EXHIBIT 3-1
LEARNING OBJECTIVES
After studying this chapter, you should be able to:
| 3-1 | Define cash larceny |
| 3-2 | Understand how cash receipts schemes differ from fraudulent disbursements |
| 3-3 | Recognize the difference between cash larceny and skimming |
| 3-4 | Understand the relative frequency and cost of cash larceny schemes as opposed to other forms of cash misappropriations |
| 3-5 | Identify weaknesses in internal controls as inducing factors to cash larceny schemes |
| 3-6 | Understand how cash larceny is committed at the point of sale |
| 3-7 | Discuss measures that can be used to prevent and detect cash larceny at the point of sale |
| 3-8 | Understand and identify various methods used by fraudsters to conceal cash larceny of receivables |
| 3-9 | Understand schemes involving cash larceny from deposits, including lapping and deposits in transit |
| 3-10 | Understand controls and procedures that can be used to prevent and detect cash larceny from bank deposits |
| 3-11 | Be familiar with proactive audit tests that can be used to detect cash larceny schemes |
CASE STUDY: BANK TELLER GETS NABBED FOR THEFT1
Laura Grove worked at Rocky Mountain Bank in Nashville, Tennessee, for five years. As a teller, she thought to herself, she wasn't getting any richer. She and her husband owed about $14,000 in credit card bills, which seemed to get higher and higher each month, especially after adopting a five-year-old girl the year before.
When she transferred to a branch bank in Cheetboro, Tennessee, the bank promoted her to head teller. In this new position, Laura had authority to open the night depository vault with another teller. For security reasons, the bank allowed each teller to possess only half the combination to the vault.
Every morning, Laura saw the bank night deposit vault door open and close after the removal of all customer night deposit bags. The bank placed only one camera on the night vault, which was turned on at 8:00 a.m. when the bank opened for business. Laura thought it would be easy to get into the night depository and take the bags. These thoughts were reinforced when a customer reported his bag missing and the bank quickly paid his money without a thorough investigation. So one Friday morning, Laura made up her mind that she could take about $15,000 with little risk of being identified. But before she actually took the money, she observed. When she opened the night vault with her coworker Frank Geffen, she saw him dial the first half of the combination and was careful to memorize the numbers. After entering the second half of the combination, they opened it as usual, removed and listed each night deposit bag, and shut the vault behind them. This time, however, Laura did not lock the vault.
Here, Laura made her first mistake. She thought she could leave the vault door open and return Monday to take the money. But just before the bank closed and employees prepared to leave, teller Melissa Derkstein checked the vault one more time. Seeing that the vault was open, she spun the dial, shaking the handle to ensure the door was locked.
Laura and the other bank employees punched their security codes on the outside door and left for the day. During the weekend, Laura considered her plot. Should she enter the combination by herself this time and place the money into a personal tote bag? Should she stay at work all day with the goods underneath her feet?
Monday morning, she still was not sure how to pull it off but had resolved to go through with the plan anyway. Arriving at 7:15 a.m., Laura was the first person in the bank that morning. After punching in her security code, she placed her tote bag and personal belongings on her chair. Immediately, she went to the night vault and dialed the full combination. Nothing happened. Her mind raced. “Maybe this won't work; this is too risky.” Her fingers tried the combination again, and once again, until she heard a click and the vault opened.
Inside, Laura removed the two customer deposit bags, ones that she knew contained large sums of cash. She placed both bags in her tote bag and walked back to her teller window. She stuffed her Weight Watchers book and purse inside the tote bag, on top of the deposit bags. She then hung her bag on the door of the storage room and returned to the teller window, straightening up her work area.
Fifteen minutes later, the branch manager, Harvey Lebrand, entered, looking surprised that Laura was already at her desk. He asked Laura why she had come into work so early this Monday.
“Oh, I just needed to get organized early, because I need to take my Bronco into the shop later today and knew I wouldn't have much time,” Laura said.
“You need to get your truck repaired?” Mr. Lebrand asked. “Why don't you go now?”
“Okay, I can get my mother to give me a ride back,” Laura said. “See you soon, Mr. Lebrand.”
Laura rushed to the storage area, grabbed the tote bag and left the bank. She drove directly to her home and emptied the contents of the bag, watching the many bills and checks spill onto her bed. She lit up with uneasy excitement. Sorting the checks into a separate pile, she gathered the money into a large heap and did a quick count. She estimated she had taken about $15,000. Placing the bills into manila envelopes, she hid them in the headboard storage compartment of the bed. The checks were placed in a small plastic bag. She then phoned her mother and asked her to meet her at the Sears Auto Center.
Laura knew there was an apartment complex next to Sears that had a large blue dumpster. After the checks had been deposited in the dumpster, Laura drove to Sears. Her mother arrived a little later to take her back to work.
A day later, Rocky Mountain Bank Audit Investigator Stacy Boone received a call from Laura's manager, informing her that two customers had not gotten credit for the deposits they'd made the night before. Each deposit was for $8,000.
Boone's investigation quickly led her to suspect Grove. The first one in the bank that morning, Grove also came in before the surveillance cameras turned on. As head teller, she had one-half of the combination to the night depository. Other employees said they “didn't trust her.” But when the investigators questioned her, Grove strongly denied any knowledge of the theft.
“During our interview with her, she broke out in a red rash” (which suggested stress). “I have seen innocent people break out into a red rash, but she was the only one we interviewed that day who did,” Boone said.
Boone also suspected Grove because the branch bank from which she'd transferred “had a lot of unexplained shortages, and she was a suspect there, but we could never pin down that she took the money. She had bought a lot of new jewelry, wore a lot of expensive clothes, but had filed bankruptcy at one point that year.”
The investigation came to a swift conclusion, however, when Boone received a call on her answering machine from Grove's husband, a former neighbor. “I was afraid he wanted to know why we were investigating his wife and hesitated to call him right back,” Boone said.
Boone decided she 'might as well get this over with and tell him I could not talk about it [the investigation]. When I called him, he told me he found the bank's money in his attic and suspected his wife. His wife had told him of the bank's investigation, but had not admitted any theft.
“Their daughter had overheard a conversation they had the day of the theft” in which Laura had expressed anxiety to her husband about the bank's investigation, Boone said. “His daughter had told him that she saw [Laura] put something in the attic. So, when she wasn't there, the husband went up in the attic and looked, and found two bags of money.”
Boone said the husband was also suspicious because his wife had lied to him before. “He told me that his mother-in-law, her mother, always won all these prizes. She had even won a car through a contest. One night, he came home and found a new big-screen LCD HDTV in the living room and asked his wife where it came from. She said ‘Oh, Mom won that.’ At the time, he really didn't think anything about it. But a couple days later, Kirby's Electronics, where the TV came from, called in regard to her credit application. They told him that she charged that TV.”
Faced with this evidence, Laura and her husband delivered the $16,000 in cash as restitution. The bank dismissed Grove and she was prosecuted for the crime but received probation in lieu of prison time.
A year later, Boone received a call from one of the bank's tellers who had seen Grove working at another bank in a small city outside of Nashville. Boone called one of the personnel employees there and talked with her. “They were a bank that did not do fingerprint checks, so they had no knowledge that she had been convicted. She did get into another bank to work, but not for very long.”
OVERVIEW
In the occupational fraud setting, a cash larceny may be defined as the intentional taking away of an employer's cash (the term cash includes both currency and checks) without the consent, and against the will, of the employer. In the case study above, Laura Grove's theft of approximately $16,000 from her employer is an example of a cash larceny.
How do cash larceny schemes differ from other cash frauds? In order to understand the distinction in our classifications, it is helpful first to break down the cash schemes into two broad groups, the first being the fraudulent disbursement schemes and the second being what we will loosely term the cash receipts schemes. Fraudulent disbursement schemes are those in which a distribution of funds is made from some company account in what appears to be a normal manner. The method for obtaining the funds may be the forging of a check, the submission of a false invoice, the doctoring of a timecard, and so forth. The key is that the money is removed from the company in what appears to be a legitimate disbursement of funds. Fraudulent disbursements will be discussed later in this book.
Cash receipts schemes, on the other hand, are what we typically think of as the outright stealing of cash. The perpetrator does not rely on the submission of phony documents or the forging of signatures; he simply grabs the cash and takes it. The cash receipts schemes fall into two categories: skimming, which we have already discussed, and cash larcenies (see Exhibit 3-1). Remember that skimming was defined as the theft of off-book funds. Cash larceny schemes, on the other hand, involve the theft of money that has already appeared on a victim company's books.
EXHIBIT 3-2 2011 Global Fraud Survey. Frequency of Cash Misappropriations*
EXHIBIT 3-3 2011 Global Fraud Survey: Median Loss of Cash Misappropriations
Cash Larceny Data from the ACFE 2011 Global Fraud Survey
In the ACFE study, cash larceny schemes were the least common form of cash misappropriations. Fifteen percent of all cash schemes in our survey involved cash larceny. The median loss for these cases was $54,000, which was also the lowest of the three categories of cash misappropriations (see Exhibits 3-2 and 3-3).
CASH LARCENY SCHEMES
A cash larceny scheme can take place in any circumstance in which an employee has access to cash. Every company must deal with the receipt, deposit, and distribution of cash (if not, it certainly won't be a very long-lived company!), so every company is potentially vulnerable to this form of fraud. Although the circumstances in which an employee might steal cash are nearly limitless, most larceny schemes involve the theft of cash:
- At the point of sale
- From incoming receivables
- From the victim organization's bank deposits
Larceny at the Point of Sale
A large percentage of the cash larceny schemes in our research occurred at the point of sale, and for good reason—that's where the money is. The cash register (or similar cash collection points like cash drawers or cash boxes) is usually the most common point of access to ready cash for employees, so it is understandable that larceny schemes would frequently occur there. Furthermore, there is often a great deal of activity at the point of sale—particularly in retail organizations—with multiple transactions requiring the handling of cash by employees. This activity can serve as a cover for the theft of cash. In a flurry of activity, with cash being passed back and forth between customer and employee, a fraudster is more likely to be able to slip currency out of the cash drawer and into his pocket without getting caught.
This is the most straightforward scheme: Open up the register and remove currency (see Exhibit 3-4). It might be done as a sale is being conducted, to make the theft appear to be part of the transaction, or perhaps when no one is around to notice the perpetrator digging into the cash drawer. In Case 1252, for instance, a teller simply signed onto a cash register, rang a “no sale,” and took currency from the drawer. Over a period of time, the teller took approximately $6,000 through this simple method.
EXHIBIT 3-4 Cash Larceny from the Register
Recall that the benefit of a skimming scheme is that the transaction is unrecorded and the stolen funds are never entered on company books. The employee who is skimming either under-rings the register transaction so that a portion of the sale is unrecorded or completely omits the sale by failing to enter it at all on his register. This makes the skimming scheme difficult to detect, because the register tape does not reflect the presence of the funds that have been taken. In a larceny scheme, on the other hand, the funds that the perpetrator steals are already reflected on the register tape. As a result, an imbalance will result between the register tape and the cash drawer. This imbalance should be a signal that alerts a victim organization to the theft.
The actual method for taking money at the point of sale—opening a cash drawer and removing currency—rarely varies; it is the methods used by fraudsters to avoid getting caught that distinguish larceny schemes. Oddly, in many cases the perpetrator has no plan for avoiding detection. A large part of fraud is rationalizing; the fraudster convinces himself that he is somehow entitled to what he is taking, or that what he is doing is not actually a crime. Cash larceny schemes frequently begin when perpetrators convince themselves that they are only “borrowing” the funds to cover a temporary monetary need. These people might carry the missing cash in their registers for several days, deluding themselves that they will one day repay the funds and hoping their employers will not perform a surprise cash count until the missing money is replaced.
The employee who does nothing to camouflage his crimes is easily caught; more dangerous is the person who takes active steps to hide his misdeeds. In the cash larceny schemes we reviewed, there were several methods used to conceal larceny that occurred at the point of sale:
- Thefts from other registers
- Death by a thousand cuts
- Reversing transactions
- Altering cash counts or register tapes
- Destroying register tapes
Thefts from Other Registers One basic way for an employee to disguise the fact that he is stealing currency is to take money from someone else's cash register. In some retail organizations, employees are assigned to certain registers. Alternatively, one register is used and each employee has an access code. When cash is missing from a cashier's register, the most likely suspect for the theft is obviously that cashier. Therefore, by stealing from another employee's register, or by using someone else's access code, the fraudster makes sure that another employee will be the prime suspect in the theft. In Case 1252 discussed above, for example, the employee who stole money did so by waiting until another teller was on break, then logging onto that teller's register, ringing a “no sale,” and taking the cash. The resulting cash shortage therefore appeared in the register of an honest employee, deflecting attention from the true thief. In another case the ACFE reviewed, Case 2127, a cash office manager stole over $8,000, in part by taking money from cash registers and making it appear that the cashiers were stealing.
Death by a Thousand Cuts A very unsophisticated way to avoid detection is to steal currency in very small amounts over an extended period of time. This is the “death by a thousand cuts” larceny scheme: $15 dollars here, $20 there—and slowly, as in Case 709, the culprit bleeds his company. Because the missing amounts are small, the shortages may be credited to errors rather than theft. Typically, the employee becomes dependent on the extra money he is pilfering, and his thefts increase in scale or become more frequent, which causes the scheme to be uncovered. Most retail organizations track overages or shortages by employee, making this method largely ineffectual.
Reversing Transactions Another way to conceal cash larceny is to use reversing transactions, such as false voids or refunds, which cause the register tape to reconcile to the amount of cash on hand after the theft. By processing fraudulent reversing transactions, an employee can reduce the amount of cash reflected on the register tape. For instance, in Case 2147, a cashier received payments from a customer and recorded the transactions on her system. She later stole those payments, and then destroyed the company's receipts that reflected the transactions. To complete the cover-up, the cashier went back and voided the transactions, which she had entered at the time the payments were received. The reversing entries brought the receipt totals into balance with the cash on hand. (These schemes will be discussed in more detail in Chapter 8.)
Altering Cash Counts or Cash Register Tapes A cash register is balanced by comparing the transactions on the register tape to the amount of cash on hand. Starting at a known balance, sales, returns, and other register transactions are added to or subtracted from the balance to arrive at a total for the period in question. The actual cash is then counted and the two totals are compared. If the register tape shows that there should be more cash in the register than what is present, it may be because of larceny. To conceal cash larceny, some fraudsters alter the cash counts from their registers to match the total receipts reflected on their register tape. For example, if an employee processes $1,000 worth of transactions on a register, then steals $300, there will be only $700 left in the cash drawer. The employee will falsify the cash count by recording that $1,000 is on hand so that the cash count balances to the register tape. This type of scheme occurred in Case 1806, when a fraudster not only discarded register tapes to conceal her thefts, but also erased and rewrote cash counts for the registers from which she pilfered. The new totals on the cash count envelopes were overstated by the amount of money she had stolen, reflecting the actual receipts for the period and balancing with the cash register tapes. Under the victim company's controls, this employee was not supposed to have access to cash. Ironically, coworkers praised her dedication for helping them count cash when it was not one of her official duties.
Instead of altering cash counts, some employees will manually alter the register tape from their cash registers. Again, the purpose of this activity is to force a balance between the cash on hand and the record of cash received. In Case 788, for instance, a department manager altered and destroyed cash register tapes to help conceal a fraud scheme that went on for four years.
Destroying Register Tapes If the fraudster cannot make the cash and the tape balance, the next best thing is to prevent others from computing the totals and discovering the imbalance. Employees who are stealing at the point of sale sometimes destroy detail tapes, which would implicate them in a crime.
Preventing and Detecting Cash Larceny at the Point of Sale Most cash larceny schemes only succeed because of a lack of internal controls. In order to prevent this form of fraud, organizations should enforce separation of duties in the cash receipts process and make sure there are independent checks over the receipting and recording of incoming cash.
When cash is received over the counter, the employee conducting the transaction should record each transaction. The transaction is generally recorded on a cash register or on a prenumbered receipt form. At the end of the business day, each salesperson should count the cash in his cash drawer and record the amount on a memorandum form.
Another employee then removes the register tape or other records of the transactions. This employee also counts the cash to make sure the total agrees with the salesperson's count and with the register tape. By having an independent employee verify the cash count in each register or cash box at the end of each shift, an organization reduces the possibility of long-term losses due to cash theft. Cash larceny through the falsification of cash counts can be prevented by this control, and suspicions of fraud will be immediately raised if sales records have been purposely destroyed.
Once the second employee has determined that the totals for the register tape and cash on hand reconcile, the cash should be taken directly to the cashier's office. The register tape, memorandum form, and any other pertinent records of the day's transactions are sent to the accounting department, where the totals are entered in the cash receipts journal.
Obviously, to detect cash larceny at the point of sale, the first key is to look for discrepancies between sales records and cash on hand. Large differences will normally draw attention, but those who reconcile the two figures should also be alert to a high frequency of small-dollar occurrences. Fraudsters sometimes steal small amounts in the hopes that they will not be noticed or so that such shortfalls will be too small to review. A pattern of small shortages may indicate the presence of this type of scheme.
Organizations should also periodically run reports showing the number of discounts, returns, adjustments, write-offs, and other concealing transactions issued by employee, department, or location. These transactions may be used to conceal cash larceny. Similarly, all journal entries to cash accounts could be scrutinized, as these are often used to hide missing cash.
Larceny of Receivables
Not all cash larceny schemes occur at the point of sale. As was discussed in Chapter 2, employees will frequently steal incoming customer payments on accounts receivable. Generally, these schemes involve skimming—the perpetrator steals the payment but never records it. In some cases, however, the theft occurs after the payment has been recorded, which means that it is classified as cash larceny. In Case 2758, for example, an employee posted all records of customer payments to date, but stole the money received. In a four-month period, this employee took over $200,000 in incoming payments. Consequently, the cash account was significantly out of balance, which led to discovery of the fraud. This was one of the cases in the ACFE studies, incidentally, in which the employee justified the theft by saying she planned to pay the money back. This case illustrates the central weakness of cash larceny schemes—the resulting imbalances in company accounts. In order for an employee to succeed at a cash larceny scheme, he must be able to hide the imbalances caused by the fraud. Larceny of receivables is generally concealed through one of three methods:
- Force balancing
- Reversing entries
- Destruction of records
Force Balancing Those fraudsters who have total control of a company's accounting system can overcome the problem of out-of-balance accounts. In Case 1663, an employee stole customer payments and posted them to the accounts receivable journal in the same manner as the fraudster discussed in Case 2758 above. As in the previous case, this employee's fraud resulted in an imbalance in the victim company's cash account. The difference between the two frauds is that the perpetrator of Case 1663 had control over the company's deposits and all its ledgers. She was therefore able to conceal her crime by force balancing: making unsupported entries in the company's books to produce a fictitious balance between receipts and ledgers. This case illustrates how poor separation of duties can allow the perpetuation of a fraud that ordinarily would be easy to detect.
Reversing Entries In circumstances in which payments are stolen but nonetheless posted to the cash receipts journal, reversing entries can be used to balance the victim company's accounts. For instance, in Case 1886, an office manager stole approximately $75,000 in customer payments from her employer. Her method in a number of these cases was to post the payment to the customer's account, and then to later reverse the entry on the books with unauthorized adjustments such as “courtesy discounts.”
Destruction of Records A less elegant way to hide a crime is to simply destroy all records that might prove that the perpetrator has been stealing. Destroying records en masse does not prevent the victim company from realizing that it is being robbed, but it may help conceal the identity of the thief. A controller in Case 1550 used this “slash-and-burn” concealment strategy. The controller, who had complete control over the books of her employer, stole approximately $100,000. When it became evident that her superiors were suspicious of her activities, the perpetrator entered her office one night after work, stole all the cash on hand, destroyed all records (among them her personnel file), and left town.
Cash Larceny from the Deposit
At some point in most revenue-generating businesses, someone must physically take the company's currency and checks to the bank. This person, or persons, literally left holding the bag, will have an opportunity to take a portion of the money prior to depositing it into the company's accounts.
Typically, when a company receives cash, someone is assigned to tabulate the receipts, list the form of payment (currency or check), and prepare a deposit slip for the bank. Then another employee, preferably one not involved in the preparing of the deposit slip, takes the cash and deposits it in the bank. The person who made out the deposit generally retains one copy of the slip. This copy is matched to a receipted copy of the slip stamped by the bank when the deposit is made.
EXHIBIT 3-5 Cash Larceny from the Deposit
This procedure is designed to prevent theft of funds from the deposit, but thefts still occur, often because the process is not adhered to (see Exhibit 3-5). In Case 1277, for example, an employee in a small company was responsible for preparing and making the deposits, recording the deposits in the company's books, and reconciling the bank statements. This employee took several thousand dollars from the company deposits and concealed it by making false entries in the books that corresponded to falsely prepared deposit slips. Similarly, in a retail store where cash registers were not used—in Case 2833—sales were recorded on prenumbered invoices. The controller of this organization was responsible for collecting cash receipts and making the bank deposits. This controller was also the only person who reconciled the totals on the prenumbered receipts to the bank deposit. Therefore, he was able to steal a portion of the deposit with the knowledge that the discrepancy between the deposit and the day's receipts would not be detected.
Another oversight in procedure is failure to reconcile the bank copy of the deposit slip with the office copy. When the person making the deposit knows that his company does not reconcile the two deposit slips, he can steal cash from the deposit on the way to the bank and alter the deposit slip so that it reflects a lesser amount. In some cases sales records will also be altered to match the diminished deposit.
When cash is stolen from the deposit, the receipted deposit slip will of course be out of balance with the company's copy of the deposit slip (unless the perpetrator also prepared the deposit). To correct this problem, some fraudsters alter the bank copy of the deposit slip after it has been validated. This brings the two copies back into balance. In Case 1446, for example, an employee altered twenty-four deposit slips and validated bank receipts in the course of a year to conceal the theft of over $15,000. These documents were altered with correction fluid or ballpoint pen to match the company's cash reports. Of course, cash having been stolen, the company's book balance will not match its actual bank balance. If another employee regularly balances the checking account, this type of theft should be easily detected.
Another mistake that can be made in the deposit function, and one that is a departure from common sense, is entrusting the deposit to the wrong person. For instance, in Case 693, a bookkeeper who had been employed for only one month was put in charge of making the deposit. She promptly diverted the funds to her own use. This is not to say that all new employees are untrustworthy—but it is advisable to have some sense of a person's character before handing that person a bag full of money.
Still another commonsense issue is the handling of the deposit on the way to the bank. Once prepared, the deposit should be immediately put in a safe place until it is taken to the bank. In a few of the cases we studied, the deposit was carelessly left unattended. In Case 2232, for example, a part-time employee learned that it was the bookkeeper's habit to leave the bank bag in her desk overnight before taking it to the bank the following morning. For approximately six months, this employee pilfered checks from the deposit and got away with it. He was able to endorse the checks at a local establishment, without using his own signature, in the name of the victim company. The owner of the check-cashing institution did not question the fact that this individual was cashing company checks because, as a pastor of a sizable church in the community, the fraudster's integrity was thought to be above reproach.
As with other cash larceny schemes, stealing from the company deposit can be rather difficult to conceal. In most cases these schemes are successful for a long duration only when the person who counts the cash also makes the deposit. In any other circumstance, the success of the scheme depends primarily on the inattentiveness of those charged with preparing and reconciling the deposit.
Deposit Lapping One method ACFE studies have identified as having been successfully used to evade detection is the lapping method. Lapping occurs when an employee steals the deposit from day one, and then replaces it with day two's deposit. Day two's deposit is replaced with day three's, and so on. The perpetrator is always one day behind, but as long as no one demands an up-to-the minute reconciliation of the deposits to the bank statement, and if the size of the deposits does not drop precipitously, he may be able to avoid detection for a period of time. In Case 1993, a company officer stole cash receipts from the company deposit and withheld the deposit for a time. Eventually the deposit was made and the missing cash was replaced with a check received at a later date. Lapping is discussed in more detail in Chapter 2.
Deposits in Transit A final concealment strategy with stolen deposits is to carry the missing money as deposits in transit. In Case 1716, an employee was responsible for receiving collections, issuing receipts, posting transactions, reconciling accounts, and making deposits. Such a lack of separation of duties leaves a company extremely vulnerable to fraud. This employee took over $20,000 in collections from her employer over a five-month period. To hide her theft, the perpetrator carried the missing money as deposits in transit, meaning that the missing money would appear on the next month's bank statement. Of course, it never did. The balance was carried for several months as “d.i.t.” until an auditor recognized the discrepancy and put a halt to the fraud.
Preventing and Detecting Cash Larceny from the Deposit The most important factor in preventing cash larceny from the deposit is separating duties. Calculating daily receipts, preparing the deposit, delivering the deposit to the bank, and verifying the receipted deposit slip are duties that should be performed independently of one another. So long as this separation is maintained, shortages in the deposit should be quickly detected.
All incoming revenues should be delivered to a centralized department where an itemized deposit slip is prepared, listing each individual check or money order along with currency receipts. Itemizing the deposit slip is a key antifraud control. It enables the organization to track specific payments to the deposit and may help detect larceny as well as lapping schemes and other forms of receivables skimming. It is very important that the person who prepares the deposit slip be separated from the duty of receiving and logging incoming payments so that he can act as an independent check on these functions. Before it is sent to the bank, the deposit slip should be matched to the remittance list to ensure that all payments are accounted for.
Typically, the cashier will deliver the deposit to the bank, while a cash-receipts clerk posts the total amount of receipts in the cash receipts journal. In some cases, the cashier does the posting, while a separate individual delivers the deposit. In either case, the duties of posting cash receipts and delivering the deposit should be separated. If a single person performs both functions, that individual can falsify the deposit slip or cash receipts postings to conceal larceny from the deposit.
Once the deposit has been totaled and matched to the remittance list, it should be secured and taken immediately to the bank, along with two copies of the deposit slip (one of which will be retained by the bank). A third copy of the deposit slip should be retained by the organization. When the deposit is made, one copy of the deposit slip is stamped (authenticated) by the bank as received. The bank then delivers this copy back to the depositing organization.
The authenticated deposit slip should be compared with the organization's copy of the deposit slip, the remittance list, and the general ledger posting of the day's receipts. If all four totals match, this verifies that the deposit was properly made. It is critical that someone other than the person who prepared the deposit reconcile the authenticated deposit slip. If the cashier, for example, is allowed to prepare and reconcile the deposit, the control function designed to prevent cash larceny at this stage is effectively destroyed. The cashier could falsify the deposit slip or force totals to conceal larceny. If fraud is suspected, verify each deposit prior to dispatch without the suspect's knowledge; then call the bank to verify that the entire deposit was made.
In order to further safeguard against larceny, two copies of the bank statement should be delivered to different persons in the organization. Each person should verify deposits on the bank statement to postings in the general ledger and to receipted deposit slips. If deposits in transit show up on a bank reconciliation, they should clear within two days of the date of reconciliation. Any instance in which a deposit in transit exceeds the two-day clear should be investigated.
To prevent deposit lapping, organizations can require that deposits be made in a night drop at the bank and verify each deposit at the beginning of the next day's business.
The following case study has been selected as an example of how an employee stole cash from his company's bank deposits. Bill Gurado, a branch manager for a consumer-loan finance company, took his branch's deposits to the bank himself, where he placed the money into his own account rather than his employer's. CFE Harry Smith audited Gurado's branch to determine the scope of his scheme. This case provides an excellent example of how an employee's perception of his company's controls can be valuable in preventing and detecting fraud.
CASE STUDY: THE OL' FAKE SURPRISE AUDIT GETS 'EM EVERY TIME2
Some people would say that auditors have no sense of humor—that they are a straight-laced, straight-faced bunch. Bill Gurado knows better.
Gurado worked as a branch manager for Newfund, a consumer-loan finance company in New Orleans. He was the highly respected leader of the company's oldest, largest, and most successful branch. With such a high profile, Gurado commanded a lot of respect. Other managers wanted to be like him. Employees respected him. Everyone in the company considered him a good guy.
For reasons not entirely clear, Gurado began stealing from the company. He did not take a lot of money. His scheme was less than brilliant. And because he did not appreciate an auditor's sense of humor, his fraud was brought to light just weeks after it began.
Newfund employed good controls, both from an accounting as well as a management standpoint. One control on which Barry Ecker, the company's internal auditor, relied was the surprise audit. He normally sprang surprise audits at least once, and sometimes twice, a year on each of Newfund's thirty branches. Due to the size of Gurado's branch, Ecker could not perform a surprise audit by himself. He would have to coordinate with the external audit staff. During these surprise audits, Ecker came in and took control from the start. He was extremely thorough. Harry J. Smith, one of the external auditors whose team would accompany him, describes Ecker as “your typical old-time sleuth-type auditor. A little bitty, short, pudgy guy who got a lot of psychic pleasure out of scaring the hell out of branch people. He'd come in and he'd be quiet and very secure about his papers and his area. He'd stare people down. He'd stare at ledger cards looking for irregularities. He'd just make people quake.” Adds Smith, “He was really fun to watch. When he was in his character, he was one for the books.” Having been through several surprise audits, Gurado knew the extent of Ecker's investigating. He probably had that in the back of his mind when he ran into Ecker at a store by chance over the weekend.
They had a brief conversation, and as might be expected from someone like Ecker, who enjoyed putting a little fear into people, he mentioned he was about to launch a surprise audit at Gurado's branch. “Well, I'll see you Monday,” he said without cracking a smile. “Harry and I are going to pull an audit on your branch on Monday morning.” Of course, he had no plans to audit the branch any time in the near future. As they parted, Gurado said, “Great. See you then.” But Gurado was not looking forward to seeing Ecker at all. He knew that Ecker, with all his searching and checking, would find some irregularities. He would piece together Gurado's fraud without much trouble at all. It would not take much effort to learn that Gurado had diverted company money into his own bank account.
Newfund's clientele was such that it received a lot of cash. For about a week Gurado took the daily deposits to the bank himself and deposited the money in his personal account. He made certain all the daily reports were sent to headquarters as usual—except, of course, the receipted bank deposit slips. It was only a few thousand dollars. But he had not yet had a chance to replace any of the money (if he had ever intended to), and he would not have time to cover his tracks before the “surprise” audit.
“He was absolutely convinced that had we audited his branch, we would find it,” says Smith. “And we probably would have. Barry Ecker did an old-style audit where you go in and seal the file cabinets and take immediate control of the cash drawers and the ledger tubs. It's a complete instantaneous control and tie-out. I'm pretty sure we'd have found it. I know the branch manager was convinced his boat was sunk.”
Gurado did some deep soul-searching that weekend. On Sunday night, he called on the president of the company, a man with a reputation of being a hard-driving, authoritarian individual. “I know it was a giant step for the branch manager to call him up that night,” Smith says. At the president's house that Sunday evening, Gurado came clean. “I know the auditors are coming tomorrow morning,” he said. Then he confessed to taking money from the company. He was immediately fired.
On Monday morning, Ecker called Smith at the accounting firm. He told Smith what had transpired, and then said, “Look, we gotta go audit the branch.” Smith and Ecker pulled out all the stops to get an audit team over to the branch to make sure there was nothing else going on.
They found exactly what Gurado had reported and nothing else. Looking back on this case, Smith feels certain the fraud would have been detected even without the misunderstood joke. Newfund practiced a control procedure that probably would have turned up the missing money within fifteen days. Because of that fact, he surmises that Gurado might have been covering some kind of short-term debt with the intent of repaying it.
Since Gurado returned the funds immediately and because he had confessed, the company did not pursue any criminal or civil action against him, feeling it a better course of action to keep the matter out of the public eye.
Word did travel quickly around the company, however—upper management made sure of that. The fact that this esteemed branch manager tripped himself up and immediately got caught went a long way toward reinforcing the importance of following proper procedures.
“People commonly measure auditing's benefit by the substance of its findings and recommendations,” Smith says. “Auditing's role in preventing abuse is hard to observe and measure and is often unappreciated. But this case clearly shows that the specter of having an audit certainly affects peoples' behavior.”
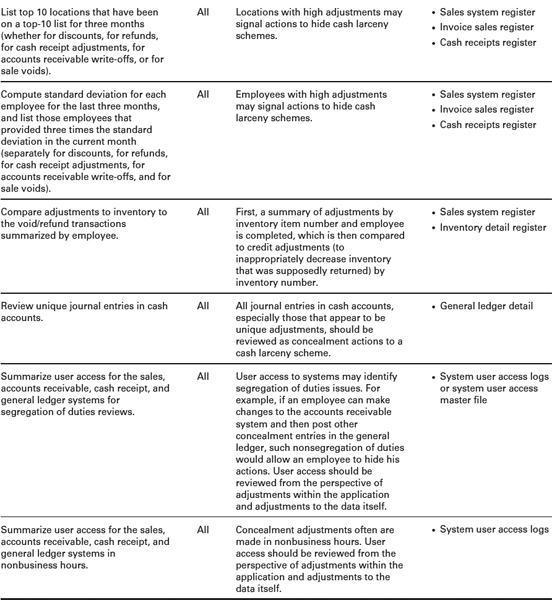
PROACTIVE COMPUTER AUDIT TESTS FOR DETECTING CASH LARCENY1

SUMMARY
Cash larceny is the intentional taking away of an employer's cash, currency, or checks, without the consent, and against the will, of the employer. Cash larceny schemes differ from skimming in that they are on-book frauds; they involve the theft of money that has been recorded in the employer's books, whereas skimming involves the theft of unrecorded cash. Because cash larceny schemes target recorded cash, these frauds leave a victim organization's books out of balance; cash on hand is reduced by the theft even as recorded cash remains constant. Cash larceny frauds are sometimes discovered as a result of this imbalance, but the perpetrator of a cash larceny scheme will often take steps to conceal the imbalance on the organization's books.
Most cash larceny schemes take place at the point of sale. Several methods can be used to conceal this type of fraud, most of them fairly uncomplicated. The perpetrator might steal from a cash register other than the one he is logged onto in order to keep from being a suspect. Another common scheme involves the repeated theft of very small amounts in hopes that the shortages will be disregarded by the organization. Reversing transactions such as fraudulent refunds can be processed to account for the missing funds. Cash counts or sales records may be altered to produce a false balance, or records may be destroyed altogether to prevent others from reconciling cash on hand to recorded sales. When employees steal receivables, as opposed to incoming sales, these thefts are typically concealed by force balancing, processing fraudulent discounts or other reversing entries, or destroying records of the transaction in question.
Cash larceny schemes also frequently target the victim organization's bank deposits. The perpetrator steals currency or checks after the deposit has been prepared but before it has been taken to the bank. These schemes frequently succeed when one person is in charge of calculating daily receipts, preparing the deposit, delivering the deposit to the bank, and verifying the receipted deposit slip. This breakdown in controls allows the perpetrator to steal cash without anyone detecting the resulting imbalances in the company's accounting records. In some cases, the perpetrator will lap daily receipts or list missing deposits as “deposits in transit” to further conceal the crime.
ESSENTIAL TERMS
Cash larceny The theft of an organization's cash after it has been recorded in the accounting system.
Cash receipts schemes Frauds that target incoming sales or receivables. Typically, the perpetrators in these schemes physically abscond with the victim organization's cash instead of relying on phony documents to justify the disbursement of the funds. Cash receipts frauds generally fall into two categories: skimming and cash larceny.
Deposit lapping A method of concealing deposit theft that occurs when an employee steals part or all of the deposit from one day and then replaces it with receipts from subsequent days.
Fraudulent disbursements Schemes in which an employee illegally or improperly causes the distribution of funds in a way that appears to be legitimate. Funds can be obtained by forging checks, submitting false invoices, or falsifying time records.
Reversing transactions A method used to conceal cash larceny. The perpetrator processes false transactions to void a sale or to refund cash, which causes sales records to reconcile to the amount of cash on hand after the theft.
REVIEW QUESTIONS
3-1 (Learning objective 3-1) What is cash larceny?
3-2 (Learning objective 3-2) How do cash larceny schemes differ from fraudulent disbursements?
3-3 (Learning objective 3-3) What is the difference between cash larceny and skimming?
3-4 (Learning objective 3-4) Where do cash larceny schemes rank among cash misappropriations in terms of frequency? In terms of median loss?
3-5 (Learning objective 3-5) What are the main weaknesses in an internal control system that permit fraudsters the opportunity to commit cash larceny schemes?
3-6 (Learning objective 3-6) What are the five methods discussed in this chapter that are used to conceal cash larceny that occurs at the point of sale? Explain how each works.
3-7 (Learning objective 3-8) How do employees commit cash larceny of incoming receivables? How are the schemes concealed?
3-8 (Learning objective 3-8) What is force balancing, and how is it used to conceal cash larceny?
3-9 (Learning objective 3-9) How do fraudsters commit cash larceny from the bank deposit?
3-10 (Learning objectives 3-5, 3-7, and 3-10) What are some basic internal control procedures to deter and detect cash larceny schemes?
DISCUSSION ISSUES
3-1 (Learning objectives 3-1, 3-6, 3-8, and 3-9) Briefly describe some common types of cash larceny schemes.
3-2 (Learning objective 3-3) Why is it generally more difficult to detect skimming than cash larceny?
3-3 (Learning objectives 3-2 and 3-3) In the case study of bank teller Laura Grove, what type of fraud did she commit?
3-4 (Learning objective 3-5) What are the internal control weaknesses that failed to deter and detect the fraud in Laura Grove's case?
3-5 (Learning objectives 3-6 and 3-7) Other than falsifying a company's records of cash receipts, how might an employee conceal larceny from a cash register?
3-6 (Learning objectives 3-10 and 3-11) What steps might an organization take to protect outgoing bank deposits from cash larceny schemes?
3-7 (Learning objective 3-8) How is the larceny of receivables often detected?
3-8 (Learning objective 3-11) In the case study “The Ol' Fake Surprise Audit Gets 'Em Every Time,” how did New-fund's accounting and management controls contribute to the detection of Gurado's fraud scheme? How did the resulting actions of management help to deter future frauds?
3-9 (Learning objective 3-11) Among the proactive audit techniques suggested in this chapter are (1) a summary, by employee, of the difference between cash receipt reports and the sales register system and (2) a summary, by employee, of discounts, returns, cash receipt adjustments, accounts receivable write-offs, and voids processed. Why would these two tests be effective in detecting cash larceny?