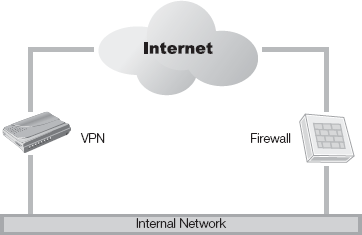
VIRTUAL PRIVATE NETWORK (VPN) MANAGEMENT is a critical component in your organization's computer security. VPNs extend the internal network beyond the perimeter secured by firewalls and other security technologies. Proper management of a VPN requires an understanding not only of VPN technologies, but also the business requirements driving VPN implementation.
Using the wrong type of VPN or a VPN that doesn't meet your organization's requirements can create security problems where none previously existed. Before selecting a VPN product or technology for your organization, create a detailed requirements document. This should factor in not only the security requirements for the VPN, but business requirements as well. Although security is important, keep in mind that security exists to support your organization's goals, not the other way around.
As soon as you have a set of prioritized requirements, start looking for a solution that meets as many of these requirements as possible. You may not be able to find a single product that meets all requirements. When that occurs, choose the solution that best fits the highest priority requirements. In some cases, using multiple solutions to meet all the requirements may be the right solution.
Good research is crucial to selecting the appropriate VPN. Don't rely solely on Web sites, technical magazine reviews, or an attractive sales pitch. Depending on your requirements, you may want to explore robust public domain solutions rather than an off-the-shelf commercial product.
Keep in mind that VPNs are a security technology, but they may also degrade the security perimeter discussed in earlier chapters. Putting the VPN in place is just the beginning of the project; you'll need to address a number of additional factors for a successful VPN deployment.
First, familiarize yourself with the recommendations, guidelines, and procedures that will allow you to manage your VPN securely, efficiently, and as cost effectively as possible. These techniques and recommendations are known collectively as "best practices" and are generally developed and published or shared by experts in the field. VPNs have been around since the late 1990s. That means a significant amount of "real world" experience is available in the industry for your reference.
A "best practice" is generally not a tool, but rather the collected wisdom of fellow security practitioners sharing what they have learned. One of the great things about working in the information security field is that a large pool of experts are generally willing to share their experience. Be warned, however: Security experts tend to have very strong opinions, so any time you are reviewing a best practice, be sure to keep the needs and requirements of your own environment in mind. A process that works great in a 25,000-person global manufacturing company may not work nearly as well in a 50-employee medical records processing company.
That said, you might well be able to adapt a process from another company to fit your environment. The key to getting the most out of best practices is to consider them with your specific environment and requirements in mind. Keep what works, modify what you can adapt, and ignore what doesn't make sense. After some time in the business, you will be the person other people come to for advice.
Provide redundancy, because everything, including VPNs, can break. If your organization will be relying on your VPN for remote access, encrypting, and securing data, or for providing a business partner access to your extranet, you will find out quickly how critical your VPN has become on the day it breaks. Most commercial VPN products offer a fail-over or load-balancing capability, so that in the event one device fails, the other will pick up the traffic.
Alternatively, keep a spare VPN product on your shelf, configured and ready to go live in the event of a failure. Generally, waiting for tech support or ordering a spare part can take more time than your organization is willing to wait for restored service. You'll learn more on this later in the chapter.
Choosing the right VPN product is critical to the long-term success of your VPN deployment. Take your time, document your requirements, carefully evaluate the capabilities of each VPN product you review, check with peers if available, and review appropriate industry literature. A security magazine review of VPN products is a valuable tool for starting your search—or even narrowing the field once you have your requirements documented—but don't select your solution solely based on who won last year's Editor's Choice Award from your favorite industry magazine. While the editors and reviewers at most industry magazines, Web sites, and blogs are technically capable and spend a lot of time looking at products, they don't have to support the product in your environment. Ultimately, you will be responsible for meeting your organization's requirements and maintaining support.
Beware the vendor with the slick PowerPoint presentation offering a free lunch. "Slideware" is not reality; avoid purchasing products based on promises rather than proven capabilities. Slideware, also sometimes known as "vaporware," is any product that appears in a vendor's PowerPoint presentation, but is not yet available as one of their products. When possible, road-test a product in your environment before purchasing. It's always a good idea to see what a product can do first hand.
Finally, when looking for a product, consider using resellers and consultants. A good reseller can do some of the legwork for you by narrowing the search to a smaller pool of products. While some resellers work much like a standard department store, selling whatever is on the shelves, many will go the extra mile to ensure you get a product that will work in your environment. This saves them the challenge of trying to support a poor product after they've sold it, and if you like the solution, they have the opportunity to sell you additional products in the future.
A VPN policy (often referred to as a Remote Access Policy) documents your organization's rules for using the VPN. We will discuss creating a VPN policy at length later in the chapter; recognize, however, that proper policy framework is a key best practice when dealing with security technologies, especially one offering remote access to your computing environment.
The client is a critical component of your VPN solution. For the most part, VPN technology is both mature and secure. VPNs are subject to Denial of Service (DoS) attacks, but VPN servers are rarely hacked. Nevertheless, VPNs remain a viable vector for someone who wants to attack your network. The target of these attacks is typically the weakest link of the VPN chain—the client. A typical VPN client runs an operating system that needs to be patched at least once a month, runs applications that may need to be patched almost as often, and is vulnerable to viruses, spyware, and other attacks. Be sure to install antivirus software, anti-malware software, and a software firewall on every client that will be connecting to your network through the VPN.
Split tunneling is a configuration setting that allows simultaneous access to both an untrustworthy network (like the Internet) and a secured VPN network connection. This may not sound like a bad idea at first—after all, why wouldn't you want someone connected to the VPN to access the Internet or their home network (or another network) at the same time? The reason split tunneling is a bad idea is that it potentially opens a door into your network that you can't control.
If the client machine is compromised by a virus that permits remote control of the system by an attacker, and that client machine connects to the VPN, the attacker now has access to your internal network from anywhere on the Internet. If you prohibit split tunneling, then, even if the attacker can compromise the client, as soon as the VPN connects, the external connections terminate, ensuring your network is secure, even if the client is not.
If it doesn't belong to the company, it shouldn't connect to the company's network. One of the challenges of working with Remote Access VPNs is making sure that the client at the other end of the connection is secure. Remote Access VPNs permit access to a secure network from a remote location across an untrustworthy network. If the client system is not secure, you run the risk of compromising your secure network.
Fortunately, you have some control over your organization's computers. You can require antivirus, anti-malware, IDS, and firewall software on any computers your company owns. With systems not owned by the organization, you cannot require anything. As a result, if you don't prohibit non-company systems from connecting to the network, you cannot control whether those systems are secure, meaning you can't ensure that your network remains secure. It's very easy for an end user to load a VPN client on a home PC and connect to your network. While some VPN solutions offer techniques to prevent uncontrolled systems from successfully connecting, it's important that you lay the groundwork by prohibiting the practice.
Effective vulnerability management can help manage your remote clients. These are the technology and business processes used to identify, track, and mitigate known weaknesses on hosts within a computing environment.
Remember, everything is vulnerable to attack. UNIX, Windows, routers, network printers, and even your VPN solution will have vulnerabilities. Examples of vulnerabilities include software coding errors, improper configurations, and poor password choices. The danger with a VPN is that it expands your network from systems you can closely control to include systems in a home office, a branch office, a hotel, a Starbucks, or even a business partner's network.
Vulnerability management is a combination of tools and processes that allow you to reduce risk in your computing environment, including VPN-connected systems and networks. Use tools that periodically test your environment, including the VPN systems, for missing patches, configuration issues, known exploits, and other vulnerabilities. This will ensure that your remote systems as well as your local systems are secure. Scan often and address issues when you find them.
Your VPN is only as secure as your authentication method. One of the easiest ways to compromise a VPN is by compromising the authentication credentials. All it takes is one user with a password of "password" to open a direct connection to your network. A best practice is to use two-factor authentication for VPN access. This is a method of proving identity using two different authentication factors. Authentication factors are something you know, something you have, or something you are. Examples include a smart card (something you have) with a PIN (something you know); a biometric device (something you are) coupled with a password (something you know); or a proximity card (something you have) that activates a fingerprint reader (something you are).
If you fail to plan, you plan to fail. Document your implementation plan! You can't simply find an open rack in the data center, run a cable, plug in a device and keep your fingers crossed that it will work. Document your implementation and support plans. You'll learn more on this later in the chapter.
Monitoring the availability of the VPN can be a lifesaver. The typical (and worst) method to discover issues with your VPN is when users start calling for help. This can be particularly challenging when the callers include members of your organization's senior management team. A corollary of Murphy's Law may be, "The likelihood that a senior management team member will be trying to access the network over the VPN is directly proportional to the likelihood that the VPN will fail." Better to alert senior management of temporary problems than to be informed by them that something isn't working. Since VPNs are network components, you can generally use the same monitoring equipment that you use to monitor routers, switches, and other network gear.
Note
Vendors can be very helpful when your equipment is down. Many technical and information security professionals believe they can fix anything, and sometimes they will work on a problem for long hours before finally reaching out to tech support. While tech support can be problematic, especially when wading through the first level of support, the vendor can be invaluable when the problem is in the VPN equipment or software.
Once you have your VPN deployed, regularly review usage. When you notice employees who are not using the VPN, you may want to remove their access. If you see employees who have multiple concurrent connections, you may have a security issue, and should investigate further.
Backup your VPN configuration regularly. This is a good practice for any network equipment, but in the event your VPN hardware fails and needs replacement, you'll want to be able to restore your known working configuration quickly. Rebuilding a VPN configuration from the default settings can be a long and challenging task—not to mention making post-incident review meetings an unpleasant experience.
Patch regularly. Vendors typically release patches and updates to VPN code throughout the life of the product. These patches address security issues, fix bugs, or provide additional functionality. In an ideal environment, you will have a development VPN that you can use to test patches and updates. In most environments, you will not have the luxury of a development VPN and will have to test when you implement in production. In either circumstance, work closely with your vendor to make sure you receive prompt notice of patches and updates, and establish an operational process and maintenance window to apply patches and updates in a timely fashion.
Your VPN solution may end up being a critical component of the organization's business continuity planning and disaster recovery planning. In the event of an incident that prevents employees from getting to their work location, a VPN that provides work-from-home is a key component of many recovery plans. Events such as earthquakes, snowstorms, tornadoes, flooding, and other natural disasters can make working remotely a viable alternative to standard operations.
This collection of VPN management best practices is meant to serve as the starting point for your successful VPN deployment. It's not meant to be comprehensive, but instead to offer some common practices and processes to help you with your VPN deployment. Depending on your VPN solution, your environment, your business requirements, and your experiences, you may find that you will use every one of these—or use only a few. The key is to ensure that you are doing what works in your environment. If you need help, don't be afraid to reach out to your peers for advice and suggestions. You will find, over time, that you will develop your own set of best practices as you gain more experience as a security practitioner, and soon others may be asking you for advice.
If you are implementing or supporting a VPN solution, use a VPN policy to ensure your users understand the requirements for computing on the VPN. A VPN policy is sometimes called a Remote Access policy, a term used when dial-up lines and modems were the primary means to access the network remotely. Keep in mind that a VPN policy should be a part of your overall policy framework, and not a standalone. If you try to develop your VPN policy in isolation from the overall policy framework, you may find that you are duplicating information, or potentially writing VPN policy that conflicts with other aspects of your overall policy framework. For example, if you put a requirement in your VPN policy that user passwords must be 10 characters long and the password policy says they have to be eight characters long, you will confuse end users.
The components of a solid VPN policy include:
Introduction—State the policy by name and tell how it fits in the organization's policy framework.
Purpose—Describe the issues the policy addresses, and how it should be used. Include references to any applicable governance, risk, or compliance issues, as well as any specific legal or regulatory requirements supported by the document.
Scope/Binding Nature Statement—Describe the systems, networks, or people covered by the policy. Describe penalties associated with not following the policy. The phrase "disciplinary action up to and including termination" is common in security policies.
Definitions/Acronyms—Define technical terms or acronyms used in the policy.
Document—Include the document creator, creation date, version, document status (for example, draft, template, policy, and guidelines), as well as any version tracking information.
Policy—The actual policy language. Be very clear in this section and leave as little open to interpretation as possible.
Summary—If your policy is very long, you may want to summarize in a bulleted list at either the beginning or end of the policy. This provides employees a quick method to check for policy statements.
Roles and Responsibilities—If your document is lengthy, or you need to document who does what under the policy, include Roles and Responsibilities. For example, a policy dealing with infrastructure might include roles for the system manager, system architect, end user, developer, or other key people within the organization.
Some specific topics to include in your VPN policy are:
Restrict remote access to the organization's VPN solution.
Define what classes of employee can access the network by VPN. This could include regular employees, vendors, contractors and temps, or it could be restricted to only home office workers, depending on business requirements.
Define what types of VPN connections will be permitted.
Define authentication methods permitted.
Prohibit sharing of VPN credentials.
List the configuration requirements for remote hosts, including current virus protection, anti-malware, host-based intrusion detection system (HIDS) and a personal firewall. Some VPN solutions include the ability to check for these types of configurations.
Prohibit the use of non-company equipment, or if personal systems may connect to the VPN, define the minimum standards for those connections.
Define required encryption levels for VPN connections.
If you will be using your VPN for network-to-network connections, define the approval process and criteria for establishing a network-to-network connection.
Have your policy reviewed and approved by your Communications, Legal, and Human Resources Departments before release. Document the appropriate approvals in the document status portion of the policy, then communicate the policy to your employees. Posting the policy to an information security or security policy intranet Web site is a common practice. Once it's available on the intranet, you can use standard communications methods to make employees aware of the policy requirements. These methods can include e-mail, a structured awareness program, inclusion in new-hire training, or even Web-based or in-person policy training. The method you select will be based on your organizational size, locations, and requirements. They key with any type of awareness training is to structure your communications to the correct audience. A group of engineers will require a very different introduction to a technical policy than a sales team might.
These are just some of the factors in developing a VPN policy for your organization. While they should form the basis for the development of your organization's policy, be sure to cover all applicable requirements. One sure way to alienate your employees is by releasing a policy that either makes no sense to them, or that you have to revise too soon to cover things you didn't think of the first time through. Take your time, consider all the requirements, and you will end up with a usable VPN Policy.
Now that you have an understanding of best practices and VPN policy, you'll look at how to select, place, and use a VPN.
Note
With proper negotiating, you generally will not have to pay list price for a VPN product. Many vendors will readily discount their products anywhere from 15 to 40 percent depending on the volume of product you buy.
The pros and cons of the different types of VPNs will be discussed in more detail in Chapter 12.
Consider these criteria during your search:
What types of VPN connections does the solution support (user access, site-to-site, or both)?
What is the encryption protocol(s) supported (IPSec, SSL, SSH, etc.) to encrypt the data?
How many VPN connections are supported?
How well does the VPN perform compared with a high-speed network?
How well does the VPN interoperate with your existing network infrastructure?
What are the support options available from the vendor?
How easy or difficult is the VPN to setup?
What are the management capabilities available with the VPN?
What additional features does the VPN offer?
Does the VPN support failover or high availability configurations?
How scalable is the VPN?
Once you have gathered this information, you can start to narrow your selection based on how well these features meet your criteria.
Next, consider where you will deploy the VPN on your network. Three common architectures typically accompany VPN solution deployments.
A bypass architecture (see Figure 11-1) deploys the VPN so that traffic to the VPN and from the VPN to the internal network is not firewalled in any way.
This was a common architecture when VPNs were first introduced to the market. The logic behind this deployment architecture is that the since the VPN will accept only encrypted connections on a specific port, the security is adequate without additional firewalling. An additional consideration is that the since the traffic is encrypted, it doesn't require additional protection. Even if you did place a firewall on the Internet-facing VPN connection, the firewall would not be able to analyze the encrypted VPN traffic. This architecture also considers anyone connected to the VPN as a trusted host. Finally, passing traffic across a firewall always causes concerns about performance impacts and justifiably so..
Two significant issues arise with this implementation model. First, VPNs are like any network device—they can have a variety of vulnerabilities. As a result, they are still vulnerable to an attack against the device itself. The second issue is that the uses for VPN have expanded greatly since the technology first appeared, and it's not uncommon in today's environment to leverage a VPN to provide untrustworthy hosts access to portions of the network. These could be customers accessing an order management portal, vendors supporting systems on the internal network, or suppliers who are transferring invoices to your internal systems. While some controls (usually routing table-related) are available in most VPN solutions, terminating a VPN directly on your internal network is a very dangerous practice. As a result, the circumstances where a bypass VPN architecture is still a viable solution are limited, unless your risk tolerance is pretty high.
An internally connected architecture (see Figure 11-2) deploys the VPN so that traffic to the VPN and from the VPN to the internal network is not firewalled in any way.
An internally connected VPN architecture recognizes that the VPN is vulnerable to attack if placed directly on the Internet, so it places the Internet-facing VPN connection behind a firewall. As we discussed in Chapter 9, Firewall Management and Security Concerns, selecting the appropriate firewall for this solution is critical to a successful implementation. The VPN then connects any remote users or site-to-site connections directly to the internal network.
While this is an improvement over the bypass architecture, it still doesn't address the potential security issues associated with untrustworthy VPN connections. This architecture is not recommended, although it will work if the only hosts connecting are trusted hosts.
A demilitarized zone (DMZ)-based implementation (see Figure 11-3) addresses the main shortcomings of the previous two architectures.
This architecture features a firewall both in front of the VPN to protect it from Internet-based attacks, as well as a firewall behind to protect the internal network. The firewall on the inside can be configured to protect important infrastructure like financial or research servers, restrict business partners to only the systems they need access to, or even limit vendor access to only those systems that they support.
The largest negative in this design is the cost of deploying multiple firewalls for the implementation. However, many companies already have DMZs set up in this configuration, so it may be just a matter of leveraging the existing infrastructure for your needs.
Note
You can use a project management application to plan your VPN rollout, or use something as simple as a word processing application. The purpose of this plan is to allow you to structure your deployment more formally than a plan written on the back of a cocktail napkin.
After selecting the ideal VPN and determining where you're going to place it in your infrastructure, it's time to work up your deployment plan.
Before we look at the components of a successful deployment plan, keep in mind that your environment is unique to your organization. Some elements we will discuss won't apply to your deployment. These are, rather, just some common elements found in most typical VPN deployment plans. Just as with the other topics we've discussed, review these while thinking of the requirements of your organization.
To deploy your VPN successfully, you need to:
Plan the physical location of the VPN. This is commonly rack space in your data center.
Ensure your selected location meets power and cooling requirements. Get information on power and cooling requirements from your VPN's technical specifications.
Plan your IP addressing for the external and internal network connections on the VPN, as well as a pool(s) of addresses assigned to clients when they connect to the VPN. Plan for peak usage when assigning these pools to the VPN—while an average number of users is an excellent use benchmark, peak use determines the maximum number of IP addresses to ensure that all users can connect. If this is a site-to-site connection, your IP addressing plan will not be as complex, but will still be important when setting up the tunnel.
If you are using firewalls as discussed in the previous section, plan the rules you'll need on the firewalls to permit the VPN to work. Generally IPSec VPNs will require UDP port 500 for the IKE packets, and TCP port 443 for the IPSec traffic. SSL VPNs use port 443 exclusively. We will discuss this in more detail in Chapter 12, VPN Technologies. Most VPN rule sets permit ICMP packets from the Internet. If you are experiencing issues with the VPN, it's frequently useful during troubleshooting to determine if the user can reach the VPN server using tools like ping or traceroute.
Configure the VPN server by setting up the IP address pools, assigning IP addresses to the interfaces, establishing your banner message, and disabling split tunneling. It's also a good idea to have the vendor review your configuration before going live to ensure you haven't missed anything in your planning. In some cases, you might even want to have the vendor install the VPN for you while you concentrate on client rollouts, policy communications, and other rollout tasks.
Setup the authentication mechanism. Ideally a token-based authentication solution, it could also be RADIUS-based authentication, or in some smaller environments, user accounts set up on the VPN itself.
Follow your organization's change management policies when deploying the VPN. If your organization doesn't have a formal change management process, be sure to inform management of your planning schedule to avoid no surprises. The last thing you want is to bring the VPN online during the same weekend Accounting is doing a major upgrade to your organization's financial systems. If there's a problem with their upgrade, you can count on at least one person blaming it on your VPN rollout.
Once the VPN is up and on the network, create a pilot group to test the deployment. Address any issues before you roll out to a larger user pool. Minimize any issues that the employees might face with the new solution. The best way to doom a new solution is to deploy it with lots of problems. You may find some employees will have a low tolerance for issues.
Develop your operations manual, which will document the configuration, the operations procedures, change planning processes, and change history.
Develop your user documentation. Include how to install the client (if a manual install is required), how to login, whom to call for support, frequently asked questions, and any other information you think will make the user's experience with the VPN easier.
Develop your support processes. Who gets the first call when there's an issue? What is the escalation path if the issue can't be resolved?
Communicate the rollout plan to management and affected employees. Let them know the timing, benefits of the new solution, and anything else that you believe will help you have a successful deployment.
Install the VPN client for any remote access users. If this is a site-to-site deployment, configure the tunnel connection.
Distribute authentication credentials, tokens, and so on.
Train your users.
Go live—and enjoy a successful VPN rollout.
You now should be able to select, plan, and successfully deploy a VPN for your organization.
Consider the threats and attacks against your VPN, and how to mitigate them. A VPN can be a critical component of your information security infrastructure. A properly implemented VPN addresses a number of common attacks against your infrastructure, including eavesdropping, man-in-the-middle, replay, and others. However, while your VPN can mitigate attacks, it can also opens up an entirely new set of security issues.
Remember VPNs are essentially network devices and subject to many of the same security issues you would find in a router or a switch. If you are running a software VPN, then your VPN can have many of the issues you find on your network's servers.
A hardware VPN solution can suffer from a number of security vulnerabilities, including:
One of the most common and easily exploited vulnerabilities on any hardware network device is the default password. Vendors set an initial password on their equipment and usually all it takes to discover this password is a quick search on the Internet. Usually it's not even particularly hard to guess. Try the vendor name, "admin," or "password," and your odds are good that you'll be able to login. It seems like a sensible mechanism—the vendor doesn't want to distribute their equipment without a password, so they set a standard password that's easy for the installer to remember.
The potential problem occurs when the installer forgets to change that password. It's not uncommon for an installer to leave the password in place for the duration of the installation. Typing in "admin" after each reboot is much easier than typing in "$$Th!s!sAS3cur3P@ssw0rd!!" every time after making a change requiring a reboot. The problem occurs when either the installer forgets to change the password when the work is done, or an attack occurs while the installer is in the middle of the installation.
Imagine the installer has a couple of additional settings to change, but it's 6:00 p.m. on a Friday and he's ready for the weekend. He decides to come in early Monday to finish up the configuration. So for the entire weekend, the VPN you're counting on to provide secure access to your network is on the Internet with the password "admin." The best way to address this type of vulnerability is through stringent system configuration procedures and strong awareness training for your support staff or contractors. Disciplinary action when an installer fails to follow the instructions is remarkably effective at getting the message across.
The second common issue with hardware VPNs is a device that is installed in the default configuration. Very few network devices will come out of the box in a fully secure configuration. For example, important configuration setting we discussed was disabling split-tunneling. A default VPN configuration might not disable that setting without modifying the configuration. If you are completing your first install, it's very tempting to just change enough of the configuration to get the VPN up and running and stay away from any unfamiliar settings.
A related issue occurs when an inexperienced installer modifies the configuration without understanding the impact of the changes. For example, an installer with a limited understanding of encryption protocols might decide that using the DES algorithm for VPN encryption would be "good enough" and would improve performance over a higher encryption algorithm like 3DES. The installer probably read somewhere that the longer the key length used for encryption, the higher the impact on performance. This is often true, but longer key lengths usually mean more secure communications. Installer-induced security threats are some of the hardest to track down. Since they were caused by someone with a limited understanding of what he or she is doing, the installer's ability to help you track down the issues is equally limited.
To mitigate the risk of these issues, make sure that you train your installer (or yourself) before installing the VPN. If you do not have the time or justification for training on the product, then engage a vendor or systems integrator to either assist with the install, or even complete it for you. Once the installation goes online, it pays to have an expert perform a vulnerability or penetration test against your VPN. It never hurts to have an expert check your work.
A software VPN solution can suffer from the following vulnerabilities:
Operating system vulnerabilities
Operating system mis-configuration
Application conflicts
Stability
Viruses and malware
While software VPN solutions are not typical in corporate environments, they are not uncommon in smaller organizations, academic environments, and other areas where a hardware VPN did not meet the business requirements. The main threats to software VPN solutions arise in the operating system. Operating systems like UNIX or Microsoft Windows consist of highly complex coding. They are designed to support a number of business-related tasks, and are more highly complex than the operating systems found on hardware-based VPNs. As a result, the software-related threats can also be much more complex.
Operating systems contain millions of lines of software code, and as with anything written by people, they always contain mistakes. Those mistakes are what attackers seek to exploit when attacking an operating system. Exploits may include buffer overflows, privilege escalation, or any number of other issues. As a result, if you run your VPN on a general-purpose operating system, your VPN becomes susceptible to the same software vulnerabilities as your operating system. In addition, software VPNs have many more possible operating system configuration errors than hardware VPNs.
Some organizations run VPN software on a server that supports multiple applications. For example, the VPN server might also be a SQL server, a Web server, or a file server. If this is the case in your environment, be aware of potential vulnerabilities created by application conflicts. This could be a matter of two applications that contend for resources on the servers causing issues, but it could also be the chance that one of the applications opens a new vulnerability in the VPN software. Think about a VPN server that is also a Web server. If the Web server is configured incorrectly, you could expose VPN configuration files to an attacker through the Web server interface. In that event, you could configure your VPN server securely just to have an attacker pull a copy of your configuration files out of a Web directory, bypassing your security.
Another potential threat associated with software VPNs is stability. Many information security professionals are reluctant to run software VPNs due to the challenges of the operating system crashing and taking the VPN with it. Many security professionals wouldn't ever want to run a VPN that could be taken out by a "Blue Screen of Death"—the nickname for the Microsoft server crash screen.
Finally, operating systems are vulnerable to viruses and other forms of malware. These would include Trojan horses, rootkits, or any of the other destructive malware currently active on the Internet. Any of these infections could compromise the security of your VPN, as well as your internal network.
If you are planning to run a software VPN, be sure to run it on a dedicated server, double-check both the operating system configuration, as well as the VPN configuration, and keep the operating system fully patched and up-to-date. When your VPN is fully configured, run a vulnerability management tool against it, or have a professional come in and conduct a penetration test. Moreover, be sure to install and maintain current antivirus and anti-malware software on the server. It's a good idea to install a firewall application and an intrusion detection/prevention application to ensure that your VPN remains secure.
Vulnerabilities common to both hardware and software VPN implementations include:
Denial of service attack
Missing patches
Backdoor attack
Unpublished vulnerability in the code
Weak client security
Weak authentication
In a Denial of Service (DoS) attack, the attacker is trying to crash or overload the VPN, essentially, to deny access to the VPN service. Attackers use specially crafted packets designed to crash the VPN, or more likely, direct a flood of traffic at the VPN in an attempt to overload it. This is not a very common attack because of the large amounts of traffic required to overload most companies' network infrastructures. Generally, you will not see a VPN targeted with a DoS, as attacks against VPNs are typically designed to allow the attacker access to the internal network. DoS is more common is against popular Web sites like Twitter or Facebook, where there is significant publicity, or against online merchants, who are subject to blackmail. When your Web site is a significant source of revenue, a DoS attack can be very expensive.
Any hardware or software platform that can run VPN software is vulnerable. That's the nature of any computer technology. When these vulnerabilities are discovered, the vendor will typically develop a patch or an update to address the issue. If you do not keep your VPN current, you leave your network open to these issues, and attackers will try to exploit known vulnerabilities with your VPN.
A backdoor account attack is pretty rare, but can happen in some instances. An example of the traditional backdoor attack was featured in the movie War Games, where the system developer left a user account and password on a secure system in case he needed to get back in. This account was exploited by an attacker (in the movie, a kid just looking to play games)—nearly causing the end of the world. Needless to say, the issues in your environment will not be quite as dramatic, but they are still of concern. Code running on VPNs and operating systems is closely scrutinized, so system developers are less likely to be a threat, but what about a system administrator who thinks he's about to be fired? Or a vendor who comes in to support your VPN and creates an account for support that he or she forgets to delete before leaving? The best way to mitigate this type of attack is through scheduled auditing of all accounts on your VPN, as well as strong, documented procedures for how and when accounts are created and deleted. This particularly applies to accounts with elevated privileges or on systems accessible from the Internet.
One of the trickiest (and fortunately rarest) security threats is an unpublished vulnerability in the VPN code. Researchers or potential attackers can discover an unpublished vulnerability. If it's unpublished, it means the vendor is not yet aware of it, and thus has not yet developed a patch or an update. These are probably the most difficult threats you will face because there isn't a lot you can do beyond following security best practices, creating a layered security environment, and monitoring the behavior of your environment for anomalies. Should you encounter this issue, be sure to follow your incident response process and work with the vendor to identify the issue and create a patch.
Another vulnerability is not directly on the VPN, but is vulnerability in the devices connecting to the VPN. VPNs offer significant security advantages, but if the client at the other end of the connection is not secure, then your network is at risk. To mitigate this risk, have a standard client configuration, which includes antivirus, anti-malware, firewall, and maybe even intrusion-detection software. Also make sure that the only clients connecting to the VPN are company-owned. Permitting personal assets to connect to your network opens a number of additional issues, since you are not able to supervise the configuration of those systems. All it takes is one employee whose daughter clicks on the video link that her friend sent her (generally with a comment like "check out this video I took of you") and you could end up with a virus on your network when Dad connects to the VPN using the same system.
A final vulnerability to consider is the challenge of weak authentication. Your VPN is really only as secure as your authentication mechanism. If you are authenticating with user ID and password, you run the risk of someone guessing or stealing those credentials and accessing your network without permission. To mitigate this risk, rely on either token-based or biometric authentication methods instead of—or in addition to—a user ID and password. If you must use user ID and password for authentication, be sure to coach users in the use of strong passwords.
A familiarity with the various threats, attacks, and mitigations is critical to the long-term support of your VPN and your total network. Be aware that no list of threats and attacks can be all-inclusive, because the attackers are constantly contriving for new methods for compromising your network. In the absence of specific threats and attacks, rely on good security practices to keep things safe.
When looking at VPN solutions, decide if you want to include the option to leverage open-source VPNs. If so, be aware of some of the tradeoffs you will encounter when leveraging an open-source VPN product.
A commercial solution offers the following benefits:
Ease of installation and management
Available management tools
Access to vendor support
Available hardware maintenance
The benefits of an open-source solution include the following:
Low cost
Flexibility
Ability to run on existing hardware
Access to Internet-based support
Both commercial and open-source solutions pose some challenges. Commercial solutions are typically easier to implement, but that ease of installation comes at a cost. Not only are commercial solutions more expensive than open-source solutions, but also they are typically less flexible. Open-source solutions like OpenVPN (www.openvpn.net) offer significant flexibility, but generally require significantly higher skill in installation and support of the product. You rarely have access to vendor support, as open-source solutions usually rely on the knowledge of the user and the development community. When you have an issue, you can normally post it on a discussion board, and the community will assist you in resolution of your issue.
While weighing the pros and cons of open-source VPN solutions, take into account a couple of other factors. First, many organizations have policies about the use of open-source software. These policies derive from the company's tolerance for risk, the open-source licensing agreements, and intellectual property implications of open source. If your organization embraces open source, an open-source VPN is probably worth considering.
The best VPN application still comes down to identifying your requirements and finding the best solution for your organization. If you're on a low budget or have access to solid technical resources, an open-source solution could be the best choice for your needs.
Much of the information in this chapter has dealt with VPNs deployed in support of an enterprise or at least a moderate-to-large network. Another class of VPN applications—the personal or individual VPN—is sometimes referred to as the small-office or home-office VPN solution. Many home routers will include support for VPN connections, and open-source VPNs are also very popular in this space. Shrew Soft (www.shrew.net) offers an open-source VPN client that will connect to many of the standards-based VPN gateways like OpenSWAN (www.openswan.org). The value of these personal VPNs is twofold. First, implementing a personal VPN provides you secure access to your home network. Even better, implementing a personal VPN provides you with some valuable experience with VPNs that you can then transfer to your organization's enterprise VPN.
A key concept to understand about VPN technologies is the difference between anonymity and privacy. Anonymity is the ability for a network or system user to remain unknown. Some tools that support anonymous access include Tor (www.torproject.org), an open software and network to anonymously surf the Web. A hardware solution that leverages the Tor network for anonymity is JanusVM (www.janusvm.com). The problem with solutions for anonymity is that they don't always protect your privacy. In many cases, the traffic carried anonymously by these applications is unencrypted, which means an attacker can read it with access to the right part of the network. If you are passing user IDs and passwords, credit card numbers, or other information that you would like to keep private, these are not the correct solutions for you.
Privacy, on the other hand, is keeping information about a network or system user from being disclosed to unauthorized people. If you want to protect your information, a VPN connection does an excellent job of this by encrypting the data that it carries. Leverage VPNs whenever you are connected to an untrustworthy network and want to send sensitive information. Wireless networks are a particularly ripe environment for attackers trying to get private information from a public network. VPNs do not offer any anonymity, however, as you are always able to track the endpoints of a VPN connection—that information is needed to maintain the VPN connection.
One of the design decisions you made when selecting your VPN was whether you needed a highly available solution. Once your users expect to access the network from a hotel, a customer location, or Starbucks, or from home when they have a sick child, you will find they have little tolerance for outages. A VPN down means none of your remote workers can do much work, and in some organizations that can mean a majority of the company could be off the network until the VPN is back up and running. A highly available solution makes a lot of sense.
The most common method for implementing a highly available VPN is pretty simple. You buy two VPN hardware units (or implement two open-source VPNs) and then configure them as a highly available pair using the vendor's high-availability mechanisms. Cisco offers the Hot Standby Router Protocol (HSRP) for example, which allows configuration of a pair of Cisco VPNs so that in the event that the primary VPN fails, the backup takes over seamlessly. If configured correctly, end users don't even notice the cutover. A more industry-standard protocol that offers similar functionality is the Virtual Router Redundancy Protocol (VRRP). You also have the option to use a third-party solution. Many of today's load balancers offer the ability to load-balance VPNs. When one VPN fails, the load balancer automatically directs all traffic to the remaining gateway.
In addition to ensuring your VPN is highly available, also ensure that your Internet circuits have similar redundancy. You don't want to end up with your VPN up, and your one Internet connection down. The net result is still unhappy users who cannot access the network. In the event of circuit outages, the user will typically need to reconnect to the VPN. This is still better than not being able to connect at all.
When you are considering a highly available VPN solution, be sure to consider not only the acquisition costs, but also the ongoing maintenance costs over the following three to five years. It's important to capture the full cost of the solution, rather than just the purchase price.
Now that your VPN is up and running, train your users on how to use the VPN. One of the most common challenges with IT infrastructure deployments, especially with security infrastructure like a VPN, is for the IT team to assume that, since they understand how the solution works, their end users understand it as well. That's almost always a bad assumption. It can turn a successful rollout into an unsuccessful one.
To develop good user training, start by setting appropriate training goals. One of the first mistakes security practitioners make when developing training is jumping past any planning and starting with taking screen shots, typing up documentation, and scheduling meetings. However, much like a successful VPN deployment, the first part of successful training is planning. Determine the following before designing your user training:
Who is your target audience for the training? Before you start writing your training, understand who will be learning.
What is the technical awareness level of your audience? Are you training tech-savvy IT professionals, or salespeople who just want to turn on their PCs and start working?
Where is your audience? Is your audience in one central location, or spread out regionally—or even nationally? This will impact the choice of media you use to train users.
What level of training are you trying to deliver? Will users need to install the client software? Do you want to include basic troubleshooting in the training? Are you trying to sell features or do you just want to train them on how to login? Should you include additional security issues in this training?
Once you gather the appropriate information, determine the best mechanism for delivering the training. You may distribute some written instructions, have a conference call, or even a Web conference. For high-profile users, or users who require significant support, hold classroom training. If you decide to go with live training, definitely plan to do additional information security training. After all, you have their attention for the period of the training—maximize the benefit not only to your users, but also to your company. Remember that well-trained employees tend to be the most secure computer network users.
Other things to keep in mind as you do user training: Make sure your training plan includes how you will train new employees. Will your training post to an intranet Web site, or load onto a DVD that new hires can watch? Will you offer new-hire training at a regular interval to ensure everyone understands how to use the VPN?
Finally, don't forget your support staff. If a user with VPN issues is supposed to call the Help Desk, make sure the Help Desk knows how to help.
To successfully troubleshoot and resolve VPN issues, be organized, methodical, and prepared. Like anything else on your network, your VPN at some point will experience an issue. The preparations you undertake during installation and maintenance will prove to be critical components of your troubleshooting process.
Before you start troubleshooting your VPN issue, have access to the following information:
A network diagram showing the placement of the VPN and other key network components like firewalls, routers, and switches.
A copy of the current VPN configuration.
Any error, system, or alert logs.
Operations guide.
Maintenance logs and change management records.
Now that you have your basic information, you can start troubleshooting. There's no one way to troubleshoot an issue, particularly a VPN issue. What you can do is determine what works best for you, and stick with that process. Some people like to start at the far end and work back to the local VPN server. Others will start at the network layer and work their way up to the application. The actual process is not as critical as having an established process and sticking with it. One way to tackle this process is the following:
Identify the symptoms—Frequently when dealing with a user-reported issue, the reported item will bear little resemblance to the actual problem. Users tend to generalize with statements like "No one can get on the VPN" or "The intranet is down from the VPN." You need more specifics before you start correcting an issue. Ideally you will receive an automated alert from your monitoring system, which generally permits you to track down issues much more quickly than a Help Desk ticket.
Determine the scope of the problem—Know whether your problem is bigger than a breadbox or a 747. Do you have one user who cannot connect, one hundred users, or the entire company? Not only will this help you get a handle on the urgency of the issue, but it also gives you valuable clues to what the problem might be. If it's one user, the odds are pretty good that it's a client issue, or possibly a network issue on the user's end, and the Help Desk can probably assist with the issue. If a large group but not everyone is affected, you can look for commonalities. Do all the users belong to the same VPN group? Do they all connect from the same part of the country (could be an ISP issue)? If you have multiple VPNs, are the problems all on one VPN?
Look for changes—Before you assume something is broken, see if anything has changed. If the issue is with a single user, did he or she install a new application like Skype or Tor that could be interfering with the VPN? If the VPN is unreachable from the Internet, was someone working on your Internet connection? Did you do a code upgrade over the weekend? The importance of formal change management is critical to successfully maintaining a production computing environment. When you are troubleshooting, determine what has changed. Be aware that sometimes the toughest part of chasing down change-related issues in a complex environment is figuring out which of the 20 or 30 changes performed during a weekend change window is causing your problem.
Call the vendor—It's never a bad idea to call the vendor and see if they have seen your issue before. If you don't have phone support with the vendor, visit their Web site and check their knowledge base. The Internet is an invaluable tool for helping with troubleshooting.
Try the most likely solution—As the resident expert, once you have gathered all the information and reviewed the likely issues, try a fix. Record these fixes not only in your Operations Guide, but also in your change control process.
Test it—You made a change; test to see if it worked. If not, back out the change you made and repeat the previous step with the next most likely fix. Repeat the process until the problem is solved. Do not keep trying fix after fix without backing out previous fixes; you could end up making so many changes that you won't be able to easily get back to a stable configuration.
Check to see if you broke anything else—This is a critical step. Changes to the environment—even if you are trying to fix something—can have unpredictable impacts. The last thing you want is to assume the problem is solved, just to get a call later saying no one can get to the Internet.
Document, document, document—This is probably the most important part of the process. If you don't write processes and procedures down, it's as if you didn't even do them. When the next expert comes along to troubleshoot, and your changes aren't documented, he or she has to start with incorrect information or guesswork. And if you encounter the same problem twelve months later, you'll be glad you can refer to your previous process to speed up the second recovery. Create be a section in your Operations Guide just for this kind of documentation.
Now that you have a general troubleshooting process, consider some other things when troubleshooting a situation:
Don't panic—During a major outage, people tend to panic. They will start sending e-mails to large distribution lists, sending alerts, escalating issues, and doing a variety of other things that are not particularly helpful to you while you're troubleshooting an issue. Keep your cool, work the problem at hand, and keep management informed of the progress you make.
Don't over commit or make promises you can't keep—If you don't know what the issue is, don't tell your manager that the network will be back up in an hour.
Focus on the problem at hand—Getting sidetracked when troubleshooting a complex issue is easy. Be sure that the problem at hand is the one you are working to address. If you identify other potential issues unrelated to the current outage, document them and handle them under your change control process. But don't go off on a tangent and delay addressing the immediate issue.
You can do a couple of quick and easy tests if you are having a major VPN outage and you just want to be sure that your VPN is still on the network. Generally your VPN will have two interfaces. One will be accessible from the Internet, and the other will be the connection to your internal network (possibly through a firewall). In the event of a major outage, start by verifying that both of those ports are functioning.
Note
When you are troubleshooting a VPN issue, management will often require frequent status updates. The worst place for you to be when the VPN is down is spending all your time on conference calls fielding questions like "When will it be fixed?" Management needs to be educated to the concept that things won't be fixed until you get off the phone and back to working the problem.
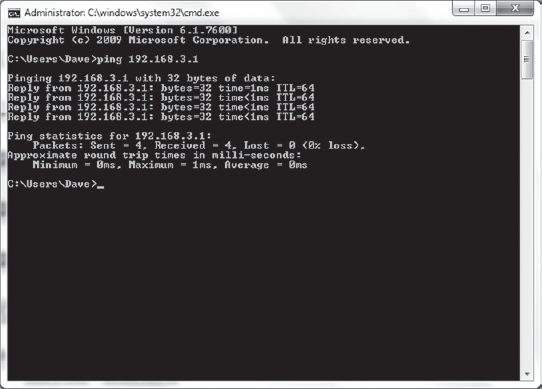
To verify the internal port is available, you can use the ping command from the Windows command prompt, or from a UNIX command line. See Figure 11-4 for a sample successful PING response.

Figure 11-5. Using Internet-based Traceroute tools to determine if your VPN is accessible from the Internet.
Once you've validated the internal port, also validate the external port. This is frequently a challenge because in most organizations a direct connection to the outside of the network is not readily available. In some larger organizations you may have a DSL Internet connection dedicated for testing, but if you don't have that type of access, a number of Internet sites will let you run network diagnostics from their Web sites. See Figure 11.5 for a sample Internet Traceroute command from www.network-tools.com If you do an Internet search on "Network Tools," you can find a number of sites that offer a similar capability.
You now have the tools to create your own troubleshooting process for your VPN, using some or all of the steps and tips discussed. You just need to determine what works best in your environment. Be methodical, don't panic, keep focused on the issue, and you will be very successful in quickly addressing VPN issues in your environment.
VPN management is a complex activity that requires attention to detail and good documentation. A variety of best practices may assist you in your VPN deployment and ongoing support. Selecting and deploying a VPN solution that meets your business requirements is essential. This includes deciding between open-source and commercial VPN solutions when selecting your product. Understanding the threats, attacks, and mitigations, and ensuring your VPN is available are key components of success. In addition, understand the difference between privacy and anonymity, know the difference between personal/individual and enterprise/network solutions and, finally, be able to train your users well. Once you have mastered all these facets of successful VPN rollout and support, you'll be ready to move on to other security topics.
Which response contains the three most common VPN deployment architectures?
Bypass, encrypted, OpenVPN
DMZ, OpenVPN, internally connected
DMZ, Encrypted, OpenVPN
Encrypted, OpenVPN, internally connected
Bypass, DMZ, internally connected
All of the following are considered VPN management best practices except:
If one is good, two is better
Patch regularly
Permit split tunneling
Do not allow employee-owned computers to connect
Review usage
Three of the threats common to both software and hardware VPNs include _______, _______, and _______.
The two different types of VPN commonly used for remote access VPN are _______ and _______.
Pick two advantages of using an open-source VPN solution instead of a commercial solution.
Low cost
Good vendor support
Minimize installation and configuration time
Use existing hardware
Easier to troubleshoot.
The ability for a network or system user to remain unknown to adversaries is _______.
Which of the following are benefits of using a commercial VPN instead of an open-source VPN solution? (Multiple answers may be correct.)
More costly
Less flexible
Product support
Requires higher skill set to deploy and support.
Dedicated hardware
A document that details the requirements for using the VPN is called a _______.
Which of the following are vulnerabilities common to both software and hardware VPN solutions? (Multiple answers may be correct.)
Default password
Unpublished vulnerability in the code
Weak client security
Weak authentication
Blue Screen of Death
Which of the following are components of a VPN Policy? (Multiple answers may be correct.)
Introduction
Scope
VPN Configuration Settings
Definitions
Backup Strategy
Keeping information about a network or system user from being disclosed to unauthorized people is known as _______.
Recognizing that vulnerabilities will be found with both hardware and software VPNs, be sure to _______ frequently.
Which of the following are not VPN best practices? (Multiple answers may be correct.)
Backup your configuration
Pick the solution that gets the best reviews
Don't permit split tunneling
Use vulnerability management
Secure your endpoints
The best authentication method for client VPNs is _______.
When protecting the availability of your VPN, it is a good practice to have _______ VPN gateways in your environment.
Which of the following are protocols that can be used for high availability with VPNs? (Multiple answers may be correct.)
IPSec
3DES
HSRP
VRRP
SSL
If you want to verify that the VPN is on the network, what is the simplest tool you can use?
Snort
Ping
Traceroute
VPN Monitor
Syslog
When troubleshooting a VPN issue, which of the following are valid troubleshooting steps? (multiple answers may be correct)
Don't panic
Gather the symptoms
Run a vulnerability scan
Review changes to the environment
Upgrade the VPN software
Your VPN policy should address which of the following topics? (multiple answers may be correct)
Define authentication methods permitted.
Define the VPN platform
Define required encryption levels for VPN connections
Define the troubleshooting process
Define how to respond to incidents
In addition to redundant VPNs, also make sure to have redundant _______ for your VPN to be truly available.