Server directory structure
It is important for a user or an administrator to understand the directory structure of a Geronimo server installation. The directory structure of a v2.1.4 server is shown in the following screenshot:
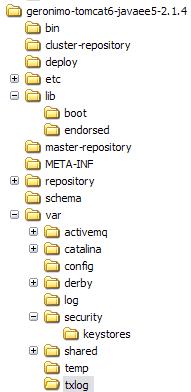
Please note that the directory that we will be referring to as <GERONIMO_HOME> is the geronimo-tomcat6-javaee5-2.1.4 directory shown in the screenshot.
The following are some important directories that you should be familiar with:
The bin directory contains the command scripts and the JAR files required to start the server, stop the server, invoke the deployer, and start the GShell.
The etc directory contains the configuration files for GShell.
The lib directory contains the JAR files required to start the basic Geronimo framework.
The var/config directory contains Geronimo configurations files. A Geronimo administrator or user can find most of the configuration information about the server here.
The var/derby directory contains the database files for the embedded Derby database server.
The var/log directory contains logging configuration and logfiles.
The var/security directory contains user credential and grouping files.
The var/security/keystores directory contains the cryptographic keystore files used for server SSL configuration.
The following are some important configuration files under the Geronimo directory structure:
config.xml: This file is located under the <GERONIMO_HOME>/var/config directory. This file preserves the information regarding GBean attributes and references that were overridden from the default values used at deployment time.
config-substitutions.properties: This file is located under the <GERONIMO_HOME>/var/config directory. The property values specified in this file are used in expressions in config.xml. The property values in this file can be overridden by using a system property or environment variable with a property name that is prefixed with org.apache.geronimo.config.substitution.
artifact_aliases.properties: This file is located under the <GERONIMO_HOME>/var/config directory. This file is used to substitute one module or configuration ID for another module or configuration ID. The entries in this file are of the form oldArtifactId=newArtifactId, for example default/mylib//jar=default/mylib/2.0/jar. Note that the version number in the old artifact ID may be omitted, but the version number in the new artifact ID must be specified.
client_artifact_aliases.properties: This file is located under the <GERONIMO_HOME>/var/config directory. This file is used for artifact aliasing with application clients.
server-log4j.properties: This file is located under the <GERONIMO_HOME>/var/log directory. This file contains the logging configuration for the server. More details about this configuration can be found in Chapter 13, Logging.
deployer-log4j.properties: This file is located under the <GERONIMO_HOME>/var/log directory. This file contains the logging configuration for the deployer. More details about this configuration can be found in Chapter 13, Logging.
client-log4j.properties: This file is located under the <GERONIMO_HOME>/var/log directory. This file contains the logging configuration for application clients. More details about this configuration can be found in Chapter 13, Logging.
users.properties: This file is located under the <GERONIMO_HOME>/var/security directory. This file contains the authentication credentials for the server. See Chapter 6, Security, for more details.
groups.properties: This file is located under the <GERONIMO_HOME>/var/security directory. This file contains the grouping information for the users defined in users.properties. See Chapter 6, Security, for more details.
Among the directories that contain sensitive information, such as user passwords, are var/security, var/derby, and var/config. These directories should be protected using operating system provided directory and file security.
