▶ 1.2 Assessing Risks
The simplest way to address a security problem is the rule-based approach. Well-known risks often imply one or more specific security measures, often from a checklist. To defend against thieves walking through an open door, we put a lock on the door and keep it locked.
Alice can’t leave her shop door locked during working hours. It remains unlocked so that customers may enter and leave. She must stay in the shop herself to help customers and to foil shoplifters or other thieves. If she needs a quick break, she closes the shop, locks the door, and leaves a sign saying “Back in 10 minutes.”
Alice didn’t perform a detailed risk assessment to arrive at this conclusion. She recognized the risks from her own shopping experiences and from working in other stores. Her experiences haven’t really taught her rules of cybersecurity.
Rule-Based Risk Assessment
One problem with Alice’s situation is its scale: While attacks on her business may have an impact on her personally, its failure won’t have an impact on the local, regional, or national economy. Attacks on large private companies or on government agencies have broader impacts. This is why NIST developed the Risk Management Framework: to provide rules by which government agencies can assess their risks and construct a list of security requirements. Agencies apply the RMF to individual systems and to systems built of multiple systems. NIST has published a series of publications, including Federal Information Processing Standards (FIPS) and Special Publication (SP), to guide users of the RMF. Here are the key documents:
■ SP 800-30, Guide for Conducting Risk Assessments
■ SP 800-37, Guide for Applying the Risk Management Framework to Federal Information Systems
■ FIPS 199, Standards for Security Categorization of Federal Information and Information Systems
■ SP 800-60, Guide for Mapping Types of Information and Information Systems to Security Categories
■ SP 800-53, Security and Privacy Controls for Federal Information Systems and Organizations
The RMF begins with a high-level estimate of the impact caused by cybersecurity failures. This is called the security category (SC). FIPS 199 explains how a system’s security category is defined, with SP 800-60 providing more detailed guidance. The RMF uses the system’s security category to help select security controls from tables provided in SP 800-53.
The security category indicates the significance of security failures in terms of three general security properties, often called the CIA properties:
Confidentiality: The organization is obliged to keep some information confidential; how bad is the impact of confidential information being disclosed by the system?
Integrity: Computer systems misbehave or fail entirely if programs or data suffer undesired or unintended modifications; how bad is the impact of such modifications to this system?
Availability: Computer systems support the enterprise’s ongoing operations. If this system isn’t available, how bad is the impact?
The process estimates the potential impact of a failure on organizations or individuals. A four-point scale indicates the potential impact for each property:
■ Not applicable (NA): The system handles public data, and disclosure has no impact. This only applies to the confidentiality property.
■ Low impact: The failure has a noticeable impact on one or more of the agencies’ missions, or it causes minor damage to assets, minor financial loss, or minor injury to individuals.
■ Moderate impact: The failure has a significant impact on mission effectiveness, or it causes significant damage to assets, significant financial loss, or significant injury to individuals that does not involve loss of life or life-threatening injuries.
■ High impact: The failure has a severe or catastrophic impact that prevents the agency from performing one or more of its primary functions, or it causes major damage to assets, major financial loss, or severe injury to individuals that involves loss of life or life-threatening injuries.
The security category is expressed by noting the impacts of failures in the three security properties. We express the SC in terms of a particular type of information or system, indicated below by name:
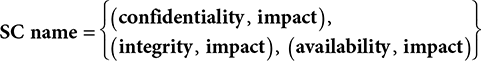
Let us look at a more specific example.
Amalgamated Widget, called “Amawig” for short, is a major manufacturer. It relies primarily on third-party distributors to sell its products. Although it has a website, the site’s purpose is to inform shareholders and to encourage potential customers to visit distributors to buy the products. A customer looking for an Amawig product through a web search will see numerous sites describing its products, most of which belong to product distributors or retail outlets.
Amawig’s website provides publicity to company products and describes the company in general. Everything it provides is public information. The website is not the only one that provides access to Amawig products. In fact, a potential customer needs to go to a distributor or retailer to buy products. To assess the three security properties:
Confidentiality: Not applicable because all information is public.
Integrity: Low because a site outage will not prevent customer sales.
Availability: Also low because a site outage doesn’t prevent customer sales.
Here is the resulting SC:

Not all websites pose such a small risk. Let us reconsider the risks after Amawig expands its business. As part of a new product introduction, Amawig has decided to offer the product directly to customers via a new website and not sell it through distributors. The new sales site represents the only way to purchase that product. After 6 months, the new product represents a small, but significant, source of revenue. We need to reassess the three security properties:
Confidentiality: Moderate because the website handles some electronic payment information from customers.
Integrity: Moderate because the website handles some electronic payment information from customers, it specifies product prices, and it directs product shipments.
Availability: Moderate because an interruption would visibly affect sales, but would not cause long-term damage to the company.
Here is the SC for the new website:

Many companies use a single organization to manage their websites, or they might host all of their web presence on a single site. What is the SC of the resulting website, if we combine both of Amawig’s sites? According to FIPS 199, we examine each security property for each website and choose the highest impact value for each, with NA being the lowest. The combined site’s SC is the same as the sales site’s SC because the sales site has a higher impact in each property.
We establish the SC as part of the first step of the Risk Management Framework. SP 800-53 identifies security controls required in response to different impact values. This provides a rule-based approach to risk management. In smaller-scale systems, the required controls may map directly to available technical measures provided by the system’s vendor. In larger-scale systems, the mapping might not be so simple, and the required controls may reflect security requirements to be met by a cooperating set of technical measures.
1.2.1 The Proprietor’s Risk Management Framework
The NIST’s RMF is well-documented and organized, but it doesn’t really apply to Alice’s situation. As sole proprietor of her business, she directly receives the benefits and troubles arising from her security measures, or lack thereof. The PRMF provides a more detailed and personalized assessment process than RMF’s rule-based framework.
In this chapter, we look at Step A of the PRMF: We establish Alice’s system and security goals. This yields a list of security requirements, sometimes called a security policy. We look at the problem of matching controls to those requirements in a later chapter. We perform Step A in three general parts: identifying risks, assessing risks, and identifying requirements. The process unfolds in six steps, as shown in BOX 1.1.
Cybersecurity risks can include a broad range of threats and potential events. In large-scale corporate or government environments, attacks can affect whole communities or regions. The RMF structures its risk assessment in those terms. If Alice’s business fails, it will severely affect Alice and some of her business associates, but it shouldn’t cripple the area or regional economy. Alice needs to consider risks at a smaller scale than the RMF.
To identify Alice’s risks, we look at her assets and threat agents. These reflect the potential attacks and defenses she will require. We produce our list of risks by studying these elements in the context of our assets and the boundaries we’ve built around them. FIGURE 1.4 illustrates the relationship of these elements.

FIGURE 1.4 Elements of identifying risks.
Our first step is to identify the goals of the activity or enterprise that uses computing resources. These may be in terms of services rendered, things built and sold, transactions performed, and so on. These goals rely on particular computing assets, which may be computing equipment, data, or supported activities.
A threat agent is someone who is motivated to attack our assets. We don’t identify threat agents by name; we identify them in terms of their behavior. Alice’s shop faces two obvious threat agents: burglars and shoplifters. Shoplifters aren’t likely to steal or damage Alice’s computing assets, but a burglar could steal her equipment. Alice uses the internet for online banking, merchandise ordering, and marketing, so she also faces internet-based threat agents.
An attack is an attempt by a threat agent to exploit the assets without permission. We call a threat agent an attacker when action replaces inclination and the attack actually takes place. If we have defined a security boundary, then an attack may be an attempt to breach the boundary. While thefts or acts of meddling may be attacks, we need to be more specific to perform a risk assessment. Typically, we identify attacks in terms of exploited vulnerabilities and broken defenses.
A vulnerability is a weakness in the boundary that protects the assets from the threat agents. We often see this as an opening or other weakness in the boundary. For example, a door represents a vulnerability because it can admit thieves into Alice’s store.
A defense, safeguard, or countermeasure is a security measure intended to protect the asset. The boundary is the basic defense. Additional defenses often are associated with specific vulnerabilities. For example, a door lock is a defense intended to address the vulnerability posed by a door.
Fine Points of Terminology
Threat agents and attackers both refer to people or other active entities; we distinguish them by what they have done, not what they might do. For example, Alice might think of customers in her store as threat agents: potential shoplifters. If a customer shoplifts, then the customer is in fact an attacker. A threat agent is a person who might attack our assets; an attacker did attack an asset.
If there is a way to exploit a vulnerability to attack the assets of a particular system, the strategy is called an attack vector. The vulnerability holds the potential for attacks; the attack vector is a practical application of the vulnerability. An attack vector in one environment might succeed and might be blocked in a different environment.
A system’s attack surface represents the range of attack vectors it faces. We generally speak of attack surfaces in relative terms: whether a change might increase or decrease the attack surface.
A compromised system is one that is no longer safe to use following an attack. An attack may compromise a system by disabling security measures, which increases the risk of leaking confidential information. An attack may also install malware that bypasses security measures and allows the attacker to easily penetrate the system again or use it as a platform to attack other systems.
A botnet is a collection of compromised systems controlled remotely by the attacker. Botnets may contain thousands of computers. Each compromised system contains special software to allow the network’s controller to give commands to the systems. Such systems often send the junk email we call “spam.” By spreading the emails out among thousands of systems, the flood of email isn’t detected as a flood.
Hackers
The hacker has become an almost mythical figure in the computing community. The term originally arose in university research labs to refer to local experts with an almost uncanny understanding of computer systems. In the 1980s, the popular press used the term to identify people who attacked computers and other systems. A lexicon has developed to identify different people involved in attacking computer systems:
■ Script kiddie—A person who uses an attack developed by another party to attack computers. The attack may be implemented using a “scripting language,” so the attacker literally executes the script to attack the computer.
■ Cracker—A person who has learned specific attacks on computer systems and can use those specific attacks. A cracker doesn’t necessarily have the technical knowledge to modify the attacks and apply them to different types of targets.
■ Phone phreak—A person who attacks telephone systems, usually to make long distance and international calls for free. John Draper (nicknamed “Captain Crunch”) was a notorious phone phreak in the early 1970s.
■ Hacker—A person with a high degree of knowledge and skill with computing systems, including the ability to attack them if so motivated. The term arose at Massachusetts Institute of Technology (MIT) in the 1950s and was applied to computer enthusiasts in the 1960s.
■ Black-hat hacker—A person skilled in attacking computer systems, who uses those skills to attack a system. During the 1980s and 1990s, Kevin Mitnick became notorious for both phone phreaking and for computer break-ins. Following a prison term, Mitnick became a writer and consultant.
■ White-hat hacker—A person skilled in attacking computer systems, who uses those skills as a security expert to help protect systems. Experts like Jeff Moss and Ray Kaplan have used their knowledge of hacking and the hacker community to bring such information to the security community.
Today, the term hacker is almost always used in the context of computer security, and the hacker is able to penetrate a system of interest. The term “black hat” or “white hat” indicates the hacker’s motivation: whether he or she is inclined to attack or to defend systems.
“Reformed” black-hat hackers pose a dilemma for the cybersecurity community. Although their knowledge is often valuable, many companies will not hire a convicted felon to do security work, regardless of skill. There are a few well-known exceptions, including Mitnick and Frank Abagnale, the central character of the film Catch Me if You Can (2002).
1.2.2 Goals and Assets
When Alice hangs pictures in her store, she uses whichever hammer she finds in her toolbox. She’s not especially aware of subtle differences between hammers and has no preference for one over another. Alice feels the same way about her computers. As long as they respond the way she expects, she doesn’t care what she uses.
Alice’s computers are not her only cyber assets, nor are they her most important cyber assets; she can use other computers if necessary. Her principal cyber assets are the data files and services available through her computers. Even if Alice has her computers insured or can easily replace them some other way, she still needs her files, databases, and passwords.
Identifying Goals
To identify assets, we first look at overall goals and objectives in a real-world context. Alice doesn’t measure her store’s success in terms of her computer’s reliability. She measures it through customer visits, repeat visits, revenues, and profits.
To identify Alice’s cyber risks, we first identify the cyber assets she uses to achieve those goals, directly or indirectly. The computer might not help her choose the item to show to a particular customer, but it helps her stay in business and bring in items that will appeal to her customers. Her goals are to stay in business and offer appealing merchandise to her customers.
Identifying Assets
Now that we have identified Alice’s goals, we identify computing activities and resources that support those goals. We should strive for a complete list. If we omit any goals supported by her computer, then we won’t identify risks associated with those goals. Here are examples of computing activities and resources to consider as Alice’s assets:
■ Computer hardware; each hardware item is itself an asset.
■ Purchased software; each purchased software package can incur an expense if it’s lost. At the least, it will cost Alice time to reinstall software if she must replace her computer hardware. There may also be extra purchase costs if the installation disks are lost.
■ Operating system installation disk, if any
■ Office software installation disk, if any
■ Computer customization; it takes time to install and organize information on a computer in a way that works efficiently. Alice takes her desktop layout very seriously. This time must be spent if a computer is lost and replaced by a new one.
■ Spreadsheets for tracking cash flow
■ Online bank account and its credentials
■ Online merchandise purchasing accounts and their credentials
■ Social media accounts and their credentials
This list is sufficient for Alice’s situation, even though the list is not necessarily complete. Every user needs to analyze goals individually or in terms of his or her organization. This asset list serves as an example.
1.2.3 Security Boundaries
Physical security is the foundation of all computer security. We need to keep our computing equipment physically protected from threat agents. If we can rely on the safety of the physical hardware, then we can focus our efforts on keeping the software secure. However, no amount of software security can redeem a system whose hardware has been compromised.
Boundaries are the essence of physical protection. A physical boundary establishes a container for our assets. We protect the assets from threat agents by denying them access to the container’s contents. We measure the degree of protection by the strength of the boundary; we achieve strong protection if the boundary is very difficult to breach without permission.
Least Privilege: A Second Basic Principle
Asset security depends on the people who can cross the boundary. In general, an asset is safer if we limit the number of people allowed inside its security boundary. We also restrict what each person may do to the asset, if possible. We call this least privilege. We enforce least privilege when we give people as few privileges as possible regarding the assets we try to protect.
Example: Boundaries in a Store
FIGURE 1.5 illustrates boundaries in and around Alice’s Arts. Although the front door is generally unlocked for customers, they are forced to pass near the sales counter when they enter or leave. Alice grants access to rooms inside the store as required by her customers or employees.

FIGURE 1.5 Physical boundaries in Alice’s store.
For example, Alice has given a set of keys to Nita, who works for her as a sales clerk. Nita is responsible for opening the store some mornings. Alice gave her a key to the front door and to the storage room in the back. These keys allow Nita to open the store and replenish items that are sold. Nita may even lock up the store, if necessary, while she runs an errand or is busy in the back of the store. The keys do not unlock Alice’s office. Nita is a trustworthy employee, but her job does not require access to Alice’s office.
We’d like to exclude all threat agents from Alice’s store, but there’s no practical way to do so. Although most customers are honest, a small number shoplift. This is why Alice always has someone in the store while it is open and has placed the sales counter next to the door.
Boundary security has an obvious problem: Protecting the boundary is not the same as protecting the asset itself. Sometimes we can’t help but grant access to a threat agent, regardless of how careful we might be. Nita herself may be a trustworthy employee, but Alice’s next hire might not be. Alice keeps her computer locked in her office most of the time. She might move it out into the store when she is working there, but she always puts it away and locks it up if she’s not in the store.
Analyzing the Boundary
Boundaries consist of two parts: the “walls” and the “doorways.” The walls are fixed parts of the boundary that nobody can cross, not even those allowed inside. The doorways are the parts of the boundary that allow passage. The security challenge is to allow passage through the doors without letting any threat agents through. In computing, we often refer to the doorways as interfaces between the inside and the outside.
When analyzing security, a boundary poses four questions:
What must a threat agent do to breach a wall?
How do we control the doorways to exclude threat agents?
How can a threat agent pass through the doorway despite our protections?
What do we trust those we let inside to do—or not to do?
The point of the boundary is to keep the threat agents outside, away from our assets, and allow the trustworthy inside. The first question asks about the risk of breaching a wall. If it’s practical for a threat agent to breach a wall, the risk assessment must include that risk in our assessment. In many cases, walls are strong enough not to be breached, and the risk is not important.
The second question asks how we control access to doorways. In a store, office, or home, the answer usually involves keys of some kind, either mechanical or electronic. In computing, we use special security controls built into our software. Our risk assessment identifies threat agents, and our security requirements identify whom we allow through the door. In Step B of the PRMF, our implementation shows how we control the door.
The third question considers the likelihood of an attacker breaking the access control or tricking it somehow. This leads to a trade-off between alternative security measures. A stronger or more sophisticated locking mechanism, or an armed guard, might further reduce the risk. The choice hinges on whether the cost of an attack justifies the more expensive security measures.
The Insider Threat
The fourth question asks about the insider threat: What threat agents exist inside our security boundary? Although it is tempting to treat all threat agents as purely bad and anyone we trust as perfectly good, the world is not so simple. Some people are clearly threat agents in some cases but are trustworthy in others.
Alice must generally trust her clerks not to steal money from her. She can detect thefts from cash sales because her POS computer keeps track of the money collected. A clerk might steal cash one day and convince Alice that it was a mistake in making change, but large and repeated errors will cast suspicion on the clerk.
Like most stores, Alice’s Arts has large glass windows and doors. A motivated burglar could definitely break some glass and steal some merchandise. Alice can’t prevent such an attack, but she can detect it. She improves her security by installing an alarm to call for help if a breach occurs. Alarms don’t provide physical protection, but they pose a risk to the attacker: Can the attack succeed and the attacker withdraw to safety before someone answers the alarm? Many attackers rely heavily on stealth, and the alarm makes a stealthy attack less likely. The alarm might not deter all attackers, but it helps us recognize when attacks occur and helps motivate a rapid response.
1.2.4 Security Architecture
We often organize a security problem by defining boundaries and doorways in one sense or another. Alice uses physical walls and doorways. Her “security architecture” consists of the security measures she applied and how they interact.
When we write a computer program, we establish boundaries when we put different functions into different procedures and files. We create doorways when we provide functions that different procedures may use. These decisions establish the structure of the program.
When we establish boundaries and doorways to address an information security problem, we produce an information security architecture. Such an architecture often relies on boundaries inside the computer to protect important information and programs from error-prone or malicious programs.
Within a security architecture, we often find separate security domains. Each domain is a place marked by security boundaries; each domain has its own set of security expectations. For example, if Alice’s store is inside a shopping mall, then the separate stores represent different security domains. Alice’s access rights to her own store do not grant her access rights to other stores. Each store has its own security expectations.
Separate domains may each require a separate security architecture. Each domain has its objectives and assets. Each domain has its policy for protecting and restricting actions. Each domain has its own trade-off to choose security over potential risk.
A security plan is a security architecture study that focuses on security requirements and implementation. The plan identifies appropriate security measures to protect against an identified set of security risks; it also guides the builders to produce a secure system. Structurally, the plan focuses on security requirements and security controls. An effective plan includes security monitoring in its requirements and controls.
Defense in Depth: A Third Basic Principle
Alice’s store opens directly onto a public street. A burglar who breaches the front door has unfettered access to her merchandise. Alice’s store might be safer as part of an enclosed shopping mall. The mall is closed to the public when the stores are closed. A burglar would then have to penetrate two separate, locked doors to reach Alice’s merchandise. This makes the burglary more challenging and Alice’s store less of a target.
Alice provides the best security for her mall store if she puts her own strong lock on the store’s entrance. The store is Alice’s own security domain. The mall’s public area is another security domain. The mall managers keep the public area locked after hours and provide keys to store personnel. Alice can reach her store even after hours, and she can keep it locked against dishonest people working in other stores.
This provides defense in depth because Alice’s store sits behind multiple security mechanisms. We also use the term layered defense because the separate security domains provide separate layers of protection. The innermost domain has the most restricted access, surrounded by another domain with less restriction, but that still enforces some access restriction.
To achieve genuine depth or layering, the access points or doorways must use truly independent security mechanisms. For example, some malls provide all the locks and keys for the stores. The locks are coordinated so that a special “master key” can open any door in the mall. The master key eliminates the separate security domains, undoing defense in depth.
