Chapter 10. Understanding Cisco Virtual Office
This chapter covers the integration of certificates in the Cisco virtual office solution. This solution represents an integration of certificates across multiple technologies. This chapter covers the following topics:
• Cisco Virtual Office (CVO) Overview
• PKI Integration
• 802.1x Integration
This chapter assumes that you are is familiar with the CVO solution set. This chapter’s objective is to highlight certificates as they relate to CVO. If you want to learn about all the elements of CVO, go to this page about the solution and solution references: http://www.cisco.com/en/US/partner/solutions/collateral/ns340/ns517/ns430/ns855/deployment_guide_c22-493157.html.
Workplaces are becoming more diverse and distributed. This trend gives greater flexibility to a work force and enables corporations to become nimble. Remote teleworkers, who spends most of their time away from the office, can benefit from having a setup at home that is congruent in functionality to being in the office. To provide this level of flexibility in a scalable fashion, security must be in place. Certificates are a cornerstone component of security for the Cisco Virtual Office solution. Certificates are used to authenticate home routers and end users.
The Cisco Virtual Office (CVO) provides an end-user workstation and desktop IP phone access to corporate resources. End users can have a router at their home or remote site that can provide wired or wireless access to their workstation and phone, as shown in Figure 10-1.
Figure 10-1 Complete Picture for the CVO Solution

The components involved in CVO are a router at the end-user location, PKI server, router that frontends the initial management connection, data plane VPN headend, configuration engine, Cisco Security Manager (CSM) and Cisco access control server (ACS) providing AAA.
To provide the flexibility to allow users to connect from anywhere, identity takes on an important role. Certificates are tied to the user, the user’s router, and potentially the user’s workstation for 802.1x. Each of these technologies has been discussed independently in separate chapters of this book. This chapter describes the application of each of these technologies. Appropriate technical references are made to the relevant chapters as necessary.
Some of the advantages CVO provides from a provisioning standpoint include the following:
• Devices deployed only need to be seeded with a small identical set of initial configuration commands or bootstrap configuration.
• No specialized pre-installation staging or configuration is required.
• An end device automatically “calls homes” to the Configuration Engine (CE) and downloads its working configuration.
For a CVO to be created at a SOHO location, a series of steps occur. Before any of the technical steps occur, a user must request the service and then that request must be approved. Depending on a corporations’ individual practices, this might be handled entirely online and result in a router being shipped to the user.
The next set of steps begins with a router sitting off a home Internet connection. The router has a default configuration. The user has only an Ethernet connection to a port on the back end of the 871.
When a user has a router in hand, the user needs to plug the router into the service provider’s device to obtain DHCP configured information. Additionally the user needs to plug in the workstation into a LAN port on the router.
The following steps result in the router obtaining full connectivity and access to the remote network:
1. The user connects to the 800 series router using the web-based interface.
2. The user initiates Secure Device Provisioning (SDP) through the GUI.
3. The router calls home and will be challenged.
4. The user provides credentials for a response to the challenge.
5. If the challenge succeeds, the router gets a bootstrap configuration downloaded (via a template created using CSM). The bootstrap configuration will have basic data to initiate a management tunnel to a management VPN headend. This includes a certificate to connect to a management VPN gateway.
6. The router attempts to reach the configuration engine as instructed by its bootstrap config. This interesting traffic initiates a management tunnel back to the headend and authenticates with the management router using its certificate obtained in the previous step.
7. The router gets its new, full configuration from the configuration engine.
8. The configuration has new PKI trustpoint information, and the router requests a certificate from the internal sub-CA. This certificate is for authenticating the router for the data-plain VPN.
9. Now the router brings up the data-plain VPN. This data-plain VPN uses DMVPN for a standard CVO deployment.
CVO PKI Highlights
CVO has several components that use certificates simply for router setup. Optionally, certificates can be used for end device authentication and phone authentication. The areas that use PKI for router setup are for setting up the management tunnel and the DMVPN tunnel. Chapter 6, “Integration in Large-Scale, Site-to-Site VPN Solutions,” describes the details of how to set up a PKI for this type of VPN deployment. To summarize, this hierarchy should use a hierarchical PKI.
The routers have trustpoints as part of their CVO templates. Chapter 5, “Generic PKI Designs,” and Chapter 6 describe the trustpoint configuration elements. Example 10-1 shows a trustpoint configuration for a DMVPN headend.
Example 10-1 Configuring Enrollment for Hub s-dmvpn-headend
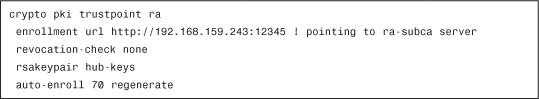
Also included in Chapters 5 and 6 are details in how to set up a hierarchical PKI. Example 10-2 illustrates some sample configurations.
Example 10-2 Sample Root CA and Sub-CA Configuration
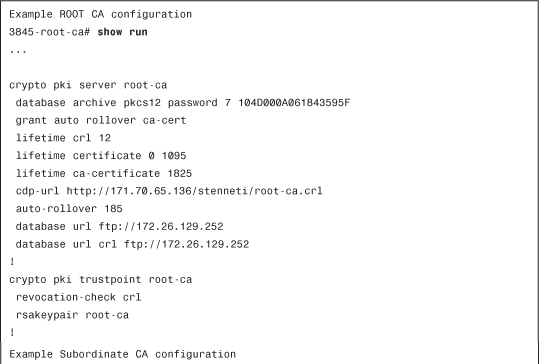
The trustpoint configuration for the management tunnel trustpoint and the DMVPN trustpoint (for data) is created by the CSM template in Step 5, and the data plain configuration is distributed by the configuration engine.
What is not shown as a step is the use of network authorization based on certificates. Chapter 3, “PKI Processes and Procedures,” describes network authorization based on certificates. An approach to enforce access uses AAA integration. A certificate can provide authentication; when combined with an AAA server, the AAA server provides authorization for the end host.
Fields in the certificate (such as subject and serial number) can be passed back to a RADIUS server or TACACS server. The server checks the credentials provided to it by the authorizing router to determine if the device is authorized for network access.
The advantage to using AAA as a solution is that it enables for authorization in addition to authentication. The moment an administrator decides a certificate is no longer authorized, the administrator can make the change in the AAA server, and it is immediately effective.
Example 10-3 shows the configuration required to point back to the ACS server on the headend router.
Example 10-3 Sample Configuration for Integrating Certificates with ACS for Network Authorization

Note
Chapter 3 of this book contains screen captures of how ACS should be configured.
The other element that can be optionally configured for end-host authentication is 802.1x for a workstation and phone. These solutions can optionally use certificates, which are the topics of Chapter 8, “Using 802.1x Certificates in Identity-Based Networking,” and Chapter 9, “PKI in Unified Communications.” Example 10-4 illustrates a sample router configuration for CVO that uses 802.1x authentication.
Example 10-4 Sample Configuration for Host Routers Using 802.1x for Workstation Authentication

Summary
Cisco Virtual Office provides a workplace a high degree of flexibility and savings. Enabling a corporation to distribute a workforce allows for resiliency in operations (if a disaster recovery occurs) and full functionality for remote workers and remote offices. It also provides for savings from a facilities standpoint.
To gain these advantages, the solution needs to provide availability from anywhere. This is where the need for strong identity comes into play. Strong identity measures bring near facility-level security, down to the port level. A central part of identity is the use of certificates and PKI in this solution.
Several parts of the CVO solution suite use certificates and PKI. The following solutions rely on certificates:
• Remote access for management tunnel, IPsec identity specifically
• Data plane tunnel identity
• Network authorization integrated with ACS and certificates
• 802.1x using EAP-TLS for workstations and IP phones
These components are cornerstones to identity the CVO solution and are driven by certificates.

