COMPLIANCE IS MORE THAN just checking items off a list. It is a dynamic process of ensuring the items in each domain meet or exceed your goals. Because conditions can change in any organization, the status of how well you are meeting your goals can change as well. You should make all decisions related to security controls to satisfy your security policy and any other relevant compliance requirements. Ensuring compliance to your security policy keeps security-related actions headed in the right direction.
Chapter 3 discussed the seven domains of a typical information technology (IT) infrastructure. The User Domain defines the components in the IT infrastructure that directly interact with information system users. User Domain components both govern and are influenced by user behavior. The best User Domain controls direct and restrict user actions and result in compliant behavior. In short, your goal in the User Domain is to persuade users to act in a way that meets or exceeds your standards of behavior. You'll learn about different opportunities to affect user behavior and how that behavior impacts your organization's security.
Information systems provide information to users. Without users, there would be no reason to invest in collecting, manipulating, and storing data. Information passes from the outside world to the information system through user actions. Keyboards, mice, and scanners are just a few of the common methods users employ to get information into the various systems. A secure system needs controls that limit the type of information users can provide and retrieve.
The User Domain is the initial domain in the IT infrastructure that formalizes how information flows in and out of computer systems. This domain defines components you need to control to ensure your environment is compliant with applicable requirements. Figure 8-1 shows the User Domain in the context of the seven domains in the IT infrastructure.
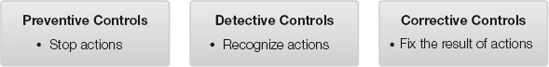
User Domain controls designed to help ensure compliance place limits on acceptable user actions. A User Domain "control" is any mechanism that interacts with a user and reacts when a user's actions meet certain conditions. The overall purpose of User Domain controls is to restrict user behavior to approved, or compliant, behavior. The control's reaction depends on what type of control it is. Controls generally fall into the following functional types:
Preventive controls—Preventive controls are mechanisms that keep an undesired action from happening, such as locked doors or computer access controls.
Detective controls—Detective controls are mechanisms that recognize when an undesired action has occurred, such as motion detectors or usage log analysis tools.
Corrective controls—Corrective controls are mechanisms that repair damage caused by an undesired action and limit further damage, such as the procedure to remove viruses or using a firewall to block an attacking system.
Figure 8-2 gives an overview of preventive, detective, and corrective controls.
By limiting what users can do, compliance-related security controls restrict users to appropriate actions. These restrictions can include limits on what users can access and what actions they can perform. Although limiting users to meet compliance requirements might be desirable or even necessary, they can make it more difficult to complete required business functions. One of the difficulties of ensuring security in the User Domain is designing secure controls that still allow and promote necessary business functions.
It is important that you implement compliance requirements in a way that minimizes the impact on business drivers. Recall that business drivers are the components, including people, information, and conditions, that support business objectives. Any negative impact on business drivers can also have a negative impact on your organization's ability to satisfy business objectives. Carefully research the impact to business drivers before you implement any compliance controls.
Remember that compliance requirements dictate how your organization conducts its activities. Whether the compliance requirement comes from legislation, regulation, industry requirements, or even your organization's standards, the end result is the focus. In most cases, your organization can control activities to ensure compliance in multiple ways. Always consider alternative controls to achieve the end result compliance requires. You'll likely find that some controls are less costly and less intrusive than others. Don't just accept the first control that does the job. Many times, alternate controls are just as good but intrude less on your organization's activities.
You can meet many compliance requirements using one of several controls. If one control has a negative impact on business drivers, consider another control. You can often justify eliminating one control if another control will achieve the same goal.
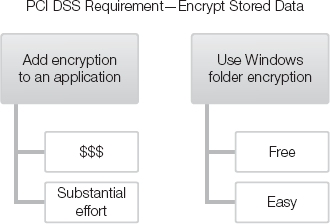
For example, Payment Card Industry Data Security Standard (PCI DSS) requires that you store credit card information as encrypted data. Implementing data-level encryption in a legacy application can be expensive and require a substantial effort. If you run Windows Server 2008, one possible alternative is to use Microsoft BitLocker Drive Encryption. BitLocker could be a compensating control for application-level encryption. Figure 8-3 shows a comparison of alternate controls using PCI DSS as an example.
Many User Domain compliance requirements relate to information access and privacy. The controls you implement will likely restrict what data and programs your users can access. Controls can also provide information on actions users have carried out. User Domain compliance focuses on accountability. Compliant systems monitor and control actions that relate to compliance.
Monitoring actions as they occur allows preventive controls to evaluate action requests and deny unsuitable actions. Operating system access controls fall into this category. The operating system denies a request to open a file if the user does not have sufficient permissions to open the file. The system can monitor access to many other objects as well. If the system uses a log file to track every access attempt, you can analyze the data. Logging object access is a type of detective control.
Proper security controls in any domain take careful planning to develop multiple layers of controls. Control layers should complement other layers and work together to avoid exposing a single point of failure. In the User Domain, an acceptable use policy (AUP) for each type of user serves as a training guide and direction document for other controls. Simply put, the AUP is a statement of what actions are acceptable and which ones are not.
The AUP is not the only security control for the User Domain but it is an important one. Solid User Domain controls help ensure compliance with your organization's security policy. As you design controls, make sure you develop multiple layers to protect each resource. Your goal should be that an attacker must defeat several controls to compromise a resource. That way, no single control failure exposes a resource to an attack. But before you can design solid controls, you need to explore components commonly found in the User Domain.
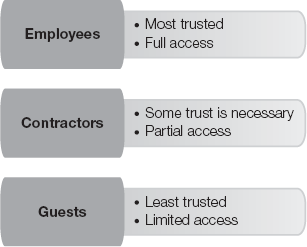
The User Domain contains several common items or components. You should consider each component when evaluating activities for compliance. People and documentation are the most common items in the User Domain. Each of the two broad categories includes several smaller types of items with unique characteristics. The following are different types of people in the User Domain:
Employees—This group has the greatest stake in the organization. Most employees feel a greater sense of responsibility toward their employer than shorter-term personnel do. Employees generally have more privileges and access to organization resources. Although you can trust most employees, an unethical employee can cause substantial damage because of access to information and knowledge of the organization.
Contractors—Contractors may bring specialized skills to an organization but they also pose potential risks. Because contractors may have access to sensitive information, you must monitor them and give them only enough access to do their jobs. Contractors may be less loyal to the organization than employees due to contractors' limited employment. All these reasons present contractors as a greater risk for security violations.
Guests/third parties—Other parties might have no duties related to sensitive information but might still have access to an organization's network. Many organizations commonly provide Internet access to visitors. You should use strict controls to ensure guests do not have access to any sensitive information.
Figure 8-4 illustrates items commonly found in the User Domain.
The User Domain contains more than just people. It is important that people who are resources to an organization have formal directions for how they carry out activities. These activities should support meeting business goals. You need a collection of documents that outlines activities that support business activities to determine whether an action is acceptable or unacceptable. The User Domain also needs documented policies to direct the actions of people. The following are different types of documentation in the User Domain that affect compliance:
Human resources (HR) manuals—HR acquires and manages an organization's personnel. Personnel management includes security awareness and education. Because many security incidents involve users, it is important to provide written documentation of an organization's policies and procedures. HR manuals provide information on how people within an organization should conduct themselves in any situation.
IT asset AUPs—AUPs provide guidance for personnel on proper use of resources. They also define what constitutes improper use. An IT asset AUP covers the use of any IT asset, such as computers, wireless access points, networks, and printers.
Internet AUPs—Internet AUPs define proper and improper use of an organization's Internet access.
E-mail AUPs—E-mail AUPs define proper and improper use of an organization's e-mail capability.
A solid basis for compliant activity requires a well-organized User Domain with clear roles and expectations. In the following sections, you'll learn about important concepts to build a secure environment of compliant behavior.
A common theme in compliance requirements is to reduce the ability of any one element to compromise data security. In the User Domain, this means that no single person should have the ability to bypass security controls that protect data. Each computer user's role should limit the scope of permitted actions.
Most computer systems restrict access to deny unauthorized users. The first step in gaining access to data is to identify yourself to the information system and authenticate your identity. This process commonly involves providing a user ID and a password. Once you are identified and authenticated, the operating system grants authority in the form of permissions and rights. These permissions and rights are defined by your assigned roles. You can only accomplish what your assigned roles allow.
The concept of separation of duties requires that users from at least two distinct roles be required to accomplish any business-critical task. This means that users from at least two roles must collude to compromise data security. Although collusion is still possible, it is far less likely than if a single user could gain exclusive access to sensitive data without anyone else looking. Going further, separation of duties helps avoid conflicts of interest. For example, the role in charge of administering a system should not be the same role that audits that system for potential compliance violations.
Table 8-1 contains some examples of separation of duties in IT environments.
Figure 8-5 illustrates separation of duties in an IT environment.
Table 8-1. Examples of separation of duties in an IT environment.
ROLE RESTRICTION | DESCRIPTION |
|---|---|
Only grant limited access for external personnel to the computer and files they need for the current project. | External personnel can help complete projects but should have limited access to resources. This restriction helps reduce the number of people who have access to each part of a system and reduces the opportunities for data compromise. |
Prohibit all access to production environments for developers. | Developers have the ability to write programs that access sensitive data and should not have the ability to bypass configuration management controls. Configuration management controls require a separate role to promote software from development to production. |
Do not allow general administrative users to create backups of critical data. | It is easy to create backups on media that fit in a pocket. Create a role for backup operators and only allow a small number of individuals to create backups. |
The first step in implementing separation of duties is to remove unnecessary user privileges. Any unnecessary privilege provides an opportunity for a user to violate the AUP and perform unauthorized data access. It makes sense to use access controls to prevent unauthorized data access. The process of allowing only the level of access your users require might be tedious, but it is necessary to secure sensitive data.
The ultimate goal is to define access control where each user has the permissions to carry out assigned tasks and nothing else. This is the principle of least privilege. User permissions beyond what is required to carry out necessary tasks are excessive and potentially insecure.
Tip
When you define permissions based on roles, or groups, you allow object owners and administrators to grant access rights at their discretion. This type of access control is a discretionary access control (DAC) and is common in commercial environments.
Putting least privilege into practice can be challenging. Organizations with many users often use roles, or groups, to define access permissions. Administrators define roles that represent small tasks, such as "accounts receivable user" and "accounts receivable manager," and grant specific permissions to each role. Individual user accounts can belong to one or more roles and inherit the permissions from each of the roles definitions.
Government organizations and some commercial organizations implement the principle of least privilege in a different way. They use a system not based on roles, but on data classification and user clearance. The operating system makes the decision to grant or deny access to any data object by matching the object's classification to the user's clearance. Because this method of access control is based on object and subject attributes and not on anyone's discretion, this is a mandatory access control (MAC). Table 8-2 shows the classification system the U.S. government uses for MAC.
Table 8-2. U.S. government MAC clearance and classification levels.
DESCRIPTION | |
|---|---|
Unclassified | No security label is needed—this object is accessible by anyone |
For Official Use Only | Objects that should not be accessible by anyone outside an organization |
Confidential | Objects that contain information that could cause harm to an organization or nation if divulged |
Secret | Objects that contain information that reasonably could cause serious harm to an organization or nation if divulged |
Top Secret | Objects that contain information that would likely cause extreme harm to an organization or nation if divulged |
Nongovernmental organizations that need to protect information at different sensitivity levels can also use MAC to secure information. The ISO 27002 standard contains suggestions for five basic classifications. These classification levels are just suggestions for organizations that do not already have a classification strategy in place. Table 8-3 shows the ISO 27002 suggested classification levels.
Table 8-3. ISO 17799 suggested clearance and classification levels.
CLASSIFICATION | DESCRIPTION |
|---|---|
Public Documents | Objects in the public domain. |
Internal Use Only | Objects that have not been approved for release to the public. |
Proprietary | Objects that contain information that might be harmful to an organization if divulged to the general public. |
Highly Confidential | Objects that contain sensitive information that is critical to an organization. Divulging such information could have a significantly negative impact on an organization. |
Top Secret | Objects that contain extremely sensitive information that would cause extreme damage to an organization if divulged. |
Whereas DAC does support the detailed control necessary for least privilege, simple data classification and user clearances do not. You need an additional control to ensure users only possess the privileges they need to do their jobs. For example, a project manager needs access to documents related to the current project only. If the documents for several unrelated projects are all labeled as "highly confidential" and the project manager holds a "highly confidential" clearance, all project documents would be available.
Note
Need to know limits access to secure objects and limits damage in the case of a breach. Assume the project manager used in this section's example leaves the organization. If she chooses to violate ethics and disclosure regulations, she could disclose the contents of all objects to which she had access. The principles of need to know and least privilege protect the organization by limiting how much information a single individual can compromise.
Although this situation might seem reasonable, it does allow a project manager to access documents that are unrelated to the current project. This capability violates the principle of least privilege. Most systems that use DAC also use the concept of need to know. In addition to possessing a clearance level that matches or exceeds the classification label of an object, a subject must have the need to know for the object as well. Simply put, need to know means that you have a need to access an object to do your job. Adding the concept of need to know to DAC does provide full support for the principle of least privilege.
Employees who work with sensitive information can be a great asset and a great risk. A person who understands the inner workings of your organization can protect sensitive information or defeat your security controls. Someone who knows your organization could make violations difficult to detect. Contractors who have access to sensitive information can be just as dangerous. How should your organization protect sensitive information from insiders? The answer is to implement a defense-in-depth strategy. Solid access controls and the principle of least privilege are both important, but neither is enough.
Some information leaks occur because of simple ignorance or carelessness. If workers don't know that information is sensitive, they might treat the information with less care. When hiring personnel, you should communicate your organization's security policy clearly. The employee or contractor confidentiality agreement is a common document that accomplishes this. Another name for this document is a "non-disclosure agreement" (NDA).
A confidentiality agreement is a legally binding document. By signing this document, each party agrees to keep certain types of information confidential. A confidentiality agreement is a necessary part of any relationship that involves sensitive information.
Note
Two types of professional relationships involving sensitive information don't require a confidentiality agreement. Privacy laws cover relationships between clients and attorneys and between patients and doctors. These relationships do not need other agreements to keep information confidential.
Confidentiality agreements allow organizations to disclose sensitive information to a small number of parties without concern that an information leak might cause harm. For example, these agreements allow organizations to share specifications of unreleased products to business partners. Sharing this type of information allows business partners to develop companion products before the release of original products. Most major software vendors, such as Microsoft and Apple, do this to allow their development partners to write software for new operating systems before the release date. The confidentiality agreement protects the operating system vendor by prohibiting partners from releasing information about the new product.
Warning
Binding confidentiality agreements should define time frames for the agreement. Confidentiality agreements are not valid forever. A good agreement specifies a date range within which parties must make disclosures and a date range within which disclosure restrictions are in force. A lack of either time frame could invalidate the agreement.
Another important feature of a confidentiality agreement is that it can protect patent rights. Publicly disclosing an invention can result in forfeiting any patent rights. An organization must keep information about the invention confidential until filing a patent application. Confidentiality agreements with anyone who has access to confidential information can protect your organization from a damaging public disclosure.
A confidentiality agreement defines the types of information parties can and cannot disclose. A confidentiality agreement also specifies how parties may use confidential information. The agreement defines expected behavior and the consequences of violating the agreement. A well-written confidentiality agreement lowers the risk of disclosing confidential information.
Many organizations perform a background check on prospective employees before hiring anyone. The purpose of a background check is to uncover any evidence of past behavior that might indicate a prospect is a security risk. In reality, all personnel are security risks because they must be trusted with sensitive information. A background check can uncover information that indicates a person might be an undue security risk.
Background checks can vary in depth, for example simply verifying a Social Security number as authentic and belonging to the applicant. Another example is conducting a police criminal check and reviewing a prospective employee's complete history. Each organization sets the scope of background checks. The job description and the organization's desire to use a prospect's history to indicate future actions affect the scope of the investigation. You can conduct background checks using internal resources or by engaging external specialists. External resources can reduce your ongoing expense and may provide higher-quality information by using specialists. However, external resources who conduct background checks operate under additional restrictions.
The Fair Credit Reporting Act (FCRA), which defines national standards for all consumer reports, also governs how you conduct background checks. FCRA governs background checks because they are labeled as consumer reports, even though a background check may consist of more than credit history information. FCRA sets time limits on negative information that investigators can include in their report. Although some states may lengthen FCRA time limits, investigators cannot include:
Bankruptcies that are over 10 years old
Civil suits or judgments that are over seven years old
Paid tax liens or other negative financial information that is over seven years old
Background checks often include much more than just financial information. Most employers are more interested than ever in a prospective employee's general past and current behavior. In many cases, social networking sites, such as Facebook or MySpace, can provide information on a prospect's behavior. Fair or not, more and more employers are looking into past behavior to attempt to decide how trustworthy a prospect may be.
Although background checks are important and might provide interesting insight into a person's background, you must perform them with care. FCRA requires that you obtain permission from the subject of a background check before you begin the investigation. In addition, if you decide not to extend an offer due to information contained in the background check report, you must provide the reason and the contact information for the investigating organization. You must give the prospect the opportunity to dispute any negative information in the report. This safeguard helps prevent incorrect information from harming an unsuspecting individual.
Background checks can reveal quite a lot about a prospective employee. A prospect with prior criminal history might not be a good candidate for a role that allows access to very sensitive information. Knowing the background of prospective employees is an important step in granting authorization to sensitive information. Although a background check won't catch every potential attacker, it can help identify some of the most likely high-risk candidates.
As you've learned in previous chapters, auditing is the process of examining systems to verify they are in compliance with defined policies. In short, auditing ensures activities comply with policy. This process provides value only when it objectively reviews evidence of actions. An auditor who overlooks any evidence of noncompliance isn't very effective. Because of the potential of negative findings, it is important that all parties engaged in auditing activities understand responsibilities to the audit process.
Don't view auditing simply as a search for problems. Auditing is an opportunity to identify noncompliance issues before they escalate and possibly cause damage. This positive attitude toward auditing must start with upper management, who should share it with all affected parties. If upper management does not fully support the efforts of auditors, it is unlikely anyone else will.
Note
Repetitive auditing and taking action on the results of audits are proactive forms of continuous improvement. The general idea is that constantly adhering to policies results in higher-quality output—not just fewer violations.
Upper management can influence audit process quality by assigning responsibilities and accountabilities. Every employee bears some responsibility in the IT security audit process. Every agent of your organization must maintain the security of your information. Because the IT security auditing process verifies compliance with security policies, all employees bear responsibility for carrying out your policies.
Each task in the audit process has one or more people who are responsible or accountable for that task. Many organizations use a RACI matrix to document tasks and personnel responsible for the assignments. RACI stands for responsible, accountable, consulted, and informed. To create a RACI matrix:
List tasks along one axis and personnel or roles along the other axis.
Assign a level or responsibility for each role and task.
Assign each person or role a level of responsibility and accountability for each task.
The entries in the matrix will contain one of the following:
R (Responsible)—Person who actually performs the work to accomplish the task; may be multiple people.
A (Accountable)—Person who is accountable for the proper completion of the task; only one person is accountable for each task. The Accountable is likely the Responsible's manager.
C (Consulted)—Person who provides input that is helpful in completing a task; may be multiple people.
I (Informed)—Person who desires to be kept up to date on a task's progress; may be multiple people.
Table 8-4 shows a simple RACI matrix for an IT audit.
The RACI matrix clarifies the responsibilities and accountabilities for a set of tasks. A RACI matrix provides upper management a tool that communicates and conveys for tasks. Without the acceptance of audit responsibilities and accountabilities, the auditing process might encounter resistance. Management and other employees might view the audit process as punitive.
Table 8-4. Simple RACI matrix for an IT audit.
TASK/ROLE | MANAGEMENT | PROJECT MANAGER | AUDITOR | USER |
|---|---|---|---|---|
Develop audit plan | A | R | C | I |
Develop audit activities schedule | A | R | C | I |
Conduct audit activities | A | R | C | |
Review audit results | A/R | R | R | C |
Identify noncompliant elements | A | I | R | C |
Develop plan to address noncompliant elements | A | R | C | I |
Develop noncompliant mitigation activities schedule | A | R | C | C |
Conduct noncompliant mitigation activities | A | R | R |
Employees often have the greatest access to an organization's critical resources. Your organization places substantial trust in its employees and takes on substantial risk in doing so. Many security incidents originate from internal personnel, including employees. Not all incidents are malicious attacks. Some are simply a failure to comply with the organization's stated security policy.
It is important to educate new employees on your organization's security policies and procedures. It is difficult for employees to comply with a policy if they are unaware of what the policy contains. Training employees on security matters can help avoid many security policy violations, including:
Weak passwords
Inappropriate use of the Internet
Inappropriate use of e-mail
Divulging confidential information
The HR department usually follows an established procedure when handling new employees. Security awareness and security procedures training should be a part of this process. You should provide training for each employee on security topics, including:
Organization's commitment to information security
Justification for security-related activities
Important security procedures
Security training should include justification. It is important that employees understand the value of security to the health of your organization. Employees should acknowledge they have received security training and agree to abide by your security policy and procedures. Many organizations make use of the employees' acknowledgment to uphold the security policy requiring it as a condition of employment. Because the security of sensitive resources is important to your organization, it should be important to your employees.
Security-related activities often have lower importance than activities that directly make money. Unless upper management clearly states the importance of security, security personnel might find it difficult to obtain funding and support to maintain secure systems. Most important, an organization's upper management is responsible for protecting the security of the organization's resources. Management is responsible to the stockholders, regulatory agencies, government entities, and the public.
In addition, management should assign accountability for each security-related activity. Creating and maintaining a secure environment requires acceptance of accountability.
HR is responsible for acquiring and managing all of your organization's personnel. This includes initial and recurrent training. Because HR is responsible for proper employee and other personnel training, the department should be accountable for ensuring each person receives training.
In fact, HR takes a lead role in the accountability of all personnel actions. Having HR take a lead role centralizes training delivery and employee-related compliance activities. HR also operates above functional management and protects the organization from role favoritism. HR ensures that the organization holds all personnel to the same set of standards.
HR also holds the responsibility to define the activities of all personnel, including IT personnel. Accurate job descriptions are necessary to acquire the best employees for each position. Job descriptions also set proper expectations for all personnel. Accurate and up-to-date job descriptions allow HR to develop the most appropriate role-based training and to ensure all employees receive proper training to carry out their tasks.
Job descriptions also set and maintain the expectations and performance standards for each employee. These expectations provide a standard for employee performance measurement. Although specific performance numbers might be outside the scope of a job description, it does contain a framework of expected performance.
In addition to defining the job description, your organization should set performance criteria for evaluating employees. Each employee should have a set of performance criteria that compares performance to goals. These criteria can be valuable during annual performance reviews.
Performance accountability is important to motivate employees. A motivated employee tends to be happier and more productive. Performing simple tasks with no accountability can lead to boredom and even sloppy work. Your organization should encourage employee accountability and reward staff for taking on more responsibility and being more accountable.
User behavior is the focus of auditing for IT compliance in the User Domain. In the simplest sense, this consists of examining user actions and comparing those actions with security policies, standards, procedures, and guidelines. If you find any differences with organizational requirements, you should report the differences and analyze their impact.
Warning
It is difficult for untrained users to comply with your security policies. For example, as basic as it might seem, you shouldn't expect users to create and use strong passwords unless you train them how to do it and tell them they are required to use strong passwords.
It is important to train all internal and external users on acceptable behavior. Training should cover the contents of your organization's security statement documents and provide users with the knowledge to comply with the documents. Training that does not cover security expectations is insufficient. Users who hold a privileged role, such as system administrator, should receive additional, specialized training pertinent to their role.
Good security training should stress the importance of compliance and cover the important parts of these types of security documents:
Security policy—A high-level statement that defines an organization's commitment to security and the definition of a secure system, such as the importance of changing passwords periodically
Security standard—A collection of requirements the users must meet, typically within a specific system or environment, such as changing a Windows password every six months
Security procedure—Individual tasks users accomplish to comply with one or more security standards, such as the steps to change a password
Security guideline—A collection of best practices or suggestions that help users comply with procedures and standards, such as suggestions on how to create strong passwords
Note
Some security violations are obvious. However, User Domain auditing reveals many less-obvious noncompliant user actions.
Your access control policies should grant access to information systems depending on users upholding the organization's security policies, standards, procedures, and guidelines. Violation of any of these security elements should carry consequences ranging from a training refresher course to losing access.
Identifying and influencing user behaviors that affect security are important to ensuring compliance within the User Domain. Behaviors that support or violate compliance with your security goals get the most attention. The following best practices do not guarantee compliance with all goals. However, they will lay the foundation to develop and maintain a secure environment:
Document all laws, regulations, and standards that require User Domain compliance for your organization.
Define AUPs for each type of IT service or equipment.
Conduct background checks for all employees and critical contractors prior to engagement.
Develop security awareness and procedures training for employees and contractors.
Require security awareness and procedures training and assessment prior to engagement.
Require users to sign confidentiality agreements prior to receiving access to any sensitive information.
Establish unique logon credentials for each user and require strong passwords.
Grant only the minimum privileges to each user required to accomplish that user's tasks.
Require action by at least two separate users to complete any business-critical function involving sensitive information.
Periodically audit user access privileges for compliance to stated goals.
The User Domain defines information system users and the actions they carry out. A critical factor of maintaining secure systems is ensuring compliance of users to security goals. Because user actions result in accessing information, it is necessary to control and monitor user actions to maintain secure systems. Systems must uniquely identify users and allow access only to information for which they are authorized. Auditing activities should examine all access decisions and the rules that govern such decisions for compliance. Defining limits within the User Domain and validating user activities provide an important security layer in a defense-in-depth approach to system security.
Acceptable use policies (AUPs)
Background check
Business drivers
Confidentiality agreement
Corrective controls
Detective controls
Discretionary access control (DAC)
Fair Credit Reporting Act (FCRA)
Mandatory access control (MAC)
Need to know
Preventive controls
Principle of least privilege
Separation of duties
Which type of control only reports that a violation has occurred?
Preventive
Detective
Corrective
Restorative
The term _______ defines the components, including people, information, and conditions, that support business objectives.
Which of the following types of policies defines prohibited actions?
Access control policy
Password usage policy
Acceptable use policy
Violation action policy
Which of the following terms ensures at least two distinct roles must perform a series of actions to complete a task?
Separation of duties
Least privilege
Need to know
User clearance
When using DAC, a subject must possess sufficient clearance as well as _______ to access an object.
Which of the following terms defines a strategy in which you grant access that allows a user to complete assigned tasks and nothing else?
Separation of duties
Least privilege
Need to know
User clearance
Which type of agreement can protect the ability to file a patent application?
Relinquish ownership agreement
Security clearance waiver
Background check agreement
Confidentiality agreement
What condition must exist for a background check to be governed by FCRA?
The investigation includes credit history.
The investigation is performed by a third party.
The investigation is performed by the prospective employer.
The investigation includes criminal history.
Which of the following best describes the purpose of auditing?
Finds root causes of violation issues
Assists investigators in identifying blame for violations
Verifies that systems are operating in compliance
Searches for hidden unacceptable use of IT resources
Using a RACI matrix, which attribute refers to the party that actually carries out the work?
Responsible
Accountable
Consulted
Informed
Which department should take the lead in User Domain compliance accountability?
Information technology
Information security
Human resources
Security
A confidentiality agreement sets the expectations of each employee and sets job performance standards.
True
False
Which of the following is a series of individual tasks users accomplish to comply with one or more goals?
Policy
Standard
Procedure
Guideline
Which of the following is a collection of requirements the users must meet?
Policy
Standard
Procedure
Guideline
Discretionary access control is based on roles and granted permissions.
True
False