We recommend treating all iOS devices the same. This means, do not try to handle jailbroken devices one manner and non-jailbroken in another manner. Essentially, try everything possible to gain access to that device. First, try a physical acquisition. If this method fails, attempt a file system acquisition, followed by a logical acquisition. If the device is locked and the passcode is required to acquire the device, attempt to crack it. The state of the iOS device should not keep you from trying your hardest to get a full physical image. For devices that are truly jailbroken, you will see how much easier this makes your life when attempting to acquire data.
There are several methods on both Mac and Windows platforms that support the acquisition of iOS devices. Earlier, we discussed the physical and file system section of this chapter; UFED Physical Analyzer offers additional support for jailbroken iOS devices. If the device is jailbroken, a physical acquisition is possible. The exception to this is the 64-bit iPhone 6, 6 Plus, 6S, and 6S Plus. Currently, Elcomsoft is the only forensic tool offering support for physical acquisition of these newer devices. However, they must be jailbroken.
Best practices recommend obtaining a forensic acquisition prior to connecting the iOS device to terminal on a Mac and attempting to access the data directly. In order to determine if the device has been jailbroken, the examiner has a few options:
- Attach the iOS device to your forensic kit and perform an acquisition. If it's a newer iOS device and physical acquisition is supported, it's likely the device is jailbroken. Caution: The reported state of the device is not always correct!
- Examine the fstab file to determine if the system partition is read only (ro) or read/write (rw). If the device is jailbroken, it can be accessed via a Mac using terminal to SSH into the device and mount the file system using iFuse or similar methods. Once the device is connected, we can navigate to private | etc | fstab. Examine the fstab to determine if
/dev/disk0s1s1is ro or rw. If the partition is rw, the device is jailbroken and is likely running a version prior to iOS 7. This file is no longer updated from ro to rw on newer iOS versions. We believe the file stopped being updated with a version of iOS 7. - Look for traces of jailbroken applications and startup screens as described in Chapter 2, Understanding the Internals of iOS Devices.
Regardless of the method used to identify a jailbreak, it is recommended that the examiner use more than one way to identify the state of the iOS device. Why, you may ask? Take a look at the following screenshot: we can see the Device Summary provided by UFED Physical Analyzer after a file system acquisition:

When examining the fstab of the same iPhone, we get the results shown in the following screenshot, which would lead the examiner to believe that this device is not jailbroken.

When a discrepancy like this occurs, it is recommended that you first identify the iOS version running on the device as explained in Chapter 2 , Understanding the Internals of iOS Devices. Once identified, if the iOS version is iOS 7+, the fstab cannot be relied upon as a trusted source of a jailbreak state. Thus, the examiner needs to try more than one tool to see what options are offered during acquisition (for example, physical acquisition success of an unsupported device, method 3 offered for file system acquisition, and so on.)
There are several methods available on both Mac and Windows computers for acquiring data from jailbroken devices. Free Windows tools, such as Magnet CE, will create image files of jailbroken devices. When a jailbroken device is connected, the tool will provide file system, hence the examiner should realize they are dealing with a jailbroken iOS device.
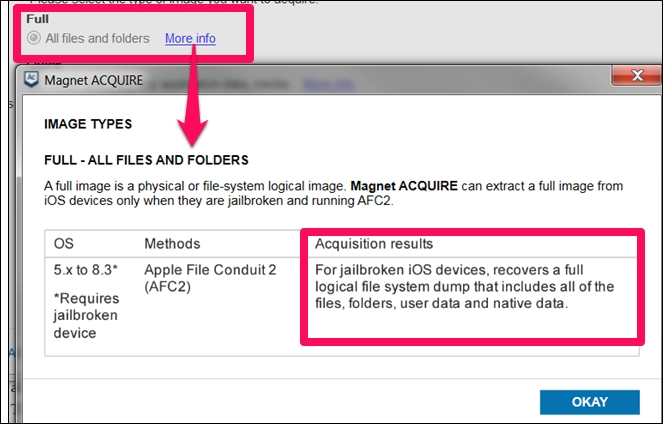
As shown in the following screenshot, Full is grayed out because the attached iOS device is not jailbroken. When the examiner selects More info this is explained. If this device were jailbroken, the option would be selectable and the acquisition would ensue.
On a Mac, a user can SSH into the jailbroken iOS device and acquire/copy data from the device onto external media for examination. This is the fastest way to triage an iOS device, as the access is immediately granted. The following screenshot shows the iPhone mounted with access to applications stored on the device:

Examining a jailbroken iPhone using ifuse to mount and view the data
While this is the fastest way to triage a jailbroken device, it's not the best method for obtaining a forensically sound image, as the device is mounted and data can be changed or modified. Best practices recommend creating a forensic image prior to interacting directly with the iOS device when possible.
For jailbroken iPhones, refer to the acquisition support in the following table. At the time of writing, it is still legal to jailbreak iPads, and they are not included in the preceding table as we are not encouraging illegal activity to gain access to user data on iOS devices.

