Mapping Requirements to Functionality
After the business requirements are defined, it is necessary to map those business requirements to functionality. It is also necessary to assign a priority to each business requirement. This priority is used when multiple business requirements are considered in the design as a particular aspect of Active Directory. The best example of this is the organizational unit (OU) structure within a domain. Administrative requirements, end user requirements, and group policy requirements must all be considered when designing the OU structure. The priority helps determine which design consideration, or requirement, takes precedence over the others.
Table 4.1 summarizes the business requirements accumulated thus far in this chapter.
Business Requirements
Business requirements, the lengthiest list, are supported by various features and functionality within Active Directory. Business requirements are also IS requirements in a solid IS environment, but they are still business requirements. Things like simplified administration, application integration, security, flexibility, and availability all top the list of business requirements that must exist before an investment should be made in an application or operating system—especially one that has the far-reaching affects of an application like Active Directory.
Single Seat Administration
Windows 2000 and Active Directory enable a single seat administration model. With Active Directory being a multi-master database, all the DCs in a domain replicate changes between each other. Any changes made by an administrator or user to any DC in the domain are replicated to all other DCs in that domain. The multi-master relationship is not limited to domain data, such as users and passwords, but the Active Directory configuration, Global Catalog (GC), and schema database partitions are replicated between DCs. Although the domain database partition is replicated between all DCs in the domain, the GC between all GC servers in the forest; the configuration and schema database partitions are replicated between all DCs in the forest. This allows for a centralized administrative model in which administrative tasks can be delegated to pre-defined administrative groups; each is granted specific administrative rights. In earlier version of Windows NT, administration was not flexible. The domain model had to reflect the administrative structure of an organization. With Windows 2000, the domain model is not overly influenced by the desired administrative model because administrative responsibilities can be delegated within a domain through groups and OUs.
Infrastructure for Business Applications
Active Directory is a distributed database that serves as a directory. As such, it provides a directory infrastructure for business applications. Several applications, such as Microsoft Exchange, use Active Directory as their sole directory. Other business applications can also take advantage of this unified directory, not only as a source of directory information, but also as a repository for application specific directory information. Microsoft is publishing an Active Directory development guide that outlines the types of information that can and should be stored in Active Directory. Businesses can use this as a guideline in developing applications that take advantage of this investment.
Another example of an application that should be integrated with Active Directory is the average HR application. An interface between a company's HR database and Active Directory can move the administrative burden of updating the user portion of the directory from IS and to HR (where it belongs), allowing HR personnel or the HR application to administer the objects that they have permission to administer. As users come and go, Active Directory automatically reflects these changes and accesses to resources are granted or denied based on the type of employee hired or fired.
Integration with BackOffice
It is only logical that Microsoft BackOffice applications evolve into a model that uses Active Directory. Microsoft Exchange, System Management Servers (SMS), Site Server, Proxy Server, and SNA Server are examples of applications that adopt the Active Directory security subsystem as their primary security interface. The resources and services these applications provide are subject to Active Directory security and security principals (users and computers). The rights that a security principal has either allow or deny access to BackOffice services. Active Directory also provides directory services to BackOffice applications as appropriate.
Again, Microsoft Exchange uses Active Directory as its directory, no longer supporting its own directory as in earlier versions. Users access Active Directory to resolve mail recipients (such as other users), mail enabled contacts (Custom Recipients), and distribution groups (distribution lists). Exchange, therefore, becomes a message store providing various protocol accesses to message store services for Active Directory users.
Directory Integration
Directory integration is available through the tools included with Windows 2000 and third-party products. Tools support application coexistence with Active Directory. For example, the Active Directory Connector (ADC) synchronizes Active Directory with the Exchange 5.5 directory. Tools, such as the Microsoft Directory Synchronization tool (MS DirSync) , allow for synchronization between Active Directory and Novell Directory Services (NDS) version 4.1x or greater. These tools facilitate Active Directory in becoming the single source of directory information for users and the single source of directory administration for administrators .
Centralized Resources
As Active Directory centralizes users in a single, distributed directory, it also centralizes resources. There are several object-classes that Active Directory can host, such as computers, printers, and DCs, which give users and administrators the ability to locate and access these resources through Active Directory. After Active Directory contains these resources, they can be managed through Active Directory. For example, policies can be set at the domain, OU, and site level that define what can be done on a computer or resource. Depending on the location of the computer in the domain, different policies can be enforced. Say you have a group of workstations that are in an unsecured area within your organization and are used for anonymous access to public resources. Policies can be set for those workstations that limit how they can be used, such as preventing the floppy drives form being accessed or software from being installed.
Security and Controlled Access
Active Directory is the Windows 2000 security subsystem. Not only does it define the users and resources in an organization, but what those users and resources can do within an organization. Through access control lists (ACL), users are granted or denied access to resources. Kerberos is used to provide authentication between client and server when accessing Active Directory. As a business requirement, user access to resources should be tightly controlled based on granted permissions that a user inherits through group membership or permissions a user has explicitly defined. The authentication process is also secured, through Kerberos, which guarantees the user accessing a resource is actually that user, and the computer being accessed is actually the intended computer. Chapter 15, "Developing a Network Security Strategy," gives a full explanation of Kerberos, and how it is used.
Flexible to Business Changes
Active Directory, if designed correctly, is flexible to business changes. It can support multiple organizations with unique identities (DNS namespaces) in the same directory.
Objects within a domain can also be moved with a click of the mouse. Between domains, objects can be moved (when in Native Mode) using tools included with Windows 2000. As users move between departments, groups, or locations, their location in Active Directory can also move. This is important in today's business environment. As a business requirement, a directory needs to be able to change with an organization. How Active Directory is designed depends on the amount of changes an organization goes through. If an organization, for example, is growing through mergers and acquisitions, Active Directory should be designed to be extensible and allow for distributed administration.
Executive Requirements
Executive requirements are general in nature, as are the aspects of Active Directory that satisfy them. Identifying these requirements legitimizes Windows 2000 with Active Directory as a next generation operating system that can add value to the way an organization does business.
Increased User Productivity
Many aspects of Windows 2000, other than Active Directory, help to increase user efficiency and productivity: Microsoft Installer, IntelliMirror, Plug-and-Play, Distributed File System (DFS), and high availability through clustering, just to name a few. Active Directory, specifically, helps increase user efficiency by virtue of being a single source for directory information, distributed across the enterprise, and available through multiple user applications. By having a single source of directory information available to users, regardless of their location, Active Directory provides a familiar, information-rich, directory to all parts of the enterprise.
Reduced TCO
Reducing cost of ownership entails reducing the cost of the workstation and software, along with reducing the maintenance and administrative overhead spent on each workstation. Simply upgrading an existing Windows NT domain structure to an Active Directory domain structure is not likely to reduce the cost of ownership. However, implementing Active Directory in such a way that increases service availability, reduces administrative overhead, and streamlines user and computer maintenance does have an overall effect of reducing the amount of resources necessary to support a computing environment.
Implementing Active Directory provides services to end users that are common across multiple applications. This makes users more productive by giving them more time to do their job because they are spending less time negotiating each application's directory. As a business requirement, a case can be made that Active Directory reduces administrative overhead and increases user efficiency, thus reducing TCO.
Competitive Advantage
A reduction in cost of ownership and an increase in user productivity can reduce the overhead in an organization, making it more competitive. Active Directory as a service is easy to use, has high availability, and provides the functionality that reduces maintenance costs; this has the effect of increasing user performance and reducing maintenance costs.
Maintenance costs are reduced by using Windows 2000, Active Directory Group Policy Objects (GPOs), and even SMS to deploy applications to specific groups within the enterprise. Rather than having a technician visit each workstation to upgrade Microsoft Office, the application is published or deployed automatically. Locking down the workstation with policies so that users cannot break their software reduces the amount of Helpdesk calls, which also reduces maintenance costs.
Administrative costs are reduced by developing and implementing an administrative model that fits an organization's requirements. Delegating administrative tasks to those groups who require them can reduce administrative costs by decentralizing some administrative functions to specific groups in an organization.
IS Requirements
The requirement of the business, its customers, and employees are rolled up into IS requirements; because after all, IS is the organization that designs, deploys, and supports the technologies that provide functionality to the business. Active Directory satisfies some IS specific business requirements.
Controlling the Environment
Active Directory, through the domain and OU structure, enables group policies to be deployed and enforced throughout the directory. An OU structure is devised that meets an organization's administrative model and allows group policies to be applied in such a way that users in specific OUs adhere to the policies of that OU and all the OUs that are above it. Through inheritance, group policies flow down through the domain, site, and OU structure and are cumulative.
Figure 4.1. Group policies are cumulative.
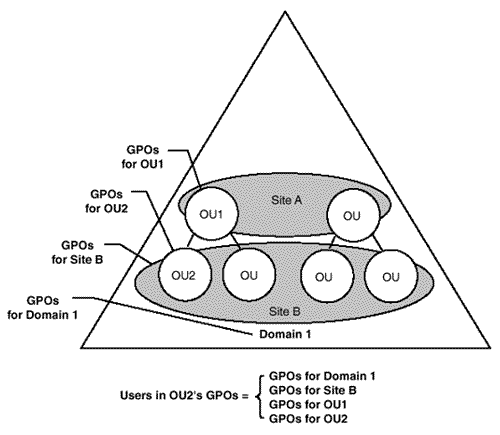
In Figure 4.1, policies can be applied at the site, domain, and OU level. If a user exists in the OU2, they are subject to the group policies of the Domain 1, the Site B, and OU1 and OU2. This means that the applications that are applied to OU1 are also inherited down to OU2. Policies that are applied to Site B are applied to the users and computers in that site. It is this type of domain, site, and OU structure that can be designed and deployed to give IS control of the environment.
Providing Services to the Client
The software distribution functionality that comes with Windows 2000 is dependent on Active Directory. Active Directory provides the security context necessary to determine if a user or workstation is eligible to receive a software distribution. Software can be published to that user so that he or she can install it if necessary, or it can be mandatory so that it is installed upon startup. This decision point uses Active Directory to determine what applications a user has available.
Fault Tolerance
Active Directory is a fault tolerant service by virtue of its distributed databases. When a DC fails, clients attempt to contact other DCs for directory services. Therefore, as long as there is more than one DC, directory services are available to the client. Now there are additional considerations, such as the placement of the DCs and the other services that Active Directory clients are reliant on, like DNS and the GC. If the Active Directory architecture is designed correctly, each of these services has built-in redundancy. This enables the DC to service clients in the event of another failed DC or other failed Active Directory reliant service.
Administrative Requirements
Administrative requirements are defined on a per organization basis through an administrative model developed as part of the Active Directory architecture each organization deploys. The administrative model can be centralized or distributed, depending on the organization and its physical and internal structure. Active Directory has the capability to meet the requirements of either a centralized or a decentralized administrative model through its domain and OU structure by delegating authority based on that specific model.
Automated Administration
To help streamline administration, Windows 2000 has a script engine that allows Active Directory administrative tasks to be automated. As administrative responsibility is delegated throughout an organization, different support or administrative groups are responsible for specific administrative tasks. It is possible to develop scripts, using ADSI, that walk these groups through their administrative tasks. For example, a script could be written that would be fed by an HR system. The HR system would upload updates that a script would use later to change Active Directory. This would be a move toward automating account creation and deletion within Active Directory. Active Directory, out of the box, gives an organization everything necessary to administer their environment. However, the scripting capabilities of Active Directory greatly expand the administrative possibilities that Active Directory provides. A more detailed description of scripting Active Directory can be found in Chapter 19, "Scripting with Active Directory."
Delegated Administration
Delegating administrative authority allows for a distributed, or partially distributed, administrative model. Defining administrative groups and delegating administrative authority to those groups is how an administrative model is implemented.
As with group policies, permissions are also inherited down the OU hierarchy. When you apply permission to an object, that permission can be propagated to that object's sub-objects (or child objects).
Administrative function can be delegated by assigning permissions in a specific OU or by assigning permission to change the permissions on objects at the attribute level. By delegating permissions at the OU level and allowing the appropriate users or administrators to administer that OU, administrative responsibility is distributed.
Attribute Level Security
Within Active Directory, administration can be specified beyond the object level to the attribute level. Administrators can be granted the ability to only change passwords on user objects for example, without having the ability to change the other attributes contained in the user object.
Security Requirements
Security in Active Directory is paramount. Active Directory is the security subsystem for Windows 2000. As such, it is important that each aspect of Active Directory, from the database to client communications, be secure.
Single Sign-On
Because Active Directory is a single distributed directory, which can be utilized by applications for user information, it is possible to have a single user logon or single sign-on. After a user is authenticated by Active Directory, that user has access to the resources to which they have been granted permission (inherited or otherwise). The user is also able to access services provided by Active Directory integrated applications without having to logon again. This means only one security policy need be maintained, one password managed by the user, and one account managed by the user administrators.
Strong Passwords
Because Active Directory aspires to be the single source of directory information and to grant or deny access to resources, it is important that a strong password policy be an option. Active Directory supports a strong policy option.
Secure Database
The Active Directory database, when hosted on an NTFS partition, is encrypted and secured. An Active Directory database cannot be copied to another Windows 2000 server with a different administrator password because that would allow that administrator to take control of the directory.
Secure Client/Server Communications
Kerberos is a secure method for authenticating a request for a service. Through Kerberos, a user or process requests an encrypted ticket from an authentication process, which can then be used to request a particular service from a server. The user's password does not have to pass through the network. This keeps passwords and other traffic between the client and server secure.
Desktop Management
Desktop management, through application control and maintenance, and desktop lock-down, helps reduce desktop maintenance and make users more productive. This has the intended result of lowering TCO and improving user efficiency.
Application Control
Through the Active Directory structure, GPOs can be created that dictate to which applications a user has access. Again, designing an Active Directory structure, which meets the application requirements for certain groups, provides those users with the applications they require, but nothing more. Moreover, users can be denied the ability to install their own applications based on their location in Active Directory. This can have the effect of increasing user performance and reducing desktop maintenance costs.
Windows 2000 and Active Directory can also be used to ensure users have applications that work. If a user or application deletes or corrupts a file that is necessary for an application to run, the deleted or corrupt file can automatically be replaced on that desktop. This reduces the number of Helpdesk calls, thus reducing maintenance costs and increasing user efficiency.
Desktop Lock-down
Desktop lock-down is achieved through GPOs. The ability to lock-down the desktop can have a significant impact on the cost of ownership. Through GPOs, desktops can be locked-down so that users can only change things for which they have permission. Designing an Active Directory structure which allows resources to be grouped in Active Directory in such a way that group policies can be applied in a logical fashion, enables desktops to be locked-down when and where appropriate.
Inventory Management
Locking down the desktop so that users only have access to applications assigned to them, makes it easier to maintain an accurate application inventory. This can allow organizations to maintain application licenses for only a subset of users and allow users to roam from computer to computer with their assigned applications always available to them.
End User Requirements
It is true that Active Directory, and the design considerations around the domain and OU design, is mainly driven by administrative requirements. However, it is important to also consider the end user. Not only can end users query Active Directory, but they can also browse Active Directory. If they are looking for a printer in a certain location or a group of users in a department, browsing Active Directory can be the most efficient way to locate these resources. If Active Directory is not designed in a way that compliments how users browse it, Active Directory's usefulness to the end user is compromised.
