CHAPTER
8
Tools and Tactics

There are numerous ways you can interact with an advanced or persistent threat. Most organizations will simply take the compromised machines offline and have them rebuilt for circulation back into the enterprise. This may suffice if you are dealing with an opportunistic criminal who has no direct interest in your enterprise’s data. However, this approach almost never works when you have a persistent threat that is willing to use advanced techniques to maintain a steadfast presence on your network for a specific motive or objective.
One of the most important things you need to remember is that you have physical control of your enterprise (in theory), while your attacker is likely far away without any direct physical access to your network. This is a serious advantage that most organizations overlook: you have the ability to choose where to battle or engage an adversary within the confines of your own enterprise. Some may not feel this is the best choice and we argue with that concept. In a perfect world threat would be external to your enterprise and we do not live in a perfect world. We know at this very moment your enterprise has at least one form of malicious code running through one of your systems or devices. The “not” knowing where a threat is within your network can be extremely damaging.
Throughout this book we have discussed many techniques and approaches for identifying the threat on your enterprise and how to lure them into systems of your choosing. These systems are the terrain you’re choosing to engage the threat on. Your entire enterprise can be looked at as your battleground and the locations you choose to engage are your terrain. Choosing the battle terrain is the single most important part in traditional combat. Evaluating and understanding your network (the battle terrain) is essential, as this will afford you the opportunity to limit the number of ingress (entry) and egress (exit) routes to and from your network. These are the points where you can concentrate your defenses against persistent threats. This will provide you a battlefield advantage and may stem the tide of information flowing out of your network. The key is to make your adversaries work harder for access to your network and the information it contains. Increase the cost per byte for your adversaries, and they may decide to pass you by.
Just sit back for a few more hours and keep reading. By the end of this chapter, you’ll know you are not so powerless. We’ll look at the tools and tactics you can use—the arrows in your quiver of tools, so to speak. We are going to discuss not only the tools (remaining vendor-agnostic) and where to best place them, but also some of the weaknesses of current solutions, such as host- and network-based systems.
You will also learn there are no silver bullets. No single company, product, or service can be an all-in-one solution. Traditional solutions have not been working as we all hoped. A decade ago, the threat was different, so security solutions were developed to address those vectors. Now the threats and their tools and techniques have evolved, and traditional security technologies have not been able to keep up, although they have been trying and continue to serve a purpose.
Detection Technologies
There are so many vendors that sell host-based and network-based security products that it is hard to tell which one is better than the other. Not every product or service is best for your environment, no matter what any vendor says. Sometimes a combination of a specific set of tools is all you need.
The larger your enterprise, the more tools you need due to the volume of data crossing your enterprise. A small firm of less than 100 users may need only one host-based solution and a few network-based security solutions. A network of more than 100,000 users could require a handful of host-based products (not all on the same machine) and several different types of network security solutions. An enterprise of a million or more users/subscribers would demand an array of host- and network-based solutions, as well as more complex information security protocols.
Hundreds of security products provide detection of malicious network activity. These technologies typically come in two flavors: host- or network-based security systems. Today, most solutions use a combination of signature, blacklist, behavior, and anomaly-based detection techniques. These tools all have their pros and cons. Tables 8-1 and 8-2 list some detection tools in alphabetical order (to not show any favoritism). These are the most prominent tools in the industry as of the second quarter of 2011. Most of these tools are complementary between the network and enterprise, and you will find that many have similar functionality at their own levels.

Table 8-1 Host-Based Detection Tools

Table 8-2 Network-Based Detection Tools
Host-Based Tools
In their simplest form, host-based security controls are the measures (applications) put in place to monitor the state of an individual host. They will monitor a system to determine if a malicious file is present, an application attempts to make changes to certain files, or any number of activities occur that may fall under the malicious category. More advanced implementations of host-based security controls include the use of an advanced application whitelist, which, in essence, tells the computer which applications it is allowed to run.
If planned and deployed properly, these tools can be used to take action against persistent threats. One major consideration is that host-based technologies are not the magical cure to what ails your network. They are just the first step in increasing your overall security posture, leaving you in a better position when facing persistent threats.
We’ll cover the following categories of tools that will help improve your host-based security posture:
Antivirus Tools
Antivirus solutions have been around for well over a decade, and they have needed to evolve at a rapid pace in order to keep up with the ever-changing threat landscape. However, when it boils down to it, generally these solutions are easier to circumvent than network-based security systems. Although these solutions do catch and prevent a significant number of malicious activities from executing, when it comes to an advanced or organized threat, these systems will be circumvented.
Things to Think About
Here are some tips on how you could increase your antivirus system as a force multiplier:
Digital Forensics
Many client-based solutions provide host-based digital forensics. These come in hardware and software forms. They monitor system activities, such as hard drive activity, processes, memory monitors, hooking functions, VMs, sandboxes, and more.
These tools are only as good as the operating system’s security policy, as they can be detected and disabled just as quickly as antivirus solutions. However, they do play an important part in the defense-in-depth strategy.
At times, these systems can capture the information you need to identify a specific threat. You can develop patterns and behaviors exhibited during the crime if these tools haven’t been disabled.
Things to Think About
Here are some tips on how you could increase your digital forensics system as a force multiplier:
Security Management Tools
Security management tools have the largest market share. These include asset management tools, file monitoring, and corporate-based security solutions that monitor each client via a running agent.
These solutions have been receiving less and less attention over the past five or six years, but are still in use today. They are similar to other security agents you have running on your system (such as antivirus agents), but their value is in notifying you when unapproved applications or packages are installed. They can also monitor the attempted altering of specific files and perform regular integrity checking of known “benign” files for any changes that would infer alterations by unapproved actions.
In order for these tools to function properly, they must run with escalated or administrative privileges. While this provides the tool with the greatest ability to monitor the state of your systems, it also has a downside. If an attacker determined how to compromise the agent, or compromise the server to which it reports, the persistent threat just created another avenue of approach into your system. However, these tools can play a part in the attribution game and should not be overlooked as a tool to increase the security posture of your systems.
Things to Think About
Here are some tips on how you could increase your security management platform as a force multiplier:
Network-Based Tools
Network-based tools are the more interesting of the two security focus areas and the most actionable. Over the past decade, crimeware has evolved into a kind of tsunami that just bears down on anyone connected to the Internet every day.
Two types of network-based tools are useful:
Firewalls
The firewall is one of the earliest technologies developed to protect organizations and network nodes connected to the Internet. Depending on the setup of your network, these may be your last line of network defense. Your demilitarized zone (DMZ) and routers are likely to see malicious traffic ahead of your firewalls.
Over the years, this family of technology has evolved into prolific systems that are quite expensive, depending on the vendor. However, firewalls can still allow criminals to get in and out of your system. Firewalls must know what to look for or have predefined access control lists in order to prevent specific threats. With most advanced cyber threats, there won’t ever be much of anything known to ensure protection beforehand.
Today, firewalls are basically great validation points when engaging active threats within your enterprise. If it’s properly configured, a firewall can be used to tell you more information about everything that has passed through it. However, you must keep in mind that the firewall is only as good as the policies, rules, and configuration a human sets for it to follow. And don’t forget to monitor the state and logs of the systems in your DMZ as well as your routers. They can provide you with more information to feed firewall rule sets.
Things to Think About
The following are some considerations for increasing the protection of firewalls:
Intrusion Detection/Prevention Systems
Developed for enterprises initially in the late 1990s to detect malicious network activity, an IDS is a sensor that is placed on your network to monitor incoming and outgoing traffic to alert administrators if anything out of the ordinary is observed. An IPS is a sensor that can respond automatically to any anomalous events, thus working to prevent malicious traffic from entering or exiting your network.
Over the years, these systems have improved quite a bit, but they face a tremendous number of challenges in keeping up with the speed at which malware is currently distributed. This type of system may not be able to stop the advanced threats you face today, but it could be one more system to alert you that something is wrong.
Things to Think About
The following are some considerations when using an IDS/IPS:
Deception Technologies
Have you ever wanted to know just how in the world the infection on your network started? How did the intruders get in? How are they communicating? What did they use to compromise your system? What traffic are they sending or receiving? Are they stealing the crown jewels of your company, or simply using your computer as just one more spoke in the spam machine? Well, keep reading.
What you might want to do is set up a system that somewhat resembles your network, luring in potential attackers so you proactively (there’s that word again) learn from them instead of waiting for the aftermath. While much progress has been made over the years to facilitate your deception, it is not for the faint at heart, because you must dedicate yourself (or someone on your team) to monitoring and learning about threats and creative mitigation technologies. To accomplish this task, the following are your new friends:
A honeynet is a grouping of honeypots. Honeynets are based around high-interaction sensors, which are simply real system servers, workstations, and network devices designed to look like legitimate production systems. Honeypots are customized with configurations that provide adversaries with interesting findings that could steer them to the honeypot versus an operational system. Through this high interaction, you can gain intelligence on threats, both internal and external to an organization.
Conceptually, honeynets are configured to host one or more honeypots integrated within production assets to serve as false targets to adversaries. Since honeypots are not production systems, the honeynet itself has no production activity and no authorized services. This state of the honeynet implies that any interaction within the honeynet/honeypot is unauthorized and malicious in nature. Through the use of honeynets, all unauthorized or malicious activity at the network and host/session level can be detected, analyzed, and acted upon, without risking production or critical system assets. This makes analyzing activity within your honeynet very simple.
With traditional security technologies, such as firewalls, IDSs, and IPSs, an analysis of the interaction needs to identify malicious activity hidden within normal and routine enterprise network traffic. This level of analysis can increase response times significantly to the point that it could take days or even weeks to identify potentially malicious activity. With a honeynet, all traffic inbound and outbound is considered malicious in nature, and can be quickly and cleanly analyzed. Honeynets increase an organization’s ability to identify and respond to malicious activity, and the clarity of information provides an extremely low number of false positives and false negatives.
Honeynets are an architecture operating within a tightly controlled network, which can be monitored and controlled locally or remotely. A honeynet is like a terrarium, where you can create a custom network environment and watch everything that is happening within the network. This clean view of the malicious activity is very helpful for prioritizing which events are higher level threats than others.
Honeypots can be made up of any type of networked system with applicable network services, user accounts, and content, which are used to interest adversaries and ensure they spend as much time on your honeypot as possible. Honeynets have a simple architecture by nature. However, when operating multiple honeynets across geographically dispersed locations, issues can arise due to the limitations of the currently available open source products. At this time, the available open source suites of honeynet technologies are in their third generation; the fourth generation is in the planning and limited development phases.
The sole purpose of a honeynet is to be compromised while keeping an adversary away from production or operational systems. This provides the honeynet operators with a full-impact analysis in a target-rich environment without threat to their operational systems. A honeynet’s main goal is to detect and monitor adversaries attempting to gain intelligence or extract critical information from a victim organization.
Honeywalls
To successfully deploy a honeynet, you must correctly deploy the honeynet architecture. The key to the honeynet architecture is what we call a honeywall, which is the accreditation boundary for honeynets. This is a gateway device that separates your honeypots from the rest of your production network. Any traffic going to or from the honeypots must go through the honeywall. This gateway is traditionally a layer 2 bridging device, meaning the device should be invisible (on a TCP/IP level) to anyone interacting with the honeypots.
Figure 8-1 shows a diagram of the honeynet architecture. Our honeywall has three interfaces. The first two interfaces (eth0 and eth1) are what separate the honeypots from everything else; these are bridged interfaces that have no IP stack. The third interface (eth2, which is optional) has an IP stack allowing for remote administration.

Figure 8-1 Generic honeynet
There are several core requirements that a honeywall must implement:
Of all these requirements, data control is the most important. Data control always takes priority because its role is to mitigate the risk associated with implementing honeynets. The following sections describe each of these requirements in more detail.
Data Control
The data control component serves to control inbound and outbound flows to the honeynet to reduce risk. The risk assumed by the implementer is the possibility of an attacker or malicious code using a honeypot to attack or harm systems that are not part of the honeynet. It is critical to ensure that all flows between the honeynet and external IP addresses are controlled in the event that an attacker or malicious code attempts to abuse the resources of the honeynet. Data control is performed using several features within the honeywall that are implemented together in order to attempt to mitigate risk.
The following are the primary data control functions of the honeywall:
These features are typically configured during the initial setup of the honeywall and/or through the /etc/honeywall.conf file, which is where all of the honeynet environment variables are stored.
As we said earlier, the function of data control within a honeynet is by far the most critical component. If data cannot be controlled, data cannot be captured effectively. The most important item to remember is that you can never rely solely on data control to remove risk when implementing honeynets.
Data Capture
The data capture component of the honeynet logs all activity at the network and host level of the honeynet and honeypots. The honeywall is the primary network-based data capture component, and Sebek is the host-based (session-based) network capture component. These components combined are capable of providing implementers and analysts with in-depth information regarding specific flows and events within a honeynet. These components provide the ability to monitor and log all of the malicious activity within the honeynet.
It is the analysis of this captured data that provides details on specific tools, tactics, and motives of attackers. The most challenging effort when implementing honeynets is the ability to capture as much data about the activity without the attacker detecting the data capture components. The data is captured and presented in layers in order to simplify the data capture and analysis processes and procedures. Layering data also protects the overall data set by preventing any single point of failure of the honeynet. The more layers that are made available during the analysis processes, the more information an analyst can learn from the attacker.
The activities of attackers are hard enough to detect over operational networks due to the ability to obfuscate their methods within operational traffic. However, when these activities are captured within a honeynet, the analyst will have a clear picture of the attacker’s events and will be able to apply that information to the rest of the production network in order to quickly identify if that attacker has already penetrated protected assets.
It’s possible that attackers will be able to detect they are operating within a honeynet, so when implementing a honeynet for optimum data capture, there are several considerations that should be addressed. The following are critical items that must be addressed prior to implementing a honeynet’s data capture components:
Data Analysis
Honeynet analysis is typically a three-part approach made up of network, host, and binary analysis. In this section, we will discuss various methods that can be employed to analyze captured honeynet data.
The only difference between analyzing production systems and honeynets is the point of view of the analyst. When analyzing production networks, it is important to identify the proverbial needle in a haystack to identify the malicious or unauthorized activity. When analyzing honeynet data, it is critical that the analyst understands every network flow is a needle and must be properly categorized. The analyst must scrutinize all of the seemingly innocuous activity, as this activity can be the most rewarding in regard to identifying attackers within your network. An analyst can perform real-time or post-mortem analysis. However, the true values of honeynets are their ability to provide real-time intelligence of current threats when they cross the path of the honeynet (the honeywall) during an intrusion attempt or active exploitation.
Honeynet Layers The layers or types of captured data come in three forms: network, host-based, and the data collected by your network devices between the network boundary and the honeynet. Each of the honeynet components has layers that can be analyzed to identify the full extent of attacker activity within your network. The external honeynet (production) has the following layers:
The network (honeynet) has the following layers:
The host (honeypot) has these layers:
Upon identifying a specific event as being truly malicious, an analyst should validate the honeynet information against the captured data from external honeynet devices. However, the most powerful layer in the preceding list is the session input/output captured data. This layer is capable of providing the analyst with previously unforeseeable information about the attackers themselves. A behavioral, social, and criminal scientist/analyst may be able to discern specific observable information from the attacker’s tools, techniques, and procedures. The following are some of the traits an analyst can discern from attackers’ interactions with a honeynet for extended periods of time:
It is legal to develop behavioral indicators of specific malicious IP addresses versus individuals. With respect to the preceding points of personality, it is very possible to observe malicious IP addresses with a standard operating procedure, method of entry, and goals or objectives. This information, when analyzed across large enterprises such as government networks, can show which areas of the production network need to be protected in order to increase defensive posture and protection levels.
Analyst Workflow It is important for an analyst to adhere to a clearly documented workflow to completely cover every aspect of the operational, intelligence, and technical impact of an attack against a production network. The workflow looks like this:
When working with honeynets, analysts need to ensure their time is spent covering as much of the overall tasks required on a daily basis in order to continue positive forward movement. Analysts should spend their time in the following three areas, as shown in the chart in Figure 8-2:

Figure 8-2 Data analyst responsibilities
Analysis Environment Most analysis environments work better on networked kernel-based VMs (KVMs) due to the ease of information sharing and system navigation.
The following are some common commercial off-the-shelf tools that can be used to perform analysis of honeynet data:
These are some open source/free analysis tools:
These lists are not comprehensive. Many comparable tools are available and useful for analyzing production-based honeynets.
Data Collection
The data collection component applies primarily to organizations that implement multiple honeynets that are centrally managed by a honeynet management server. Typically, the architecture will have numerous honeywalls (roo) reporting to a honeywall manager (kanga). Roo is the name for the third-generation honeywall, and kanga is the name of the honeywall manager server for enterprise ready and highly distributed honeynets. The honeywall itself collects data for the honeynet and sends it to a kanga, which can manage more than 100 roos. This theme was borrowed by the Honeynet Project.
Generally, most organizations simply deploy a single instance of a honeynet. However, larger enterprises sometimes require multiple honeynets with various locations and types to fully understand a network’s true defensive posture. Distributed honeynets, where all data is centrally stored and correlated for the purpose of network defense or counterintelligence purposes, also fall into this category.
To date, the open source Honeynet Project has not released any stable or scalable enterprise sensor to manager builds. Savid Corporation is the only firm in the United States that provides US government-certified honeynet solutions that are custom and focus on the niche requirements of implementing enterprise honeynets. Figure 8-3 shows a simple diagram of a data collection architecture that is commonly used by production-based honeynet implementations.

Figure 8-3 Generic data collection
Although they are more commonly found in larger enterprises, data collection methods are still applicable to single honeynet deployments where the management channel (eth2) of the honeywall requires the secure transfer between the honeywall and the actual systems where data is managed and analyzed. The following could be used as a simple approach to configure the basic open source honeywall to ship data between a sensor and a manager:

Honeynets as Part of Defense-in-Depth
The National Security Agency (NSA) generated a document titled Global Information Grid Information Assurance Capability/Technology Roadmap. This is meant to serve as a fundamental manual for implementing a complete defense-in-depth security architecture for any government organization operating and defending networks. On page 366 in Section 2.6.3.2, “Deception Technologies,” it clearly states that honeynet technologies are the only viable solution when attempting to quickly identify and acquire unauthorized or malicious activity within a government network.
This document contains more than 20 pages of material discussing honeynet technologies and their ability to dramatically augment and improve a network’s intrusion detection capabilities, while also providing security teams with the ability to quickly identify and act upon these unauthorized and/or malicious entities. This suite of technologies is accredited for NIPRNET and SIPRNET (names of the two major networks used by the US government cyber operations) use and has been researched as augmentations by various Department of Defense, Justice, and Energy organizations that are interested in learning more from cyber threats in order to enhance their network protection.
Research vs. Production Honeynets
In the early planning phases of a honeynet implementation, understanding what type your honeynet will be is critical. The two primary types of honeynets are research-based and production-based. The primary difference is in the goals of each type of honeynet. However, the following primary overall goals of honeynets are applicable to both types:
The following sections briefly discuss the primary two types of honeynets and their advantages and disadvantages.
Research-Based Honeynets
Research-based honeynets are typically found in research institutes of academia or as nonrequirement-driven research projects for personnel within organizations as an educational tool. This type of honeynet is typically not managed regularly or held to any specific overall set of defined standards or reporting requirements. Due to the nature of research-driven honeynets, their goals are generally project or interest based. Research honeynets will generally not be used as an operational test bed unless you have finished reading this book and are planning on researching our recommended best practices, tools, and tactics we have passed onto you through this book.
Research-based honeypots are primarily used for the following purposes:
Maintaining individual research-based systems requires a lot of work.
Generation II honeynets were originally designed to suit research-based honeynet deployments. This was the second generation of honeynet technologies developed through the Honeynet Project. More important to note is that most of the organizations that donated resources to development of the GenII were computer science and security research groups within organizations or universities.
Production-Based Honeynets
Production-based honeynets are typically found in larger organizations or government entities that have definitive requirements for network defense, intelligence, or counterintelligence requirements. This type of honeynet is generally developed with a full development plan and reporting requirements. It is based on a strict configuration management plan in order to get the most out of the operational investment.
Production-based honeynets increase the capability of monitoring and analysis for a large enterprise or production network. The following are some of the primary goals of a production honeynet:
Production-based honeynets are easier to hide, close, or mesh within production environments than research-based honeypots. They are also harder to manage than research-based honeynets.
Generation III honeynets were the beginning of the direction toward a more stable, and scalable enterprise-ready honeynet. However, the generation III (Gen III) was, according to some of the developers on the project, “never completed the way it was supposed to be in spirit.” The reason said being that some of the tools and modules for the backend data crunching of the roo and the initial lack of development for kanga had been missed due to resources and time. However, within three years of the initial deployment of Gen III, most of these modules and platforms had been developed as add-ons and are now available today, as they have been for years, on the Honeynet Project’s website www.honeynet.org/project/.
Honeynet Architectures
Designing enterprise frameworks is an important step when considering production-based honeynet implementations. When building a production honeynet or grid, you must ensure that important components have identified solutions to generate actionable information or have any value. This is due to the limitations of the system itself through the cumbersome processing and transmission, and the updating of one SQL database to another. Analysts need to have access to actionable data within enough time to act when a threat is active or the point of the solution is pointless. When you are engaging an active threat, you need to be presented with and understand observed data in real time. Data access to a honeynet in addition to other devices can help a trained counterintelligence analyst present data in a workflow, process each item, and generate any hypothesis or questions about suspicious observables. The more data available, the better, as it can help validate observed actions or activity. The placement of your honeynets is very important as to where on your enterprise that makes sense for your goals or requirements. Here is a short list of typical locations where honeynets can prove most effective:
The following architecture types are available for production-based honeynets:

Figure 8-4 Centralized architecture

Figure 8-5 Distributed architecture

Figure 8-6 Federated architecture
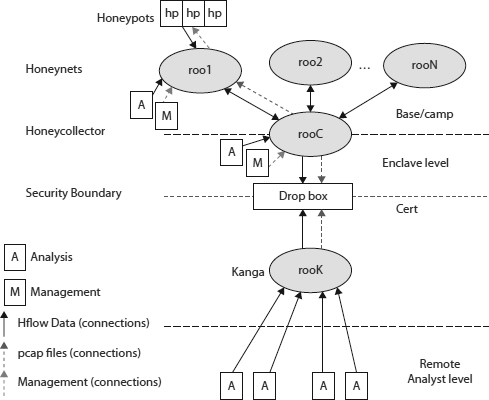
Figure 8-7 Confederated architecture
Centralized deployments are the most effective in small to large enterprises and easily scalable. In a centralized architecture, all of the data is local and can be easily accessed. However, when requirements mandate a distributed architecture in the event of network failure or latency, data can be lost or not received in a timely manner to ensure the focus believes in the perceptual consistency of your deception. This type of architecture can sometimes disrupt your ability to effectively respond to threats, which, in effect, reduces the value of a production honeynet.
Honeywall Accreditation
Currently, the honeywall is DoD Information Technology Security Certification and Accreditation Process (DITSCAP) accredited through the Defense Information Systems Agency. The honeywall has specific versions available to operate on US government networks who still accept the DITSCAP certification standard.
Not every version of the honeywall operating system (roo) is accredited. Only specific versions with an accompanying Security Readiness Review (SRR) are available for use. However, the accreditation boundary of the honeywall allows for honeynets freely running and operating within production networks.
Content Staging
There are indicators on all machines that users regularly use any given system. The method of content staging is important when configuring your honeypots (sensors) prior to deployment.
Ensuring that the correct information is on your honeypots is critical from the beginning. Attackers will expect information to be on any organizational system. You must ensure the right data is on the honeypot to entice the attacker to interact with your honeypot for as long as possible.
The following are some items that need to be addressed when performing initial content staging of a honeypot.
Files
When setting up files, make sure the following types of files are on a system and continue to be added to the system as a common computer user. So, whether you want to protect your files or generate a perceptually consistent deception, these files should be updated at least every 48 hours in order to ensure perceptual consistency of a light casual computer user. Remember, perceptual consistency to a remote attacker can be everything. These files are the files a remote Trojan, bot, or crimeware will look through for specific keywords and some will generate keywords based on certain data types. Here is a short list of the major file types that will be searched for. They are present everywhere.
Numerous types of files should be on any given system within user folders:
Network or Organizational
The following are network or organizational considerations:
The following are of more concern when addressing government networks:
Realism
The following are important to make your honeypot look real:
Host and Applications
When setting up your host and applications, consider the following:
You can add realism as follows:
Content Filling
Content filling is the act of regularly filling the honeynet with host and network content that is perceptually consistent with production network traffic, while allowing for additional pieces of information that could be used as bait to entice the attacker into interacting with your honeynet. Content filling is very important when adversaries compromise a honeypot and set up a host or network monitor. Again, you need to think like the attacker. You want the attacker to feel comfortable with the types of host and network activity on any given network segment.
The following are some of the high-level considerations regarding content filling:
Honeynet Training
A honeynet team must be properly trained in order to fully understand the possible components, scenarios, outcomes, goals/objectives, and missions that honeynets can provide an organization. Currently, the following training courses are available:
Honeynet Objectives
An enterprise honeynet or grid project should provide the capabilities to observe the tools, tactics, procedures, and motives used by adversaries attacking the organization(s) you are protecting by monitoring, recording, and analyzing unauthorized traffic traversing simulated networks.
Based on information observed, the following are common honeynet objectives:
Table 8-3 shows examples of types of Gen III honeynet solutions ranging from low interaction to high interaction based suites. As you can see, high interaction is more for the active engagement of a state-sponsored cyber threat or other highly organized group. Low-interaction honeynets are best to serve as an early warning or scanning detection engine. Honeyclients can be used to analyze websites your users are visiting to see if any of them have successfully exploited and modified settings of a system. In our years of practice, we strongly recommend the build you deploy for your Honeyclient should be your own organization’s system build.

Table 8-3 Honeynet Risk/Benefit Matrix
This will always let you know if your corporate build has exploitable vulnerabilities or if your build is missing a protection measure or setting. If your organization has a system build and you automate a honeyclient where you could pass all of your user local area network DNS traffic analysis engine, this honeyclient would then analyze and determine which of your users could have been or might be infected and could be sending information out of your network to organized opportunistic or targeted criminals.
Honeynet Risks and Issues
Honeynets can be a powerful tool. They allow you to collect extensive information on a variety of threats. To obtain this information, you need to allow attackers and malicious code access—potentially privileged access—to your honeypots. As a result, the price you pay for this capability is risk. Any technology developed by a human can also be defeated by a human.
Risk means different things to different organizations. You will need to identify which risks are important to you. Also, organizations have different thresholds for risk. We cannot determine what is right and wrong for you. Your organization must make those policy decisions for itself. All we can do is help make you aware of the risks.
NOTE
We will not address legal issues of honeypots, or specifically honeynets. That is specific to your country and organization. It is recommended that you consult your organization’s legal counsel for more information, especially in reference to privacy or liability issues.
Four general areas are associated with risk:
There are several measures you can take to mitigate these risks beyond what we have discussed so far. Two measures are human monitoring and customization.
With human monitoring, a trained professional is analyzing your honeynet in real time. This gives you the ability to detect a failure in your system—a failure that automated mechanisms may fail to detect or react to. By having a human analyzing honeynet activity, instead of just depending on automated techniques, you help protect yourself against new or unknown attacks or honeynet countermeasures.
Customizing your honeynet can also help mitigate risks. This book and all honeynet technologies, including the Honeywall CD-ROM, are open source and publicly available. This means that anyone has access to this information, including members of the black hat community (who we assume are reading this book and developing counterattack methods). To help reduce risk, you want to modify your honeynet from any default settings or normal behavior. The more your honeynet differs from standard or default configurations, the more difficult it will be for others to detect or attack it. However, understand that no matter what measures you take, risk is not eliminated, but only mitigated.
Check Yourself Before You’re Wrecked
You can improve the security posture of your network by proactively monitoring your network and systems. It is critical to apply various tools that block, filter, and monitor traffic, but you must also think and act like those who wish to do your business harm. Discover what they use to find holes in your network, and use them yourself to test your defenses. Check yourself, discover the weaknesses, and then fix them.
There are complete books that are dedicated to this subject. Here, we’ll touch on some of the higher-level areas that should be checked. The tools mentioned in this section are just a small sampling of those that can be used to take proactive measures to keep you and your network safe.
What’s the Status of Your Physical Security?
An extraordinary number of measures can be applied to your computer systems to lock them down. Antivirus programs, firewalls, file-system security, disk encryption, policies, strong passwords, and so on are great (and necessary) for the overall health of your network, but do you know that they can all be bypassed with the touch of one keyboard button during the boot sequence?
The base state of your system’s security begins at the lowest level of your computer, moving up into the operating system, and then into the applications installed on the system. There are a few easy things you can do to shore up your security at this level, yielding a large return on the time investment.
What Are You Looking For?
Check the following:
How Does Your Wireless Network Look?
You would be hard-pressed to find a company today that doesn’t have some type of wireless network. It’s cheaper than running cables to each workstation and easily allows for the addition of devices, all reducing the overall maintenance cost and overhead. However, if not configured properly, these wireless devices can leave a gaping hole in your network. In addition, if not careful, your business could find itself hosting one or more rogue access points, meaning that someone has placed an unauthorized wireless access point on your network. Don’t discount the usefulness of a wireless network, but make sure you test its security. Table 8-4 lists some free tools that can help you in this effort.

Table 8-4 Free Wireless Network Discovery Tools
These tools work as follows:

Figure 8-8 KisMAC in action
What Are You Looking for?
Check the following:
What’s Traveling on Your Network?
Whether your network is large or small, you likely have a lot of traffic entering and leaving it each and every day. While you are probably reluctant to believe any people you work with would maliciously transmit anything they shouldn’t, you don’t know unless you are an active participant in your network security. Plus, without checking, you may not know until it is too late that one of your coworkers mistakenly clicked on that malware-laden PDF, which caused one or more machines on your network to be recruited into a botnet. Keeping up with all the traffic on your network is a daunting task, but it is a necessary evil about which you must be diligent. Some of the tools listed in Table 8-5, which are available at no cost, may help you in this endeavor.

Table 8-5 Free Traffic Capture Tools
These tools work as follows:

Figure 8-9 Packet capturing with Wireshark
What Are You Looking For?
Check the following:
What About Your Host/Server Security?
Testing the security of the hosts on your network is absolutely critical to ensure that your friendly hacker doesn’t find them for you. Patches are released frequently from multiple application and operating system vendors, and depending on your manpower to adequately push all of these patches, you may find yourself at risk.
What’s more important is that patches are not the panacea of host/server security. They may wind up modifying the security configuration you had to lock down your machines. In addition, unless you have the proper mechanisms in place, do you really know if the patches have made any changes that compromise the security of your network?
You need to take one step beyond the mindset of employing preventative host-based IDSs and IPSs. One small avenue of approach is all your adversaries need to find. It’s better to proactively find it yourself before they can. Table 8-6 lists some of the tools that can assist in these efforts. There are free and paid versions of each tool.

Table 8-6 Host/Server Vulnerability Testing Tools
These tools work as follows:

Figure 8-10 Check yourself with Metasploit
What Are You Looking For?
Check the following:
How Are Your Passwords?
While you may have a robust password enforcement policy on your hosts and network, some are not so fortunate. Your users’ passwords are the gateway into your network.
Usernames can be discovered pretty easily: just look at your e-mail addresses. With one half of the battle down, there’s only one more piece to complete that username/password combination to gain access to your network. As such, it is imperative that passwords be as secure as possible. While enforcing good passwords will not solve all of your problems, a password is one of those targets that your attacker will pine for. Table 8-7 lists some of the tools that can help you in your quest for password security.

Table 8-7 Password Checking Tools
These tools work as follows:

Figure 8-11 Cain & Abel revealing no password for the Guest account
What Are You Looking For?
Check the following:
How’s Your Operational Security?
Well, you’ve made it this far. You are taking all the appropriate measures to protect your systems from compromise, but is it all for naught?
Many of your common and advanced threat actors begin their work by performing reconnaissance on you, your coworkers, your employees, and your company. They will learn as much about your company as possible in order to maximize their chances of success and reduce their risk of getting caught. What better way to gather intelligence on their target than to see what you or those who you work with post online? It’s not only the data contained within the documents that could do you harm, but the hidden data (such as metadata) that can reveal information about your network to the attacker.
One of the tools that can help you find out if you are your own worst enemy is FOCA. You simply point the program at a domain name, tell it what documents you want to check (such as Microsoft Word .doc files), tell it which files to download, and extract the metadata. Figures 8-12 and 8-13 illustrate FOCA in use.

Figure 8-12 Finding publicly accessible documents with FOCA

Figure 8-13 Pulling hidden information from documents
What Are You Looking for?
Check the following:
Crimeware/Analysis Detection Systems
So, you’ve applied some of the preventative measures mentioned earlier in the chapter, and you’ve checked your protection on a regular basis as we just discussed, but they still got in. The people you spent so much time protecting yourself against were able to breach your defenses, muck with your best-laid plans, and take your valued information. Well, that is the nature of the beast. It happens, and it will probably happen again. What comes next and how you learn from the incident will help define the future state of your security.
To really learn from what has happened, you should take some time to evaluate the incident, study the tools used by your attackers to find out how they got in, and incorporate these into your lessons learned. In order to do that, you will need to grab some tools commonly used by digital forensic investigators. Here, we’ll provide a short introduction to some of those tools and concepts. The coverage is not exhaustive, as you can find complete books dedicated to these topics, but it will point you in the right direction.
What Happened on Your Box?
To discover exactly what happened, you can employ the skills of those well-versed in the art of digital forensics. This can involve taking an exact copy of the hard drive on the machine, copying what is currently in the machine’s memory, and analyzing it for artifacts left by your attacker. In addition to a thorough log file analysis, performing this activity can help you determine how attackers got on the machine and what they did once they occupied your space. Table 8-8 lists a couple of tools, one commercial and one open source, that can help you accomplish this task. These tools work as follows:

Table 8-8 Forensic Tools
What Did That Malicious Software Do?
So now you’ve come to the moment of truth. You found a piece of malware that you think is responsible for the malicious gateway into your network. The digital forensic tools described in the previous section can help you find out how it got on the machine. However, now you want to know what it was doing while on the compromised host. Was it communicating with other machines external to your local area network? Was it siphoning information from your network? This is an art, and there are different ways to determine what you are looking for (such as static and dynamic binary analyses), but the small set of tools listed in Table 8-9 can help your team get started on this quest.

Table 8-9 Debugging Tools
These tools work as follows:
Conclusion
There are many tools you can use to protect yourself and your organization. This chapter covered just a small sampling to point you in the right direction so that you can see how they fit into your enterprise security architecture.
Understanding the state of your network is key to implementing a good deception (honeynet) architecture. Likewise, understanding how your enemy operates via the honeynet affords you the opportunity to test your defenses based on the TTPs observed. We’ve covered preventative measures, actively capturing your enemies during the midst of their malicious activity, being proactive in checking your security posture, and taking measures to understand your enemies after your security has been compromised.
Your ability to fend off advanced threats depends on tools such as those mentioned in this chapter. If these are not a good fit for you, take the time to find out which ones are suitable. If you don’t employ tools such as these, it will be very difficult to determine your attacker’s techniques and determine attribution (guess what the next chapters are about).
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
