ORGANIZATIONS ARE BECOMING more diverse and dispersed. Many organizations that used to conduct business from a single, central location or a small number of locations are now finding themselves spread out across many areas. Employees work from home and while on the road. Customers and partners need access to central information to maintain their business relationships. Many organizations are finding that supporting remote access to their data is a primary requirement for doing business in today's global economic environment. Both applications and users are placing increasing demands to access data from remote locations, often using untrusted wide area networks (WANs). Extending trust to remote users requires more planning and effort but provides the basis for keeping data secure regardless of how far it travels.
Securing data as it travels from your protected internal network across an untrusted WAN to remote users depends on the ability to trust in the identity those users provide. Not only do you establish trust when you establish a connection, but also you establish trust throughout the conversation. You need to trust the user or entity on the other end of a connection during each data exchange. The purpose of the Remote Access Domain is to provide mechanisms to establish and maintain trust between remote users and components within other domains in your organization. In this chapter, you'll learn about the Remote Access Domain, the components commonly found in the domain, and techniques to keep the domain secure and compliant.
Empowering users from many locations to use resources that might not be located near them makes economic sense. In most cases, shared resources are less costly than duplicated resources. Of course, sharing resources only makes sense if you can do it securely in a way that supports your business functions. Providing effective and secure access for remote users and resources is the primary focus of the Remote Access Domain.
This domain contains the components that can bring your distributed environment together and make its resources available and useful to remote users. When your organization provides this level of service, you are enabling remote users to operate more effectively and efficiently without having to physically be at your main location.
This capability is a benefit to users who are geographically separated from your physical resources either permanently or temporarily. Your users can do their jobs from more locations if they can access your resources remotely. The Remote Access Domain provides the access path for your remote users. Figure 13-1 shows the Remote Access Domain in the context of the seven domains in the IT infrastructure.
Take necessary steps to secure your data in all seven domains of the IT infrastructure. Distributing your data far from its secure storage locations exposes it to more threats of attack. You'll likely need to show compliance with one or more requirements that directly address sensitive data sent to remote users. For example, the Health Insurance Portability and Accountability Act (HIPAA) requires controls to protect the privacy of medical data. The Payment Card Industry (PCI) requires credit card privacy controls. Many states require privacy controls on any personal identifiable data. These are only a few of the requirements you'll need to satisfy when supporting remote users. Your security policy should include all of the necessary elements to meet compliance requirements and support efficient and cost-effective operation. Making sure you have the proper controls in place to secure the Remote Access Domain is one important part of an overall plan for data security.
The primary security concern for remote access is data privacy. Although availability is important, confidentiality and integrity get far more attention in compliance requirements. The most important consideration when allowing remote users to access data is ensuring private data remains private. Ensuring data privacy essentially means only allowing authorized users to view or modify it. Because remote users commonly use public WANs to access data and applications, keeping sensitive data away from unauthorized users is difficult, if not impossible.
Your organization does not control access to your data in the WAN. The WAN service provider is responsible for controlling access to the traffic it transports. Although you should establish a level of trust with your WAN service provider, you can't enjoy the same level of privacy assurance as you do for data inside your own networks. However, you still must protect the privacy of your data even in the WAN. The specific controls you use are not important. The important goal is to ensure the privacy of your data does not suffer when it is transmitted to remote users.
The most common control for protecting data privacy in untrusted environments is encryption. Recall that encryption is the process of scrambling data in such a way that it is unreadable by unauthorized users but can be unscrambled by authorized users to be readable again. Encrypted data ensures only users who possess the decryption key can properly decrypt a message. When you only provide decryption keys to authorized users, you protect data from being accessed by unauthorized users.
You must encrypt sensitive data before sending it to a remote user or location to ensure compliance with all appropriate requirements. Technically, you can send data that is not considered sensitive in the clear. However, classifying data at run time is time consuming and increases the potential to miss sensitive data and accidentally send it in the clear, or unencrypted. It is generally easier and more consistent to encrypt all data transferred in a session. Although you can use a variety of methods to decide what data to encrypt, there are three main strategies for encrypting data to send to remote users:
Application data encryption—The application determines what data should be encrypted and encrypts it. The client application on the remote side decrypts the data and presents it to the user. This method of encryption requires substantial effort and overhead but can avoid encrypting data that does not need it.
Application connection encryption—The application requires clients use secure connections when exchanging data that might be sensitive. An example is the payment screen of an e-commerce application. Although your application may allow customers to shop using unencrypted connections, using Hypertext Transfer Protocol (HTTP), payment process requires a secure connection, using Hypertext Transfer Protocol Secure (HTTPS). The application validates the connection type, not the actual data. This strategy requires less application interaction than application data encryption and still offers assurance of data privacy. One drawback is the reliance on the connection encryption strength to ensure data privacy. If the connection is not configured well, your data could be at risk.
System connection encryption—The third strategy does not require any application intervention or changes at all. The connection with the remote user handles the encryption. The most common way to implement system connection encryption is by setting up a secure virtual private network (VPN). A secure VPN encrypts all traffic on the connection. The system encrypts the data before placing it on the VPN at the endpoint and it is decrypted after it is removed from the remote endpoint. VPNs are useful because they allow any type of application to transfer data across an untrusted network without sacrificing data privacy.
Your budget and the operating systems you support will have an impact on which encryption strategy you select. Each strategy has many choices, each with benefits and challenges. Choose the best option to fit your needs. One of the most popular options to ensure data privacy for remote users is the VPN. Examine the VPN choices available for your environment and select one that meets your security needs.
Although the most common security control in the Remote Access Domain is encryption, don't forget the controls on remote users and the computers they use to access your network from a remote location. Remote users must adhere to your remote access acceptable use policy (AUP). Encryption can help protect your sensitive data, but a user who isn't careful or a poorly secured laptop can leave the data vulnerable once it gets onto the remote computer. You'll learn more about the vulnerabilities associated with each Remote Access Domain component in the next section. Make sure you protect all components with the best controls.
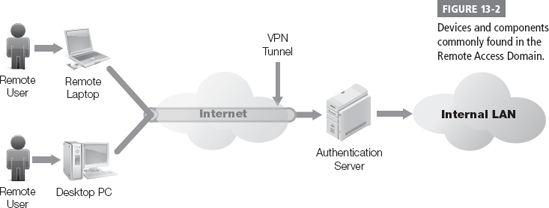
The Remote Access Domain provides access to remote users and remote resources. It exists, in part, to provide a secure way to exchange data with remote components without sacrificing data privacy. This domain consists of several components that work together with your WAN to ensure your data is private and your environment is compliant. Figure 13-2 shows the devices and components commonly found in the Remote Access Domain.
The first component of the Remote Access Domain is the remote user. A remote user is a person who connects to, and accesses, resources or applications from a remote location using a WAN to connect. The first remote users used dial-up connections to access computers and networks remotely. Personnel who traveled often needed to access data from the organization's central database when they were away from the office.
This example is a classic case for remote access. The classic solution to this need was to provide a modem, or bank of modems, attached to the internal network. Users could dial in and access resources just like local users. The growth of high-speed networks and the Internet have changed the connection methods but not the basic requirements and problems.
Remote users pose several problems for data privacy. Those problems that are most common with remote users are:
Remote users connect to an organization's resources using untrusted networks. Whether you use the Internet or some other WAN, your network traffic flows across someone else's networks and may be intercepted along the way. If there is a packet sniffer on the WAN, you won't know others are examining your traffic.
Remote users often use public computers or terminals. Many travelers use business center computers in hotels to access the Internet and other resources. Users leave traces of their activities on computers used to access networks. It is possible that users leave traces of sensitive data after accessing it from a remote location.
Remote users can be sloppy. You must have a strong remote access AUP in place that sets standards for how remote users handle data. Remote access introduces more risk because the data is transferred away from the protection of your organization's internal controls. Ensure you deploy controls that protect your data all the way to a remote user's computer—and once it is there.
Remote user access should require a higher standard of care than local user access. Local users enjoy the additional protection of the local environment and its security controls to protect data. Remote users do not have the additional layers of protection. You must ensure your users agree to comply with your remote access AUP and you have sufficient controls in place to protect the security of your data even in remote locations.
Remote users are really just normal users who access resources and applications from a remote location. They use workstations or laptops to establish the connection to the desired resources. In short, the remote user logs on to a computer. The computer accesses a WAN and uses it to establish a connection with other resources. The computer, laptop, or other device becomes the remote device. Remote devices aren't special devices—they just have the ability to connect to a WAN and establish a connection to some other resource. In fact, more and more personal digital assistants (PDAs) and smartphones contain the capability to act as remote devices.
Remote devices need two main capabilities to handle remote connections in a secure manner:
Remote devices must be able to handle encryption. The most common type of encryption used in remote access is the secure VPN. As long as your device supports the VPN you've chosen for remote access and can establish a secure connection, the device passes the first test.
Remote devices must be able to protect stored data. Even when using a VPN, the data gets decrypted when it arrives at the remote device. If your remote device can't ensure data privacy through its own controls, it should not be allowed to retrieve or process your confidential data.
As computers and other devices mature, it is common to see VPN support and local data privacy protection as standard features for computers. You can use operating system encryption or third-party utilities to encrypt data. Either way, most of today's computers with recent operating systems already contain the ability to act as secure remote access devices.
Enabling remote access depends on both the remote devices and the remote servers cooperating. Because remote access depends on one endpoint at the remote location and another endpoint in your local environment, the Remote Access Domain actually spans several domains. By definition, the Remote Access Domain components use the WAN Domain to communicate. The Remote Access Domain server components also generally reside in the LAN-to-WAN Domain environment, even though they still belong to the Remote Access Domain.
When a remote user wants to access the organization's internal network, the remote device requests a connection from the remote access server. The remote access server queries the remote device for identification and authentication credentials. If the identity authenticates, the remote access server grants a connection and rights based on stored authorization information. Figure 13-3 shows the remote connection process.
The basic steps don't really differ much from a local logon process. The main difference is that the three basic steps are handled by the remote access server. Once a remote user successfully connects, the user can access resources like any other user. The three basic steps required to establish a remote connection are:
Identification—The remote user provides a user ID or user name.
Authentication—The remote access server prompts the remote user for authentication credentials. These credentials can be a password, a PIN, a smart card, or data from a biometric reading. The remote access server looks up the stored authentication information for the supplied user. If the authentication credentials provided by the user match the stored credentials, the user is authenticated.
Authorization—Depending on the type of remote access server, the authorization information may be stored with the authentication information or may be stored in a separate location. In either case, the remote access server looks up the authorization information for the authenticated user and assigns rights and privileges based on the remote user's security settings.
The process in the previous section describes how the authentication process works for remote users. There are many ways to authenticate remote users, but three main approaches are used most often. The first two, RADIUS and TACACS+, rely on centralized authentication databases and servers to handle all remote users. Either of these approaches works well when there are a large number of remote users or you need to manage remote users in a central location. You'll learn about the third method in the next section.
Remote Authentication Dial In User Service (RADIUS) is a network protocol that supports remote connections by centralizing the management tasks for authentication, authorization, and accounting for computers to connect and access a network. RADIUS is a popular protocol that many network software and devices support and is often used by Internet service providers (ISPs) and large enterprises to manage access to their networks.
RADIUS is a client/server protocol that runs in the application layer and uses User Datagram Protocol (UDP) to transport authentication and control information. Servers with RADIUS support that control access for remote users and devices communicate with the RADIUS server to authenticate devices and users before granting access. In addition to just granting access and authorizing actions, RADIUS records usage of network services for accounting purposes.
Note
The application layer is layer 7 in the Open Systems Interconnection (OSI) reference model, or layer 4 in the Transmission Control Protocol/Internet Protocol (TCP/IP) reference model.
Terminal Access Controller Access-Control System Plus (TACACS+) is another network protocol that was developed by Cisco. TACACS+ has roots back to an earlier protocol, TACACS, but is an entirely different protocol. TACACS+ provides access control remote networked computing devices using one or more centralized servers. TACACS+ is similar to RADIUS in that it provides authentication, authorization, and accounting services, but TACACS+ separates the authentication and authorization information. TACACS+ also uses the Transmission Control Protocol (TCP) for more reliability.
One difference between RADIUS and TACACS+ is of interest to a discussion of security. RADIUS only encrypts the password when sending an access request packet to the server. TACACS+ encrypts the entire packet. That makes it a little harder to sniff data from a TACACS+ packet.
VPNs are one of the most popular methods to establish remote connections. A VPN appears to your software as a regular network connection. It is actually a virtual connection, also called a tunnel, that uses a regular WAN connection of many hops but looks like a direct connection to your software. Most VPNs offer the option to encrypt traffic using different modes to meet different needs.
The concept of tunneling is central to most VPNs. Tunneling allows applications to use any protocol to communicate with servers and services without having to worry about addressing or privacy concerns. Applications can even use protocols that aren't compatible with your WAN. Here's how tunneling works:
Your application sends a message to a remote address using its application layer protocol.
The target address your application used directs the message to the tunnel interface. The tunnel interface places each of the packets from the application layer inside another packet using an encapsulating protocol. This encapsulating protocol handles tunnel addressing and encryption issues.
The tunnel packet interface then passes the packets to the layers that handle the WAN interface for physical transfer.
On the receiving end, the packets go from the WAN to the remote tunnel interface where the packets are decrypted and assembled back into the application layer packets and then passed up to the remote application layer.
This arrangement provides excellent flexibility and security. Depending on your operating system and VPN solution choices, you can choose from among several encapsulating protocols, including:
Generic Routing Encapsulation (GRE)—A tunneling protocol developed by Cisco Systems as an encapsulating protocol that can transport a variety of other protocols inside IP tunnels
Internet Protocol Security (IPSec)—A protocol suite designed to secure IP traffic using authentication and encryption for each packet
Layer 2 Forwarding (L2F)—A tunneling protocol developed by Cisco Systems to establish VPNs over the Internet. L2F does not provide encryption—it relies on other protocols for encryption.
Point-to-Point Tunneling Protocol (PPTP)—A protocol used to implement VPNs using a control channel over TCP and a GRE tunnel for data. PPTP does not provide encryption.
Layer 2 Tunneling Protocol (L2TP)—A tunneling protocol used to implement a VPN. L2TP is a newer protocol that traces its ancestry to L2F and PPTP. Like its predecessors, L2TP does not provide encryption itself.
The VPN you select depends on several factors. Some VPN solutions are vendor specific and rely on one type of hardware. Other types of VPNs are operating system specific. For example, the new Secure Sockets Tunneling Protocol (SSTP) is only available for the Windows operating system. SSTP is Microsoft's attempt to provide a solution that works on any networking hardware. SSTP uses Secure Sockets Layer (SSL) to transport PPP or L2TP traffic. Using SSL removes many of the firewall and network address translation (NAT) issues some other protocols encounter. Once you have assessed your needs and environmental restrictions, select the VPN solution that best fills your needs for functionality, security, and maintainability.
One of the more common ways to establish remote connections is using the Internet. Because it is easy to establish Internet connections and the access points are numerous, it makes sense to at least consider it for your remote connections needs. Historically, there have been several issues that must be resolved to use the Internet as a remote access WAN:
Both sides of the connection must use the same WAN. When using the Internet as the WAN, all each side must do is establish an Internet connection. The LAN-to-WAN Domain already ensures your internal networks are connected to your WAN. All that is left is for the remote node to connect.
Because the Internet is a public use network, encryption is an absolute necessity. VPNs work well to transport data securely over the Internet.
Reliable access must be available for remote nodes. Internet access is becoming easier to find than ever before. Many Wi-Fi hotspots exist to allow computers and devices to connect to the Internet.
Remote connections must be fast enough to be usable. This requirement is one that will likely cause the most potential issues. Internet service is easy to find and it is easy to use VPNs. Sometimes, especially in more remote areas, it is difficult to find high-speed Internet access. In such cases, it is important to provide access through low-bandwidth methods to ensure data availability.
Although the Internet might not be the fastest WAN, it is fast becoming the most cost-effective medium and the easiest use for remote connections.
The last point in the previous section regarding Internet access was speed. Historically, most users connected to the Internet by dialing into an ISP modem. Modems are rated at speeds as high as 56 kilobits per second (kbps), although real transmissions rarely sustain the maximum data rate. Even at the highest rate, interacting with remote resources can be slow. As the volume of data that needs to be exchanged increases, dial-up connections become more and more frustrating for remote users.
The alternatives to dial-up include broadband techniques that substantially increase the network connection speed. Broadband refers to the technique of only using a portion of the full bandwidth of a channel. Dial-up connections use baseband techniques that require the entire channel's bandwidth. Broadband Internet access is defined as any customer connection that provides service at 256 kbps or higher. Many ISPs now provide asymmetric digital subscriber line (ADSL), cable, wireless, cellular, and satellite connections that classify as high-speed, or broadband, Internet service. The proliferation of broadband connections makes using the Internet for remote connections an even more attractive option.
Any time you allow remote access to your internal protected local area network (LAN) by remote users, you increase the risk of security violations. It is important that you know who is using the remote access features you've enabled to access your resources. There's a lot you can monitor with respect to remote access, but the best place to start is by identifying and validating just who is using remote access. There are at least three activities of interest you should be monitoring:
Create VPN connection—Your VPN server has the ability to track both successful and unsuccessful VPN connection requests. Although auditing all connection requests can create a large amount of information, it can also provide valuable information on how remote users are accessing your resources. Know who is using your resources, where those people are connecting from, and how they are using your VPN.
Remote access connection—Once a remote user establishes a VPN, it is also interesting to see what they're doing with it. You can audit resource connections to see how remote users and resources are using your VPN. You should also audit non-VPN remote connection requests. Unless you're using a non-VPN encryption solution, all non-VPN remote connection requests should be denied.
Remote computer logon—Another interesting piece of information you should audit is any remote logons to your computers or devices. Each operating system contains functions to audit logons. In fact, the operating systems can audit much more than just logons. You should be auditing access to sensitive resources at some level. As with all auditing activity, don't audit more than you need. Audit log files can become very large.
The overall idea is to keep track of who is using your VPNs and what they are doing. For example, assume your primary VPN is optimized for large volumes of small messages. Your expectation when you enabled the VPN was that users would use it to access your online order management system. VPN and remote access monitoring has shown you that most VPN users are running very large custom reports from your database to analyze data. The VPN is actually transporting large volumes of data for a relatively small number of users. You find that you can change some VPN settings that make it run faster for the way your users are using the VPN. Reports run faster and your data is more available. Table 13-1 lists a few programs that help monitor remote access and VPN usage.
Table 13-1. Remote access and VPN monitoring tools.
SOURCE | |
|---|---|
CodePlex Remote Access Monitor (Open source) |
|
SoftSea Remote Access Monitor (Free) |
|
Cisco VPN Monitor |
|
SNMP | Not a vendor-specific product |
The last entry in Table 13-1 is the Simple Network Management Protocol (SNMP). SNMP is a network protocol used to monitor network devices. Most network devices include SNMP support and can run SNMP agents to report conditions that require attention by another computer or device running network management system software. SNMP uses UDP protocol messages to retrieve information from network devices and for the devices to send updates when conditions you define are met. Although there are many ways to use SNMP, you can configure devices to send an alert to the network manager when remote users connect to your network.
Monitoring connections and events related to remote access users is important to learn about who is accessing your network from remote locations. But to ensure your VPNs are configured to best utilize your VPN bandwidth, it is important to monitor the traffic flowing along your VPNs. Although you can't monitor the contents of traffic in encrypted VPN tunnels, you can monitor traffic statistics to understand how well your remote users are utilizing VPN bandwidth. You can also detect unusual VPN activity that could indicate malicious activity or excessive use.
Because both endpoints are within domains in your IT infrastructure, you can monitor decrypted packets once they emerge from the end of the VPN tunnel. It is important to note that monitoring VPN traffic does not replace any other types of network monitoring.
It is still important that you monitor WAN traffic to understand how your organization uses your WAN connections. VPN traffic monitoring provides additional information on how individual tunnels are behaving within your overall WAN usage. Excessive WAN usage might indicate a network usage problem. Further investigation using VPN monitoring could reveal that one remote user using a VPN is attempting to launch a denial of service (DoS) attack on your organization. In this case, WAN traffic monitoring revealed a high-level problem and VPN traffic monitoring revealed the cause of the problem. You need to monitor at both levels to get the whole picture.
You can implement VPN traffic monitoring and analysis using the same methods as LAN and WAN traffic monitoring and analysis. You can install software or devices on the perimeter of the VPN where you establish the endpoint. You can also use any of a wide variety of network management software packages that support SNMP to monitor traffic directly from the network devices that transport VPN traffic. Regardless of the methods you employ, monitoring and analyzing VPN traffic is important to ensure your private data is secure and compliant.
You learned about the importance of managing network configuration settings in the previous chapters on the LAN, LAN-to-WAN, and WAN Domains. Managing the changes to your VPN and remote access configuration is crucial to maintaining a secure environment for remote users and resources. Just as with devices and computers in other domains, ensure that you control configuration changes to Remote Access Domain components, including:
VPN client software
Authentication servers
VPN servers
Remote access servers
Network management system servers
The strategies and techniques for managing configuration settings and controlling configuration changes should match your activities in the LAN, LAN-to-WAN, and WAN Domains. Refer to Chapters 10, 11, and 12 for more information on proactively managing configuration setting changes. Just as with other domains, managing the configuration settings of your Remote Access Domain components is an important part of keeping your overall environment compliant and secure.
Managing remote access components means ensuring each one fulfills the goals for which it was designed. It also means to continually update your configuration to satisfy new and updated goals. Remote access management covers several related activities, including:
Authorizing users and nodes to connect remotely
Verifying privacy settings are in place
Monitoring VPN performance
Changing configuration settings to optimize performance
Changing configuration to support new requirements
Adding necessary controls to address security issues
Maintaining components of a current recovery process
Adding, changing, and removing hardware components as requirements dictate
The specific tools and procedures you use to manage remote access components depend on the operating systems and products you use. Configuring remote access users is similar to configuring local users. In fact, remote access settings are generally just additional configuration settings for regular users. For example, in Microsoft Windows Server 2008 R2, you enable remote desktop connections on the server machine and define authorized users using the "Remote" page of the System Properties window. Then you can define a Group Policy object for users or groups that define specific settings for remote sessions. Figure 13-4 shows the Start a Program on Connection setting in the Group Policy Management Editor.
In addition to operating system settings, some remote access authentication and authorization products require additional configuration information. Learn what your environment requires to define and configure users and devices for remote access. Most network device vendors have their own management software. The remaining management tasks are similar to tasks in the LAN and LAN-to-WAN Domains. The main focus is on ensuring you configure each network device properly and optimally.
Explore options for VPN monitoring and management software for your operating system and network devices. Software that assists your network administrators will likely simplify managing your VPNs and make it easier to validate compliance with your stated security goals.
The degree to which you grant rights and permissions to remote users depends on your general access model and your operating system. In most cases, remote users accessing your environment via a VPN enjoy the same rights as users on your LAN. The idea behind a VPN is that once it is established, it operates just like a LAN. VPN users are essentially the same as other LAN users. Although it is possible to exclude some users from accessing your network using a VPN at the operating system level, it is generally easier to use the remote access authentication server to define which users can use remote access.
The main goal for all networking issues is to keep things simple. Complexity leads to an increased exposure to risk and requires more effort to maintain. Try to keep three lists of users: internal network users, remote access users, and global users. If you don't need to separate most local and remote user rights, then just defining a global user list keeps things simple. Once you create the users, you'll need to support remote access; your operating system provides the ability to define what each user can do through permissions or access control lists (ACLs). Refer to Chapter 8 for a discussion of user rights and permissions in the User Domain.
Warning
Do not include administrative users in a global user list. If you do allow remote administration, you should create administrative accounts specifically defined for remote administration. This practice makes auditing and controlling remote users with elevated privileges easier.
In addition to user rights, your remote access servers can define how you handle remote connections. You should set up VPNs to appear as networks that are separate from your physical LANs. Defining all VPNs in a specific range of subnets gives you the ability to define filtering or access rules that affect just your VPN connections. Defining rules for VPNs gives you the ability to identify and filter suspicious traffic or any traffic that is not authorized. For example, suppose you want to prohibit remote users from using Server Message Block (SMB) to map network resources as shares. You could set a rule in a firewall that sits between your VPN endpoint and your LAN to drop any TCP traffic for the default SMB port, 445. in this way, you prohibit any SMB access from your VPNs.
You can use user rights, permissions, ACLs, and firewall rules to restrict what remote users can do. Document what you'll allow remote users to do and use the appropriate controls to enforce your rules. The more remote users can do increases the risk to your data security. Allowing remote users to access your environment can increase your organization's effectiveness at the risk of reducing your overall security. Ensure you have the necessary controls in place to limit what remote users can do and to ensure your data is safe regardless of where it travels.
Validating compliance in the Remote Access Domain includes validating the controls that satisfy compliance requirements. With respect to the Remote Access Domain, most compliance concerns focus on data privacy. It is important to evaluate all controls to ensure all three properties of the availability, integrity, and confidentiality (A-I-C) triad are satisfied. There are three main areas of concern in the Remote Access Domain: client-side configuration, server-side configuration, and configuration management verification. Each area focuses on a slightly different component of the Remote Access Domain. Taken together, validating these three areas provides assurance that components in your Remote Access Domain are compliant with the necessary requirements.
Each VPN client stores configuration details to connect to the organization's VPN server. Typically, VPN details include information such as:
Host name or address (primary and backup)
Logon user name
Password (optional—dependent on authentication method)
Authentication method
Transport protocol
Local address options
Local log settings
Each of the client settings should match the server settings. In some cases, servers support multiple types of clients and will negotiate settings, such as authentication method and transport protocol. It is important that you verify each client's settings to ensure clients are in compliance with organizational VPN settings standards. One of the easiest ways to verify client settings is to restrict your server settings to deny any connection requests that fall below certain standards. If your clients meet the standards, they can connect. If not, their connections fail.
There are two types of access controls for remote access. The first are the access controls for computers or devices. These access controls define which computers or devices can establish remote connections. Your authentication servers or VPN servers store computer and device access controls. The location depends on the type of VPN and operating system you are using. The second type of access control is at the user or group level. This type of access control is the same as access control in the User Domain. Once a remote user authenticates and is authorized to access resources, the normal operating system access controls take effect.
Most Web development languages and many applications have the ability to require secure connections. For example, you can require that a particular Web page or cookie can only be sent to a client using a secure connection. If the client attempts to render a secure Web page using an insecure protocol, the page does not render. You would have to use HTTPS to render the page. In other words, you would have to use HTTPS in the address to reach the page.
Warning
Consult the setup and configuration guide for your Web server. Some Web servers enable all encryption modes by default, including a debugging mode that actually doesn't encrypt traffic. If you leave this option enabled, attackers can trick your Web server into sending private data without using Secure Sockets Layer/Transport Layer Security (SSL/TLS) with encryption. Unless you're using a VPN, the Web server sends the data in the clear.
To verify compliance with data privacy for remote users, you should enforce the following:
All Web pages that access sensitive data require secure HTTPS connections or have local host addresses.
Local host addresses for Web pages require VPN connections.
Require all users authenticate before accessing any resources or data.
Only VPN nodes can access sensitive data directly.
Operating system-and application-specific access controls define which users can access sensitive data.
Adhering to these rules will ensure your data is safe from unauthorized remote users.
Warning
When using encryption between Web browsers and Web servers, always require 128-bit SSL/TLS encryption. Older algorithms only used 40-bit encryption that is easily compromised. If your Web server still supports 40-bit encryption, an attacker can force the weaker encryption and compromise your data.
You learned about the FCAPS approach to network management in Chapter 11. Recall that the "C" in FCAPS stands for configuration. You can use the same tools, such as the RANCID and Canner as mentioned in Chapter 11, to help manage VPN configuration settings. Managing all your network devices' configuration settings keep unauthorized changes from reducing your data's security. RANCID and Canner, along with other available tools, can help you create baselines of configuration settings and compare changes over time. You should develop a schedule and process to frequently compare configuration baselines and verify all changes to your network's configuration.
Recall that a solid network configuration management process includes managing changes to all configuration settings. A formal process makes it easy to classify any configuration changes as authorized or unauthorized. You just compare baseline differences to your authorized changes list to see which changes occurred that were not authorized. Implementing the FCAPS approach across all your networks will help formalize the process and make your networks more secure.
Table 13-2. Common compliance controls in the Remote Access Domain.
Security doesn't just happen. A secure environment is the result of solid plans and faithful adherence to those plans. If your organization takes the time to plan the best ways to achieve compliance and security assurance, it makes the most sense to follow the plans. Each component of your plans should address one or more of the basic A-I-C properties of data security. As you select and deploy controls, ensure each one supports your organization's security policy. Many organizations end up deploying controls that seem good but are not indicated in their policy. Such a situation indicates either the control is not needed or the policy needs amending. In either case, your controls should be the result of enacting your security policy. Above all else, it is important that your security policy be current and complete. Table 13-2 lists the types of controls you'll likely need to ensure are compliant in your Remote Access Domain.
These controls won't meet every compliance goal but will satisfy many current compliance requirements and make your Remote Access Domain more secure.
The Remote Access Domain opens applications and resources to remote users. Doing so has the potential for exposing your internal environment to more threats. Because this domain commonly connects remote users to your environment using an untrusted WAN, you must ensure the controls protect your internal resources. Selecting, deploying, and managing the right security controls can provide efficient and secure access across an untrusted WAN.
This list of best practices covers the most common suggestions and goals many organizations have found helpful in securing the Remote Access Domain. These pointers will help you get started to develop a plan and select the right security controls to ensure your remote users enjoy a high level of service without sacrificing your data's security:
Map your proposed remote access architecture, including redundant and backup connections. Use one of the several available network-mapping software products to make the process easier.
Update the network map any time you make physical changes to your network.
Install at least one firewall between your VPN endpoint and your internal network.
Select a VPN provider that your clients can easily access. If you select a vendor-specific VPN solution, develop a method to distribute and maintain the VPN client software to your users.
Use global user accounts whenever possible.
Use strong authentication for all user accounts.
Create a limited number of administrative accounts with permissions for remote administration.
Develop a backup and recovery plan for each component in the Remote Access Domain.
Don't forget to include configuration settings for network devices in your backup and recovery plans.
Implement frequent update procedures for all operating systems, applications, and network device software and firmware in the Remote Access Domain.
Monitor VPN traffic for performance and suspicious content.
Carefully control any configuration setting changes or physical changes to domain nodes.
Update your network map after any changes.
Require encryption for all communication in the Remote Access Domain.
Enforce anti-malware minimum standards for all remote computers as well as server computers in the Remote Access Domain. Ensure all anti-malware software and signature databases are kept up to date.
Review the suggested best practices and implement the controls that work best for your environment. Each organization has different needs and will end up with different controls to best ensure functionality and security in the Remote Access Domain.
This chapter covered how to enable remote users to access your network's internal applications and resources by implementing components in the Remote Access Domain. You learned to address the increased risks associated with allowing remote users to access your network using untrusted WANs. You also learned about controls and strategies that work well in the Remote Access Domain to keep your environment functional without sacrificing compliance.
Baseband
Broadband
Encapsulating protocol
Hypertext Transfer Protocol (HTTP)
Hypertext Transfer Protocol Secure (HTTPS)
Secure Sockets Tunneling Protocol (SSTP)
Server Message Block (SMB)
Simple Network Management Protocol (SNMP)
Tunneling
The primary concern for remote access is availability.
True
False
Which entity is responsible for controlling access to network traffic in the WAN?
WAN optimizer
Your organization
WAN service provider
Network Management Platform
________ is the primary security control used in the Remote Access Domain.
All VPN traffic is encrypted.
True
False
Given adequate security controls, PDAs are appropriate for use as remote access devices.
True
False
Which of the following terms means the process to decide what a user can do?
Identification
Authentication
Clearance
Authorization
Which of the following protocols is used for encrypted traffic?
HTTPS
SNMP
IP
L2TP
________ is a technique that creates a virtual encrypted channel that allows applications to use any protocol to communicate with servers and services without having to worry about addressing privacy concerns.
Which of the following protocols works well with firewalls?
GRE
SSTP
L2TP
L2F
Which of the following transmission techniques requires the entire bandwidth of a channel?
Multiband
Baseband
Broadband
Duplex
________ is a network protocol used to monitor network devices.
The use of global user accounts can simplify user maintenance.
True
False
Which protocol is commonly used to protect data sent to Web browsers when not using VPNs?
IPSec
PPTP
GRE
SSL/TLS
Which of the following controls would best protect sensitive data disclosure to unauthorized users using remote computers?
Encryption
Strong passwords
Firewalls
Configuration management tools
Which protocol does SNMP use to transport messages?
TCP
UDP
SSL
GRE