The CMO and CPO—Convergence Between Privacy and Security
By now, you have had the opportunity to discover the responsibilities and roles of most CxOs as they relate to cybersecurity in an organization. The Chief Marketing Officer (CMO) has the job of leading a company’s efforts to create, communicate, and provide value-added solutions to consumers, clients, and business partners. This includes collecting data used to determine marketing strategies. When it comes to protecting employee data and customer information, the Chief Privacy Officer (CPO) is the executive responsible for putting in place policies and procedures and ensuring compliance with privacy laws and regulations. Privacy policies should outline how businesses handle information obtained from customers, clients, and employees.
In simple words, a CMO aims to collect data and ensure the expansion of business with leads, while the CPO may slow down that process by managing the risk of noncompliance during data collection, process, storage, or disposal.
Both roles are incredibly critical to a business and essential to the business’s cyber resilience.
There’s a lot of talk in the business world these days about the CMO and the CPO, but what do these roles actually entail? What do they have in common, and where do their responsibilities diverge? In this chapter, we’ll take a closer look at both the CMO and the CPO and explore what makes them both so important to businesses’ cyber resilience.
We will cover the following topics in this chapter:
- What the CMO and CPO roles have in common
- The role of marketing and privacy in cybersecurity
- The intersection of privacy and security
- The role of marketing and communication following a cyber incident
- Questions to ask your CMO and CPO
What the CMO and CPO roles have in common
Everything revolves around data, and data is what both of the CMO and CPO roles have in common—one collects it and the other protects it.
With regard to clients, marketing has access to the most sensitive information. It is the responsibility of the marketing team to indicate how the information was gathered with technology, and how it will be utilized by the company. (The technology marketing uses generally will have been approved by the CTO or CIO.) As a result, the CMO must ensure the team adheres to data best practices. Those best practices are usually defined by the privacy policies established by the CPO, in alignment with the relevant privacy regulations and laws. For example, features such as unsubscribing from mailing lists or notifications of privacy policies are mandatory by law in certain countries.
As soon as the data is collected, both the CMO and CPO need to make sure they handle it properly, as each data record relates to an individual, and a breach can cause long-term harm to the victim—for example, identity fraud. On the surface level, there might seem to be a conflict of interest between both roles, as the CMO looks to acquire and use customer data while the CPO endeavors to safeguard it.
CMOs and their teams today are incredibly data-driven. They ingest and exploit vast volumes of data with analytics to do more than just create new leads. Data-driven CMOs and their teams are entrusted with ensuring every touchpoint of a firm is personalized to each client’s unique customer journey.
To collect the data, a company must acquire and use a variety of tools and systems. In addition to these tools, marketing departments also use third-party suppliers for a broad range of tasks, and many of these services are linked directly to a company’s core systems through its website or applications. While these technologies are essential in ensuring a memorable customer experience, they also create major security and privacy risks to the company’s user data. Unauthorized parties may access consumer data through a third-party tag on a website, all without the company’s knowledge.
CPOs need to be aware of any marketing suppliers that may have access to a company’s customer data because of the risks that marketing technology poses to the organization. However, this does not imply that the CMO and CPO’s aims are directly in conflict. Both roles are concerned with making sure consumers have a positive experience with the business, and this includes protecting their personal information.
Vendor screening, internal communication, and manual procedures can’t completely remove the risks associated with third-party vendor partnerships. CMOs and CPOs need to realize this. If CMOs and CPOs want to avoid a tug of war over customer data and third-party technology and work together for a company’s interests, they need to put in place effective marketing security and data protection measures, bringing the CISO into the game.
In the end, CMOs and CPOs have more similarities than they realize. They may be the two most knowledgeable people in the company regarding the importance of customer data and a positive customer experience. Both roles need to work in sync and foster a strong and collaborative relationship.
In the next section, we will describe how these two executives can focus their time on the initiatives that matter most to the future of their company, with the help of the proper technology, rather than just being micro-focused on data privacy procedures.
The role of marketing and privacy in cybersecurity
There’s no doubt the introduction of the General Data Protection Regulation (GDPR) in 2018 has had huge regulatory impacts on all businesses, including those outside of the EU and UK. The GDPR replaced the 1995 Data Protection Act and sets out new rules around how personal data must be collected, processed, and stored. Businesses that don’t comply with the GDPR can face hefty fines, so it’s essential to understand what these changes mean for your organization.
GDPR mandates that all companies introduce new policies, methods, and practices for handling the personal data of their customers, users, suppliers, and employees located in the EU. As a result, any organization anywhere in the world interacting with EU residents’ personal data must adhere to the new transparency, security, and accountability criteria set out by the EU.
In Singapore, the Personal Data Protection Act (PDPA) provides a basic level of security for personal data. As a supplement to industry-specific laws and regulations, such as those governing banking and insurance, it consists of a number of standards that regulate how personal data is collected, used, disclosed, and handled in Singapore. As a part of this legislation, there will be a nationwide Do Not Call (DNC) registry.
In Australia, the Notifiable Data Breaches (NDB) scheme aims to strengthen the protection of people’s data and improve consumer confidence that their data is safe. As part of the NDB scheme, Australian organizations must notify individuals who may be at risk of serious harm from a data breach—where a reasonable person would expect the breach to cause serious damage in the form of physical, emotional, financial, economic, or reputational harm.
Individuals are increasingly aware of the trend toward collecting personal information and monetizing data. Consequently, customers’ expectations for data privacy are rising.
According to the Trusted Tech Report from the Consumer Intelligence Series, 84 percent of customers will stop doing business with a firm if they don’t feel confident it processes, stores, and transfers their personal information safely and securely. A company’s ability to preserve client data is critical to maintaining consumer trust.
As customers’ expectations increase, privacy and security become even more intertwined.
It starts and ends with data management, or rather data governance. The collection, generation, identification, categorization, inventory, protection, and destruction of data are governed by processes and technology.
- Data protection: Both the marketing and privacy functions should enable effective communication programs and training, raising employees’ understanding of how the data governance process happens and where risk might arise, focusing especially on potential risks around data breaches and regulatory noncompliance.
- Business differentiator: Customers and other external stakeholders, such as regulators, want to understand and ensure data protection across the data life cycle within the technological realm. This competitive advantage can only be achieved with an unwavering and united view of the company’s approach to its customers, shareholders, and regulators.
- Privacy by design: Adding software capabilities and features that generate or gather large amounts of data, most of it personal data, is a common practice for most businesses. It is cheaper to integrate privacy and security controls and practices right from the design phases, rather than having to add them to a product or service after it has been launched. Companies can generate a single set of specifications and a uniform experience for developers to guarantee products and apps are developed in a trustworthy way, by converging the cybersecurity and software development teams.
Risk mitigation
CMOs and CPOs have a key role in risk mitigation and cybersecurity response. Data loss, information corruption, unauthorized access to confidential documents, and the inability to access critical systems are all possible outcomes of cyberattacks, and they represent critical cyber risks for a firm.
For CMOs, however, the most important consideration is the impact on brand reputation, consumer trust, and revenue. Nick Flude, Sekuro’s CMO, and former CMO of Secure Code Warrior and F5 Networks’ Head of Marketing A/NZ, shares his perspective that “CMOs are the head cheerleader for the company’s customers and brand. As such we are acutely aware of that responsibility to protect both. We also have access to the company’s CRM, so have access to all that valuable personally identifiable information (PII).
“Global CMOs also grapple with differing regulatory environments regarding PII. As a marketer, I really want to know everything about you, but as an ethical marketer, I know I can only ask for what is deemed necessary to achieve the thing being engaged with, and I have to be able to demonstrate my handling of that PII when asked. I’ve worked with the governance, risk, and compliance team on privacy policies, terms of use, collection statements, etc. Personally, I’ve taken the strictest regime—GDPR—and built all my systems and processes to adhere to that, irrespective of where my business has been geographically located.”
The legal consequences for marketing activities can be quite severe, especially if data theft is involved. Depending on the severity of the noncompliance, a company could be fined up to several million or even be forced to dissolve entirely. In addition, individuals responsible for protecting the compromised data in the event of theft may also face jail time in some countries.
With more and more companies collecting and storing customer data, the risk of this data being stolen or leaked has also increased. This has led to a number of high-profile legal cases, such as the 2016 LinkedIn data breach case that saw the personal information of over 100 million users leaked.
The financial costs to companies keeps going up, too, as we’ve noted several times throughout the book.
For CPOs, the most important consideration is compliance with the regulatory requirements during a data life cycle. An organization’s reputation and brand might be tarnished if sensitive or personal data is leaked, damaged, or destroyed.
A company’s ability to continue operating might even come under threat if it is involved with a major data breach. Financial costs have risen 10 percent from its prior year, with losses estimated at $4.24 million per incident on average, and with 38 percent of that amount coming from lost revenue, according to Ponemon Institute and IBM. When a firm’s reputation suffers as a result of a breach, customers are less likely to do business with that company in the future, further impacting the bottom line. At the very least, people want to do business with those who can keep their personal information safe.
Brand damage from cyber risk—in the form of fines and the on-flow impact of losing customer trust—can be very tangible. This is illustrated by Marriott’s loss of about $600 million after its 2018 data breach (https://www.reinsurancene.ws/marriott-breach-cyber-industry-loss-could-be-up-to-600m-air/); it suffered long-term brand damage and saw some customers switch to its competitors. Every company, and everyone within the company, should be aware of the ramifications of external data breaches like this.
Figure 9.1 demystifies the overlapping responsibilities between the CMO, CPO, and CISO.

Figure 9.1 – High-level roles and responsibilities
An organization’s data governance structure defines who has power and control over data assets and how those data assets may be utilized. People, procedures, and technology are all part of the data asset management framework. All personal data must be maintained with the utmost care, including real protection while using technology.
To guarantee protection, the CMO needs to provide clarity and visibility on the company’s data collection processes, among other things, and then collaborate with both the CPO and CISO to maintain data protection through established standards for security and privacy. This includes but is not limited to all current legislative requirements and those that may come into effect, while data is stored online or by digital means.
A policy that integrates both security and privacy should assure that the CMO champion the deployment of the most up-to-date security procedures. The CMO plays an important role throughout the data life cycle in ensuring all investments and customers are protected. In the following section, we will discuss adopting this convergent operational model, integrating security and privacy programs, and aiming to safeguard personal information, and how the best practices used to do this have a lot in common and can be leveraged widely.
The intersection of privacy and security
Organizations’ data owners often face conflicting mandates and data requests when privacy and security teams work independently. A single information risk governance team may save money and create a more efficient process. As a result, it is easier for the company’s data owners to fulfill their responsibilities of interpreting and enforcing the law.
Separate programs for privacy and security put stakeholders in danger of being misled, and resources are at risk of being wasted because of the separate, sometimes duplicate, plans and implementation efforts. Integrating both programs allows for much more effective work.
In the context of privacy and security, this usually means developing risk assessment procedures that stakeholders must complete before implementing their projects (sometimes known as “security reviews” or “privacy impact assessments”). With a single risk assessment team, both programs’ criteria may be met, eliminating duplicative procedures that demand the attention of the stakeholders and providing essential knowledge on new business endeavors and technologies. It is thus possible to offer a single set of requirements and suggestions for a risk-managed business activity, which results in a more timely and cost-effective execution.
Per the World Economic Forum, privacy laws increasingly and oftentimes require data protection. Enabling and achieving this requires the support of the CISO.
The privacy framework Venn diagram in Figure 9.2 depicts the convergence between privacy and security very well. Traditional privacy and cybersecurity tasks have overlapping areas of interest.
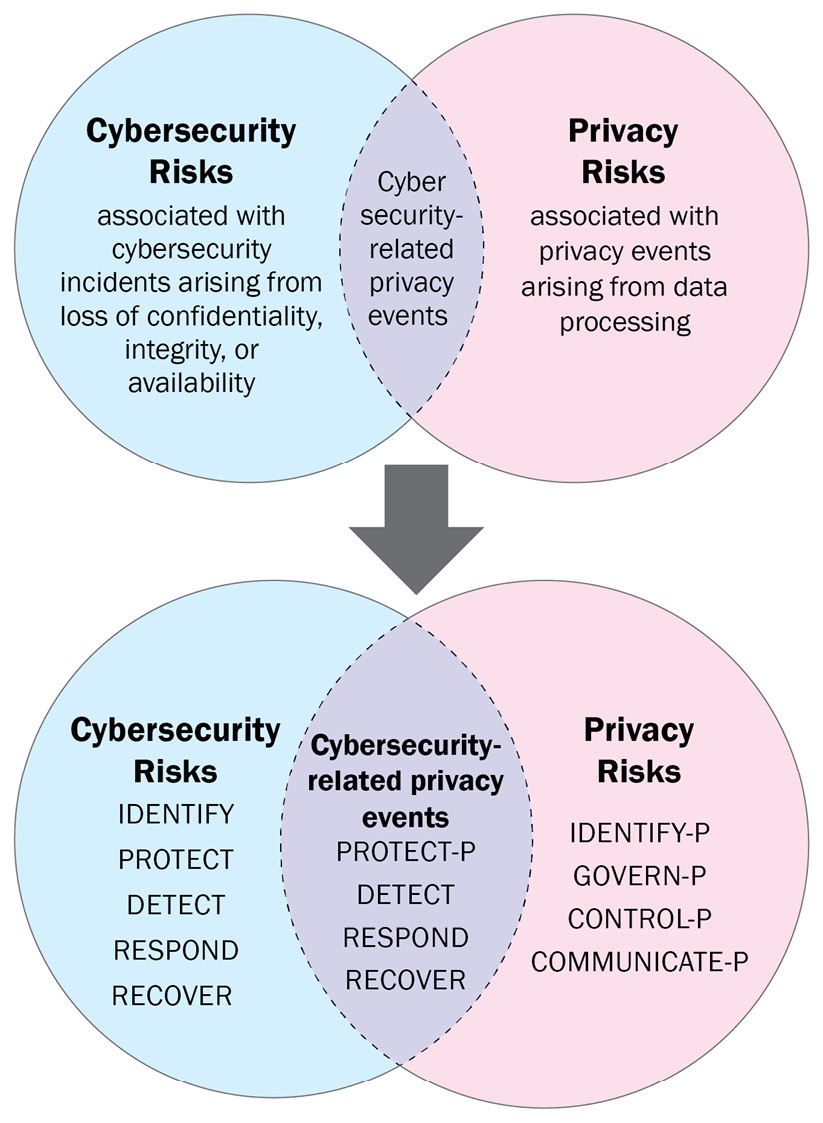
Figure 9.2 – The privacy framework Venn diagram
Although strategic data deletion is one of the most cost-effective and efficient ways to reduce data security risk, security teams frequently disregard privacy controls, even though strategic data deletion is a critical component of most privacy initiatives. Data that has been disposed can be a target of cyber criminals.
In Figure 9.2, individuals’ rights to access and erase their data are protected by a number of practices found on the diagram’s privacy-only side, such as having a legal basis for data collection, being clear about data-sharing procedures, and being fair in how personal data is put to use.
The CMO and CPO share a number of goals in cybersecurity, such as protecting an organization’s valuable data and ensuring the availability of systems critical to the organization’s operations. This includes protecting product designs, strategy documents, and company financials. However, there are many domains where the security and privacy functions perform comparable or related duties with similar aims, and interact with the same stakeholders in the middle.
For this reason, companies should try to take advantage of the synergies between privacy and security teams and consider merging their operations.
In the following section, we will take a closer look at how these advantages can be exploited in more detail with a specific case of a data breach response.
The role of marketing and communication following a cyber incident
When a company is breached, news spreads. It hits the news headlines. The brand and reputation of the business are threatened. People speculate, and customer confidence is impacted. You also often see a sudden downward dip in the company’s share price on the stock market.
More and more mature companies increasingly recognize the importance of having a cyber-resilient organization, which contributes to the business’s sustainable growth, and the CMO plays a valuable part in this.
It is chiefly the CMO who is responsible for customer trust, brand, and reputation. With the marketing and communication resources they have at their disposal, much can be done to support and promote cybersecurity awareness internally. In building a healthy security culture, the CMO plays a key role in focusing on the customer/client data, ensuring simple things such as not sharing or sending spreadsheets of PII, and working closely with its vendors to establish what level of PII needs to be shared so that services can be delivered.
For businesses that have strong existing security practices, promoting their internal practice externally can also be leveraged as a marketing tool to instill confidence in their customers.
In a cyber incident or a cyberattack emergency, communication is key and the breach response messaging is critical. The CMO’s role, together with their access to CRM systems and data, will become instrumental for public relations (PR) and communications. They have to operate quickly and objectively, working closely with the CISO to communicate internally and managing PR and external communications to everyone who has been impacted. As much detail as possible should be given without finger-pointing or blaming. An organization requires an incident response that involves the key stakeholders, including the CMO, CPO, and CISO. Such communication plans should be included in the business continuity plan and disaster recovery plan.
In the event of a privacy or data breach, it must be analyzed immediately and the CPO notified as soon as possible when personal data is involved. The CPO needs to be involved to determine whether the company is obligated to report the incident, per regulation requirements. The mandatory incident reporting requirements in Australia require every private and public company to report a cyber breach to the Office of the Australian Information Commissioner (OAIC). Also, if the company’s annual turnover is $3 million or more, they are obligated to notify the customers affected as soon as they become aware of the breach.
In Singapore, as another example, the PDPA requires data breaches that involve more than 500 records to be reported. After such an incident, CMOs and the marketing team might work to repair the damage for months, if not years. They need to make sure everyone on the team and the company’s social media accounts are conveying the same consistent message and tone.
During the hysteria and confusion of a cyber event, it is easy to overlook accountability and the involvement of key stakeholders. In addition to cybersecurity and risk officer updates, the CMO, CEO, and board members should get reports on reputational risk from the CRO/Environmental, Social, and Governance (ESG) department. Customers’ faith in the CMO and CEO must be safeguarded in the event of a security incident.
An example of a good response occurred in 2017, when a third-party provider, through a human error, exposed an Australian Red Cross Blood Service file containing information on roughly 550,000 potential blood donors . Those who were impacted and the Australian Information Commissioner were quickly alerted by the organization. According to the Commissioner (https://www.oaic.gov.au/updates/news-and-media/australian-red-cross-blood-service-data-breach#australian-red-cross-blood-service-data-breach), “Australians may be assured by how the Red Cross Blood Service reacted to this situation. At every stage of this process, they have been completely truthful to the public, open with my office, and accept full responsibility.”
In times of crisis, it is key to communicate properly with consumers, suppliers, employees, regulators, and other stakeholders to ensure that cyberattacks aren’t made worse by inadequate planning and communication. CMOs are professionals in this area. They must be prepared to be at the forefront of an organization’s response during a cyber event. If a company’s marketing staff downplays the gravity of a data breach, they risk further harming their company’s reputation. In Cyber Mayday and the Day After, by Shamane and her co-author Dan Lohmann, their different research studies revealed that the gravity of post-crisis outcomes is impacted by the communication that goes out during the crisis. Even if the information is not be available right away, a company that takes ownership of the crisis through speedily acknowledging it and providing an official channel for updates and feedback can be a game changer in rebuilding trust and mitigating the loss of customers.
With the current communication landscape, where misinformation and disinformation abound, an information vacuum will only be detrimental to an organization’s reputation. The crisis communication process must be part of regular simulation exercises testing an incident or data breach. This will ensure that a holistic and pragmatic approach is taken and that efforts are streamlined, with no redundant tasks.
So, it’s crucial your CMO and CPO are in alignment, and are part of the cyber risk management team. The following section highlights the most important questions to ask both your CMO and CPO executives.
Questions to ask your CMO and CPO
When a firm starts growing quickly with a data-driven marketing strategy, it is critical to ensure privacy and security are integrated at every step, rather than considering them at the end of the process. The following questions for your CMO and CPO are the ones we recommend focusing on initially:
- Who owns the data governance process? Does this process involve our CPO (or CMO) and our CISO?
- Is there any redundancy in our privacy and security assessments? How can they be further streamlined?
- How do we ensure efficient compliance with data protection requirements, especially with the current massive technological adoption?
- Does our incident response process include the CMO, CPO, and CISO?
- Is there a communication/PR plan to respond to a cyber incident and data breach?
We close this chapter with an important message in relation to the correlation and convergence between various roles and responsibilities. In our current environment, highly technologically dependent organizations need to consider streamlining most of their programs to reduce costs and mitigate risks.
Summary
In this chapter, we have seen the importance of the CPO and CMO in building a company’s cyber resilience, as well as their roles during a data breach incident. A data breach could tarnish any company’s reputation permanently, and the reputational damage might be more difficult to recover from than monetary losses. It may result in customer churn and revenue losses. Potential new clients will be turned off by tainted Google searches and constant unfavorable coverage in the media.
A data breach is a long-term problem rather than just a single incident. It requires appropriate data protection and a proper data breach response in case of an incident. To achieve those results, collaboration between various CxOs is critical and remains at the core of successful preparation and recovery. From the CEO to their executive team, everyone in an organization needs to understand their role and collaborate with each other.
The next chapter addresses the key success factors for developing an effective cyber-resilience strategy that includes all these key players working together from the top down, specifically the board of directors.
