Chapter 2
Security
Introduction
In a world where cyberattacks are escalating in both frequency and sophistication, security should be top of mind for every IT organization. The increasing complexity of applications and their supporting infrastructures, whether on premises or in the public cloud, only compounds the concerns surrounding IT security. Organizations must ensure that security is not an afterthought or a bolt-on to any given process or service but rather baked into their foundations from the beginning. Security is paramount in the design, development, integration, and testing of the Intersight platform. Intersight users can rest assured knowing that Intersight complies with the Cisco Secure Development Lifecycle guidelines (http://cs.co/9009HkkPd) and Cisco’s strict security and data handling standards (http://cs.co/9002HkkPq) in order to keep Intersight environments, users, and data safe. Furthermore, Intersight’s centralized model, secure connectivity, granular access control, and integrated access to current security updates and advisories provide unique security advantages beyond those that traditional operations practices can achieve.
This chapter discusses the importance of security in every human and device interaction with Intersight and explains how Intersight ensures secure practices at every level of the platform and the targets it manages.
Connectivity
Each of the nearly 1 million devices connected to the Intersight cloud uses Transport Layer Security (TLS) with restricted ciphers on port 443 utilizing Advanced Encryption Standard (AES) with a 256-bit randomly generated key to communicate with the Intersight service. This scale is a testament to the architecture and security of the platform.
Communication between a Cisco-branded claimed target and Intersight is always initiated by Device Connector, whether Device Connector is embedded in the target itself or external to the target (that is, the Intersight Appliance; see Chapter 1, “Intersight Foundations,” for more information on Device Connector). With the use of these secure communication standards, firewalls need only allow outbound HTTPS port 443 connections, with no special provisions for Intersight. This eases the configuration burden on the network team and avoids exposing data centers to additional security risks. Intersight communicates directly with non-Cisco targets such as public clouds and storage systems using those targets’ recommended security practices.
Device Connector uses a cryptographic key to uniquely identify itself and a private/public key pair to initiate the connection to the Intersight URL via HTTPS. During the creation of the SSL connection, the Intersight certificate is validated by Device Connector against a list of trusted certificate authorities (CAs). The HTTPS connection is converted to a websocket, which allows low-latency, bidirectional secure communication between the target and Intersight. These properties of the websocket make it well suited for latency-sensitive operations such as tunneled vKVM.
The use of cryptographic tokens by the target ensures that only legitimate devices can attempt to authenticate to Intersight, thereby protecting against Trojan horse attacks. In addition, Intersight’s use of a signed certificate allows Device Connector to validate the identity of Intersight, thereby protecting against on-path attacks (formerly called man-in-the-middle attacks). If Device Connector receives an unsigned or invalid certificate from Intersight, it aborts the connection attempt.
User connectivity is handled with the same level of caution and security as for Intersight targets. Users can utilize a Cisco login ID with support for multifactor authentication (MFA) when using the SaaS platform. Both SaaS and on-premises implementations of Intersight allow single sign-on (SSO) through SAML 2.0 and integration with the most popular identity providers (IdPs), which means an organization can use its preferred authentication services.
Claiming
Before an organization can bring a new target into Intersight for visibility and management, the target must first be claimed. Target claiming options are described in detail in Chapter 1, but for the specific case of Device Connector–embedded hardware targets, the process begins with Device Connector establishing the secure connection to Intersight. However, there are some restrictions that administrators can place on that connection:
Device Connector can be turned off completely, preventing the device from communicating with the Intersight cloud in any way.
Device Connector can be configured for read-only access from Intersight, allowing the device to be monitored but not controlled from Intersight.
Tunneled vKVM traffic can be disabled. This option allows remote console access to the device from properly authenticated users of Intersight using the Device Connector websocket data path for the vKVM data. This option requires an appropriate server license.
Device Connector can be configured to allow configuration only from Intersight and to disable local configuration.
Device Connector can be configured to utilize an HTTPS proxy, with all of the proxy settings (that is, hostname, IP address, port, and username and password) available on the Device Connector settings page.
Figure 2-1 shows the settings for these restrictions.
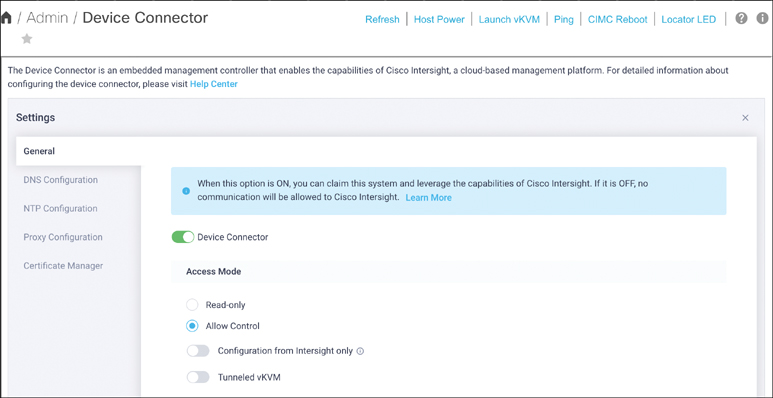
Figure 2-1 Cisco IMC Device Connector configuration
Administrators need physical or network connectivity to a device being claimed as well as proper login credentials for that device. Due to the control available through Device Connector, access to the target should be appropriately limited to administrators only, and local security measures should be in place.
Intersight uses two-factor authentication for device claiming. Administrators need the device ID as well as the rolling claim code issued by Device Connector, which refreshes every 10 minutes. This process prevents malicious entities from claiming a device that does not belong to them, even if they can guess the device ID. Figure 2-2 shows examples of the device ID and claim code. The claim code has a blue expiration bar beneath it, indicating how much time is left before the claim code will be invalidated and a new one will be displayed.

Figure 2-2 The claim process for a Cisco Unified Computing System (UCS) rack server
It is possible to unclaim a target from Intersight through Device Connector, although it is recommended to unclaim devices from within Intersight when possible.
Role-Based Access Control (RBAC)
RBAC provides a way to define a user’s or group’s capabilities and scope of access within the Intersight platform. Once a user is authenticated, that user’s capabilities are restricted by the roles assigned to that user directly or to the groups to which that user belongs. Administrators can take advantage of the following RBAC concepts in order to precisely govern user visibility and actions within Intersight:
A resource group is a collection of one or more Intersight targets. Targets can belong to multiple resource groups.
An organization is a logical grouping of Intersight constructs, such as profiles, policies, pools, and so on. In addition, one or more resource groups can be added to an organization, and a resource group may belong to more than one organization.
Privileges are permissions and/or restrictions applied to a user or role.
A role is a grouping of privileges applied to one or more organizations.
For example, Figure 2-3 shows the creation of a role that has multiple privileges for the TheRanch organization but only read-only privileges for the HX-Cloud-Native-Kit organization.
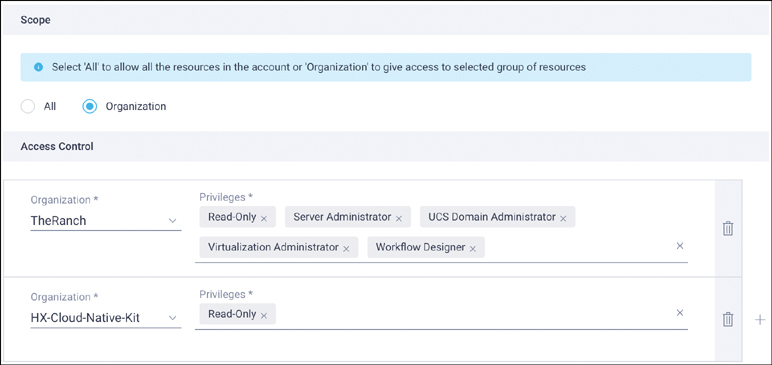
Figure 2-3 Creating a granular role within Intersight
Roles can be assigned to either individual users or groups, as shown in Figure 2-4. It is possible to assign multiple roles to each user or group by clicking the plus sign (+) when creating or editing a user or group. Figure 2-4 shows two roles assigned to the user being created (on the left) but only one role for the group being created (on the right). Group membership is maintained within the IdP so that Intersight is never out of sync with a company’s organizational changes.

Figure 2-4 Creating Intersight users and groups
Finally, Intersight targets can be assigned to one or more resource groups, which can in turn be assigned to one or more organizations within the platform. Since roles associate privileges to organizations, roles effectively assign users privileges to collections of targets, policies, pools, and so on. Account administrators can create new organizations within their accounts, as needed. Creating a new organization involves just naming it and selecting which resource groups belong in that organization, as shown in Figure 2-5.
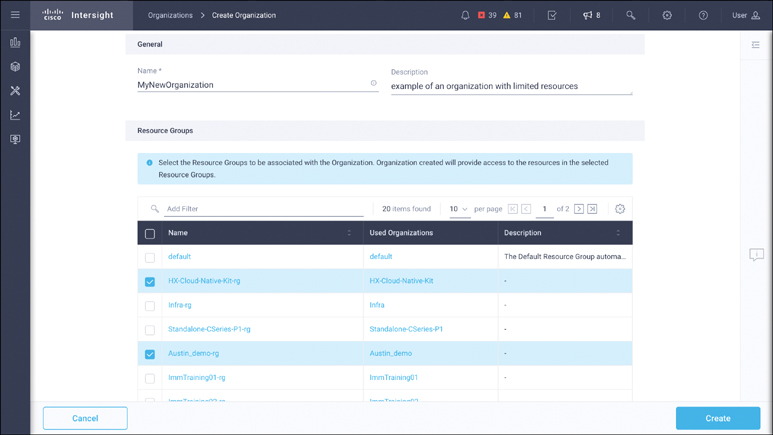
Figure 2-5 Creating a new organization
Audit Logs
Good security requires the collection and examination of audit logs. Intersight facilitates and simplifies this work for IT departments. Intersight saves information related to events (login, logout, created, modified, and deleted) that occur on every managed object within Intersight, including user accounts, pools, profiles, servers, and clusters.
The Intersight interface can be used to browse the audit logs and search by event, user email, client address, or session ID, as shown in Figure 2-6. A session ID is assigned to each user login session so that administrators can locate every action performed by a user in a given session. Audit logs can also be searched programmatically using the Intersight API. See Chapter 11, “Programmability,” for more information.

Figure 2-6 A view of Intersight audit logs
Intersight stores audit logs by using the same data protection standards described in the following section, “Data Security.” To ensure a reliable record of Intersight events, audit log entries cannot be deleted, even by an Intersight account administrator.
Data Security
Data security begins with an understanding of what data is collected by Intersight and how that data is protected from other users of Intersight. Security is a continuous process that involves audit and certification by third parties.
Data Collected
Device Connector transmits the following data to Intersight:
Inventory and configuration data for servers, hyperconverged nodes, fabric interconnects, and the inventory and configuration data of their subcomponents
Server operational data, such as performance, environmental, and fault data
Technical support files created when requested by Cisco TAC
Customers using Connected Virtual Appliance (CVA) can control whether any of this data is transmitted to the Intersight cloud or kept locally. For more information on CVA and the data it sends to Intersight, see Chapter 1.
Device Connector does not collect or transmit sensitive data such as passwords.
Data Protection
Customer data is segregated by an Intersight account within the Intersight cloud. Data segregation and per-customer encryption keys ensure that each Intersight account can only access the data for that Intersight account. At rest, data is encrypted with block storage or volume encryption. While in transit, data is encrypted with TLS 1.2 and higher with restricted ciphers and HTTPS on the standard HTTPS port 443.
Third parties are never given access to the data stored in the Intersight cloud.
Certifications
The ISO/IEC 27001 standard specifies an information security management system (ISMS) that identifies stakeholders, controls, and methods for continuous improvement for information security. Intersight has achieved ISO 27001:2013 compliance, which defines how Intersight perpetually manages the implementation, monitoring, maintenance, and continuous improvement of security within Intersight. Certification is performed by an independent third-party accredited certification body, and additional annual audits are performed to ensure continued compliance.
Service Organization Control 2 (SOC 2) governs the development, documentation, and ongoing implementation of practices assuring the security, availability, integrity, confidentiality, and privacy of customer data. Intersight has achieved SOC 2 Type 2 compliance, which has been verified by an independent auditor.
By design, end-user traffic (including cardholder data) never flows through Intersight. As a result, the Payment Card Industry Data Security Standard (PCI DSS) is out of scope and not applicable to Intersight.
Similarly, individually identifiable health information (IIHI) never flows through the Intersight platform, making the Health Insurance Portability and Accountability Act (HIPAA) out of scope and not applicable to Intersight.
Compliance reports are published at https://trustportal.cisco.com/.
Security Advantages
Intersight development follows continuous integration/continuous delivery (CI/CD) practices. New features are deployed to the platform weekly, and critical bugs and security fixes are deployed continuously. When security risks are identified, they are addressed in Intersight without requiring that IT departments download new software or establish a maintenance window to patch anything. The fact that Intersight is a SaaS platform with CI/CD development means that IT departments have one less thing to worry about.
Device Connector facilitates communication with the Intersight cloud by establishing and maintaining the websocket connection. It has an important role, so it must always remain updated with the latest security patches. Intersight automatically upgrades Device Connector, keeping an organization’s environment secure without the hassle of manual upgrades.
The Cisco Product Security Incident Response Team (PSIRT) is tasked with detecting and publishing any potential security vulnerabilities that affect Cisco products. Intersight curates those reports and pushes the relevant ones as security advisories; this feature requires a license. Organizations can read the publicly available reports, but Intersight customizes alerts by providing only the advisories (and details for their remediation) that affect an organization based on the devices in the organization’s account and the software and firmware versions installed on those devices. Many organizations do not have the time or personnel to correlate these reports manually and filter out the signal from the noise. Intersight gives them only the information they need, when they need it.
Cisco publishes a hardware compatibility list (HCL) that details combinations of software, firmware, and hardware that have been validated by Cisco. Most organizations have processes in place to ensure that servers are deployed with a configuration listed in the HCL but do not have processes in place to periodically verify that server configurations remain in compliance with the HCL. Such organizations can be exposed to performance and security vulnerabilities if their systems are running configurations that have not been validated for compatibility. Intersight can alert organizations about devices that do not match the Cisco HCL and provide steps for remediation; this feature requires a license.
In addition, Intersight can facilitate the generation of compliance reports. With an organization’s entire infrastructure available from a single portal, reports can be generated to show everything from support contract status to which vendors supplied the disks in every server.
Summary
Many organizations are understandably concerned about potential security risks when consuming services from a public cloud, especially when such a service has the power to directly manage their on-premises infrastructure. Intersight was conceived from the start not just as a secure cloud SaaS platform but as a cloud platform that enables its customers to achieve a greater degree of overall security than they might otherwise be able to attain on their own. By leveraging its CI/CD pipeline to provide up-to-the-minute security alerts and patches; by centralizing infrastructure operations, regardless of physical location, thereby avoiding policy sprawl and configuration drift throughout the organization; by integrating directly with Cisco support and compatibility databases and systems to speed problem resolution; and by leveraging corporate access control and user management systems, Cisco Intersight helps organizations move to a more secure operations model.
References
Cisco, “Trust Portal,” https://trustportal.cisco.com/c/r/ctp/home.html
Cisco, “The Trust Center,” http://cs.co/9002HkkPq
Cisco, “Cisco Secure Development Lifecycle,” http://cs.co/9009HkkPd
