The CEO Cyber Manual
If we could travel back in time even just a few years, no one could have imagined a global pandemic would strike, causing massive social upheaval and affecting almost every sector. The COVID-19 pandemic that swiftly transmitted to almost every nation in early 2020 impacted life as we know it, including how we work, interact with each other, and, essentially, how we live.
Businesses and educational institutions shut down, employees were forced to work from home or remotely from other locations, supply chains were disrupted, individuals were compelled to self-isolate, most travel was prohibited, and in-person meetings and conferences transitioned to virtual gatherings. When we started writing this book, these interruptions had already been going on for several months. Even as we put our pens down, nearly two years later, the times we live in have changed drastically, and the economic, commercial, and social consequences will be felt for years.
Nonetheless, businesses need to operate in this new environment. Livelihoods depend on it. Corporate operations and services need to keep running smoothly and efficiently. Technology has been a viable solution, used in both conventional and creative ways.
With more businesses adopting digital technologies in their bid to improve efficiency, value, and the pace of innovation, we have found ourselves in the age of digital transformation. Many processes and services are continuously moving online, and technologies such as cloud computing, robotics, drones, artificial intelligence, chatbots, virtual realities, augmented reality, autonomous systems, and the Internet of Things is shaping the future of the workplace.
Technology plays a vital role in all activities, from operations in healthcare, business, education, government, the legal system, and community services to consumer-connected houses. Recent technological advancements have altered significantly how we conduct our everyday personal and business activities.
While many C-level executives are excited about how technology can enable businesses and individuals, its adoption comes with drawbacks, such as increased interconnectivity and dependency on third parties. This dependency also raises concerns about emerging cyber risks.
As boards of directors are frequently seeing cyberattacks (from advanced nation-state attackers all the way down to average malicious threats) and cyber warfare in the headlines, it is natural for them to be increasingly concerned and wary about businesses falling victim. At the same time, business stakeholders have found themselves overwhelmed by the technical jargon and misalignment between business and cybersecurity. In this handbook, we will describe each executive position’s responsibilities in achieving a cyber-resilient business.
In this first chapter, we’re going to answer the main business stakeholders’ most frequent questions by addressing the following topics:
- Why cybersecurity should be a CEO’s priority
- Understanding cyber risks and their implications on a business
- Understanding cybersecurity challenges, organization, and reporting
- Quantifying cyber costs versus return on investment
- Building a culture of cybersecurity
- Preparing a business for cyberattacks
- Cybersecurity considerations for a CEO’s first month
- Questions to ask yourself as a CEO when considering your cyber risk coverage
Why cybersecurity should be a CEO’s priority
As a Chief Executive Officer (CEO), chief administrator, or just Chief Executive (CE) in charge of managing an organization, four goals are critical for businesses in the new normal:
- Cloud and digital transformation, which has accelerated due to long-term remote working.
- Increasing the pace of automation, supported by technology adoption.
- Placing sustainability at the heart of all initiatives.
- Skills development and talent retention, which gets harder by the day due to changing job market demand.
We live in a globally connected world, where information is the lifeblood of an organization, and technology the blood vessels. Traditionally, companies build trust through physical files and locks, protecting their customers’ interests with manual security processes. As businesses evolve and the nature of how they deliver products and services to customers changes, their reliance on technology also increases, whether they realize it or not.
Today, customers interact with businesses through digital channels, creating a plethora of digital data and avoiding any form of physical paper and files. Through this change in customer expectations, businesses try to keep up, and sometimes even try to stay ahead of the curve, by adopting new technologies, including cloud networks, the Internet of Things (IoT), artificial intelligence, and blockchain, at a fast rate. The year 2020 specifically saw an explosion of digitization, driven by people who were forced to work from home. Quarantine requirements meant customers could no longer just walk into any physical store. Due to the threats posed by COVID-19, companies were forced to adopt more technology-driven business models to remain competitive.
These changes are beneficial for businesses as they increase revenue by providing automation and better customer service, with everything at the customers’ fingertips. However, the intangibility of data and assets stored in digital form in the cloud and other technology systems has created a false sense of security.
These transformational changes, including the increasingly complex ecosystems in which companies operate, have inevitably increased organizations’ risk exposures and, therefore, their cyber risk. Due to the intangibility of data and digital platforms, CEOs historically haven’t seen a clear value in investing in cybersecurity and the emerging risks technology adoption brings: “I am not a target, and I have an information technology team working on the problem. I am safe.” Such is the typical feedback we have heard regularly from leaders of organizations.
For many other businesses, cybersecurity is still seen as nice to have, a nonfunctional requirement driven only by customer demands. It is, therefore, unfortunate it has taken businesses falling victim to cybercrime before they start seeing cyber risk as a tangible business risk.
It is ultimately the CEO’s responsibility to create, institute, and maintain a cybersecurity strategy. In a May 2022 AICD survey on Board’s Cyber Resilience Practices Report, of the 856 board directors in Australia, the majority indicated the CEO as the executive primarily responsible for building cyber resilience in the organization. Figure 1.1 shows the results of that survey.
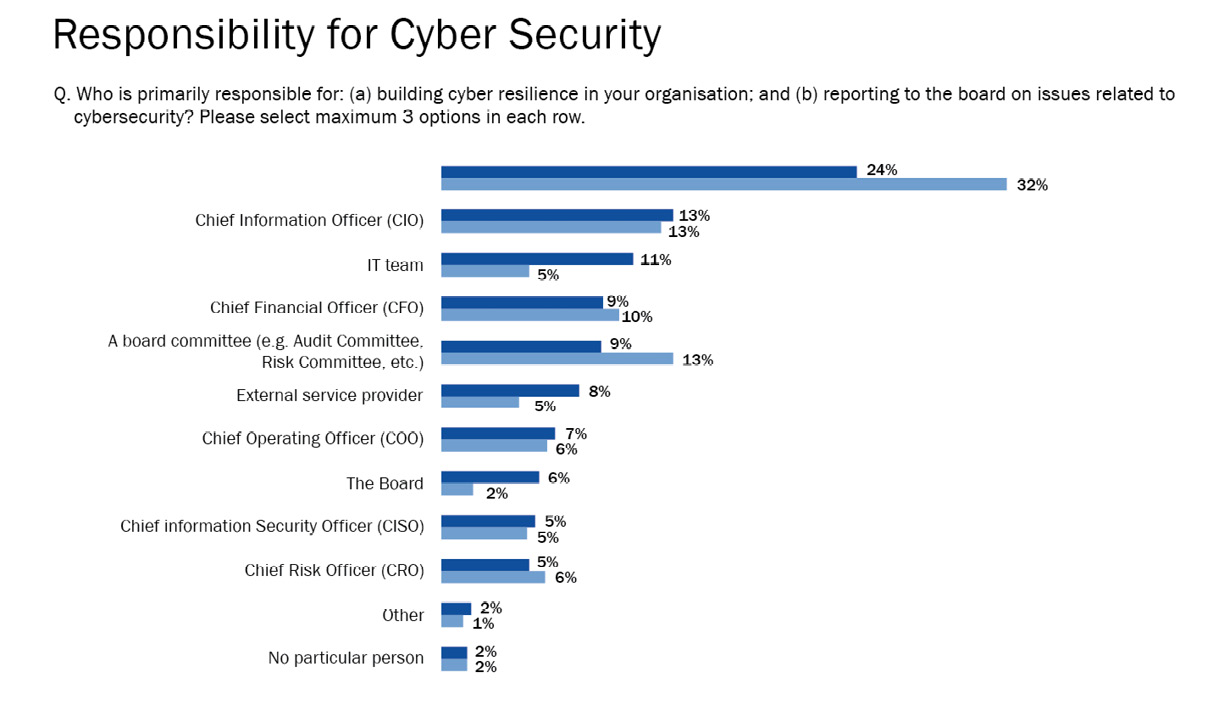
Figure 1.1 – Survey of who is responsible for building cyber resilience in their organization
With businesses becoming more dependent on technology to provide services to customers, and with new changes to their operating model, CEOs need to re-evaluate the ways they are going to retain, and after a cyberattack, regain trust with their customers.
Dependency on technology—a critical business failure blind spot
Businesses now have more flexibility, automation options, and mobile capabilities thanks to technology. It’s unsurprising to see how reliant company owners are on technology and how technology aids the growth of businesses. According to a recent study, over 48 percent of company owners say the ability to operate their firm from a mobile device is critical. This statistic is supported by the fact that a typical company owner uses their mobile device at least twenty-one times every day.
The mass digitization of core business processes, from sales to accounts receivable, business analytics, production lines, cost optimization, and productivity improvement, has increased the potential impact a technological failure can have on a business. Every business process depends on technology, from a simple spreadsheet to a complete technology platform.
Cyber risk is defined as any risk of financial loss, disruption, or damage to an organization from a failure of its information technology systems due to a cyber threat. This risk extends to technology disruption, data loss, theft or disclosure of data, and product recalls as examples of plausible business risks.
Every organization (and indeed every individual) is a target. The dependence on information and technology has exponentially exposed all to cyber risk, regardless of industry, size, or geography. It is simply not realistic to claim, “We will never be attacked” or “It won’t happen to us.” It is widely acknowledged that companies fall into two categories—the ones that have been hacked and those that do not yet know they have been hacked.
The more tech-savvy and cyber-aware CEOs know that changing business models and growing technological dependencies lead to newly emerging cyber risks that can have a tangible impact on their businesses. This is a starting point for organizations to address those cyber challenges and decide on adequate and cost-effective cyber initiatives. Building security into a new technology platform early on will often be cheaper than having to rework a solution at a later stage. We cover this in more detail later in the chapter.
Cybersecurity is a critical environmental, social, and governance pillar
Investors today are just as concerned about a firm’s cybersecurity posture as they are about system capability and operational stability. They often review data protection and information security policies to assess a firm’s cyber risks. As our digital economy continues to flourish and evolve, executive management and global investors are also rapidly becoming more cognizant of the widespread business and social impact of a cyber breach (such as financial or reputational damage). Cybersecurity, which was once primarily a technological problem, is now recognized as a critical Environmental, Social, and Governance (ESG) concern—in particular, a key metric of the social pillar.
ESG frameworks are a practical way to assess business behavior. By including cybersecurity as one of its concerns, a new dimension is introduced, providing insight into how an organization approaches cyber risks and employees’ online behaviors, both of which are vital elements of the overall ESG picture.
As the global workforce has shifted to working from home, more employees are placed outside the security protections offered by their office IT systems and environments. This has resulted in an increased vulnerability in organizations’ security defenses (perhaps caused by insecure habits due to lack of awareness or security apathy), leading to more frequent cyber incidents and, naturally, focusing more attention to the area of cybersecurity. If companies do not sufficiently safeguard their information networks, they risk being fined in the event of a breach and/or damaging their reputation. We have seen this become increasingly common in the IT sectors and financial and communications services, along with sectors that traditionally haven’t invested as much money in cybersecurity.
Cybersecurity has become a social concern, and a global perspective needs to be factored in, taking into consideration geographical and geopolitical data when analyzing cyberattacks. It is also a growing industry, with core security spending estimated to reach $1.75 trillion over a five-year period from 2021 to 2025, according to Cybersecurity Ventures.
Increasing investment in a company’s systems, products, and services to boost protection against cyberattacks can benefit many businesses across different industry sectors, which means organizations, investors, and the general public increasingly are aware of the need for cybersecurity protection. Although including cybersecurity as an ESG metric is still a relatively new concept, there is an undeniable increase and continued interest in this across industries. In a discussion Shamane (co-author of this book) had with a group of board directors, they highlighted with great enthusiasm that the current two hot topics constantly brought up in the boardroom are ESG and cybersecurity. That cybersecurity becomes a concern of ESG, therefore, makes perfect sense.
Cybersecurity is no longer just a technical problem; it’s not only here to stay as an ESG concern but will also expand to other segments of a business with time as recognition of its necessity becomes commonplace.
Now that we’ve unpacked the role and future of cybersecurity and why it must be a priority for all CEOs, in the next section, we will dive further into understanding the business fundamentals concerning cyber risk. We will demonstrate how cybersecurity can be aligned to business goals and priorities, and help translate the technical jargon into business risks.
Understanding cyber risks and their implications for businesses
Cybersecurity is often an afterthought, a contractual requirement, a compliance checkbox, or a tender requirement mixed in with other functional requirements. Rarely is it included as an embedded strategy within a business. As a cyber risk is perceived as complex and intangible (until a company is victimized by a cyberattack), many executives are challenged to understand and evaluate the need to incorporate it into their business plan and instead approach it as enterprise risk in general.
The following list details some questions executive leaders should ask about the cybersecurity strategy at their company:
- “What is my cyber ROI?”
- “What is my exposure?”
- “What are my losses in the event of a cyberattack?”
- “Will a cyber event cause physical damage to our systems?”
- “How much should I spend on cybersecurity, and what should I prioritize?”
- “How ready would we be if a significant security event occurred?”
These questions raise and define the current challenges of tackling cyber risks. The recent race to adopt digital solutions for business coupled with a lack of cyber awareness and minimal or patchwork regulation has created the urgent need for organizations to develop awareness and understanding of their exposure to cyber risk, the general importance of cybersecurity, and their return on investment (ROI).
First and foremost, it is important to align a company’s cybersecurity with its business goals. Protecting a business from cyberattacks and data breaches is crucial and requires skilled resources with an adequate budget. However, it doesn’t just stop at purchasing expensive tools, or getting your IT team to work with those tools. Security programs should have a long-term vision, and there is never an “end date.”
Cyber risk management requires a holistic risk approach that incorporates mitigating controls across the spheres of people, processes, and technology. It needs to align with the business priorities and the company’s risk appetite. Cyber risks are often inadequately addressed (if at all) by business stakeholders, probably because they lack the awareness to do so. “It won’t happen to us.” Too often, organizations tend to bury cyber risks under general technology risk, which in turn gets buried under operational risk. Cyber risks are not just malware; a cyber risk can result in business operation disruptions, data breaches, data loss, and/or reputational damage. Unfortunately, too many companies, and too many executives, have yet to start viewing a cyberattack as a risk and not only an IT problem. Too often, cybersecurity remains a problem when professionals who support cybersecurity strategies do not have the right skills, experience, and qualifications.
Cyber risk is a business risk. Just as any business that operates a physical office space needs to take precautions to protect against threats to property, organizations today need to protect themselves from technology risks, especially with the increasing adoption of work-from-home policies and a growing amount of business activities solely performed using technology.
Mitigating cyber risk requires cybersecurity controls to protect information and systems from unauthorized access, loss, theft, and disruption. Organizations need to ensure information, applications, and IT systems are easily accessible to staff and authorized users and, at the same time, protected from harm and disruption while ensuring their cybersecurity plans are worth the investment. Possible controls here are not limited to technical solutions but are based on a balance among people, processes, and technology controls that support the business and mitigate the risk to the business.
Lastly, local regulations influence cybersecurity strategies. Inevitably, when organizations and industries fail to meet community expectations and address consumers’ safety and security, the government’s role is to step in through regulation. In some countries, governments have been proactive and built regulatory frameworks to support companies in their cybersecurity journey, directing them via guidelines, laws, and regulations. In Singapore, specific grants (such as the GoSecure program) are available to businesses as co-financed cybersecurity initiatives to expedite the adoption of basic cyber hygiene throughout the country. Other examples of government-backed schemes include Cyber Essentials in the UK and the Cyber Security Skills Partnership Innovation Fund in Australia. The level of involvement and role of governments differ from country to country and there isn’t a one-size-fits-all model. What is clear is that cybersecurity needs to be a priority of all governments.
A CEO or a business leader needs to understand this before discussing, starting, or hiring their business cyber capabilities. Cybersecurity is not an IT problem—it is, in actual fact, a business risk.
With this necessitates understanding the challenges cybersecurity faces and how it is organized. In the next section, we will demystify the current cybersecurity challenges, focusing on the critical question: Why do companies get continuously hacked while appearing to do the “right” thing?
Understanding cybersecurity challenges, organization, and reporting
Cybersecurity is a young and emerging profession. That is one reason why it is not fully understood or taken seriously by many C-level executives. While many CEOs and board members have extensive cross-functional experience in accounting, finance, marketing, or HR, few have much cybersecurity experience. As a result, cyber risks are not commonly understood in boardrooms. Many companies leave cybersecurity to the organization’s Chief Information Officer (CIO)/Chief Technology Officer (CTO), and cyber risk management is perceived as a cost confined to the IT department where it must compete for resources/budget against new initiatives for revenue generation, profit increase, customer acquisition, and so on.
A Chief Information Security Officer (CISO) who is responsible for the confidentiality, integrity, and availability of data often reports to a CIO or CTO. While this structure is common, it has proven ineffective due to the CISO’s objectives regarding cybersecurity and associated conflict of interest with the CIO. The CIO aims to ensure the implementation of any business technology is completed within the required timeframe and budget, but security requirements might slow this process by requiring further checks and tests before the launch. In many cases, the security elements might not even be treated as a business priority.
When Hai (co-author of this book) was the CISO at Western Australia Police Force, he suggested to a senior executive, “If security is responsible for the availability, integrity, and confidentiality of information, then perhaps the CIO/CTO should report to the CISO, rather than having to compete for organizational resources.” This was an attempt to shift the executive’s mindset about how the role of security was perceived.
The senior executive’s counterview was that security was kept “healthy” by competing with other business facets for resources. It is a fact, however, that cyber risk is a business problem that can only be solved through collaboration, not competition. Cybersecurity must be seen as an integral part of achieving business goals successfully. A product or service provided without the necessary safeguards in place to protect and the company will prove costly in the end.
IBM’s Cost of a Data Breach Report 2021 (https://www.ibm.com/au-en/security/data-breach) revealed that 2021 saw the highest average total cost of data breaches in the seventeen-year history of the report. This cost rose from $3.86 million in 2020 to $4.24 million in 2021, suggesting it is becoming more costly to recover from a cyberattack than to address security by design at the initial stage of technology adoption. It also shows that it goes beyond the capabilities of an IT department and its goals.
Having worked with IT departments across law enforcement, government, academia, and the private sector, Hai adds, “I have seen that most IT departments do not have the capability and capacity to manage cyber risks or the skill set necessary to address technical security controls.” Some of the skills may be similar but the focus is completely different.
Cybersecurity and information technology—similar skills but with a different focus
Left to the IT department, cybersecurity is often considered a technical issue, a cost center, and a low-priority task that competes for budget resources against other IT projects, most of which demonstrate better ROI for the business.
In Asia, approximately 10 percent of the companies Magda (co-author of this book) has interacted with have hired a CISO. In her many years of experience, most of Magda’s customers rely on their IT teams, rather than cybersecurity teams, to perform cybersecurity tasks. A misaligned organizational structure such as the one where cybersecurity is a component of, rather than separate from, IT often leads to operational ineffectiveness and challenges.
This shows the challenges cybersecurity professionals have to influence business leaders within their own organizations. Cybersecurity executives are just like any other executive and should have the ability to communicate effectively. Even though their skills to perform their role might be mostly technical, having communication skills at the leadership level is critical. Unfortunately, security professionals have addressed cybersecurity for years using technical jargon. This trend has driven a wedge between cybersecurity leaders and businesses. It’s crucial to communicate in nontechnical language.
As well, CISOs are expected to understand what their organization does from a business perspective and be able to speak about business strategies (and, in some cases, even customer engagement). A common discussion on social media revolves around how the CISO (or equivalent security executive) should communicate with and influence executives, and failure to do so effectively should be considered a failure of the security function.
Unfortunately, cyber is sometimes a thankless job, with an average eighteen-month turnover rate for a CISO. In an interview Shamane conducted with a group of APAC CISOs, they attributed stress as a key factor in why they leave a company, originating in part from a misalignment of views in the senior leadership team, as well as the wider culture of the company. There is only so much a CISO can do if they are unable separate cybersecurity from the IT department and effectively influence the necessity of a broader cybersecurity strategy and its need for the appropriate resources. In essence, corporate success is a team effort. It is commendable progress, therefore, that as time goes by IT and security are increasingly being recognized as critical, and separate, components to professional success. Hai’s career timeline and progression is one good example:
- In 2005, when Hai was the IT security manager in a government agency, he had five levels of management above him before reaching the chief executive.
- In 2009, when he was the associate director of information security at a university, there were three layers of management between his position and the chief executive.
- In 2013, as CISO of a police force, there were two management layers between his position and the chief executive.
- In 2020, Hai held both the CEO and Chief Security Officer (CSO) positions in a not-for-profit organization.
It is notable that, while on the surface, being appointed both a C-level executive (CxO) and CSO or CISO might demonstrate a commitment to cyber by making a CxO accountable for cyber through a secondary appointment as the CSO or CISO, CEOs need to appreciate having a CISO in the same way they would their Chief Financial Officer (CFO) or CIO. In a digitally connected world fraught with cyber risk, the CISO and their team help keep their organizations running.
The CEO needs to be an organization’s cybersecurity leader and role model. They need to promote a cyber-safe, -active, and -responsible culture where each team member understands their responsibility for managing cyber risks to the business and recognizes that cybersecurity is not merely an “IT problem.” Everyone in the organization has a critical role. Once in agreement with the cybersecurity strategy and roadmap defined by the CISO, the CEO needs to back its communication, adherence, and enforcement to ensure everyone in the organization plays a critical role to achieve cyber safety for the organization.
Beyond technology—cyber risk is a business risk
When cybersecurity fails, it affects the whole business, not just the IT department. Just look at the reporting on the cyberattacks on Garmin, Toll, MyBudget, Travelex, and Lion, to name just a few. It’s crucial to think about cyber first and make it a business-wide joint function that coordinates security, finance, HR, corporate risk, and IT.
Tackling cyber challenges requires a strong security culture, prioritizing cyber risk and addressing it accordingly to keep it within an organization’s risk tolerance. An organization is led by the CEO and supported by a team promoting the same values and goals. If the CEO supports a cyber-aware culture, all stakeholders will consider cybersecurity as part of their priorities and address it.
Cyber risk, while intangible, can be identified by the CISO, who then defines the right strategy and roadmap in alignment with the company’s risk tolerance. The strategy should consider the previously identified cyber challenges, the company’s current security control landscape, any gaps identified, and the roles and responsibilities of its workforce while maintaining alignment with the organization’s business strategy, trajectory, and stakeholders. Everyone within an organization has a role. This handbook describes all business executives’ responsibilities and expectations to achieve a resilient cyber-secure business.
The bottom line: cybersecurity professionals must be encouraged to avoid using technical jargon and align their thinking toward business impacts. Part of that includes taking technical language and terms and explaining it clearly and deliberately.
Demystifying data breaches and cyberattacks
Let’s examine two commonly interchangeable terms—data breach and cyberattack:
- A data breach occurs when personal information is accessed without authority. Data breaches, in general, are also personal data breaches, and they may be either unintentional or purposeful.
- A cyberattack is more severe than a data breach since it is likely to impact the organization more directly. It is a deliberate, intentional act.
Data breaches are just one of many different types of cyber risks businesses of all sizes and industries face daily. A data breach might happen without a cyberattack when there is a misconfiguration and unauthorized parties manage to access data.
The size and scope of a security event or data breach vary from one instance to another. A data breach or security event may have a significant financial and reputational effect on a business.
Although a security event may be mitigated by a timely, deliberate, and well-organized response, without sufficient preparedness, companies can undoubtedly be subjected to severe consequences from which they may never completely recover. The CEO needs to understand the impacts and financial consequences for a business when a cyber incident occurs and communicate it effectively to all stakeholders.
Quantifying cyber costs versus return on investment
While some organizations have well-developed cybersecurity strategies and programs, most think they have adequate processes in place, and many more still believe they are not a target for cybercriminals. Those who think they have appropriate programs and those who think they are not targets have little to support their current comfort level, other than they have not yet experienced any discomfort. However, it may already be too late when they do encounter a cyber incident, which is inevitable. According to IBM’s Cost of a Data Breach Report 2021, the average cost of a data breach in the United States is an alarming $8.64 million.
Many small businesses would not survive such an expense, and larger businesses that can take on such a big expense would still feel a painful financial impact. In addition to the financial loss, other costs include direct and indirect losses following a cyberattack and/or data breach. There can be investigation or forensic costs, profit losses due to reputational damage, revenue losses due to business disruption, share value impact, incident response costs, customer notification costs, recovery costs, and so on. Everything just adds up.
As mentioned earlier, a data breach may result from a security event or incident, but it may also arise from a non-security–related event. With varying privacy and breach reporting regulations depending on a company’s location, for example, the requirements and consequences of a data breach may vary.
When a security event or a data breach happens, companies must analyze a variety of criteria to determine the true financial ramifications, expenses, and losses. There can be significant expenses from a data breach:
- Notification costs might include fees, charges, and expenditures required to inform customers, regulatory agencies, and any other impacted parties who must be informed. Following the notice, a corporation should be prepared to respond to questions and clarify any issues that emerge as a result of the breach, as well as class action lawsuits. Those activities have a monetary cost.
- The expenses incurred as a result of a data breach may involve forensic investigations, a change in processes, improved security precautions, and compensation for losses or damages. These variables contribute to the company’s financial losses after a data breach, both directly and indirectly, and are included in the cost of a data breach.
In the event of a successful cyberattack, a company might face significant interruption of essential systems, disruption to business operations, damage to the integrity of business data, and business stagnation. The different factors contributing to the financial impact of a cyberattack include:
- Direct and indirect expenses and third-party expenditures contribute to the company’s financial losses following a successful cyberattack.
- Forensics costs, notification costs, and share value losses may be incurred in addition to the immediate business interruption, employee overtime, communication costs, and direct expenditures (such as recovery costs).
- On a medium timescale, the impact of a successful cyberattack might be a loss of customers, a decrease in sales, and a decrease in earnings. In addition, with time, this might lead to a reduction in market share, a decline in value, or a delay in an initial public offering (IPO).
- The organization will need to assess the overall recovery time after a successful cyberattack. The interruption, whether days, weeks, or months, will impact a company’s operations and finances, including expenditures associated with market recovery.
- In the event of a successful ransomware cyberattack, the organization may experience business disruption or operational paralysis. When a company’s activities are interrupted, it suffers a financial loss. There is likely to be lower sales and higher labor costs; future income streams are lost due to possible reputational harm.
According to Comparitech, breached firms underperform in the market over time, growing 8.38 percent on average the year following the attack but still underperform the Nasdaq index by 6.5 percent. Target’s data breach in 2013 is a fantastic example. Target experienced a significant data breach that exposed the personal information of about 70 million people. The cost of this data breach was estimated to be $252 million.
For any company that is publicly traded, following a cyberattack there will be a stock price decline after a breach; it will take time for a corporation to reclaim whatever market share it may have lost due to the occurrence. Significant reputational damage as a result of the attack impacts the time it will take to recover, resulting in a greater loss of market share and more time needed to resume operations.
The 2017 WannaCry ransomware attack affected more than 200,000 computers globally across many industries. Users’ files were held hostage until demands for a ransom payment in Bitcoin were met. With over 150 countries affected, this attack had an estimated cost of $4 billion on the global economy.
All successful cyberattacks leave an impact that will affect an organization financially. Depending on the organization’s sector, the extent of the damage will vary. Take, for example, a cyberattack against an industrial control system (ICS)—a breach of an ICS could result in property damage, such as fire or explosion, and even loss of life. Cyberattacks can have bigger ramifications than a breakdown of technology systems. Recovery from a cyber incident may not only be costly but lengthy as well, such that the business could be interrupted or stalled for a long period while the situation is being rectified.
The cost of a cyberattack is a complicated calculation that takes into account all of the ramifications that may occur. It goes well beyond the expense of restoring a server or an IT activity. In reality, it is putting a price on a business risk becoming a reality. The financial, reputational, and legal consequences of a security incident can be forecasted, with the associated financial losses also quantified. This quantification gives greater clarity and insight into the actual cost, and thus also the ROI on a cybersecurity investment. We will unpack this further in Chapter 5, Working with Your CISO.
Good cybersecurity enables organizations to build and protect their reputation and trust with their customers. To succeed, organizations need to ensure they have the proper risk management fundamentals, they have the appropriate structure for the cybersecurity team, and the relevant staff feel empowered to protect the organization. While the trend to elevate cybersecurity to the C-suite is a step in the right direction, making it a secondary responsibility of another CxO is counterproductive. The CISO should have a seat at the main table.
With a clearer picture of the financial and reputational costs of a cyberattack, in the following section, we address the importance of cybersecurity awareness and creating a culture that builds and nurtures a cyber-ready company.
Building a culture of cybersecurity
The CEO needs to lead in promoting a culture that reinforces the idea that cybersecurity is an organizational capability rather than just a problem for IT to solve.
A strong cybersecurity culture drives the members of the organization to behave in unison when faced with security challenges. An established, well-thought-out cybersecurity plan approved by the board of directors is only helpful if every staff member understands their role and responsibilities before, during, and after an event, appreciates the significance of cyber threats, complies with security measures and guidelines, and understands what it means to remain cyber-vigilant.
A cybersecurity plan needs to be approached holistically to be successful. Every part of the organization must understand that processes and technology play a critical role in developing and maintaining a robust cybersecurity culture. Cyber risk must be taken as seriously as risks such as natural disasters or acute illnesses. Most importantly, we must test, audit, practice, and rehearse cyber threats, keeping in mind the goal isn’t to be 100 percent secure; there’s no way to ensure that. Rather, cyber resilience is about understanding security threats, maintaining effective security controls, and having a swift and focused cyber-incident response prepared to reduce the impact of any incident.
Regardless of an organization’s cyber maturity, the main cyber-resilience goal of any company should be the preservation of business operations, protecting the confidentiality of its data, and, in the event of a cyberattack, recovering as quickly as possible with minimal disruptions and losses. One of the biggest challenges is knowing where to start and what good cybersecurity practices and processes look like. It does not start with IT and cannot be left to the CIO or CTO.
Understanding cybersecurity at the board level does not require an understanding of security jargon or technical terminology. It comes down to defining the business risks that might materialize following a cyber event, such as a data breach, business disruption, or data theft.
When the board and management are aligned and clearly understand its cyber risks, their risk tolerance needs to be defined and agreed upon before building or discussing the cyber strategy.
Table 1.1 is an example of risk considerations for a business. The board and the CEO must acknowledge and consider cyber risks at the same level of priority as other risks for the organization:

Table 1.1 – An example of high-level risk considerations
According to a study conducted by Allianz, 2,700 risk management experts surveyed in over 100 countries identified cyber incidents as the “most important business risk” in 2020, a vast difference from 2013 when it ranked 15th place (see https://www.agcs.allianz.com/news-and-insights/expert-risk-articles/allianz-risk-barometer-2020-business-risks.html).
Table 1.2 lists the negative impacts of cyberattacks. Business stakeholders are more and more concerned about the implications for their companies and have started prioritizing cyber risk in their risk management process.

Table 1.2 – Types of risk by priority
The CISO is an invaluable resource and leader in helping an organization develop the most appropriate cybersecurity strategy, but they cannot do this alone. Once the board and CEO are aligned in their risk tolerance and a cyber strategy has been created and approved, it must include a plan to create a culture of cybersecurity and embed it within the organization. All staff must understand the fundamentals of cybersecurity instead of merely complying with policies and following technical guidelines. Senior management must lead by example. Cybersecurity strategies must align with business goals, be assessed against an organization’s risk tolerance, be planned and executed accordingly through collaboration between business units, and not be in competition with other departments for resources.
Once an organization has established solid cybersecurity fundamentals across the board, once it is part of the culture, the business can operate effectively and without major disruptions or regulatory implications if a cybersecurity incident occurs.
The organization’s cybersecurity strategy is a collaborative strategy that requires everyone’s involvement, especially when the organization is undergoing a cyberattack or is suffering from a disaster caused by a cyberattack. Everyone in the organization, not just the CEO and the board, needs to understand that it isn’t a question of whether their organization is breached but a matter of being prepared for when it is. The following section explores this in detail.
Preparing a business for cyberattacks
Cyberattacks are generally targeted and very well defined, designed to cause maximum impact and disruption to business operations.
The CEO needs to prepare their business for such situations. Often, organizations wrongly believe that because they have an extensive security team, a cyberattack will never succeed. Or that because they have made a substantial investment to protect against attacks, a cyberattack will never be successful. Those are myths—100 percent security should not be a goal, nor is it a realistic target.
Securing your organization is about ensuring that if an attack does prevail, the business will be able to continue its operations. Resilience is about keeping your information assets accessible to the organization as much as keeping them safe. Such resilience builds trust among your customers and protects your reputation in the event of an attack. Hence, it is crucial to plan for failure, including security control failures. Preparing for failure ensures your organization can survive and continue to operate while other preventive measures are built over time. This will help you cope with the threat of a cyber incident and prepare your business to deal with other disasters.
Gillian Findlay, board member and former CEO at Vamp, a global branded content platform, and former Chief Operating Officer (COO) at Australian Software as a Service (SaaS) unicorn SafetyCulture, shared a typical CEO’s concerns: “There are so many cybersecurity issues that should be front of mind for any CEO, but ransomware has become the most front of mind. We cannot expect end users to protect their company from this threat, so companies must secure end-user devices while enabling the employees to work efficiently and effectively. Otherwise, ransomware breaches will continue to blight our lives.”
While many CEOs and boards might consider the risk of becoming a victim of ransomware is minimal, or might think their IT department will restore from backups while the business reverts to manual processes, very few organizations have put that to the test. Those that have done so were forced to because of a real crisis, and they quickly discovered that reverting to manual processes or restoring backups was easier said than done. We will discuss business continuity plan (BCP) further in Chapter 7, The COO and Their Critical Role in Cyber Resilience.
Preparing a company in the event of a cyberattack must be a top priority for any CEO. A CEO should make a security strategy a focus upon assuming the role. Next, we discuss cybersecurity considerations as part of a CEO’s leadership assignment and risk assessment for the first month of their tenure.
Cybersecurity considerations for a CEO’s first month
With so many pressing issues requiring their attention, many newly appointed CEOs overlook the importance of cybersecurity in their first month or even first year on the job. That is a mistake.
A newly appointed CEO needs to ensure a CISO and their team are in place and working effectively while becoming familiar with the organization’s cyber risk posture, from its cyber risks and risk appetite to risk tolerance. Unfortunately, threat actors and cyber risks will not wait until a CEO is ready. Some cyber criminals may also view a leadership change as an opportunity to attack if they believe an organization is unprepared. This also concerns mergers and acquisitions. A cyber disaster could ruin a CEO; a cyber event leading to significant data loss, data theft, or business interruption may jeopardize the CEO’s reputation, position, career, revenue, and operations.
A newly appointed CEO should prioritize reviewing their cyber incident response preparedness, BCP and disaster recovery plan (DRP), along with evidence that these plans have been regularly tested and updated. The plans must include and adequately address technology considerations and vendor support. Having a current and well-rehearsed incident response, BCP, and DRP will ensure an organization can quickly recover and resume operations in the event of a cyber disaster.
Ideally, the BCP should encompass the cyber incident response. However, Magda has also witnessed a lack of integration during her work in Asia, where the BCP remains focused on a simple IT DRP and doesn’t consider a significant cyberattack. An IT DRP is unlikely to hold up against a well-planned cyberattack.
A communication plan is a key element of cybersecurity planning. The CEO must consider their visibility in an organization’s crisis communication plan. To this end, templates and guidelines for communication from the CEO to staff, media, customers, and the public should be included in the BCP. Communication in the event of a cyberattack is critical for reputation management and maintaining customers’ trust. A mismanaged cyber communication plan will undoubtedly impact the share value of a business.
The communication plan is merely one element. The CEO must address tactical issues of ensuring an appropriate incident response, effective business continuity, and disaster recovery with a sound security strategy.
If an organization does not have an established cybersecurity strategy or team, within the first month, the CEO needs to prioritize establishing one immediately. This begins with understanding and communicating that cyber risk is a major concern to the company’s board of directors and seeking approval for a cyber budget. If there is no internal expertise available to identify and lead discussions to address and define the organization’s current cyber exposure, residual risk, and risk tolerance, the CEO may engage an external cybersecurity consultant while hiring a CISO to build internal capabilities.
A cyber-resilient business identifies its cyber risks beyond the IT department, defines its risk appetite and tolerance, and builds its cybersecurity strategy, which is then embedded into the business’s operations and activities as a fundamental must-have and not an afterthought. It’s not an easy task, but it’s a necessary one for any CEO to take at the outset. Fortunately, there are some specific questions that can be asked to assess an organization’s cyber risk coverage.
Questions to ask yourself as a CEO when considering your cyber risk coverage
How does a CEO determine what the organization’s cyber risk coverage should be? A challenge for non-cyber executives is knowing the right questions to ask, such as:
- Does my organization consider cyber risk within the enterprise risk management process, or is it still considered an IT problem?
- Are all in the C-suite held accountable for cyber risk, or has it been left to the CIO or CISO/CSO?
- Do I understand the organization’s assets, including intangible ones?
- Do I understand that my organization’s cyber strategy should be based on identifying risks, mitigation/transfer/approval of cyber risks, response, and recovery?
- Does my organization recognize residual cyber risks and understand its risk appetite and tolerance?
- Has the organization quantified cyber risks, and does it understand the impact and likelihood of such events?
- What is my current security risk posture, and how do I know the controls are working effectively?
- Have I considered the damage to the brand, reputation, and trust of the organization resulting from a cyber event?
- Does the organization have an effective BCP/DRP, and when was it last tested?
- Is my organization ready to respond and recover?
- Is my organization able to prove due diligence and due care following a cyber incident or could the shareholders/regulators consider my inaction negligent?
- Does my organization understand that 100 percent security does not exist?
These questions are not mere one-time questions a CEO or board of directors should ask. Such questions should be asked repeated and addressed as part of a company’s security strategy and processes adjusted based on the answers.
Summary
In a digitally connected world, organizations are dependent on information and technology now more than ever before. This state of affairs exposes organizations to global threats, some even sponsored by nation-states. Cybersecurity not only ensures your organization continues to operate in these challenging circumstances, but good cybersecurity increases customer trust and brand reputation, too.
CEOs and boards of directors should develop a healthy cybersecurity culture that encourages an entire organization to embed cybersecurity into all aspects of people, processes, and technology. These are some of the essential fundamentals you’ve learned from this chapter. Finally, cybersecurity needs to be considered a business need, complementary to business functions instead of competing with them.
The following chapters will examine what roles other CxOs play in cybersecurity, starting with the CFO.
