16
Artificial Intelligence Approach for Signature Detection
Amar Shukla, Rajeev Tiwari*, Saurav Raghuvanshi, Shivam Sharma and Shridhar Avinash
University of Petroleum and Energy Studies, Dehradun, Uttarakhand, India
Abstract
The globe today relies on multiple security systems to protect its data and monetary transactions. Handwritten signature recognition uses a variety of methods and algorithms. In this paper we leverage the OpenCV library and Qt for GUI to implement Support Vector Machine (SVM) and Histogram of Oriented Gradients (HOG). By using the SVM algorithm, one can find an N-dimensional plane that provides a distinctly classifiable classification of data points on a plane. Meanwhile, HOG is a feature descriptor of an image that simplifies the image by extracting the helpful information while discarding the extraneous information. We will convert the image into a feature vector of length according to the precision set by the end-user or developer, using HOG feature descriptors.
Keywords: HOG, SVM, machine learning, Open CV, signature recognition
16.1 Introduction
The Security Systems are designed for the authentication of the user who is trying to access any kind of confidential data with the verification techniques like Iris Scanner, Fingerprint detection, Handwritten signature Recognition, Vocal sound recognition system, any alphanumeric pass code, and many more techniques for the same.
With the advancement of technologies in today’s era, the number of intruders is also increasing all over the globe and fraudsters are multiplying day by day. Keeping this main aspect in mind, our project has derived which will initiate a basic security system in regard to Actual Signature and Frauds being caused due to Signature Forgery. There are ample cases intercepted daily in banks or places where a signature is still a must as an authentication factor that there are forged signatures that are so similar that normal people can neglect it and it won’t be cached.
This Handwritten Signature Security System will work on precision and if it detected any forgery, the output will be shown as wrong or Fraud! In the future this handwritten security system along with face detection algorithms can be used in ATM to withdraw cash to enhance security the OTP will send to the registered customer. Handwritten signatures are used regularly for a variety of purposes. Every individual will utilize a personal signature to sign a contract, approve a check payment, or review a job paper.
Haar Cascade Classifier (HCC) [1] is a machine learning technique for quick object detection based on a boosted cascade of hairlike features. The HCC technique had not previously been employed for handwritten signature identification and verification. The Persian writer database contains 8,280 pictures, while the GPDS synthetic Signature database contains information on 4,000 people. Every classifier was trained and tested using hundreds of thousands of signatures created by digitally modifying a signature image. This method outperformed other machine learning models in terms of results.
The text that follows provides a proposed practical [2] offline signature recognition system that uses the ORB feature extraction technique, which was created for a similar reason. The new technique they have proposed is simple to use and requires only a few signatures per user to achieve a high level of accuracy. The solution achieves a 91 percent recognition rate with a median matching time of only 7 ms.
The Support Vector Machine was used as the classification approach that we used. This approach enables student’s [3] signatures to identify and classify documents from the University of Mostar, such as essays and exams.
The most prevalent method of identifying a [4] person is through signature verification. This verification system was created to distinguish between false and genuine signatures. CNN’s have been used to learn attributes from preprocessed authentic and fraudulent signatures. The Inception V1 project served as the foundation for the CNN architecture (GoogleNet).
The study describes a method for [5] recognizing signatures and manuscripts on mobile devices that uses the Gray Level Co-occurrence Matrix (GLCM) for texture-based feature extraction and bootstrap for a single classification model. The strategy is successfully implemented for both offline and online use. During a user-based assessment, the experiment has an accuracy level of between 34% and 44%. Data from the same person produces 84.62% and 88.46% accuracy when it comes to online signature recognition. It has a success rate of 70% to 90% for online handwriting recognition.
- With the advancement of technologies in today’s era, the number of intruders is also increasing all over the globe and fraudsters are multiplying day by day.
- Keeping this main aspect in mind, our project has derived which will initiate a basic security system in regard to Actual Signature and Frauds being caused due to Signature Forgery.
- There are ample cases intercepted daily in banks or places where a signature is still a must as an authentication factor that there are forged signatures that are so similar that normal people can neglect it and it won’t be cached.
- This Handwritten Signature Security System will work on precision and if it detected any forgery, the output will be shown as wrong or Fraud!
- In the future this handwritten security system along with face detection algorithms can be used in ATM to withdraw cash to enhance security the OTP will send to the registered customer.
With the advancement of technologies in today’s era, the number of intruders is also increasing all over the globe and fraudsters are multiplying day by day. Keeping this main aspect in mind, our project has derived which will initiate a basic security system in regard to Actual Signature and Frauds being caused due to Signature Forgery.
There are sample cases intercepted daily in banks or places where a signature is still a must as an authentication factor that there are forged signatures that are so similar that normal people can neglect it and it won’t be cached. This Handwritten Signature Security System will work on precision and if it detected any forgery, the output will be shown as wrong or Fraud. In the future this handwritten security system along with face detection algorithms can be used in ATM to withdraw cash to enhance security the OTP will send to the registered customer.
16.2 Literature Review
The below study describe the detailed literature analysis in the field of signature recognition and the open CV techniques.
It is the method of verifying [6] authorship by comparing the signature to previously investigated and stored samples. This method is available both on-premises and off-premises and focuses on offline techniques. The work uses SIFT and SURF to improve offline signature recognition. To train and evaluate the SVM classifier, we used bag-of-words and radial basis functions (RBF). Vector quantization, each training picture was converted into a uniform dimensional histogram. Images were processed with OpenCV C++. This article compares SIFT and SURF on SVM-based RBF kernels. SIFT has 98.75 percent accuracy with the SVM-RBF kernel system, whereas SURF has 96.25 percent accuracy.
Facial Recognition Through Camera (FRTC) is a [7] case study that seeks to demonstrate the current state of the art in biological signature recognition in the wild with minimal data and maximum accuracy. Modern recognition technologies (OpenCV and Face API) were added to the FRTC system to improve the field recognition of biological signals. FRTC was supposed to outperform OpenCV and Face API. However, when these systems were tested in the field, their accuracy dropped substantially. The FRTC is 7.02 percent more accurate than OpenCV and -1 percent more accurate than Face API. The FRTC case study will be scrutinized based on students’ unknowing attendance.
A handwritten signature [8] is used in several applications regularly. One’s signature will be used to sign a contract, job papers, petitions, or authorize check payments. We can recognize and classify the work of University of Mostar students and other test materials using this daily-based biometric characteristic. This work accomplished feature extraction using an image processing tool known as the OpenCV library. We used a Support Vector Machine (SVM) to categorize our data.
Bank checks [9] are widely used for financial transactions in a variety of industries. Cheques are always hand examined. The traditional verification technique will always include the date, signature, legal information, and payment printed on the cheques. Preprocessing the image, extracting the relevant information, and finally recognizing and confirming the handwritten fields are steps in extracting legal information from a recorded cheque image. Image processing techniques such as thinning, median filtering, and dilation are also used in this procedure.
This article [10] processes photos using convolution neural networks for deep learning. Binary classification can be used to determine the origin of a signature. The most successful method is to insert the signature region of a scanned document into the trained model. It is the same sort of paper with the exact signature location. Tensor-slicing on Numpy arrays is used to choose a document element. Text and signatures are extracted using OpenCV. On a short data set, the researchers evaluated premade neural network models. The general audience is familiar with well-known writers’ signatures. Convolution networks can be used for real-world problems. The findings might be an excellent resource for students learning deep learning and applying it to computer vision problems.
Signatures are [11] vital to human existence as they represent identity. Innovative home solutions that leverage the Internet of Things are becoming more popular (IoT). Signature verification and recognition may also benefit finance, banking, home security, and insurance. This project aims to build a signature recognition system utilizing a Raspberry Pi 3 with an LCD touchscreen. Cropping and resizing the acquired signature picture Then, a binary image was used to train the artificial neural network (ANN). The trained ANN categorized the input signature to distinguish authenticity or counterfeit. A 99.77 percent identification rate was achieved during testing using an 85% confidence level.
Handwritten Signature Verification [12] has much room for improvement. It is challenging building feature extractors that can distinguish between valid signatures and sophisticated forgeries without dynamic information about the signing process. Writer-independent circumstances make this verification effort more difficult. This paper proposes an offline writer independent Deep Learning Ensemble model. So we RGBT cate-gorized our final prediction vector using two CNNs. To ensure the data set is diversified, we tested it on various data sets. Many data sets showed the best results.
Document identification, authentication, and indexing are all typical uses of signatures. Open document analysis has lately gotten more complex due to the prevalence of free-form items such as signatures. It has two main problems. Multiscale signature detection and segmentation from document pictures are proposed in this work. A new method computes 2D contour segments’ dynamic curvature rather than focusing on local changes. An LDA-based supervised learning approach for merging complementary shape information is presented herein. We investigate modern form representations, shape matching, dissimilarity measures, and multiple instance querying of documents for document picture retrieval. Offline, our matching methods are put to action. For this, we analyzed enormous datasets of printed and handwritten English and Arabic writings.
Denoising and extraction [13] are crucial in defect prognostics because noise obscures weak features. The wavelet transform has been widely used to minimize noise because it can encode frequency and time. SVD determines the optimal wavelet scale for periodicity detection. Both simulated and real-world data validate the proposed signal denoising technique. There are many ML based techniques which offers denoising and improve the scalability of images using various augmentation techniques [14–17].
It is difficult to detect and separate [18] free-form items in cluttered backgrounds. However, no suitable methods for document signature detection exist yet. This work presents a revolutionary multi-scale approach for recognizing and segmenting signatures on various materials. Our approach captures a signature’s structural saliency rather than its local aspects. This strategy is easy and customizable. A saliency metric measures the dynamic curvature of 2D contour pieces. These results were validated on vast datasets of handwritten and machine-printed texts.
16.3 Problem Definition
Recognizing signatures ignoring the variations such as: Variations due to different pens; variations arising out of the fact that “No two signatures of the same person are exactly the same”; any marks on the paper or any such element; overcoming the above variations and establishing the authenticity of a Signature; handwritten signature verification has been extensively studied and implemented. Its many applications include banking, credit card validation, security systems, etc. In general, handwritten signature verification can be categorized into two kinds of online verification and offline verification. On–line verification requires a stylus and an electronic tablet connected to a computer to grab dynamic signature information. Offline verification, on the other hand, deals with signature information that is in a static format.
16.4 Problem Definition
The basic workflow of the project which constitute the training and the testing phase of the process involved in the recognition system.
A signature recognition and verification system (SRVS) is a system capable of efficiently addressing two individual but strongly related tasks:
- Identification of the signature owner as described in the Figure 16.4.1.
- The decision whether the signature is genuine or forger as described in the Figure 16.4.2.
The procedure for classification of the signature image is as follows:
- Acquire the Signature images.
- Enhance image to remove noise and blurring.
- Extract the various features.
- Use these features to train the system using Feed Forward neural network.
- Employ unknown Signature image to extract its features.
- Perform the pattern matching with the data set.
- Do the classification.
- Decide between originals or forgeries.

Figure 16.1 Flow chart for the entire process.

Figure 16.2 Overall architecture of the signature recognition system contains signature acquisition, preprocessing, feature extraction, and classification.
Signatures are scanned in gray. The purpose of this phase is to make signatures standard and ready for feature extraction. The preprocessing stage includes the following steps:
- Image binarization
- Background elimination
- Noise reduction
- Width normalization
- Thinning.
16.4.1 Data Flow Process
The below process contains the data flow, which state the exact precision of the data in the right direction where the signature detection and the creation of the model is proposed in Figures 16.4.1.1 and 16.4.1.2.

Figure 16.4.1.1 Block diagram for the signature verification.

Figure 16.4.1.2 Data flow process.
16.4.2 Algorithm
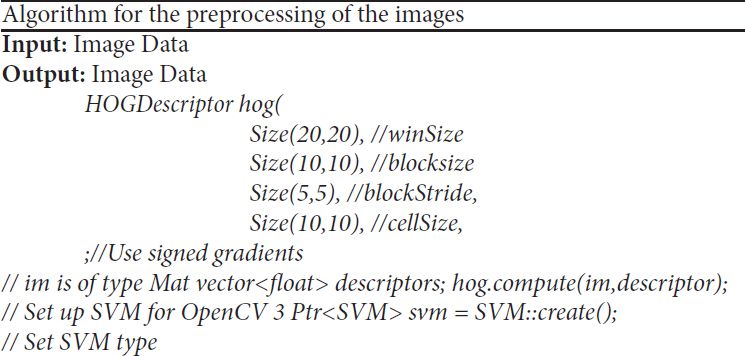
The below algorithm contains the preprocessing of the images where it contains the specific feature set of the signature to normalize the images and the removal of unnecessary noise this process becomes essential as achieved through the algorithm represented in the Table 16.4.2.1.
Table 16.4.2.1 Algorithm for the preprocessing of the images.

The below algorithm in Table 16.4.2.2 describes about the histogram of gradient approach for the detection of the hand written recognition which is essential for the demonstration of the intensity level in the images for detecting out the correct signature proportion.
Table 16.4.2.2 Algorithm for the histogram of gradients.

16.5 Result Analysis
There has been certain observation in the process of the algorithm where it contains the significant approach for the detection of the signature and also the descriptive analysis on the basis of the result achieved is shown in Figures 16.5.1, 16.5.2 and 16.5.3.

Figure 16.5.1 Training, testing phase of the data set and the grey scale and signature identification of the image set.

Figure 16.5.2 Features of the desired object are saved.

Figure 16.5.3 Intensity and the density observation on the basis of the image.
There has been the certain observation which continues the better observation of the Signature and demonstrates the effective prediction rate of the Signature. Since other graph base analysis is also performed in the study which demonstrates the intensity level of the identified Signature. Calculating the feature of the person which has to be identified from the image data set.
The average rate of the thresholding of the predicted signature from the data set.
16.6 Conclusion
We suggested a unique signature detection and segmentation technique based on the idea that object recognition may be seen as a process. A Substantial approach has determined the motivation that can enrich the application’s use in all the e verification and documentation. It is also one of the effective signature identification techniques that have to be achieved to detect and recognize the signature in document verification. This novel approach provides better accuracy in detecting the signature, a natural handwriting approach.
References
- 1. Blajer, J.A.G.W. and Krawczyk, M., The inverse simulation study of aircraft flight path reconstruction. Transport, XVII, 3, 103–107, 2002.
- 2. Al-Tamimi, A.K., Qasaimeh, A., Qaddoum, K., Offline signature recognition system using oriented FAST and rotated BRIEF. Int. J. Electr. Comput. Eng. (2088-8708), 11, 5, (2021).
- 3. Marušić, T., Marušić, Šeremet, Identification of authors of documents based on offline signature recognition, in: 2015 38th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), pp. 1144–1149, 2015.
- 4. Mohapatra, R.K., Shaswat, K., Kedia, S., Offline handwritten signature verification using cnn inspired by inception v1 architecture, in: 2019 Fifth International Conference on Image Information Processing (ICIIP), pp. 263– 267, 2019.
- 5. Hiryanto, L., Yohannis, A.R., Handhayani, T., Hand signature and handwriting recognition as identification of the writer using gray level co-occurrence matrix and bootstrap, in: 2017 Intelligent Systems Conference (IntelliSys), pp. 1103–1110, 2017.
- 6. Nasser, A.T. and Dogru, N., Signature recognition by using SIFT and SURF with SVM basic on RBF for voting online, in: 2017 International Conference on Engineering and Technology (ICET), pp. 1–5, 2017.
- 7. Gandhi, V. and Singh, J., Intensified biological signature recognition in the wild: A case study, in: 2021 12th International Conference on Computing Communication and Networking Technologies (ICCCNT), pp. 1–6, 2021.
- 8. Marušić, T., Marušić, Šeremet, Identification of authors of documents based on offline signature recognition, in: 2015 38th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), pp. 1144–1149, 2015.
- 9. Dhanawade, A., Drode, A., Johnson, G., Rao, A., Upadhya, S., Open CV based information extraction from cheques, in: 2020 Fourth International Conference on Computing Methodologies and Communication (ICCMC), pp. 93–97, 2020.
- 10. Afanasyeva, Z.S. and Afanasyev, A.D., Signature detection and identifi-cation algorithm with CNN, Numpy and OpenCV, in: Proceedings of the Computational Methods in Systems and Software, pp. 467–479, 2020.
- 11. Gunawan, T.S., Hamzah, N.A., Kartiwi, M., Effendi, M.R., Ismail, N., Anwar, R., Security enhancement of smart home system using signature recognition on raspberry Pi, in: 2020 6th International Conference on Wireless and Telematics (ICWT), pp. 1–6, 2020.
- 12. Das, S.D., Ladia, H., Kumar, V., Mishra, S., Writer independent offline signature recognition using ensemble learning. arXiv preprint arXiv:1901.06494, 2019. https://doi.org/10.48550/arxiv.1901.06494.
- 13. Qiu, H., Lee, J., Lin, J., Yu, G., Wavelet filter-based weak signature detection method and its application on rolling element bearing prognostics. J. Sound Vib., 289, 4-5, 1066–1090, 2006.
- 14. Kaur, P., Harnal, S., Tiwari, R., Upadhyay, S., Bhatia, S., Mashat, A., Alabdali, A.M., Recognition of leaf disease using hybrid convolutional neural network by applying feature reduction. Sensors, 22, 2, 575, 2022.
- 15. Kaur, P., Harnal, S., Tiwari, R., Upadhyay, S., Bhatia, S., Mashat, A., Alabdali, A.M., Recognition of leaf disease using hybrid convolutional neural network by applying feature reduction. Sensors, 22, 2, 575, 2022.
- 16. Kaur, P., Harnal, S., Tiwari, R., Alharithi, F.S., Almulihi, A.H., Noya, I.D., Goyal, N., A hybrid convolutional neural network model for diagnosis of COVID-19 using chest X-ray images. Int. J. Environ. Res. Public Health, 18, 22, 12191, 2021.
- 17. Nagaraju, M., Chawla, P., Upadhyay, S., Tiwari, R., Convolution network model based leaf disease detection using augmentation techniques. Expert Syst., 39, e12885, 2022.
- 18. Zhu, G., Zheng, Y., Doermann, D., Jaeger, S., Multi-scale structural saliency for signature detection, in: 2007 IEEE Conference on Computer Vision and Pattern Recognition, 39, pp. 1–8, 2007.
Note
- * Corresponding author: [email protected]; [email protected]
