15
An Efficient Elderly Disease Prediction and Privacy Preservation Using Internet of Things
Resmi G. Nair* and N. Kumar
Department of Computer Science and Engineering, Vels Institute of Science, Technology & Advanced Studies (VISTAS), Pallavaram, Chennai, India
Abstract
IoT (Internet of Things) is the physical object network that connects many inbuilt devices to the Internet for data collection and exchange. The ability to link such systems to vast pools of data, such as the cloud, is an essential improvement. IoT is widely applicable in many aspects of our life by integrating integrated appliances and cloud servers. Embedding devices with a cloud server will give aged people a more versatile facility without going to hospitals with the ageing population. While the sensor-cloud paradigm has benefits, there are still many security challenges. Therefore, it is important to understand the architecture and integration of security problems such as authentication and data protection to protect elderly people’s privacy. An intelligent and safe health control system is proposed in this article with an IoT sensor focused on cloud storage and encryption. Here, initially, using the IoT devices, a smart wearable device can be designed using ESP 32. Then, the obtained data can be normalized, and pointed features can be extracted by using the semantic component analysis method. Then, by implementing the iterative multistate uplift, ANN can classify and identify the diseased data precisely. Then, the data is stored on a cloud server or maintained and monitored. The PHR must be protected from the attack in the cloud. To comply with this privacy preservation system, techniques of cryptography are used. The polynomial HMAC encryption algorithm is initially used for the PHR service. The cloud server produces the key for authentication purposes as the data owner queries the file and checks it out with the user. The user will access the decrypted file when the key is given using a polynomial HMAC algorithm. Then, the emergency message and the generated key can be sent to the patient and doctor for earlier treatment. Finally, the performance analysis is performed, and the proposed and the existing techniques are analyzed to demonstrate the scheme’s efficiency. The proposed scheme achieves authentication and provides essential security requirements.
Keywords: IoT, sensor-cloud, cryptography, ESP 32, ANN, cloud server, HMAC encryption
15.1 Introduction
Over the last years, the Internet of Things (IoT), medical sensors, and Internet software have exponentially expanded to provide remote patient care. It is worth remembering that, every year, there are an increased number of elders with chronic illness. An ageing community refers to a demographic paradigm that meets or exceeds a certain percentage of the ageing population. According to the UN Norm, a city is regarded as a culture of the age, in which 10% of the population is individuals over 60 years of age and 7% of the population over 65. People aged 65 years are included under the new norm. From 12% to 22% between 2015 and 2050, the world population is expected to nearly double over 60. Ageing means low fertility, ageing, and social care scheme lagging behind. Meanwhile, elderly well-being has been a global concern illuminated. When more and more elders need long-term care, they choose independence and involve themselves to remain in their own homes as long as possible. They cannot be handled properly because of the scarcity of medical facilities. A central process in hospitals is the continuous surveillance of essential vital symptoms of patients. This is normally done today using a range of cable sensors connecting to patients and bedside monitors. The limit is for elderly people to be hooked to bedding devices. Consequently, it was practicable and necessary to identify medical conditions personally through a repository without hospitals. This situation opens up the modern body sensor networks with the growing availability of IoT and health sensors for personal use. This conditions new technologies which can play an important role in many applications, Wireless Sensor Network (WSN). The exponential Development of physiological sensors allowed a new generation of WSNs now being used for traffic monitoring, crops, utilities, and welfare. The body area network area is an interdisciplinary area that provides cost-effective and consistent health monitoring by medical information online in real-time. However, sensor networks have posed several challenges: mobility, scalability, and heterogeneous information services. The WSN cloud integration provides increased connectivity, endless resources, immense computing power, and customer reaction. The modern data infrastructure paradigm of cloud computing is offered to researchers. The provision (and inclusion within the current infrastructure) of computing services and storage resources and software is pay-per-use. Cloud storage has become much more versatile for personal use in order to offer more appropriate and convenient network services. Since the cloud is a wide range of resources, companies can select when, where, and how to use cloud storage. Cloud platforms are widely known as “software as a service” (SaaS), “platform as a service” (PaaS), and “infrastructure as a service” (IaaS). Various surveys have shown that the future trend is simply cloud-based services. The online programming applications, apps, and data are supported through a browser with cloud computing services. To ensure confidentiality and protection of user data, cloud services need to adhere to security and privacy policies.
Despite the consensus and certification of parties to browse patient records, due to theft, data transmission times, and long-lasting data retention issues, the public is also concerned about the electronic medical record systems. However, several systems are suggested that do not guarantee the anonymity and non-repudiation of a patient. This chapter suggests a smart and stable surveillance regime using cloud-based IoT sensors to safeguard elders’ privacy. The biggest issue here is that the elderly increase daily and do not have to be linked to their beds with surveillance devices, leading to disadvantages and the waste of medical services. The elderly, on the other hand, are at great risk of acute pain or episodes like heart attacks. Without adequate medical aid, the consequences would be very severe. The EHR will provide our system with a diverse and appropriate medical service. The suggested system should focus on the advantages of cloud computing and the safety of information for elderly people because of the importance of the privacy of the elderly.
15.2 Literature Survey
Chavan Patil and Sonawane [1] proposed microcontroller (AAB) that is a passway for communication with different sensors, for example, the pulse sensor, ECG sensor, drip trace sensor (blood or saline), and sensors to track motion, which is the AVR-328 microcontroller (Arduino board). The microcontroller captures the sensor data and passes it into the network via Wi-Fi and thus tracks medical parameters in real-time. The physician will view the data at any time. The controller is also attached to a buzzer to alert the controller to sensor output variations. The Android-based application attached to the cloud service sends alerts to the doctor when the extremity is present. The doctor can then conveniently use NFC tags to quickly take provisional prescriptions without looking manually at patient records. With low power consumption, simple setup, high efficiency, and time-to-time response, this device are efficient. Sow et al. [18] proposed variations in data, including biodiversity and climate, that were used to predict the result of a particular disease in supervised learning. Bui and Zorzi [6] proposed applications for healthcare focused on an Internet-based solution to things. Islam et al. [9] proposed the IoT for health care. Birje et al. [5] proposed the IoT. Kumar [11] proposed the novel IoT Architecture and Healthcare System Design. Ženko et al. [22] proposed variability of pulse rate and detection of the quality of blood oxidation by the wearable mini-skill system. Shu et al. [17] proposed a heart rate tracking pressure sensor device with polymer-based pressure sensors and a post-processing interference circuit. An et al. [3] proposed a versatile, uncontrolled R.F. pulse detection sensor based on array resonators. Larson et al. [12] proposed a lung monitoring system that can be easily updated on any of the android devices. Milici et al. [14] proposed the air sensor based on a wearable modulated frequency selective surface. Baker et al. [4], on the web, proposed for smart healthcare things, barriers, and opportunities. Gubbi and Amrutur [8] proposed for low pulse oximetry adjustment pulse width monitoring and sampling. Von Rosenberg et al. [19] proposed smart helmet that can be activated by using the ECG and EEG multichannel. The proposed wearable can be very effective. Schäck et al. [16] proposed on the computer effective atrial fibrillation detection algorithm for photoplethysmography using smartphones. Yuce [21] proposed the implementation of wireless health services area networks. Lei Clifton [13] proposed mobile monitoring of patients by combining wearable and clinical observations. Parae et al. [15] proposed Smart Healthcare Monitoring System focused on the cloud. Wang et al. [20] proposed a hybrid mobile-cloud approach to smart, customized health care with ECG telemonitoring. Dunsmuir et al. [7] proposed the production of pre-eclampsia triage m-health applications.
15.3 Problem Statement
Owing to the diverse, healthy habitats, the well-being of elderly people in the digital world has been bad every day. They do not have the time to track their own condition. A person’s relative state of well-being and disease reflects the nature of the biochemical or neurological disorder, signs, and physical disability. Health beliefs are individual assessments of the person’s health status. A safe automated health management system is therefore essential to provide the individual with an appropriate human health rating and take the necessary measures to improve his or her health and to preserve his or her health data.
15.4 Proposed Methodology
The IoT in the area of health will attempt to initialize the accurate tracking of elderly health and will be able to provide people with wake-up information about their ailments at an acceptable time. In this chapter, we suggested a method in which patients have read the findings of a monitoring system of the body temperature, heart rate, body movements, blood pressure, etc. This is an automatically coded system in which elders can monitor the condition of the person without any further work on the health status tracking process. The extraction and classification of this information will then be performed. Confidential data can be saved in a cloud server, and a warning letter can be sent to the family doctor and patients, along with a clone key to access their confidential private health records, depending on the classified results. The proposed flow diagram will clearly show how the new monitoring system is developed. The data collection is performed using the sensor components of the IoT.
The schematic description of the proposed flow is shown in Figure 15.1. In this context, all IoT components will form a well-connected network, all connected with the health care system. Even the person may simply feed personal information to the computer to instantly connect the person to a hospital or healthcare unit.
15.4.1 Design a Smart Wearable Device
The device is implemented with hardware modules combined. During the implementation process, all hardware parts are assembled. In Figure 15.2, the circuit diagram of the device formed is shown. With physical pins, all sensors are connected to ESP32. The Wi-Fi module is built-in, so ESP32 is used as a computing unit. The Vcc and GND are attached to all sensors by the ESP32 Vcc and GND pin. The signal pin is wired to the D26 pin of the ESP32 in the case of the heartbeat sensor.
The LM35 data pin has a D35 microcontroller pin mapping (ESP32). This applies to a certain patient. The DHT11 database pin is connected to the D14 pin of ESP32 for room state tracking. DHT11 is only used for the calculation of room moisture. For testing poisonous gases in the room surroundings, the MQ-9 and MQ-135 optical outlet pins are attached to ESP32 D27 and D34, respectively. The data will then be reviewed after the collection of all health data from the elders and safely deposited on the server.

Figure 15.1 Schematic representation of the suggested methodology.
15.4.2 Normalization
The normalization of values calculated at a differing balance to a notionally common scale is often needed for the operation of data processing, often before the average. Certain normalization forms only require a rescaling method to retrieve the values correlated with certain other elements.

Figure 15.2 Hardware prototype.
We need to change the mistakes by making easy changes as we know data parameters. Following the adjustment of the errors, the health data values will usually not be spread randomly. The first step in the normalization process is to get the z-point. The Z-score will be represented in Equation (15.1):
where μ is the mean of the health data and σ is the standard deviation of the health data.
where L is the mean of the sample and S is the standard deviation of the sample.
Then, the Hat matrix (H) can be calculated by using Equation (15.2):
The variance for the Hat matrix is represented in Equation (15.4):
Then the residual can be calculated by using Equation (15.6)
where σ is an estimate if the σ which is the mean values
where L is a random variable and E is the expected value.
Use the mean μ particularly for the usually ordered distribution to standardize the distribution of the variable.
where Cv is the coefficient of the variance.
In order to obtain all values from 0 to 1, the feature scale procedure should be performed. This approach is known as standardization based on continuity. The normalized equation will be in the form of L′
Since standardizing the data in the data collection, the spectrum and data variability will then be equalized. The redundancy of data is mostly reduced or evenly removed. The normalized data could then be entered in the compilation steps as an input.
15.4.3 Feature Extraction
We can then delete the unwanted features by using the SCA process. This is a means of excluding second-degree mathematical dimensions. This approach was used in many applications. This is a mathematical activity that normally eliminates errors efficiently. The accuracy of the data can also be seen. It is important to distinguish the data during the study period. SCA defines the frequency of the effects in a given exact differential field. The details were challenged, and other information is pointed to as Ø route l and m adjacent. Generally, m only gets one benefit, and Ø is good in the way. The directional value then obtained will delete the data attributes. The method of removing functions is as follows:
where G is the frequency vector, m, n, and o are that the frequencies of that particular constituent normally has the l and m values, k is the data characteristic (l,m), and l is variable, Ø is the uniform constant. The multiple attributes can be obtained using the SCA approach. You can also display the features with this method. This is one of the most popular methods of extraction. The maximum variance is seen when removing the axis from the results. This SCA measurement method evaluates whether or not data consistency is helpful. Certain correlation parameters use the criterion value dependent on the absolute and partial combining of goal and unnecessary results. SCA is mainly feedback to the evaluation of the features of controlled and unregulated classification applications. The whole procedure depends on the device’s load, input changes, and IDS output. Using the removal process, the modified objects are produced during the selection phase. The unwanted details are separated. We would then point out any of the most significant characteristics below. The details are set as follows, duration and characteristics:
15.4.4 Classification
Back propagation absorbs results that include symptoms of the disease by matching the symptoms of the disease to the disease forecast using the known real goal value by the replicated processing. For the sake of estimation, the target value might be the known value. A weight set is modified for each data in order to reduce the average squared error between the network prediction and the real value. This modification is made from the output layer to the first hidden layer and the expression “backward”. These revisions take the “reverse” direction. The steps concerned some of the parameters include inputs, outputs, and errors. The first step is to measure the value of the data set to reduce problems with the binary classification, where F(l) is a functional matrix that can be represented by Equation (15.14)
where W is the classifier of the dual variables.
After that need to discuss the relationship among the data
The error can be the classification by using the below equation
Finally, a ranking is generated for the abnormality matching distance of database data
where the E.D. signifies the Euclidean distance, q denotes the query data, and s is the signal score value.
The classification was concluded as
15.4.5 Polynomial HMAC Algorithm
The proposed security framework ensures stable and effective data sharing in the cloud. For public-key encryption, the polynomial HMAC algorithm provides an alternative to the RSA. Many modern ABE strategies can handle private and public keys with only one authority. Device operators exchange data with actual users controlled by a different entity in some cases. In order to deal with this issue, many multi-authorities have been set up. The data holder includes ciphertext update access control structures and related status attributes. In the suggested scheme, a protection algorithm is used to weight cloud storage data. The 64-bit symmetrical polynomial HMAC algorithm has a variable-long address between 32 and 448 bit (14 bytes). The algorithm has been developed to correctly and continuously encrypt 64-bit plaintext in a 64-bit chip.
In choosing the operations of the algorithm, the table scan, node, addition, and bit by bit are used or to reduce the necessary 32-bit processor encryption and decryption time. The algorithm has been built purposefully, so that code functions remain simple, straightforward, and secure. Polynomial HMAC algorithm has a 16 round Feistel network for encryption and decoding, much like the DES (Data Encryption Standard). However, 32-bit knowledge on the left and right is changed for each round of polynomial HMAC algorithms relative to DES, changing only the proper 32-bit at the next round and eventually turning left. Included on the left before modification to the F function or 32-bit right for the next round, the Polynomial HMAC Algorithm was a bit exclusive 32-bit operation. Polynomial HMAC algorithm also consists of two proprietary trade and exchange operations after 16 checks. The method is based on the DES permutation shape.
In the proposed device configuration, the polynomial HMAC algorithm is given for the encryption, decryption, and generation of keys. The results are also authenticated via a code matching operation. Instead, the software generates user weight according to its capabilities. The polynomial HMAC algorithm is typically divided into two components, e.g., key extension and coding. In 16 rings, the data is encrypted. The main- and data-dependent displacement or substitution are often carried out at all times. In relation to 32 bits, this add-on (four indexed search tables). All of this is seen in the polynomial HMAC algorithm. The CA must have a user I.D. as a single user linked to the customer.
Nevertheless, the individual ciphers the features and sends them their signature to the authority. The legitimacy trait authenticates the user’s personality. The hidden keys and weight will be set if the current person is the right one. CA and officials forward a hidden key to the network and issue the new recipient a secret key separately. With configuration and program algorithms from the central government and with public keys to the intruder, the challenger will be supplied with the correct keys. A single I.D. is logged in, and an asymmetrical dataset key is automatically selected before a data file is sent to the server. First, the device user downloads and uses a decryption algorithm to decode cloud storage. The method calculates these weights by value if the secret key given by the data owner has been accepted. The receiver will decode the weighted text data file.
Finally, after the process of secret cryptography key can be generated. The secret key, along with a message, can send to the elders and the doctors. By using the secret key, the family doctors and the patient can access their personal health records safely and securely.
15.5 Result and Discussion
By comparing, it with the other current approaches, the efficiency of the proposed classification system was evaluated.
15.5.1 Accuracy
It shows the ordered errors, an indicator of the predisposition of arithmetic; the poor precision creates a difference between a result and the “real” value. This news is named ISO. This ensures that rare samples or data are checked using the same algorithm frequently and how accurate the data are collected from the device. Precise outcomes are the proportion of really positive and negative results in the overall data.
15.5.2 Positive Predictive Value
Precision is a random error portrayal that reflects an algebraic variability metric
15.5.3 Sensitivity
Also called sensitivity is the true optimistic rate, the reminder or identification in Any fields calculate the proportion of real positives found correctly.
15.5.4 Specificity
In addition, the specificity of the actual pessimistic rate tests the number of actual negatives defined correctly.
15.5.5 False Out
The false-positive rate of incorrect rate of incidence is measured as a combination of the number of incorrectly classified negative events and the overall number of negative events.
15.5.6 False Discovery Rate
In zero hypothesis testing when making multiple comparisons, the false discovery rate (FDR) is a way to design a type-I error rate. FDR monitoring protocols are designed to control the anticipated percentage (no hypotheses rejected) of incorrect discoveries (incorrect rejections).
15.5.7 Miss Rate
The false-negative rate is the proportion of positive results produced by the test.
15.5.8 F-Score
F-score is the harmonic mean for consistency and recalls the average balance.

Figure 15.3 Health data vs. specificity.

Figure 15.4 Health data vs. sensitivity.
The relation of precision for the suggested iterative multistate uplift ANN with other known approaches is seen in Figure 15.3. The suggested approach clearly achieves classification precision of 97% and forecasts the disorder with accuracy by its symptoms.
Figure 15.4 provides a contrast of sensitivity to other existing approaches for the suggested iterative multistate uplift ANN-raising classifier. The suggested approach clearly achieves a sensitivity for classification of 95% and predicts the disorder correctly from its symptoms.
In Figure 15.5, the proposed false out probability is estimated for other current approaches by iterative multistate uplifting ANN. It is clear that in comparison with the current scheme, the proposed approach achieves a false classification rate of less than 0.011%.
Figure 15.6 shows the positive predictive value with the other current approaches of the iterative multistate uplifting ANN. It is apparent that in contrast with the current procedure, the proposed approach produces a positive predictive value score of less than 0.16%.
Figure 15.7 represents the determination of the FDR of the proposed iterative multistate uplift ANN classifier with the other existing methods. It is clear that the proposed method achieves a FDR of less than 0.057% when compared to the existing system. It is very low.
Figure 15.8 represents the determination of the miss rate of the proposed iterative multistate uplift ANN classifier with the other existing methods.

Figure 15.5 Health data vs. false out.
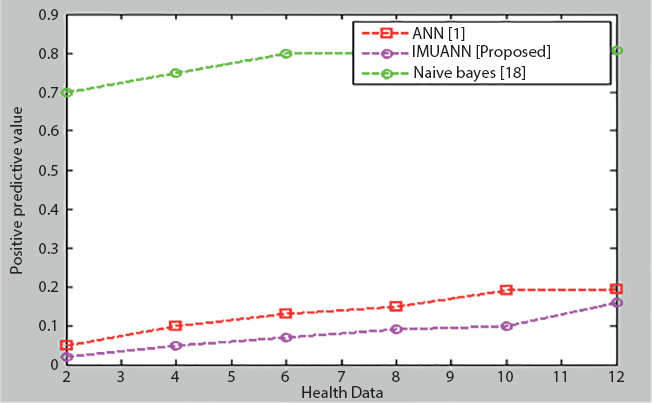
Figure 15.6 Health data vs. positive predictive value.

Figure 15.7 Health data vs. false discovery rate.
It is clear that the proposed method achieves a miss rate of less than 0.15% when compared to the existing system. It is very low.
The F-score for the suggested iterative multistate uplift ANN classifier with the other current methods is shown in Figure 15.9. Of course, as opposed to the current scheme, the proposed approach earns a 97% F-score.

Figure 15.8 Health data vs. miss rate.
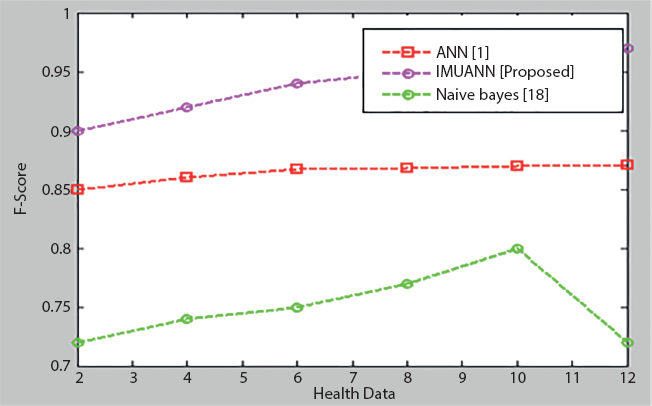
Figure 15.9 Health data vs. F-score.
The consistency of the proposed iterative multistate uplift ANN classifier with the other current methods is seen in Figure 5.10. It is obvious that, relative to the current scheme, the proposed approach achieved an F-score of 97%. The suggested method, therefore, yields successful results in comparison to all other established approaches. Therefore, the suggested solution provides efficient efficiency contrary to all other established approaches. The suggested cloud protection, polynomial HMAC efficiency metrics, is measured by its useful time in order to demonstrate the usefulness of the polynomial HMAC algorithm, as described in Tables 5.1 and 5.2. The suggested cloud security metrics were contrasted with the current security algorithm.

Figure 15.10 Health data vs. accuracy.
Table 15.1 Comparison of encryption time.

Table 15.2 Comparison of decryption time.
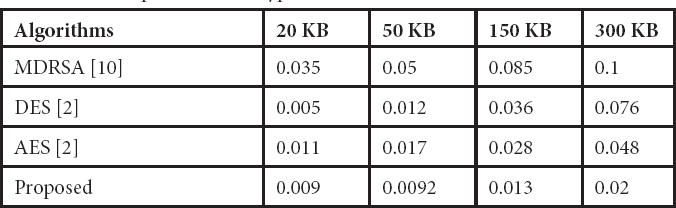
The re-encrypted ciphertext is decrypted by the medical professionals’ private key. The period required to encrypt re-encrypted data over the re-encrypted file size is described in Table 15.2. Figure 15.11 shows the time required for encryption simulation data.

Figure 15.11 Time taken for encryption.

Figure 15.12 Time taken for decryption.
In the encryption and decryption time between 20 and 300 KB, as seen in Figure 15.12, the polynomial HMAC algorithm is faster than AES, MDRSA, and DES. We checked and compared the four algorithms with different file sizes, which results in the encryption and decryption of small files faster than the other existing methodologies. The suggested speed approach is sharply increased on larger files. The results showed finally that the polynomial HMAC algorithm is more effective, quicker, and elegant.
15.6 Conclusion
In predicting the disease of wearable people, the new smart wearable device proposed would be very useful. Hence, the iterative multistate uplift ANN approach has been developed, which depicts diseases by studied their effects. The goal is to improve the user-friendly framework. Here, iterative multistate uplift ANN elevation is a new and efficient approach used to forecast diseases accurately. The aim of this new technology application is to alert patients beforehand during illnesses. Instead, the polynomial HMAC algorithm does not only provide a semi-trustful cloud service provider with data security and central authorities, but it also builds a lightweight key management system for large-scale applications. Overall, the proposed approach is superior to other current approaches.
References
1. Chavan Patil, A.B. and Prof. Sonawane, S. S., To Predict Heart Disease Risk and Medications Using Data Mining Techniques With an IoT Based Monitoring System For Post Operative Heart Disease Patients. Sixth Post Graduate Conference for Computer Engineering (cPGCON 2017) Procedia International Journal on Emerging Trends in Technology (IJETT).
2. Al-gohany, N.A. and Almotairi, S., Comparative Study of Database Security In Cloud Computing Using AES and DES Encryption Algorithms. J. Inf. Secur. Cybercrimes Res., 2, 1, 102–109, 2019.
3. An, Y.J., Kim, B.H., Yun, G.H., Kim, S.W., Hong, S.B., York, J.G., Flexible non-constrained R.F. wrist pulse detection sensor based on array resonators. IEEE Trans. Biomed. Circuits Syst., 10, 2, 300–308, 2016, Informatics, 18, 3, 722–730, May.
4. Baker, S.B., Xiang, W., Atkinson, I., Internet of things for smart healthcare: technologies, challenges, and opportunities. IEEE Access, 5, 26521–26544, 2017.
5. Birje, M.N., Kumbi, A.A., Sutagundar, A.V., Internet of things: a survey of architecture, requirements, and applications. Int. J. Hyperconnectivity Internet Things (IJHIoT), 1, 2, 45–71, 2017.
6. Bui, N. and Zorzi, M., Health care applications: a solution based on the Internet of things, in: Proceedings of the 4th International Symposium on Applied Sciences in Bio-medical and Communication Technologies, ACM, 2011.
7. Dunsmuir, D., Payne, B., Cloete, G., Petersen, C., Development of m-Health Applications for Pre-eclampsia Triage. IEEE J. Biomed. Health Inf., P.P, 99, 2168–219, 2014. January.
8. Gubbi, S.V. and Amrutur, B., Adaptive pulse width control and sampling for low power pulse oximetry. IEEE Trans. Biomed. Circuits Syst., 9, 2, 272–283, 2015.
9. Islam, S.M.R. et al., The Internet of things for health care: a comprehensive survey. IEEE Access, 3, 678–708, 2015.
10. Kiran Kumar, Y. and Mahammad Shafi, R., An efficient and secure data storage in cloud computing using modified RSA public-key cryptosystem. Int. J. Electrical & Comput. Eng., 10, 1, 2088–8708, 2020.
11. Kumar, N., IoT architecture and system design for healthcare systems, in: 2017 International Conference on Smart Technologies for Smart Nation (SmartTechCon), IEEE, pp. 1118–1123, 2017.
12. Larson, E.C., Goel, M., Redfield, M., Boriello, G., Rosenfeld, M., Patel, S.N., Tracking lung function on any phone, in: Proceedings of the 3rd ACM Symposium on Computing for Development, ACM, p. 29, 2013.
13. Clifton, L., Clifton, D.A., Pimentel, M.A.F., Watkinson, P.J., Tarassenko, L., Predictive Monitoring of Mobile Patients by Combining Clinical Observations with Data From Wearable Sensors. IEEE J. Biomed. Health, 2014.
14. Milici, S., Lorenzo, J., Lázaro, A., Villarino, R., Girbau, D., Wireless breathing sensor based on wearable modulated frequency selective surface. IEEE Sens. J., 17, 5, 1285–1292, 2017.
15. Parade, K.A., Patil, N.C., Poojara, S.R., Kamble, T.S., Cloud-based Intelligent Healthcare Monitoring System, in: In the proceedings of International Conference on Issues and Challenges in Intelligent Computing Techniques (ICICT), Ghaziabad, Indian, February 7-8, pp. 697–701, 2014.
16. Schäck, T., Harb, Y.S., Muma, M., Zoubir, A.M., A computationally efficient algorithm for photoplethysmography-based atrial fibrillation detection using smartphones. 39th Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), 2017, pp. 104–108.
17. Shu, Y., Li, C., Wang, Z., Ma, W., Li, Y., Ren, T.L., A pressure sensing system for heart rate monitoring with polymer-based pressure sensors and an anti-interference post-processing circuit. Sensors, 15, 2, 3224–3235, 2015.
18. Sow, B., Mukhtar, H., Ahmad, H.F., Suguri, H., Assessing the relative importance of social determinants of health in malaria and anemia classification based on machine learning techniques. Inf. Health Soc. Care, 1–13, 2019.
19. Von Rosenberg, W., Chanwimalueang, T., Goverdovsky, V., Looney, D., Sharp, D., Mandic, D.P., Smart helmet: wearable multichannel ECG and EEG. IEEE J. Transl. Eng. Health Med., 4, 4, 1–11 2016.
20. Wang, X., Gui, Q., Liu, B., Jin, Z. et al., Enabling Smart Personalized Healthcare: A Hybrid Mobile-Cloud Approach for ECG Telemonitoring. IEEE J. Biomed. Health Inf., 18, 3, 739–745, 2014, May.
21. Yuce, M.R., Implementation of wireless body area networks for healthcare systems. Sensor Actuators A: Phys., 162, 1, 116–129, 2010, July.
22. Ženko, J., Kos, M., Kramberger, I., Pulse rate variability and blood oxidation content identification using miniature wearable wrist device, in: 2016 International Conference on Systems, Signals and Image Processing (IWSSIP), IEEE, 2016.
- *Corresponding author: [email protected]









