17
Information Technology Act, 2000
Learning Objectives
17.1 INTRODUCTION
The Information Technology Act is divided into 13 chapters, 94 sections, and 5 schedules.
Chapter 1: Scope and Definitions
Chapter 2: Authentication of Electronic Records Using Digital Signature
Chapter 3: Electronic Governance
Chapter 4: Attribution, Receipt, and Dispatch of Electronic Records
Chapter 5: Secure Electronic Records, and Secure Digital Signature
Chapter 6: Regulation of Certifying Authorities
Chapter 7: Digital Signature Certification
Chapter 8: Duties of Subscriber
Chapter 9: Penalties and Adjudication
Chapter 10: Cyber Regulation Appellate Tribunal
Chapter 11: Offences
Chapter 12: Network Service Provider Not be Liable in certain Cases
chapter 13: Miscellaneous (described the power of various government bodies to make the rules under the IT Act, 2000).
17.1.1 Cyber Laws
Businessmen nowadays are increasingly using computers to manage their commercial activities in electronic form instead of traditional paper form. Information kept in electronic form is higly economic, easier to store, retrieve, and speedier to communicate. Now, people are using new communication systems and digital technologies for transacting their business electronically. Although people are aware of advantages which the electronic form of business provides, but they are are reluctant to conduct business or execute transactions in electronic form due to lack of a proper legal framework.
Electronic Commerce eliminates the needs for paper-based transactions. The two principal hurdles which stand in the way of facilitating electronic commerce and electronic governance are requirements of writing and signature for legal recognitions.
At present, many legal provisions assume the existence of paper-based records which should bear the signatures. The law of evidence is traditionally based upon paper-based records and oral testimony.
To facilitate e-commerce, the need for legal changes has become a quintessential requirement. The Government of India realized the need for introducing a new law for making suitable amendments to the existing laws to facilitate e-commerce and to give legal recognitions to electronic records and digital signature. The legal recognitions to electronic records and digital signatures, in turn, will facilitate the conclusions of contract and creations of legal rights and obligations through electronic communications like the internet. The need of legal recognitions to electronic commerce gave birth to the Information Technology Bill, 1999.
In the year 2000, both the houses of parliament passed the Iinformation Technology Bill. The Bill received the assent of the President in August 2000 and came into existence as the Information Technology Act, 2000. This act contains the various aspects of the Cyber Laws.
17.2 OBJECTIVE OF ACT
The objectives of the IT Act, 2000 are as follows:
- To grant legal recognitions for transactions carried out by means of Electronic Data Interchange and other means of communication, commonly referred to as - ’Electronic Commerce’ in place of paper-based method of communication.
- To give legal recognitions to Digital Signature, for authentication of any information or matter that is subjected to authentication under any law.
- To facilitate Electronic Filing of documents with various government departments.
- To facilitate electronic storage of data.
- To facilitate and give legal sanctions to Electronic Fund Transfer between banks and financial institutions.
- To give legal recognitions for maintaining books of accounts in electronic form by the bankers.
- To Amend the Indian Penal Code, the Indian Evidence Act of 1872; the Banker’s Book Evidence Act of 1891, and the Reserve Bank Of India Act of 1934.
17.3 SCOPE OF THE ACT
Information Technology Act, 2000 extend to whole of India. It applies also to any offence or contravention, thereunder committed outside India. However, the act does not apply to the following categories of transactions:
- A negotiable instrument other than cheque. It means, the IT Act is applicable to Cheque.
- A power of attorney.
- A trust as defined in India Trusts Act.
- A will.
- Any contract for sale or conveyance of immovable properties.
- Any such class of documents or transactions as may be notified by the Central Government in the official Gazette.
17.4 DEFINITIONS
17.4.1 Access—Section 2(1)(a)
‘Access’ with its grammatical variations and cognate expressions means gaining entry into, instructing or communicating with the logical, arithmetical, or memory function resources of a computer, computer system or computer network.
17.4.2 Computer—Section 2(1)(i)
‘Computer’ means any electronic, magnetic, optical or other high-speed data processing device or system which performs logical, arithmetic, and memory functions by manipulations of electronic, magnetic or optical impulses, and includes all input, output, processing, storage, computer software, or communication facilities which are connected or related to the computer in a computer system or computer network.
17.4.3 Computer System—Section 2(1)(I)
‘Computer System’ means a device or collection of devices, including input and output support devices and excluding calculators which are not programmable and capable of being used in conjugation with external files, which contain computer programs, electronic instructions, input data, and output data that performs logic, arithmetic, data storage and retrieval, communication control, and other functions
17.4.4 Communication Device—Section 2(1)(na)
‘Communication Device’ means cell phones, personal digital assistance (sic), or combination of both or any other device used for communication, to send or transmit any text, video, audio, or image.
17.4.5 Computer Network—Section 2(1)(j)
It means, interconnection of one of more computers using satellite, microwave or other communication channels. It also includes ‘computer systems’, ‘computer devices’ and also use of wire or wireless media.
17.4.6 Function—Section 2(1)(u)
‘Function’ in relation to a computer, includes:
- Logic
- Control
- Arithmetical process
- Deletion,
- Storage and retrieval
- Communication, or
- Telecommunication from or within a computer
17.4.7 Information—Section 2(1)(v)
‘Information’ includes:
- Data
- Message
- Text
- Images
- Sound
- Voice
- Codes
- Computer programs
- Software
- Databases
- Micro film, or
- Computer-generated microfiche.
17.4.8 Data—Section 2(1)(o)
‘Data’ means:
- a representation of information, knowledge, facts, concepts or instructions
- which are being prepared or have been prepared in a formalized manner,
- and are intended to be processed, are being processed or have been processed in a computer system or computer network.
It may be in any form including computer printouts, magnetic or optical storage media, punched cards, punched tapes or stored internally in the memory of a computer.
17.4.9 Digital Signature
It means authentication of any electronic record by a subscriber through an electronic method. Digital signature has been replace by ‘electronic signature’ wide Information Technology Amendment Act, 2008.
17.4.10 Electronic Signature—Section 2(1)(ta)
‘Electronic signature‘ means authentication of any electronic record by a subscriber by means of the electronic technique specified in the second schedule and includes digital signature.
17.4.11 Asymmetric Crypto System—Section 2(1)(f)
It means system consisting of secure key pair, private key and public key.
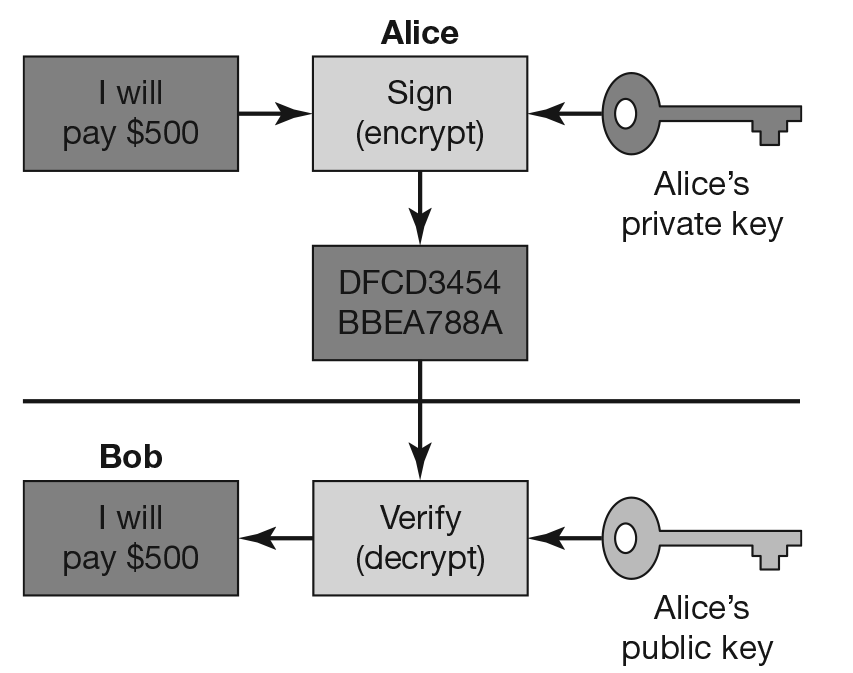
Figure 17.1 Asymmetric crypto system.
A message that is signed (encrypted) with the private key can be verified (decrypted) with the public key. Since the public key is public, anyone can verify the signature. The public key cannot create such signatures. Validity depends on private key security.
Key Pair: It is a private key and corresponding mathematically related public key.
Private Key: It means key of key pair used to create digital signature.
Public Key: It means key of key pair used to verify digital signature.
17.4.12 Secure System—Section 2(1)(ze)
‘Secure System’ means computer hardware, software, and procedures which:
- are reasonably secure from unauthorized access and misuse;
- provide a reasonable level of reliability and correct operation;
- are reasonably suited to performing the intended functions; and
- adheres the generally accepted security procedures.;
17.4.13 Cyber Security—Section 2(1)(nb)
‘Cyber Security’ means protecting

17.4.14 Cyber Café — Section 2(1)(na)
‘Cyber Café’ means any facility from where access to the Internet is offered by any person in the ordinary course of business to the members of the public.
Originator: ‘Originator’ means a person, who sends, generates, stores or transmits any electronic messages or causes any electronic message to be sent, generated, stored or transmitted to any other person, but does not include an intermediary.
Service Provider: Service Provider includes any authorized individual, private agency, private company, partnership firm, sole proprietor firm or any such other body or agency which has been granted permission by the appropriate Government to offer services through electronic means in accordance with the policy governing such service sector.
17.4.15 Intermediary—Section 2(1)(w)
Intermediary includes:
- Telecom service providers
- Network service providers
- Internet service providers
- Web hosting service providers
- Search engines
- Online payment sites
- Online-auction sites
- Online-market places
- Cyber cafes
17.5 DIGITAL SIGNATURE
Digital signature is like a handwritten signature. It should be difficult for the sender to forge and difficult for the receiver to repudiate (reproduce). Generation of Digital Signature uses a technology known as Key Pair (Public Key and Private Key). Users who want to enter into electronic agreement should have key pair. Public key is for distribution, whereas a private key is for the user himself.
For any legal valid electronic document there are two requirements. One is integrity of document, that is, the document has not been changed and authentication, i.e., document is signed.
So, an electronic document to be a legally valid document is two aspects:
- Hash Function is used for integrity of document
- Digital signature used for authentication of documents.
17.5.1 Hash Function
Hash Function is an algorithm that runs a message or content of agreement. It generates a big alphanumeric number which is known as message digest.
The message digest is an unique value for a single message or content. If anyone changes even a single character in the original message and runs the hash function, it will not generate the same number. This change in value will indicate that the original message has been changed. Always a same number is generated when hash function algorithm is run over the original message.
The Hash Function technique is used for checking the integrity of a message. After generating the message digest from message with Hash Function, the message digest is encrypted with the private key of its sender. It again generates a value which is known as Digital Signature. This value is transmitted along with the original document in encrypted or direct form. Its receiving authorizes the receiver with the public key of the sender and, therefore, to decrypt the digital signature by generating the message digest. The receiver again generate the message digest by running hash function over the actual message and if it generates the same message digest which the receiver has obtained after decrypting the digital signature, then it will ensure that the message content has not been changed and digital signature belongs to the person who has given the public key to the receiver.
For transmitting a public key safely and providing a proof that the public key with the receiver belongs to the person who has claimed for this, a certificate is obtained from a certifying authority that gives a Digital Certificate and it ensure that the public key actually belongs to a person who has claimed for it. The most popular certifying authority who issues digital certificate is VeriSign.
Message Digest Encrypted with Private Key of the Sender generates digital signatures which are affixed on the agreement document and sent to the receiver. At the receiver’s end, digital signatures are decrypted with the sender’s public key, and then the Message Digest is generated.
The receiver, again, generates the Message Digest by running the Hash Function Algorithm over the original content of the message. If this Message Digest matches with the Message Digest generated after decrypting the digital signature of the sender by using the sender’s public key, it proves that the contents are authentic and the signatures were made by the sender himself.
The Central Government of India has the power to make rules from time to time with respect to Digital Signatures, etc., that is, types of digital signatures, manner and format, procedure for affixing digital signatures, etc.
17.5.2 Electronic Signature—Section 3(A)
A subscriber may authenticate any electronic records by using his/her electronic signature or electronic authentication technique which is considered to be reliable and specified by the government. The central government is authorized to fix the procedures for affixing such type of signature.
17.5.3 Reliable Electronic Signature—Section 3A(2)
Electronic signature or electronic authentication technique shall be considered reliable if:
- the signature creation data or the authentication data
- are within the context in which they are used, linked to the signatory or the authenticator and to no other person,
- were at the time of signing, under the control of the signatory or the authenticator and of no other person,
- any alteration to
- the electronic signature made after affixing such signature, or
- the information made after its authentication by electronic signature is detectable, and
- it fulfils such other prescribed conditions.
17.5.4. Secure Electronic Signature—Section 15
An electronic signature shall be deemed to be a secure if the signature creation data –
- at the time of affixing signature, was under the exclusive control of signatory and no other person; and
- was stored and affixed in such exclusive manner as may be prescribed.
17.6 ELECTRONIC GOVERNANCE
17.6.1 What Is Electronic Governance?
Electronic Governance (i.e., E-Governance) means filing of any form, application or other document with government department in electronic form and similarly issue or grant of any license or permit or receipt or payment from government offices and its agencies through electronic means or electronic form.
17.6.2 Benefits of Electronic Governance
Electronic Governance helps in low cost, efficient and transparent working of the government departments. Iusses, such as manpower shortage in government organizations and the instances bribery can be easily avoided. Accuracy and record maintenance becomes faster and simplified.
17.6.3 Rules of Electronic Governance
The IT Act also provides for legal recognition for Digital Signature. It means any document or data digitally signed will be treated as valid and authenticated electronic records. Filing of any form, application, etc., to government can be done through electronic means, and similarly government department can issue or grant any license, permission, etc., through electronic means.
Examples
e-filing of Company incorporation and related documents (www.mca.gov.in)
e-filing related income tax (www.incometaxindiaefiling.gov.in)
e-filing for patent application (www.ipindiaonline.gov.in/on_line)
17.6.4 Legal Recognition of Electronic Records—Section 4
Where any act requires that information should be in writing and if such information or form is stored or saved in electronic form, the requirement of the act is satisfied if information or matter is:
- Rendered or made available in an electronic records; and
- Accessible, so as to be usable for a subsequent reference.
17.6.5 Retention of Electronic Records
If any act provides that documents, records or information shall be retained for any specific period, then requirement of the act is said to be satisfied if such documents, records or information are retained in electronic form:
- Information contained in electronic form remains accessible and useable for future period of time.
- Electronic records are retained in the same format in which it was originally sent or received or generated.
- Details of identification of origin, destination, date and time of dispatch or receipt of records are available.
17.6.6 Validity of Electronic Contract—Section 10(A)
Where any contract is made in electronic mode (i.e., communication of proposal, the acceptance of proposals, revocation of proposals and acceptances) or expressed in electronic forms or by means of electronic records, such contract is valid, enforceable and binding the parties involved.
17.6.7 Attribution of electronic records—Section 11
An electronic record shall be attributed to the originator:
- If it was sent by the originator himself;
- By a person who had the authority to act on behalf of the originator in respect of that electronic record; or
- By an information system, programmed by or on behalf of the originator, to operate automatically.
17.6.8 Acknowledgement of Receipt of Electronic Records—Section 12
Where the originator has not agreed with the addressee that the acknowledgment of receipt of electronic record be given in a particular form or by a particular method, an acknowledgment may be given by:
- Any communication by the addressee, automated or otherwise; or
- Any conduct of the addressee, sufficient to indicate to the originator that the electronic record has been received.
Where the originator has stipulated that the electronic record shall be binding only on receipt of an acknowledgment of such electronic record by him, then unless acknowledgment has been so received, the electronic record shall be deemed to have been never sent by the originator.
Where the originator has not stipulated that the electronic record shall be binding only on receipt of such acknowledgment, and the acknowledgment has not been received by the originator within the time specified or agreed or, if no time has been specified or agreed to within a reasonable time, then the originator may give notice to the addressee stating that no acknowledgment has been received by him and specifying a reasonable time by which the acknowledgment must be received by him, and if no acknowledgment is received within the aforesaid time limit, he may after giving notice to the addressee, treat the electronic record as though it has never been sent.
17.6.9 Time and Place of Despatch and Receipt of Electronic Record—Section 13
Save as otherwise agreed to between the originator and the addressee, the dispatch of an electronic record occurs when it enters a computer resource outside the control of the originator.
Save as otherwise agreed between the originator and the addressee, the time of receipt of an electronic record shall be determined as follows, namely:
- If the addressee has designated a computer resource for the purpose of receiving electronic records:
- receipt occurs at the time when the electronic, record enters the designated computer resource; or
- if the electronic record is sent to a computer resource of the addressee that is not the designated computer resource, receipt occurs at the time when the electronic record is retrieved by the addressee;
- if the addressee has not designated a computer resource along with specified timings, if any, receipt occurs when the electronic record enters the computer resource of the addressee.
Save as otherwise agreed to between the originator and the addressee, an electronic record is deemed to be dispatched at the place where the originator has his place of business, and is deemed to be received at the place where the addressee has his place of business.
For the purposes of this section:
- if the originator or the addressee has more than one place of business, the principal place of business, shall be the place of business;
- if the originator or the addressee does not have a place of business, his usual place of residence shall be deemed to be the place of business;
- “usual place of residence”, in relation to a body corporate, means the place where it is registered.
17.7 DIGITAL SIGNATURE CERTIFICATION
Certifying Authority will issue a Digital Certificate to a Subscriber on payment of certain fees not exceeding ₹ 25000/- after satisfying itself that subscriber hold the private key for corresponding public key to be listed in Digital Certificate, and private key is capable for creating digital signature, etc.
17.7.1 Procedure for Obtaining Digital Certificate
A sender sends his public key to the Certification Authority along with information specific to his identification and other relevant information. Application should be accompanied by certificate of practice statement.
The Certification Authority uses this information to verify a sender and his public key, if everything is correct, the Certification Authority returns the sender a Digital Certificate that confirms the validity of the sender’s public key.
Actually, a Certifying Authority certifies a public key by digitally signing the sender’s public key with an authorized private key. This authorization put the sign on a Digital Certificate. Any user, who wants to use someone’s public key, can verify its validity by applying the Certification Authority’s public key to the digital signature of the Certifying Authority on the available certificate. In this way, the user gets the actual public key of the sender and can tally this public key with that of the public key available on the digital certificate.
No application can be rejected without giving reasonable opportunities.
17.7.2 Suspension of Digital Signature Certificates
A certifying authority may suspend digital signature certificate in public interest, for a period not exceeding 15 days. The certifying authority may suspend a digital signature if a request in this regard is received from the subscriber. On suspension of a digital signature, communication should be made to the respective subscriber.
17.7.3 Revocation of Digital Signature Certificates
A certifying authority may revoke a digital signature issued by it:
- Where the subscriber or any other person, authorized by him, makes a request to that effect.
- Upon the death of the subscriber.
- Upon the dissolution of a firm or winding of a company.
The certifying authority may revoke the digital signature if the material fact represented in the digital signature certificate is false or concealed or where the requirement of the digital signature certificate was not satisfied or the subscriber has become insolvent. On revocation of the digital signature, communication should be made to the subscriber.
17.8 CYBER APPELLATE TRIBUNAL—SECTION 49
Civil courts have been barred from entering any suit or proceeding in respect of any matter which an adjudicating officer or tribunal is empowered to handle. Provisions relating to tribunal and adjudicating officer are as follows.
17.8.1 Appellate Tribunal
The Cyber Appellate Tribunal shall be a appellate body where appeals against the orders passed by the Adjudicating Officers shall be preferred.
The Tribunal shall not be bound by the principle of the code of the civil procedures, but it shall follow the principles of natural justice and it shall have the same powers as those are, vested in a Civil Court. The Appellate Tribunal shall consist of a single person only. The person is called the Presiding Officer of the Tribunal. He shall be appointed by the Central Government. The presiding officer shall be a person qualified to be a judge of a High Court or has been a member of the Indian Legal Service in the post (Grade I) of that service for at least three years. He shall hold office for a term of five years or up to the maximum age of 65 years, whichever is earlier.
Against an order or decision of the Cyber Appellate Tribunal, an appeal shall be made to the High Court within 60 days.
17.8.2 Adjudicating Officer
Affected Party Report for Offences to Cyber Appellate Tribunal shall consist of one person only. The said person is known as the Presiding Officer. He shall be appointed by Central Government. Such a person is equivalent to High court Judge.
An appeal against an Adjudicating Officer’s order within 45 days can be made to the Appellate Tribunal. The adjudicating officer pas orders for any reported offence.
17.8.3 Powers of Cyber Appellate Tribunal
The jurisdiction, powers and authority of the Cyber Appellate Tribunal may be exercised by the Benches thereof. A Bench may be constituted by the Chairperson with one or two Members of such a Tribunal as he may deem fit.
The Benches shall sit at New Delhi and at such other places as may be specified in notification by the Central Government in consultation with the Chairperson. The Central Government shall, by notification, specify the jurisdiction areas of each Bench. Chairperson may transfer a Member from one Bench to another Bench.
If at any stage of the hearing of any case or matter, it appears to the Chairperson or a Member, that the case or matter is of such a nature that it ought to be heard by a Bench consisting of more Members, then they may be transferred by the Chairperson to such Bench as he may deem fit.
17.9 PENALTIES AND ADJUDICATION
An Adjudicating Officer has the power for holding an inquiry in relation to certain computer crimes and for awarding compensation. Penalties can be imposed by adjudicating officer for damage of computer or computer network, for:
- Copy or extract any data from database without permission.
- Unauthorized access and downloading.
- Introduction of virus.
- Damage to computer system and computer network.
- Disruption of computer, computer network.
- Denial to authorized person to access computer.
- Providing assistance to any person to facilitate unauthorized access to any computer.
- Charging the service availed by a person to an account of another person by tampering and manipulation of other computers, etc.
Section 43 of this act provides for a penalty of compensation to the affected persons for damage to a computer system, etc. as decided by a Adjudicating Officer.
17.10 OFFENCES
Following are the offences and penalties under the IT Act:
17.10.1 Offences
- Tampering with computer source documents.
- Damaging a computer or computer system.
- Publishing of information which is obscene in electronic form.
- Electronic forgery, that is, affixing of false digital signature, making false electronic records.
- Punishment for cyber terrorism.
- Electronic forgery for the purpose of cheating.
- Electronic forgery for the purpose of harming one’s reputation.
- Using as genuine a forged electronic record.
- Publication of digital signature certificate, for fraudulent purpose.
- Offences by companies.
- Breach of confidentiality and privacy.
- Publishing false Digital Signature Certificate.
- Misrepresentation or suppressing of material facts.
- Destroys, deletes or alters any information residing in a computer resource or diminishes its value or utility or affects it injuriously by any means.
- Steal, conceals, destroys or alters or causes any person to steal, conceal, destroy or alter any computer source code used for a computer resource with an intention to cause damage.
17.10.2 Penalty for Offences
Various penalties prescribed under act are shown in below mention table:
Network Service Providers shall not be liable for third parties information or data made available by him if he proves that the offences, was committed without his knowledge or consent.
17.10.3 Compounding of an offence—Section 63
The person accused of an offence under this Act may file an application for compounding in the court in which offence is pending for trial and the provisions of sections 265B and 265C of the Code of Criminal Procedure, 1973 shall apply.
17.10.4 Cognizable Offence
Any offence punishable with imprisonment of three years and above shall be a cognizable offence. Any offence punishable with imprisonment of three years shall be bailable.
17.11 LIABILITY OF BODY CORPORATE
Where a body corporate, possessing, dealing or handling any sensitive personal data or information in a computer resource which it owns, controls or operates, such a body corporate shall be liable to pay for the damages that it caused by way of compensation to the person so affected.
- is negligent in implementing and maintaining reasonable security practices and procedures, and
- thereby causes wrongful loss or wrongful gain to any person,
Body Corporate means any company and includes a firm, sole proprietorship or other association of individuals engaged in commercial or professional activities.
Reasonable security practices and procedures means security practices and procedures designed to protect such information from unauthorized access, damage, use, modification, disclosure or impairment, as may be specified in an agreement between the parties or as may be specified in any law for the time being in force and in the absence of such agreement or any law, such reasonable security practices and
Procedures, as may be prescribed by the Central Government in consultation with such professional bodies or associations as it may deem fit.
Sensitive personal data or information means such personal information as may be prescribed by the Central Government in consultation with such professional bodies or associations as it may deem fit.
17.12 DUTIES OF CONTROLLERS OF CERTIFYING AUTHORITY
The duties of controllers of Certifying Authorities can be regarded as functions of controller. A controller may perform all or any of the following functions, namely:
- Exercise supervision over the activities of the Certifying Authorities.
- Certifying public keys of the Certifying Authorities.
- Laying down standards to be maintained by the Certifying Authorities.
- Specifying the qualifications and experience which employees of the Certifying Authorities should posses.
- Specifying the conditions, subject to which the Certifying Authorities shall conduct their business.
- Specify the contents of written or visual material and advertisement that may be distributed or used in respect of a Digital Signature Certificate and the public key.
- Specifying the form and content of a Digital Signature Certificate.
- Specifying the form and manner in which accounts shall be maintained by certifying authorities.
- Specifying the terms and conditions subject to which auditors may be appointed and remuneration paid to them.
- Facilitating the establishment of any electronic system by Certifying Authority either solely or jointly with other Certifying Authority and regulation of such system.
- Specifying the manner in which Certifying Authorities shall conduct their dealings with the subscriber.
- Resolving any conflict of interests between the Certifying authorities and the Subscribers.
- Laying down duties of the Certifying Authorities.
- Maintaining a database containing the records of every Certifying Authority like containing such particulars as may be specified by regulations, which shall be accessible to public.
17.12.1 Licence to Issue Electronic Signature Certificates
Any person may apply to the controller to obtain license to issue electronic signature certificate. License is granted to issue electronic signature certificates on fulfillment of certain conditions like qualification, expertize, manpower, and financial resourses. License granted is valid for specified period and not transferable or heritable.
Every application for license made shall be accompanied by certificate practice statement and identification of applicant. License can be renewed by application and on payment of prescribed fees.
Controller on receipt of application may grant or reject the application. But, when application is rejected, applicant should be given reasonable opportunity of being heard.
Controller may revoke license on grounds of incorrect or false material information or on ground of contravention of any provisions of act. No license can be revoked without a show cause notice.
A license can be suspended for a period not exceeding 10 days after giving reasonable opportunity of being heard. On suspension, the controller shall publish the notice of suspension or revocation of licenses on the database maintained by him on the website maintained by him.
17.13 DUTIES OF THE CERTIFYING AUTHORITIES
Duties of certifying authorities can be summarized as follows:
- The Certifying Authorities to follow certain rules for providing services of issuance of Digital Certificate to subscribers.
- Make use of hardware, software and procedures that are secure from intrusion and misuse.
- Provide a reasonable level of reliability in its services.
- Adhere to security procedures to ensure that secrecy and privacy of the Digital Signatures are assured.
- Observe such other standards as may be specified by regulations.
- Certifying Authority shall ensure the compliance of Act.
- Certifying Authority shall display its license at the place of business.
- A Certifying authority, whose license is suspended or revoked, shall immediately surrender the license to the controller.
- Disclosure: Every Certifying Authority shall disclose its Digital Signature Certificate which contains public key corresponding to its private key, which is used by the Certifying Authority to sign the Digital Signature Certificate of the subscribers.
- Act in Accordance with the procedure specified in its certification practice statement.
17.14 THE DUTIES OF A SUBSCRIBER
In respect of electronic and digital signature, a subscriber has the following duties:
- Generate Key pair, i.e., public key and private key.
- Publish Digital Signature Certificate on acceptance of a Digital Signature Certificate.
- By accepting a Digital Signature Certificate the subscriber certifies to all who reasonably rely on the information contained in the Digital Signature Certificate that
- The subscriber holds the private key corresponding to the public key listed in the Digital Signature Certificate.
- All representations made by the subscriber to the Certifying Authority and all material relevant to the information contained in the Digital Signature Certificate are true.
- All information in the Digital Signature Certificate that is within the knowledge of the subscriber is true.
- Control private key.
Every subscriber shall exercise reasonable care to retain control of the private key corresponding to the public key listed in his Digital Signature Certificate and take all steps to prevent its disclosure to a person not authorized to affix the digital signature of the subscriber.
If the private key related to Digital Signature Certificate has been compromised, then the subscriber shall communicate the same, without any delay, to the Certifying Authority.
17.15 POWER OF THE CENTRAL GOVERNMENT TO MAKE RULES—SECTION 87
The Central Government has power to make rules by notifying in the Official Gazette in respect of certain matters, like:
- Specify the manner for matter or electronic records which may be authenticated by a digital signature.
- Specify the format by which electronic records shall be filed or issued.
- Specify the type of digital signature and the manner, and the format in which it may be affixed.
- Specify security procedure for the purpose of creating the same electronic records and secure digital signature.
- Specify the qualifications, experience, and the terms and conditions of the services of the Controller, Deputy Controller and Assistant Controller.
- Specify the requirements, manner, and the form in which applications is to be made for a license to issue Digital Signature Certificates.
- Specify the period of validity of the license.
- Specify the qualifications, experience of an adjudicating officer as well as other officers.
- Specify salary, allowances, and the terms and conditions of service of the Presiding Officers, etc.
Note:
A State Government’s rule making powers is limited to the provisions relating to electronic forms and the manner and format of e-records and the fees for their filing.
17.16 ISSUE NOT COVERED IN INFORMATION TECHNOLOGY ACT
The Information Technology Act has not addressed the followings areas:
- Jurisdiction aspects of electronic contracts.
- Jurisdiction of the Courts and Tax Authorities.
- Taxation of Goods and services traded through e-commerce.
- Stamp Duty aspects of the Electronic Contracts.
- Protection of the Domain Name.
- Infringement of the copy right law.
17.17 EXCLUDING LIABILITY OF INTERMEDIARIES—SECTION 79
- An intermediary shall not be liable for any third party information, data, or communication link made available or hasted by him.
- Point 1 shall apply if: –
- the function of the intermediary is limited to providing access to a communication system over which information made available by third parties is transmitted or temporarily stored or hasted; or
- the intermediary does not: –
- initiate the transmission,
- select the receiver of the transmission, and
- select or modify the information contained in the transmission;
- the intermediary observes due diligence while discharging his duties under this Act and also observes such other guidelines as the Central Government may prescribe in this behalf.
- Point 1 shall not apply if:
- the intermediary has conspired or abetted or aided or induced, whether by threats or promise or authorize in the commission of the unlawful act;
- upon receiving actual knowledge, or on being notified by the appropriate Government or its agency that any information, data or communication link residing in or connected to a computer resource controlled by the intermediary is being used to commit the unlawful act, the intermediary fails to expeditiously remove or disable access to that material on that resource without vitiating the evidence in any manner.
Note:
For the purposes of this section, the expression, “third party information” means any information dealt with by an intermediary in his capacity as an intermediary.
17.18 NATIONAL NODAL AGENCY—SECTION 70A
The Central Government may, by notification published in the Official Gazette, designate any organisation of the Government as the national nodal agency in respect of Critical Information Infrastructure Protection. National nodal agency is responsible for all measures including Research and Development relating to protection of Critical Information Infrastructure.
17.19 INDIAN COMPUTER EMERGENCY RESPONSE TEAM—SECTION 70B
The Central Government shall, by notification in the Official Gazette, appoint an agency of the Government to be called the Indian Computer Emergency Response Team. The Central Government shall provide the agency with a Director General and such other officers and employees as may be prescribed.
The salary and allowances and terms and conditions of the Director General and other officers and employees shall be such as may be prescribed. The Indian Computer Emergency Response Team shall serve as the national agency for performing the following functions in the area of cyber security:
- collection, analysis and dissemination of information on cyber incidents;
- forecast and alerts of cyber security incidents;
- emergency measures for handling cyber security incidents;
- coordination of cyber incidents response activities;
- issue guidelines, advisories, vulnerability notes and whitepapers relating to information security practices, procedures, preventation, response and reporting of cyber incidents;
- such other functions relating to cyber security as may be prescribed.
For carrying out the above functions, the agency may call for information and give direction to the service provides, intermediaries, data centres, body corporate and any other person.
Any service provider, intermediaries, data centres, body corporate or person who fails to provide the information called for or comply with the direction, shall be punishable with imprisonment upto 1 year or with fine upto ₹ 1 lakh or with both. No court shall take cognizance of any offence under this section, except on a complaint made by an officer authorised in this behalf by the agency.
17.20 POWER OF A POLICE OFFICER AND OTHER OFFICERS TO ENTER, SEARCH, ETC.—SECTION 80
Notwithstanding anything contained in the Code of Criminal Procedure 1973,
- Any police officer not below the rank of Inspector, or
- Any other officer of the Central or State Government, if so authorized by the Central Government.
May enter any public place (includes public conveyance, any hotel, any shop or any other places accessible to the public) and search and arrest without warrant any person found therein who is reasonably suspected of having committed or of committing or is about to commit any offence under this Act.
Where any person is arrested by an officer other than a police officer, such an officer shall immediately send the arrested person to:
- A magistrate having jurisdiction, or
- The officer-in-charge of the nearest police station.
LIST OF LANDMARK JUDGEMENTS
- State vs Amit Prasad
State vs Amit Prasad, was India’s first case of hacking registered under Section 66 of the Information Technology Act, 2000. A case with unique facts this case demonstrated how the provisions of the Indian Information Technology Act could be interpreted in any manner depending on which side of the offence you were on.
- State of Chattisgarh vs Prakash Yadav and Manoj Singhania
This was a case registered on the complaint of the State Bank of India Raigarh branch. Clearly a case of Spyware and Malware this case demonstrated in early days how the IT Act could be applicable to constantly different scenarios.
- State of Tamilnadu vs Dr L. Prakash
State of Tamilnadu vs Dr L. Prakash was the landmark case in which Dr L. Prakash was sentenced to life imprisonment in a case pertaining to online obscenity. This case was also a landmark in a variety of ways since it demonstrated the resolve of the law enforcement and the judiciary not to let off the hook one of the very educated and sophisticated professionals of India.
- NAASCOM vs Ajay Sood and Others (2005)
The Delhi High Court declared ‘phishing’ on the Internet to be an illegal act entailing an injunction and recovery of the damages. It is a form of Internet fraud where a person pretends to be in a legitimate association such as a bank or an insurance company in order to extract personal data from a customer, such as access codes and passwords. The personal data so collected by misrepresenting the identity of the legitimate party is commonly used for the collecting party’s advantage. The court held the act of phishing as passing off and tarnishing the plaintiff’s image.
- SMC Pneumatics (India) Pvt Ltd vs Jogesh Kwatra
The ex-employee of the company had forwarded several emails to the managing director of the company and its other several subsidiary company which are considered by the court as distinctly obscene, vulgar, abusive, intimidating, humiliating and defamatory in nature. The prima facie case of defamation has been observed by the Hon’able Delhi High Court and the restrain order has been issued for not publishing this kind of email in the cyber world.
- State of Tamilnadu vs Suhas Kaati (2004)
The case related to posting of the obscene defamatory and annoying message about a divorcee woman in the yahoo message group by Suhas Kaati. The e-mails were also forwarded to the victim for information by the accused through a false e-mail account opened by him in the name of the victim. The posting of the message resulted in annoying phone calls to the lady in the belief that she was soliciting. The court has ordered the imprisonment and fine, under Section 67 of the Information Technology Act, for harassing by using Internet as medium.
SOME IMPORTANT CASES
Pune Citibank MphasiS Call Centre Fraud
An amount of USD 3,50,000 from the accounts of four US-based customers was dishonestly transferred to some bogus accounts. This incident caused a lot of ammunition to those lobbying against outsourcing in the United States. Such cases often happen all over the world, but when it happens in India it is a serious matter, and we cannot ignore it. It is a case of sourcing engineering. Some employees gained the confidence of customers and obtained their PIN numbers to commit the fraud. They committed this fraud under the guise of helping the customers to get out of difficult situations.
As per standard business practice, highest level of security measures are practised in the call centers operating from India. If not, they there are fair chances that these organization may lose business. There was not as much of breach of security, but of sourcing engineering. The entire call center employees are checked when they go in and out, so that they cannot note down numbers and, therefore, they could not have noted these down. They must have remembered these numbers, gone out immediately to a cyber café and accessed the customer’s Citibank accounts. All those accounts were opened in Pune. The customers complained that the money from their accounts was transferred to those Pune accounts and that’s how the criminals were traced. Police has been able to prove the honesty of the call center and has frozen the accounts where the money was transferred. There is need for a strict background check of the call center executives. However, best of background checks cannot eliminate the bad elements from coming in and breaching security. We must still ensure such checks when a person is hired. There is need for a national ID and a national database where a name can be referred to. In this case, preliminary investigations did not reveal that the wrongdoers had any criminal background. Customer education is important to keep them safe from unwanted troubles of this nature. Most banks are guilt of not implanting this.
sony-sambandh.com Case
India, recently, has seen its first cybercrime conviction. It all began after a complaint was filed by Sony India Pvt. Ltd, which runs a website, named, www.sony-sambandh.com, targeting the non-resident Indians. The website enables NRIs to send Sony products to their friends and relatives in India after they pay for it online. The company undertakes the job of delivering the products to the concerned recipients. In May 2002, someone logged onto the website under the identity of Barbara Campa and ordered a Sony colour television set and a cordless headphone. She gave her credit card number for payment and requested that the products be delivered to Arif Azim in Noida. The payment was duly cleared by the credit card agency and the transaction processed. After following the relevant procedures of due diligence and verification, the company delivered the items to Arif Azim. At the time of delivery, the company took digital photographs showing the delivery being accepted by Arif Azim. The transaction closed at that point. But after one and a half months, the credit card agency informed the company that this was an unauthorized transaction as the real owner had denied having made the said purchases.
The company lodged a complaint for online cheating with the Central Bureau of Investigation (CBI) which registered a case under the Sections 418, 419 and 420 of the Indian Penal Code. The matter was investigated into and Arif Azim was arrested. The investigation revealed that Arif Azim, while working at a Noida-based call center, illegally gained access to the credit card number of an American national, which he misused on the company’s website.
The CBI recovered the colour television set and the cordless headphone. In this matter, the CBI had enough evidences to prove their case, and the accused admitted his guilt. The court convicted Arif Azim under Sections 418, 419 and 420 of the Indian Penal Code. And this was the first time that a cybercrime has been convicted. The court, however, felt that as the accused was a young man of 24-year-old and a first-time offender, a lenient view on his conviction were needed to be taken. The court, therefore, released the accused on probation for one year.
This judgement is of immense significance for the entire nation. Besides being the first conviction in a cybercrime matter, it has shown that the Indian Penal Code can be effectively applied to certain categories of cybercrimes which are not covered under the IT Act, 2000. Secondly, a judgment of this sort sends out a clear message to everyone that law cannot be taken for a ride.
TEST YOUR KNOWLEDGE
What is Cyber Law?
(Ref. Para-17.1)
What are the objectives of the Information Technology Act, 2000.
(Ref. Para-17.2)
What is the scope of Information Technology Act and describe various relevant definitions in it.
(Ref. Para-17.3,17.4)
Explain the computer, computer network and computer system under the Information Technology Act.
(Ref. Para-17.4)
What is digital signature? How is it used for the authentication of electronic record?
(Ref. Para-17.5)
What do you understand by the term ‘hash function?’
(Ref. Para-17.5)
What is e-governance? Explain the various provisions for e-governance in Chapter-3 of IT Act.
(Ref. Para-17.6)
Write a short notes on digital signature certificate.
(Ref. Para-17.7)
Write a short note on the Cyber Appellate Tribunal.
(Ref. Para-17.8)
Which activities can be considered as offences under the Information Technology Act and what are the penalties thereof in IT Act?
(Ref. Para-17.9,17.10)
Explain the liabilities of companies in the Information Technology Act.
(Ref. Para-17.11)
Explain the duties of the controller of certifying authorities
(Ref. Para-17.12)
Explain the duties of the certifying authorities.
(Ref. Para-17.13)
What are the duties of a sub scriber?
(Ref. Para-17.14)
What are the powers of Central Government to make rules under the act?
(Ref. Para-17.15)
Explain the various issues covered and not covered in IT Act.
(Ref. Para-17.16)
MULTIPLE-CHOICE QUESTIONS
- The Information Technology Act is popularly known as _______
- Cyber law.
- Hacking law.
- Electronic law.
- Security law.
- The Information Technology Act is not applicable to
- Whole of India.
- Whole of India except state of Jammu and Kashmir.
- Power of attorney.
- None of the above.
- The Information Technology Act is not applicable to
- Will.
- Cheque.
- Bills of exchange.
- All of the above.
- The Information Technology Act consists of _______ chapters.
- 12
- 13
- 14
- 15
- The Information Technology Act consists of ________ sections.
- 90
- 99
- 100
- 94
- Out of the following, which are the objectives of the Information Technology Act?
- To give legal recognization of e-commerce transactions.
- To facilitate electronic storage of data.
- Both (i) and (ii).
- None of the above.
- Out of the following, which are the objectives of the Information Technology Act?
- To give legal recognization to digital signatures.
- To eliminate signatures.
- Both (i) and (ii).
- None of the above.
- Out of following, which are the objectives of Information Technology Act?
- To facilitate the electronic filing of documents.
- To facilitate electronic storage of data.
- To facilitate online crime investigation.
- None of the above.
- Out of following, which are the objectives of Information Technology Act?
- To recognize e-commerce transactions.
- To allow chat between persons.
- To pay stamp duty online.
- Both (i) and (iii).
- _______ is the key of the key pair used to creating digital signature.
- Public key
- Private key
- Both (i) and (ii)
- Pass key
- _______ is the key of the key pair used to verify digital signature.
- Public key
- Private key
- Both (i) and (ii)
- Pass key
- Key pair includes
- Public key.
- Private key.
- Both (i) and (ii).
- Pass key.
- By using _______ any one can verify digital signature.
- Public key
- Private key
- Both (i) and (ii)
- Pass key
- _______ is the unique value for message or content.
- Hash
- Message digest
- Encryption
- Private key
- Electronic Governance means and includes
- Filing any form online.
- Filing any form offline.
- Make application online.
- Both (i) and (iii).
- What are the benefits of electronic governance?
- Low cost
- Efficient working of government
- Transparency in working of government
- All of the above
- _______ provides legal recognition for electronic records.
- The Indian Contract Act
- The Companies Act
- The Evidence Act
- The Information Technology Act
- _______ issue digital certificate.
- The Certificate Authority
- The State Government
- The Central Government
- NASCOM
- An appeal can be made to _______ against the order of an appellate tribunal.
- A Magistrate Court
- A High Court
- The Supreme Court
- Both (i) and (ii)
- An appeal can be made to high court against the order of appellate tribunal within _______ days.
- 30
- 45
- 60
- 90
- _______ is an offences under the Information Technology Act.
- Sending offensive message
- Stealling information
- Video conference
- both (i) and (ii)
- Digital signature can be suspended by the certifying authority in case of _______
- Public interest.
- Interest of any person.
- Interest of user.
- Both (i) and (ii).
- Digital signature can be suspended by _______
- The Central Government.
- A State Government.
- A Certifying authority.
- The Controller.
- Digital signature can be issued by _______
- The Central Government.
- A State Government.
- A Certifying Authority.
- The Controller.
- Digital signature cannot be suspended for period exceeding _______ days.
- 15
- 30
- 45
- 60
- Certifying authority can be appointed by _______
- The Central Government.
- A State Government.
- A Certifying authority.
- The Controller.
- An application for licence to issue electronic signature certificates is made along with which document?
- Certificate of practice.
- PAN.
- Driving licence.
- Electricity bill.
- The controller shall publish notice of _______ of licence in the database maintained by him.
- Suspension
- Revocation
- Both (i) and (ii)
- None of above
- Controller may revoke a licence on ground of _______ information contained in application.
- False
- Incorrect
- Both (i) and (ii)
- None of above
- No licence shall be suspended by controller for period exceed than _______ days.
- 10
- 15
- 30
- 45
ANSWER KEYS
- i
- ii
- iv
- ii
- iv
- iii
- i
- iv
- i
- ii
- i
- iii
- i
- ii
- iv
- iv
- iv
- i
- ii
- iii
- iii
- i
- iii
- iii
- i
- iv
- i
- iii
- iii
- i

