17
Leveraging Threat Intelligence
One area of incident response that has had a significant impact on an organization’s ability to respond to cyberattacks is the use of cyber threat intelligence or, simply, threat intelligence. The term Cyber Threat Intelligence covers a wide range of information, data points, and techniques that allow analysts to identify attack types in their network, adequately respond to them, and prepare for future attacks. To be able to properly leverage this capability, information security analysts should have a solid foundation in the various terminologies, methodologies, and tools that can be utilized in conjunction with threat intelligence. If analysts can utilize this data, they will be in a better position to take proactive security measures and, in the event of a security incident, be more efficient in their response.
In this chapter’s discussion of cyber threat intelligence, the following key topics will be discussed:
- Threat intelligence overview
- Sourcing threat intelligence
- The MITRE ATT&CK framework
- Working with IOCs
- Threat intelligence and incident response
Threat intelligence overview
Like some terms in information security and incident response, threat intelligence is a bit nebulous. Various organizations, such as the government and academics, produce information and data that is often touted as threat intelligence. Various commercial providers also have information available, either through free or paid subscriptions, that is touted as threat intelligence. This often results in difficulty when determining what threat intelligence is and what, simply, data or information is.
A good starting point to determine what comprises threat intelligence is to utilize a definition. Here is the Gartner research company’s definition of threat intelligence:
When examining this definition, there are several key elements that need to be present for data or information to be considered threat intelligence:
- Evidence-based: This chapter will examine how evidence obtained through other processes, such as malware analysis, produces threat intelligence. For any intelligence product to be useful, it must first be obtained through proper evidence-collection methods. In this way, analysts that rely on it can be sure of its validity.
- Utility: For threat intelligence to have a positive impact on a security incident’s outcome or an organization’s security posture, it must have some utility. The intelligence must provide clarity, in terms of context and data, about specific behaviors or methods to determine whether an analyst is evaluating an incident against other incidents of a similar nature.
- Actionable: The key element that separates data or information from threat intelligence is action. Intelligence should drive action, whether that is a specific sequence of events or a specific focus area of an incident or whether a specific security control is implemented in the face of intelligence about what cyber threats the organization is most likely to face.
To see how this plays together, imagine a scenario where an incident response team at a healthcare institution is attempting to ascertain what types of attacks are most likely to occur against their infrastructure. Vague data about cybercriminals wanting to steal data is not useful. There is no specific context or information in that dataset, and the end result is that the organization cannot put that information into action.
On the other hand, say that the incident response team leverages a third-party threat intelligence provider and this third party outlines a specific criminal group by name. The provider also indicates that these groups are currently utilizing PDF files sent via email to hospital employees. The PDF files contain a remote access Trojan that is controlled from C2 servers, which are spread out in Europe. The third party also provides the team with MD5 file hashes of malware, the IP and domain addresses of the C2 servers, and, finally, the filenames most associated with the PDF document.
With this information, the incident response team can align their security controls to prevent PDF attachments from opening in emails. They can also utilize tools to search their infrastructure to determine whether an infection has already occurred. Finally, they may be able to configure their event management solution in order to alert the team if any host within the network attempts to communicate with the C2 server.
The major difference between these two scenarios is that the latter scenario drives actions within the organization. In the first scenario, the information was so vague and useless that the organization was left no better off. In the second scenario, the team could execute specific actions to either prevent an adverse condition or be better prepared to respond to one.
Threat intelligence is a response to the increased complexity and technical skill of cyber threat actors. The focus of threat intelligence is on the following threat actor groups:
- Cybercriminals: Organized and technically skilled, cybercriminals have been responsible for a variety of financial crimes against banking, retail, and other organizations. The motive for these groups is purely mercenary, and their goal is to acquire data that can be monetized. For example, attacks against retailers such as Home Depot and Target involved the theft of credit card data with the intent of selling numbers on the dark web or other black markets.
- Hacktivism: Groups such as Anonymous and the Idlib Martyrs’ Brigade are hacker groups that take on large businesses, governments, and even religious institutions to further a political cause. Penetrating networks to obtain confidential data for disclosure or conducting denial-of-service attacks is done as part of an overall political versus monetary objective.
- Cyber espionage: Nation-states such as the United States, Russia, China, Iran, and North Korea continually engage in espionage activities involving penetrating networks and obtaining intelligence. One of the most well-known cyberattacks, the Stuxnet virus, was reportedly perpetrated by the United States and Israel.
Another key element to understanding threat intelligence is the concept of Advanced Persistent Threat (APT). The term APT has been around for approximately a decade and is used to describe a cyber threat actor whose capability and motivation go far beyond that of a cybercriminal or cyber vandal. APT groups often target organizations for an intended purpose with a clear objective in mind and over a long period of time. As the term APT describes, these groups have the following characteristics:
- Advanced: APT threat actors have advanced skills. These skills often involve intelligence-gathering skills that exceed what can be obtained through open source methods. This includes sources such as Imagery Intelligence (IMINT), which includes pictures available through sites such as Google Earth. Signals Intelligence (SIGINT) is intelligence gathered through the compromise of voice and data communications that use telephone infrastructure, cellular data, or radio signals. Finally, APT groups can leverage Human Intelligence (HUMINT) or gather intelligence from interacting with human sources. Further, these groups can not only utilize advanced network penetration tools, but they are also adept at finding zero-day vulnerabilities and crafting custom malware and exploits that specifically target these vulnerabilities.
- Persistent: APT threat actors are focused on a clearly-defined objective and will often forgo other opportunities to get closer to achieving their objective. APT threat actors will often go months or even years to achieve an objective through the intelligent leveraging of vulnerabilities and continuing at a pace that allows them to bypass detection mechanisms. One of the key differentiators between APT threat actors and others is the intention to stay within the target network for a long period of time. While a cybercriminal group will stay long enough to download a database full of credit card numbers, an APT group will maintain access within a network for as long as possible.
- Threat: To organizations that face APT groups, they are most definitely a threat. APT threat actors conduct their attacks with a specific objective and have the necessary infrastructure and skillset to attack targets such as large corporations, the military, and government organizations.
Threat intelligence is a wide field of study with many elements that are tied together. In the end, threat intelligence should drive action within an organization. What that action may be is often decided after careful evaluation of the threat intelligence. This involves understanding the type of threat intelligence being reviewed and what advantage each of those types provides the organization.
Threat intelligence types
When discussing the wide variety of information types and datasets that constitute threat intelligence, they often fall into one of three main categories:
- Tactical threat intelligence: This is the most granular of the three threat intelligence categories. Information in this category involves either Indicators of Compromise (IOCs), Indicators of Attack (IOAs), or Tactics, Techniques, and Procedures (TTPs):
- IOCs: An IOC is an artifact observed on a system that is indicative of a compromise of some sort. For example, a C2 IP address or an MD5 hash of a malicious file are both IOCs.
- IOAs: An IOA is an artifact observed on a system that is indicative of an attack or an attempted attack. This can be differentiated from an IOC, as an IOA does not indicate that a system was compromised but rather attacked due to indicators left by an adversary attacking a system. An example may be connection attempts left in a firewall log that are indicative of an automated port scan utilizing Nmap or another network scanning tool.
- TTPs: Humans are creatures of habit and, as a result, cyber attackers often develop a unique methodology for how they attack a network. For example, a cybercriminal group may favor a social engineering email that has an Excel spreadsheet that executes a remote access Trojan. From there, they may attempt to access the credit card point of sale (POS) device and infect it with another piece of malware. How this group executes such an attack is their TTPs.
- Operational threat intelligence: The past decade has seen more and more coordinated attacks that do not just target one organization but may target an entire industry, region, or country. Operational threat intelligence is data and information about the wider goal of cyberattacks and cyber threat actors. This often involves not just examining the incident response team’s own organization but examining how cyber threat actors are attacking the larger industry. For example, in returning to a previous example where incident responders at a healthcare institution were preparing for an attack, wider knowledge of what types of attacks are occurring at similar-sized and staffed healthcare institutions would be helpful in aligning their own security controls to the prevalent threats.
- Strategic threat intelligence: Senior leadership such as the CIO or CISO often must concern themselves with the strategic goals of the organization alongside the necessary controls to ensure that the organization is addressing the cyber threat landscape. Strategic threat intelligence examines trends in cyberattacks, what cyber threat actors are prevalent, and what industries are major targets. Other key data points are changes in technology that a threat actor or group may leverage in an attack.
The best use of threat intelligence is to understand that each one of these types can be integrated into an overall strategy. Leveraging internal and external threat intelligence of all three types provides key decision makers with an understanding of the threat landscape, managers with the ability to implement appropriate security controls and procedures, and analysts with the ability to search for ongoing security issues or to prepare their own response to a cyberattack.
The Pyramid of Pain
A useful construct for describing the various types of IOCs and IOAs that an adversary can leverage and their ability to modify them during an attack is the Pyramid of Pain. This construct, developed by David Bianco, describes the relationship between the IOCs, IOAs, and TTPs that an attacker makes available through observations by the defender and the attacker’s ability to change those indicators. The following diagram shows the relationship between the various indicators and the work effort necessary to modify them to bypass security controls:

Figure 17.1 – The Pyramid of Pain
For example, an attacker may have crafted a piece of malware that spreads through lateral movement via the Windows SMB protocol. To bypass traditional signature-based malware prevention tools, the attacker uses a polymorphic virus that changes its hash every time it is installed. This change allows the piece of malware to bypass this control. Other indicators, such as network or host artifacts, are harder to change for the attacker and, as a result, responders have a greater chance of successfully stopping an attack by aligning their security controls at the top layers of the pyramid.
From a threat intelligence perspective, the Pyramid of Pain allows responders to align threat intelligence requirements with what would be useful from a long-term strategy. Having detailed information and intelligence about the TTPs in use by threat actors will provide more insight into how the threat actor operates. Lower-level indicators such as the IP addresses of C2 servers are useful, but responders do need to understand that these can easily be changed by the adversary.
The threat intelligence methodology
Threat intelligence goes through a feedback cycle to keep pace with an ever-changing environment. While several methodologies can place context around this challenge, one that is often utilized is the cycle of intelligence used by the US Department of Defense. This cycle provides the framework and a starting point for organizations to incorporate threat intelligence into their operations:

Figure 17.2 – The intelligence cycle
The phases are explained as follows:
- Direction: Decision makers, such as the CISO, information security personnel, or incident response analysts, set down what threat intelligence is required. In determining the requirements for intelligence, it is good practice to identify the users of each of the types of threat intelligence previously discussed. For example, a CISO might want threat intelligence about what trends in cyberattacks against hospitals are anticipated in the next year. An incident response analyst may require intelligence on what individual IOCs of malware are being seen in other healthcare institutions. The organization may also start by looking at what critical systems and applications are in use, as well as the critical data they are trying to protect. Another good starting point is if an organization already has some information about what types of cyber threats they may face.
- Collection: In the collection stage, the organization obtains the data and information from its sources. In terms of cyber threat intelligence, this can come from government organizations such as government-sponsored CERTs or through commercial organizations that sell curated and analyzed threat intelligence. Finally, there are a great many Open Source Intelligence (OSINT) feeds that an organization can leverage. For example, malware sites such as VirusTotal and Malware Bazaar make IOCs and complete examples available to the larger cyber security and response communities. There are also providers such as AlienVault that provide a full platform that can be searched for IOCs. Commercial entities will also make some threat intelligence available to the community. OSINT is extremely valuable for organizations that are just starting out and need to show the value of threat intelligence without breaking the bank. Additionally, OSINT can also serve as a significant portion of an organization’s overall intelligence collection.
- Processing: The sheer amount of intelligence that an organization may obtain can be staggering. During the processing stage, the organization takes the raw data, evaluates it, determines the relevance and reliability of the data, and then collates it for the next step.
- Analysis: During the analysis stage, the organization evaluates the data that has been processed and combines it with other data from other sources. From here, it is interpreted, and the finished product can be deemed curated or properly evaluated threat intelligence.
- Dissemination: The newly curated threat intelligence is then sent to the various users within the organization for use.
The cyclical nature of this methodology ensures that feedback is part of the process. Those analysts involved in the collection and processing should make sure that they receive feedback on the relevance and veracity of the intelligence that is disseminated. From here, they would be able to tune the intelligence product over time. This ensures the highest level of relevancy and fidelity of intelligence consumed by end users.
Now that we have covered the foundational elements of threat intelligence, let’s look at how to source this data.
Sourcing threat intelligence
There are three primary sources of threat intelligence that an organization can leverage. Threat intelligence can be produced by the organization in an internal process, acquired through open source methods, or, finally, through third-party threat intelligence vendors. Each organization can utilize its own internal processes to determine what its needs are and what sources to leverage.
Internally developed sources
The most complex threat intelligence sources are those that an organization internally develops. This is due to the infrastructure that is needed to obtain the individual IOCs from malware campaigns and TTPs from threat actors. To obtain IOCs, the organization can make use of honeypots or other deliberately vulnerable systems to acquire unique malware samples. They will also need to have the expertise and systems available to not only evaluate suspected malware but reverse engineer it. From there, they would be able to extract the individual IOCs that can then be utilized.
Other systems such as SIEM platforms can be utilized to track an attacker’s TTPs as they attempt to penetrate a network. From here, a Security Operations Center (SOC) analyst can record how different attackers go about their penetration attempts. With this information, the organization can build a profile of specific groups. This can aid in the alignment of security controls to better prevent or detect network intrusions.
Developing threat intelligence internally requires expertise in areas such as malware analysis, network, and host-based forensics. Furthermore, the infrastructure required is often cost prohibitive. As a result, organizations are often forced to rely on third-party providers or what is shared openly among other organizations.
Commercial sourcing
An alternative to internal sourcing is to contract a threat intelligence vendor. These organizations utilize their personnel and infrastructure to acquire malware, analyze attacks, and conduct research on various threat groups. Commercial threat intelligence providers will often process the threat intelligence so that it is tailored to the individual client organization.
Often, commercial vendors provide SIEM and SOC services for a variety of clients utilizing a common SIEM platform. From here, they can aggregate samples of malware and attacks across various enterprises that span the entire world. This allows them to offer a comprehensive product to their clients. This is one of the distinct advantages of utilizing a commercial service. This is in addition to the cost savings that come from transferring the cost to a third party.
Open source intelligence
One sourcing area that has become quite popular with organizations of every size is OSINT providers. Community groups, and even commercial enterprises, make threat intelligence available to the larger cyber community free of charge. Groups such as SANS and US-CERT provide specific information about threats and vulnerabilities. Commercial providers such as AlienVault provide an Open Threat Exchange (OTX) that allows a user community to share threat intelligence such as IOCs and TTPs. Other commercial organizations will provide whitepapers and reports on APT groups or strategic threat intelligence on emerging trends within the information security industry. Depending on the organization, OSINT is often very useful and provides a low-cost alternative to commercial services.
The widespread use of OSINT has led to various organizations creating methods to share threat intelligence across organizations. Depending on the source, the actual way that an organization can obtain threat intelligence is dependent on how it is configured.
While not a completely exhaustive list, the following are some of the formats of cyber threat OSINT that are available:
- OpenIOC: OpenIOC was first developed so that Mandiant products could ingest threat intelligence and utilize it to search for evidence of compromise on the systems analyzed. It has evolved into an XML schema that describes the technical IOCs that an incident responder can use in determining whether a system has been compromised.
- STIX: The Structured Threat Information Expression (STIX) is a product of the OASIS consortium. This machine-readable format allows organizations to share threat intelligence across various commercial and freeware threat intelligence aggregation platforms.
- TAXII: The Trusted Automated Exchange of Intelligence Information (TAXII) is an application layer protocol that shares threat intelligence over HTTPS. TAXII defines an API that can be utilized to share threat intelligence in the STIX format.
- VERIS: The Vocabulary for Event Recording and Incident Sharing (VERIS) is a comprehensive schema for standardizing the language of cybersecurity incidents. The one key problem that the VERIS schema attempts to solve is the lack of a standard way to document security incidents. VERIS provides a structure in which organizations have a defined way to categorize the variety of attacks that may occur. The VERIS schema also serves as the collection point of data provided by organizations that is incorporated into the Verizon Data Breach Study.
With a variety of intelligence sources available, one challenge that presents itself is the ability of organizations to aggregate, organize, and utilize threat intelligence. In the next section, a discussion of threat intelligence platforms will provide insight into solving these issues.
The MITRE ATT&CK framework
Looking back at the Pyramid of Pain discussion in the previous section, we can see at the very top are the TTPs that the adversary uses. Modifying these requires additional resources and time on the adversary’s end. Focusing on TTPs from a threat intelligence and mitigation perspective also provides defenders better protection as detections are not tied to an indicator such as a domain name or IP address, which can be easily modified.
The MITRE Corporation has created the Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) knowledge base, available at https://attack.mitre.org/. This knowledge base incorporates adversary tradecraft, tactics techniques, and adversary behaviors that run through the various stages of a cyberattack. It was started in September 2013, and, as of the time of writing, is now on its ninth version.
The ATT&CK knowledge base started out focusing on the Windows operating system but, over its lifetime, has incorporated malicious activity directed at macOS and Linux as well. MITRE has also included as part of the knowledge base pre-attack techniques such as resource development and reconnaissance. Finally, MITRE recently included tactics and techniques in use by adversaries to compromise mobile devices.
This behavioral model has three core components. The first of these components is Tactics. The fourteen separate Tactics represent the adversary’s goal during the sequence of attack. For example, let us look at the Persistence tactic as defined by MITRE in the following screenshot:
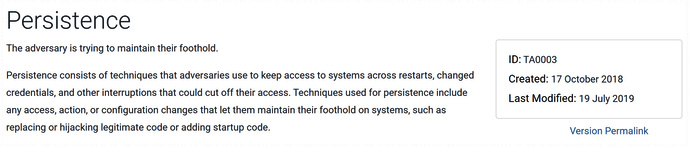
Figure 17.3 – MITRE ATT&CK Persistence
MITRE defines persistence as the adversary trying to maintain their foothold. This definition is further expanded to address the next component, techniques. Techniques are the means and methods that an adversary uses to achieve the overall tactical goal. For example, adversaries can make use of boot or logon scripts to maintain persistence as the MITRE ATT&CK technique T1037 indicates in the following screenshot:

Figure 17.4 – MITRE ATT&CK technique T1037
The technique description provides not only a definition but other key resources as well. For example, the Data Sources field shows incident responders and digital forensic analysts’ potential sources of evidence to confirm the use of the technique. The Common Attack Pattern Enumeration and Classification Identification (CAPEC) ID cross-references the MITRE ATT&CK framework with the MITRE CAPEC. The CAPEC, available at https://capec.mitre.org/, provides details of adversary attack patterns.
Many of the techniques in the MITRE ATT&CK framework also contain sub-techniques. These sub-techniques provide a more granular look at the various methods and tools the adversary uses in the execution of the technique. For example, if we drill down further, we see the entry ID T1037.001, as in the following screenshot:
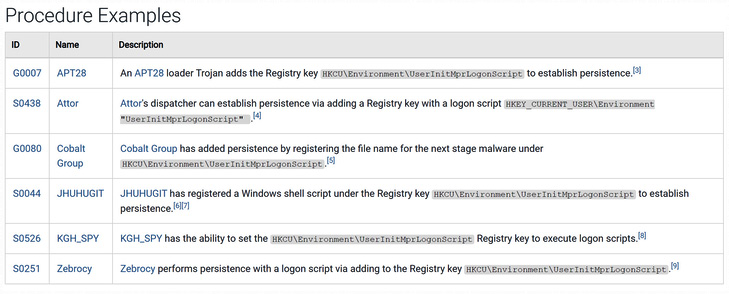
Figure 17.5 – MITRE ATT&CK T1307.001 procedure example
This provides real-world context to the tactics and techniques that threat actors use. In this case, for example, we see that the threat group APT28 uses a Trojan and adds the HKCUEnvironmentUserInitMprLogonScript registry key to maintain persistence on a system.
Outside of the tactics and techniques, the MITRE ATT&CK framework also serves as a clearing house of sorts for both malicious tools and threat actor groups. For example, we identified that APT28 utilizes a specific tool to maintain persistence, but we may not even know who or what APT28 is. Pivoting off the link in the techniques section, we see that the MITRE ATT&CK framework contains an overview of the threat actor, its origins, aliases, and a review of the high-profile attacks it has carried out.

Figure 17.6 – APT28 profile
When discussing aliases, there are several challenges with tying tactics and techniques to groups. First, groups may pop up and then disappear after a campaign. Individuals may shift. Finally, threat intelligence researchers such as FireEye and RecordedFuture have their own nomenclature for describing groups. As we saw in the previous example, APT28 could be tied to other groups as well. MITRE provides a more detailed breakdown of the group and its associated designations.

Figure 17.7 – APT28 Associated Group Descriptions
Drilling down into the dossier, there is a list of the tactics and techniques that the group has been known to use when carrying out attacks.

Figure 17.8 – APT28 Techniques Used
In addition to the tactics and techniques that the APT28 group has been shown to use, MITRE also includes specific tools, such as exploit frameworks, malware, and exploits, such as the use of credential harvesting tools, as shown in the following screenshot:
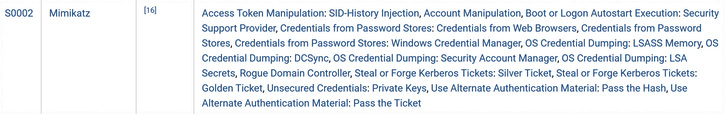
Figure 17.9 – Mimikatz tool use
You might have already surmised that we can pivot off the Mimikatz entry to get a better understanding of the tool itself. If you had that thought, you would be correct. Clicking on Mimikatz shows an overview of the tool.
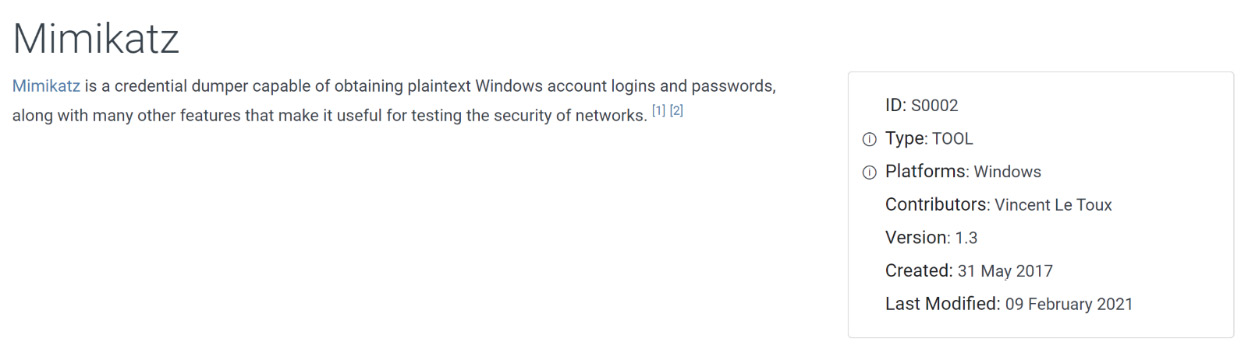
Figure 17.10 – Mimikatz tool profile
Aside from an easily searchable interface that allows threat intelligence professionals to cross-reference tools, techniques, and tactics, the framework is meticulously footnoted. The source material for the information contained can be readily searched and accessed via hyperlinks, saving time and resources if an analysis requires a review of the source material.
The ATT&CK framework also includes a Navigator for easily viewing the various tactics, techniques, and tools that are included. The Navigator can be accessed at the URL https://mitre-attack.github.io/attack-navigator/v2/enterprise/. The site lists the tactics in the top row with the corresponding techniques in the columns as seen in the following screenshot:

Figure 17.11 – ATT&CK Navigator
The Navigator also has several controls that allow the user to interact with the tool. In this case, Figure 17.12 shows the various controls available:

Figure 17.12 – ATT&CK Navigator controls
For example, we will use the multiselect feature to highlight the techniques used by the group APT28. First, click on the hamburger icon with the plus sign under selection controls, as shown in Figure 17.13. This will produce the following menu:

Figure 17.13 – ATT&CK Navigator multiselect feature
The drop-down menu contains intelligence on threat groups and software that are contained within the ATT&CK framework. Scroll down the threat groups to APT and then click Select. This will put a border around the techniques associated with the group. Next, click on the color palate under layer controls:
Figure 17.14 – ATT&CK Navigator palate control
The palate allows you to change the background colors of the various techniques. In this case, we are only examining one layer so, in the Low value setting, change 0 to 1 to highlight the APT28 techniques in red.
The next step is to set the scoring to show the APT28 techniques. Access the scoring menu by clicking the bar chart icon under technique controls:

Figure 17.15 – ATT&CK Navigator technique control score
Enter the number 1 under score and then click Enter. This will then highlight the techniques in red. At this point, you can explore the Navigator by right-clicking on a specific technique and clicking view technique. This will bring you to the specific technique’s page as we saw earlier.
The final feature we will look at right now is the ability to download the techniques associated with APT28. Under the layer controls, you can download the file as a JSON file using the down-arrow icon, a Comma Separated Value (CSV) document via the graph icon, and finally, an image via the camera icon.

Figure 17.16 – ATT&CK Navigator capture options
Clicking on the camera icon will open a second tab in Navigator. At the far right, a copy of the image can be downloaded.
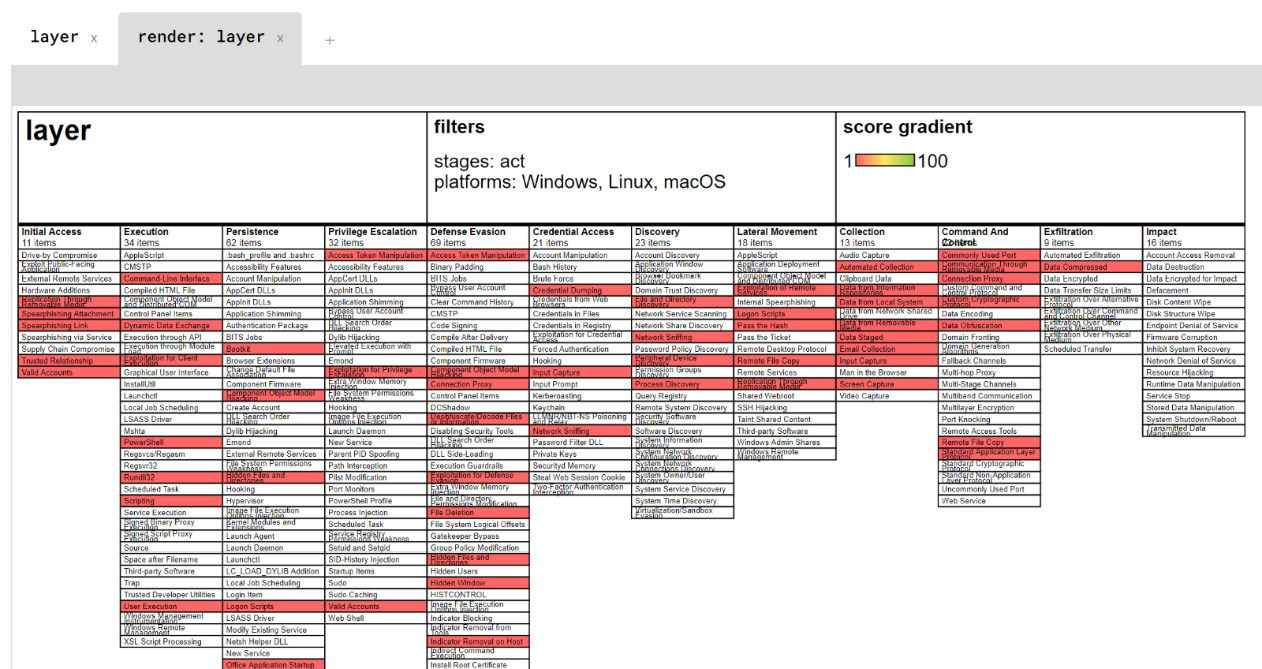
Figure 17.17 – ATT&CK Navigator APT28 tactics and techniques
The ATT&CK framework is an excellent resource for gaining insight into the tactics, techniques, and tools in use by threat actors. Since its inception, this framework has been tied into organizations’ threat intelligence and incident response reporting, quickly turning the framework into the rubric by which organizations define their observations.
Working with IOCs and IOAs
A common mistake that is often made by organizations that start the process of leveraging threat intelligence is to subscribe to a few commercial or open source feeds and turn them on. This approach will see the enterprise quickly become inundated with data. Most of this data will be unusable for the organization. The reality is that analysts and other stakeholders should work through crafting what data is relevant to their organization and use sources that can provide the best data to fit that relevance.
In this case, we will focus on OSINT sources. There are several commercial organizations, such as CrowdStrike and AlienVault, that make IOCs and IOAs available to the community. Other sites are strictly focused on servicing the cybersecurity community without a commercial component. The following are some resources that analysts can leverage:
- AlienVault Open Threat Exchange (OTX): This site, available at https://otx.alienvault.com/, aggregates indicators and threat intelligence reports from commercial enterprises such as Cisco Talos and Palo Alto Unit 42 as well as independent researchers from around the world. This intelligence is aggregated and allows users to search on keywords, IOCs, and even specific threat actors.
- VirusTotal: One of the key sources of IOCs is VirusTotal. The site, https://www.virustotal.com/, and the associated data are owned and operated by Google and it is arguably the go-to spot for analysts and responders when it comes to intelligence about malware.
- Hybrid Analysis: Hybrid Analysis, available at https://www.hybrid-analysis.com/, is operated by CrowdStrike. A unique feature of antivirus and EDR providers is that they often have an extensive collection of malware IOCs due to their presence in a range of organizations. Hybrid Analysis is a combination of a malware sandbox and an IOC database that allows users to both analyze samples and search on existing samples.
- MalwareBazaar: Another malware IOC resource that is handy is MalwareBazaar. What the site lacks in bells and whistles, it makes up for in the sheer number of samples and IOCs available. The site, https://bazaar.abuse.ch/, is part of the abuse.ch set of subdomains that provide IOCs related to botnets and malware.
These four sites only scratch the surface of what is available for IOCs but do provide a solid foundation for a focused collection plan. All four of these sites provide community accounts with minimum functionality that is still very useful. They also include searching for keywords, IP addresses, and file hashes. The final feature that is of interest to analysts is the API, which allows for querying the databases through scripts or through other programmatic means. We will look at how this feature can be leveraged later in the chapter.
To access these sites, the analyst only must provide an email address and password. One technique that minimizes stress is to create an email address devoted strictly to threat intelligence sites. Many of these sites will send notifications, sometimes dozens of alerts, a day. Having an email account that is strictly for accessing these sites and aggregating alerts will remove the need to continually clean up a primary email account.
Awesome threat intelligence sources
There are sites that specifically aggregate sites specifically dedicated to providing IOCs and IOAs to the wider community. There are also GitHub repositories such as https://github.com/hslatman/awesome-threat-intelligence that can be used to craft sources for collection. Again, proceed with caution and do not try to collect the ocean.
Now that we have some sources outlined, let’s look at a sample workflow where IOCs are obtained from a threat intelligence site and put into use. In this case, an analyst wants to take threat intelligence related to the threat actor HAFNIUM and search through logs or other evidence for indications that their systems have been compromised.
In this case, we will leverage the AlienVault OTX. A keyword search for HAFNIUM brings up several results. In this case, we will look at the following hit: https://otx.alienvault.com/pulse/6127557db7ec02a119d8c23d.
Navigating to the URL reveals the references shown in the following screenshot:

Figure 17.18 – HAFNIUM intelligence sources
The IOCs are listed below the references:

Figure 17.19 – HAFNIUM IOCs
To make use of these IOCs, we need to download them. In the top-right corner of the page is the Download button. This allows the user to download in a variety of formats, such as STIX, OpenCTI, and CSV files. In this case, download a CSV file.

Figure 17.20 – IOC download
Once downloaded, navigate to the site https://cti.uncoder.io/. This site, provided to the community by SOC Prime, will convert the IOCs contained in the download into a SPLUNK query. In this case, click Upload IOCs and navigate to the AlienVault CSV file that was downloaded:

Figure 17.21 – CTI Uncoder upload
Now that the IOCs have been downloaded, we can use the Uncoder CTI to build a SPLUNK query to search log files for any matching domain names associated with HAFNIUM. In this case, under Generate Queries by IOC Types, select Domain. Under Query Platform, select SPLUNK. The rest of the settings can be left as their default. Click Generate and the following SPLUNK query is generated:
(dest_host="api.onedvirer.xyz" OR dest_host="rawfuns.com" OR dest_host="yolkish.com" OR dest_host="back.rooter.tk" OR dest_host="lab.symantecsafe.org" OR dest_host="mm.portomnail.com" OR dest_host="ns.rtechs.org" OR dest_host="p.estonine.com" OR dest_host="soft.mssysinfo.xyz" OR dest_host="www.averyspace.net" OR dest_host="www.komdsecko.net")
This query can then be run against the analyst’s dataset to find any matching hits.
This is a simple workflow but shows how the raw IOCs or IOAs provided by community or OSINT sources can be leveraged for queries and other investigative tasks. Building on that concept, we will examine how IOCs can be leveraged specifically for incident response and digital forensics as part of the investigation.
Threat intelligence and incident response
During an investigation, the CSIRT or analysts may come across a situation where an incident investigation seems to have stalled. This could be because the analysts know something is wrong or have indicators of a compromise but no concrete evidence to point in a specific direction. Threat intelligence can be leveraged by analysts to enhance their ability to discover previously undiscovered evidence.
Autopsy
Many of the forensic tools that are available can ingest threat intelligence to aid incident response analysts. For example, disk forensics platforms, discussed in Chapter 11, can ingest hashes from threat intelligence feeds to search for IOCs. In addition to commercial disk forensics tools, the Autopsy platform can conduct searches against a hash set. For example, we can import the MD5 hashes from the HAFNIUM Pulse that we examined in the previous section. In this case, we will extract the MD5 hashes from the CSV file that was downloaded, as seen in the following screenshot, and input that into Autopsy.
Figure 17.22 – IOC CSV file
From here, the hash values can be loaded into Autopsy:
- First, open Autopsy, and from the home page, click on Tools and then Options. Find the Hash Sets icon and click on it:

Figure 17.23 – Autopsy Hash Sets upload

Figure 17.24 – Create Hash Set
- Enter a name for the hash set database. In this case, HAFNIUM is a good selection as the hash files are associated with exploits leveraging that vulnerability. Click Save As, and an Explorer window will open. This provides a location for the database that will be created. It is fine to leave the default location. Click on OK.
- In the next window, click on Add Hashes to Database. A window will appear that allows for the input of hash values. Copy the MD5 hashes from the HAFNIUM intelligence report and paste them into the window:

Figure 17.25 – Hash values
- Click OK and the following window should appear after the hash values have been added successfully. Click OK:
Figure 17.26 – Hash set upload
- On the final screen, click Apply and then OK. At this point, the hashes have been loaded into the database.
This capability allows analysts to search through disk images for matching hashes. This is a much more efficient way to search for evidence than attempting to find the files through other methods. Autopsy also allows different databases depending on the incident. This ability to continually feed updated information allows analysts to find evidence of a new type of compromise from an event from a week or two ago that would have gone undetected if using traditional searching.
Maltego
One tool that is useful for searching a variety of intelligence sources related to an IOC is Maltego. This tool utilizes transforms that connect the platform to third-party sources such as VirusTotal. This allows the analyst to search various sources for additional context on an indicator such as a file hash, IP address, or domain. There are several pricing tiers, but Paterva, the company that has developed Maltego, makes a community edition available at https://www.maltego.com/downloads/.
Once it's downloaded, you will need to provide an email address and password to configure an account. Once installed and signed in, the following screen will appear:

Figure 17.27 – Maltego GUI
The right side of the GUI is the Transform Hub. This is where the user can download and configure the specific tools that are used to pull data from various sources. In this case, we select the VirusTotal (Public API) transform. It is worth noting that the community edition has limited transforms. This is sufficient for testing and some limited research but if you need more information, consider purchasing a licensed copy. Hovering the cursor on the VirusTotal transform brings up the following window:
Figure 17.28 – VirusTotal transform
A dialog box will appear, click Yes to install the transform. The following window will appear:
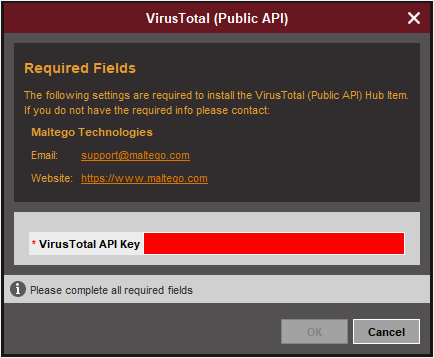
Figure 17.29 – VirusTotal transform API
The VirusTotal transform requires an API key from VirusTotal. This can be obtained by creating an account on VirusTotal. The API key is free and allows Maltego to run the queries from VirusTotal. Once the API key is entered, click OK. You can repeat this process for any additional transforms. For example, AlienVault OTX also has a transform that is useful when conducting incident investigations.
Now that we have some transforms installed, we can start using Maltego. Click on the upper left-hand corner circle and click New. This will open a new graph as shown in the following screenshot:
Figure 17.30 – Maltego New Graph
On the left-hand side of the GUI is Entity Palette. These are the specific types of IOCs that Maltego can search and graph for the user. In this case, we will look at a simple IP address, 138.68.79.195, to determine what relationship it has to any other indicators. Click on Ipv4 Address in Entity Palette and drag it into the center screen, then cut and paste the IP address. Right-click on the entity, and the Run Transforms window will open:
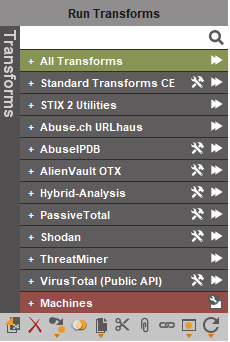
Figure 17.31 – Run Transforms
For this example, we will look at running the AlienVault OTX transform. Click the right arrow. The transform will query AlienVault OTX for any related entities or IOCs related to the IP address:

Figure 17.32 – IP address graph
In this case, the transform found several domain registrations, an IP address, URLs, and a file hash associated with malware. The same process can be repeated for the hash. Here, the VirusTotal transform is run against the malware entity, which indicates that the IP address is associated with the post-exploitation tool Cobalt Strike:

Figure 17.33 – VirusTotal hash return
Maltego is a useful tool for uncovering the relationship between IOCs and the larger adversary infrastructure. As we saw, a simple IP address that may have been found in a review of firewall logs can be turned into a profile of the adversary, their infrastructure, and their tools by leveraging OSINT sources. Along with being useful in uncovering links between IOCs, OSINT can be used to detect the presence of hidden malware or other exploits using the YARA rules discussed in the last chapter.
YARA and Loki
In the previous chapter on malware, we looked at the pattern-matching tool YARA, including how to create rules. In this example, we are going to look at applying a wide range of YARA rules through a scanner that will attempt to identify files or executables that match the pattern.
A good tool for scanning systems with YARA rules is Loki, a simple IOC scanner available at https://github.com/Neo23x0/Loki. This lightweight platform allows incident response analysts to scan folders, files, or even entire volumes for IOCs such as YARA rules, known bad file hashes, filename IOCs, and known C2 servers. Out of the box, Loki has an extensive library of IOCs that are updated regularly. To get started with Loki, take the following steps:
- To check a system volume for specific IOCs, download and extract Loki to a USB device or to a local system. Open the loki folder and the following files are found:
Figure 17.34 – Loki files
- Loki must be updated with the most current IOCs, so right-click on loki-upgrader and run as administrator. The upgrader will run, updating both the executable and the signature files. Once completed, the updater will close.
- Navigate back to the Loki file and a new file called signature-base will have been added:
Figure 17.35 – The signature-base file
This folder contains all of the IOCs that Loki can search for a volume against. This also allows analysts who create their own YARA rules to load them into the file as well, giving them the ability to customize the solution.
- To run a scan of a system, right-click on the loki.exe application and run it as an administrator. This will start the executable and open the following window:
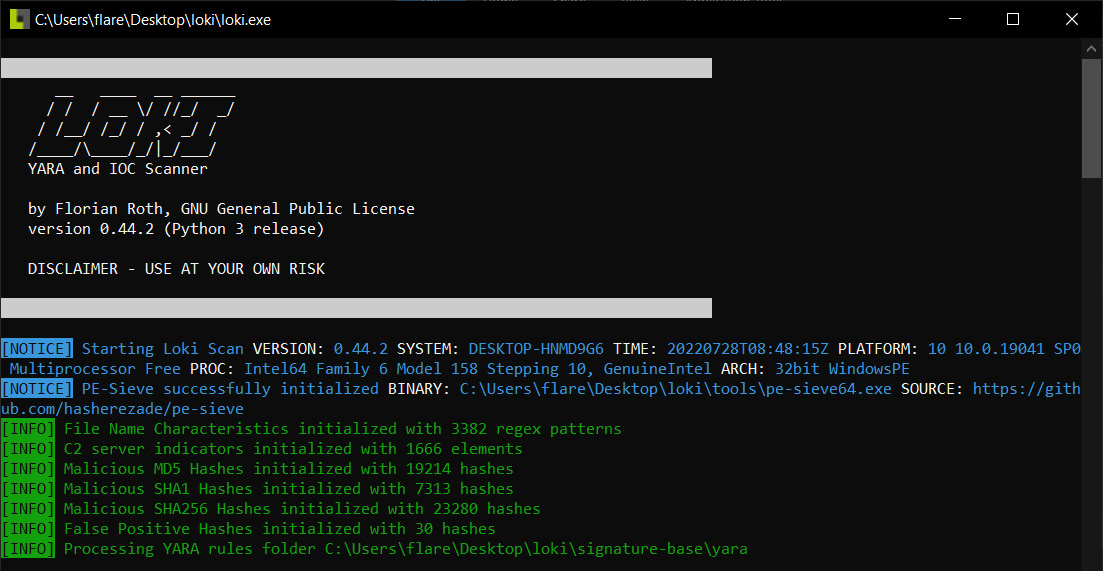
Figure 17.36 – Loki scan
- After the ruleset is updated, Loki will then begin searching the volume for any matching patterns or IOCs:

Figure 17.37 – Loki scan output
- Any matching rules will show up in red. In this case, Loki has hit on the tool Nmap, which is often used to scan internal networks for both legitimate and malicious reasons:

Figure 17.38 – Loki scan hit
From here, the analyst can take note of any hits and conduct an examination later. Another key feature is that Loki can be deployed on multiple systems as part of the triage of systems that have possibly been infected with a new strain of malware. For example, an incident response analyst may be able to search for the IOC of the Petya ransomware attack using YARA rules taken from a threat intelligence provider, such as ReversingLabs, which includes a download of the YARA rules from GitHub: https://github.com/reversinglabs/reversinglabs-yara-rules.
From here, the YARA rules can then be fed into Loki or another platform and utilized to triage suspected systems.
The number of tools that an incident response analyst can bring to bear is increasing every day. These include commercial tools and freeware tools that integrate a variety of threat intelligence feeds and functionality. These tools can be used proactively to detect and alert as well as investigate an incident in progress. CSIRTs should make a concerted effort to examine these tools and integrate them into their processes. Doing so will aid them in detecting and efficiently investigating an incident.
Summary
Sun Tzu’s The Art of War includes the strategic concept of knowing your adversary and knowing yourself. Through this, you can be confident in your ability to prevail in the contest. Threat intelligence has quickly become a critical component of an organization’s proactive security controls, as well as an important factor in its ability to respond to an incident. This chapter examined the emerging techniques and methodologies of cyber threat intelligence and the sources, technology, and methods to put this data to use.
To move forward, organizations looking to leverage the advantages that threat intelligence provides must first understand the threat. From there, they can define their requirements and begin the intelligence process. Finally, by integrating their toolset to utilize threat intelligence, they can position themselves to have more effective proactive controls and the ability to respond efficiently. While threat intelligence may not remove the fear of an adversary entirely, it allows organizations a good deal more ammunition to combat today’s threats. Threat intelligence also serves an important function when looking at the proactive practice of identifying threats in an environment through threat hunting, which is the subject of a later chapter. Before we get into hunting, we are going to examine a specific type of threat: ransomware.
Questions
- What is not a key element of intelligence?
- Indicator of compromise
- Utility
- Evidence-based
- Actionable
- Which of the following is part of the cyber kill chain?
- Phishing
- Weaponization
- Malware
- IOC
- TTPs describe actions taken by adversaries during a network attack.
- True
- False
- Which is not a threat intelligence type?
- Operational
- Strategic
- Defense
- Tactical
Further reading
Refer to the following for more details on the topics covered in this chapter:
- Operationalizing Threat Intelligence: https://www.packtpub.com/product/operationalizing-threat-intelligence/9781801814683
- What Is Threat Intelligence? Definition and Examples: https://www.recordedfuture.com/threat-intelligence-definition/Threats/Vulnerabilities: https://www.sans.org/reading-room/whitepapers/threats/paper/38790
- Yara GitHub repository: https://github.com/VirusTotal/yara
- Suricata: https://suricata-ids.org/
- The Zeek Network Security Monitor: https://www.zeek.org/
- Snort: https://www.snort.org/
