COMPLYING WITH SECURITY-RELATED REGULATIONS, legislation, and other requirements means ensuring your organization protects the security of your information. In most cases, ensuring information security means ensuring users take appropriate actions and refrain from inappropriate actions. Although the directive seems simple, implementing it can be complex. In Chapter 8, you learned about compliance in the User Domain. You learned about the requirements of information system users and their responsibilities in ensuring the security of your organization's information.
If all users were perfect and completely compliant, there wouldn't be a need to consider any further security layers. Remember that users include both authorized and unauthorized users. Attackers fall into the category of unauthorized users. Because users are imperfect and often noncompliant, you must include additional layers of security controls to protect your information's security. The defense-in-depth philosophy provides the best strategy to secure information and remains the basic blueprint for designing security controls. In this chapter, you'll learn how to follow the defense-in-depth strategy to enforce compliance within the Workstation Domain.
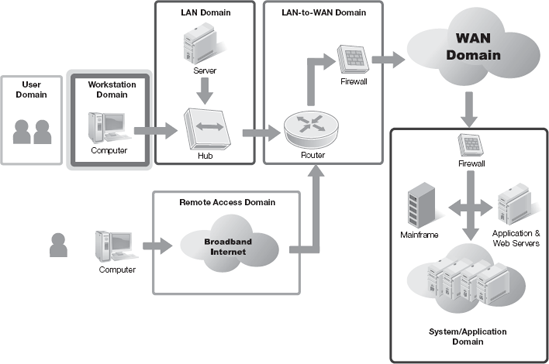
Users generally access information from workstations. This is not always the case, but it is the most common access method that allows users to view and modify your organization's information. Because workstations provide access to information, they become an attack vector for unauthorized users. It is important that you ensure all items in the Workstation Domain are compliant. Figure 9-1 shows the Workstation Domain in the context of the seven domains in the IT infrastructure.
As with all domains, ensuring compliance in the Workstation Domain satisfies two main purposes:
Increases information security—Because information is a material organizational asset, and in some cases, the primary organizational asset, ensuring the security of information equates to protecting the viability of the organization. It is just as important as protecting any other major assets of the organization. A loss of any important asset will likely disrupt your organization's ability to conduct normal operations. It is important to protect your organization's ability to do business.
Reduces liability—If one or more attacks are successful against your organization's information, you might be liable to damages caused to third parties. If information loss or leakage causes damage to other people or organizations and the damage is a result of noncompliance, your organization might be liable for part, or all, of the damages. At the very least, disclosed successful attacks against your organization can degrade confidence in your commitment to security. An attention to compliance details and strong security can dramatically reduce your organization's exposure to liability clams.
Many recent legislative and regulatory requirements extend the scope of threats to information to include all users. There is no assurance users will be compliant. Organizations need additional layers of controls to protect information because not all threats come from malicious users—some threats come from simple ignorance. For example, procedural changes might prohibit users from transferring protected files to remote workstations. Properly trained users should not attempt to transfer files to remote workstations, but well-meaning users who are not aware of the new policy might unknowingly violate the policy. The proper way to handle this situation is to:
Ensure all users receive updated training.
Place access controls in the Workstation Domain to prohibit inappropriate actions.
You need both types of controls to secure information from all users.
Increased attention to security increases the need to hold employees accountable for security. Because employees generally have more access to information than other authorized users, they have greater ability to impact the information's security. Great ability to impact security means you need a greater scope of controls. The most common concern for information security that is reflected in most recent legislation is protecting information privacy. Although information integrity and availability are important, privacy is a primary concern of many regulations. All information system users are accountable for the privacy of the information they access. This puts a greater amount of responsibility and accountability on users.
A solid security strategy should include several types of controls to ensure user compliance. You've already seen some controls in the User Domain. The Workstation Domain is the domain that contains the devices and components to access information. Controlling activities in the Workstation Domain can provide an effective layer of information security. Workstation Domain controls should validate and support controls in other domains. Although controls in the User Domain are important, you need additional controls to ensure compliance with your security policy and any additional security requirements. Controls in the Workstation Domain should work with controls in other domains to ensure a high level of overall compliance.
Workstation Domain controls are security controls that prohibit, validate, or detect user actions. Users initiate actions in the Workstation Domain that generally involve some stored information. In short, users generally access information using some type of workstation device. It makes sense to place controls at the workstation level to ensure information access is compliant. Proper controls in the Workstation Domain should work with other controls in all domains to enforce compliance without interrupting normal operation.
For example, Payment Card Industry Data Security Standard (PCI DSS) prohibits merchants from storing the Card Verification Value (CVV) number. The CVV number is a three- or four-digit number that card issuers print on each credit card. The CVV number provides additional authentication when rendering payment for online transactions. One control to avoid storing the CVV is to remove any user prompts for the CVV. Although that complies with the PCI DSS data requirement, it also disables the merchant's ability to ask for the CVV to authenticate the transaction. You should not implement this control because it interrupts a necessary business function. Look for another control that balances security and business requirements.
A good strategy to identify the best Workstation Domain controls is to start with your security policy. Identify any requirements that directly relate to workstation components and create appropriate controls. The task of identifying controls is much easier if consulting ISO/EIC 27001, which provides a concise list of security controls. For more in-depth understanding of every control, ISO 27002 is the best reference. Once you have a list of potential controls, compare your list to the User Domain controls. The Workstation Domain controls should complement controls in other domains, but should specifically support User Domain controls. A good way to enforce this guideline is to create controls of different types for different domains. For example, suppose you want to enforce your password policy. You may have an administrative control in the User Domain that mandates user training on proper passwords. A good Workstation Domain control would be to enforce complex passwords on all workstations. This would be a technical control that enforces strong passwords by prohibiting weak passwords. Users should already know how to create strong passwords from their training class. However, forcing strong passwords using a Workstation Domain control ensures users follow the requirements. Once these controls are put into practice, they serve as countermeasures for the organization. Countermeasures are the controls you put in place to mitigate a risk. This is another example of a defense-in-depth strategy.
Note
Your Workstation Domain controls should not just duplicate User Domain controls, but should provide a second level of assurance.
The Workstation Domain connects users to local resources. You'll learn about how to handle remote users in Chapter 13. The Workstation Domain includes all local resources that support user functionality and allows users to interact with your information system. In some cases, Workstation Domain items collect and present information as well as process that information. In other cases, processing occurs in another domain.
In either case, users use the Workstation Domain to interact with the rest of your environment, including your data. Each type of device or component in the Workstation Domain presents potential vulnerabilities and security challenges. It is important that you carefully consider each type of component when you design Workstation Domain controls. Figure 9-2 shows the most common devices and components you'll find in the Workstation Domain.
An uninterruptible power supply (UPS) provides continuous usable power to one or more devices. Some UPS models also provide the ability to protect data connections from power surges that could damage computers or other hardware. A UPS can protect many types of devices and may exist in several domains. Their primary purpose is to support the availability of Workstation Domain devices. UPS devices generally provide several types of protection, including:
Continuous power—A primary purpose of a UPS is an integrated battery that provides power to connected devices when the AC power fails. When the AC power fails, or even falls below usable voltage, the UPS automatically switches to its battery to provide uninterrupted power to any devices connected to the UPS. This feature allows the connected devices to continue operating normally during power outages. Because the backup power depends on the UPS battery, the duration of the power is limited—generally around 30 minutes. Although larger UPSs include backup power generators that can provide power for extended periods of time, devices in the Workstation Domain generally do not require such measures. The ability to survive short duration power outages is generally sufficient.
Surge protection—Nearly all UPSs condition the power supplied to connected devices. Conditioned power means that any voltage surges are removed before providing power to devices. This surge-filtering capability protects connected devices from potential damage from high voltage. Some UPSs include network connectors that protect networking connections from power surges as well as power connections.
Structured shutdown—Many UPSs provide the ability to establish a communications connection to a primary computer. This connection allows the UPS to send a shutdown request to the computer when the UPS power is in danger of running out. When a power outage duration approaches the UPS power limit, the UPS can alert the computer and allow it time to shut down gracefully. This ability protects data integrity by avoiding uncontrolled shutdowns that could cause damage to open data files.
Desktop computers have historically been the most common type of Workstation Domain device. That trend is rapidly giving way to more portable computers. Desktop computers are designed to be stationary and are often physically connected to an organization's network to share information and devices. Because they are commonly connected to other network resources, it is important to carefully control access to these computers.
Most desktop computers have substantial local processing power and are often used to locally create and manage data. Although this ability can reduce the workload on other domain devices, it can also lead to data leakage. Users who are comfortable working with information locally on a desktop computer might not be diligent about backing up the information or perhaps about protecting the information.
Desktop computers have grown in power and storage capacity in recent years to the degree that they rival the capabilities of some server computers. This increase in power encourages users to install more and more software on their desktop computers. Allowing unsupervised software installations can lead to desktop computers that are difficult to support or even dangerous to your organization. Many computer problems relate to conflicts between programs that are competing for resources. Allowing users to install unapproved programs increases the likelihood of conflicts with approved programs.
A lack of desktop computer control also increases the likelihood users will unknowingly install malicious software. A desktop computer with malware is not only a threat to locally stored information, but also to all other devices connected to your network. It is important to understand the risks of allowing too much user freedom and implement the appropriate controls to protect your organization.
As computers shrink in size and grow in capabilities, several new classes of computers now rival the desktop as the most popular type of workstation. Laptop computers are generally the larger, more powerful class of portable computers. Laptop computers can do nearly everything a desktop computer can do while maintaining a small enough profile to be very portable. Most laptop computers fit easily into briefcase-size bags and backpacks. Although laptop computers generally lack all of the capacity and power of desktop computers, laptops still can boast substantial capabilities that make them full-featured devices.
Netbook computers are relatively new devices that are smaller and lighter than laptop computers. Their smaller size and lighter weight means that they generally have fewer hardware options and limited capabilities. Netbook computers are generally designed to act as access devices to network devices and don't provide much local storage. Although they lack much local storage space, they still pose risks because of their support for network access.
As with desktop computers, it is important to control access to network resources and the ability to install unauthorized software. In fact, the need to control portable computers is more important than with desktop computers. The portable nature of laptop/netbook computers means these computers are likely transported and used at locations physically outside of your organization. In most cases, users connect portable computers to other networks when they are away from your organization's building. Connecting to unprotected networks can be extremely dangerous. Users can pick up infected programs when connected to other networks and then introduce them the next time they connect to your network. Your security policy should include specific standards for using portable computers to connect to your networks.
A local printer is any printer connected directly to a local computer. Many organizations use networked printers, which you'll learn about in Chapter 10. Local printers aren't shared by multiple users. Because these printers aren't connected to your organization's network, they aren't controlled from a central location. This means local users can print anything they want. Allowing users to access local printers without any controls can lead to several types of issues, including:
Personal use of the organization's resources—Users can print any files to local printers. This can include personal information that might violate the acceptable use policy.
Disclosure of private information—Users can print files with little or no control over content. There is always the chance that printed documents could end up in the wrong person's hands.
Printer buffer access—Most printers retain copies of recently printed documents. It is not difficult to get a printer to reprint previously printed documents. It can be difficult to control this behavior on local printers.
Minimize local printer use in your organization. Printers should generally be networked and managed from a central location in another IT domain.
Analog modems can pose serious threats to organizations. At first glance, they don't seem too dangerous, but they can provide damaging backdoor entryways into your network. Modems do have a place in a secure environment but not in the Workstation Domain. Modems provide a connection to another computer or network and belong in another domain where you can control them in a way that protects your network. Modems connected to Workstation Domain devices are almost always uncontrolled and installed to bypass network access controls.
Although many users consider modems to be harmless, they can be valuable tools for attackers. Many attackers still employ an old technique called war dialing. War dialing is instructing a computer to dial many telephone numbers looking for modems on the other end. The war dialing computer records any modems it finds for later analysis. Each modem that answers a war dialing computer is a potential target. Attackers will dial identified numbers and attempt to access the computer on the other end. Unauthorized modems are rarely secured well and are known to be fairly soft targets. The attacker attempts to access the computer to which the modem is attached and then move on to attack the organization's network.
Warning
As innocent as it might seem, simply connecting an analog modem can potentially compromise your network. It is important that you search for rogue modems and ensure you either eliminate or carefully control each modem in the Workstation Domain.
Virtually all general-purpose computers have at least one internal, fixed hard drive. Computers primarily use fixed hard drives to store the computer's operating system as well as application programs and data. Some leading-edge or special-purpose computers use solid state memory to store programs or information, but most of today's computers use regular hard disk drives. Disk drives store files that contain data, instructions, or both data and instructions.
Privacy laws and regulations address both types of file contents. Compliance with different requirements often means restricting how you access certain types of information or how you must store information. For example, under the Health Insurance Portability and Accountability Act (HIPAA), you must protect all private medical information from unauthorized disclosure. That often means using centralized storage with carefully monitored access and storage controls. You implement centralized storage in another IT domain, not in the Workstation Domain. Continuing the example, assume you use your workstation to access private medical information. You decide to copy the information into a document and store it locally on your workstation while you edit the information. The decision to store the information locally potentially just violated HIPAA. The problem is that you have just placed private medical information in an area that unauthorized users can potentially access.
You must carefully control what devices in the Workstation Domain can do. The good news is that you do have some control when Workstation Domain devices "reach across" domains. You'll learn more about controlling access and storage in the LAN Domain in Chapter 10. Storing information from another domain is only one issue. You also need to control files stored on the hard disk that originate outside your organization's IT infrastructure. Outside programs and files often result from activity while you are connected to another network. In most cases, Internet access provides the inbound path for unwelcome files. Malicious files and software can infect unprotected computers and then spread to other computers and devices in your organization. Controls in the Workstation Domain for disk drive access can help prevent infections and protect the rest of your network.
One last category in the Workstation Domain includes devices you connect to computers as you need them. You use most of the devices in this category to store files to transport to another computer. These devices include:
Removable hard disk drives
Universal serial bus (USB) flash drives
Removable CD-ROM and DVD drives
Removable tape drives
There are other removable storage devices, but these are the most common. In fact, the most common devices are USB flash drives. These drives are compact, are easily available, and can store from 128 MB to over 256 GB of data, depending on device capacity.
Because you can transport removable media easily and connect it to other computers, it is important that you control the files you transfer both to and from any such devices. In general, you should control two types of transfers:
Control information you copy to a removable device to ensure you protect data privacy. This type of control keeps you from divulging private information.
Control data you copy from a removable device to block malicious code or data. This type of control protects the rest of your environment from introducing malicious code.
Understanding the devices and components in the Workstation Domain is the first step to establishing controls to secure this domain. The next step is to understand data and device access controls. You'll learn about Workstation Domain access rights and controls in the next section.
You learned in the previous sections how important it is to implement the correct controls in the Workstation Domain. Proper security controls limit access to objects based on a user's identity. Access control methods may be based on the permissions granted to a user or group, or they may be based on a user's security clearance. Either way, access rights start with knowing which user requests access to an object and what the user's identity permits him to do.
Most computers require you to log on before you can access any resources on the computer. Even systems set up to automatically log on are actually logging on to a predefined user account. The first step in logging on is to provide a user ID or username. Providing user credentials or claiming to be a specific user is called identification. Simply identifying yourself is not enough. If all you have to do is claim to be a user, anyone can claim to be a system administrator and gain permission to carry out potentially harmful actions. Operating systems require users to follow the identification step with authentication. Authentication is the process of providing additional credentials that match the user ID or username. Only the operating system and the real user should know the authentication credentials. The most common authentication credential is the password. Other options include security tokens and biometric characteristics. Once you provide the correct user ID and authentication credentials, you are logged on to your user account.
As the operating system logs you on, it looks up security authorization information and grants you access permissions based on your identity. There are two main approaches for authorizing users to access objects. Both approaches evaluate whether a user, also called a subject, has the permission to access some resource, also called an object. Access objects can be files, directories, printers, or any resource. There are other methods as well, but two methods are the most common ones you'll encounter.
The first access method uses access control lists (ACLs), which are lists of access permissions that define what each user or security group can do to each object. Each object uses ACLs or permissions to define which users can access it. The object's owner can grant access permissions to any desired user or group. Because granting access is at the owner's discretion, this type of access control is called discretionary access control (DAC).
The second type of access control is not based on specific permissions but on the user's security clearance and the object's classification. Organizations that use this type of access control assign a specific classification to each object. Security classifications used by the U.S. government include Top Secret, Secret, Confidential, and Unclassified.
Other governments and nongovernmental organizations use slightly different classifications but most classification schemes are similar. Each user receives a security clearance that corresponds to one of the classifications in use. The operating system grants access to objects based on a user's security clearance and the requested object's classification. For example, a user with a Secret clearance can access Secret, Confidential, and Unclassified objects but cannot access Top Secret objects. Because there is no discretion involved in granting access, this access method is called mandatory access control (MAC).
Regardless of the access control method you use, the end result is the ability to restrict access to objects by user account. Access control methods allow you to define an access control strategy that allows you to define controls to support your security policy.
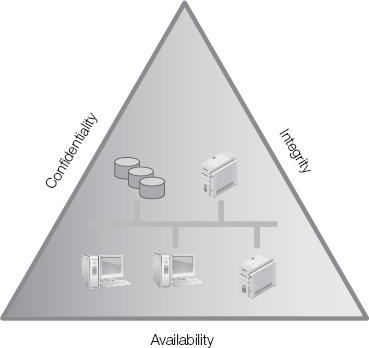
The overall purpose of compliance requirements is to enforce the basic pillars or tenets of security. Recall from Chapter 2 that secure environments satisfy the A-I-C properties of security. Although some compliance requirements might seem to be unnecessary, they all should work together to support the A-I-C properties of secure systems. As a review, here are the three tenets of information security:
Availability—Assurance the information is available to authorized users in an acceptable time frame when the information is requested
Integrity—Assurance the information cannot be changed by unauthorized users
Confidentiality—Assurance the information cannot be accessed or viewed by unauthorized users
Figure 9-3 shows the A-I-C triad.
Notice that a central theme of the A-I-C properties is the difference between authorized and unauthorized users. The identification, authentication, and authorization process you learned about in the previous section provides the foundation for securing information in any domain. Maximizing the A-I-C properties is all about ensuring authorized users can access trusted data and unauthorized users can't.
Secure information serves the purpose for which it was created. This means that secure information must be available when the information is requested. This requirement means that information should be available during normal processing, but also during and after unusual events. Unusual events include minor events such as short-term power outages up to major disruptions and disasters. There are two main areas in the Workstation Domain that can affect availability:
Surviving power outages
Executing a solid backup and recovery strategy
You should address each area when you create Workstation Domain controls.
The easiest way to ensure your computers and devices can continue operating in the event of a power outage is by using a UPS. The first step in implementing the right UPS is to list each of the computers and devices you want to protect. Consider any supporting devices you'll need along with computers. For example, if you want to stay online to the Internet during a power outage, you'll need to ensure you connect any network access devices to the UPS as well. Once you have a list of all devices, add up the power requirements for all devices you'll attach to the UPS. Then, search UPS manufacturers for a UPS that will satisfy your service and power requirements. An Internet search is a good place to start.
A UPS is fine to keep your computers up and running when the power goes out for a few minutes, but what do you do in case of a disaster? What happens to the programs and data on your Workstation Domain computers if a fire in your office destroys the computers? Fire is only one type of disaster your computers might encounter. Information that burns up in a fire or is destroyed in a flood is not available when you need it. Because the information isn't available in this situation, it isn't very secure.
You must have a plan to periodically create secondary copies of your important information. This secondary copy is often called a backup. Creating a backup copy of information is an important step, but only one step in a plan to ensure availability. The real key to ensuring availability is to have a plan for restoring your information to the state in which it existed before a disaster. Your backup and recovery strategy should include the following:
Backup plan—A plan to create frequent backup copies of important files. This plan includes identifying the files you need to back up, deciding on which backup utility to use, and setting a schedule for creating backups.
Safe media storage plan—A plan to protect your backup copies. This plan includes procedures for transporting backup media to a protected location. In most cases, you want to keep copies of your important information in remote locations to keep them safe from disasters that might affect your primary office. Consider keeping backup copies far enough away from your primary office that a disaster won't affect them. For example, a flood or earthquake can affect a large area. You may need to store backup copies far away, even in a different geographic region.
Restore plan—A plan to use the backup media to restore your environment to working order. This is often the plan most people overlook. You need backups, but you also need a plan that tells how to use the backups to build a working system.
The most important aspect of ensuring availability is to plan for situations that might disrupt your organization's activities and know what to do in those instances. Plan ahead and you won't likely be caught not knowing what to do when a disaster strikes.
The term "malware" refers to a collection of different types of software that share the goal of infiltrating a computer and making it do something. In many cases, malware does something undesired and operates without the explicit consent of the owner. This is not always the case, however. Some types of malware are downloaded and installed with the owner's full knowledge. Malware can be loosely divided into two main categories: programs that spread or infect and programs that hide.
Programs that spread or infect actively attempt to copy themselves to other computers. Their main purpose is to carry out instructions on new targets. Malware of this type includes:
Virus—A software program that attaches itself to, or copies itself into, another program for the purpose of causing the computer to follow instructions that were not intended by the original program developer
Worm—A self-contained program that replicates and sends copies of itself to other computers, generally across a network
Other malware hides in the computer to carry out its instructions while avoiding detection. Malware that tends to hide includes:
Understanding these five basic types of malware and how to protect your systems from them is important to a solid security plan. You install anti-malware software to protect Workstation Domain computers. There are many anti-malware software products from which you can choose. Carefully review suppliers and their products for costs, functionality, and support. The best place to look for specific anti-malware for your operating system is the Internet. Use an Internet search engine to search for "antivirus software" and "antispyware software."
Once you decide on one or more anti-malware products, you must develop procedures to ensure the products and their signature databases are kept up to date. With over 150 new viruses, worms, and Trojan horses being released every day, it is important your software be kept current to recognize as many new threats as possible. Up-to-date anti-malware software can help make your Workstation Domain computers more secure and able to ensure information integrity.
Because Workstation Domain computers may store sensitive or private information, it is important to protect the information from disclosure to unauthorized users. Two methods are commonly used to protect information confidentiality. Access controls can help ensure unauthorized users cannot access protected objects. The easiest way to deny access to anyone other than authorized users is through access permissions. If you only grant read and write access to authorized users, the operating system ensures the information's confidentiality. Regardless of your choice of access control methods, you can assign user accounts to enforce confidentiality.
There is a drawback with using operating system access control. It is possible for an attacker with physical access to a computer to boot the computer using alternate boot media. Most Workstation Domain computers have USB ports and CD/DVD drives. Either of these can support booting. If you insert a bootable CD/DVD or USB drive, many computers will boot from the alternate devices instead of the internal disk drive.
Booting from alternate boot media makes it easy to use tools to access files directly from the disk. If you boot from a CD/DVD or USB drive, you can bypass the operating system access controls and access any files you want. So, operating system access controls don't fully protect the confidentiality of your information. To protect private information at all times, you need to protect it even when the operating system isn't running. Only encryption provides that much protection.
Encrypting data makes it unreadable to everyone without the decryption key. You can encrypt all sensitive information and only provide the decryption key to authorized users. Attackers can still boot your computer using alternate media; however, they will only see encrypted files and will be unable to read their contents.
Tip
Each operating system supports encryption a little differently and some need third-party software to encrypt folders or entire drives. Explore how your operating system supports encryption and use it to secure private information.
Because Workstation Domain computers and devices are commonplace and plentiful, they make good attack targets. Workstations generally are not located in areas that are secure as devices in some other domains. They also exist in sufficient numbers that there is a high probability of finding vulnerable computers.
Although you can't make every computer and device totally secure, you can make them secure enough to frustrate all but the most determined attackers. In general, your computer environment doesn't have to be totally secure—just more secure than the attacker's next target. If you can get an attacker to give up and go on to another target, you have been successful.
One of the first attack activities is to identify a target machine's operating system and look for any known vulnerabilities. There are multiple methods attackers use to identify, or fingerprint, a target machine. Fingerprinting a computer means identifying the operating system and general configuration of a computer. Attackers will fingerprint a computer and use that information to identify known vulnerabilities for that operating system version.
Tip
Explore options for automatically acquiring and applying operating system patches. Automatic updates can reduce the administrative workload by ensuring the latest patches get installed on Workstation Domain computers.
It is important to keep your operating system up to date and patched to the latest version of your operating system. Applying the latest security patches eliminates many of the vulnerabilities attackers are looking for when planning attacks.
After fingerprinting, a computer attacker scans target computers for information on resident applications. Just like operating systems, applications may contain security vulnerabilities and provide attackers with an opportunity to compromise a computer. It is important to keep your applications up to date as well as your operating system.
Develop a plan to keep all applications up to date. Each application's provider may approach the update process differently. Some vendors provide automatic update notifications and others only report updates when directly queried. Know the update policy for each of your vendors. Create procedures to ensure you update all applications with the latest security patches. Keeping applications current will reduce the number of vulnerabilities on your computers and make it harder for attackers to succeed.
Workstation Domain computers and devices are often the most visible components to users. The majority of users access an organization's applications and information using Workstation Domain computers. That means Workstation Domain computers and devices tend to interact with users a lot. Many security issues result from user errors and can be addressed with proper training. However, training can only address some of the security issues related to users. Eventually, an untrained, unmotivated, or careless user will violate security policy and will take action that causes a security incident. The incident might be large or it might be very small and unimportant. Regardless, it is important to employ multiple layers of controls to ensure security does not rely on any single control. Even organizations with very effective training programs encounter problems that users create.
A solid security policy should define multiple layers of controls working together to keep your information secure. Your security policy should direct security activities and state standards that maintain compliance with legislation, regulations, and any other state requirements. Following procedures and guidelines should always result in fulfilling your security policy as well as any other organizational policies.
Periodically, an organization should assess its adherence. To accomplish this, an organization can perform a gap analysis to determine what holes might exist in how it enforces the security policy. Specifically, the organization compares the present situation with the desired situation. Once identified, the gap between is used to create actionable tasks.
Procedures define the steps necessary to fulfill the intent of the security policy. The Workstation Domain procedures can cover many aspects of maintaining computers and devices, but should include the following:
Change password procedure
Logon/logoff procedure
Backup procedure, including handling backup media
Recovery procedure
Update operating system and application software procedure
Maintaining private data procedure
Malware alert procedure
Grant/deny object access procedure
Procedures provide the step-by-step instructions for fulfilling the security policy but cannot include every variable. In some cases, you have to make decisions based on the information at hand. In these cases, guidelines help make decisions that still comply with your security policy and any other organizational policies. Workstation Domain guidelines can include:
Strong password guideline
Document-naming guideline
Printer use guideline
Software installation guideline
Handling backup media guideline
Internet use guideline
Use operating system controls whenever possible to enforce Workstation Domain policies. These controls will not fulfill all aspects of the security policy, but they will provide a solid foundation for ensuring your information's security. Controls you will find in most current operating systems include:
General object access permissions
Shared object access permissions
Private object access permissions
Printer permissions
Audit logging settings
Authentication requirements
User rights
Taken together, policies, procedures, and guidelines provide the instructions and limits that enable your users to comply with your security policy when using components of the Workstation Domain. Even though you design and deploy controls to limit user actions, you still should deploy additional controls to detect noncompliant behavior. Use your operating system's access audit logging features to keep log files of interesting object access requests. Carefully consider which objects you want to audit. Auditing access requests for all objects will slow your computers down and waste disk space. Identify the objects that contain sensitive or private information and enable audit logging for those objects.
Note
Reviewing audit logs will show how users are using Workstation Domain computers and devices. The audit process uses these log files to validate that usage complies with your security policy.
A second useful technique during an audit is to compare a snapshot, or baseline, of a computer or device as it currently appears with a baseline from a previous point in time. Any differences between baselines could indicate unintended changes and possible vulnerabilities. Your audit plan should include procedures to create periodic baselines you can use to detect unwanted changes to your computers and devices. A baseline can contain many types of information, but should include the following information:
Users and settings
Groups and members
File list with access permissions
Access control lists
Configuration settings for important applications and services
Installed application list
Startup/shutdown and logon scripts or batch files
Network adapters and configuration
You should include any other information that describes the configuration of a specific computer. One of the easiest ways to create baselines is to include the commands that list the desired information in a script or batch file. You can compare saved output from any baseline to see configuration changes between snapshots. Creating periodic baselines supports the overall audit process to ensure compliance with stated security goals.
Workstation Domain computers and devices provide local computing resources and often provide initial access into your organization's shared resources. It is important to maintain a secure Workstation Domain both for the security of the locally stored information but also to keep other domains secure. Allowing Workstation Domain components to be insecure increases the vulnerability for other domains you access from workstations. There are many strategies for keeping the Workstation Domain secure. Each organization should customize their Workstation Domain policies, procedures, and guidelines for their specific set of requirements. If the organization is a federal entity, compliance with the NIST 800-53 standard is mandatory. The assessment of those controls is covered in depth in guideline NIST 800-53a. Here are general guidelines and best practices to attain and maintain compliance within the Workstation Domain:
Require unique user accounts for each person. Do not allow multiple people to use the same user account.
Require strong passwords and train users on the importance of keeping passwords private. Require users to change passwords at a specified interval, such as every six months.
If one person performs duties of several roles, create a unique user account for each role.
If using DAC, assign object permissions for all shared objects to grant access only to necessary subjects.
If using MAC, establish simple standards for assigning security classifications to objects.
Create a backup schedule that minimizes the amount of work that would be lost if a disaster destroyed the computer just before the next backup.
Document procedures for labeling, transporting, storing, and reusing backup media.
Document the steps necessary to restore your system from a backup after data loss.
Test your recovery procedure at least every six months.
Test the power outage operation of your UPS at least monthly.
Conduct informal monthly audits that include creating monthly baselines.
Check for anti-malware software and signature database updates daily.
Scan for operating system and application updates at least weekly.
Audit users, groups, and access permissions/data classification at least quarterly.
Although this list of best practices is not exhaustive, it is a good foundation to keep Workstation Domain computers and devices secure.
The Workstation Domain contains computers and devices that provide the primary interface for most users. Many information systems users access local and networked resources from computers in the Workstation Domain. Securing components in this domain has a dual effect of securing information on individual workstations and helping to avoid introducing vulnerabilities into the organization's network.
You learned about the importance of access controls, maximizing the A-I-C properties of security, and backing up and restoring information. You also learned strategies for staying malware-free and keeping the operating system and application software up to date. The tasks necessary to keep the Workstation Domain secure cover several areas and require diligence. The result is a domain that supports your organization's business functions and keeps your information secure.
A-I-C
Access control lists (ACLs)
Authentication
Authorization
Availability
Card Verification Value (CVV)
CIA
Due diligence
Fingerprinting
Identification
Multifactor authentication
Object
Owner
Permission
Subject
Two-factor authentication
Type I authentication (what you know)
Type II authentication (what you have)
Type III authentication (what you are)
Uninterruptible power supply (UPS)
War dialing
_______ means the ongoing attention and care an organization places on security and compliance.
PCI DSS allows merchants to store the CVV number.
True
False
Which of the following choices protect your system from users transferring private data files from a server to a workstation? (Select two.)
Increase the frequency of object access audits.
Deliver current security policy training.
Place access control to prohibit inappropriate actions.
Enable access auditing for all private data files.
Some attackers use the process of _______ to find modems that may be used to attack a computer.
Which security-related act requires organizations to protect all personal medical information?
HIPAA
GLBA
SOX
SCM
A data DVD can store up to 256 GB of data.
True
False
Which of the following is the process of verifying credentials of a specific user?
Authorization
Identification
Authentication
Revocation
Which of the following is the process of providing additional private credentials that match the user ID or username?
Authorization
Identification
Authentication
Revocation
A security token is an example of _______, or "what you have," authentication.
Which access control method is based on granting permissions?
DAC
MAC
RBAC
OAC
The _______ property of the A-I-C triad provides the assurance the information cannot be changed by unauthorized users.
What are the types of malware? (Select two.)
Programs that actively spread or infect
Programs that slow down data transfer
Programs that cause damage
Programs that hide
A _______ is a type of malware that is a self-contained program which replicates and sends copies of itself to other computers.