7
Analyzing the Application of Edge Computing in Smart Healthcare
Parul Verma* and Umesh Kumar
Amity Institute of Information Technology, Amity University, Uttar Pradesh, Lucknow, India
Abstract
The evolution of IoT devices is not only to facilitate the human lives, but at the same time its potential is exploited by various industries that include agriculture industry, healthcare industry, manufacturing industry, and everything in between. It provides wide range of applications to these industries and makes them to work more smartly, accurately and efficiently. IoT Architecture consists of various connected devices; they may be sensors, smart phones, or wearables that produce data which is transmitted to the cloud through IoT gateway. After processing and ana-lyzing the data, the resultant data is forwarded back to the device for execution of further tasks. The volume of the collected raw data is huge that consequences various challenges like low latency, high bandwidth, data analysis and many more. Integrating edge computing into existing IoT architecture is a possible solution to overcome these challenges. Edge computing supports data processing near to the devices that generates it. In this chapter we are going to present an analytical view of application of edge computing for Smart Healthcare and discuss various edge architectures that are available and are being exploited by the smart healthcare applications along with the prospective uses cases in healthcare sector.
Keywords: IoT, edge computing, smart healthcare, real time analytics
7.1 Internet of Things (IoT)
In last years, the scope of the internet is expanded, and it is not limited between two or more computers but something more than that. Now inter-net allows connecting wide range of devices or things which are around us like bulb, refrigerator, washers, and dryers, AC, wearables, and so on. Interconnection of such devices to the internet is coined a term as IoT (Internet of Things). IoT devices are capable in sending data, receiving data and computing the data without human intervention. Such devices are considered as smart devices and allow us to live smart life. Such smart devices change our way of living and transform it into smart living. For example: Handling your home appliances with smart phone from remote location. Gubbi et al. [1] presented an implement of IoT setup that is cloud based and elaborated the technologies and applications to be used in near future.
In addition to our smart home appliances, IoT (Figure 7.1) is an essential technology in other industries like smart healthcare, smart farming, smart manufacturing, smart transportation and many more. In manufacturing industry, it allows companies to automate processes that reduce the overall cost, reduce wastage of materials, and improve quality of product. In healthcare sector it helps in early detection of diseases and remote monitoring of patient. If we talk about smart transportation it helps to predict traffic congestion.
7.1.1 IoT Communication Models
The standard guidelines in the form of architectural document were released by Internet Architecture Board (IAB) in the year 2015. The guidelines outlined four communication models for IoT devices. Rose et al. [2] briefly discuss the various technical communications models described by IAB and highlight the flexibility of connecting IoT devices. The discussion below explains key characteristics of each model.
Figure 7.1 Internet of Things.
Device-to-Device (D-to-D) Communication: In this type of communication two or more devices connect and communicate without intervention of any other device. Such devices connect and communicate with each other using different types of protocols like Bluetooth, Z-wave, and Zigbee. This communication model (Figure 7.2) is commonly used in to control home appliances (like smart light bulb, smart door lock, smart switch etc.) where small packet of information needs to be communicated with low data rate. The limitation of this model is interoperability. It means devices belong to Z-wave protocols are not compatible with devices belongs to Zigbee protocols.
Device-to-Cloud (D-to-C) Communication: In Figure 7.3, this type of model IoT devices directly communicates to cloud service provider. This model support data storage and computation in cloud due to the limited data storage and computation power of IoT devices. It uses existing communication structure like wired Ethernet or WiFi connection to connect devices with cloud server. The performance of this model basically depends on bandwidth and available network resources.
Device-to-Gateway (D-to-G) Communication: In Figure 7.4, device-to-gateway communication model IoT devices are connected to cloud service provider through gateway. Application layer gateway will act as an intermediary between devices and cloud service provider. This model improves the security and brings some level of computation at application layer that improves the performance of IoT devices. For instance, Smartphone act as a gateway that runs some application to communicate with IoT devices and the cloud.

Figure 7.2 D-to-D communication model.

Figure 7.3 D-to-C communication model.

Figure 7.4 D-to-G communication model.
7.1.2 IoT Architecture
IoT architecture (Figure 7.5) is basically classified into three layers. The upcoming and latest technologies are upgrading these layers day by day. Sethi and Sarangi [3] had elaborated IoT architecture in their work. They also explained about protocols, and various applications of IoT in versatile domain.
IoT Devices
IoT devices collect data through various sensors that are connected to each other. The data collected by these sensors is transferred further to IoT gateway. These devices are called as data generator devices and they generate different types of data like environmental data, health data, and motion data to name a few.

Figure 7.5 Layered architecture of IoT.
IoT Gateway
The role of IoT gateway is to perform data processing on the collected data from variety of sensors. The initial processing of data will convert it into meaningful data which is further transmitted to the cloud server. There are many data transfer technologies that might be used like- ZigBee, Bluetooth, Wireless Area Network, Wi-Fi etc.
Cloud Server
Cloud servers are used to store huge volume of data generated by sensors and passed to them through IoT gateway. Data is processed and analyzed and drawn results, by application of various machine learning algorithms. The results are transmitted to the end user in the form of some alert message, text message of may be through email. For example: Any fluctuations in health related data of the patients will send alarm to the concerned healthcare center.
7.1.3 Protocols for IoT
The protocols can be defined as collection of norms that mention common set of standards for data exchange among various devices. In a previous section, the role of different layers in IoT architecture were described, now in this section the focus is to explain the different protocols (Figure 7.6) responsible for seamless communication among the layers. Shadi et al. [4] describes various protocols used in different layers for communication of data.
7.1.3.1 Physical/Data Link Layer Protocols
The section will elaborate various physical and MAC layer protocols. The role of these protocols is to connect various IoT devices; it may be two sensors or sensors and gateway. There are many protocols functioning at this layer, but some most commonly used protocols are discussed below:
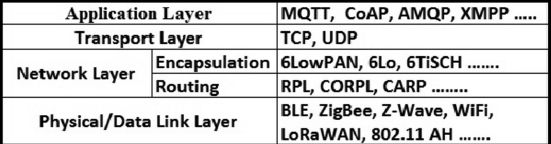
Figure 7.6 IoT protocol stack.
Bluetooth: It is used for short range communications and works at 2.4 GHz in ISM band. It works on the concept of master and slave. In two connected Bluetooth device one may by master and other one will be slave [5]. Two new protocols are introduced under IoT protocols Bluetooth Low Energy (BLE) or Bluetooth Smart for the low power consumption devices. As compared to classical protocol it uses less power and less latency as well. These protocols use adverting and data frames, when nodes are communicating then only, they are awake.
ZigBee: This IoT protocol is meant to be used in applications with less frequent data exchange. The connectivity range between nodes is 100 meters and data transmission rate is 250 Kbps. The protocol is normally used with the applications related to building and home automation, industrial control system etc. It is latest version 3.0 is based on IEEE 802.15.4 standard. It is the unification of the various ZigBee wireless standards into a single standard. Another variant ZigBee smart energy is developed for variety of IoT applications, and it supports different types of topologies as well like peer-to-peer, cluster-tree, or star. This protocol is easier to install and maintain. Zigbee Alliance [6] established in 2002 is responsible for maintaining and publishing the Zigbee standards.
Z-Wave: This wireless protocol uses low energy radio waves and it is basically meant to be used with home appliances. Z-wave [7] allows the user to control the home appliances remotely like light control, door lock, thermostats etc. via the internet from a smart phone or tablet. In different countries it operates at different frequencies and covers physical range 100 meters. It supports data rates up to 100kbit/s. Like Bluetooth it also follows master/slave architecture where master sends the command to slaves and controls the whole network. It is MAC protocol and uses CSMA/CA for collision detection to avoid the possibility of data loss. [RFC 5826] elaborates the basic requirements for the data routing over lossy and low power networks specifically for home appliances.
LoRaWAN: This Long Range Wide Area Network protocol covers long range and consumes less power. It is basically used for the intercommunication between smart devices that consume low power and meant to be used in smart cities. The LoRaWAN [8] uses varied frequency in variety of networks and the data transmission rate is varied between 0.3 Kbps-50 Kbps. [RFC 8376] describes an overview of the LoRaWAN protocol and architecture.
WiFi: The IEEE 802.11 standard (also called WiFi). The commonly used protocol for intercommunication among devices to transfers the high-speed data i.e. up to 1 Gbps. The frequencies are 2.4GHz and 5GHz bands. The range it covers is 50 m. It works in integration of IP (Internet Protocol) IEEE 802.11, but it is not appropriate for IoT applications due to power consumption and frame overhead issue. To overcome this problem IEEE 802.11ah was developed. The elementary 802.11ah MAC layer had features like efficient bidirectional packet exchange, increase sleep time, short MAC frame.
7.1.3.2 Network Layer Protocols
The basic functions performed by network layer are Routing and Encapsulation. Packet formation is facilitated by protocols at encapsulation layer whereas for selecting the optimal path for packet transfer is facilitated by protocols at routing layer. Some important protocols are discussed below.
Routing Protocol for Low-Power and Lossy Networks (RPL): The protocol works on distance vector algorithm. Each node maintains a record of routing table. The algorithm works on the principal of periodic updating of routing table by fetching information from neighbor node. RPL [9] orga-nize a topology as a Direct Acyclic Graph (DAG) that is partitioned into one or more Destination Oriented DAGs (DODAG). DODAG has only one route from each leaf node to the root. To establish communication between leaf node and any other node, it sends Destination Advertisement Object (DAO) to its parent node and then further DAO it is transmitted to root node. Finally, root node will take decision to send the communication request to the respective node at it has complete knowledge of entire DODAG. [RFC 6550] specifies the IPv6 routing protocol for low-power and lossy networks that supports point to point, multipoint to point and point to multipoint traffic. An extension of RPL is Cognitive RPL (CORPL) that is designed for cognitive network.
Channel-Aware Routing Protocol (CARP): It is a lightweight distributed routing protocol used for IoT. It is a protocol design for underwater wireless sensors. It provides significant performance in term of latency and power consumption. CARP avoids loops and forward the packets in a hop-by-hop manner. The drawback of the protocol is to not support reus-ability of data collected earlier. E-CARP is an enhancement of CARP that overcomes the problem of reusability of data and reduce the communication overhead.
IPv6 over Low power Wireless Personal Area Network (6LoWPAN): Due to quite long addresses in IPv6 they are not fit for data frames for IoT data link as the frames are smaller in size. 6LoWPAN [10] allows encapsulating IPv6 datagram in MAC layer frames for use in IoT applications. The important features of this protocols that makes it suitable for IoTs are: supports different network topologies, low bandwidth, low power consumption, long sleep time, mobility, scalability, reliability, and size cannot exceed 128 byte length. 6LoWPAN uses four headers: 00, 01, 10, and 11 which means No 6LoWPAN headers, dispatch headers, mesh headers, and fragmentation headers respectively. 00 is used to discard that frames that does not follow 6LoWPAN specification, 01 used for multicasting and compression, 10 is used for broadcasting and 11is used to break long headers. [RFC 8138] specifies IPv6 over 6LoWPAN routing header that supports low power and lossy network.
IPv6 over Time-Slotted Channel Hopping (6TiSCH): These are the protocols to make specifications for passing long headers through TSCH [11] mode of IEEE 802.15.4e data links.It specifies ways to pass long IPv6 headers through TSCH [11] mode of IEEE 802.15.4e data links. The working is based on channel distribution matrix that consist available frequencies in column and their time slots in row. The complete matrix is classified into various sections that consist of information related to time and frequencies which are visible to all nodes in a network. [RFC 8180] mentions minimal mode of operation for an IPv6 over the TSCH mode of IEEE 802.15.4e network
7.1.3.3 Transport Layer Protocols
Transport layer focuses on end-to-end communication and ensure complete delivery of packets. It also ensures that packets are arriving in order at destination, congestion avoidance, and flow control in network. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two most common protocols working in this layer.
Transmission Control Protocol (TCP): It is a connection-oriented protocol that provides reliable data transmission. It means there is a guarantee that data will reach to destination without losing the integrity of data. TCP [12] protocol establish the virtual path before sending the data to destination, once connection is established then sends the data and finally terminate the connection after successful delivery of data. The packet overhead is very large and consumes more power from the devices, so it is not suitable for the low power devices. [RFC 9006] provide guidance on how to implement and use TCP in constrained node network and explains various techniques to simplify a TCP stack.
User Datagram Protocol (UDP): It is a connectionless and non-reliable protocol as there is a chance of packet loss before reaching to destination but provide fast data transmission in comparison to TCP protocol. Here each packet is independent and select their own path to reach to the destination, there is no predefined path like TCP that is why there is a chance that some packets may struck somewhere in a network and considers as lost packet. After reaching to destination all packets will rearrange because there is possibility that packets will reach in different order as they selected different paths. It is a light weighted protocol that is the reason it is suitable for wireless sensor network communications. UDP protocol is useful for real time application like watching live on your mobile.
7.1.3.4 Application Layer Protocols
This layer protocols helps to provide services offered by any application to the users in a seamless manner. There are many protocols working in this layer, but some common protocols are discussed below.
Message Queue Telemetry Transport (MQTT): The MQTT was initially presented by IBM in the year 1999 and later on in the year 2013 OASIS finally standardized it. It is transport meant for the purpose of messaging and works on the principal of publish/subscribe. It is heterogeneous in nature and its basic role is to monitor heterogeneous devices in the network [13]. It is made up of three basic components- subscriber, publisher, and broker. Publishers are generally light weighted sensors that generate data and transmit data to the subscribers with the help of broker. Initially data is sent from publisher to broker, then the data is classified in topics at broker and finally broker informs to subscribers for any new arrival of data and reverts them their topic of interest.
Advanced Message Queuing Protocol (AMQP): It works at application layer and its major role is to transmit data seamlessly and in a secure manner. Its basic role is to transmit data between cloud and other connected devices with the help of TCP protocol. AMQP [14] architecture is very much similar to MQTT instead of broker is sub divided into two parts. Broker has three core components: Exchange, Binding, and Message Queue. The role of exchange is to receive message and put them in queue. The message queue stores the message until consumed by client app. The binding component is meant for connecting, exchanging, and messaging queue data. Initially exchange will receive the publisher message, then distributes to message queue according to predefined role and conditions there it is classified as topics and finally subscribed by subscriber whenever data is available in message queue.
Constrained Application Protocol (CoAP): It works on the principle of client-server model and its basic role is to make HTTP protocol adaptable to the low power devices and gadgets. CoAP [15] architecture is classified into messaging and request/response layer. UDP (User Datagram Protocol) is used to connect two ends. The messaging technique of CoAP is classified as confirmable, non-confirmable, piggyback and separate that represents reliable transmission, non-reliable transmission, response is send with acknowledgement and response and acknowledgement sends separately respectively. [RFC 7252] defines specification of CoAP usage in the constrained network and it is designed to be get easily integrated with HTTP protocol.
Extensible Messaging and Presence Protocol (XMPP): There are two architecture supported by XMPP – publish/subscribe and request/response and any one of them can be selected by developer. The base of XMPP [16] protocol is XML language and is basically used as communications protocol. Lot of power consumption is involved with XML messages due to headers and tags involved in it and hence considered appropriate for IoT applications. However, later the architecture is enhanced so that XML communication may support IoT applications. Various mode of communications is allowed by this protocol like voice/video calls, chat (multi party), routing of XML data to name a few. The protocol does not support end to end encryption and QoS.
7.1.4 IoT Applications
IoT applications make our life smart and safe. There are many sectors where we found it is playing an important role like smart house, smart healthcare, smart farming, smart manufacturing, smart transportation and many more. Zeinab and Elmustafa [17] reviewed various application of IoT and suggested future avenues for many related technologies. Some applications are discussed below.
Smart Home: The concept of smart home refers to a technology where home appliances and devices can be controlled remotely from anywhere with the help of smart phone, laptop or tablet. The wide range of devices and home appliances are interconnected through the internet that makes the user to control it remotely like room temperature, light, door lock, washers and dryers, refrigerator and many more. Electricity prediction and home security are the most useful applications in smart home as it helps to forecast home energy consumption and allows monitoring home remotely. Matta and Pant [18] addresses the current trends, major research challenges, and application domains in the field of Internet-of-Things (IoT).
Smart Healthcare: Healthcare is one of the applications of IoT that makes many researchers, industries and the public sector to work on it. IoT technology makes doctors to monitor the patient remotely and allows patient to visit virtually. In this way it improves the quality of care and reduces the cost of care in comparison of traditional method of healthcare. It also helps hospital to track patient, staff, and various equipment. As many healthcare devices IoT it helps in early detection of diseases. Dang et al. [19] in the year 2015 gave an analytic review on the prominent usage of IoT devices in the healthcare industry.
Smart Farming: Smart farming is a concept of farming integrating it with technologies like IoT, Artificial Intelligence, Drones, Sensors, Robotics. IoT may help in resolving many critical issues of traditional farming and improves productivity at a lower cost. Smart farming includes various activities like remote monitoring of crop, automation of irrigation, weather forecasting, analyzing ideal time of plantation and harvesting, detection of pests, observing soil conditions and many more [20]. Smart farming relates to improvement in both quality and quantity with low risk. Gill et al. [21] suggested an automatic information system for smart farming based on cloud server. The system provides updated and required information the end-users automatically.
Smart Manufacturing: Industry 4.0 or in other word smart industry represents revolution in manufacturing industry. It is a fourth generation of industry where entire manufacturing process is automated that increases the overall profit of company. It changes how products are invented, manufactured and shipped. Each machines and various industrial equipment are embedded with sensors that generate data which is helpful to analyze the errors in productions process and takes correct action. Vuksanović et al. [22] discussed the role of IoT devices and its usage in the future scenario of the factories.
Smart Transportation: The idea of smart transportation deals with predicting the traffic congestion in advance that helps the user to avoid unnecessary traffic jam by knowing the alternative route. As in many countries’ government is supporting to design electric vehicles to reduce the fuel cost and impact of global warming. In some countries there is a progressive research in the direction of designing self-driving car. In such types of research IoT will perform an important task like detecting pedestrians, traffic signs, obstacles etc. Ferdowsi et al. [23] discuss deep learning in intelligent transportation systems for traffic flow prediction, self-driving car and traffic signal.
7.1.5 IoT Challenges
Internet of things applications outlined above is rapidly increasing over last few years but still there are some challenges while implementing IoT. Omid Helmi et al. [24] analyzed and elaborated different types of challenges that are there in IoT environment. Following are the area of concern-
Security and Privacy: IoT devices do share lot of personalized data of the end user, this leads to the various security and privacy concerns for that data. In a study it has been observed that almost 70 percent of IoT devices are vulnerable in nature due to non-availability of standard encryption and authentication techniques. The manufactures and policy makers should frame some standards to deal with this scenario. Alansari et al. [25] elaborated about vulnerabilities of IoT systems and discussed about various model that may be used to protect data and systems.
Interoperability: IoT includes millions of interconnected devices over the internet. These devices are smart devices and able to process the information. But each device has different information, processing, and communication capabilities as the manufacturing companies around the globe produce various product categories. Interoperability among heterogeneous devices connected in any application is one of the critical issues with IoT devices. There are numerous interoperability challenges that can be dazed by the proposed CoRE framework by Mazayev et al. [26].
Data Analytics: The voluminous amount of data generated by heterogeneous IoT devices cannot be analyzed in a proper manner due to poor quality of data. It is a tough task to segregate useful and useless data among such huge volume of data. There are numerous challenges regarding data management that are pointed by Cooper and James [27].
Volume of Data: Some IoT applications include frequent communication between devices and continuous collection of data that will increase the volume of raw data. The processing, storing and management of huge amount of data is another challenging task with IoT technology. Constante et al. [28] in his work analyzed the impact of large volume of data and the processing challenges. They also draw attention towards research works tools used for such data analysis.
Power Supply: The smart IoT devices are not connected with continuous power supply hence they need self-reliant energy source. The power consumption depends mainly on data processing, transmission, and sensing as well. The power supply requirement for the wireless technologies is towards higher side be it Bluetooth or Wi-Fi. This generates a demand of less power consuming wireless technologies. Perković et al. [29] developed power estimation analysis system. The core work of their system it the sum up the various possibilities for its future use.
7.2 Edge Computing
Centralization and Decentralization is the core of computing. In a history in each decade a wave shifts from centralization to decentralization. Starting from mainframes and then shifting to personal computers and then again moving on to the cloud. In the last two decades we were storing each and everything on cloud even our personal data. Cloud has it pros and cons like any other technology; privacy of data and cost management are the two major drawbacks of cloud [30].
The latest wave of decentralization is in the name of Edge computing. It lies between the date generation sources like sensors and other IoT devices and cloud server. Weisong et al. [31] addressed the various issues related to the edge computing, current status and future avenues. Edge resolves the latency issue of cloud and bandwidth issue by transferring only relevant data to the cloud after performing real-time processing.
7.2.1 Cloud vs. Fog vs. Edge
In this section, Table 7.1 compare cloud computing, fog computing and edge computing.
Table 7.1 Cloud vs. fog vs. edge.
| Cloud computing | Fog computing | Edge computing | |
|---|---|---|---|
| Architecture | Centralized | Distributed | Distributed |
| Processing of data | Central cloud server which is very far from source of data. | LAN hardware or IoT gateway | Sensors connected devices |
| Processing Power | Advanced processing technology | Low processing | Low processing |
| Storage | High | Medium | Low |
| Purpose | Data analytics for long term processing | Quick analysis for real time response | Real Time Analytics |
| Advantages | Scalable, Big data processing, Unlimited storage | Low latency, Data security, Low bandwidth, Reduce network traffic | Low latency, Data security, Low bandwidth, Reduce network traffic, low power consumption |
| Disadvantages | High latency, Slow response time, High power consumption | Limited processing and storage | Limited processing and storage |
7.2.2 Existing Edge Computing Reference Architecture
The new paradigm of computing in network environment is edge computing, where resources and services are now shifting from cloud to the edge. Edge is now gaining momentum and various researchers provided different architecture, capabilities, terms and features for Edge architecture. The following section elaborates various reference architectures (RA) with respect to edge computing.
7.2.2.1 FAR-EDGE Reference Architecture
FAR-EDGE RA [32] is an effort of leading experts in manufacturing, industrial automation and future internet (FI) technologies. According to this RA there are two viewpoint of a factory automation- functional viewpoint and structural viewpoint. Functional viewpoint focuses the functionality of the industries and divided it into three domains- Automation, Analytics and Simulation whereas structural viewpoint represents the detailed structure of factory automations that covers the various steps from collecting the data to utilizing the processed data. Figure 7.7 represents four tiers under structural viewpoint – Field Tier, Edge Tier, Ledger Tier and Cloud Tier.
7.2.2.2 Intel-SAP Joint Reference Architecture (RA)
Intel and SAP [33] developed reference architecture for edge computing environment that delivers solutions for cloud and sensors integration. The RA facilitates the enterprises to understand the secure management of smart network of IoT devices. The network of IoT devices collects, manages and analyze the data and combine it with business intelligence. Figure 7.8 represents the various blocks of Intel-SAP joint RA.

Figure 7.7 FAR-EDGE reference architecture.
Figure 7.8 Intel-SAP joint reference architecture.
7.2.3 Integrated Architecture for IoT and Edge
The integrated architecture of IoT and edge (Figure 7.9) helps in eradication of various challenges in the existing architecture. It handles voluminous data, issue of latency, privacy and many more. The edge facilitates processing of collected data near to the source like gateway, router, laptop etc. The core of edge computing is to reduce overhead on cloud. Wei Yu et al. [34] briefed the integration of IoT with edge and elaborated its challenges and benefits.
Sensors and Actuators: In IoT environment data is generated through sensors and they are capable to sense the surrounding environment such as temperature sensors, humidity sensors, motion sensors, smoke sensor, gas sensor etc. The role of actuators is to convert energy into motion. Sensors are capable data collection only, so the data collected with these sensors pass to IoT board that is capable in data processing and data communication.

Figure 7.9 Integrated architecture for IoT and edge.
Edge Computing: The latency in case of edge computing is reduced in various real time applications by performing data processing just near to the source of data generating devices. Edge computing improves the performances of IoT devices, reduces bandwidth utilization and provided better security and privacy. It helps to offload the various important tasks which are earlier performed by the centralized server called cloud server. It includes two major components one is called edge devices and the other one is edge gateway.
Edge Devices: Edge devices perform real time data processing based on the trained model. These devices are either IoT devices which is a primary source of raw data or IoT board that is directly connected to the sensors which collects the real-world data. There are some single board computing devices are also available that are so powerful and smart enough to replace the desktop in near future. These devices are even capable to execute machine learning algorithms and very small in size and low in cost. Some of the popular single board computers and their specifications are – Raspberry Pi 4 model, Latte Panda Alpha, Udoo Bolt and Jetson Nano (NVIDIA).
Edge Gateway: Edge gateway performs pre – processing of data, allows data storage and various intelligent algorithms are installed. The devices that can be used as edge gateway are network devices (like routers, switches, and gateway), intelligent controllers (like PLCs, RTUs, and DCS) and micro cloudlets. Micro cloudlets are also called as micro data centers with high end processing speed, large amount data storage capacity and high bandwidth wireless LAN. The Edge gateway provides communication standards for various interfaces like wire, radio-based and technologies like – Bluetooth, 3G mobile radio, ZigBee, Z-Wave, LTE. Preprocessing of data and preliminary learning of data at edge gateway will help to offload the work of centralized cloud server that results the performance of the time sensitive applications will improve and provides the benefits to the end user.
Centralized Cloud Server: Cloud server is accountable for further processing of data received from edge computing layer, enhance the analysis of data by introducing advanced machine learning techniques and store the data as a historical data for future research. It mainly handles large set of data by using big data processing tools and technologies. Some of the best big data tools are Hadoop, HPCC, Storm, Qubole and many more. These tools are cost effective and incorporate time management in various data analytics tasks. It also includes some advance learning techniques called deep learning. Deep Learning (DL) creates multi-layered structure of neural networks. In comparison to ML algorithms Deep learning algorithms are step ahead. Popular DL algorithms are ANN (Artificial Neural Network), CNN (Convolutional Neural Network), RNN (Recurrent Neural Network), RBM (Restricted Boltzmann Machines), DBN(Deep Belief Network), LSTM (Long Short Term Memory Networks) to name a few. Training and testing of models are performed at cloud server and finally the trained model is deployed over edge devices to take early decision.
IoT Application: IoT applications are various apps that are delivering the services to end user and act as a user interface with the help of API (Application Programming Interface). These apps help the user to access the real time data and make them to take early decision. There are various sectors where sectors where IoT plays an important role.
7.2.4 Benefits of Edge Computing Based IoT Architecture
Introducing edge computing in IoT architecture brings various benefits in IoT implementation that includes less response time, low bandwidth and efficient communication. This section will elaborate various benefits of integrated architecture of IoT and Edge.
Network Performance: The network performance of Edge Computing environment can by evaluated on latency, network bandwidth and network traffic. Edge computing improves the performance of applications by reducing latency. Latency is basically dependent on delays (transmission, propagation, computing, and queuing). Krittin et al. [35] studied the effect of communication and computational latency in edge environment. The major contribution of edge is to pre-process data that results into its size reduction before transmitting it to cloud. SpanEdge reduces latency and bandwidth consumption as proposed by Sajjad et al. in [36].
Efficient Data Management: Processing data at edge computing will provide efficient data management. It is like preprocessing of raw data before sending to cloud server for further processing and analysis. The preprocessing involves cleaning, integration and transformation of data. Huge amount of data is collected by IoT devices, but some small percentage of total data is important that needs to be sent to cloud server. Edge computing will allow finding out important data and aggregating it that results reduced data size which will improve the analysis and helps various applications to perform their task efficiently. The advancements in edge computing with respect to its impact on IoT applications are analyzed by Hassan et al. in [37].
Data Analytics and AI: Edge computing will allow some extend of data analytic and artificial intelligence to those IoT services which need fast response. Artificial Intelligence (AI) is achieved by introducing machine learning models at edge itself. It will improve the learning performance as well as reduce network traffic. For example, self-driving vehicles fast response is necessary to avoid any hazardous consequences. Wazir et al. [38] highlighted the significant role of edge computing in versatile real time applications where sending responses in real time is the fundamental requirement of applications like healthcare applications.
Security and Privacy: Edge computing offers many operations closer to the devices that collect data. By applying various advanced tools and techniques edge will provide security of data. The distributed nature of edge computing will have limited impact if there is any attack on the network. Security services at the edge can be used to ensure that the devices which are more vulnerable will isolate easily and protect from any attack. In addition to security aspects of IoT, additional areas like confidentiality, access control, data integrity and authenticity is also in consideration to improve security and privacy. Edge and IoT integration was presented by Lin et al. in [39]. They also conducted a summary of IoT with respect to system architecture.
Low Power Consumption: Edge computing also contributes in reduction of power consumption by reducing data transmission load on network. Processing data near to the devices that produce it leads to reduction of power consumption. Improvement in latency may also improve battery life of IoT devices as communication channels are opened for short span of time. Impact of energy consumption in various IoT devices is analyzed by Mocnej et al. [40]. They also elaborated the utilization of edge computing in the IoT.
7.3 Edge Computing and Real Time Analytics in Healthcare
The concept of application of ML in integrated environment of Edge Computing and IoT is rising day by day. The combination of these technologies is now in application phase and is being deployed by many industries in various use cases. Smart devices may use ML and DL techniques at edge and reducing the burden on cloud as the processing will be performed at the local or device level.
Traditionally the data collected by IoT devices are processed by the cloud sever. The huge volume of such data overburdened cloud servers; the edge here plays a crucial role in diminishing the load of cloud server by application of ML/DL algorithms and classifying which data to be processed at edge and the other needs to be processed at cloud server by more powerful algorithms. There are many applications which need real time analytics to be performed on some crucial data especially healthcare and some financial applications; the application of ML/DL techniques at edge is an added performance benefit for such applications. Edge ML also deals with the security aspects of an application where personalized information is being stored at Cloud which is global in nature.
Healthcare sector is more and more focusing on providing better support to patients. The role of Deep Learning is becoming a promising and transformative in healthcare. Basically Deep learning models consists of multiple layers, the input data passes through multiple layers and each layer performs a kind of matrix multiplications on data. After passing through multiple layers the last layer will ultimately produces a feature set or final output. There are variety of deep learning models used in a specific scenario like – DNN (Deep Neural Network), CNN (Convolutional Neural Network) and RNN (Recurrent Neural Network). Integration of deep learning with edge computing improves real time processing which is a crucial aspect in case of healthcare systems. To address the issue of latency and quick performance in real time applications, variety of integration model of edge with deep learning are proposed.
The general architecture of an Edge Computing Environment includes a sensor/smart device and edge/fog/cloud computing node. The edge layer is being used to bridge the gap between the cloud server and the IoT devices. IoT layer consists of variety of healthcare sensors each having unique identification. The data collected from these sensors is further transferred to the edge layer using WiFi, Bluetooth, or ZigBee.
The variety of devices is being used by researchers in various healthcare models categorized as smart device, medical instruments or IoT based sensor kits. The edge devices are growing day by day starting from Nokia mobile or PDA in their initial days. The latest smart phones are now being used in variety of healthcare applications. Smart phones sensors though are easy to use but have limitation of embedding variety of sensors in it. Using dedicated medical sensors helps in collecting and handling large volume of health data that may lead to more accurate diagnosis [41].
Author Liu et al. [42] proposed RMCS (Remote Medical Care System) model for miners to assess their physical and mental health by making use of biosensors. They applied emotion shift theory knowledge and made use of EHR (Electronic Health Record) to draw inferences. The brain wave sensors are fixed in miner’s helmet which collects data about physical and mental status of minors and issue early warning signals. The overall system uses ZigBee network. The information collected through sensors will be transmitted to minor’s mobile phone and from there the information will be transmitted to backend system where the physical and mental status of miners is evaluated using EHR ontology model. In case of emergency miner’s family and paramedic facilities are automatically informed.
Dubey et al. [43] developed a fog computing architecture (Figure 7.10) that emphasized on data reduction, low power consumption and highly efficient. Their proposed architecture is service oriented, and its main asset is low power embedded computer. The model performs data mining techniques and analytics on the data collected by number of wearable devices. The data read is in time series pattern and further analyzed by embedded computer. The analytics helps in identifying the unusual data in the series of data which are further transmitted to cloud for analysis.
The Intel’s Edison processor used by them is low power device that is supported by rechargeable battery. They used the DTW (Dynamic Time wrapping) algorithm for pattern mining in data. The role of DTW is to find similarity between two data series. Further they used CLIP (Clinical Speech Processing Chain) that is a series of operation to filter speech data. To compress data they used GNU zip for compression and decompression algorithm. Fog processor reduces data transmission and storage at cloud by processing it at local level for data for healthcare.

Figure 7.10 Fog computing architecture.
Speech Monitoring for Patients of Parkinson’s Disease: They collected speech data from smart watches and sent it to fog gateway. The Intel Edison processor at fog computer processes the speech data by DTW and CLIP. The features and patterns extracted at fog are further sent to the cloud. The data compression performed by DTW, CLIP and GNU. Among all CLIP achieved 99 percent of data reduction.
The authors proposed a cascading architecture as mentioned in Figure 7.10 based on fog computing which has three sub-systems as – BSN (Body Sensor Network) is used for data acquisition, the second sub-system is a fog gateway which will process the acquired data and for further back-end analysis cloud server is used. The role of fog gateway is to filter out the relevant information that needs to be transferred to the cloud server for further processing.
Gaura et al. [44] in their proposed work moved analytics at IoT nodes that leads to less transmission of data hence reducing network loads. This edge mining techniques takes place at the edge of IoT device. L-SLIP (Linear Spanish Inquisition Protocol), Class Act and BN (Bare Necessities) these three algorithms developed by authors are used to reduce sensing messages and eventually reducing less energy and less storage as well. Various sensors transmit redundant data, edge mining focus on saving packets rather than bits and hence improve performance.
The authors proposed the processing of data collected by various sensors at the edge nodes that are near to the sensors only and they convert raw signals into some meaningful information. The real work of edge nodes is to estimate the states and convert it into some meaningful information that is required for the application. The raw data from the sensors may give raw information like someone entered the room; however the state information like how many people are there in the room may be inferred from filtering information collected from the sensors. Further to state estimation, event detector will decide about the significant change in state.
The purpose of L-SIP algorithms is to acquire data from sensing applications and re-construct the signal if it’s loses energy. The purpose of Class Act algorithm is to recognize human posture and store the various timestamps in the change in posture. The BN algorithm provides the time spent in different positions. The overall performance is recorded as L-SIP reduces the packet transmission rate by 95%, BN reduces 99.8%, and Class Act reduces packet transmission by 99.6%. The results justified the importance of edge mining in various IoT based applications.
Bhargava et al. [45] proposed a WNS based system for the localization of elderly suffering from Alzheimer disease. The author proposed a system that will perform analysis of data collected at the local level close to the data source for better response and detailed analysis is performed at cloud level based on historical data. The fog based wireless sensor network system was proposed by authors for outdoor localization of elderly people. The analysis was performed on data collected through wearable devices obtained from the Kasteren dataset. The proposed system is a combination of two nodes – wearable device and cloud gateway. They used genetic algorithm for the activity recognition using IEM (Iterative Edge Mining) that facilitates localization. The mining algorithms on edge are based on SIP (Spanish Inquisition Protocol) that converts raw data into application specific states. The data is further transmitted to a cloud only if it is not predicted by past estimation or approximation model. The general SIP models are as follows -
L-SIP works on sensing applications where reconstruction of original signal is required.
Class Act approach is used to detect human postures; it stores and transmits timings of change in human postures but not the original signal. It is based on decision trees; it takes signals from body worn accelerometer sensors and then performs posture estimation. It is well suited for embedding in wireless sensors, it is simple and closely knitted with the application and hence capable of making strong assumptions about the output.
BN does not keep a record of timing it is appropriate to get summa-rized information of time duration of different states. States are being represented in the form of distributed and non-overlapping bins. Change in distribution of these bins represents occurrence of any event. Class Act and BN are destructive approaches hence preferably used in the applications where reconstruction of signals is not required. The results confirm that our system can achieve a high positional accuracy despite a short initial training period and low frequency of data computations on the resource constrained sensor devices.
Althbeyan et al. [46] proposed system that collects patient data like temperature, glucose level and other activities and transmits that data to the cloudlets. The abnormal values are further transmitted to the MEC (Mobile Edge Computing) servers and removed immediately from the memory in order to maintain privacy. The decision support system attached with MEC system has to analyze only abnormal value instead of bulk of values. This reduction technique to reduce computing complexity is called inexact computing used along with morphological filtering to reduce data processing.
The model proposed consists of four major components- cloudlets, MEC system, DSS (Decision Support System), DCS (Data Collection System). Their proposed model observed reduction in power consumption and per user delay.
Bhunia et al. [47] applied fuzzy techniques for selection of data to be transmitted for analysis of data collected through IoT sensors. Authors used this technique for the identification of heart condition of the patients. They prepared knowledge base and rules for the detection of some early signs of any serious heart trouble in real time. The data collected from the various sensors is aggregated and send to fuzzifier. The role of fuzzifier is to classify the parameters using some predefined functions. Finally, fuzzy inference system processes fuzzy sets that are based on the input from rule engine.
They programmed fuzzy system on the Arduino board which they used as an aggregator in the healthcare application. The selection of data to be transmitted is done by fuzzy rules. Required data to generate alert is only transmitted. They compared normal data collection technique with their proposed technique, and they observed considerable reduction in energy consumption. By adopting this approach, they can reduce energy consumption by sending only required data over costly communication channel.
Borthakur et al. [48] proposed usage of machine learning approach on the edge computing device which requires considerable fewer amounts of resources. They collected speech data of patients suffering from Parkinson’s disease through smart watches used by patients. They employed Intel Edison and Raspberry Pi as a Fog computer architecture. In general machine learning model are implemented at cloud to process physiological data for the traditional telecare model. K-means clustering algorithms are used for the analysis of data. Clustering of unlabeled data is performed at fog layer. This clustering can be helpful for the real time sub-grouping of Parkinson’s disease data. They collected 164 speech samples and selected features as average fundamental frequency and intensity. The feature extraction is done using Praat an acoustic software for analysis. K-means algorithm used for clustering is implemented in Python. Their proposed architecture is useful in handling speech processing and disorders in real time. Fog computing architecture reduces the dependency on cloud server. Their work utilized low resource machine learning approach on fog device and the results show that proposed architecture is promising for low- resource machine learning.
Hosseini et al. [49] developed a system for the monitoring and regulation of epilepsy. An automated edge computing framework (Figure 7.11) proposed by them to process volume of data generated which is a part of decision support system. The estimation model for the estimation of epi-leptogenic network using EEG and rs-fMRI is also developed. An unsupervised technique based on Deep CNN to differentiate between interictal epileptic discharge (IED) periods and nonIED periods using electrographic signals from electrocorticography (ECoG).
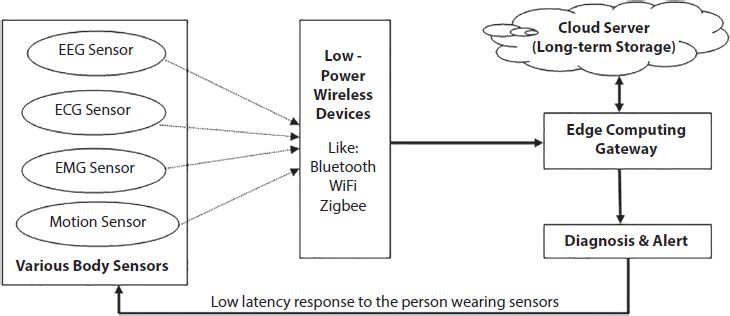
Figure 7.11 Automated edge computing framework.
Their proposed framework is divided into three layers- Sensing layer, Edge computing gateway and cloud computing layer. Sensing layer consists of various biosensors to collect physiological data like heart rate, motion etc. The sensors are wearables and implantable also and the data collected is transferred to the Edge Gateway through Bluetooth, ZigBee and Wi-Fi as well. The Edge gateway does not work just like simple Access Point or Base Station it performs initial diagnosis and finally data is being transferred to cloud layer for long term storage.
The volume of data that is collected by the Biosensors is pre-processed at the edge layer before it is transferred to the cloud environment for further processing. Pre-processing of data at edge layer will provide real-time services to the patients. The EEG and rs-FMRI data collected is processed at local level. The data pre-processing is performed by Butterworth band pass filter which cuts frequencies and removed unwanted frequencies. Further for the identification of abnormalities at functional level re-clustering is applied. Wavelet transformations are applied to capture rhythmic nature of an epileptic seizure and for high level feature extraction. An edge computing gateway operates constantly even in the situation when connectivity between cloud and monitoring system is lost. Edge gateway supports cloud-based system by supplementing them in terms of real-time computing, low latency, heterogeneity, and scalability.
Sood et al. [50] proposed fog computing based system for the continuous monitoring and analysis of hypertensive patients. The data is collected through IoT sensors at fog layer for the identification of various stages of hypertension in the patients. After identification of stages, further analysis of risk level is done by application of Artificial Neural Network (ANN).
The fog-based system collects health related temporal data in a specified time window. This helps in risk assessment of hypertensive patients. The granulation of temporal data collected is associated with attribute of data values that is collected in a window time. The real time processing of data collected is performed for diagnosis. The diagnosis will produce an alert message on the end users phones to take preventive measures on time. The results show promising efficiency in bandwidth, minimum delay good response time, and higher accuracy.
Shammin et al. [51] proposed an edge computing-based system to control spread of COVID-19 epidemics. The biggest challenge of real-time monitoring of epidemic is to collect and process pathological, radiographic, and other types of information. They used Deep Neural Network for the processing and analysis of data collected during epidemic. Their three- layered framework - in which bottom layer consists of end users, stakeholders, hospitals and the decision makers. At this layer general health data is being collected like Blood pressure, temperature, and cough quality through app by patients. AI based module will investigate these preliminary symptoms and will categorize further action as per the rules. Middle layer is the combination of edge server, cache, and nodes. The topmost layer is cloud that consists of cloud servers and global storage.
Deep learning model works on cloud that contains servers with high computational power. The global storage area at cloud stores hospital and physiological test signals. These signals are in form of variety of images (X-Ray, CT-scan, protease sequences), and other physiological features like body temperature, blood pressure so on. The signals are collected from the connected network of hospitals. Three Deep Learning models are adopted ResNet50, deep tree, and Inception v3. Various streams are used for different types of image signals. Final step is decision fusion that is performed by each stream that helps in decision making even if any of the modality is missing.
The middle layer during the off-peak times downloads the DL model and shifts it to edge. The edge server is located nearby to the specified hospital. The collected data samples are transferred to edge through wireless technologies. The role of edge server is to secure the data using blockchain and further forward it to DL model. The explainable AI at edge is used for the understanding of output of each layer of DL model in the healthcare applications. The test data from hospitals and other symptoms are analyzed at edge using latest high power edge computers.
Ejaz et al. [52] developed an integrated system of edge computing and blockchain for the smart healthcare system. The objective of their system is to avoid long operating times, network issues, security and cost in highly dynamic network conditions. They assessed their system on the basis of following key terms like latency, power consumption, network utilization and computational load and compared the performance with the systems where blockchain is not used. Their model monitored various health parameters of the elderly person like blood pressure, heart rate, oxygen or blood sugar level. In case the parameters value goes beyond the range the alert message is issued for the healthcare centers.
Figure 7.12 represents a proposed framework consists of 3 layers – local tier, access tier and core tier. The local tier consists of variety of sensors that may collect data from various resources and then pass it on further to the edge or cloud servers for further processing.
At local tier, the edge nodes that are resource constrained do pass the data to the higher computational capacity node. The local nodes of edge are in the vicinity of the elderly or disabled person. The permissioned blockchain will run at the local edge nodes for the transfer of trusted information among different entities of the system like end users, healthcare workers, emergency units etc.
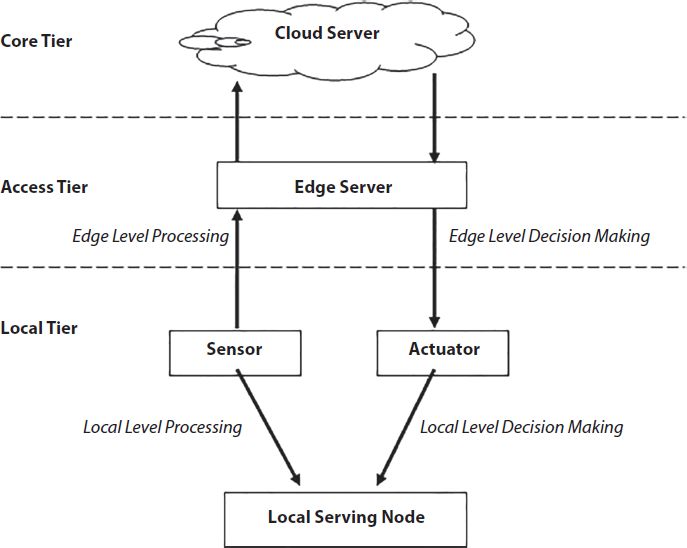
Figure 7.12 Integrated edge computing and blockchain architecture.
The access tier is much richer as compared to local tier and includes edge server, MEC servers and their role is to provide computational capabilities to the monitoring services. The basic role of this tier is to perform data analytics, decision making, security and privacy services, and allocation of resources. At this layer only blockchain provides an auction/renting of various resources for processing and storage capacity and/or for health-care services as well.
Core tier is the richest in term of resources it provides huge number of resources. The major role of this tier to provide service logic that is used to manage overall working of healthcare systems and provide required resources.
The integration of edge and blockchain results into secure, trusted and delay-critical healthcare services for remote monitoring cases such as monitoring of elderly and disabled people. Their proposed Health-BlockEdge framework brings resources near to the end users and performs real time data analytics and decision-making functions to improve system-level resource efficiency.
7.4 Edge Computing Use Cases in Healthcare
The current scenario of pandemic has raised the demand of digital health-care system. The fast-spreading disease like COVID-19, need real time responses from the healthcare industry, and put a pressure on healthcare providers to work in tight margins. Digital health is necessary now to meet the requirements of better resource management and collaboration across the healthcare industry. The key driver for the digital health in the coming future will be edge computing. Edge computing is all set to revolutionize the healthcare services. Following are few of the use cases.
Ambulance Service
The emergency services in healthcare system require prompt ambulance services to transport the patients to the healthcare centers. The unstructured way of ambulance management is one of the key reasons for so many causalities in recent time of pandemic. In emergency real time alerts and reachability of the services is required.
The promising performance of edge computing (along with 5G) with low latency, and high data processing capabilities may enable accurate and fast diagnosis and treatment by healthcare centers. It can provide more coarse information at the healthcare centers about the status and location of incoming patients and centers may take appropriate measures and be prepared to handle any adverse situation.
It can be achieved by the following:
- The data is transmitted to the hospital collected through body cams (enabled through 5G). This information will give live updates about the patient situation and healthcare staff will plan for potential treatment before patient reaches there.
- Real time analysis of patient data regarding blood pressure, heart rate at the edge and response by the healthcare personnel.
- To display patient’s information like treatment history and other details can displayed on augmented reality glasses at edge to empower healthcare personnel.
- Diagnostics by remote ultrasounds using Haptic-enabled tools. Haptic also known as 3D touch is a technology where electronic and mechanical movements can be experienced through an interface.
Companies like Vodafone and BT are exploring the potential of this use case and trying to develop point of care to deliver services by exploiting the potential of 5G and MEC (multi-access edge computing). STL partners are also looking forward and trying to quantify its potential in the industry.
Patient Monitoring
Variety of monitoring devices is being used by healthcare sector like glucose monitors, various sensors, and health tools as well. These monitoring devices are either not connected or they store data at cloud. The security concern for such data is very high and limits its adoption.
The solution can be on-premise edge where data will be stored locally to maintain privacy. It will also facilitate processing of hospital data from various sources and extracting meaningful information. Edge is capable of sending notifications to doctors about unusual symptoms of patient behavior through analytics. Implementing edge at local level will observe significant resource efficiency, increase in productivity and will definitely decrease cost per patient.
Few implementations in this context are as follows:
Google Deep Mind/Google Health used for the early prediction of kidney injury so that early action can be taken to regulate it.
CareAI – This is a platform used majorly for the monitoring of critical patients, even when they come out of the critical situation. It helps in improving the quality of healthcare services an also improves their operational efficiency.
AWS Outposts – AWS is all set to target healthcare industry integrating it with its own on-premise edge technology. They are more concerned about the security and privacy of personalized healthcare data. AWS is set to provide power of core cloud to the healthcare industry.
Remote Care
The lifestyle and pressure of various factors on people lives is directly reflecting in their health and this needs prompt and reachable healthcare services. In the present scenario the healthcare staffs are overburdened. Treatment of chronic diseases such as diabetes, cardiac disease needs regular monitoring. Another scenario where rural peoples are not able to access the healthcare services due to reach ability issues or expensiveness.
Remote monitoring of patients (elderly and living in rural areas) may improve healthcare scenario. Wearable, sensors, IoT devices may provide real time updates of patient’s health status and can alert healthcare workers to take action.
Processing health data at cloud is not safe as there are lot of critical information of patient’s health is there. Data at edge is safe as it is processed at local level between patient and healthcare provider only. The low latency is required to process data in a real-time scenario can be will supported by edge. Processing data at edge reduces cost by processing data close to the source itself.
Examples:
Intel and Flex created an innovative Healthcare Application Platform. It enables healthcare solutions to deliver their services in a secure manner across the connected and always expanding healthcare edge and cloud. The Intel and Flex IoT engine enhance robustness and ease of use for various healthcare solutions.
Dibatacare monitors blood sugar level through mobile apps and devices; it sends the data to the healthcare centers, clinicians. Personalized treatment is provided to patients as per the requirements and periodic visits are adjusted to the nearest clinic in case of any emergencies.
TELUS Home Health Monitoring is used for remote monitoring of patients. It helps in reducing the pressure on healthcare systems. It regularly monitors basic health factors and reports any deviation from the standard values to the healthcare centers/providers.
7.5 Future of Healthcare and Edge Computing
Integration of 5G and edge computing has the potential to bring revolution in the healthcare industry. Edge computing creates a safe environment for the healthcare devices and also trying to remove dependency on cloud environment. Latest technologies like Internet of Things, Augmented Reality, and Virtual Reality are playing crucial role in virtual healthcare systems. Removing dependency on cloud resolves various issues of downtime, network congestion and latency as well. In healthcare solutions small delay leads to the critical situations.
Edge computing is contribution these days in recording patients vital through wearables and other connected devices. CPE (Customer Premises Equipment) and VCPE (Virtual Customer Premises Equipment), gateway and switches send the collected vitals to the edge servers. The data at edge syncs with the cloud in specific time interval. Sometimes edge computational device is also implemented at edge for real time data processing, analysis and drawing conclusions.
The latest reports of GM insights the IoT healthcare market is going to grow by 15% by 2024. The demand for remote monitoring applications in healthcare sector is getting hike. The Business Insider reports that 5.6 billion IoT devices are in use by the organizations and government for collecting data and for processing it in 2020 and will keep on growing in the coming years as well. These reports visualize the future of real time processing in healthcare systems using edge computing in the upcoming years.
7.6 Conclusion
This chapter provides a detailed overview of integration of edge computing technology with the traditional IoT architecture which helps to discover the solution of various challenges we are facing with existing model. In edge computing based IoT architecture, processing of data, analysis of data and some extend of data storage is occurred at edge of network. That results low latency, improved data security, low bandwidth, reduce network traffic, more efficient data management, scalability, and long battery life for IoT devices. This concept will also improve the QoS (Quality of Service) of such application that needs real time data for processing and analyzing. To summarize our work, we have investigated various researchers work in healthcare sector and found that most of the researchers observed promising results by the application of edge/fog computing layer in the framework of modern healthcare systems.
References
- 1. Gubbi, J., Buyya, R., Marusic, S., Palaniswami, M., Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst., 29, 7, 1645–1660, 2013.
- 2. Rose, K., Eldridge, S., Chapin, L., The Internet of Things: An overview, in: Proc. Internet Society (ISOC), pp. 1–53, 2015.
- 3. Sethi, P. and Sarangi, S.R., Internet of Things: Architectures, protocols, and applications. J. Electr. Comput. Eng., Hindawi, 2017, 1–25, 2017, https://doi.org/10.1155/2017/9324035.
- 4. Al-Sarawi, S., Anbar, M., Alieyan, K., Alzubaidi, M., Internet of Things (IoT) communication protocols: Review. 8th International Conference on Information Technology (ICIT), IEEE, 2017.
- 5. Nieminen, J. et al., IPv6 over BLUETOOTH(R) Low Energy, IETF RFC 7668, October 2015, https://tools.ietf.org/html/rfc7668.
- 6. Zigbee Alliance, Connectivity Standards Alliance, 2021, https://zigbeealliance.org/solution/zigbee/.
- 7. Brandt, A. et al., Home automation routing requirements in low-power and lossy networks, IETF RFC 5826, April 2010, https://tools.ietf.org/html/rfc5826.
- 8. Farrell, S. (Ed.), Low-Power Wide Area Network (LPWAN) Overview, IETF RFC 8376, May 2018, https://tools.ietf.org/html/rfc8376.
- 9. Winter, T. (Ed.), et al., RPL: IPv6 Routing protocol for low-power and lossy networks, IETF RFC 6550, March 2012, https://tools.ietf.org/html/rfc6550.
- 10. Thubert, P. (Ed.), et al., IPv6 over Low-Power Wireless Personal Area Network (6LoWPAN) routing header, IETF RFC 81338, April 2017, https://datatracker.ietf.org/doc/html/rfc8138.
- 11. Vilajosana, X. (Ed.), et al., Minimal IPv6 over the TSCH mode of IEEE 802.15.4e (6TiSCH) configuration, IETF RFC 8180, May 2017, https://data‐tracker.ietf.org/doc/html/rfc8180.
- 12. Gomez, C. et al., TCP usage guidance in the Internet of Things (IoT), IETF RFC 9006, March 2021, https://datatracker.ietf.org/doc/html/rfc9006.
- 13. MQTT version 3.1.1, A. Banks and R. Gupta (Eds.), OASIS Standard, 29 October 2014, http://docs.oasis‐open.org/mqtt/mqtt/v3.1.1/os/mqtt‐v3.1.1‐os.html. Latest version: http://docs.oasis‐open.org/mqtt/mqtt/v3.1.1/mqtt‐v3.1.1.html.
- 14. OASIS Advanced Message Queuing Protocol (AMQP) Version 1.0 Part 0: Overview, OASIS Standard, 29 October 2012, http://docs.oasis‐open.org/amqp/core/v1.0/os/amqp‐core‐overview‐v1.0‐os.html.
- 15. Shelby, Z. et al., The Constrained Application Protocol (CoAP), IETF RFC 7252, June 2014, https://datatracker.ietf.org/doc/html/rfc7252.
- 16. Saint-Andre, P., Extensible Messaging and Presence Protocol (XMPP): Core, IETF RFC 6120, March 2011, https://tools.ietf.org/html/rfc6120.
- 17. Mohammed, Z.K.A. and Ahmed, E.S.A., Internet of Things applications, challenges and related future technologies. World Sci. News, 67, 2, 126–148, 2017.
- 18. Matta, P. and Pant, B., Internet-Of-Things: Genesis, challenges and applications. J. Eng. Sci. Technol., 14, 3, 1717–1750, 2019.
- 19. Minh Dang, L., Jalil Piran, Md., Han, D., Min, K., Moon, H., A survey on Internet of Things and cloud computing for healthcare. Electronics, 8, 768, 2019.
- 20. Verma, P. and Kumar, U., Smart farming: Using IoT and machine learning techniques, in: Internet of Things and machine learning in agriculture, J.M. Chatterjee, A. Kumar, P.S. Rathore, V. Jain (Eds.), pp. 3–20, De Gruyter, Berlin, Boston, 2021, https://doi.org/10.1515/9783110691276‐001.
- 21. Gill, S.S., Chana, I., Buyya, R., IoT based agriculture as a cloud and big data service. J. Organ. End User Comput., 29, 4, 1–23, 2017, https://doi.org/10.4018/JOEUC.2017100101.
- 22. Vuksanović, D., Ugarak, J., Korčok, D., Industry 4.0: The future concepts and new visions of factory of the future development. SINTEZA, International Scientific Conference on ICT and E-Business Related Research, 2016.
- 23. Ferdowsi, A., Challita, U., Saad, W., Deep learning for reliable mobile edge analytics in intelligent transportation systems. IEEE Veh. Technol. Mag., 14, 1556–6072, March 2019.
- 24. Helmi, O., Ehsankanani, Sokeh, M.A., Sepidnam, G., The challenges facing with the Internet of Things. Int. J. Sci. Study, 5, 4, 527–533, July 2017.
- 25. Alansari, Z., Anuar, N.B., Kamsin, A., Belgaum, M.R., Alshaer, J., Soomro, S., Miraz, M.H., Internet of Things: Infrastructure, architecture, security and privacy, in: 2018 International Conference on Computing, Electronics Communications Engineering (ICCECE), Aug 2018, pp. 150–155.
- 26. Mazayev, A., Martins, J.A., Correia, N., Interoperability in IoT through the semantic profiling of objects. IEEE Access, 6, 19379–19385, 2018.
- 27. Cooper, J. and James, A., Challenges for database management in the inter-net of things. IETE Tech. Rev., 26, 5, 320–329, 2009.
- 28. Constante, F., Silva, F., Herrera, B., Big data analytics in IoT: Challenges, open research issues and tools, in: Trends and Advances in Information Systems and Technologies, pp. 775–788, March 2018.
- 29. Perković, T., Damjanović, S., Šolić, P., Patrono, L., Rodrigues, J., Meeting challenges in IoT: Sensing, energy efficiency, and the implementation. Fourth International Congress on Information and Communication Technology, January 2020, pp. 419–430.
- 30. Kumar, U., Verma, P., Qamar Abbas, S., Bringing edge computing into IoT architecture to improve IoT network performance. 2021 International Conference on Computer Communication and Informatics (ICCCI), pp. 1–5, 2021.
- 31. Shi, W., Pallis, G., Xu, Z., Edge computing. Proc. IEEE, 107, 8, 1474–1481, August 2019, Digital Object Identifier 10.1109/JPROC.2019.2928287.
- 32. P. FAR-EDGE, FAR-EDGE Project H2020, 2017, Available online: http://faredge.eu/{#}/.
- 33. INTEL-SAP, IoT joint reference architecture from Intel and SAP, Technical report, INTEL-SAP, 2018, Available online: https://www.intel.com/content/dam/www/public/us/en/documents/reference‐architectures/sapiot‐reference‐architecture.pdf.
- 34. Yu, W., Liang, F., He, X., Hatcher, W.G., Lu, C., Lin, J., Yang, X., A survey on the edge computing for the Internet of Things. IEEE, 6, 6900–6919, 2018, Digital Object Identifier 10.1109/ACCESS.2017.2778504.
- 35. Intharawijitr, K., Iida, K., Koga, H., Yamaoka, K., Practical enhancement and evaluation of a low-latency network model using mobile edge computing. 41st Annual Computer Software and Applications Conference (COMPSAC), IEEE, 2017.
- 36. Sajjad, H.P., Danniswara, K., Al-Shishtawy, A., Vlassov, V., SpanEdge: Towards unifying stream processing over central and near the-edge data centers, in: Proc. IEEE/ACM Symp. Edge Comput. (SEC), Oct. 2016, pp. 168–178.
- 37. Hassan, N., Gilani, S., Ahmed, E., Yaqoob, I., Imran, M., The role of edge computing in Internet of Things. IEEE Commun. Mag., 56, 99, May 2018.
- 38. Khan, W.Z., Ahmed, E., Hakak, S., Yaqoob, I., Ahmed, A., Edge computing: A survey. Article Future Gener. Comput. Syst., 97, 219–235, February 2019.
- 39. Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H., Zhao, W., A survey on Internet of Things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J., 4, 5, 1125–1142, Oct. 2017.
- 40. Mocnej, J., Miškuf, M., Papcun, P., Zolotová, I., Impact of edge computing paradigm on energy consumption in IoT. IFAC PapersOnLine, 51, 6, 162– 167, 2018, 10.1016/j.ifacol.2018.07.147.
- 41. Hartmann, M., Hashmi, U.S., Imran, A., Edge computing in smart healthcare systems: Review, challenges and research directions. Special Issue Article Emerging Telecommun. Technol., © 2019 John Wiley & Sons, Ltd., 1–25, 2019.
- 42. Liu, L., Yang, Y., Zhao, W., Du, Z., Semi-automatic remote medicine monitoring system of miners. UbiComp/ISWC’15 Adjunct: Adjunct Proceedings of the 2015 ACM International Joint Conference on Pervasive and Ubiquitous Computing and Proceedings of the 2015 ACM International Symposium on Wearable Computers, September 2015, pp. 93–96, https://doi.org/10.1145/2800835.2800879.
- 43. Dubey, H., Yang, J., Constant, N., Amiri, A.M., Yang, Q., Makodiya, K., Fog data: Enhancing telehealth big data through fog computing. Proceedings of the ASE Big Data & Social Informatics 2015ASE BD & SI ‘15, ACM, New York, NY, USA, pp. 14:1–14:6, 2015.
- 44. Gaura, E.I., Brusey, J., Allen, M., Wilkins, R., Goldsmith, D., Rednic, R., Edge mining the Internet of Things. IEEE Sens. J., 13, 10, 3816–3825, 2013.
- 45. Bhargava, K. and Ivanov, S., A fog computing approach for localization in WSN. 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC).
- 46. Althebyan, Q., Yaseen, Q., Jararweh, Y., Al-Ayyoub, M., Cloud support for large scale e-healthcare systems. Ann. Telecommun., 71, 9, 503–515, 2016.
- 47. Bhunia, S.S., Dhar, S.K., Mukherjee, N., iHealth: A fuzzy approach for provisioning intelligent healthcare system in smartcity. 2014 IEEE 10th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), pp. 187–193, 2014.
- 48. Borthakur, D., Dubey, H., Constant, N., Mahler, L., Mankodiya, K., Smart fog: Fog computing framework for unsupervised clustering analytics in wearable Internet of Things. 2017 IEEE Global Conference on Signal and Information Processing (GlobalSIP), pp. 472–476, 2017.
- 49. Hosseini, M., Tran, T.X., Pompili, D., Elisevich, K., Soltanian-Zadeh, H., Deep learning with edge computing for localization of epileptogenicity using multimodal rs-fMRI and EEG big data. 2017 IEEE International Conference on Autonomic Computing (ICAC), pp. 83–92, 2017.
- 50. Sood, S.K. and Mahajan, I., IoT-fog-based healthcare framework to identify and control hypertension attack. IEEE Internet Things J., 6, 2, 1920–1927, 2019.
- 51. Hossain, M.S., Muhammad, G., Guizani, N., Explainable AI and mass surveillance system-based healthcare framework to combat COVID-19 like pandemics. IEEE Network, 34, 4, 126–132, July/August 2020.
- 52. Ejaz, M., Kumar, T., Kovacevic, I., Ylianttila, M., Harjula, E., Health-blockedge: Blockchain-edge framework for reliable low-latency digital healthcare applications. Sensors, 21, 2502, 2021, https://doi.org/10.3390/s21072502.
Note
- *Corresponding author: [email protected]
