TODAY'S ORGANIZATIONS depend on a workforce that is mobile and widely dispersed. Work has to get done regardless of where the workers might be at any one moment. An IT infrastructure that supports this type of mobility and flexibility has to include the ability for workers to connect from almost anywhere. Organizations are deploying resources and applications that are easier than ever to access from remote locations. These organizations need a framework to describe how to provide access to the organization across town or across the world and do it securely.
In Chapter 11, you learned about the LAN-to-WAN Domain and how data travels between a local area network (LAN) and a wide area network (WAN). In this chapter, you'll learn about what happens to data in the WAN Domain and how you can ensure compliance as your data travels outside your environment.
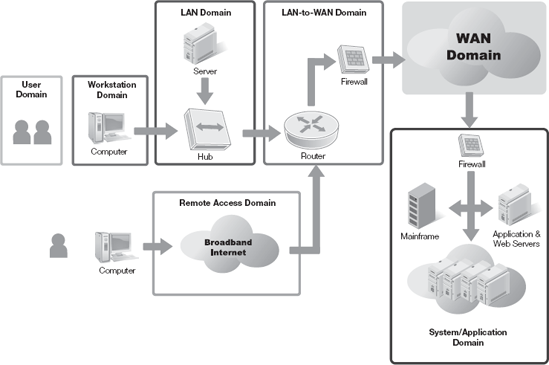
You learned in the introduction how more and more organizations rely on distributed architectures. Many organizations deploy their enterprise applications as distributed applications. Although the actual applications and resources belong in other domains, clients need the ability to access resources and run distributed programs. Providing the ability to connect diverse resources is the main purpose of the WAN Domain. Although making your resources and data available to more users is a good thing, you must pay close attention to security. Keeping your data secure as it leaves your network takes advance planning. Always consider how secure your data is in each of the domains of your IT infrastructure. Figure 12-1 shows the WAN Domain in the context of the seven domains in the IT infrastructure.
Remember that your responsibility to keep your data secure doesn't stop when that data leaves the controlled area of your networks. The WAN Domain represents an area that might be largely out of your control. Your responsibility to secure data means to protect it in such a way that it is secure even when traveling across an untrusted network. Ensuring data is safe even in the WAN Domain makes it possible for your organization to deploy distributed applications that can provide unprecedented functionality to remote users. Implementing the controls necessary to support your security policy in the WAN Domain makes your organization more secure and allows you to provide a higher level of visibility to your data.
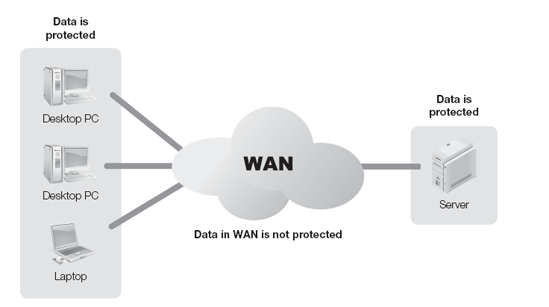
WANs provide the valuable service of connecting your networks together without having to install or maintain the interconnection network media. In other words, you use someone else's network to connect your networks together. You can connect your headquarters to several branch offices using a WAN. You connect each of your networks to the WAN and all your nodes can communicate. The only problem is that you now depend on another organization to communicate. Each time you send a message from your headquarters to a branch office, that message travels across someone else's network. You no longer have control over who sees your network traffic or who can alter it. Figure 12-2 shows how data traveling from one of your nodes to another across a WAN is out of your control.
One of the most important concerns when sending data across public networks is confidentiality. Although not all data is confidential, any data you exchange with a remote resource using a WAN is potentially available for anyone else to see. Consider all WANs to be hostile and insecure. Your organization likely controls the access to your LANs and has some measure of assurance of how private the LANs are.
WANs are different. You don't have control over who accesses them or who can access data traveling across a WAN. You must deploy sufficient controls to protect the privacy of any data in the WAN Domain.
The primary control type you'll use in the WAN Domain for any data is encryption. You have many encryption choices, and the right control depends on how you'll use the data and which component applies the encryption methods. Your application may encrypt your data or another component may encrypt the connection in another domain. You'll learn about different approaches to encryption later in this chapter. Some solutions require multiple layers of controls. You select the best controls that support a few general principles. These are the same principles you saw in the LAN-to-WAN Domain in Chapter 11, and they apply to the WAN Domain as well:
No data in the WAN Domain should ever be transmitted in the clear.
When using encryption, select the algorithm based on needs; don't just select the largest key.
Assume an attacker can intercept and examine any network messages.
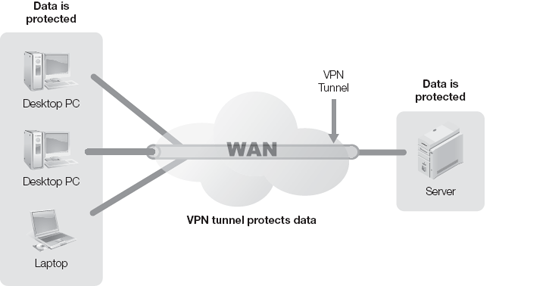
Figure 12-3 shows a simple diagram of how a VPN tunnel protects encrypted data as it moves across the Internet.
The WAN Domain exists to transport network messages from one node to another. In most cases, the WAN is a network that is owned and managed by some other entity. Your ability to affect the WAN's security is limited or nonexistent. You must ensure that you transmit data across the WAN in a secure fashion using secure protocols and techniques. In this section, you'll learn about the devices and components you'll commonly find in the WAN Domain that support communication, both secure and insecure. Once you've learned about the devices and components, you'll learn about controls to ensure compliance in the WAN Domain.
Few organizations have the resources to create and manage their own global WANs. The most common approach to deploying applications and functionality across a WAN is to lease network access from a WAN service provider. A WAN service provider is in the business of providing WAN bandwidth to subscribing organizations. The WAN transports traffic among subscriber nodes and subscribers pay for the service. The WAN service provider handles all routing, connection media, and hardware issues within the WAN. All the subscribers do is connect to the WAN and use it to send and receive traffic.
Table 12-1. WAN options.
DESCRIPTION | COMMENTS | |
|---|---|---|
Dedicated line/leased line | A point-to-point connection between two physical devices | Most secure, but also one of the most expensive; exclusive access to all bandwidth |
Circuit switching | A dedicated circuit established between two points for the duration of a conversation | Lower cost, but requires time to establish circuit and circuit switching is slower than the next two options |
Packet switching | Messages travel in variable-length packets along point-to-point or point-to multipoint links through WAN switches | Can be substantially faster than circuit switching but media is shared and can suffer congestion |
Cell relay | Similar to packet switching but with fixed-length cells | Best for transporting voice and data but overhead can reduce speed |
VPN over Internet | A VPN established between two nodes | Very inexpensive but performance and stability depend on your Internet connection |
The three main concerns when selecting a WAN provider are cost, speed, and stability. There are other factors to consider but these three are often the most important characteristics when selecting a WAN. Each type of WAN has its own characteristics and works best in different types of environments.
Today's WAN service providers offer several types of WANs for different budgets and performance requirements. Each type of WAN has its strengths and weaknesses. You need to evaluate each option based on your specific needs to find the best fit for your organization. Table 12-1 lists the main types of WANs available from WAN service providers.
One of the three primary considerations of how well a particular WAN fits your business requirements is stability. An inexpensive WAN that is very fast still isn't worth very much if it doesn't stay operational as often as you require. Examine the WAN service provider's service level agreement (SLA). The SLA states a level of guaranteed uptime. In most cases, WAN service providers will provide several levels of service for different subscription amounts.
Pay attention to the cost for WAN service as well. Some WAN providers offer service for a fixed monthly fee, whereas other products carry a usage charge. Estimate your monthly usage and calculate your costs for each type of service.
Note
Although cost is only one factor when considering a WAN provider, it can be a determining factor.
Your particular WAN needs will direct you toward the best WAN choice. If your primary need for a WAN is to connect a small number of LANs to one another, dedicated lines might be the best choice. A dedicated line, also called a dedicated circuit, is a permanent circuit between two endpoints. A single dedicated line works very well when connecting two LANs, campus area networks (CANs), or even metropolitan area networks (MANs). You can connect more than two networks using multiple dedicated lines.
Dedicated lines are always available, fast, and secure. Because no one else shares your dedicated line with you, your organization has exclusive access to the traffic flowing along the line. Of course, the WAN service provider has access to your traffic as well, but no one else should be able to see your traffic. If your budget and connectivity needs support dedicated lines, they can return some of the best performance of all WAN options.
Note
With a dedicated line, or a dedicated circuit, you don't share the bandwidth with anyone else—the entire bandwidth is always available for your use. Because the circuit is permanent, there is no overhead in creating a circuit.
If your requirements include connecting more than three or four locations, as in connecting multiple branch offices to the headquarters, dedicated lines will likely be too expensive. Another option in such a case is Multi-Protocol Label Switching (MPLS) networks supporting a virtual private network (VPN). MPLS works with many WAN technologies and provides very good overall performance using packet-switching and circuit-switching networks. Although MPLS networks are not optimal for high-bandwidth, large-volume network transfers, they work very well in most environments where you need to maintain connections between several other networks.
For high-bandwidth needs within smaller geographic regions, a hybrid of a WAN and a LAN has emerged that fills a particular niche of small WANs. Historically, MANs have been implemented as small-scale WANs using WAN protocols. Technical advances in networking hardware and connection media have enabled the deployment of the well-known Ethernet technology in larger networks. Ethernet, a longtime favorite LAN protocol, is inexpensive to deploy and provides substantial bandwidth for the low cost. This hybrid network that uses Ethernet in a MAN is called an Ethernet MAN or Metro Ethernet.
Most discussions of network protocols include a discussion of the Open Systems Interconnection (OSI) reference model. The OSI reference model is a generic description for how computers use multiple layers of protocol rules to communicate across a network.
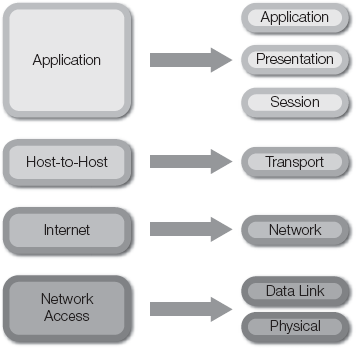
The OSI reference model defines seven different layers of communication rules. You'll also likely encounter another popular reference model, the TCP/IP reference model, when discussing network protocols. The Transmission Control Protocol/Internet Protocol (TCP/IP) reference model defines four different layers of communication rules. Both models are useful to describe how protocols work and how to implement them in network communications. Figure 12-4 shows the TCP/IP reference model and the OSI reference model.
You might hear hardware devices or software protocols referred to as "layer 2 devices" or "layer 5 protocols." These references generally refer to the OSI reference model layer to describe where the referenced hardware or software operates. In the context of WANs, most WAN protocols operate at OSI layer 2. MPLS actually operates between layers 2 and 3 and is sometimes called a layer 2.5 protocol. Most traditional network switches operate at OSI layer 2, but newer devices use advanced techniques to provide more sophisticated switching capabilities at OSI layer 3.
Recall that traditional layer 2 switches use the Media Access Control (MAC) addresses in each packet to forward the packet to its proper destination. One type of layer 3 switch extends the concept of a traditional layer 2 switch by implementing fast Internet Protocol (IP) routing using hardware. Most routing using IP addresses requires software to examine each packet. Software is always slower than hardware and, thus, routing has historically been slower than switching. A layer 3 switch can greatly speed up routing by using advanced hardware to make the routing decision.
All components in all domains can fail. It is important that each component have a backup or alternate component to replace it if it fails. Your WAN connection is no exception. If your organization relies on a single WAN connection and that connection fails, your entire access to your WAN fails.
You have already learned about the importance of redundant and alternate WAN connections in the chapter on the LAN-to-WAN Domain. The issue bears repeating here. Remember that your organization's ability to use a WAN to communicate with central resources and functions depends on the availability of your WAN to support the connection. A failure anywhere in the WAN violates your organization's data availability. Make sure you take these steps to protect the availability and security of your data across the WAN Domain:
Ensure the SLA for each WAN service provider meets or exceeds the required uptime goals for each WAN.
Establish backup or redundant WAN connections, either multiple connections to the same WAN or multiple connections using different WANs.
Install backup or redundant connection devices in the WAN Domain to ensure connection hardware failure does not result in a failure to connect to your WAN.
Monitoring the traffic and performance of your WAN Domain can directly translate into concrete results. WAN usage might cost money, but it always costs in time. Any time you can reduce WAN usage, you are saving time and perhaps money as well. Recall that a secure network is one that provides smooth operation and only allows authorized traffic on the network. Access to your WAN is one of the necessary pieces in a distributed environment. If the WAN is down or unreachable, your distributed applications can't function. As you learned in Chapters 10 and 11, which covered the LAN and LAN-to-WAN Domains, network problems could cause service interruptions and could result in noncompliance. You need to be aware how all parts of your network are working to ensure you are compliant.
Traffic monitoring and analysis for a WAN are nearly identical to the process you learned about in Chapter 11. The WAN Domain differs from other domains in that you probably don't own or control the hardware or the software in the WAN. Your organization pays a subscription fee to connect to another organization's WAN. You generally pay the WAN service provider either by bandwidth usage or a flat fee for a specified bandwidth limit. Because you likely pay for WAN access, managing WAN traffic proactively can reduce your need for additional bandwidth and reduce your WAN costs.
You can implement WAN traffic monitoring and analysis software and devices in two ways. You can install software or devices on the perimeter of the WAN where you connect to it or rely on your WAN service provider to supply traffic flow data. You gain far more control monitoring the WAN yourself but you only have limited capability to affect the WAN's performance. One technique is to send a message to another node on the WAN and have that node echo a response. The first node can analyze the route and duration the message took for the round-trip. Comparing sample traffic with baseline data will reveal if the current performance is normal.
Several vendors provide tools to help monitor WAN traffic and optimize your WAN's throughput. Real-time WAN optimization software can analyze current WAN performance and then modify how new traffic is sent across the WAN. WAN optimizers can exclude unnecessary traffic, use compression to maximize bandwidth, cache data, and prioritize traffic to make the best use of your WAN. The result can be a noticeable increase in network speed. In this case, you haven't made the network any faster but you have used the available bandwidth more efficiently and increased your data throughput. Table 12-2 lists some WAN optimization products.
You can choose from many products to help optimize your WAN usage. Explore the solutions presented here, as well as other solutions, and select a product that best meets your security goals.
Table 12-2. WAN optimization tools.
PRODUCT | WEB SITE |
|---|---|
Riverbed Cascade |
|
ManageEngine OpManager |
|
BlueCoat WAN Optimization product line |
|
Cisco WAN Optimization |
|
F5 WAN optimization solutions |
|
Juniper Networks Application Acceleration Platforms |
|
Expand Networks ExpandView |
|
You learned about the importance of managing network configuration settings in the previous chapters on the LAN and LAN-to-WAN Domains. You don't have nearly the control over the WAN network components because most of the actual devices belong to your WAN service provider. However, you still need to proactively manage the components you do control. You can manage the settings of at least these WAN Domain components:
WAN access device—The device or computer you use to physically connect to your WAN.
WAN account—Your WAN service provider will provide access for you to configure specific settings to your WAN account. It is important that you create a backup of these settings. Even if your WAN service provider only allows you to manage your account using a Web page, saving screen shots of each configuration page is better than having no record of your settings.
WAN optimization device—Any hardware or software that optimizes WAN traffic belongs to the WAN Domain and is a prime candidate for configuration management.
The strategies and techniques for managing configuration settings and controlling configuration changes should match your activities in the LAN and LAN-to-WAN Domains. Refer back to Chapters 10 and 11 for more information on proactively managing configuration setting changes. Just as with other domains, managing the configuration settings of your WAN Domain components is an important part of keeping your overall environment compliant and secure.
Because the WAN service provider bears the responsibility of maintaining the actual WAN, there isn't much left to do to manage components in your WAN Domain. It is important to ensure all of the components in the WAN Domain are doing their jobs, but there isn't much you can do to manage the actual WAN. You learned about WAN optimization tools earlier in this chapter. Managing components in the WAN Domain primarily means managing how well your organization uses the WAN resources. There are three main categories of WAN management tasks, including:
Providing the best WAN option for specific traffic
Caring for WAN Domain components
Optimizing WAN usage
In this respect, the WAN optimization tools from Table 12-2 are also WAN management tools. Your organization likely has different needs for WANs. As a result, you will likely use different WAN solutions. You may make the decision of which WAN to use in other domains but the actual access point exists in the WAN Domain. It is important to ensure each WAN access is configured and optimized to provide the best level of service for your needs.
Because there are limited components in the WAN Domain, there are also limited opportunities to enforce access control for the domain. There are essentially two places to control access to the WAN. First, you can deploy controls to limit access to the WAN access device. Device and user authentication and authorization controls should limit which users can access the WAN access point. The second opportunity to control WAN access is in the access device itself. The WAN access point also has the ability to enforce access controls. In this way, the WAN access device controls which users can get through the device and onto the WAN.
WAN access devices and WAN optimization devices both contain the ability to selectively grant access to the WAN. Although the WAN access device generally operates like a firewall or gateway, WAN optimization devices can make more sophisticated decisions about WAN access. Granting access may include decisions regarding time- or bandwidth-sensitive rights. Some users might only be granted WAN access during slow periods, while other users might get access on demand. You have the ability to grant or deny WAN access based on your security and functional needs.
Implementing more complex controls means you should spend more time testing the controls under different circumstances. If you implement load-based controls using WAN optimization, ensure you test the controls under different network loads, either real or simulated. Use auditing to create logging entries for repeated access denials to ensure your controls aren't degrading the ability of your users to do their jobs. As always, avoid auditing too many events. Only audit the ones you'll need to analyze your WAN's ongoing performance.
You have seen in previous chapters that your main goal in all domains is to deploy and maintain controls that support all of the A-I-C properties of security for your data. The WAN Domain contains several components that play critical roles in providing secure access to your organization's data; maintaining that security requires diligence and the right controls.
Each WAN service contract includes specific promises of stated levels of service called service level agreements, or SLAs. SLAs state what your WAN service provider promises to deliver in terms of various types of service. The first of two main SLAs addresses the availability property of data security. You should subscribe to a WAN service that guarantees the level of availability your organization requires to conduct business.
Availability SLA terms depend on the type of service you purchase. Most WAN service providers offer customers a choice of service guarantees for different costs to meet different customers' needs. Table 12-3 shows a sample list of availability service choices. Note that the differences in levels of service differ based on the reliability or recovery options selected.
The level of availability you choose will dictate the cost and hardware requirements for your WAN service. Examine the impact of expected or scheduled annual downtime and select the level of service that fits your organization.
Most WAN service provider SLAs also include provisions for recovering from major interruptions due to hardware or carrier failure. Each SLA should contain a commitment for the maximum amount of time it should take to restore your organization's WAN service after a failure. The Time To Recover (TTR), or Time To Repair, commitment states the acceptable amount of time that is allowed to repair or replace failed components. For global networks, WAN service providers often employ the services of local technicians to decrease response time. The WAN service provider would have their own SLAs with their subcontractors.
As with the availability SLA, you should select a recovery SLA that meets your organizational goals for data availability. Review your own plans to ensure that when your WAN service provider restores their service, you are ready to connect and use the WAN to continue your business operations.
Table 12-3. Availability service choices.
SERVICE | AVAILABILITY | COMMENT |
|---|---|---|
Dual routers/dual circuits | 100% | Redundant hardware and connections provide uninterrupted service. |
Single router with backup | 99.95% | Backup hardware can replace primary router with very little downtime; estimated annual downtime is 4.4 hours. |
Single router | 99.5% | A single router is a single point of failure—and you must replace failed hardware; estimated annual downtime is 43.8 hours. |
Table 12-4. Common VPN protocols.
PROTOCOL | DESCRIPTION |
|---|---|
Common tunneling protocol that defines a connection between two endpoints. You need another protocol, such as Internet Protocol Security (IPSec), to provide encryption services. | |
A layer 2 protocol that defines a tunnel between two endpoints. PPTP is older and generally less secure than L2TP. | |
Secure Sockets Layer/Transport Layer Security (SSL/TLS) | Common protocol used to transport encrypted Hypertext Transfer Protocol (HTTP) traffic. Can also be used to create an encrypted tunnel. |
New protocol used by Cisco hardware to create a generic VPN that works well in most network architectures. | |
Secure Socket Tunneling Protocol (SSTP) | New protocol from Microsoft for Windows Server 2008 and Windows Vista Service Pack 2. SSTP works at the transport layer to provide a VPN that works with most firewalls. |
SLAs define levels of service that protect the availability property of data. Additional concerns when sending data across any WAN include integrity and confidentiality. The main type of control you can use to ensure the integrity and confidentiality of your data is encryption. One of the more common types of encryption in use in the WAN Domain is encrypted traffic over a VPN.
A VPN is a persistent connection between two endpoints commonly created over a WAN. Although not limited to WANs, VPNs make it easy to establish what appears to be a dedicated connection over a shared-access WAN. VPNs work well in creating persistent connections, also called tunnels, over the Internet or other types of WANs. Many VPNs also encrypt the traffic in the tunnel, making it an attractive option for WAN traffic that may contain sensitive data. Encrypted VPNs are also called secure VPNs. Even though others might be able to see the traffic as it travels through the WAN, no one can read it or even change it undetected because the data is encrypted.
Today's networks often support multiple VPN protocols. Consult your WAN service provider for information on which VPN protocols your WAN supports. Use VPNs anytime you need to ensure integrity and confidentiality for sending sensitive data over a WAN. Table 12-4 lists some of the more common VPN protocols in use today.
Note
You'll learn more about VPNs in Chapter 13, which addresses the Remote Access Domain.
Statement on Auditing Standards (SAS) 70, Service Organizations is an internationally recognized auditing standard developed by the American Institute of Certified Public Accountants (AICPA).
A SAS 70 statement of compliance signifies that a service organization has had its control objectives and control activities examined by an independent auditing firm. Because so much emphasis is placed on security and compliance with multiple sources of requirements, service providers must demonstrate that they have adequate controls in place to securely handle their customers' data. In addition, the requirements of Section 404 of the Sarbanes-Oxley Act of 2002 make SAS 70 audit reports even more important to the process of reporting on the effectiveness of internal control over financial reporting.
According to the SAS 70 Web site, "SAS No. 70 is the authoritative guidance that allows service organizations to disclose their control activities and processes to their customers and their customers' auditors in a uniform reporting format. The issuance of a service auditor's report prepared in accordance with SAS No. 70 signifies that a service organization has had its control objectives and control activities examined by an independent accounting and auditing firm. The service auditor's report, which includes the service auditor's opinion, is issued to the service organization at the conclusion of a SAS 70 examination."1
SAS 70 defines two different types of service auditor reports, Type I and Type II. A Type I report describes the audited organization's security controls as of a specific point in time. A Type II report includes a description of the audited organization's security controls and a detailed examination of the performance of the controls over at least a six-month time period. Table 12-5 compares the contents of a SAS 70 Type I and Type II report.
A SAS 70 compliance audit demonstrates that a WAN service provider stands behind its security controls and has confidence in its ability to protect customer data. You should insist on doing business only with WAN service providers who can show evidence of a SAS 70 audit.
Table 12-5. Comparing a SAS 70 Type I and Type II audit report.
REPORT SECTION | TYPE I REPORT | TYPE II REPORT |
|---|---|---|
Auditor's opinion of control description completeness and effectiveness | Required | Required |
Description of controls | Required | Required |
Time period (minimum six months) test results and statement of control effectiveness | Optional | Required |
Supplemental/supporting information | Optional | Optional |
Table 12-6. Common compliance controls in the WAN Domain.
COMPONENT | DESCRIPTION | |
|---|---|---|
Preventive | Enforce privacy through encryption Optimize WAN throughput Assurance of WAN service provider security Assurance of WAN availability User-based access controls for WAN resources Configuration change control | Deny any unencrypted traffic to travel to the WAN. Use a WAN optimizer to identify and deny unnecessary WAN traffic. Insist that all WAN service providers provide evidence of SAS 70 (or equivalent) compliance. Establish WAN service that provides SLAs that meet or exceed your organization's uptime and recovery requirements. Restrict access to WAN to reduce traffic and resource exposure. Limit changes to all network device configuration settings and filtering rules. Require approval for all changes before deploying them. |
Detective | Performance monitoring Traffic analysis Configuration settings monitoring Penetration testing | Frequently sample WAN traffic flow metrics and alert for any unusual activity. Examine traffic for known attack signatures and to ensure data is encrypted. Compare WAN device configuration settings with stored baselines to detect any unauthorized changes. Conduct periodic penetration tests to identify security control weaknesses. |
Corrective | WAN component patching Attack intervention Business continuity plan (BCP) and disaster recovery plan (DRP) | Keep WAN devices and applications patched to the latest available level. Automatically modify filtering rules to deny traffic from sources generating known attack signature packets. Develop and maintain plans to survive and continue operations in the face of small or large disruptions. Coordinate your BCP and DRP with your WAN service provider's SLAs. |
Compliance in the WAN Domain depends on implementing the best controls you can, and ensuring your WAN service provider's controls are compliant as well. As with other domains, explore alternate controls for each security goal. You must ensure the correct controls are in place to balance each of the three A-I-C security properties.
As you analyze controls in the WAN Domain to meet compliance requirements, ensure each control satisfies your security policy. If a control does not support any part of your security policy, you should question its value to your organization. Although different legislation, regulations, and vendor standards have different requirements, Table 12-6 lists the types of controls for which you'll likely need to ensure compliance in your WAN Domain.
Implementing multiple types of controls decreases the likelihood an attack will be successful and makes your WAN Domain more secure.
The WAN Domain allows multiple locations to establish network connections without having to manage the physical networks yourself. Because this domain connects your environment to an untrusted WAN, you must ensure the controls protect your internal resources. Solid planning, along with aggressive management, can provide both easy access across an untrusted WAN and the ability to maintain your data's security.
The following best practices represent what many organizations have learned. Plan well and you can enjoy a functional WAN Domain that makes internal information and resources available for use to WAN users. Here are general best practices for securing your WAN Domain:
Map your proposed WAN architecture, including redundant and backup hardware and connections, before establishing WAN service. Use one of the several available network-mapping software products to make the process easier.
Update the network map anytime you make physical changes to your network.
Establish multiple WAN connections to avoid any single points of failure. Use fault-tolerant hardware that can maintain WAN connectivity if the primary connection or devices fail.
Use load-balancing techniques on the multiple WAN connections to utilize the bandwidth of both connections.
Develop a backup and recovery plan for each component in the WAN Domain. Include recovery plans for damaged or destroyed connection media.
Don't forget to include configuration settings for network devices in your backup and recovery plans.
Implement frequent update procedures for all operating systems, applications, and network device software and firmware in the WAN Domain.
Monitor WAN traffic for performance and traffic for suspicious content.
Carefully control any configuration setting changes or physical changes to domain nodes.
Update your network map after any changes.
Use automated tools whenever possible to map, configure, monitor, and manage the WAN Domain.
Use WAN optimization devices or software to maximize WAN utilization.
These best practices give you a brief overview of the issues you'll need to consider when implementing WAN access. Consider each of the best practices and add your own that will make your organization safer when transporting data across a WAN.
The WAN Domain allows your users to connect to your resources and applications through a WAN from anywhere the WAN reaches. Opening your environment up to a WAN also opens new possibilities for attacks from WAN users. Connecting to a WAN offers many advantages and pitfalls. Learn about the components in the WAN Domain and how to secure them. Through solid planning, you can empower your environment with the flexibility and functionality of WAN access while minimizing the security issues.
American Institute of Certified Public Accountants (AICPA)
Dedicated line
Ethernet MAN
Metro Ethernet
Open Systems Interconnection (OSI) reference model
Secure VPNs
Service level agreement (SLA)
TCP/IP reference model
Time To Recover (TTR)
WAN optimizers
WAN service provider
The WAN Domain commonly contains a DMZ.
True
False
One of the most important concerns when sending data across a WAN is confidentiality.
True
False
Which of the following is the primary type of control employed in the WAN Domain?
Firewalls
Encryption
Hashing
Compression
Who writes SLAs?
Subscribing organization
Telecom company
WAN service provider
SAS 70
Which type of WAN generally has the highest speed and is most secure?
Dedicated line
Circuit switching
Packet switching
MPLS network
The_____contains the guaranteed availability for your WAN connection.
Which WAN technology is a cost-effective solution for connecting multiple locations?
MPLS
ISDN
MAN
L2TP
Most WAN protocols operate at which level in the OSI reference model?
7
3
2
1
A_____can exclude unnecessary traffic from the WAN.
WAN subscription cost tends to decrease as availability increases.
True
False
By definition, VPN traffic is encrypted.
True
False
Which of the following best describes SAS 70?
Security specification
Auditing standard
Encryption standard
WAN specification
Both types of SAS 70 audit reports include a description of security controls.
True
False
A_____makes it easy to establish what appears to be a dedicated connection over a WAN.
Which of the following describes a common LAN protocol deployed to a network the size of a city?
IPSec MAN
Urban Ethernet
TCP MAN
Metro Ethernet