Chapter 5
802.11 Control Frames
In this chapter, you will learn about the following:
- Understanding Control Frames
- Carrier Sense
- Virtual Carrier Sense
- Physical Carrier Sense
- RTS/CTS Frames
- CTS-to-self
- Protection Mechanism
- Preventing Collisions
- ERP Information Element
- Triggering Protection Mechanism
- Acknowledgement Frame
- Block Acknowledgement Request
- Block Acknowledgement
- PS-Poll
- Control Wrapper
- Contention Free
In this chapter, we will take a detailed look at the different control frames and discuss the purpose of each of the frames. Control frames are the traffic cops of the 802.11 network, assisting with the delivery of data and management frames.
In addition to defining frames that are used to transport data from one station to another, the 802.11 standard defines frames for managing the wireless communications and assisting with the delivery of data frames. To provide dependable communications, the 802.11 standard defines three different frame types and an assortment of frame subtypes. The three frame types are control, data, and management. Each of these frame types is subdivided into multiple frame subtypes, with each subtype providing a different function and having a different frame structure.
Control frames assist with the delivery of data and management frames. Unlike management and data frames, control frames do not have a frame body. In addition to the PHY and preamble, control frames contain only a layer 2 header and trailer. Control frames perform many different functions; therefore, they can be transmitted at different data rates. In a mixed PHY environment, control frames are typically transmitted at one of the defined basic rates. This helps assure that all stations can receive the control frames. Section 9.6 Multirate Support of the 802.11-2007 standard defines a set of transmission rules that must be followed by all stations.
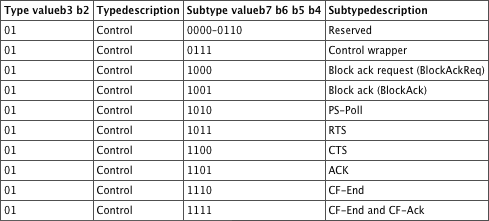
Every 802.11 frame has a Frame Control field (Figure 5-1), which specifies information about the frame. The Type and Subtype subfields of the Frame Control field are used to identify the function of the frame. The Type field is 2 bits long, and the Subtype field is 4 bits long, and they are used to identify the function of the frame. As shown in Figure 5-1, many of the values of the other fields of a control frame are fixed, such as the type value of 01, which identifies the frame as a control frame. Table 5-1 displays the Type and Subtype values for control frames, along with a subtype description of each frame.
Figure 5-1: Control frame: Frame Control fields

Table 5-1: Control frames: valid Type and Subtype combinations
The first step that an 802.11 CSMA/CA device takes to begin transmitting is to perform a carrier sense. This is a check to see whether the medium is busy. Think of it like listening for a busy signal when you call someone on the phone. A carrier sense is performed in two ways: virtual carrier sense and physical carrier sense. Both methods will be covered in greater detail in Chapter 7; however, a brief overview of virtual carrier sense is needed prior to learning details about control frames.
Virtual Carrier Sense
Virtual carrier sense uses a timer mechanism known as the network allocation vector (NAV). The NAV timer maintains a prediction of future traffic on the medium, based on the Duration value information seen in a previous frame transmission. When an 802.11 radio is not transmitting, it is listening. As depicted in Figure 5-2, when the listening radio hears a frame transmission from another station, it looks at the header of the frame and determines whether the Duration/ID field contains a Duration value or an ID value. If the transmitted frame is a PS-Poll frame (PS-Poll frames are discussed later in this chapter), then the Duration/ID field contains the association identifier (AID) of the station that transmitted the frame. In all other frames, the Duration/ID field contains a Duration value. If the field does contain a Duration value, the listening station will set its NAV timer to this value. The listening station will then use the NAV as a countdown timer, knowing that the RF medium should be busy until the NAV countdown reaches 0.
Figure 5-2: Virtual carrier sense
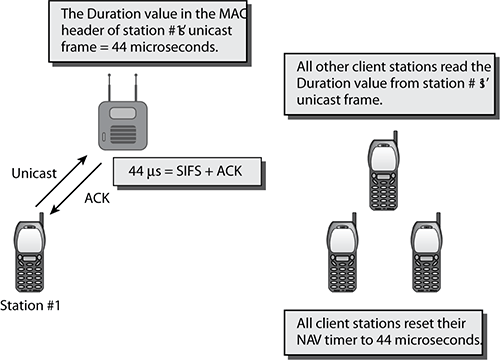
This process essentially allows the transmitting 802.11 radio to notify the other stations that the medium will be busy for a period of time (Duration/ID value). The stations that are not transmitting listen and hear the Duration/ID, set a countdown timer (NAV), and wait until their timer hits 0 before they can contend for the medium and eventually transmit on the medium. A station cannot contend for the medium until its NAV timer is 0, nor can a station transmit on the medium if the NAV timer is set to a nonzero value.
Physical Carrier Sense
The virtual carrier sense is one method of keeping other stations from transmitting while another radio has control of the RF medium. However, it is possible that a station did not hear the other radio transmitting so was unable to read the Duration/ID field and set its NAV timer. There could be numerous reasons why, but that is irrelevant at the moment. CSMA/CA utilizes another line of defense to ensure that a station does not transmit while another is already transmitting: the 802.11 standard defines a physical carrier sense.
Physical carrier sensing is performed constantly by all stations that are not transmitting or receiving. When a station performs a physical carrier sense, it is actually listening to the channel to see whether any other transmitters are taking up the channel.
Physical carrier sense has two purposes. The first purpose is to determine whether a frame transmission is inbound for a station to receive. If the medium is busy, the radio will attempt to synchronize with the transmission. The second purpose is to determine whether the medium is busy before transmitting. This is known as the clear channel assessment (CCA). The CCA involves listening for 802.11 RF transmissions at the Physical layer. The medium must be clear before a station can transmit.
It is important to understand that both virtual carrier sense and the physical carrier sense are always happening at the same time. Virtual carrier sense is a layer 2 line of defense, while physical carrier sense is a layer 1 line of defense. If one line of defense fails, ideally the other will prevent collisions from occurring.
Request to send (RTS) and clear to send (CTS) frames are used to enhance the virtual carrier sense process. For a client station to participate in a basic service set, it must be able to communicate with the access point. This is straightforward and logical; however, it is possible for the client station to be able to communicate with the access point but not be able to hear or be heard by any of the other client stations. This can be a problem because a station performs collision avoidance by setting its NAV when it hears another station transmitting (virtual carrier sense) and by listening for RF (physical carrier sense). If a station cannot hear the other stations or cannot be heard by the other stations, there is a greater likelihood that a collision can occur.
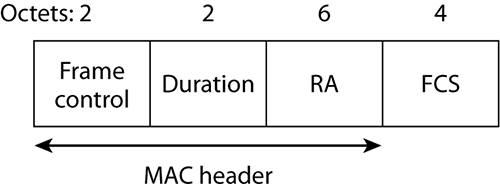
Request to send/clear to send (RTS/CTS) is a mechanism that performs a NAV distribution and helps prevent collisions from occurring. The NAV distribution reserves the medium prior to the transmission of the data frame. When RTS/CTS is enabled on a station, every time the station wants to transmit a frame, it must perform an RTS/CTS exchange prior to the normal data transmission. When the transmitting station begins to transmit data, it first sends a 20-octet RTS control frame (Figure 5-3). The Duration value of the RTS frame includes the time needed for the subsequent frames in the transmit operation to be transmitted. This value is in microseconds. All listening stations will set their NAV timers to this value and cannot contend for the medium or transmit data until their NAV counts down to 0. After the RTS frame is transmitted, the receiving station responds by sending a 14-octet CTS control frame (Figure 5-4). The Duration value of the CTS frame includes the time needed for the subsequent frames in the transmit operation to be transmitted.
Figure 5-3: RTS frame

Figure 5-4: CTS frame
When the RTS frame is created, the receiver address (RA) is the address of the intended receiver of the pending data or management frame. The transmitter address (TA) of the station is transmitting the RTS frame and pending data or management frame. When the CTS frame is created, the RA field is copied from the TA field of the RTS to which it is responding. Figure 5-5 displays the RTS/CTS duration periods and frames that are transmitted if the NAV reservation is being provided prior to the transmission of a single data frame.
Figure 5-6 depicts an RTS/CTS exchange between a client station and an access point, along with displaying how two nontransmitting stations may use these frames to reset their NAV.
The phrase RTS/CTS not only refers to two types of control frames but also to a method of performing NAV distribution. CTS-to-self is simply another method of performing NAV distribution that solely uses CTS control frames. CTS-to-self is used strictly as a protection mechanism for mixed-mode environments. When a station is using CTS-to-self, prior to transmitting a data frame, it performs a NAV distribution by sending a CTS frame. This CTS frame notifies all other stations that they must wait until the DATA and ACK have been transmitted, as shown in Figure 5-7. Any station that hears the CTS-to-self will set their NAV to the value provided. The CTS-to-self NAV distribution mechanism requires less network overhead than the RTS/CTS NAV distribution mechanism; however, it is also less robust against hidden nodes and collisions than RTS/CTS.
Figure 5-5: RTS/CTS Duration values
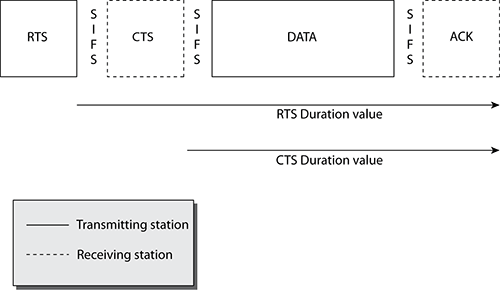
Figure 5-6: RTS/CTS frame exchange

Figure 5-7: CTS-to-self frame Duration values
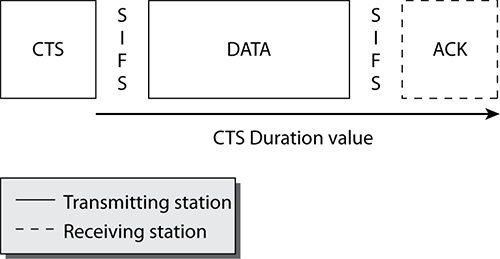
CTS-to-self is better suited for use by an access point. It is important that all stations hear the CTS to reserve the medium, and this is most likely to occur if it is being sent by an access point. If a client station were to use CTS-to-self as a protection mechanism, there is a chance that another client station on the opposite side of the BSS might be too far away from the CTS and would not realize the medium is busy. Even though this is true, from our experience, it appears that most use CTS-to-self on client stations to reserve the medium instead of RTS/CTS. CTS-to-self is used because of the decreased overhead when compared with RTS/CTS. Some vendors allow the user to select whether the client station uses RTS/CTS or CTS-to-self when in Protected mode.
The 802.11-2007 standard mandates support for both direct sequence spread spectrum (DSSS) and orthogonal frequency division multiplexing (OFDM) technologies for clause 19 ERP radios (802.11g). When clause 18 HR-DSSS (802.11b) client stations need to communicate in a basic service set with an ERP (802.11g) access point and ERP (802.11g) client stations, the 802.11g devices need to provide compatibility for the slower 802.11b devices. ERP access points must also be backward compatible with legacy clause 15 DSSS (802.11) client stations. This environment is often referred to as mixed-mode. Contrary to what some people believe, the 802.11g devices do not simply switch to 802.11b mode and communicate using 802.11b data rates. For 802.11g, 802.11b stations, and legacy 802.11 DSSS stations to coexist within the same BSS, the 802.11g devices enable what is referred to as the protection mechanism, also known as 802.11g Protected mode.
Many access point vendors offer three configuration modes for an 802.11g access point:
802.11b-Only Mode When an 802.11g AP is running in this operational mode, support for DSSS technology is solely enabled. Effectively, the access point has been configured to be an 802.11b access point. Legacy 802.11 DSSS clients, 802.11b HR-DSSS clients, and 802.11g clients using ERP-DSSS will all be able to communicate with the AP at data rates of 1 and 2 Mbps, and 802.11b HR-DSSS clients and 802.11g clients using ERP-DSSS will also be able to communicate with the AP at data rates of 5.5 and 11 Mbps. Aggregate throughput will be the same as achieved in an 802.11b network.
Protection mechanisms are used to provide coexistence between ERP (802.11g) radios and non-ERP legacy radios, such as DSSS (802.11) and HR-DSSS (802.11b). Higher-speed HT clause 20 radios have to deal with some of the same issues, providing backward compatibility with earlier 802.11a/b/g radios. In Chapter 10, you will learn about the four different 802.11n protection modes.
802.11g-Only Mode APs configured as g-only will communicate with only 802.11g client stations using ERP-OFDM technology at data rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mbps. Support for DSSS and HR-DSSS is disabled; therefore, 802.11b HR-DSSS clients and legacy 802.11 DSSS clients will not be able to associate with the access point. Ideally, aggregate throughput will be equivalent to what can be achieved in an 802.11a network. The aggregate throughput of an AP with a data rate of 54 Mbps might be about 19 to 20 Mbps; however, you will learn later in this chapter that this is often not the case. G-only wireless LANs are sometimes referred to as a pure G networks.
802.11b/g Mode This is the default operational mode of most 802.11g access points and is often called mixed-mode. Support for both DSSS and OFDM is enabled. Legacy 802.11 DSSS clients and 802.11b HR-DSSS clients will be able to communicate with the AP at data rates of 1, 2, 5.5, or 11 Mbps, depending upon the capability of the client. The ERP (802.11g) clients will communicate with the AP by using the ERP-OFDM data rates of 6, 9, 12, 18, 24, 36, 48, and 54 Mbps.
You need to understand that these vendor configurations are not part of the 802.11-2007 standard. Although most vendors do indeed support these configurations, the standard mandates support for 802.11b clause 18 devices and 802.11g clause 19 devices within the ERP basic service set.
How Can You Make Sure That 802.11g Networks Are Transmitting at 802.11g Speeds?
Even if all the wireless devices in your company support 802.11g, your WLAN will enable the protection mechanism if it sees even one 802.11b device. This 802.11b device could be a visitor to your company, someone driving past your building with an 802.11b wireless adapter enabled in their laptop, or a nearby business or home that also has a wireless network. If you want your network to always use the higher ERP-OFDM rates, you must configure the access points to support 802.11g clients only. Remember that if you do this, any 802.11b and legacy 802.11 DSSS devices will not be able to connect to your network, and these clients will not be recognized as 802.11 devices. Any signals that they transmit will be recognized as RF interference. So, even though you may think that you are ignoring these legacy devices, you are not; you are just identifying them differently.
Preventing Collisions
As mentioned earlier in this chapter, one of the ways of preventing collisions is for the stations to set a countdown timer known as the network allocation vector (NAV). This notification is known as NAV distribution. NAV distribution is done through the Duration/ID field that is part of the data frame. When a data frame is transmitted by a station, the Duration/ID field is used by the listening stations to set their NAV timers. Unfortunately, this is not inherently possible in a mixed-mode environment. If an 802.11g device were to transmit a data frame, 802.11b devices would not be able to interpret the data frame or the Duration/ID value because the 802.11b HR-DSSS devices are not capable of understanding 802.11g ERP-OFDM transmissions. The 802.11b devices would not set their NAV timers and could incorrectly believe that the medium is available. To prevent this from happening, the 802.11g ERP stations switch into what is known as Protected mode.
In a mixed-mode environment, when an 802.11g device wants to transmit data, it will first perform a NAV distribution by transmitting a request to send/clear to send (RTS/CTS) or a CTS-to-self using a data rate and modulation method that the 802.11b HR-DSSS stations can understand. The RTS/CTS or CTS-to-self will be heard and understood by all the 802.11b and 802.11g stations. The RTS/CTS or CTS-to-self will contain a Duration/ID value that will be used by all the listening stations to set their NAV timers. To put it simply, using a slow transmission that all stations can understand, the ERP (802.11g) device notifies all the stations to reset their NAV values. After the RTS/CTS or CTS-to-self has been used to reserve the medium, the 802.11g station can transmit a data frame by using OFDM modulation without worrying about collisions with 802.11b HR-DSSS or legacy 802.11 DSSS stations.
Within an ERP basic service set, the HR-DSSS (802.11b) and legacy 802.11 DSSS stations are known as non-ERP stations. The purpose of the protection mechanism is that ERP stations (802.11g) can coexist with non-ERP stations (802.11b and 802.11 legacy) within the same BSS. This allows the ERP stations to use the higher ERP-OFDM data rates to transmit and receive data yet still maintain backward compatibility with the older legacy non-ERP stations.
ERP Information Element
The ERP information element (IE) contains information about clause 15 (802.11) or clause 18 (802.11b) stations in the basic service set that are not capable of communicating using clause 19 (ERP-OFDM) data rates. It also identifies whether the AP should use protection mechanisms to optimize performance in the BSS and whether to use long or short preambles. The ERP information element, as shown in Figure 5-8, is 3 octets long; however, the length is flexible and can be expanded in the future. The element ID field contains the value 42, which identifies the IE as an ERP IE, and the length field contains the value 3. The fields r3 through r7 are reserved and set to 0 by default.
Figure 5-8: ERP information element
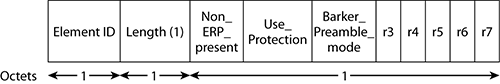
The remaining three fields are NonERP_Present, Use_Protection, and Barker_Preamble_Mode. When a non-ERP station is associated to the BSS, the Non-ERP_Present bit is set to 1. If one or more associated non-ERP stations are not capable of using short preambles, then the Barker_Preamble_Modebit is set to 1.
Included on the CD of this book is a white paper titled “Protection Ripple in ERP 802.11 WLANs” by Devin Akin. This white paper goes into much greater detail about the protection mechanism and is highly recommended extra reading for preparing for the CWAP exam.
Triggering Protection Mechanism
So, what exactly triggers the protection mechanism? When an ERP access point decides to enable the use of a protection mechanism, it needs to notify all the ERP (802.11g) stations in the BSS that protection is required. It accomplishes this by setting the NonERP_Present bit in the ERP information element in the beacon frame. Every time the access point transmits a beacon, any ERP station that hears the beacon will see the NonERP_Present bit and will know that Protected mode is required. There are an assortment of reasons why Protected mode may be enabled. The following are three scenarios that can trigger protection in an ERP basic service set:
- If a non-ERP STA associates with an ERP AP, the ERP AP will enable the NonERP_Present bit in its own beacons, enabling protection mechanisms in its BSS. In other words, an HR-DSSS (802.11b) client association will trigger protection.
- If an ERP AP hears a beacon from an AP where the supported data rates contain only 802.11b or 802.11 DSSS rates, it will enable the NonERP_Present bit in its own beacons, enabling protection mechanisms in its BSS. In simpler terms, if an 802.11g AP hears a beacon frame from an 802.11 or 802.11b access point or ad hoc client, the protection mechanism will be triggered.
- If an ERP AP hears a management frame (other than a probe request) where the supported rate includes only 802.11 or 802.11b rates, the NonERP_Present bit may be set to 1.
How Does 802.11b Affect 802.11g Throughput?
A common misconception is that 802.11g radios revert to 802.11b data rates when the protection mechanism is used. In reality, ERP (802.11g) radios still transmit data at the higher ERP-OFDM rates. However, when an HR-DSSS (802.11b) station causes an ERP (802.11g) BSS to enable the protection mechanism, a large amount of RTS/CTS or CTS-to-self overhead is added prior to every ERP-OFDM data transmission. The aggregate data throughput loss is caused by the extra overhead and not by using slower 802.11b rates. A data rate of 54 Mbps usually will provide about 18–20 Mbps of aggregate throughput when protection is not enabled. After protection is enabled, even though the ERP STA may be transmitting frames at ERP rates, the overhead of protection will likely reduce the aggregate data throughput to below 13 Mbps and possibly as low as 9 Mbps.
Since 802.11 stations are not able to transmit and receive at the same time, while a station is transmitting a frame, it is not able to determine whether the frame was received or whether there was a collision. Therefore, every time an 802.11 radio transmits a unicast frame, if the frame is received properly, the 802.11 radio that received the frame will reply with a 14-octet acknowledgement (ACK) frame. Figure 5-9 illustrates this frame exchange along with the NAV reservation set by the Duration value of the data frame. 802.11 is also capable of sending a single acknowledgement for multiple unicast frames. This is known as block acknowledgements and is discussed later in this chapter.
Figure 5-9: Data frame and acknowledgement
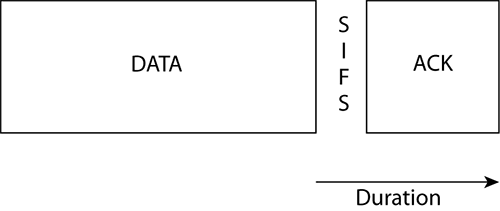
If the ACK is received, the original station knows that the frame transfer was successful. All unicast 802.11 frames must be acknowledged. Broadcast and multicast frames do not require an acknowledgement. If any portion of a unicast frame is corrupted, the cyclic redundancy check (CRC) will fail, and the receiving 802.11 radio will not send an ACK frame to the transmitting 802.11 radio. If an ACK frame is not received by the original transmitting radio, the unicast frame is not acknowledged and will have to be retransmitted.
This process does not specifically determine whether a collision occurs; in other words, there is no collision detection. However, if an ACK frame is not received by the original radio, there is collision assumption. Think of the ACK frame as a method of delivery verification. If no proof of delivery is provided, the original radio card assumes there was a delivery failure and retransmits the frame.
Another environment where delivery failure and retransmits may occur is when using long-distance bridges. When a frame is transmitted, because of the distance, a delay can occur in generating and receiving the ACK. By the time the ACK is received, the ACKtimeout of the transmitting station may have already expired, leading the transmitting station to believe that the frame was not received. In reality, it was just delayed. Many bridge and mesh vendors provide easy techniques to modify the ACKtimeout value to help prevent this problem from occurring.
Figure 5-10 displays the frame format for the ACK frame. The receiver address (RA) field is copied from the address 2 field of the frame that is being acknowledged.
Figure 5-10: ACK frame

The mortal enemy of WLAN performance is layer 2 retransmissions that occur at the MAC sublayer. As you have learned, all unicast 802.11 frames must be acknowledged. If a collision occurs or any portion of a unicast frame is corrupted, the cyclic redundancy check (CRC) will fail, and the receiving 802.11 radio will not return an ACK frame to the transmitting 802.11 radio. If an ACK frame is not received by the original transmitting radio, the unicast frame is not acknowledged and will have to be retransmitted.
Excessive layer 2 retransmissions adversely affect the WLAN in two ways:
- Layer 2 retransmissions increase overhead and therefore decrease throughput. Many different factors can affect throughput, including a WLAN environment with abundant layer 2 retransmissions.
- If application data has to be retransmitted at layer 2, the timely delivery of application traffic becomes delayed or inconsistent.
Applications such as VoIP depend on the timely and consistent delivery of the IP packet. Excessive layer 2 retransmissions usually result in latency and jitter problems for time-sensitive applications such as voice and video. When discussing VoIP, latency and jitter often get confused. Latency is the time it takes to deliver a VoIP packet from the source device to the destination device. A delay in the delivery (increased latency) of a VoIP packet because of layer 2 retransmissions can result in echo problems and can even cause the VoIP connection to be dropped. Jitter is a variation of latency. Jitter measures how much the latency of each packet varies from the average. If all packets travel at exactly the same speed through the network, jitter will be zero. A high variance in the latency (jitter) is the more common result of 802.11 layer 2 retransmissions. Jitter will result in choppy audio communications and reduced battery life for VoWiFi phones.
Most data applications in a Wi-Fi network can handle a layer 2 retransmission rate of up to 10 percent without any noticeable degradation in performance. However, time-sensitive applications such as VoIP require that higher-layer IP packet loss be no greater than 2 percent. Therefore, Voice over Wi-Fi (VoWiFi) networks need to limit layer 2 retransmissions to 5 percent or less to guarantee the timely and consistent delivery of VoIP packets. How can you measure layer 2 retransmissions?
A good 802.11 protocol analyzer can track layer 2 retry statistics for the entire WLAN. 802.11 protocol analyzers can also track retry statistics for each individual WLAN access point and client station. Unfortunately, layer 2 retransmissions are a result of many possible problems. Multipath, RF interference, and low SNR are problems that exist at layer 1 yet result in layer 2 retransmissions. Other causes of layer 2 retransmissions include hidden node, near/far, mismatched power settings, and adjacent cell interference, which are all usually symptoms of improper WLAN design.
The 802.11e amendment introduced a block acknowledgement (BA) mechanism that is now also defined by the 802.11-2007 standard. A Block ACK improves channel efficiency by aggregating several acknowledgements into one single acknowledgement frame. When a station intends to use the Block ACK mechanism to transmit QoS data, it first checks to see whether the peer station is capable of performing the Block ACK mechanism. As shown in Figure 5-11, an originator station sends a block of QoS data frames to a recipient station. During this transmission, a NAV reservation is performed so that the block of frames can be sent without risk of the other stations trying to transmit. Each of the frames has the Ack Policy subfield in the QoS Control field set to Block ACK. The originator requests acknowledgement of all the outstanding QoS data frames by sending a block acknowledgement request (BlockAckReq) frame. Figure 5-12 shows the BlockAckReq. The RA field is the address of the recipient station, and the TA field is the address of the station transmitting the frame. The Multi-TID and Compressed Bitmap subfields determine whether this is a basic Block ACK request, a compressed Block ACK request, or a multi-TID Block ACK request.
Instead of acknowledging each unicast frame independently, the block of QoS data frames are all acknowledged by a single Block ACK.
Figure 5-11: Immediate block acknowledgement process
Figure 5-12: BlockAckReq frame
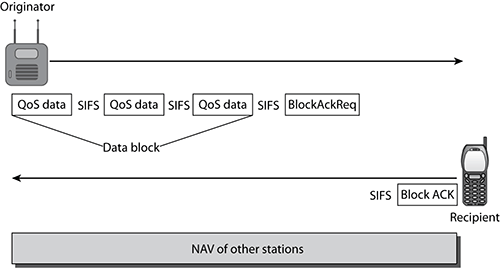

Figure 5-13 shows the BlockAck frame. It is used to acknowledge a block of QoS data frames, instead of acknowledging each unicast frame independently. A bitmap in the BlockAck frame is used to indicate the status of each of the received data frames. The RA field is the address of the station that requested the BlockAck frame. The TA field is the address of the station transmitting the BlockAck frame.
Figure 5-13: BlockAck frame

When a client station is set for Power Save mode, it will shut down some of the transceiver components for a period of time to conserve power. The wireless card basically takes a short nap. The station indicates that it is using Power Save mode by changing the value of the Power Management bit to 1. When the station sends a frame to the AP with the Power Management bit set to 1, the access point is informed that the client station is using power management, and the access point buffers all of that client’s 802.11 frames.
Any time a station associates to an access point, the station receives an association identifier (AID). The access point uses this AID to keep track of the stations that are associated and the members of the BSS. If the access point is buffering data for a station in Power Save mode, when the access point transmits its next beacon, the AID of the station will be seen in a field of the beacon frame known as the traffic indication map (TIM). The TIM field is a list of all stations that have undelivered data buffered on the access point waiting to be delivered. Every beacon will include the AID of the station until the data is delivered.
After the station notifies the access point that it is in Power Save mode, the station shuts down part of its transceiver to conserve energy. A station can be in one of two states, either awake or doze:
- During the awake state, the client station can receive frames and transmit frames.
- During the doze state, the client station cannot receive or transmit any frames and operates in a very low power state to conserve power.
Because beacons are transmitted at a consistent predetermined interval known as the target beacon transmission time (TBTT), all stations know when beacons will occur. The station will remain asleep for a short period of time and awaken in time to hear a beacon frame. The station does not have to awaken for every beacon. To conserve more power, the station can sleep for a longer period of time and then awaken in time to hear an upcoming beacon. How often the client station awakens is based on a variable called the listen interval and is usually vendor specific.
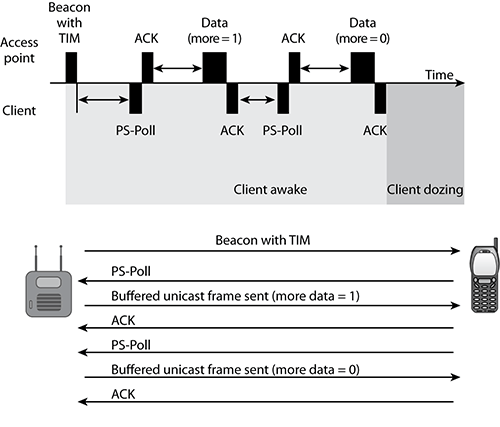
When the station receives the beacon, it checks to see whether its AID is set in the TIM, indicating that a buffered unicast frame waits. If so, the station will remain awake and will send a 20-octect PS-Poll frame to the access point. When the access point receives the PS-Poll frame, it will send the buffered unicast frame to the station. The station will stay awake while the access point transmits the buffered unicast frame. When the access point sends the data to the station, the station needs to know when all the buffered unicast data has been received so that it can go back to sleep. Each unicast frame contains a 1-bit field called the More Data field. When the station receives a buffered unicast frame with the More Data field set to 1, the station knows that it cannot go back to sleep yet because there is some more buffered data that it has not yet received. When the More Data field is set to 1, the station knows that it needs to send another PS-Poll frame and wait to receive the next buffered unicast frame.
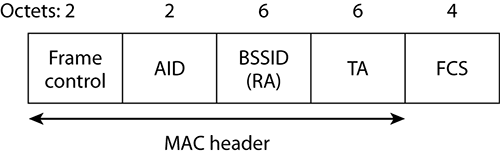
As shown in Figure 5-14, the PS-Poll frame consists of five fields. The BSSID (receiver address) is the MAC address of the AP that the client is associated with. The transmitter address (TA) is the MAC address of the station that is generating the PS-Poll frame. The AID is the association ID that was assigned to the station by the access point. In most frames, this field is actually the Duration value; however, in the PS_Poll frame, it is used to identify the ID of the station making the PS-Poll request.
Figure 5-14: PS-Poll frame
The IEEE 802.11e amendment introduced an enhanced power management method called automatic power save delivery (APSD). Two APSD methods are defined: scheduled automatic power save delivery (S-APSD) and unscheduled automatic power save delivery (U-APSD). These power management methods are discussed in Chapter 8. The Wi-Fi Alliance’s WMM Power Save (WMM-PS) certification is based on U-APSD. WMM-PS is an enhancement over the legacy power-saving mechanisms discussed earlier in this section. The goal of WMM-PS is to have client devices spend more time in a doze state and consume less power. WMM-PS also is designed to minimize latency for time-sensitive applications such as voice during the power-management process.
The legacy power-management methods have several limitations. As pictured in Figure 5-15, a client using legacy power management must first wait for a beacon with a TIM before the client can request buffered unicast frames. The client must also send a unique PS-Poll frame to the AP to request every single buffered unicast frame. This ping-pong power-management method increases the latency of time-sensitive applications such as voice. The clients must also stay awake during the ping-pong process, which results in reduced battery life. In addition, the amount of time that the clients spend dozing is determined by the vendor’s driver and not by the application traffic.
Figure 5-15: Legacy power management
The Control Wrapper frame was defined by the 802.11n amendment, which defined high throughput (HT) transmissions. The Control Wrapper is used to carry any other control frame, other than another Control Wrapper frame, together with an additional HT Control field. Figure 5-16 shows the Control Wrapper frame. The values of the Duration/ID field, Address 1 field, and Carried Frame Control fields are copied from the corresponding fields of the carried frame and used in the Control Wrapper frame.
The Carried Frame field contains the fields that follow the Address 1 field for the control frame that is being carried, with the exception of the FCS field. The FCS files of the Control Wrapper frame is a typical FCS field containing a 32-bit CRC, calculated over all the fields of the MAC header and the frame body, in this case the Carried Frame field.
Figure 5-16: Control Wrapper frame format

Two additional control frames are defined by the 802.11-2007 standard: CF-End and CF-End+CF-ACK. The CF-End frame, as shown in Figure 5-17, is a 20-octet frame that is used to indicate the end of a contention-free period.
Figure 5-17: CF-End frame format

The CF-End+CF-ACK frame, as shown in Figure 5-18, is also a 20-octet frame that is used to indicate the end of a contention-free period and acknowledge receipt of a frame. The CF-End+CF-ACK is structurally identical to the CF-End frame.
Figure 5-18: CF-End+CF-Ack frame format

Both of these control frames are defined for use with an optional medium access method known as Point Coordination Function (PCF). This access method is a form of polling. The access point performs the function of the point coordinator (PC). Because an access point is taking the role of the point coordinator, the PCF medium access method will work in only a basic service set (BSS). PCF cannot be utilized in an ad hoc network because no access point exists in an independent basic service set (IBSS). Because polling is performed from a central device, PCF provides managed access to the medium.
For PCF to be used, both the access point and the station must support it. If PCF is enabled, DCF will still function. The access point will alternate between PCF mode and DCF mode. When the access point is functioning in PCF mode, it is known as the contention-free period (CFP). During the contention-free period, the access point polls only clients in PCF mode about their intention to send data. This is a method of prioritizing clients. When the access point is functioning in DCF mode, it is known as the contention period (CP).
If you want to learn more about PCF, we suggest that you read the 802.11-2007 standard document. As we stated earlier, PCF is an optional access method, and as this book is being written, we do not know of any vendor that has implemented it.

If there are no vendors that have implemented PCF, how is it possible to receive CF-End or CF-End+CF-ACK frames? Technically, it is not. However, when a packet analyzer identifies a frame, it reads the contents of the Type and Subtype fields from the frame that is received, looks them up in a table, and displays the frame description from this lookup. Wireless transmissions are subject to many outside influences, and as such, sometimes frames become corrupted between when they are transmitted and when they are received. Stations will identify corrupted frames and retransmissions should enable the communication to be success. Packet analyzers are designed to listen and report what they hear, even if what they hear is corrupt. So, if any packet analysis or network analysis software indicates that you have received a contention-free frame, what you have actually received is a corrupted frame.
In this chapter, we discussed the purpose of control frames, the different types of control frames, and the tasks that each type of control frame performed. RTS/CTS and CTS-to-self frames are used to perform NAV reservation and to provide protection mechanism in mixed-mode environments. The ACK frame is one of the most commonly transmitted frames and is used to provide delivery verification by acknowledging the successful receipt of unicast frames. Block Acknowledgement Request frames and Block Acknowledgement frames improve channel efficiency by aggregating several acknowledgements into one single acknowledgement. PS-Poll frames aid with power conservation and the delivery of buffered unicast frames. Although defined by the 802.11 standard, contention-free PCF is optional and, to our knowledge, has not been implemented by any vendors.
Know the different control frame subtypes. Identify which frames are control frames vs. data or management frames. You should also be able to identify data and management frames; however, those frame types are covered in other chapters.
Describe carrier sense. You should be able to describe carrier sense and virtual carrier sense. You need to know how the Duration/ID field is used to perform NAV reservation.
Explain how and why protection mechanism is performed. Explain how, in a mixed-mode environment, RTS/CTS and CTS-to-self is used to allow different PHYs to coexist, along with how these techniques affect network performance.
Understand the use of acknowledgements and block acknowledgements. Understand how ACKs, BlockAckReqs, and BlockAcks are used to confirm the successful receipt of unicast frames.
Understand the use of PS-Poll frames. You should know how PS-Poll frames are used by stations that have Power Save mode enabled.
Know the different contention-free control frames. Know the two types of contention-free control frames, along with the optional medium access method known as Point Coordination Function (PCF).
802.11g Protected mode
acknowledgement (ACK)
association identifier (AID)
block acknowledgement (BA)
block acknowledgement request (BlockAckReq)
carrier sense
CF-End
CF-End+CF-ACK
clear to send (CTS)
Control frames
CTS-to-self
Duration/ID field
frame subtypes
frame types
mixed-mode
network allocation vector (NAV)
physical carrier sense
Point Coordination Function (PCF)
Power Save mode
protection mechanism
PS-Poll frame
receiver address (RA)
Request to send (RTS)
transmitter address (TA)
virtual carrier sense
1. ACK and CTS frames follow which interframe space?
A. EIFS
B. DIFS
C. PIFS
D. SIFS
E. LIFS
2. 802.11 collision detection is handled using which technology?
A. Network allocation vector (NAV)
B. Clear channel assessment (CCA)
C. Duration/ID value
D. Receiving an ACK from the destination station
E. Positive collision detection cannot be determined
3. What would cause an 802.11 station to retransmit a unicast frame? (Choose all that apply.)
A. The transmitted unicast frame was corrupted.
B. The ACK frame from the receiver was corrupted.
C. The receiving station was set to PCF mode.
D. The transmitting station will attempt to retransmit the data frame.
E. The transmitting station will send a retransmit notification.
4. A station has enabled protection mechanism and has to enable RTS/CTS to provide NAV reservation. During this process, which of the following frames are transmitted by the station? (Choose all that apply.)
A. RTS
B. CTS
C. DATA
D. SIFS
E. ACK
5. When Power Save mode is enabled, the station uses the TBTT to determine when to awaken so that it can listen for the frame, specifically looking to see whether its is set in the field.
A. Data, AID, TIM
B. Data, AID, ATIM
C. Beacon, AID, TIM
D. Beacon, AID, ATIM
E. Beacon, SID, TIM
F. Data, SID, TIM
6. While performing a packet analysis, you periodically see some CF-End frames along with some CF-End+CF-ACK frames. Why are these frames occurring? (Choose all that apply.)
A. These are corrupted frames.
B. You are running an IBSS network that has PCF enabled.
C. You are running a BSS network that has DCF enabled.
D. These are normal frames in a contention network.
7. Which of the following are protection mechanisms? (Choose all that apply.)
A. NAV back-off
B. RTS/CTS
C. RTS-to-self
D. CTS-to-self
E. WEP encryption
8. Control frames contain which of the following components? (Choose all that apply.)
A. Layer 2 header
B. Layer 3 header
C. Layer 2 trailer
D. Layer 3 trailer
E. Frame body
F. Data
9. The Type and Subtype fields are used to identify the function of the frame. The Type field is bits long, and the Subtype field is bits long.
A. 2, 2
B. 2, 4
C. 4, 4
D. 4, 8
E. 8, 8
10. During a packet capture, you see that the Barker_Preamble_Mode bit of the ERP information element is set to 1. What is the likely cause?
A. All nodes support ERP.
B. A station is not capable of using short preambles.
C. This is a setting that was manually configured on the AP.
D. A station is only capable of complementary code keying.
E. This is the default setting.
11. Which field in the MAC header of an 802.11 frame resets the NAV timer for all listening 802.11 stations?
A. NAV
B. Frame control
C. Duration/ID
D. Sequence number
E. Strictly ordered bit
12. Prior to using the Block ACK mechanism to transmit QoS data, which of the following is true? (Choose all that apply.)
A. The station must first check to see whether the peer station is capable of performing the Block ACK mechanism.
B. All stations are capable of performing Block ACK, so no validation is required.
C. Notify the station of the QoS mode being used.
D. Block ACK cannot be used with QoS data.
13. A station is operating in a mixed-mode environment and is using RTS/CTS to perform NAV distribution. Assuming that the station is not using block acknowledgements, when the station transmits the RTS frame, the Duration field will include the time necessary for which of the following to occur? (Choose all that apply.)
A. One SIFS
B. Two SIFS
C. Three SIFS
D. RTS transmission
E. CTS transmission
F. ACK transmission
G. Data transmission
14. What are the two reasons that 802.11 radios use physical carrier sense? (Choose two.)
A. Synchronize incoming transmissions
B. Synchronize outgoing transmissions
C. Reset the NAV
D. Start the random back-off timer
E. Assess the RF medium
15. The presence of what type of transmissions can trigger the protection mechanism within an ERP basic service set? (Choose all that apply.)
A. Association of an HR-DSSS client
B. Association of an ERP-OFDM client
C. HR-DSSS beacon frame
D. ERP beacon frame with the NonERP Present bit set to 1
E. Association of an FHSS client
16. Which of the following frames will receive an acknowledgment if the transmission is successful? (Choose all that apply.)
A. Simulcast frames
B. Multicast frames
C. Broadcast frames
D. Unicast frames
17. While performing a packet analysis, after the data transfer is complete, you notice that you captured three data frames and two ACKs. Which of the following can explain this capture? (Choose all that apply.)
A. One of the ACKs is providing a block acknowledgment for two data frames.
B. One of the frames was not received properly, so there was no ACK.
C. All frames were received properly; however, for some reason the packet analyzer did not hear the third ACK.
D. There is not enough information to explain this occurrence.
E. This is a normal packet capture.
18. A station is participating in a mixed-mode network and wants to transmit data. The station is configured to use CTS-to-self as its protection mechanism. Which of the following frames are transmitted by the station? (Choose all that apply.)
A. RTS
B. CTS
C. Data
D. ACK
E. SIFs
19. ACKs are required for which of the following frames?
A. Unicast
B. Broadcast
C. Multicast
D. Simulcast
20. During a basic RTS/CTS transmission, when a station sends. an RTS, the Duration/ID field notifies the other stations that they must set their NAV timers to which of the following values?
A. 213 microseconds
B. The time necessary to transmit the DATA and ACK frames, along with one SIFS
C. The time necessary to transmit the CTS frame
D. The time necessary to transmit the CTS, DATA, and ACK frames, along with three SIFS
1. D. ACK frames and CTS frames may follow a SIFS. LIFS do not exist.
2. E. 802.11 technology does not use collision detection. If an ACK frame is not received by the original transmitting radio, the unicast frame is not acknowledged and will have to be retransmitted. This process does not specifically determine whether a collision occurs. Failure to receive an ACK frame from the receiver means that either a unicast frame was not received by the destination station or the ACK frame was not received, but it cannot positively determine the cause. It may be because of collision or other reasons such as a high noise level. All of the other options are used to help avoid collisions.
3. A, B. The receiving station may have received the data, but the returning ACK frame may have become corrupted, and the original unicast frame will have to be retransmitted. If the unicast frame becomes corrupted for any reason, the receiving station will not send an ACK.
4. A, C. During the RTS/CTS process, the transmitting station will first transmit the RTS. After a SIFS, the intended recipient of the frame will transmit a CTS. After another SIFS, the station will transmit the data frame, and then following another SIFS, the intended recipient will transmit an ACK if the frame was received correctly.
5. C. When Power Save mode is enabled, the station uses the Target Beacon Transmission Time along with the Beacon frame’s time stamp to know when to awaken prior to the transmission of a Beacon. If the AP has cached frames for the station, it will notify the station by indicating the station’s Association ID (AID) in the Traffic Indication Map (TIM) field.
6. A. Contention-free (CF) frames occur if a Point Coordination Function (PCF) network is configured; however, to our knowledge, no manufacturers have implemented PCF. If PCF were implemented, it would require an AP to operate as the point coordinator, so PCF could not operate on an IBSS or ad hoc network. Since no manufacturers have implemented PCF, the only way these frames could be displaying in the packet analyzer is if other frames are corrupted and are being misidentified as PCF frames.
7. B, D. RTS/CTS and CTS-to-Self provide 802.11g protection mechanisms, sometimes referred to as mixed-mode support. NAV back-off and RTS-to-Self do not exist. WEP encryption provides data security.
8. A, C. Unlike management and data frames, control frames contain only a layer 2 header and trailer.
9. B. In any frame, the Type field is 2 bits long and identifies whether the frame is a data frame, management frame, or control frame. The Subtype field is 4 bits long.
10. B, C. If one or more associated NonERP stations are not capable of using short preambles, then the Barker_Preamble_Mode bit is set to 1. This is a setting that can also be manually set on many access points.
11. C. When the listening radio hears a frame transmission from another station, it looks at the header of the frame and determines whether the Duration/ID field contains a Duration value or an ID value. If the field contains a Duration value, the listening station will set its NAV timer to this value.
12. A, D. When a station intends to use the Block ACK mechanism, it must first check to see whether the peer station is capable of performing the Block ACK mechanism.
13. C, E, F, G. When RTS/CTS is enabled, the RTS frame performs a NAV distribution by setting its Duration field to the time it will take for the following to occur, in this order: SIFS, CTS transmission, SIFS, Data transmission, SIFS, ACK transmission.
14. A, E. The first purpose is to determine whether a frame transmission is inbound for a station to receive. If the medium is busy, the radio will attempt to synchronize with the transmission. The second purpose is to determine whether the medium is busy before transmitting. This is known as the clear channel assessment (CCA). The CCA involves listening for 802.11 RF transmissions at the Physical layer. The medium must be clear before a station can transmit.
15. A, C, D. An ERP access point signals for the use of the protection mechanism in the ERP information element in the beacon frame. Three scenarios can trigger protection in an ERP basic service set. If a non-ERP STA associates to an ERP AP, the ERP AP will enable the NonERP_Present bit in its own beacons, enabling protection mechanisms in its BSS. In other words, an HR-DSSS (802.11b) client association will trigger protection. If an ERP AP hears a beacon with an 802.11b or 802.11 supported rate set from another AP or an IBSS STA, it will enable the NonERP_Present bit in its own beacons, enabling protection mechanisms in its BSS. If an ERP AP hears a beacon from another ERP access point with the NonERP_Present bit set to 1, it also will enable protection mechanisms in its BSS.
16. D. Only Unicast frames will be acknowledged.
17. B, C. Every data frame needs to receive an ACK to acknowledge that the data was received properly. Since there are three data frames, there should be three ACKs. One possible reason is the one of these data frames was not successfully received by the intended recipient; therefore, there is no ACK. The other possible reason is that all of the data frames were successfully received and acknowledged. However, the station that was performing the packet analysis did not hear one of the ACKs.
18. B, C. When CTS-to-self is enabled, the transmitting station will transmit a CTS, wait for a SIFS, and then transmit the data frame. If the frame is received correctly, after another SIFS, the receiving station will transmit an ACK.
19. A. All unicast 802.11 frames must be acknowledged. Broadcast and multicast frames do not require an acknowledgement. Simulcast frames do not exist.
20. D. When the RTS frame is sent, the value of the Duration/ID field is equal to the time necessary for the CTS, DATA, and ACK frames to be transmitted, along with a SIFS before each of these frames.
