THE ACTUAL DEPLOYMENT of a firewall is a fairly straightforward process. This process begins with understanding the network environment, includes selecting a product that satisfies security needs, and ends with a more secured network infrastructure. Toward that end, this chapter examines a few of the remaining concepts that are often part of the decision-making process.
Firewalls are useful in many different situations. Every network infrastructure can benefit from proper use of a firewall. This chapter presents additional concerns and decision points for small and large network environments, host software firewalls, native operating system (OS) firewalls, third-party OS firewall alternatives, internet service provider (ISP) connection device firewalls, commercial firewall options, open-source firewalls, hardware firewalls, and virtual firewalls.
Firewall options for the individual or for those running a small office range from native OS firewalls to special-purpose devices. Most individuals and small office/home office (SOHO) users are concerned about security but don't want to spend more than really necessary. Obtaining a reasonable level of security for most home or small office environments is actually quite easy and cost effective.
First, understanding the common threats facing such an environment suggests that firewall options can be simple and inexpensive. While the Internet is not a safe place, interacting with Internet resources is not an automatic recipe for damage and destruction. Common sense and use of basic security tools greatly reduces the likelihood that a significant compromise from the Internet will take place.
Generally, Internet threats fall into two main categories: passive and active. Passive threats are those you must seek out to be harmed. For example, you have to visit a Web site to be harmed by malicious code embedded in that site. Likewise, downloading infected content occurs only when you elect to click on a download link. Most users can avoid most passive threats by making good and safe choices as to where to go and what to do on the Internet.
Note
Installing a handful of security tools doesn't mean that you can throw caution to the wind and randomly explore the entire Internet safely. Instead, by using simple security tools along with common sense, most threats are either blocked or avoided. Potential exceptions can always affect this rule, of course, such as when a trusted site is compromised and your next visit results in the transfer of malware to your hard drive.
To address passive threats, modern Web browsers include pop-up blockers, cookie filters (Figure 10-1), and malicious site managers to limit exposure. The use of antivirus scanning, an anti-spyware scanner, and anti-SPAM filters addresses other common threats. Adding a firewall to your security stance protects against most of the passive threats on the Internet that might be casually triggered. While it's still possible to go looking and find trouble, most well-known and popular sites take security seriously and strive to make accessing their resources as secure as possible.
The other category of Internet threat is active. An active threat is one that takes some type of initiative to seek out a target to compromise. These can be hackers, intruders, or automated worms. In any case, an active threat seeks out vulnerable targets. If you do not have reasonable security deployed and an active threat discovers your system, you might be at risk for a compromise.
Fortunately, most individuals and small office environments are not significant or primary targets of most hacker activity. There just isn't enough value or benefit in spending the time and effort to compromise a moderately secured single computer or small network. If your business is getting lots of traffic and orders or you happen to be hosting hundreds of systems, then you naturally become a more valuable target to hackers.
In most circumstances, the average home user and most small offices (such as those operating a dozen or fewer computers in a network) can obtain reasonable security protection from very simple and inexpensive firewall options.
The first firewall option to consider is any native firewall of the operating system. Most OSs include a default or native firewall. If so, investigate its features and options before automatically tossing it aside. Many of the firewalls found in the latest releases of operating systems are as good as or better than most commercially available third-party host software firewall options.
One of the most well-known examples of a native operating system firewall is Windows Firewall. The Windows Firewall made its debut in the Windows OS as part of Service Pack 2 for Windows XP. Initially, Windows Firewall was panned because it imposed security, restrictions, and control on the Windows OS where none existed before. Many applications and services failed to function with the Windows Firewall. Ironically, many of these "failures" were caused not by Windows Firewall, but by a service performing insecure and unfiltered activities blocked by the security provided by the new OS firewall.
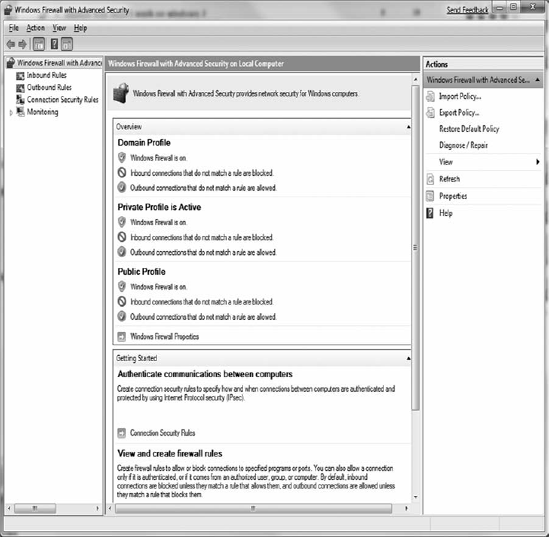
Since its initial release, Windows Firewall has matured. It appeared as a standard native feature in Windows Vista and Windows 7 (Figure 10-2). The measure is likely to remain a key OS component in future versions of Windows. The feature set and uses of Windows 7 Firewall are discussed in a later section in this chapter.
Other OSs may or may not have a firewall as well recognized as Windows Firewall, but you should still investigate the standard options and feature set provided natively before seeking out alternatives. After all, you'd never custom turbo-charge a brand new car until you've driven it and road tested its standard features.
Linux distributions do not automatically come with a native software firewall. And even when Linux provides a native firewall, it's not likely to be enabled or configured by default. Due to the wide range of variations in Linux distributions, Linux provides a range of firewalls. Linux firewalls include older products such as ipchains and iptables, as well as newer options such as PF, Netfilter, and Vyatta.
In addition to the free or native OS firewall options, another simple and easy firewall that individuals and SOHOs can use is firewalls hosted by ISP connection devices or wireless access points. Most ISP connection devices, including cable modems, digital subscriber line (DSL) modems, satellite modems, and wireless modems include firewall features. A firewall feature may or may not represent a fully functional firewall. Some are basic filtering tools that block IP addresses, ports, or protocols using a simple blacklist technique.
If the ISP connection device provides firewall services, obtain a copy of the original manufacturer's user manual for the device. This will provide the best initial information on accessing and configuring the device's firewall, since your ISP has probably chosen to lock down access to the connection device. For more on the use of an ISP connection device firewall, please see the section later in this chapter.
An ISP connection device may or may not offer wireless connectivity. If the provider does not offer a wireless option or requires you to pay extra for wireless via their equipment, you should consider deploying your own wireless access point. Most wireless access points for consumers and SOHO environments cost under $100 and offer firewall services as well as wireless connectivity.
The use of native host OS firewalls and a hardware firewall provided by an ISP connection device or wireless access point is usually more than sufficient filtering security for a home user or a small office network. However, if you want to explore other options or you have a larger, riskier, or more sensitive environment, consider the other firewall alternatives.
Note
Before installing any third-party software firewall, always double-check for full compatibility with your current operating system version and patch level. If the firewall's documentation does not specifically list your operating system as being fully compatible, don't assume that the measure will work properly. Firewall security is not something to leave to chance.
The next step up from a native OS firewall (or even an OS without a firewall) is a third-party host software firewall. These options include both open-source and commercial software firewalls for most operating systems.
You can use a host software firewall in several situations. The first and most obvious use is simply to protect a client system. This is the original and intended purpose of a host software firewall. Keep in mind that a host software firewall provides protections for both inbound and outbound communications. A host software firewall protects the client from compromises on the network and protects the network from compromises on the client.
Use a host software firewall as an additional layer of protection on a server system. Most server operating systems do not include a host software firewall. Therefore, often a dedicated firewall appliance deploys on the network. A host software firewall on a server is never a substitute for an appliance firewall. However, it can be a supplement.
Note
When installing a third-party software firewall, make sure all native or other firewalls are disabled or uninstalled. Do not attempt to run two software firewalls simultaneously on the same computer system. It's acceptable to run different software firewalls on different systems and to even use one or more appliance hardware firewalls. Just do not attempt to use two software firewalls on one system.
A host software firewall can provide firewall filtering services in relation to a virtual private network (VPN). Just because the VPN link itself may be encrypted does not guarantee that the other end of the VPN connection is as secure as you might desire. Using a host software firewall in conjunction with either a software host VPN (such as a transport mode VPN or a remote access VPN) or an appliance VPN adds an additional layer of protection against compromises that could traverse the VPN connection.
A host software firewall can provide modest protection for small networks. Home networks, gaming networks, and small office networks are sometimes constructed using a primary system connected to the Internet that shares that connection with a small network off of a secondary network interface. On a Windows system, this Internet Connection Sharing service makes this type of network configuration simple. Use a host software firewall and provide the secondary network with modest firewall filtering services.
A host software firewall likely has many other uses. Don't limit your imagination or deployment options to those discussed in books, described in manuals, or prescribed by the vendor. Use host software firewalls in any network configuration. The goal is to establish additional layers of security, not conform to static notions of design and implementation.
Software firewall products are important options to consider when designing and deploying a security solution for home environments as well as corporate IT infrastructures. However, as with any type of software, the available products change constantly. Updated versions of software firewalls are released frequently; some products disappear from the marketplace, while new firewall products appear on the scene all the time.
Before selecting a specific firewall product, do research to confirm that the firewall is still a fully supported and maintained solution. You don't want to "buy into" a product that has already been marked for retirement or phase-out, or be invested in the installation of a version imminently at risk of being superseded. Verify that the vendor is still supporting the firewall product. Check on the revision history and, based on previous time frames, estimate if the current version release is it a bit stale or a bit tardy for a revision.
Beware the textbook answer. Most authors are reluctant to recommend specific current products. Books typically take six to twelve months to reach the hands of readers once the author completes the manuscript; coincidentally, six to twelve months is often the lifespan of many product versions. A product an author recommends might no longer be the best option by the time that recommendation reaches readers.
So, take caution when following any specific "textbook" advice about a specific product, especially a specific version of a product. Question a product's shelf life. Gather fresh information. Always double-check the facts, reviews, and suggestions via current Internet search resources, vendor Web sites, IT association blogs and discussion forums, industry journals, and the mass market computing magazines available. Like milk and cheese, most computer software products have an effective "use by" date that you should be familiar with.
A host of third-party software firewalls are worth considering. Here are just a few of the more widely known options:
Checkpoint ZoneAlarm Pro (free and retail)
Comodo Firewall Pro (free)
eConceal Pro (retail)
Injoy Firewall (retail)
Jetico Personal Firewall (retail)
Lavasoft Personal Firewall (retail)
Look'n'Stop (retail)
Norman Personal Firewall (retail)
Outpost Firewall Pro (free and retail)
PC Tools Firewall Plus (free)
Prevention (retail)
PrivateFirewall (free)
Sphinx Software Windows 7 Firewall Control (free and retail)
Tall Emu Online Armor Personal Firewall (free and retail)
In addition to standalone, third-party firewalls, some firewalls come packaged as part of a security suite. These suite-member firewalls are not available as standalone products. However, the collection of security applications might be a worthwhile collection if you don't already have existing solutions. Some security suites to consider include:
Bullguard Internet Security
Computer Associates Internet Security
F-Secure Internet Security
Kaspersky Internet Security
McAfee Personal Firewall Plus
MicroWorld eScan Internet Security Suite
Norton Internet Security and Norton 360
Panda Internet Security
Trend Micro Internet Security
Webroot Internet Security Essentials
How fresh are these lists? These products were current and available as of summer 2010. The lists are not exhaustive and include only well-known products. As you read this, new firewall options might now be available and some of the listed products might have been terminated. If you want to search for more or current options, search using keywords such as software firewall, and review.
The native Windows Firewall of Windows 7 (Figure 10-3) is a sufficient security measure for many situations. Before rushing to replace this free security component, take the time to evaluate the benefits of this capable firewall option. The Windows 7 firewall is available only on Windows 7 and is a host software firewall. However, it can be used in a variety of situations and network configurations for most home and SOHO environments.
Windows 7 Firewall includes configuration profiles, so you can create custom firewall configuration settings for Work, Home, and Public connections. This allows strict limitations in public, modest settings at work, and more options available when accessing from home (or whatever your preferences). The benefit is that, once configured, the firewall will adjust its settings based upon the network connection each time you're connected to a known, previously accessed network.
Windows 7 Firewall creates a password-protected homegroup or workgroup that allows file and printer sharing between systems authorized by a password. This is an improvement over previous versions of the Windows Firewall, which often encouraged users just to turn off the whole firewall rather than properly configure file and printer sharing access rules. In addition, this applies not just to Windows systems, but any devices or computers recognized as media sharing devices (such as an Xbox 360).
Other Windows Firewall improvements in the Windows 7 version include a more granular control and configuration management interface, more extensive logging, and extended ability to be managed from a command line (using "netsh advfirewall firewall" command instead of the previous "netsh firewall" command).
While not revolutionary, and still lacking a few features such as being a true two-way personal firewall with program control, Windows 7 Firewall is a worthwhile host software firewall for most clients in most network situations. That said, you should still explore how this product fits your own computing environment and security needs.
A Linux system can benefit from a host software firewall or can support a software firewall for a network. The first idea is simply to install a host software firewall for the benefit of the local user. This is the same idea as the Windows Firewall on client versions of Windows. A variety of host firewall options are available for Linux, including both open-source and commercial options including:
IPCop
SmoothWall (Figure 10-4)
IPFire
pfSense
mOnOwall
If you selected Linux for its low cost of entry, then selecting an equally low-cost host software firewall is often an attractive option. However, paying for commercial host firewall products might offer a greater range of functions or services, along with better technical support.
Using a Linux software firewall as a replacement for a commercial firewall appliance can be a very cost-effective solution. Linux often can repurpose computer hardware that's no longer sufficient to support larger, bulkier, more resource-intensive operating systems, such as Windows. Linux can often extend the useful lifetime of computer hardware by several years. A repurposed computer system running Linux is a great option for use as a software firewall host. For a more complete examination of the use of Linux as a host OS for a software firewall, see Chapter 13, Firewall Implementation: A Thorough Case Study.
In addition to the free or native OS firewall options, another simple and easy firewall that individuals and SOHOs can use is firewalls hosted by ISP connection devices, routers, or wireless access points. Most of ISP connection devices, including cable modems, DSL modems, satellite modems, and routers, include firewall features. A firewall feature may or may not be a fully functional firewall. It could be a basic filtering tool that blocks IP addresses, ports, or protocols using a simple blacklist technique.
An ISP connection device is any hardware connecting a local network—or even a single computer—to a telco's carrier network to access the Internet. Common ISP connection devices include DSL modems and cable modems (remember that these are modems in merchandising-name only; they are really routers). This definition can also include a wide range of other broadband devices, including routers, switches, and wireless access points, especially when required by the ISP to establish an Internet connection.
Tip
If the ISP connection device provides firewall services, obtain a copy of the original manufacturer's user manual for the device. This documentation will provide the best initial information on accessing and configuring the device's firewall.
Most ISP connection devices use a Web interface. To initiate access to the management interface, point a Web browser to the IP address of the device. In most cases, the device's IP address is the default gateway address, DHCP address, or possibly DNS address of the client's interface directly connected to a physical port on the device.
Attempting to open the configuration interface is likely to prompt for authentication credentials. The vendor's user manual should indicate the device defaults for these. If not, search the Internet using keywords such as "default password" along with the device name, make, and model. If that fails, try username "admin" with a password of "admin" or "password." It's shocking how often these are correct.
Your ISP has likely chosen to lock down access to the connection device. This is sometimes done as a precaution against the uninitiated, who might cause increased technical support hassles. If you discover that your ISP connection device is locked down, try calling your ISP and asking them to grant you access (often by their revealing the credentials to log into the device).
If they refuse to offer this information, then you have four choices. First, you can accept their refusal as "just how it is" and employ some other device as a hardware firewall. Second, you can change ISP or service provider to a carrier that will grant you access to configure the device. Third, see if you can replace the carrier's device with one that you own and fully control. Fourth, you can seek out ISP and device-specific information on the Internet, which might include bypass or hacking details. However, be very cautious when choosing this latter route; it's often unproductive, is probably a violation of the ISP terms of service, is unethical, and may even be illegal.
Note
Whatever their reasons, cable providers are generally less likely to allow you access into their connection device, while most DSL providers seem willing to grant at least partial access.
If you are unable to find a legitimate path to accessing the configuration interface of your ISP connection device, hacking the device should be your last and final option. Hacking an ISP-provided device will void your contract and could make you liable for the cost of the device plus fines and possible legal action. A more ethical solution would be to replace the device with one you own and control, or switch ISPs altogether.
Note
Be careful about searching for Web sites that offer information on how to hack or bypass ISP equipment. Often the sites are "booby trapped" with malware to trap the unsuspecting visitor. In addition, some ISP equipment may be leased, not sold, and attempting to access internal features may violate the contract, if not the law.
If all else fails, add your own firewall between the ISP connection device and your first networked system. With this configuration, you are still gaining the benefit of an in-line firewall without violating any contracts or flirting with legal troubles. In most cases, you'll want to supplement or disable an ISP connection device's firewall anyway. Thus if your ISP blocks access to it, just design your security as if the device offered no firewall protection to begin with.
Many home routers have sufficiently robust features that you can configure them to function as firewalls. To ensure ease of use (and minimize product returns), these devices are usually shipped with all security features turned off. Because "plug 'n' play" results in immediate connectivity, many users never go back to configure their equipment for security. Thus, hackers and malware often are able to intrude easily into home networks. You can prevent that by understanding what is available in this class of products.
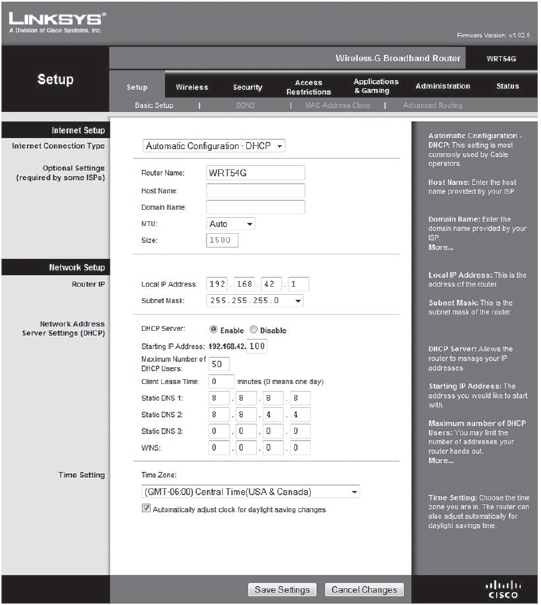
To access a home router, type into your browser the IP address of your gateway. To determine that on a Windows machine, type Start > Run > Command, and at the C:> prompt, type ipconfig. Most routers ship with a default address of 192.168.1.1. If you remember, 192.168.X.X is a non-routable range of IP addresses, which means that traffic inside that address range will not be shared with addresses outside that range.
Once logged in, consider changing a number of settings (Figure 10-5). First, if the router is a wireless device, change the Service Set Identifier (SSID) from the default setting. You do not want to be one of eight "Linksys" access points in your neighborhood. Why is this important? Most PCs will grab the strongest wireless signal from a known SSID. If you have standard SSIDs such as "Linksys" in your wireless access table, you may find yourself on a neighbor's (or hacker's) system some day without realizing it. Another good idea is to change the default IP address range to something else other than 192.168.1.X. This creates a custom range for your own network. If you hard-code your internal network range to something like 10.20.30.X, you're less likely to stumble into that situation.
Most routers enable dynamic host configuration protocol (DHCP) by default. You could lock down your network by either hard-coding IP addresses into each authorized machine (and turning off DHCP), or by setting a strict upper limit on the number of devices permitted to have DHCP leases (most default settings are 100). If you have five devices, limit the number of connections to five. (Don't forget about the Xbox 360 or PS3—they need IP addresses too)!
For firewall settings, most routers will have a configuration page to block services or control port access. Determine what ports you need to access the Internet, and then block all of the rest. Note this setting restricts OUTBOUND traffic. So why block it if it originates from within? Malware, zombies, bots, and other hostile applications usually have to connect to the outside to do their damage. If you accidentally download dangerous malware onto your laptop at your favorite coffee bar, and then connect to your home or office network behind the firewall, that malware may have access to all of your peer systems. However, if you are blocking all nonessential outbound traffic, then most malware won't be able to exfiltrate your sensitive information or ask for evil instructions. Only those applications that use a common port (like 80) will be able to get through.
Which outbound ports should you block? First, consult your policy, or determine what programs you are using. For the most part, you'll want to PERMIT the following outbound ports open at all times:
Port 25—SMTP (outbound mail)
Port 53—DNS
Port 80—http
Port 110—POP (initiate request for inbound mail)
Port 443—https
Ports 465 and 995—SMTP and POP (if you're using Gmail)
Port 1024-1035—DCOM ports for downloading files (increase number of ports based on number of systems protected; ten is usually sufficient for a home network)
Beyond port 1035, you may not need to allow outbound traffic, unless you are using cPanel to access an externally hosted Web site on port 2083, or port 11371 if you're looking up PGP keys. By blocking all other high ports, you'll also quickly hear from people who may have been using some of these ports, which are dedicated to gaming software. At home, you might want to allow (or set time limits); at work, you probably want to block these ports.
In general, you should not accept any connections that originate from outside your firewall. Your policy may permit exceptions, such as remote access tools, so be careful about blocking everything. Some home firewalls don't provide a direct way to block specific incoming ports, but most allow you to do "port forwarding." A clever way to use this to thwart external attacks is to forward to a nonexistent port. So, for example, if your local network range goes from 10.20.30.40 to 10.20.30.49, forward incoming connection requests to port 10.20.30.99—where no one is listening! Ports you might consider forwarding are:
Ports 20 and 21—ftp-data and ftp. Prevent external connections from downloading your files.
Port 23—telnet. Prevent external connections from insecurely logging into your internal systems.
Port 53—DNS. Prevent external entities from poisoning your DNS cache.
Port 80—http (unless you are running a Web server from behind your firewall, which is a bad idea).
Ports 81 and 82—often used as "overflow" for port 80. No valid use, so block them.
Ports 137, 138, 139—netbios. Often exploited by malware, this provides access into Windows systems.
Port 443—https (unless you are running a secure Web server from behind your firewall, which is still a bad idea).
Port 445—netbios for Windows 2000 and later.
Port 3074—Xbox game port. Don't allow strangers to connect to your Xbox while you're away. Remember—it "lives" on your internal network.
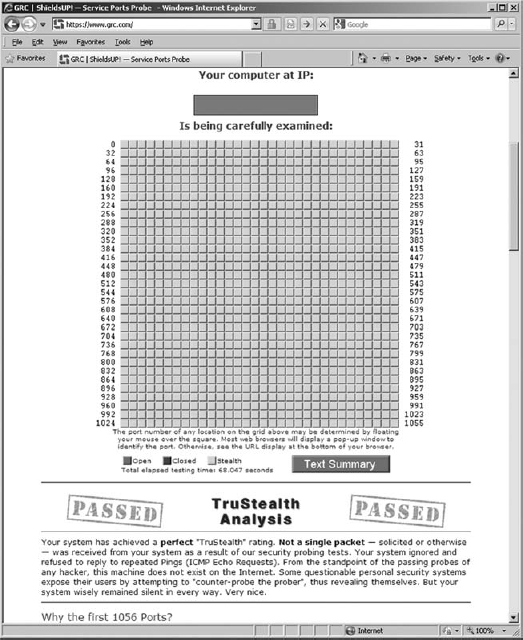
An excellent way to test your configuration is to go to Steve Gibson's http://www.grc.com Web site and run his free ShieldsUP! port scanning tool (Figure 10-6). Most people end up scoring poorly. If you can achieve 100 percent stealth, you've done a great job.
Commercial software network firewalls install onto your own hardware and provide network-level security services. Some commercial software network firewalls install on top of existing operating systems, such as Windows. Others are complete OS replacements, many of which are Linux-based.
As with any firewall selection, know your environment and understand your security needs before shopping for a firewall solution. It's bad security to purchase a product because it's on sale, is prominently advertised, or is recommended by a salesperson (or even an author). Instead, match your security needs with the product that best suits, fulfills, or satisfies those needs.
An open-source software network firewall is a product that is usually available at no monetary cost and whose source code is available for review. An open-source solution often can be a cost-effective option. However, just because a product is free does not ensure its reliability or trustworthiness. Additionally, being able to review the source code doesn't warrant the reliability of a product.
You should thoroughly review and test every security product, including firewalls, before purchase and deployment. Seek out a product that meets your specific organizational security needs, rather than selecting something just because it's open source or free of charge.
Appliance firewalls, whether called device or hardware firewalls, are common and nearly essential elements of every moderate to large network infrastructure. A hardware firewall is a dedicated hardware device that has been specifically built and hardened to support the functions of the firewall software running on it. A hardware firewall is also known as an appliance firewall.
A hardware firewall does not require any additional hardware or software for its deployment. All it needs is network connections and a power connection. A hardware firewall has dedicated hardware resources not shared with any other service. A hardware firewall can protect a single system or an entire network.
A hardware firewall can filter only traffic that reaches the network interfaces of its appliance. However, you can position a hardware firewall on a network at a choke point or gateway to analyze and filter all traffic.
Firewalls, specifically hardware appliance firewalls, typically have two or more network interfaces. A firewall with two interfaces is known as a dual-homed firewall, while a firewall with three interfaces is known as a triple-homed firewall or a three-legged firewall.
The benefit of multiple interfaces is that the segments, subnets, or networks connected to each firewall interface are electronically isolated from each other. This prevents unfiltered traffic from leaping from one segment to another in an attempt to bypass firewall filtering.
However, for firewalls using multiple interfaces, ensure that you disable the TCP/IP protocol feature IP Forwarding. IP forwarding is actually a router rule that allows traffic from one interface to traverse to another interface without needing to move any further up the protocol stack than where IP resides. In many cases, IP forwarding allows packets to bypass filtering. If you're using the system as a firewall, be sure to disable this feature.
A personal hardware firewall can be part of an integrated firewall product, such as a wireless access point or a cable/DSL modem. Another variation of the personal hardware firewall is the repurposing of a client or server computer into a home-crafted, open-source firewall. One example of this is SmoothWall, a hardened bootable Linux-based firewall. A case study of deploying SmoothWall is found in Chapter 11, Firewall Deployment: A Case Study.
A commercial hardware firewall usually handles the complexity of larger organizational networks. A commercial hardware firewall is often very expensive—$10,000 or more is not uncommon.
The personal and commercial variants of software and hardware firewalls might include different add-ons or enhancements than their commercial equivalents. These add-ons or enhancements include antivirus, password management, registry protection, driver protection, VPN gateways, remote access support, IDS, IPS, spam filtering, and more. Usually these add-ons make the firewall products more attractive to the potential individual buyer. However, most commercial entities would generally avoid integrated firewall solutions in favor of dedicated products to handle the distinct security or management functions. An integrated device might offer easier administration, but represents a single point of failure for multiple services. Additionally, such devices are more difficult to troubleshoot due to the complexity of the communications supported.
A variety of manufacturers and vendors make and service appliance firewalls. The specific products in this category change constantly, so including a list of exact make and models would be outdated within months. (Remember the "sell by" date on that carton of milk?) Instead, to find the best products available for either SOHO or enterprise-sized environments, visit the vendor's technical review sites for updated product discussions, blogs and discussion forums, and buyer's guides. Some of the major vendors/brands to consider include:
Barracuda
Cisco
D-Link
Fortinet
Juniper Networks
Linksys (now owned by Cisco)
NetGear
SonicWall
WatchGuard
ZyXEL
When selecting a hardware or appliance firewall, keep a few important points in mind. Commonsense or basic concerns include ease of use, secured management interfaces, port filtering support, stateful inspection filtering, and the ability to be firmware/software upgraded.
Never skimp on throughput. Firewalls often represent bottlenecks to network bandwidth and thus should be selected to maintain wirespeed. Be sure a hardware firewall can more than handle the current network speeds and allow for future growth. If you are currently pushing a 1 Gbps network, consider a firewall capable of filtering at 2.5 Gbps wirespeed or higher.
For larger networks, centralized and remote management options are often essential. If firewall management requires direct physical contact or if you can configure only a single firewall at a time, you may find these significant hindrances to managing very large networks. An important part of a realistic firewall solution for enterprise networks can be multiple device management, including simultaneous configuration synchronization features.
Consider whether add-ons, upgrades, or extras are available and whether that's important to your decision. Some firewall devices convert to firewall-plus devices or true multifunctional devices. Additional features may include e-mail scanning, message quarantine, attachment stripping, virus scanning, mobile code filtering, anti-spyware, intrusion detection system (IDS) and intrusion prevention system (IPS) features, spam filtering, compliance monitoring, and network access control. Products that support expansion or firewall additions are known as unified threat management tools or may fall under the heading of advanced intrusion detection and prevention systems.
Whatever the options presented by a vendor, always consider them in light of your actual current and future network needs. Just because a product is expensive does not guarantee it will work better than a free, build-it-yourself alternative.
The term "virtual firewall" describes a variety of firewall and firewall-like concepts. This can include virtualized software firewalls that provide filtering services for a standard physical network, as well as firewalls running virtualized between virtualized client and server operating systems. In theory, the use of a virtualized software firewall as a replacement for a network appliance could work as long as the host OSs network communication is routed through the virtual firewall before leaving the host's network interface controller (NIC).
This is a relatively new and growing area for firewall deployment. Virtualization offers numerous benefits over traditional a single OS to a single hardware box deployment. Virtualization allows for rapid development, quick prototyping, isolation, traffic management, quick recoveries, testing, and so on. By virtualizing firewalls along with operating systems, you can craft new network architectures that do not or could not exist in the traditional network architectural concepts.
For example, with a virtualized firewall, you could route every communication between every virtualized OS through the filtering services. This would be the equivalent of deploying an appliance firewall between every system, but without the hassle, expense, or complexity.
Most of the content discussed in this book applies to software, hardware, and virtualized firewall solutions alike. Virtual firewalls are not a universal panacea. Virtual firewalls will not be useful in every situation, but they are an interesting new option for deployment to monitor, manage, and filter network traffic over traditional or virtualized network segments.
A few mundane concerns affect every firewall user when employing a firewall of any type. In most cases, these issues are common sense or at least "well known," but they are often overlooked, forgotten, or discounted. To avoid this, they are included here.
After writing a firewall security policy, obtaining approval, and obtaining the firewall to install, the first step in deploying a new firewall is to change the default password of the administrator account. Better yet, modify every pre-defined user account and every default access code of any type. Use something unique, original, and difficult to predict.
Testing is essential. No change or alteration of configuration is so minuscule that testing is inappropriate. Every change should trigger a test to confirm that the change took effect and caused no unintended consequences.
Many firewall appliances can be quickly reset to factory defaults with the simple press of a button. Some devices have a reset button prominently located and labeled so that anyone with a finger can casually revert to default status. However, such an obvious button has disadvantages, such as accidental or innocent hand movements.
Fortunately, a growing number of devices that still offer button-based reset options have receded the button behind a tiny pinhole. A straightened paper clip (or an expensive tiny screwdriver) depresses the reset button. Often a single quick press is insufficient to reset the device; a series of presses or a prolonged 10- or 30-second depress may be necessary to trigger a reset. This feature makes accidental depression impossible but also makes intentional resetting a bit of a challenge. Be sure to consult the user manual for instructions that may not be obvious or intuitive.
Keep a printed or written copy of all rule sets and settings on hand. Periodically, verify manually that all settings remain as you want them. This is done by viewing the configuration or management interfaces and comparing the live settings to those defined in your documentation. Whenever you discover a discrepancy, investigate and repair it at once.
Finally, regularly visit the vendor's Web site and discussion forums (including non-vendor supported ones) for news and information about your firewall product. Keep current with announcements of updates, problems with updates, newly discovered holes or exploits, alternative configuration ideas, troubleshooting options, and more.
Firewalls are useful in many different situations. Every network infrastructure can benefit from proper use of a firewall. When making a choice about what firewall to deploy, consider a breadth of options, including the needs of both small and large network environments, host software firewalls, native OS firewalls, third-party OS firewall alternatives, ISP connection device firewalls, commercial firewall options, open-source firewalls, hardware firewalls, and virtual firewalls.
What types of Internet threats are considered passive, in the sense that the user must seek them out to be harmed? (Select all that apply)
Malicious Web sites
Worms
Downloaded content
SPAM
Trojan Horse
Average home users and workers at a large corporation can both benefit from which of the following:
Open-source hardware firewall
Gateway server firewall
Commercial appliance firewall
Host firewall
Proprietary device firewall
What are the two locations that a home or SOHO user is likely to find a firewall by default? (Select all that apply)
A self-installed software firewall
Hosted by the operating system
A build-it yourself appliance firewall
Hosted by the ISP connection device
A commercial firewall device
Windows operating systems are the only operating systems that include a native or default host firewall.
True
False
What is the maximum number of host software firewalls that should be operating on a single computer at any point in time?
One
Two
Three
Four
None
Firewalls are design to provide protection for both _______ and _______ communications.
An organization should consider purchasing last year's model firewall instead of this year if they receive a significant discount.
True
False
When considering the deployment of a firewall, which of the following should be considered? (Select all that apply)
Commercial firewalls
Legacy firewalls
Open-source firewalls
Beta firewalls
Do-it-yourself (DIY) firewalls
The Windows 7 firewall includes a new easy-to-configure feature that allows file and printer sharing between systems authorized by a password. This feature no longer encourages users to just turn off the whole firewall rather than figure out how to properly configure file and printer sharing access rules. What is this feature called?
Internet connection sharing
Quick config
Homegroup
Shared computing
Microsoft Easy Access Firewall
What is the command line tool used to configure the Windows 7 firewall?
route firewall
netsh advfirewall firewall
new use firewall
firewall config
netsh firewall
Using a Linux software firewall as a replacement for a commercial firewall appliance can be a very cost-effective solution. Linux often can repurpose computer hardware that is no longer sufficient to support larger, bulkier, more resource-intensive operating systems.
True
False
The firewall configuration on an ISP connection device is most commonly accessed through what type of management interface?
SMTP
HTTP/HTTPS
SSH
FTP
RSH
If your ISP refuses to grant access to configure their connection device, what legal options are available to you as alternatives? (Select all that apply)
Live without configuring it
Hack into it
Deploy your own hardware firewall alternative
Purchase your own connection device
Change ISPs
What is the command line utility used to display the IP configuration of your Windows computer?
ifconfig
net use network
netconfig
ipconfig
netstat
When configuring a wireless access point to provide firewall services, which of the following are important configuration actions to take? (Select all that apply)
Change the default administrator password
Block unwanted ports
Change the SSID
Turn off SSID broadcasting
Change the default IP address range
In general, you should not accept any connections that originate from _______ your firewall.
If your home firewall device is unable to block ports, use _______ instead to route data to nonexistent hosts.
It is best to pick a firewall based on:
Actual network security needs
Recommendations of a salesperson
The list of awards given the product
The price
Prominent advertisement
Appliance firewalls are only and always commercial firewalls.
True
False
When selecting a firewall, especially a hardware firewall, never skimp on _______.