7
An Overview of IoT and Its Application With Machine Learning in Data Center
Manikandan Ramanathan* and Kumar Narayanan
Department of CSE, Vels Institute of Science, Technology and Advanced Studies, Chennai, India
Abstract
Internet of Things (IoT) enables the gadgets, tools, machines, computers, instruments, or any devices that are associated to the internet and controlled through the internet from anywhere. Consequently, an unimaginable amount of data is generated, and this needs to be monitored and processed, and actions are needed to be taken. In this regard, through data centers, along with IoT, AI, and machine learning techniques, and through implementing edge computing, we can achieve the required high-speed computation. This chapter describes the IoT protocols, surveys IoT in the data center, and edge computing with machine learning techniques.
Keywords: IoT, AI, data center, machine learning, edge computing
7.1 Introduction
The Internet of Things (IoT) is the interconnection of devices, instruments, tools, vehicles, home utilities along with sensors, actuators, and software over the network. The data is collected from these devices and transferred over the internet network, and also, it receives the data from the external world through internet. IoT means making the device as internet-aware [8].
IoT applications [9] can be as follows:
- Mobile devices
- Smart meters and objects
- Washing machine
- Health care implementations
- Smartwatches
- Fitness devices
- Interconnected automobiles to achieve automatic car
- Home automation systems: lighting, home security, cameras, AC control, media control, etc.
- Sensors to measure: weather, traffic, ocean tides, road signals, gas appliances
IoT protocols with OSI standard is mapped in Figure 7.1.
Figure 7.2 and Table 7.1 can be referred for various IoT protocols [14].
Internet: IPv6 over Low Power Wireless Personal Area Network (6LoWPAN) is the first and most standard. Refer Figure 7.3 for various IoT packet headers [9].
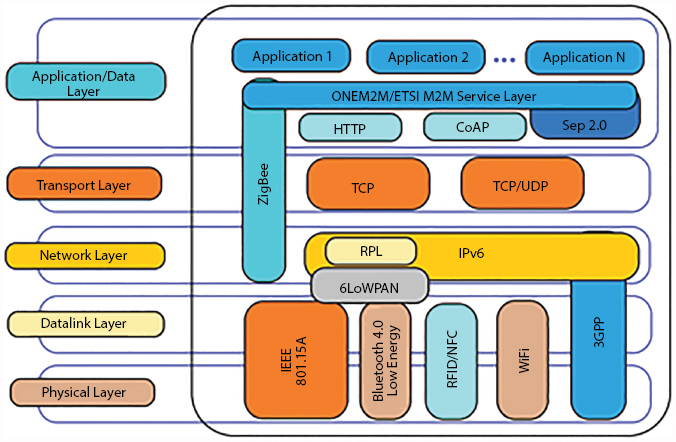
Figure 7.1 IoT protocol with OSI standard.
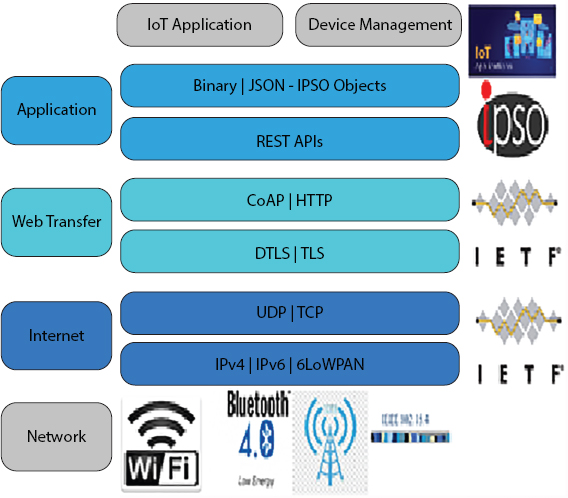
Figure 7.2 IoT layers and protocols.
Table 7.1 IoT protocols.
| Infrastructure | IPV4/IPV6, 6LowPAN |
| Identifier | RFID, EPC, IPv6, URIs, uCode |
| Communication | Bluetooth, Wi-Fi, LPWAN |
| Data Exchange | CoAP, MQTT, Rest API, HTTP |
| Service Discovery | DNS-SD, mDNS |
| Semantics | JSON |
| Management of Device | TR-069 |
7.1.1 6LoWPAN
- 6LoWPAN is IPv6 over Low Power Wireless Personal Area Networks defined in RFC 6550.
- 6LoWPAN layer lies between data link and network layer.

Figure 7.3 IoT packet headers.
- This provides a method to transfer the data with respect to IPV6 over IEEE 802.15.4 networks. It can have direct connection to internet or any kind of network [2].
- This protocol encapsulates long IPV6 headers in to IEEE 802.15.4, not beyond 128 bytes.
- IEEE 802.15.4 handles the MAC layer and drivers.
- 6LoWPAN sites on top of WPAN devices and acts as adaptation layer to be used by the normal IPv6 stack.
- 6LoWPAN transparently handles the fragmentation and reassembly between different MTUs.
- Frames in 6LoWPAN are of four types and they are as follows:
- No 6loWPAN header (00)
- ✓ Any frame which is not following 6LoWPAN specifications will be discarded.
- Dispatch header (01)
- ✓ This header is used for compression of multicast and IPV6 header.
- Mesh header (10)
- ✓ This header is used for broadcasting.
- Fragmentation header (11)
- ✓ Break the IPV6 long headers to fit in the fragment size of 128 bytes length.
7.1.2 Data Protocols
There are few data exchange protocols that are followed in IoT, in which major data protocols of IoT are CoAP [2], MQTT [2], Rest API, etc.
7.1.2.1 CoAP
CoAP is a simple IoT protocol; CoAP is Constrained Application Protocol.
This protocol is mainly developed for small smart devices designed for constrained devices and networks, which are made up of microcontrollers. This protocol is used to transfer data between end points, and it is designed same like HTTP.
CoAP has two kinds of message passing between server and client. Server and client are also called as end points. They are nothing but the smart devices connected to the network. Each message is embedded with message ID which is unique ID and it is used to detect the duplicate messages.
Two types of messages are as follows:
- Confirmable Message (CON): This is a message where the sender gets the acknowledgement of each message with respect to mapping the key or ID for each message. For each confirmable message, if the receiver is not able to process and if its CPU or controller is busy, then it can send RST (Rest) message to sender to stop sending for some specified time. Each CON message has token ID embedded in it; this token identifier is used to match with the acknowledgement of messages. Refer Figure 7.4 for message sequences of confirmable messages.
- Non-Confirmable Message (NON): Sender sends the message to receiver, and it will not wait for any acknowledgement. This is called as non-confirmable messages. Refer Figure 7.5 for non-confirmable message sequence.
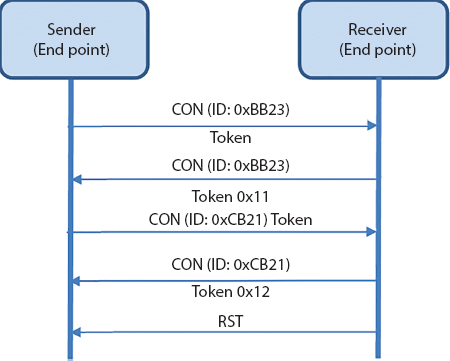
Figure 7.4 Confirmable message passing mechanism.

Figure 7.5 Non-confirmable message passing mechanism.
CoAP Features
- Synchronous message
- Asynchronous message exchange
- Simple parsing mechanism
- URI and content-type support
- Caching support
CoAP Security
Datagram TLS over UDP is used for securing mechanisms in CoAP. Datagram TLS supports RDA, AES, etc.
7.1.2.2 MQTT
MQTT is Message Queuing Telemetry Transport; it is an IoT data protocol. It uses publish/subscribe messaging mechanism. This also acts on client/server mechanism. The client is a sensor that “publishes” the information to server and it sends to all the subscribers of that server. The communication mechanism is based on TCP. Refer Figure 7.6 for MQTT subscriber-publisher model.
Comparison of CoAP and MQTT is discussed in Table 7.2.
7.1.2.3 Rest APIs
Rest API is representational state transfer application programming interface (API). Rest is used to publish the requests of controller to an application. Rest API is used as communication mechanism between controller and application. A secured TCP connection is established between controller and associated network elements (NEs).

Figure 7.6 MQTT subscriber-publisher model.
Table 7.2 Comparison of CoAP and MQTT.
| S. no. | CoAP | MQTT |
| 1 | It uses Request-Response method | This protocol uses Publisher-Subscriber |
| 2 | One-to-one protocol, sending message | Uses Central Broker to dispatch messages from publisher to clients |
| 3 | State Transfer Protocol | Event-Oriented Protocol |
Representational State Transfer (REST) is an architecture framework and methods with set of guidelines used to create web services. Rest API supported systems uses HTTP (Hypertext Transfer Protocol) to communicate with HTTP defined methods such as GET, PUT, POST, and DELETE. These operations are used to retrieve the webpages by web browsers, and it sends data to servers which are present in remote. These are mapped to read, create, update, and delete operations with respect to HTTP methods. These operations are referred as CRUD.
- The HTTP server running on port 80 receives all REST request.
- If the server finds a “/rest/” in the URL, then it redirects that request to the REST server running on local loopback interface. GET
The GET method is used to retrieve the data of a resource or group of resources of the system.
POST
A resource is created by sending the HTTP POST method to the URI of the collection in which the resource will reside. The body of the request is used to send either a representation of the object to be created or a list of parameters providing information necessary for the creation of the resource. PUT
The PUT method is used to perform complete replacements on pre-existing objects.
DELETE
The DELETE method is used to remove resources.
REST RESPONSE CODES
- HTTP_METHOD uses different response codes depends on command.
- 200OK is SUCCESS RESPONSE CODE.
- 404 Not Found—non-existent resource.
- 500 Internal Server Error.
- 201 Created—for POST SUCCESS.
- 400 Bad Request—incorrect parameters.
- 405 Method Not Allowed—unsupported HTTP_ METHOD.
- 204 No Content.
Standards-based protocols are used to provision the application-based network’s NEs.
7.1.3 IoT Components
IoT has three major elements; these are as follows:
- Hardware
- a. Physical devices—sensors and actuators
- Middleware
- a. Data acquisition
- Visualization
- a. Application and representation
IoT components [1] are depicted in Figure 7.7.
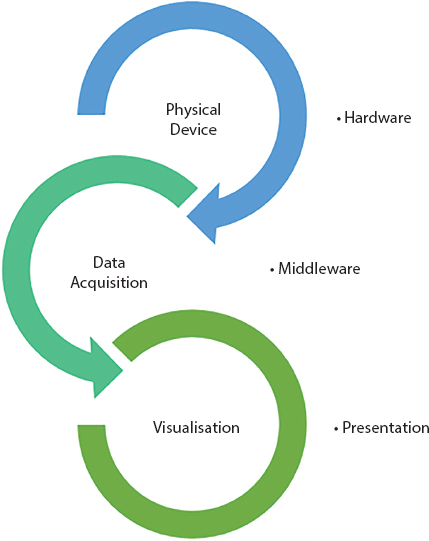
Figure 7.7 IoT components.
7.1.3.1 Hardware
This layer is a physical layer consisting of physical devices such as sensor and actuators. Any device which is going to get monitored and controlled over the internet will be part of hardware elements. The communication among them is depicted in Figure 7.8.
- Sensors
Sensor is a device which is used to monitor and detect the events and converts one form of energy to another form in our IoT to digital form from electrical transmission signals. Based on these readings, data needs to be interpreted and sent to control center. There are different group of sensors such as mechanical, thermal, gas, and voltage. We must select the sensors based on the IoT applications [13].
- Control Center
Control center gets the signals from sensors and converts them to digital signals and sends the messages to actuators.
- Actuators
Actuators convert the certain form of energy to motion. Any device which gets the message from control center and acts upon it is called as actuators. In gas monitoring system, cylinder is the actuator [13].
- Transducer Interface
Transducer interface [13] is through electronic data sheets which are embedded in sensors and actuators through TEDS sheet (Transducer Electronic Data Sheets); these are stored in embedded memory. XML-based mechanism can be used which is popular among various manufacturers. The parameters it may contain are device identifiers, data attributes, sensor measurement parameters, etc.
7.1.3.2 Middleware
Middleware is the data exploration and acquisition. It generates the messages; each message is stored and computed, and based on the results of the computation, the events have to be generated [12, 13].

Figure 7.8 IoT communication architecture.
7.1.3.3 Visualization
Visualization component is the representation or application which should GUI displays to understand the control and management of IoT devices over the internet through these user interfaces.
7.2 Data Center and Internet of Things
7.2.1 Modern Data Centers
Data center can be used to compute, process, and store data from various end users of the systems like insurance, banking, educational universities, colleges, government offices, and private offices. The data processed in the data centers are extremely large, and the high latency or service disruption is not acceptable for the customers.
Day by day, the usage of internet increases, network bandwidth increases, number of users increments, and work load increases; in addition to this introduction to IoT, all such factors would affect the data center when everything has to be computed at data center. With respect to IoT environment, any device will be connected to internet and it will be managed for anywhere which might affect the speed and latency and this will also become an overload to the data center when all transactions are stored in data center [6].
Data center is connected across the core network and backbone by connecting the end users to access devices, access devices connected to distribution side of the network [16]. The distribution network consists of distribution or aggregation switches and routers. The distribution switches are connected to core-switches. The core switched will have uplink which will be connected to cloud or WAN. High availability and backup is achieved at all the three levels. At each level, there is a backup device at core, distribution, and access devices to ensure the availability and avoid disruption to the end users. This is depicted in Figure 7.9.
There is a backup path at all levels; disaster recovery mechanism is important for any data centers to take care of the highly valued data of customer data and communication between them.
7.2.2 Data Storage
Over the years, the internet working of devices makes the data volume very high and the data passed between devices needs a very less latency in the response. The increase of small devices and electronic devices in industries, home, hospitals, road traffic and signal, automobiles, etc., increases the data with high volume.
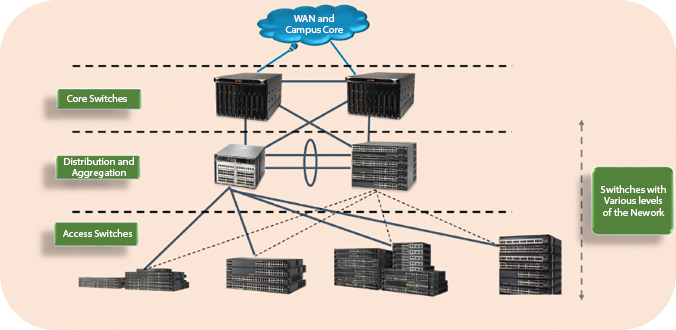
Figure 7.9 Data center architecture.
IoT is the emerging technology, and because of the huge smart devices, the amount of data becomes very high. So, it becomes a critical issues and challenging on maintenance of data storage, data analysis, and computation. Data centers will face highly challenged environment in terms of energy efficiency, reliability, and availability of data.
Artificial intelligence and machine learning techniques such as supervised learning, unsupervised learning, neural network, and genetic algorithms need to be applied to make automatic decision-making. There should also be a distributed environment to access the top of rack in data center to access the data storage devices. Distributed and modular architecture in both software and hardware design is required to reduce the latency.
7.2.3 Computing Process
Another important factor of IoT is method of processing the IoT data; various frameworks of computing [3] are as follows:
- Fog Computing
- Cloud Computing
- Edge Computing
- Distributed computing
7.2.3.1 Fog Computing
In this computational framework, computation is held at edge servers; this filters the data to data center. All data will not be sent to data center. The load of data center is reduced by offloading the computation, network services, and storage to servers at the edge. Fog computing architecture will do limited operations, computations, services, and storages at edge servers [4, 5]. This is majorly implemented in military and health applications.
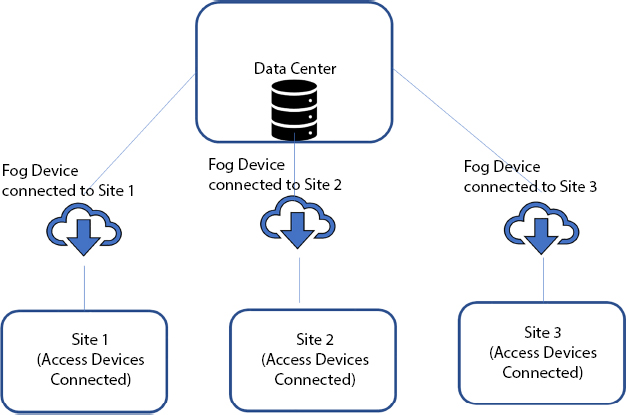
Figure 7.10 Fog computing.
In Table 7.3, pros and cons of fog computing is discussed.
Table 7.3 Pros and cons of fog computing.
| Pros | Cons |
| Amount of data sent to cloud is reduced | Physical location takes away from anytime, anywhere any data benefit of the cloud |
| Bandwidth of the network is conserved | Lot of security issues seen, by spoofing the IP address |
| Latency is less, response time is quick | Issues in privacy |
| Data is very closer to edge, the data in edge is secured rather than issues seen while sending to data center | Availability of the device is a challenge |
| Simplifies the network and CPU load is reduced | Security concerns in wireless network |
Each site in the access side is connected to the fog device or fog computer. Each fog device is connected to data center. When there is a local processing and storage that happens, it happens in fog device and it will only contact cloud data center only based on the special services and data storage. This method of computing increases the speed while it processes and computes at fog devices itself. Fog computing deployment can be referred in Figure 7.10.
7.2.3.2 Edge Computing
Data is processed at the edge of the internet connecting device, processing the data where the sensors of the device are connected. This device is called as edge device. This is far away from the internet backbone; some of the data needs processing at the edge itself where the redundant data copy is required at edge and other layers. Edge computing deployment can be referred in Figure 7.11. But still, the enhancement of security implements the speed in data computation. Action will be taken in nanoseconds. Edge computing is achieved with smaller networks where the edge servers connected to IoT data; this becomes a distributed architecture. Single point of failure can be avoided in this method. Edge computing solves the bandwidth issue which is visible in cloud computing. Bulk data pushing to cloud data center is not required in edge computing. This computing is suitable for less latency and real-time applications. All the IoT devices are connected to IoT gateways which will perform computation and storage.
7.2.3.3 Cloud Computing
In cloud computing, the data is sent to data center for further processing; big data is sent and processed at data center. Cloud computing involves high latency and speed cannot be achieved as like other computing frameworks. Considering the huge data generated by IoT, the load of the CPU will also be high. The following are the different types of computing: cloud computing is a centralized way of processing the data, lot of chances for single point of failure. Sending the huge data of IoT to cloud will increase the bandwidth and the cost.
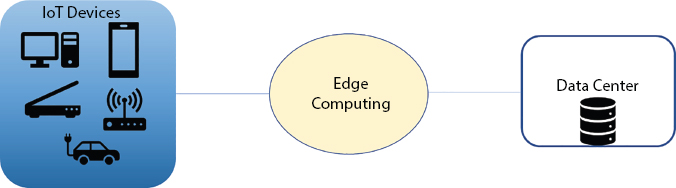
Figure 7.11 Edge computing.
Cloud architects mapped the degree to common service types [10]:
- Software as a Service (SaaS)
- Application itself is shared as a service.
- Examples: GoTo meetings, Cisco Webex Meetings, Zoom Meetings, Google Meet, and Google Apps.
- Platform as a Service (PaaS)
- It provides a framework or environment for development which is shared as a service, which can be used to build customized development or application.
- Examples: Google Application Engine, Windows Azure, Amazon AWS Elastic, Notebook Jupyter, and Google Code collaborator.
- Infrastructure as a Service (IaaS)
- Services offered for computation, storing along with network deployments.
- Examples: Google Compute Engine, Microsoft Azure, and Amazon AWS.
A huge amount of data moves to cloud computing, and it adds more pressure on the data center. Data center needs to be a central management platform and should have ability to perform quickly and easily.
7.2.3.4 Distributed Computing
Distributed computing architecture is mainly developed for handling huge amount of data. The major challenges are faced when IoT application generates huge data by sensors and actuators. In this architecture, data is partitioned to packets and each partitioned packet is assigned to different central processing units for computation. Hadoop and Spark are examples of such frameworks. Advantages of this architecture are as follows:
- Low latency
- High processing speed
- Able to handle voluminous data
- Saves energy
- Reduced CPU load
7.2.3.5 Comparison of Cloud Computing and Fog Computing
Table 7.4 compares the cloud and fog computing with respect to IoT attributes of application and its processing.
7.3 Machine Learning Models and IoT
Big data generated by IoT connected devices to be interpreted and takes decisions within microseconds. Machine learning models can be utilized to learn the model based on the data and predict the action. Also, big data analysis can be quickly interpreted based on the machine learning models. Various machine learning models can be used with IoT, and major machine learning models such as Supervised Machine Learning, Naïve Bayes Method, and K-Nearest Neighbor can be used. Also, neural networks and deep learning techniques can also be used. Figure 7.12 can be referred for various machine learning phases.
Table 7.4 Comparison of cloud and fog computing.
| Requirement | Cloud computing | Fog computing |
| Latency | Low | Huge |
| Server node is placed at | Within the core internet and backhaul | Edge device of the network |
| Security | Spoofing attack is possible | Can determine a method |
| Geographical distribution | Centralized | Distributed |
| Real-time interactions | Supported | Supported |
| Delay in response | High | Low |
| Interconnection between client and server | Multiple nodes interconnected across the device and data center | Immediate next hop |
Figure 7.12 Stages of machine learning.
Identifying the best machine learning models to be applied for IoT application is based on the following factors.
- The type of application in which IoT is implemented.
- IoT parameters and attributes that get generated from the IoT device.
- Machine learning algorithm based on data driven mechanism.
Main IoT data characteristics are amount of data, accuracy, redundancy, dynamicity, velocity, completeness, noisy reduction, etc. These data characteristics play an important role in choosing the machine learning model. Machine learning algorithms and IoT together can achieve high speed response, better communication, accuracy in data, better decision-making [11], etc. To solve the real-world complex issue, along with IoT, machine learning also plays an important role. Both IoT and machine learning together analyze the data to its depth and help for critical decision-making from the huge sensory data generated by IoT.
7.3.1 Classifications of Machine Learning Supported in IoT
Different types of machine learning algorithms [3] that are supported with IoT framework are depicted in Figure 7.13.
7.3.1.1 Supervised Learning
In supervised learning, the learning model is trained with “labeled data”. Outcomes can be predicted for unforeseen data as input. The label can be a True or False, Yes or No, Positive or Negative, etc., i.e., either binary value of “1” or “0”. The following machine learning algorithms are part of supervised learning.
- Decision Tree
- Naïve Bayes
- Support Vector Machines
- K-Nearest Neighbor
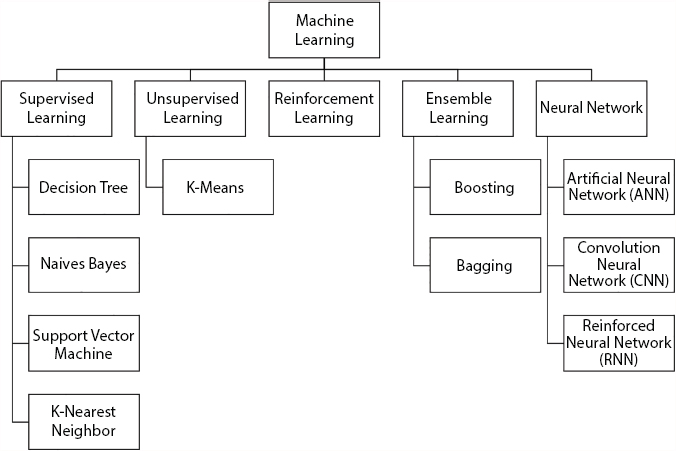
Figure 7.13 Classification of machine learning that can be supported in IoT.
Supervised learning collects the data and provides the data output from the previously learnt data. This learning method is used to solve real-world problems.
7.3.1.2 Unsupervised Learning
In unsupervised learning, the learning model is trained with “unlabeled data”. Outcomes can be predicted for unforeseen data as input. The input data can be random, no systematic pattern, and there will not be any associated labels. K-Means algorithm is an example of this learning method.
7.3.1.3 Reinforcement Learning
In reinforcement learning, reinforcement agent decides on what action to be performed on the given data. It learns from experience when training data set is not present. This method maps the actions to rewards to suit the best possible rewarding action by trial-and-error method.
7.3.1.4 Ensemble Learning
The ensembling method is combining the prediction of various predictions of various models. This kind of combined prediction is to increase the accuracy. This model can be used for classification and regression algorithms. Weighted average is used in bagging, whereas weighted voting is used in boosting. Gradient Boosting, Random Forest, and Bagging are the examples of ensemble learning.
7.3.1.5 Neural Network
Neural network model is designed based on the simulation of biological neurosystem. Each active unit is called “neuron”. Each neural network is designed with neuron, network architecture, and learning method. Neuron is a unit, and the main purpose is for computational component. The input signals are multiplied with weights and the signals are aggregated. Aggregated signals are compared with threshold, and it is called bias. If the aggregated signal is higher than bias, then the neuron is activated using an activation function.
7.4 Challenges in Data Center and IoT
7.4.1 Major Challenges
The following are the major challenges of IoT [2] and data center; this is also depicted in Figure 7.14.
- High Availability: All devices in the network should be highly available, and if any device restarts or switched off, then the recovery mechanism or backup communication path should be defined and should be in operational condition.
- Speed: With high speed, latency should be less. It should also achieve high speed in processing the data and computational speed [7].
- Data Storage: IoT system should have required data storage, since it generates huge amount of data. Any disk repository failures should be identified well in advance; currently, we have RAID (Redundant Array of Inexpensive Disks). To be more effective IoT systems, identify machine learning models and predict the failures well in advance to reduce the downtime of the data center [15].

Figure 7.14 Challenges in IoT and data center.
- Machine Learning Methods: Proper machine learning models to be identified to make decision automatically. If the machine learning techniques are not proper and learning is not performed properly, then the automatic decision-making in IoT will become risky.
- Scalability: Architecture should support high scalable numbers of devices in IoT network. All the applications and computational mechanisms should be highly scalable.
- Security: Unsecured devices can block the services. The network traffic should be monitored to detect the malicious traffic. It should detect the suspicious behavior in the IoT environment [10].
7.5 Conclusion
IoT is playing a significant role in the smart technology world. IoT along with machine learning and AI techniques becomes the world’s giant powerful communication between smart devices. IoT can connect any small devices over the internet and it can be controlled from anywhere in the world through this technology. The processing of data in the network along with IoT, data center, edge computing, and AI techniques will be an optimistic environment for smart control and automation. Advantage of big data analysis can also be utilized. In this chapter, we have discussed IoT, IoT protocols, handling IoT in modern data centers, various IoT applications, and major challenges.
References
1. Gubbi, J., Buyya, R., Marusic, S., Palaniswami, M., Gubbi, J. et al., Internet of Things (IoT): A vision, architectural elements, and future direction. Future Gener. Comput. Syst., 29, 1645–1660, 2013.
2. Salman, T., Networking Protocols and Standards for Internet of Things. Internet of Things Protocols and Standards (wustl.edu).
3. Mahdavinejad, M.S., Rezvan, M., Barekatain, M., Adibi, P., Barnaghi, P., Sheth, A.P., Machine learning for internet of things data analysis: a survey. Digital Commun. Networks, 4, 161–175, 2018.
4. Aazam, M. and Huh, E.-N., Fog computing micro datacenter based dynamic resource estimation and pricing model for iot, in: 2015 IEEE 29th International Conference on Advanced Information Networking and Applications, IEEE, pp. 687–694, 2015.
5. Shi, Y., Ding, G., Wang, H., Roman, H.E., Lu, S., The fog computing service for healthcare, in: Future Information and Communication Technologies for Ubiquitous HealthCare (Ubi-HealthTech), 2015 2nd International Symposium on, IEEE, pp. 1–5, 2015.
6. Turing, A.M., Computing machinery and intelligence. Mind, LIX, 236, 433– 60, 1950.
7. Jouppi, N.P., Young, C., Patil, N., Patterson, D., Agrawal, G., Bajwa, R. et al., In datacenterperformanceanalysisofatensorprocessingunit, in: Proceedings of 2017 ACM/IEEE 44th Annual International Symposium on Computer Architecture, Toronto, ON, Canada, 2017 Jun 24–28, pp. 1–12, 2017.
8. Big Data in IOT, Available from: https://mindmajix.com/big-data-in-iot.
9. Atzori, L., Iera, A., Morabito, G., The Internet of Things: a survey. Comput. Networks, 54, 15, 2787–2805, 2010.
10. Botta, A., de Donato, W., Persico, V., Pescape, A., Integration of cloud computing and Internet of Things: a survey. Future Gener. Comput. Syst., 56, 684–700, 2016.
11. Bottou, L., From machine learning to machine reasoning. Mach. Learn., 94, 2, 133–149, 2014.
12. Gama, K., Touseau, L., Donsez, D., Combining heterogeneous service technologies for building an Internet of Things middleware. Comput. Commun., 35, 4, 405–417, 2012.
13. Liu, C.H., Yang, B., Liu, T., Efficient naming, addressing and profile services in Internet of Things sensory environments. Ad Hoc Netw., 18, 85–101, 2014.
14. Miao, W., Ting-Jie, L., Fei-Yang, L., Jing, S., Hui-Ying, D., Research on the Architecture of Internet of Things. Paper presented at the 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), 20–22 Aug. 2010.
15. Nastic, S., Vögler, M., Inzinger, C., Truong, H.L., Dustdar, S., rtGovOps: A Runtime Framework for Governance in Large-Scale Software-Defined IoT Cloud Systems. Paper presented at the 2015 3rd IEEE International Conference on Mobile Cloud Computing, Services, and Engineering, March 30, 2015–April 3, 2015.
16. Liu, Y., Muppala, J.K., Veeraraghavan, M., Lin, D., Hamdi, M., Data Center Networks, Springer Briefs in Computer Science, 2013.
- *Corresponding author: [email protected]
