▶ 8.7 Resources
Important Terms Introduced
Abbreviations Introduced
8.7.1 Review Questions
-
R1. Summarize the challenges of key management.
-
R2. If we need enough entropy for a 16-byte key, why should we hash a 20-byte (or larger) passphrase?
-
R3. Explain the reused key stream problem.
-
R4. Describe the role of the nonce in preventing reused key streams when using the same passphrase to encrypt different files.
-
R5. Describe how key wrapping may be applied to file encryption.
-
R6. What is the difference between key splitting and key wrapping?
-
R7. Summarize the reasons for rekeying an encrypted file.
-
R8. Describe the different categories of asymmetric encryption algorithms and how they are used in practice.
-
R9. What information must be shared to implement Diffie–Hellman key sharing? What is the result?
-
R10. What information must be shared to exchange a wrapped key using RSA?
-
R11. What information must be shared to validate a digital signature using RSA?
-
R12. What information must be available to validate a chain of certificates?
-
R13. Describe the differences between a hierarchical PKI and one that relies on a web of trust.
-
R14. Explain how one might establish trust in a self-signed certificate.
8.7.2 Exercises
-
E1. We want to calculate the amount of “secret entropy” in different implementations of file encryption—that is, the amount of truly secret, unpredictable information used to produce the ciphertext. We need a 16-byte secret key to encrypt the file. Use the estimate of three letters per character when estimating the entropy in text. (See Section 6.4.2.)
Assume we encrypt the file with a 24-letter text passphrase truncated as shown in Figure 8.1.
Assume we encrypt the file with a 24-letter text passphrase hashed as shown in Figure 8.2.
Assume we encrypt the file with a 24-letter text passphrase hashed with a nonsecret nonce as shown in Figure 8.5.
-
E2. Redraw Figure 8.6 to show how to decrypt a ciphertext file that contains a wrapped key. Be sure to include all necessary components from the original diagram and omit any unnecessary components.
-
E3. Redraw Figure 8.6 to incorporate passphrases collected from two separate users. Combine the passphrases so that the encrypted file can be decrypted if either passphrase is provided. This allows someone who knows either passphrase to decrypt the file.
-
E4. Redraw Figure 8. 6 to incorporate passphrases collected from two separate users. Combine the passphrases to implement Separation of Duty. The encrypted file should be decrypted only if both passphrases are provided.
-
E5. Assume that we can perform 10 million trials per second on our desktop machine. How long will it take us to crack a 1024-bit Diffie–Hellman key? Use the information in Table 8.2.
-
E6. Bob plans to use Diffie–Hellman to construct a shared secret to encrypt a file shared with Alice. Eve wants to perform a bucket brigade attack and read the shared file.
Draw a diagram similar to Figure 8.14, showing how Eve takes part as an invisible participant of the Diffie–Hellman exchange between Bob and Alice.
Based on your answer to (a), draw a diagram showing how the contents of Bob’s file is shared with Alice.
-
E7. Bob’s little brother loves crypto, especially public-key technology, but he doesn’t understand how some of it works. He wrote his own encryption program, shown in FIGURE 8.33. Draw a diagram showing how Bob could decrypt this message. Omit unnecessary steps.
-
E8. Bob signed an IOU with a digital signature. The signature uses a 2048-bit RSA key and a 128-bit hash.
How many trials should it take, on average, to crack the RSA key?
How many trials should it take, on average, for a birthday attack to succeed against a 128-bit hash?
Given the previous answers, which is weaker—the hash or the RSA key?
-
E9. PGP uses public keys to wrap the content key when encrypting a file. Bob wants to share a file with Tina and Alice. He has public keys from each of them. Draw a diagram showing how the file is encrypted and the keys wrapped so that either Tina or Alice may decrypt the file.
-
E10. Amalgamated Widget has entered a partnering agreement with Foonley Corporation. As a result, email encryption will interoperate between Amalgamated and Foonley. Instead of inserting a second root key into everyone’s email software, Amalgamated has published a certificate containing Foonley’s root key, signed by Amalgamated’s root. Draw a diagram showing how a certificate signed by Foonley’s root is thus validated using Amalgamated’s root key.
-
E11. Identify one or more DRM systems that you use yourself. Describe any problems that occurred using them.
-
E12. Locate a news report of a cyberattack that subverts public-key certificates. For example, this could be an attack on a certificate authority, or theft of a private key associated with a victim’s published public-key certificate (i.e., for a website). Write an attack case study about it.
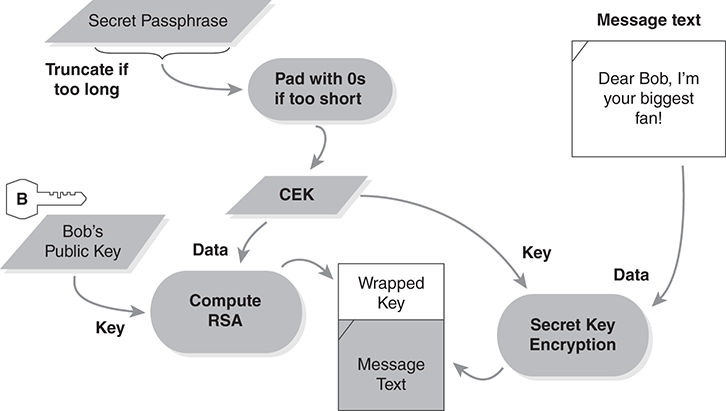
FIGURE 8.33 Little brother’s encryption program.
