. Of course, they chose to fight against the Germans. Their neutrality was world renown. They had not had a serious threat, let alone engaged in a unilateral combat operation, for hundreds of years. Being such a dire situation with economic crisis so close, many people, corporations, and nations would be withdrawing money from the Swiss banking system, which could affect their economy in a dramatic fashion. The Swiss were not taking any chances either, and as relations degraded with the Germans, they felt it was time to put the final parts of their plan into motion. The Federal Council of Switzerland, the executive body, had planned for many situations with different types of contingency plans—this was one of those plans.
The Swiss army staffed slightly under 140,000, which was significantly larger than the German standing forces, which totaled under 90,000. However, as the Germans started to move forces toward the deputed territory, the Swiss high command wasted no time in maneuvering troops and finalizing plans for defense of their homeland. The Germans’ confidence in their troops soared. With their new GPS-enabled technology, they could track their forces. Attacking Switzerland was not in the cards until recently, but if the German Heer was to navigate the mountainous terrain, there needed to be advanced technology to get them through. Paul and Rick had done their job, got their payday, and arrived back at their office in Stockholm before any shots were fired. They had no interest in belligerents engaged in hostilities. They just did their job and got out to see another payday.
The Swiss, being keenly prepared for this possibility, relied on a team of specialists to swing the advantage in their favor. They knew that the Germans were purchasing more sophisticated technologies in preparation for future battles. Several years earlier, a few human intelligence specialists from the Swiss military had contacted the foreign subcontractor under Paul and Rick’s corporation who specialized in creating the German software slated to provide the real-time data for tracking forces. After much research into the lives of several contractors at this facility, the Swiss identified a couple of personnel sympathetic to their cause. These individuals, armed with several new lines of code developed by the Swiss, created additional functionality in the German tracking system, which the Germans would never know about … until it was too late.
When the Germans started making their way across the Swiss border, the Swiss computer specialists’ work began. Back at the main German headquarters, where the brass was observing the real-time movements of their forces, their display began to show German forces dispersing in a manner inconsistent with their operational plan. This same information was displayed on the fighting units’ displays, on which the German forces had become so reliant. As the chatter increased among the Germans to return to their predetermined formations, heated arguments ensued that all forces were in place as had been planned. This served as a useful distraction for the Swiss.
The extra lines of code provided by the Swiss allowed them access to the German tracking system. With this access, the Swiss specialists were able to view the exact locations of the German forces, as well as tamper with the displays and force locations as seen by the Germans. With the Germans confused about their own locations, and the Swiss having full knowledge of the German locations, the Swiss unleashed an assault that drove the Germans back across the border posthaste. With a little research, well-placed contacts, and technical skills, the Swiss had preserved the sanctity of their homeland with minimal loss of their fighting forces.
Postmortem
One overlooked aspect of information security involves acquisition security. Secure contracting and acquisition channels are often taken for granted. A secure acquisition channel does not guarantee a secure acquisition, and the same goes for secure contracting: it is not a guarantee. The factors involved in assessing acquisition and contracting are not all inclusive, but they are as comprehensive as reasonably possible. An additional look at these processes and programs should be a part of every security professional’s routine.
Technology giveth and technology taketh away, and not always in equal measure.
—Neil Postman, “Informing Ourselves to Death” (speech at the German Informatics Society meeting, October 1990)
The prospect of coordinated and complex virtual deception is a reality. To improve security, paradigms must be broken, and new ideas must be incorporated and synchronized with traditional efforts. The linear thinking that leads us down the path of compliance with security recommendations of industry and government leaves us inherently vulnerable. Both attacker and defender share knowledge of every aspect of the network. Governments give us standards that are published for the world to see. It must be done that way for compliance. Industries develop their products, which they sell, so advertising and specifications are out there for both the attacker and defender. Unwittingly, the defenders lose the traditional home-field advantage because the attackers already know with what and how the defenders are doing their job; game over.
In recent years, military actions have been prefaced with deception and cyber attacks. It is believed Russia launched attacks on two occasions: one against Estonia and a second against Georgia. Both times, it crippled critical infrastructure and staggered the IT security folks. With Symantec commercializing its honeypots, an additional level of obfuscation for attackers and defenders alike has been added to the mix. How will this play out with the commercial sector engaging in military-style tactics to defend its networks?
Traditional honeypots are used for early warning and surveillance, but in the nonlinear asymmetric world, should more be done with them? By definition, honeypots should have no production value, and everything that touches them is malware and nefarious. But should that be the limit? Along with software and networking issues, computers have inherent structural vulnerabilities, as there are regular vulnerabilities introduced into various platforms by vendors.
Tall Tale 4
A senior-ranking executive of an international organization (let’s call him Mr. Smith) was sent an e-mail regarding a 20-year college reunion. He was aware that it was his upcoming 20th-year reunion, so he read the sender’s address, the subject, and the body of the e-mail. After feeling somewhat comfortable with the e-mail’s content, he looked at its attachments, which were said to be an RSVP form in Microsoft Word format and a flyer for the reunion in PowerPoint format. He opened the attachments without a second thought, and then after reading them, he realized something was wrong because the content for the attachments was slightly off. One of the images was used in the last reunion according to his memories of the previous event.
Mr. Smith called a colleague he had graduated with, and discovered that peer had not received anything. That old classmate had knowledge of the real reunion, and told Mr. Smith that the date and location of the upcoming reunion were all wrong, and the coordinators on the RSVP form were also incorrect. This sent an immediate red flag, and the hairs on the back of Mr. Smith’s neck went up. Working for an organization that handles sensitive projects for the government, he knew of the dangers of spear phishing and SSCTs.
Mr. Smith then called his security manager to send a trusted team of digital forensic investigators to his office and inspect his computer for any possible foul play. As he waited for the investigators to arrive, he began to sweat as he considered the volume of sensitive information he had stored on his laptop and all of the critical information that could be lost if this were an incident. Some time passed before the team arrived in Mr. Smith’s office and began examining his laptop for any possible infections. They performed the standard operating procedures, by first disconnecting the system from the enterprise’s network and then making copies of his Microsoft Outlook e-mail file folders where a possible infection may be residing. The team told Mr. Smith they did not want to turn off his system, but wanted to leave it unplugged for the time being in the event there was an infection present and it was memory-resident. If the system were turned off, they might lose additional evidence if the initial exploit code in the attachments had already downloaded the stage-two sample from a remote site. They didn’t want to take the chance of losing any information if something had occurred. From that point on, all information between the infected system and the remote connections were logged for analysis.
The security team headed away with a copy of Mr. Smith’s Outlook files and folders on a flash drive and his laptop still running (and power supply in tow). Luckily, this organization had a proactive policy of making a backup image of every senior-ranking official’s laptop and had a four-month-old image of Mr. Smith’s laptop. The examiners copied Mr. Smith’s Outlook files and folders to the appropriate location on his backup Windows system, which they were running within a virtual machine (VM) based on the Linux platform’s Xen Virtual Machine Manager (VMM) environment. While this task was being carried out, another investigator plugged Mr. Smith’s laptop into a sandboxed network running the same DHCP range as the corporate network. This provided perceptual consistency to network-aware malware, which can shut down if plugged into networks not associated with specific network ranges. With both systems being set up together on two separate sandboxes, and network sniffers running on each network, both systems were monitored for a planned period of 24 hours. For the purpose of this tall tale, we are going to call the VM system Honeypot 1 and the system being investigated System A.
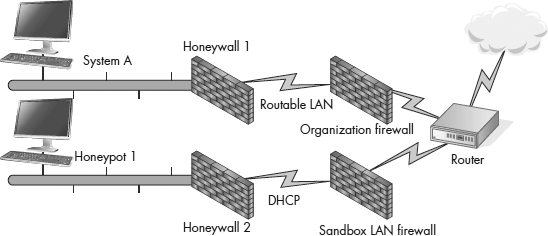
A counterintelligence operations network
Honeypot 1
An interesting thing occurred when the examiners installed the suspicious Outlook files, opened Mr. Smith’s e-mail, and followed the same path that Mr. Smith had told them he had taken when opening the message and the attachments. Once the attachments were opened, a process had opened a TCP socket and began phoning out (communicating with a remote system) to www.hotgirltvshow.com, and attempted some HTTP POST and GET commands. Luckily, this sandbox actually had an Internet connection and was able to download the stage-two Trojan, which came right down in both an executable (.exe) and a dynamic link library (DLL) file. Once these files were on the system, using external analysis tools for VM introspection (tools that can inspect the functions and actions of a VM), the team was able to ascertain the executed commands of the stage-two Trojan that had been downloaded from www.hotgirltvshow.com. The following commands were initially executed on the system (in this order):
This information was quite useful for the examiners. They were able to validate that the attached files were malicious, and they were able to gain crucial intelligence on the actual infection technique and the initial sequence of events that transpired on the system while Mr. Smith had been sitting in his office waiting for the security team to arrive. Shortly after these commands were executed, the security team also saw that since the .p12 file for Mr. Smith was on the system, they could identify that it had in fact been sent out to a host that was resolving to www.marinetimemac.com at that time. It downloaded an XML file once the appropriate verification had been made by the Trojan that the server was up and that the system could reach the file that was needed from the server. This was an XML file that would be used as an instruction list of tools that support a Linux-based interface that allows remote connections and issuances of various Unix commands on a Windows host, without the host knowing of its presence.
The modules that were listed in the XML file that was downloaded from the www.marinetimemac.com host supported Xfce, which runs a number of core components for the minimum tasks you would expect from a desktop environment (such as window, desktop, session, file, and settings managers). Most important is that this tool also provides the ability for remote Secure Shell (SSH) connections. The following is a short list of the captured Xfce packages that were remotely installed by the attacker in this incident:

NOTE
Xfce is a great open source project and is in no way malicious in and of itself. It just so happened that the attackers favored this methodology for performing remote control of Mr. Smith’s system. Xfce was installed on the system by the attackers and was not originally a part of the system build.
The next step the examiners took was to contact their counterintelligence group and inform them of their findings. After a dialogue of the observed events, it was determined that active responses were needed for a threat of this motivation and skill. The modules that were loaded onto the honeypot system were analyzed. Since this system was a six-month-old image and the true image of Mr. Smith, the cyber counterintelligence (CCI) security team went to work. They opened a dialogue with Mr. Smith and provided him with a temporary operating account that had a moderate attribution layer while his account was being investigated. The CCI team began copying some of the more recent information off of Mr. Smith’s laptop after examining what the stage-two Trojan had been seen searching for, which were files of the following types:
At this point, several new documents were generated by the CCI team that were newer than the information that had been on Mr. Smith’s system. The analysis team also sent this information from a known colleague of Mr. Smith to increase the perceptual consistency and authenticity of the transmitted materials. Some of the documents provided information on special research and development initiatives that were crucial new security technologies that would change the face of the organization’s security posture.
The team sat down and discussed the deception plan, They decided that in order to lure the cyber threat out into the open, they would need some juicy false intelligence to focus the threat on a specific objective within a timely manner. This would allow the CCI team to identify how motivated, skilled, and resourceful the active threat was. The CCI team leader spent a day interacting with other officials, and decided that a project that had been proposed six months earlier and was benched was a great fit, if certain modifications were made to the proposal materials within a 24-hour period. The next step was to integrate the plan into the rest of the organization by having a handful of other senior members begin a dialogue with Mr. Smith via e-mail about this new project and how important and critical the project was to the overall organization’s competitive advantage. Mr. Smith received and sent e-mail messages with a perceptually consistent theme, and the other executives replied with short but very strong messages, after taking seemingly enough time to review the content.
This content included a project proposal, financial information, logistical information, and even some information on a recently initiated demo of that new competitive advantage system. This was all performed within a 72-hour period, ensuring the focus had remote access to the local backdoor the threat currently held over this honeypot image of Mr. Smith’s system.
By monitoring the processes and functions of the honeypot, the CCI team was able to clean Mr. Smith’s real system, and everything that was on his system was analyzed. Fortunately, the enterprise security team had a full packet-capture system for their enterprise network. They were able to determine how much information may have been leaked from Mr. Smith’s production image. After identifying that only minimal information had been leaked, as the threat didn’t use any form of encryption on the first- or second-stage Trojan, it was easy to see what was left. Once the team had determined that not enough information had been leaked, they decided to continue with the deception operation against the elusive threat.
After the stage had been set with the content-staged information (falsified information to mislead the focus), and the organization manufactured dialogue regarding this new project and its importance, the Trojan on Honeypot 1 transmitted the findings to the remote server. The Trojan collected every piece of information that had been staged by the CCI team. The only step was to watch and wait for the focus to change the threat’s direction to that new project, which were in reality systems within a honeynet (Honeynet 2) using a customized third-generation honeynet suite. Unfortunately for the threat, the focus did change the team’s objectives, and entered the honeynet that was waiting for the threat. More information on currently available honeynet solutions will be covered in depth in Chapter 8.
Postmortem
The CCI team collected volumes of valuable intelligence on the threat over the course of a few weeks. Once there was enough intelligence collected on the tools, tactics, and objectives of the threat, the CCI team turned off all of the systems and moved on to the next set of intrusions. Mr. Smith had access to his cleaned system, and the intruders were attributed to an ongoing intrusion set against the organization that had been an ongoing threat for well over eight years (Chinese hackers). One of the threats had even inadvertently typed into the system shell a few sentences to a colleague, which were probably meant for another application or an instant messenger platform and their true identities (source of the threat, Chinese hackers) had been divulged inadvertently and things went back to how they were.
For the purpose of this tale, we cannot divulge specifics, but can convey the overall steps that were taken to lure the focus into taking action against the threat with a fully planned operational deception that lured a targeted threat into an area where it could be monitored, analyzed, and attributed (thanks to the unobservant Chinese hacker).
Conclusion
You have just read a handful of tall tales based on professional experiences of the authors. We needed to move things around a little, but the context is completely accurate, and the steps that were taken are also accurate.
There are many ways to implement an operational deception within your organization to counter an active threat. Most important to the operation is the coverage from your leadership and legal departments. However, there are things such as honeytokens (digital traps, accounts, or files that shouldn’t be touched, and when they are touched, the security team is notified) that can be used as trip wires (booby traps). Threats can also use radio frequency-based technologies to hop from one device to another (such as from portable electronics to a PC or printer) and propagate from there. These types of deceptions can be found only by investigating (having access to) the network traffic.
By using the control of your enterprise, you can do almost anything you must in order to get the intelligence you need to control the battlefield terrain (your network). Remember the principles of deception: determine the motivation and intent of the threat. Without performing some level of counterintelligence operations, you will not learn anything, and the onslaught will continue.
In the next chapter, you will learn about some of the tools, tactics, and methods used in some of these tall tales (and also some tall tales that were taken out by a three-letter agency as we were on the verge of going to jail for writing about them). But if you want more information, feel free to catch up with one of us at a conference.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
